Logical ports are essential elements of computer networking, enabling communication between devices and applications. These virtual points, identified by numbers ranging from 0 to 65535, are categorized into two main types: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) ports.
Here is our list of the best free port scanners:
- Paessler Port Monitoring with PRTG EDITOR’S CHOICE A port range monitor that is part of a wider infrastructure monitoring system. Runs on Windows Server. The first 100 sensors are for free, download the 30-day free trial.
- ManageEngine OpUtils (FREE TRIAL) This combination of an IP address manager and a switch port manager is a paid tool but it has a free version. Available for Windows Server, Linux, and AWS. Access a 30-day free trial.
- Zenmap Free network security monitoring tool for Windows, Linux, BSD Unix, and Mac OS.
- PortChecker Free, online port scanning tool.
- Open Port Scanner Free port scanner from the Web Tool Hub website.
- IP Fingerprints network port checker Free online port scanning utility.
- Free Port Scanner Free downloadable port scanner that checks TCP ports and runs on Windows.
- Port Checker 1.0 Free port scanning utility that runs on Windows.
- What is my IP Port Scanner Free online port scanner offered by the WhatismyIP? website.
- TCPView A free process monitor that identifies port activity. Installs on Windows.
- Spiceworks IP Scanner A cloud-based console with an onsite agent that installs on Windows, Mac OS and Ubuntu and Debian Linux.
TCP ports establish reliable, connection-oriented communication, ensuring data is delivered accurately and in sequence, making them ideal for applications like web browsing (port 80) and email (port 25). In contrast, UDP ports provide connectionless communication with faster transmission, suitable for real-time applications like video streaming or DNS queries (port 53).
When an application or service on a device listens for incoming connections, it uses a specific logical port, known as an open port. For example, a web server typically listens on TCP port 80 (HTTP) or 443 (HTTPS). While open ports are necessary for enabling specific functionalities, they can also introduce vulnerabilities if left unprotected. Cybercriminals often exploit open ports to launch attacks, such as port scanning to identify vulnerable services, or by using these ports as entry points for malware.
Firewalls play a critical role in managing port security. They monitor and control incoming and outgoing traffic based on predefined rules, allowing only authorized traffic through specific ports. However, the presence of unnecessary open ports increases the attack surface, potentially exposing sensitive systems to unauthorized access or data breaches.
It is essential to periodically review and audit which ports are open on your computer or firewall. Understanding the role of each port helps you decide whether it should remain open or be closed to minimize risks. Closing unnecessary ports reduces exposure to potential threats, strengthening the overall security posture of your network and devices.
Port Checker Operating Systems Table:
| Port Checker | Linux | Windows | Mac OS | Online |
|---|---|---|---|---|
| Paessler PRTG (FREE TRIAL) | No | Yes | No | No |
| ManageEngine OpUtils (FREE TRIAL) | Yes | Yes | No | Yes |
| Zenmap | Yes | Yes | Yes | No |
| Port Checkers | No | No | No | Yes |
| Open Port Scanner | No | No | No | Yes |
| IP Fingerprints Network Port Checker | No | No | No | Yes |
| Free Port Scanner 3.5 | No | Yes | No | No |
| Port Checker 1.0 | No | Yes | No | No |
| What is my IP Port Scanner | No | No | No | Yes |
| TCPView | No | Yes | No | No |
| Spiceworks IP Scanner | Yes | Yes | Yes | Yes |
The best Free Port Checkers
Our methodology for selecting a free port scanner
We reviewed the market for port scanners and analyzed the options based on the following criteria:
- An option to scan ports on one device or many
- The ability to query a specific port or a range of ports
- A system that can scan computers across a network and not just its host
- A service that explains the protocol that maps to each examined port
- A way to extract a list of ports and their statuses as an export
- A free tool that can be used without having to pay
- A competent port mapping system that is worth the effort to install and set up
Using this set of criteria, we looked for port scanners that are free to use. We paid particular attention to monitoring packages that offer more utilities than just the port querying function.
1. Paessler Port Monitoring with PRTG (FREE TRIAL)
Paessler PRTG is an infrastructure monitor that covers network devices, network links, servers, and applications. The PRTG system is implemented by sensors. A sensor detects a specific attribute of system performance, or covers a particular hardware attribute.
Key Features:
- Two port mappers
- Network, server, and application monitor
- TCP ports
- Check a range of ports
- Operates per device
Why do we recommend it?
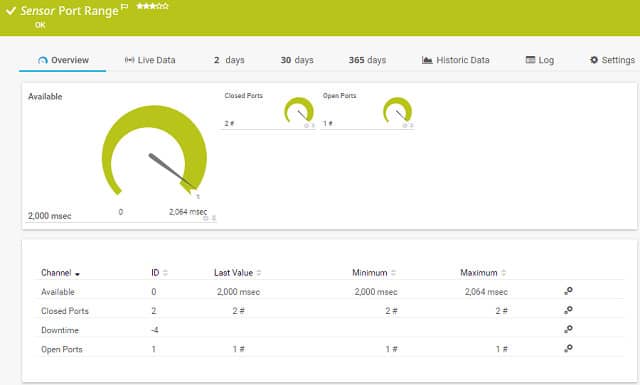
Port Monitoring is one of many network status indicators that you can get from Paessler PRTG. This package uses Ping and SNMP to discover and map the devices on a network, listing switch ports but not Transport Layer ports. Use the NetFlow sensors to look at traffic or the Port Scanner sensor to look for open ports.
The monitor includes two types of port sensors that will keep an eye on port activity for you. These are the Port sensor and the Port Range sensor.
The Port sensor is allocated to a given port number on a device. It will try to connect to that port and then report back on whether the port is open or closed and how long it took for the connection request to be served. This sensor only monitors TCP ports. You can choose whether or not to operate the sensor with Transport Layer Security. Including TLS will give you a more accurate report on the experience of secure connections when accessing that port.
As the name suggests, the Port Range sensor interacts with a given range of port numbers. This also deals only with TCP connections and doesn’t check on UDP operations to the ports on your devices. The port numbers that you want to check don’t have to be contiguous because you can choose to submit a list of port numbers instead of a range. The actions of this sensor are very similar to the Port sensor. It will access each port number in sequence and report on whether that port is open or closed and how long it took the device to accept a connection at that port. This sensor doesn’t give you the option of connecting with TLS.
Who is it recommended for?
Any business would benefit from the PRTG monitoring system because it can watch over the performance of applications, servers, and networks. The package contains a large number of sensors and you don’t pay anything to use 100 of them. Paid allowances start with 500 sensors.
Pros:
- Uses flexible sensors to monitor ping, as well as dozens of other metrics across networks, applications, and servers
- Designed to sweep larger networks
- Sensors can be customized and tailored to specific applications
- Pricing is based per sensor and allows both large and small businesses to scale within the PRTG ecosystem
- Supports autodiscovery, great for long-term monitoring
Cons:
- Feature-rich – takes time to learn all of the features and functionality the platform offers
Paessler PRTG is priced on the number of sensors that you want to monitor. The system is free for up to 100 sensors. If you use the Port sensor, you will need to create a new sensor instance for each IP address/port combination. So, you will use up your sensor allocation very quickly because each instance counts as a separate sensor for pricing purposes. You can get a 30-day free trial with unlimited sensors to assess the software. Paessler PRTG installs on Windows, or you can access it online as a cloud-based service.
EDITOR'S CHOICE
Paessler PRTG is our top pick for a free port scanner tool because this system is a much larger package of monitoring tools so you get to use other monitoring systems as well as a port mapper. Paessler sells PRTG, so businesses are expected to pay for the port scanner. However, the package includes a large number of sensors and if you only activate 100 of them, you never have to pay anything. That means you get a top quality network monitor with a port scanner for nothing.
Download: Daownload 30-day free trial
Official Site: https://www.paessler.com/download/prtg-download
OS: Windows Server
2. ManageEngine OpUtils (FREE TRIAL)
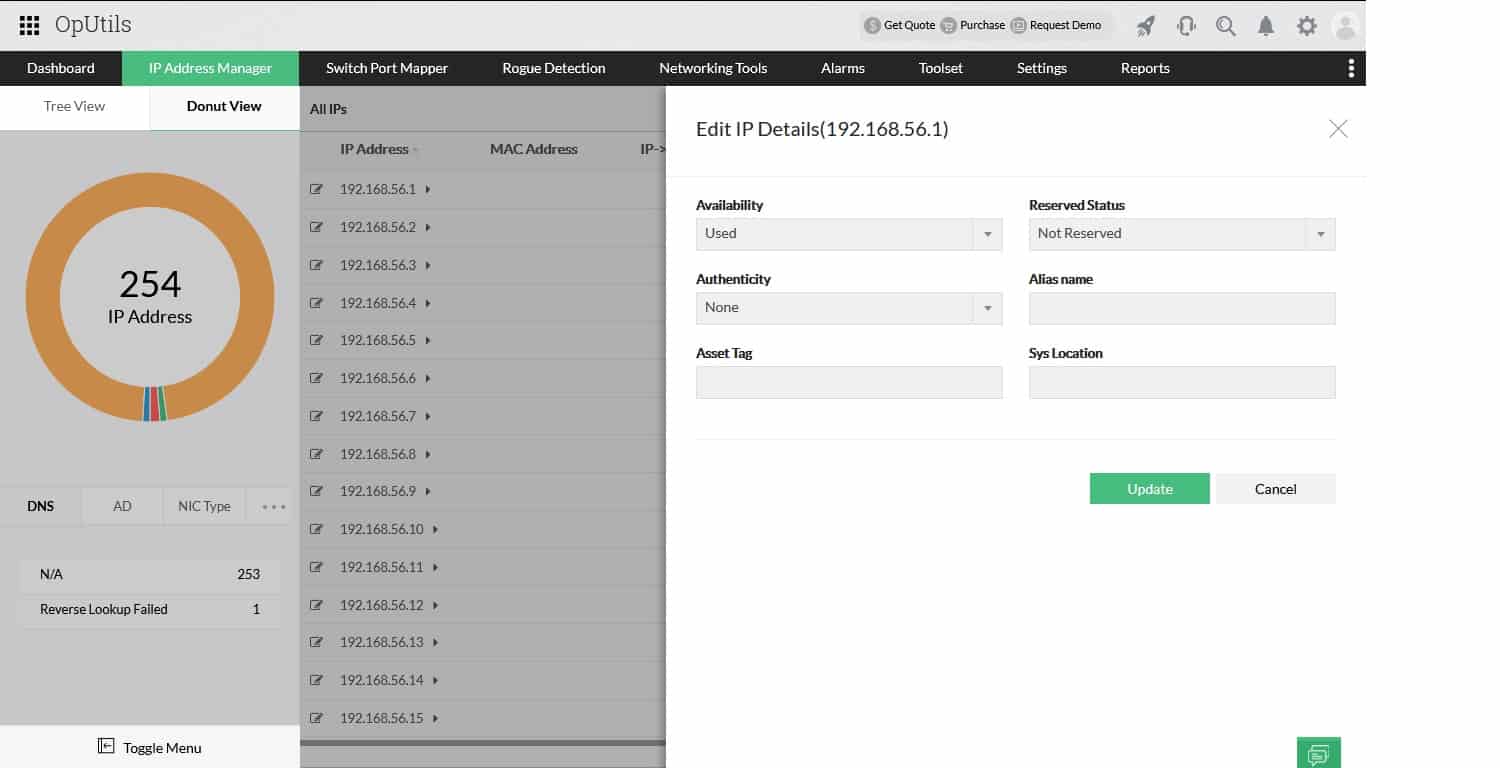
ManageEngine OpUtils is a combination of an IP address manager and a switch port mapper. That switch port system is a little confusing because that term doesn’t apply to the logical ports that port scanners deal with. Instead, this package looks at the cable sockets on a switch and details the device that is at the other end of the cable connected to each.
Fortunately, this package does also have a port scanner included. So, you can scan computer ports with a separate part of the package from the switch port mapper. Although the OpUtils package is not intended for use as a network monitor, the system does include a number of network monitoring tools and the port scanner is one of them.
Key Features:
- Scans a range of logical ports
- Details the protocol of each scanned port
- Indicates if the port is open
- Also offers physical port mapping
Why do we recommend it?
ManageEngine OpUtils provides scanning for all types of address issues, which includes IP Address scanning for IP Address management. The tool also includes a port scanner and a switch port mapper – which are two different types of ports. This is a top-of-the-line port scanner that can provide you details on the service behind each port.
A nice aspect of getting this port scanner is that it is just one part of a useful package of tools. You also get a network scanner and diagnostic tools. The IP address manager in the package provides reports on address usage, letting you see abandoned addresses, duplicate addresses, and rogue devices on the network.
Who is it recommended for?
This system is available in a Free edition, but that version won’t give you the port scanner – just an IP address scanner. You can use the paid version for free for 30 days. Otherwise, this tool doesn’t really qualify as a free port scanner tool.
Pros:
- Scans a range of ports for a given device
- Identified the device by IP address
- Shows ports that are open
- On-demand scanning
Cons:
- Doesn’t run continuously
There is one problem with the OpUtils system that means it only makes it onto this list by the skin of its teeth: this is a paid tool. There is a Free edition for OpUtils but that doesn’t include the port scanner. You can access the OpUtils for free, but only for a short period – ManageEngine offers OpUtils on a 30-day free trial. This software package installs on Windows Server and Linux. The paid version is also available as a service on AWS.
3. Zenmap
Nmap is a free network testing and security auditing tool. Zenmap is a user-friendly interface for Nmap. You can check on a lot of different factors about your computer and other computers connected to the same network with Nmap, not just ports and services.
Key Features:
- It can be installed on Windows, Linux, BSD Unix, and Mac OS
- Autodiscovery
- IP and port scanning
- Security monitoring
Why do we recommend it?
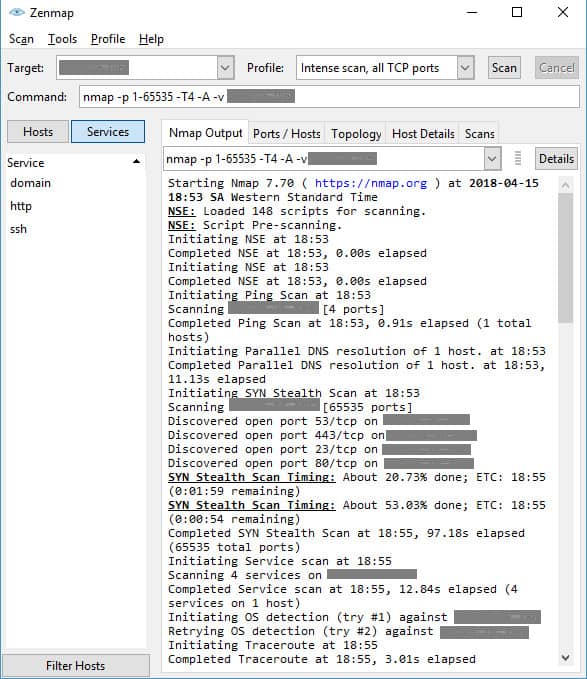
Zenmap provides an interface for the use of Nmap and also has a number of other utilities built into it. Nmap is very widely used by hackers and penetration testers for system reconnaissance and includes a port scan report option. It also provides version information on each system behind each open port.
The layout of the interface is not very sophisticated, but the system does its job well and offers you a range of tests to try. The utility will scan all of the ports on all of the computers connected to your network, or on your router. The follow-up tests are only performed on the open ports that Nmap discovers.
The standard test uses ping and a preliminary system check before scanning for open ports. However, there is a Ping-less alternative. You can perform a complete scan, scan all TCP ports, or scan all UDP ports. An intense scan uses a SYN Stealth methodology. These types of scans don’t get logged as connection attempts because the port never completes a connection sequence. An intense scan can take a long time — more than an hour and a half for one device.
Zenmap gives you a lot of different information types to investigate and it works for a single router or computer, so it isn’t just for network administrators.
Who is it recommended for?
The Nmap command has a lot of options and you need to study it for a while before you master it. Once you have that expertise under your belt, you can choose to use Nmap at the command prompt or through the Zenmap interface.
Pros:
- Doubles as a security tool, allowing administrators to discover open ports, and applications communicating over ports that are suspicious
- A massive open-source community is one of the most popular free network mapping tools available
- Offers a lighter CLI version called Nmap
- Can run standard ping checks as well as advanced SYN, TCP, and UDP scans
Cons:
- Zenmap can have a steep learning curve for new users
4. PortChecker
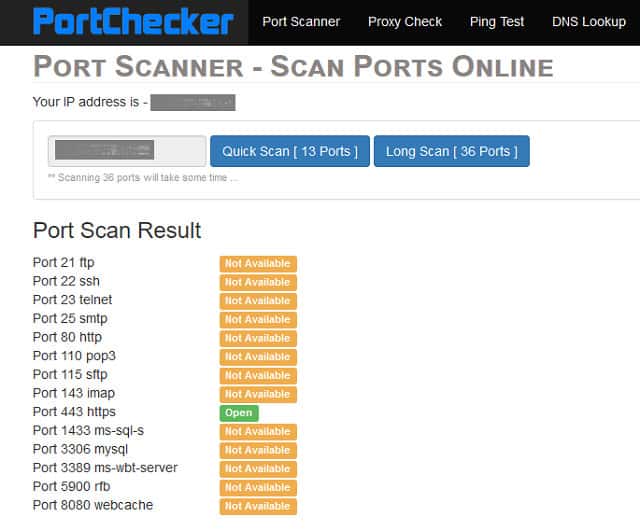
The Port Scanner page of the Port Checkers website gives you an online test of the ports on your computer. Not all of the ports are checked. The service will examine 36 of the well-known ports to see whether they are accessible from the internet and whether a service is running on each of them. A shorter scan will check just 13 of those ports.
Key Features:
- Online service
- Suggests port number ranges
- Focuses on important protocols
Why do we recommend it?
PortChecker is an online tool. It can only test internet-connected devices, not computers within a network. You don’t have to be the owner of the system that the tool probes – it can check any device that has an IP address on the internet and it only checks one port at a time.
The services that the port scanner checks include FTP data and control channel (ports 20 and 21) and also TFTP and SFTP ports. Ports for networking protocols SNMP, DHCP, and DNS are all checked as are communication and security services such as HTTPS, HTTP, SMTP, POP3, POP3 SSL, IMAP SSL, SSH and Telnet.
The results of the scan are shown in a table on the web page. In many instances, it is necessary to keep these essential ports open. However, in other cases, you will be able to close them down with your firewall. Examples of services that you might not use are the SMTP, POP3, and IMAP protocol. These are email protocols and only apply if you run an email agent on your computer. If you only use webmail, you don’t need to run these services.
Who is it recommended for?
This is more of a pen testing tool because it lets you see which ports can be accessed remotely and it doesn’t limit its probes to the computers of the requestor. As such, it could also be of interest to hackers. However, both of these user types would probably use Nmap.
Pros:
- No download or install required, PortCheckers is accessed through any web browser
- Can easily see which ports are open, closed, or filtered at a glance
- Can identify services on each port with a fair degree of accuracy
Cons:
- The test does not cover the full range of ports
- Not as comprehensive as other competing tools
There is no charge for using the Port Checkers Port Scanner.
5. Open Port Scanner
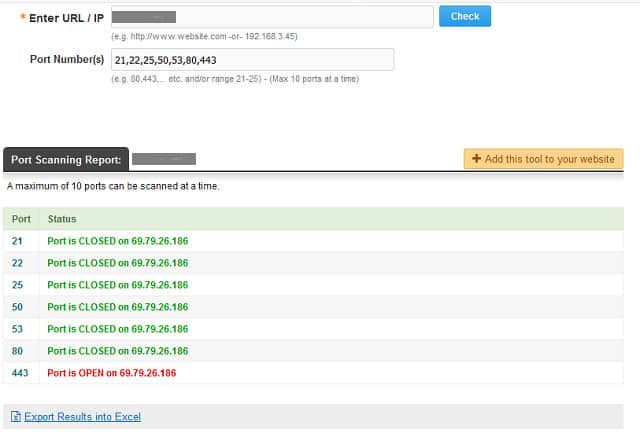
The Open Port Scanner is available at the Web Tool Hub website. This free online port checker lets you choose which ports to scan. You need to enter your IP address and then list the ports that you want checked. Each run of the scanner can only cope with 10 ports at a time.
Key Features:
- Delivered from a website
- A range or non-consecutive port numbers
- Identifies open ports
Why do we recommend it?
Open Port Scanner is available from WebToolHub and you can integrate it into your own site if you want to. The tool is similar to PortChecker because it is an external scan and won’t get inside your network to scan ports on your computers – it can only check your gateway router.
The results of the scan are shown in a table with the status of each port and its regular service listed alongside. Although it can be laborious typing in the port number, you can enter ranges, for example “21-29.” Results come back very quickly and you can export them to a CSV file.
Getting a full report on all of your computer’s ports would take a very long time, however, because the IANA port allocation list goes up to number 65,535.
The Web Tools Hub includes a long list of useful tools for online activities. These include an IP location checker, a backlinks checker, a WHOIS lookup facility, and a Ping test.
Who is it recommended for?
The typical user for this tool is the same as that for PortChecker. An advantage that this Web tool has over PortChecker is that it can report on 10 ports at a time rather than just one at a time. The tool does distinguish between UDP and TCP.
Pros:
- Good for checking a small range of ports quickly
- No download or install required, this tool is accessed through any web browser
- Is part of a larger toolset that offers IP geolocation analysis, backlink checker, and WHOIS lookups
Cons:
- Can only scan 10 ports at a time, not great for comprehensive tests
- Very limited reporting options
- Cannot sort port results based on current state or custom range
6. IP Fingerprints Network Port Checker
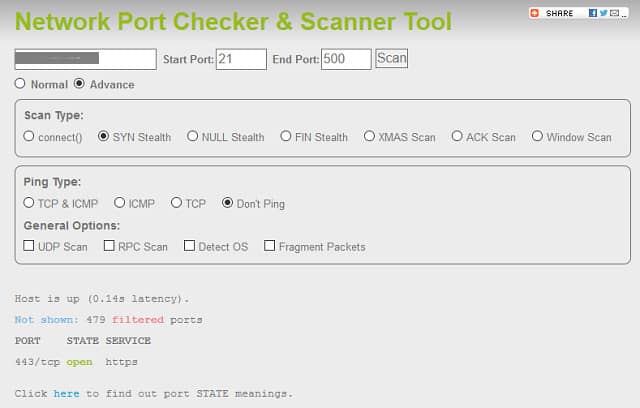
The IP Fingerprints website is another source for useful online tools and these include a Network Port Checker and Scanner. In this free online tool, you enter an IP address and a range of ports to check. This would be a lot more useful for getting through all of the ports on your computer because there is no limit on the number of ports you can scan in one go. However, the website text warns a port number range that exceeds 500 will take a very long time, and a large range will start a search that may never end. So, you will still need to run your full scan in segments.
Key Features:
- Autodiscovery
- IP and port scanning
- Security monitoring
Why do we recommend it?
IP Fingerprints Network Port Checker is another external scanner, like the PortChecker and Open Port Scanner systems. Realistically, this tool can only scan the ports of devices that are directly connected to the Internet. So, it will not scan the ports of computers within your network.
Despite this warning, I ran a search on ports 21 through 500. The results came back in less than a minute. Unfortunately, the system only reported on one of the four open ports that Nmap spotted. However, that may be because IP Fingerprints operates from the internet and Nmap works on the computer, behind the firewall.
This scanner claims to be able to see around firewalls. The Normal scan will check which ports are visible from the outside world and which are covered by the firewall. Advanced port scan options give you the choice of launching a connect() command test or a SYN Stealth test. SYN and connect() methods are particularly interesting because these are the avenues that hackers like to use in order to detect for services. The website claims that these can get around a firewall. The SYN method is a favorite strategy for DDoS attacks.
Other useful tools on the IP Fingerprints site include a geolocation tool and a WHOIS facility.
Who is it recommended for?
Like other online tools, this system will only scan the Internet and it can check on any computer, not just the ones that you own. This makes it a hacker or Pen tester tool. An important feature of this tool is that it can scan a range of up to 500 ports at a time.
Pros:
- Available online through your browser, no installation needed
- Can scan a custom range of ports
- Supports complex scans such as SYN, ACK, and FIN
- Can scan using fragment packet to avoid detection
Cons:
- A larger scan exceeding 500 ports can take a long time, in our test this took upwards of 15 minutes
- Lacks graphical reporting options
7. Free Port Scanner
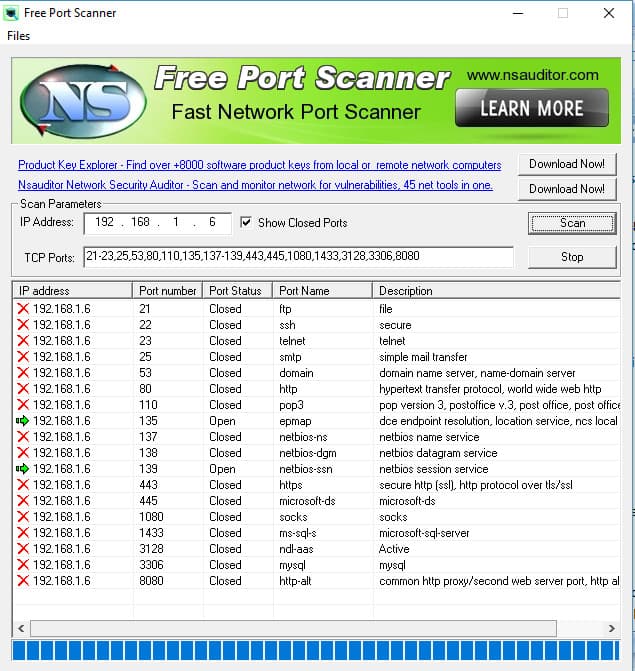
You need to download a program to run Free Port Scanner. It is available from Major Geeks and it runs on Windows. The creators of this program, Nsasoft, make no mention of the utility on their own website, so the only place you can get it is through third-party software download sites. The file that you download is an installer and it will also create an icon for the tool on your Desktop.
Key Features:
- Scans ranges or non-consecutive port numbers
- Shows open ports
- Explain port purpose
Why do we recommend it?
The Free Port Scanner downloads onto Windows and it lets you scan computers on your network. You can also use it to scan remote computers that are connected to the internet but not devices inside a remote private network. However, the tool is very useful as a quick, free port checker from within your network.
This utility allows you to scan ranges of ports, so you can get through the full list of port numbers in one run if you have time on your hands. The interface detects your IP address when it launches and a selected list of ports to look at is also provided by default. The scan takes a long time to perform if you request a wide range of port numbers. It is also very slow if you want to test the ports on another device, such as your WiFi router. So, if you ever wanted to scan all of the ports on your router, you would probably have to leave the program running all day. If you connect to the internet through a WiFi router, then you must enter your network IP address to scan your computer. You can scan the ports on your router by giving Free Port Scanner the public IP address that identifies you on the internet.
You can elect to show closed ports as well as open ones. There is no documentation with the tool and so there is no way of knowing which test method the utility uses. Free Port Scanner only tests TCP ports.
Who is it recommended for?
As it works from within the network, this is a much better option for network scanning than any of the Web-based systems that don’t use on-site agents. You can also use this system to scan remote, internet-connected devices. The software is only available for Windows.
Pros:
- A simple port scanner that is easy to use
- Automatically detects your IP address allowing for quick scans
- Includes a description of the service that port is open for
Cons:
- The interface is outdated and can be clunky when scanning all open and closed ports on a network
- Is slower when compared to other port scanners tested on this list
- Includes banner ads
8. Port Checker 1.0
The Port Checker 1.0 program can be downloaded from Softpedia. You need to be careful about downloading free utilities because they can sometimes be used as a front for a Trojan. Softpedia checks all of the code of the programs that it puts on its site, so you can have confidence that you are not downloading a virus.
Key Features:
- Portable executable
- Scans one port at a time
- Shows port status
Why do we recommend it?
Port Checker 1.0 is a simple port checker for internal scanning. However, you can also use it to check a port on a remote device that is directly connected to the internet. This tool can only check one port at a time, so it isn’t as good as the Free Port Scanner (above).
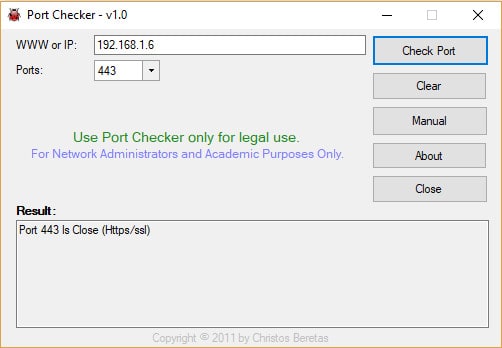
This free tool runs on Windows. There is no installer file for this tool: you just download a zip file with the executable in it. Extract the program and double-click on the file to run it. The program is very small and it can even be stored on and run from a USB stick.
The interface is very basic and easy to use. Just enter an IP address and select a port number from a drop-down list. A drawback is that you can’t scan for any port you like, just those in the list, and it isn’t possible to enter ranges of port numbers. If you have a wifi router, enter your network IP address to check ports on your computer and your internet IP address to get a report on a router port.
Who is it recommended for?
This tool downloads onto Windows but you can also save it onto a USB stick and use it from there to check on the computer to which you attach that device. The limit of one port at a time is annoying and reduces the attraction of this utility.
Pros:
- Very barebones, lightweight application
- Can be run from a USB, great to throw in a technicians toolkit
Cons:
- Cannot specify a port range
- Missing filtering features
- No auto-discovery of IP addresses
9. What is My IP? Port Scanner
What is my IP? is a very popular web service for discovering your IP address. The website has a number of other tools, including a port scanner.
Key Features:
- Online tool
- Free and paid versions
- Scans ranges or non-consecutive lists of ports
Why do we recommend it?
WhatIsMyIP Port Scanner offers external scans and can give you reports on one port number at a time or a group of ports that you select from a pick list. You need to pay in order to scan a range of port numbers. However, remember that this tool can’t get into your network.
This free online port checker has a number of useful features. First of all, it is fast: results for multiple port numbers come back within seconds. You can enter ranges of port numbers and create custom lists, although those two features are only available to the site’s paying members.
What is My IP has come up with a very nice free utility that gives you the opportunity to check a single IP address, but it has a unique option that no one else in the market seems to have thought of. It offers scans on themes of ports and services. This is called a “package.” For example, you can choose the Games package and then the test will include ports used by the major online gaming platforms. Other package options include Basic, which checks ports for things like email and FTP; Web, which includes HTTP, HTTPS and FTP (again); and Malicious, which looks at ports known to have been used by malware and hackers.
Who is it recommended for?
The WhatIsMyIP website is used by members of the public to check whether a proxy or VPN is in place. It shows what address the requestor is represented by and what geographical information is attached to it. This port scanner is an additional service for users of the IP address checking service.
Pros:
- Very fast for a web-based port scanner
- Uniquely scans for themes of port ranges based on popular games and applications
- Can scan based on single address or custom range of ports
Cons:
- Not a viable option if you’re unable to access the internet from your testing location
10. TCPView
TCPView is available as a free program to download onto Windows. This port scanner takes a different perspective from all the other programs in this list. Rather than looking at the ports and then checking whether a service is active on each, this system looks at all of the processes running on the computer, lists those associated with ports, and lists the port number. This approach gets you a lot more details than the external scan. For example, the other scanners didn’t notice ports above the “well-known” range even through some of the scanners claimed to be checking all ports.
Key Features:
- Scans UDP as well as TCP
- Process list
- Identifies ports per process
Why do we recommend it?
TCPView is a free tool from Microsoft and it provides a list of all processes that are running on a computer. Those processes that are engaged in communication across the network or the internet have the details of the correspondent on their list entry. This also shows the local and remote ports involved in transmissions.
TCPView includes processes listening at ports and the display is refreshed every second. You can slow down this snapshot rate and lengthen the interval to 2 seconds or 5 seconds. When new processes are encountered, they go into the list in a green-colored record. Processes that end stay in the list briefly with a red-colored record. Processes with changed statuses are colored yellow.
The display also shows the number of packets and the quantity of bytes of data sent and received on each port. Despite its name, TCPView also covers UDP ports.
Who is it recommended for?
This is an on-board utility and it will tell you what the computer that the software runs on is doing. It isn’t a networked tool, so you can’t check on the ports of remote computers. You will see the ports in use on remote computers if they are communicating with the host computer.
Pros:
- Scans local processes and identifies ports associated with those services
- Built with troubleshooting in mind, the tool provides details about services, protocol, remote address, and wait status
- Is lightweight, can run very quickly without using a large number of resources
- Uses color coding that makes it easy to identify open ports
Cons:
- Has a steeper learning curve for non-technical users
- Could use better reporting functionality
11. Spiceworks IP Scanner
The Spiceworks IP Scanner has two elements. The dashboard for the tool is online, but you need to install a small monitoring program onto your computer to get it working.
Key Features:
- Requires on-site agent
- Device details
- Lists all open ports
Why do we recommend it?
Spiceworks IP Scanner is an online tool. You download an agent onto one device and get network data for all devices on your network, which includes a list of open ports. The agent provides more detailed information, such as a software inventory, about devices that have agents running on them.
The agent on your computer sends gathered data to the cloud server. All communications between the agent and the server are encrypted and you need to sign up and create a user account in order to log in and see your scan results.
The installed program will run on Ubuntu and Debian Linux and also on Windows and Mac OS. The free network tool gives you plenty of information about all of the computers in your network, or just your computer if you don’t have a network. All of Spiceworks’ tools are free of charge, but they are ad-supported.
Once you have installed the program and created your account, you log into the dashboard through a browser. The system cannot be accessed through a Safari browser. The IP scanner will search your network and discover all of the devices connected to it. For each device, it will report the MAC address, see the IP address, the hostname, the manufacturer, the operating system, and a list of open ports.
If you don’t have a network, you may prefer to use the Spiceworks Port Scanner and Tester. This is a free online tool and it can be accessed from any operating system without having to install software. The Port Scanner checks the status of a number of the ports on the computer for which you enter the IP address.
Who is it recommended for?
This is a good choice for a small business, particularly an owner-managed enterprise where no technical skills are available. The tool can show mobile devices that are on the network as well as desktops. You don’t get much detail on the open ports of each device.
Pros:
- The agent can be installed on Windows, Linux, or Mac
- Better tool for long-term monitoring
- Great interface makes it easy to view all ports, services, and their current state
Cons:
- Installation requires a local install and the use of the online browser, making installation longer than other tools
- Includes banner ads
- Does not support the Safari browser
- Won’t work offline
Online port scanner or installed: which is better?
As you can see from our list of recommended port scanners, half of them do not need to be installed on your computer because they are available on websites. This is a good strategy because the position of the scanner outside of your system gives you a proper view of what hackers and the outside world can see about your network, be it a home network or a business service.
Switching to a computer-based port scanner can help as well because it shows you the many processes listening on computer ports. As you can see from the examples of checker output shown above, the remote checks find fewer services on ports than the computer-based scanners can detect. This shows that your firewall is working to mask the security weaknesses of services running on your computer. So, it is probably better to use one of each of these types of systems — both online and installed.
Free online port checkers
Some other free online port checkers that you could try are:
- Portchecker.io
- CanYouSeeMe
- You Get Signal
- Ping.eu Port Check
- Pentest Tools TCP Port Scan with Nmap
- T1 Shopper Online Port Scan
These online services are very easy to use. They are ideal for small businesses that can’t afford to pay for consultants or external services to monitor their security from outside of the network.
What are ports?
If you are new to networking technology, a little background on ports should help you out. Ports are addresses, and a large number of them have specific purposes that seasoned networking specialists can recall off the top of their heads.
The allocation of port numbers to specific services is a global standard operated by the Internet Assigned Numbers Authority, which is also known as IANA. This organization is also responsible for distributing IP addresses and preventing duplication. You can get a look at the IANA register of port numbers at their website.
The very long list of port numbers is divided into three sections. The first 1024 ports (numbers 0 to 1023) are called the “well-known ports” because the long running services that everybody uses, such as HTTP and IMAP, all have their port numbers within this range. Not all of the numbers in this section are in use. A service used by many different applications, such as FTP or the domain name service (DNS), will be in the well-known range of ports numbers.
The next range of port number goes from 1024 to 49151. These are the registered ports. Proprietary applications will be allocated a port number in the registered range. For example, the Steam online game platform is assigned port number 1725.
All of the port numbers from 49152 up to 65535 are available for any programmer to use. These are called “private” or “ephemeral” ports. Often, a service will listen on a well-known port, but then switch to a private port by agreement with the connecting client. This enables the daemon listening at that well-known port to be available for other connections while the first transaction is ongoing.
So, even though a particular service operates on one specific port, it can also arrange to run on another port high up in the ephemeral port number range.
The exchange of data over a network can either follow a connection-based system, called TCP (the Transmission Control Protocol) or a connectionless model, called UDP (the User Datagram Protocol). Most scans use the TCP system because UDP has no connection control and so expects no acknowledgements or error messages back. Those responses from the server make port scanning possible.
List of ports
Some of the most widely used ports are listed in the table below together with the service that they cater to.
| Port Number | Service |
|---|---|
| 20 | FTP (File Transfer Protocol) data channel |
| 21 | FTP (File Transfer Protocol) control channel |
| 22 | SSH (Secure Shell) |
| 23 | Telnet |
| 25 | SMTP (Simple Mail Transfer Protocol) |
| 37 | Time Protocol |
| 43 | WHOIS |
| 53 | DNS (Domain Name System) |
| 69 | TFTP (Trivial File Tranfer Protocol) |
| 79 | Finger Protocol |
| 80 | HTTP (Hypertext Transfer Protocol) |
| 88 | Kerberos |
| 109 | POP2 (Post Office Protocol v 2) |
| 110 | POP3 (Post Office Protocol v 3) |
| 115 | SFTP (Secure File Transfer Protocol) |
| 123 | NTP (Network Time Protocol) |
| 143 | IMAP (Internet Message Access Protocol) |
| 161 | SNMP (Simple Network Management Protocol) |
| 162 | SNMP (Simple Network Management Protocol) Trap |
| 179 | BGP (Border Gateway Protocol) |
| 194 | IRC (Internet Relay Chat) |
| 443 | HTTPS (Hypertext Transfer Protocol Secure) |
| 464 | Kerberos reset password |
| 465 | SMTPS (Simple Mail Transfer Protocol over SSL) |
| 514 | Sylog |
| 530 | RPC (Remote Procedure Call) |
| 543 | Kerberos login |
| 544 | kshell (Kerberos remote shell) |
| 554 | RTSP (Real Time Stream Control Protocol) |
| 993 | IMAPS (Internet Message Access Protocol over SSL) |
| 995 | POP3S (Post Office Protocol 3 over SSL) |
Open and closed, blocked and unblocked ports
An “open” port is not the same as an “unblocked” port, and a “closed” port is not the same as a “blocked” port. An open port simply has a process associated with it. These processes are part of a service. They are called “daemons” and they run continuously in a very small loop checking to see if a packet addressed to a specific port has arrived at the computer. This is why it is important that port numbers are universally known. The well-known ports mean that anyone writing their own version of a particular service, such as an FTP program, just has to check for packets arriving for that service’s port number.
The program will only break out of the loop and continue down the lines of code when a message arrives with the right port number. So, if a port is open, that means that there is a daemon checking for that port number over and over again. To close a port, you just stop that process. A “closed port” just means that there is no repetitive program looping around waiting for that port number to appear in a packet.
A “blocked port” may be open or may be closed. The block is performed by a firewall. If there is a daemon running and waiting for a particular port number, it will be waiting forever if the firewall refuses to allow through packets addressed to that particular port number. In that example, the port is open, but blocked. To unblock that port, you would have to adjust your firewall rules to allow through traffic addressed with that port number.
If the process that waits for a message with a specific port number is on a computer behind a router, you may have to instruct the router to direct the traffic for that port. This process is called “port forwarding.”
Types of port scans
Basic port checkers
A standard port scan sends out a connect() command to every port number in turn. This command only works with TCP ports. If an acknowledgment to a request to connect to one port number receives a reply, the scanner registers that the port is open, meaning there is a daemon listening.
If a hacker wants to try to get into your computer, there is no point sending his intrusion attempts to a port number that does not get a response from a daemon. It would just be a waste of time.
Hackers might favor particular port numbers. Some viruses have a specific port written into them, and antivirus companies have learned them. In those cases, firewall software gets updated and the success of the virus comes to an end. The hacker will then try to find a different port and rewrite the virus. Then the virus will probably earn a different name from the antivirus community.
Remember that with many services, the initial connection takes place on a well-known port and then gets transferred to an ephemeral port number. As viruses are automatic processes, each will have its favored ephemeral port. So, if you discover that one of the private ports is open, this could be an indication that your computer is already infected.
A strobe
When a scan just focuses on a range of port numbers rather than all 65536, that search is called a “strobe.” Making regular scans of all ports can raise an alarm, so limiting the scan to a small number of ports can keep the scan under the radar. Each connection request gets logged, so a sudden burst of connection requests shows that something untoward is going on. Networks that run intrusion prevention systems will automatically lock out all activity from a particular IP address if port scanning is detected.
Stealth scan
A stealth method that some hackers use to avoid getting blocked out is to perform the scan very slowly over a number of days. Stealth scans tend to be strobes because limiting the number of connection requests to just the ports that the hacker knows is a good bet that cuts down the time that a slow scan can take.
An incomplete connection request or connection requests spread over several packets are other stealth methods.
SYN scan
The connection process consists of three messages. The client sends a SYN message and the server sends back a SYN-ACK. The client replies to the SYN-ACK with an ACK. This three-phase process is very useful to hackers and a SYN flood is commonly used as a denial-of-service attack. This is because the server will wait for a short period of time for an ACK to come back. That short wait period, combined with a large number of SYNs, can create enough of a delay that genuine requests time out before being served.
A SYN flood would register an alarm on a computer. However, just one SYN on each port doesn’t even get logged. This is because most systems only log successful, but subsequently inactive connection request that are made up of the SYN/SYN-ACK/ACK process carried out by the TCP connect() command.
So, the SYN scan sends out a SYN message. If it receives back a SYN-ACK, it knows that port is open. If no SYN-ACK comes back, it knows that port is closed. In both instances, it never sends back an ACK message.
Fragmented packet scan
Some intrusion detection systems and firewalls can be duped by fragmented packet scans. This is because many of those systems operate on the transport layer, looking for “signatures”, or patterns of behavior in incoming packets. Working at the transport level means that the detection rules of a firewall or IDS would not recognize a fragmented request.
However, the split request is united by TCP when preparing messages to pass to the application. So the parts of the request get through because they don’t look to the firewall like a connection request. However, by the time the request reaches the daemon, it is a fully recognizable connection request.
Some firewalls on the market will examine the packets in their reconstituted form. In those instances, this packet fragmentation technique is trounced. However, buffering and ordering of packets by the firewall is rare because those actions slow down the network.
NULL scan
A NULL scan is a way to test for UDP ports. In fact, it is just about the only way to check UDP ports because the whole purpose of UDP is that there are never any responses sent back by the protocol. However, sending an empty UDP “datagram” may or may not get an error response from the listening process. It is much more likely to provoke a message from another protocol if that port is closed. This is the ICMP protocol, which has the capacity to send back a “port unreachable” message.
The same technique can be used to test TCP ports with an empty TCP “segment.” So, any NULL message that doesn’t get a “port unreachable” response indicates that the port is open. However, network monitoring software and system administrators have got wise to this trick and most network systems now limit ICMP “port unreachable” messages to a certain number per day, or just send one out every nth response. So the lack of a response doesn’t always mean that a port is open, and this method of scanning has become unreliable.
XMAS scan
A TCP segment contains a shorthand section of bits that are set to 1 to indicate certain conditions of the connection requests. In a TCP NULL scan, all of those bits are set to zero, which tells the server nothing. In an XMAS scan, all of those bits are sent to 1, which is gobbledygook because some bits are mutually exclusive.
The XMAS scan should provoke an error message from an open port and silence from a closed port. However, this type of scan doesn’t always produce correct results because an error message may have been sent but got lost on the way. Also, different operating systems have different policies in response to the XMAS scan, so such packets don’t always send back error messages even if the port is open.
FIN scan
A FIN scan is similar to the NULL scan and the XMAS scan because it is designed to be intentionally wrong and provoke an error message. A FIN TCP message closes a connection, so if it is sent to a port on which no connection exists, it is clearly an error.
A peculiarity of this message type is that it is dealt by the operating system and not by the daemon on the port. The convention is that if a FIN message is sent to an open port to which there is no connection, the daemon ignores it, and sends no response. However, if a FIN message is sent to a closed port, the operating system will send back a RST message. No response to a FIN means that the port is open and an RST means that the port is closed.
ACK scan
This is another malformed request technique that provokes an RST response from the operating system on behalf of closed ports and silence from open ports. You will recall that the ACK message is the last stage in the SYN/SYN-ACK/ACK process of establishing a connection under TCP rules. So, an ACK arriving before a SYN is just nonsense and an open port will ignore it.
Port scanning issues
You will come across a few other settings in port checkers that are additional features rather than scanning techniques. These include Ping, Traceroute, RPC checks, operating system fingerprinting, and DNS resolution checks.
These are nice features and they indicate that the producers of that port checker are trying to create a network traffic analyzer rather than just a straightforward port scanner.
Port mapping, port forwarding, port triggering
Port mapping is a function of routers that practice network address translation (NAT). NAT enables several computers on a network to use the same public IP address on the internet. The network gateway identifies each computer on the network by a port number, which it tacks onto the end of the IP addresses on outgoing messages. When a response comes in to that port number, the gateway knows which computer the message is meant for.
Port mapping is a form of NAT, which is called port address translation (PAT). This enables computers on the network to send out requests with a port number on the end of the source address. The gateway than replaces that port number with a substitute that represents the network address of the originating computer and the port number on the original request. Port mapping is also called port forwarding.
Port triggering enables a computer on a network to allocate an extra port number on the NAT gateway to itself. An example of this is the port triggering needed for the Internet Relay Chat (IRC). When a computer on the network contacts a remote host for an IRC session it has to send the request to a specific port number, the host will connect back on a different port number (113) for verification. So when the original request goes out, the sender notifies its gateway that it wants to receive traffic coming in on port 113. When the gateway gets a message to that port number it forwards it on to the network computer, preserving the 113 port number in the header. This access is only active for a short period.
Port checker options
Sometimes, it takes a thief to catch a thief, so thinking like a hacker and employing “white hat” hacking techniques will help you keep your computer and your network secure. Try out a free port checker to get an idea of services that could provide entry points for hackers. Remember to try both an installed program and an online service to get a complete overview of your port activities.
Port scanner FAQs
What are closed and open ports?
A port number is like an apartment address in a building. While the IP address gets a packet to a computer, a port number identifies the process that the packet is intended for. Constantly running processes, called daemons check on the arriving packets to see if there is one intended for them and that is indicated by the port number. If a daemon is running for a specific port number, that is called an open port. If there is no daemon running for that port number, it is a closed port.
How do I scan for open ports?
Use a port scanner to check for open ports. This tool sends a packet to a specific UDP or TCP port and checks on the response. It is like Ping only to a specific port rather than just to the computer.
What Is an Open Port Checker vs. Open Port Scanner?
A port scanner will look at all of the ports on a computer to see whether they are open or closed. A port checker looks at the ports on a firewall or gateway from outside of the network to see whether traffic to each port is being forwarded on to computers within the network.
What ports do hackers use?
Hackers usually focus on the ports that handle specific protocols because they structure their attacks on particular protocols. So, TCP port 21 is a big target (FTP) as are TCP ports 22 (SSH), 23 (Telnet), 25 (SMTP), and 110 (POP3). TCP and UDP ports 53 (DNS), 135 (RPC), and 443 (HTTP) are also frequently targeted.
How do I check if a port is open on Windows 10?
To see all ports on a computer running Windows 10:
- Type cmd into the Start menu search field
- Click on Command Prompt Run as administrator in the search results
- At the command prompt, type netstat -ab
- Look through the results of the command. Ports marked as LISTENING are open
Further Reading
Comparitech networking guides
- Best network intrusion detection tools
- Best packet sniffers and network analyzers
- Best free bandwidth monitoring software and tools to analyze network traffic usage
- LAN monitoring tools
- The definitive guide to DHCP
- The definitive guide to SNMP
- The ultimate guide to mobile device management (MDM)
- The ultimate guide to BYOD
- Top server management & monitoring tools
- The best free NetFlow analyzers and collectors for Windows
- Best free network vulnerability scanners and how to use them