Here is our list of the best MDM software solutions:
- NinjaOne Mobile Device Management EDITOR’S CHOICE This MDM is part of a cloud platform of remote monitoring and management services and it will manage, monitor, and protect mobile devices running iOS and Android. Get a 14-day free trial.
- Kandji (FREE TRIAL) This cloud-based package is an Apple device management solution, handling macOS, iOS, and iPadOS devices. It provides automation and security features that streamline deployment and compliance without compromising confidentiality Start a 14-day free trial.
- ManageEngine Mobile Device Manager Plus (FREE TRIAL) A complete enterprise device management package with both on-premises and cloud-based versions. Start the 30-day free trial.
- Ivanti Neurons for MDM This package was originally called MobileIron and was ranked as a groundbreaking mobile device management system. It still provides an efficient mobile and desktop management system under the Ivanti brand.
- Citrix Endpoint Management If you are looking for XenMobile, this is it. Citrix has integrated its MDM package into the full endpoint system that relies on virtualization.
- Scalefusion This cloud-based endpoint and mobile device management package includes monitoring and security services as well as onboarding and content hosting.
- Samsung Knox Mobile An affordable fleet management system for Samsung devices. It manages devices running Android or ChromeOS.
- Miradore Mobile Device Management This cloud-based mobile device manager provides controls for devices running Windows, macOS, iOS, and Android.
- Omnissa Workspace ONE Mobile device management solution that can configure policies for devices remotely, automatically deploy applications, and more.
- BlackBerry Unified Endpoint Management Solution design that supports Windows, macOS, iOS, Android, and Chrome OS.
- SureMDM This cloud-based package provides security, content, and application management for mobile devices with options for kiosk mode device configurations.
- SOTI MobiControl Endpoint management software that supports Windows XP, Windows CE, Mac OS, iOS, and Android.
- IBM MaaS360 Enterprise mobility management solution with real-time data usage monitoring, application updates, endpoint device malware detection, and more.
- Cisco Meraki Includes a container system to deliver apps to user-owned devices and also has loss protection procedures.
- Jamf Now A cloud-based service that manages iOS devices.
Mobile Device Management (MDM) solutions are security tools designed to help IT teams manage, monitor, and secure employees’ mobile devices that access organizational data. As mobile devices like smartphones, tablets, and even laptops become integral to modern work environments, MDM solutions are essential for protecting sensitive company information.
MDM platforms enable IT administrators to control mobile endpoints through a centralized system. Key functions include device enrollment, ensuring that every device connecting to corporate networks is registered and adheres to company policies. They also support device configuration, allowing consistent settings and permissions across all devices.
Security features are a cornerstone of MDM, with capabilities such as remote locking and wiping to protect data on lost or stolen devices. Other essential features include software distribution for streamlined updates, enforcement of security policies, and data containerization, which separates personal and corporate data on devices. MDM solutions also typically facilitate VPN setup, ensuring secure connections for remote workers.
In addition, MDM platforms provide comprehensive reporting and analytics tools. These dashboards offer insights into device usage, security compliance, and potential risks, helping organizations maintain control over their mobile environments. By supporting these functions, MDM solutions enable businesses to enhance security while accommodating the increasing demand for mobile flexibility in the workplace.
What kind of MDM do I need?
Mobile Device Management systems range in size and complexity. A basic MDM simply enables a central administrator to provision a fleet of devices with a bundle of software. More complex systems provide device tracking, remote locking, and wiping functions. Top-of-the-line MDM systems provide full modules for Mobile Content Management, which provides security for corporate data, and Mobile Application Management, which is concerned with the software on devices, narrowing the definition of MDM to device security.
Other considerations when looking for MDM solution lie with device ownership. Are you only interested in fleet management of corporate-owned devices or do you want to be able to deliver business system access to user-owned devices? MDM can also extend to “kiosk” devices, which are tablets or smartphones that are locked into limited functions, usually for use in retail spaces.
If you want to limit the functions of a mobile device or deliver corporate data and system access to user-owned devices, you should look at virtualized desktop systems or containerized delivery methods. These prevent any business-owned data from being stored in the operating system of the device.
The two key factors you need to consider are ease of access to corporate facilities while simultaneously ensuring the confidentiality of corporate data.
The best MDM solutions
Our methodology for selecting a mobile device management system for your business
We reviewed the market for mobile device management software and analyzed tools based on the following criteria:
- An option to set up a fleet of devices in bulk
- Device tracking
- Device blocking and wiping functions
- Device performance monitoring
- Options for IoT device management
- A free trial or a free demo for a risk-free assessment opportunity
- Value for money in a system that provides a full mobile device management service at a fair price
With these selection criteria in mind, we identified a number of systems that perform onboarding, tracking, and monitoring of mobile devices.
1. NinjaOne Mobile Device Management (FREE TRIAL)
The NinjaOne Mobile Device Management system is built into the NinjaOne remote monitoring and management cloud platform. This system is suitable for use by managed service providers because it has a multi-tenant architecture that keeps the data of MSP clients separate. However, the platform can also be used by IT departments.
When we tested NinjaOne Mobile Device Management we found the following key features
Key features:
- Creates a unified endpoint management service
- Security features include locking and wiping
- Passcode resets and access restrictions
- Mobile application management
Unique feature:
This unit adds mobile device management to the endpoint management services in the NinjaOne platform. This creates a unified endpoint management package that covers devices running Windows, macOS, Linux, iOS, and Android. The cloud platform also provides software distribution and patch management.
Why do we recommend it?
The NinjaOne Mobile Device Management system expands the RMM to mobile devices, which is particularly important for businesses that have roaming employees. As managed service providers for a large share of NinjaOne’s customer base, the ability to offer more services improves MSP marketability and so also makes the NinjaOne package more attractive.
While the main functions of the RMM include software deployment, that translates to mobile application management on devices running iOS and Android. That function doesn’t just enable administrators to add or remove approved apps from mobile device but it also enables devices to be locked down, preventing users from installing their own favorite but unapproved apps.
Security features include tracking plus locking and wiping for lost or stolen devices. Mobile content management provides secure delivery of corporate data in files to mobile devices. All of these functions can be managed by the technicians of MSPs on behalf of clients.
In addition to the endpoint management services in the RMM package, you get automated system discovery, documentation, and monitoring. The RMM includes an alerting mechanism that triggers when performance issues arise. This means that technicians can assume that everything is OK if they don’t hear otherwise. The RMM console can be setup to forward alerts by email, SMS, push notification, or Slack, PagerDuty, or Teams messages.
Who is it recommended for?
This system is suitable for managed service providers to look after the mobile devices of their clients and for IT departments that want to manage their own systems in house. The tool is hosted in the cloud and it can manage multiple sites within one account, so it is a good choice for multi-site businesses.
Pros:
- Centralizes the management of all types of endpoints
- Controls the distribution of files to mobile devices
- Offers options such as kiosk mode for retail devices
- Remote screen viewing for troubleshooting devices
Cons:
- No public price list
NinjaOne is a cloud-based system, so you sign up for the package at the company’s website rather than downloading any software. You can assess the service with its mobile device management unit with a 14-day free trial.
2. Kandji (FREE TRIAL)
Kandji.io specializes in the management of Apple devices. This includes desktop Macs and mobile devices. The fleet management features in the package include onboarding systems and update management.
When we tested Kandji we found the following key features.
Key features:
- Automated Device Management: Streamlines device setup and configuration, allowing for zero-touch deployment and automated onboarding.
- Compliance Management: Offers compliance templates that help organizations adhere to industry regulations and security standards.
- App Management: Simplifies the deployment and management of applications, including App Store and custom apps.
- Security Controls: Includes features like encryption enforcement, password policies, and remote locking/wiping to enhance device security.
- Inventory Management: Provides real-time visibility into device status, configurations, and usage, allowing for effective asset tracking.
Unique feature:
This is a unique offer for businesses that have all Macs for their endpoints and iOS devices distributed to employees. The package enables you to unify the treatment of all of those devices that your users have with onboarding, tracking, security policy enforcement, and remote locking.
Why do we recommend it?
The Kandji system offers a cloud platform for Apple device management that enables you to control the security of devices to protect your company’s data from falling into the wrong hands.
The setup for a group of devices is planned in a system called Blueprints. You can create the same Blueprints for different models of mobile devices. The features that you include in one of these plans relate to the applications and access rights, which sit on top of the operating system and aren’t hardware dependent. You don’t have to apply the same Blueprint to all devices, so you can create different plans for different groups of users.
Functions in the Kandji package include security services, such as configuration locking and vulnerability scanning. The system includes a patch manager that allows each device user to decide when to run the update batch. Administrators can create security monitoring and maintenance automation scripts by assembling workflows through the selection of pre-written templates.
User accounts can be acquired from third-party apps, so you can import the accounts that you have already set up in systems, such as Slack or Okta. This allows you to easily create a single sign-on environment for all of your mobile devices, also coordinating access rights to on-premises Macs.
Who is it recommended for?
The Kandji focus on Apple devices is interesting but it reduces the potential customer base for this service. If you have Windows PCs on your site or if you allow BYOD for users with Android phones, you would have to switch to other unified endpoint management tools to watch over them.
Pros:
- User Management: Facilitates user role management and access controls, ensuring appropriate permissions are set for different users.
- Custom Workflows: Allows for the creation of custom workflows to automate routine tasks and enhance efficiency.
- Third-Party Integration: Supports integration with various third-party tools and services, enhancing its functionality within existing IT ecosystems.
- Strong Apple Focus: Tailored specifically for macOS, iOS, and iPadOS, ensuring deep integration with Apple’s ecosystem.
- Excellent Support: Kandji provides strong customer support and resources, including training materials.
Cons:
- Apple-Only Focus: Limited to Apple devices, which may not suit organizations with diverse operating systems.
You set up an account on the Kandji website and then download an agent onto each of the devices that you enroll in the service, so there are both cloud and on-device elements to this system. Pricing is determined based on the type of plan you choose and how many users are managed. You can get in contact with the Kandji team for a tailored quote. You can also register for a 14-day free trial, which starts with a system demo to assess the Kandji service.
3. ManageEngine Mobile Device Manager Plus (FREE TRIAL)
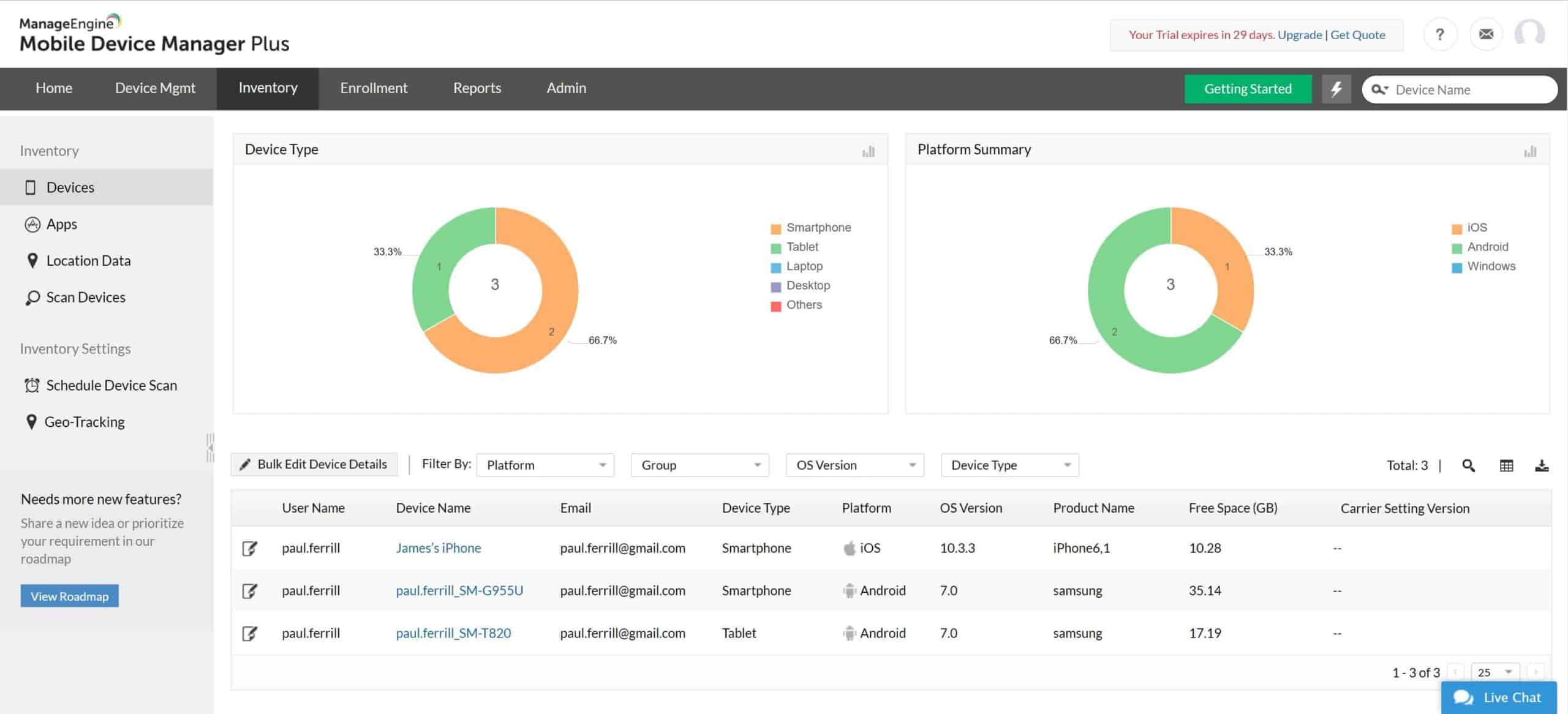
ManageEngine Mobile Device Manager Plus is a free MDM solution that can monitor desktop computers, laptops, smartphones, and tablets. The software supports multiple operating systems including Windows, Mac OS, Chrome OS, iOS, and Android. Through the customizable dashboard you can monitor mobile smart device status, giving you complete visibility over the connected devices your employees bring to work.
Key features:
- Supports Windows, Mac OS, Chrome OS, iOS, and Android.
- Remote device control
- Device scanning
- Out-of-the-box reports
Unique feature:
The unique feature of the ManageEngine Mobile Device Manager Plus system is that its Free edition is very generous, letting you monitor up to 25 devices without paying anything ever. There are many small businesses that will be able to operate successfully within this limit.
Why do we recommend it?
Apart from its free tier, ManageEngine Mobile Device Manager Plus is an impressive package because it offers a range of solutions for mobile device management, such as containerization for BYOD and remote tracking and locking for managed devices.
The mobile asset management experience offered by ManageEngine Mobile Device Manager Plus is very comprehensive. The dashboard also enables you to view additional information on devices including device owners, installed applications, and more. You can schedule regular device scans to keep this information updated.
If there are any problems with a device you can use remote troubleshooting to take control of the device and find the root cause of the issue in real-time. The administrator can use a remote chat to communicate with the end-user of the device. The chat can also be used to issue security commands.
ManageEngine Mobile Device Manager Plus is a complete enterprise mobile management package that comes in both on-premises and cloud-based versions. It includes a configuration manager for single or mass device set up and there is also a self-enrollment app that you can use for your device enrollment program. You can also set different policies for business-owned and user-owned devices.
It’s a mobile device management solution for device management that supports Windows, Mac OS, Chrome OS, iOS, and Android.
Who is it recommended for?
Mobile Device Manager Plus is suitable for enterprises of all sizes. The UEM system allows desktops running Windows and macOS to be included in the management scheme along with mobile devices running iOS, Android, and Chrome OS. The system can also manage IoT devices. The only problem is that it doesn’t include the management of computers running Linux.
During our testing, we identified the following pros and cons related to Mobile Device Manager Plus.
Pros:
- Designed to work right away, features over 200 customizable widgets to build unique dashboards and reports
- Leverages autodiscovery to find, inventory, and map new devices
- Uses intelligent alerting to reduce false positives and eliminate alert fatigue across larger networks
- Supports email, SMS, and webhook for numerous alerting channels
- Integrates well in the ManageEngine ecosystem with their other products
Cons:
- Is a feature-rich tool that will require a time investment to properly learn
ManageEngine Mobile Device Manager is recommended to enterprises that want a free mobile device management solution. The software’s free for up to 25 devices. ManageEngine Mobile Device Manager Plus is available on-premises (for Windows) and in the cloud. For pricing information, you must request a personalized quote from the company directly. You can download the 30-day free trial.
4. Ivanti Neurons for MDM
Ivanti Neurons for MDM was known as MobileIron until 2020 when Ivanti bought the mobile device management tool and integrated it into its Neurons line of products. This system is driven from the cloud and can be accessed from each device through an onboard app.
Key Features:
- Mass onboarding
- Virtual desktop
- Containerization
Unique feature:
The Ivanti Neurons for MDM system lets you create a standard desktop for each user or group of users that extends to each device that the user logs in from. Essentially, this is a virtual machine that is attached to the user account and can be accessed from anywhere.
Why do we recommend it?
Ivanti Neurons for MDM containerizes the delivery of mobile applications, tied together with access to storage space. This means that, when the user logs out, there are no assets of the company left on the device. This prevents business data from being leaked through loss or theft of the device. It also means that users can access the business system from their own devices, keeping personal and work systems completely separate.
Ivanti Neurons doesn’t just apply to mobile devices. It will also provide services to computers running Windows and macOS. Mobile devices can be running iOS or Android. The administrator sets up an application profile that contains a menu of software packages and services. Each user account then has a profile associated with it. The user is then able to self-enroll and access that workspace from any device.
The Ivanti system includes a VPN service. So, by installing an app on a mobile device, the user can open a portal that has a secure connection through to the business’s space on the Ivanti server. This account space can be accessed from anywhere.
Who do we recommend it for?
Ivanti Neurons for MDM is a very scalable product. It might be over-complicated for very small businesses, such as owner-run companies that could probably do just as well with a remote desktop system for mobile devices. However, mid-sized and large organizations that have a lot of roaming employees would benefit from this system.
Pros:
- Linked to other Ivanti products for security and computer management
- Activity monitoring
- Cloud-hosted application installers
Cons:
- Doesn’t extend to managing Linux
Ivanti doesn’t publish its prices. The cloud-based system is easy to sign up for and the application profile setup process is guided and device-agnostic. You can examine Ivanti Neurons for MDM with a 30-day free trial.
5. Citrix Endpoint Management
Citrix used to have a mobile device management tool, called XenMobile. However, the company has integrated that system into its UEM, which is called Citrix Endpoint Management. This system will manage devices that run Windows, macOS, iOS, Android, and ChromeOS. When we tested Citrix Endpoint Management we found the following key features.
Key Features:
- Two operating options
- Posture scanning
- Containerization
Unique feature:
The Citrix mobile management strategy is offered in two modes of operation. It is possible to install applications on company-owned devices, track them and optionally lock and wipe them. This is offered in the lowest of the three Citrix Endpoint Management plans. The two upper plans provide a portal service that delivers company assets to mobiles through containerization. This is ideal for dealing with user-owned devices.
Why do we recommend it?
The application management version of the Citrix service is called Workspace Premium. This provides a very similar strategy to other options on this list, which containerizes company data. The company-owned devices have broader access to the company network. However, those devices are scanned for security risks, such as malware or insecure apps before they are allowed to connect. So, you get two secure avenues of protecting your network from the risk of malware lateral movement.
The Workspace Premium option operates as a virtual desktop system that is attached to a user account. So, the user can log into a workstation at work and then leave the office and use a mobile device while out on site. That device can be company-owned or user-owned. The delivery of the application profile is managed in the same way regardless of device ownership.
Under the Workspace Premium scenario, the device should have a screen lock and no data is saved to the device. Thus, if the user mislays the device, anyone finding it will be unable to unlock that device and so would not be able to access company data.
Who do we recommend it for?
Citrix publishes a price list for its three UEM plans and they are levied per user or per device. This makes the system suitable for use by any size of business. The Citrix Endpoint Management service is based in the cloud and so the administrator can be located anywhere and administer user accounts and devices anywhere in the world.
Pros:
- Offers device management or virtualized access
- Security posture scanning
- Cross-device usage continuity
Cons:
- No coverage for Linux
The price for Citrix Endpoint Management varies depending on how many devices are included in the plan. However, Citrix publishes an average price for guidance. For the Stand-Alone plan, which enables direct device management, the price is $4 per user per month or $3 per device per month. The virtualized Workspace Premium system is available in two levels with the higher plan called Workspace Premium Plus. The lower plan costs $18 per user per month and the higher plan is priced at $25 per user per month.
6. Scalefusion
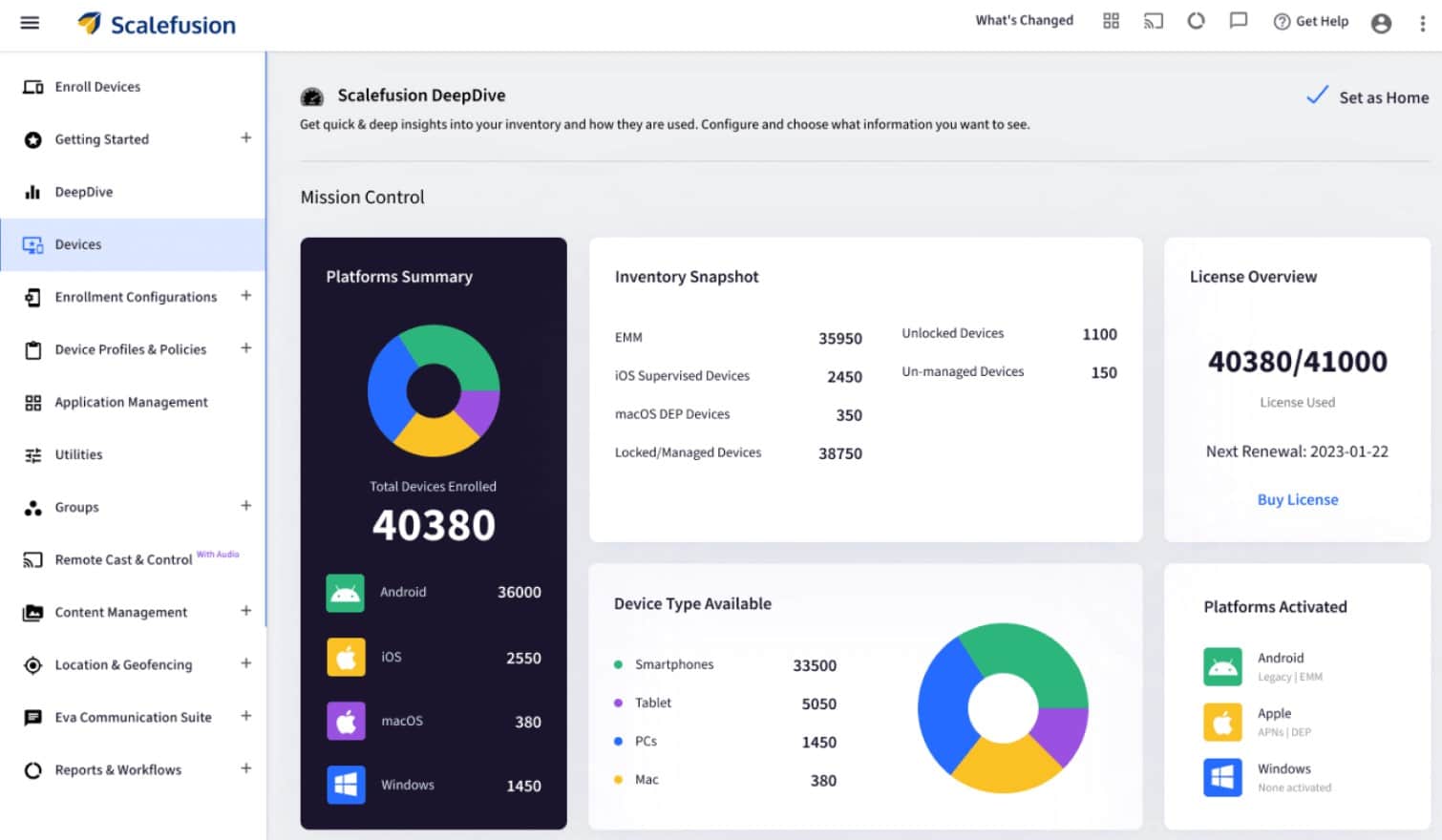
Scalefusion is a cloud-based unified endpoint management system that includes endpoint management for Android, iOS, Windows, macOS and Linux devices. They support varied device types like Smartphones, Laptops, Desktops, Kiosks, Digital Signage, Rugged Devices, Handheld Computers, VR Devices, POS Devices and more.
When we tested Scalefusion we found the following key features
Key features:
- Cloud & on-premise deployment
- Advanced location tracking and geo-fencing
- OS & 3rd-party patch management
- Shared device
Unique feature:
The VoIP calling with Remote Cast and Control feature offered by Scalefusion is unique. It enables IT admins to start a voice call from the remote cast and control session and talk with the end user for simplified communication.
Why do we recommend it?
While all MDM packages offer onboarding, tracking, locking, and wiping, the provisioning features of Scalefusion are outstanding. The ability of this tool to mirror screens of iOS and Android devices for support troubleshooting is also a very useful tool for technicians that other MDMs lack.
The cloud service includes an app storage space so you can create profiles and set up your in-house apps in the Scalefusion App Store. This enables you to define onboarding routines to download apps from the official app stores together with your own apps.
Once devices are up and running, you can contact them through screen mirroring for maintenance issues. The technical support module of Scalefusion integrates with third-party Service Desk utilities to manage tickets.
Security measures in the Scalefusion package include device tracking, vulnerability scanning for user-owned devices, and remote locking and wiping for managed devices. It is also possible to host your content on the Scalefusion server and deliver it through a remote access viewer, so files don’t need to be downloaded.
Who is it recommended for?
Although the per-device pricing of Scalefusion makes this comprehensive MDM accessible to businesses of all sizes, the technician tools in this system make it particularly interesting to large organizations or managed service providers that maintain teams of support technicians.
Pros:
- Delivers apps and data in a containerized mode for user-owned devices
- Include devices inventory management and software inventory control
- Provides patching and device security scanning to prevent vulnerabilities
Cons:
- The services of this package are more thorough for mobile devices than for desktops
Scalefusion is among the few MDMs that support Linux devices as well. They offer a subscription service with four plan levels, all with a rate per device per month. The Starter package costs $2 per device per month. You can get to know the Scalefusion system by accessing a demo. Why not check out Scalefusion for yourself on a free trial.
7. Samsung Knox Mobile
Samsung Knox Manage is part of a platform of device management system, called Knox Suite. The Manage unit is specifically focused on managing mobile devices that are provided by Samsung. A separate module in the suite provides device on-boarding.
Key Features:
- Location tracking
- Phone call cost limits
- Kiosk function
Unique feature:
Rather than delivering containerized apps, Knox Manage provides a kiosk mode for devices. The administrator loads one or many apps onto the device and then blocks any other changes. So, the user isn’t able to install other apps. The system also provides security posture scanning that can block devices from accessing the company network under certain circumstances.
Why do we recommend it?
The Knox system protects devices from misuse by preventing the user from adding unauthorized apps. It also scans each device according to a policy that you set up. It will prevent it from accessing your network and assets, such as file stores if it is in the wrong location or if some setting presents a security risk. This is a useful tool for enforcing some data protection standards, such as GDPR, which bans access to data from outside a stated country.
Other features in the Knox Manage system include remote access to all managed devices for troubleshooting. This system has a cloud-based console and it is able to manage and access devices anywhere in the world. This makes it a useful system for global businesses that want centralized management for all sites. Device users can travel overseas and the device can still be managed.
The statistics gathering feature of the Knox Manage system can extract contract usage information such as call charges and data plan usage. Bill costs can be limited and devices can be blocked from making high-charge calls, such as to premium numbers.
Who do we recommend it for?
Knox Suite is provided by Samsung and it only operates on Samsung devices. All Samsung devices run Android and so you won’t be able to manage iOS devices with this system and there is no associated workstation management package.
During our testing, we identified the following pros and cons related to Knox Suite.
Pros:
- Tracks mobile devices
- Remote access
- Service usage controls
Cons:
- Only works with Samsung mobile devices
Knox Manage isn’t a standalone package. You subscribe to Knox Suite, which includes Knox Manage. Samsung doesn’t provide a price list for Knox Suite but it does offer a 90-day free trial.
6. Miradore Mobile Device Management
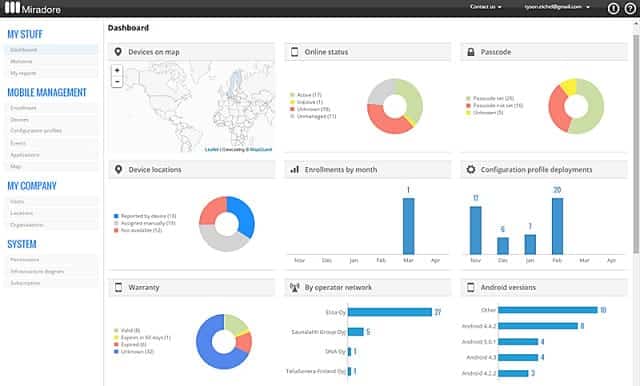
Miradore Mobile Device Management is a cloud-hosted service with a Free edition. Miradore actually has three levels of service – there are two paid plans as well as that Free edition. Those upper plans are called Premium ($3.30 per device per month) and Premium+ ($4.75 per device per month). All plans can manage Windows and macOS computers and mobile devices running iOS and Android. Those Windows and macOS computers can be workstations or laptops.
Key features:
- Workstations, laptops, smartphones, and tablets
- Mass onboarding feature
- Patching and app updating
Unique feature:
Free editions are nice but they are usually pitched to small businesses and have a limit on the number of devices they will manage. The free version of Miradore has no limit on the number of devices that it will run. However, there are fewer features in the package.
Why do we recommend it?
Miradore Mobile Device Management has all of the classic elements of an MDM: mass onboarding, tracking, locking, and wiping, containerized apps, and device encryption. This system is hosted in the cloud, so you don’t need to download and manage any software. The package’s dashboard is accessed through a dashboard and the tool lets you manage endpoints wherever they are in the world.

It is difficult to see past the Free edition. However, exciting though it is to get anything for free, there are reasons that people decide to pay for one of the two Premium packages. There are many functions that you can only get in the paid versions.
Examples of utilities that you only get in the paid editions include peripheral device management, drive encryption for workstations, containerization for work apps and data, and automated patching. An important distinction is that the Premium packages provide a unified endpoint management (UEM) service because they include functions for on-premises equipment.
All versions get the same dashboard – there are just a few more tabs available in the Premium plans. The most eye-catching feature of the console is a location map. This pinpoints the location of all your registered devices. Data on your hardware inventory is also presented in charts and graphs on the home page and more detailed information is available in tables on the back pages.
Who is it recommended for?
The Free edition is good for small businesses but remember that you can also get management functions for on-premises devices with the Premium editions, so many SMBs might be tempted to pay. The automation features for software management also provide a lure through to the Premium plans. Large organizations with many roaming users will definitely be interested in the Miradore system.
Pros:
- Device security
- Containerization for application and data delivery
- Tracking, locking, and wiping
Cons:
- Don’t get mesmerized by the Free editions
Miradore Mobile Device Management is easy to sign up for and set up. The Free edition is a good introduction to the service but you can go one better and try the Premium edition on a 14-day free trial. Your package will switch to the Free edition after that if you decide not to pay.
9. Omnissa Workspace ONE
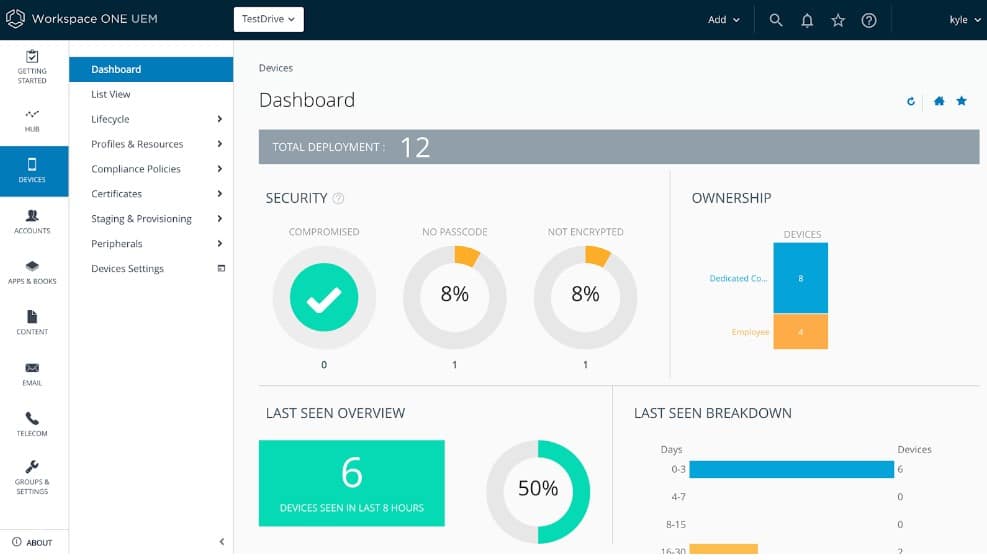
Omnissa Workspace ONE UEM is a mobile device management tool that can be used to remotely manage devices. With Omnissa Workspace One you can configure devices in bulk with the Apple Device Enrollment Program, Know Mobile Enrollment, and Android zero-touch enrollment.
When we tested Omnissa Workspace ONE we found the following key features.
Key features:
- Configure devices on bulk
- Automatically deploy applications
- Use onboarding workflow to add new devices
Unique feature:
Omnissa is a leader in virtualization and this expertise, applied to unified endpoint management with Workspace One, produces an exceptional virtual desktop service that can be accessed from any device, including mobiles. It doesn’t matter whether the device is user or company owned, all corporate assets are kept away from the device’s operating system by a hypervisor.
Why do we recommend it?
Omnissa Workspace One offers a sophisticated solution to the management of desktops and mobile devices that can be managed or user-owned. By treating every device as a support system for a Omnissa operating system, the tool standardizes the delivery of applications, attaching the desktop to the user account instead of to the device.
To manage devices, you can configure policies that determine restrictions and assign them to devices. You can distinguish between devices and assign them based on the operating system or ownership type. Ownership types are divided into BYO (Bring Your Own) and corporate-owned so you can tell which devices are company-owned and which are owned by employees.
The platform also enables you to automatically push applications to devices. This means you can purchase applications in bulk and deploy them efficiently without wasting any time. When it comes to adding new devices, users can enter credentials into an onboarding workflow to join the management solution.
Who is it recommended for?
Omnissa offers a flexible pricing structure with per-user and per-device options that make this service accessible to businesses of all sizes. The use of virtualization is widespread these days and any system administrator who has already learned how it works will have no problems understanding the Workspace One package.
Pros:
- Supports platforms like Apple Enrollment as well as Android Zero Touch
- Great for both managed devices as well as BYOD environments
- Can build workflows and policies with little platform knowledge
Cons:
- Can take some time to explore the product
Omnissa Workspace ONE is suitable for enterprises of all sizes and comes with a range of pricing options, due to its seven editions. Prices start at $1.66 (£1.33) per device and $3.00 (£2.40) per user. You can try the 30-day free trial to manage up to 100 devices.
10. BlackBerry Unified Endpoint Management

BlackBerry Unified Endpoint Management is an endpoint management solution designed for monitoring the Internet of Things (IoT) devices. Through one centralized user interface, you can view an overview of devices, users, and applications in use throughout your network. The tool supports operating systems including Windows 10, Mac OS, iOS, Android, and Chrome OS.
When we tested Unified Endpoint Management we found the following key features.
Key features:
- Manage device policies
- Supports iOS, Android, Chrome OS, Windows, and Mac OS
- Activate uses with a QR code (iOS and Android only)
- Available on-Premises and in the cloud
Unique feature:
The use of a QR code for onboarding is pretty unique and makes self-service enrollment very easy for users to implement with their own devices. The tool is also able to manage corporate devices alongside BYOD.
Why do we recommend it?
BlackBerry UEM offers a cloud-based service but you can also choose to get it as a software download and host it yourself. Its ability to centralize the management of user and corporate-owned devices is helpful and its ability to include Windows, macOS, and Chrome OS devices is also useful. Unfortunately, like many other options on this list, BlackBerry UEM can’t manage Linux devices.
Managing policies with BlackBerry Unified Endpoint Management is very easy. You can manage policies, users, groups, and applications from the console. Tasks you can complete including assigning apps to user accounts, distributing applications to containers, and configuring native apps.
Onboarding new users is also incredibly efficient, with the option to activate new devices via QR code for iOS and Android users. Groups can also be linked with Active Directory to automatically onboard new users. There is also the option to set aside work activities from personal ones with multiple activation types such as Work and Personal devices and Work Only.
Who is it recommended for?
The BlackBerry presentation for its UEM stresses the system’s suitability for use with IoT devices. However, it is also designed to manage desktops and mobile devices. Although other systems don’t put that capability in their headline, many of the packages on this list have equal IoT management capabilities.
Pros:
- Sleek highly customizable interface
- Cross-platform support with Windows, Mac OS, Linux, Android and iOS
- Available on-premise and as a cloud service
Cons:
- Would like to see more options for mobile security
- Better suited for enterprise networks
BlackBerry Unified Endpoint Management is a solid MDM solution that’s available on-premises and in the cloud. To view the pricing information you need to request a quote from the sales team directly. You can start the free trial.
11. SureMDM
SureMDM from 42Gears Mobility Systems provides a mobile device fleet management solution from a cloud platform. This service can also provide secure access to corporate services for user-owned devices.
Key features:
- Fleet management strategies
- Remote management and maintenance
- Robust mobile app
Unique feature:
This system is very comprehensive although it is pitched at smaller businesses, thanks to its per-device pricing. The package is a SaaS platform that includes cloud storage; buyers have the option of installing the system on their own cloud accounts, but the SureMDM price is the same so that strategy increases the cost of running the MDM.
Why do we recommend it?
SureMDM is able to manage mobile devices running Android and iOS. It is also able to track wearable tech and VR equipment. However, this tool can manage devices running Windows, macOS, and Linux, which extends the abilities of the system to desktops, making it a Unified Endpoint Management (UEM) system.
Fleet devices are managed through a mobile app. This app provides a portal. Think of it as an app locker – tapping on it opens a folder that includes icons for all your corporate apps. This is Mobile Application Management (MAM) strategy and it is applied to user-owned devices through containerization.
The containerized version works in the same way as the app locker. Users tap on the app and get prompted to log in. A single sign-on mechanism in the app then flows through authorization to all of the apps in the opened folder. Any data that gets accessed through one of the apps in the folder cannot be saved to the device because the container provides a floating operating system that neither apps nor users can break through.
The Kiosk Mode is also implemented through containerization, only this configuration possesses the device entirely. Thus, settings for keyboard commands and conditions such as WiFi access are blocked unless they are specified within the container’s operating system. Thus, it is possible to tightly control the functions of the device that a user can access while still enabling remote management down to the device’s operating system. This technique can also be allied to VR and wearable devices.
Device security features in the SureMDM package include tracking, locking, and wiping. The tool is able to track devices all over the world and its administrator interface is available in multiple languages, including French, Spanish, and German as well as English.
Who is it recommended for?
The per-device charging structure of this system makes it accessible to businesses of all sizes. Some higher functions are available as paid add-ons, which makes right-sizing provision easier. There is a multi-tenant account version, called SureMDM Hub for managed service providers.
Pros:
- Strategies for fleet management, user-owned access, and kiosk systems
- Remote access plus automated processes for maintenance
- Security scanning in the highest plan
Cons:
- You need to study a long list of features to work out which of the plans you should get
You can check out this MDM system by accessing a 30-day free trial of SureMDM or SureMDM Hub.
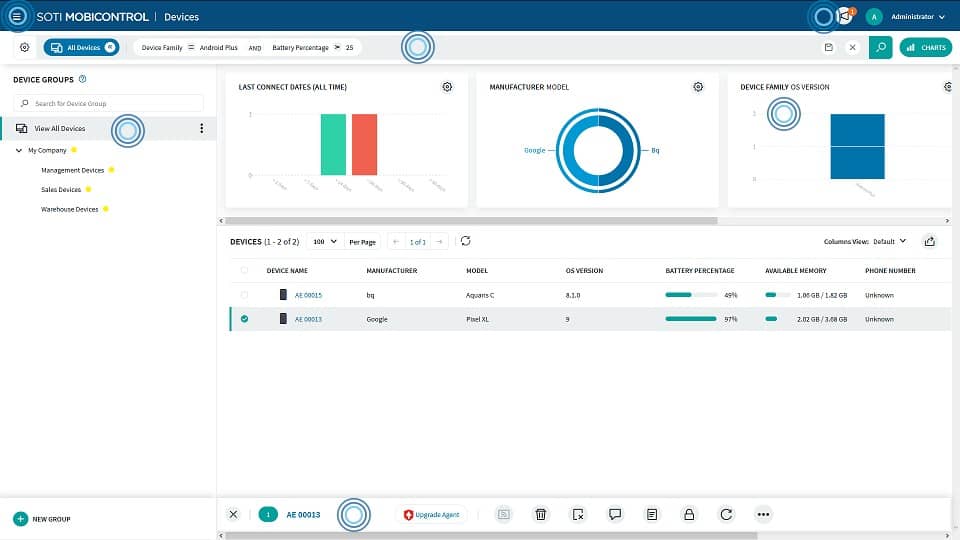
12. SOTI MobiControl
SOTI MobiControl is an endpoint management solution that can monitor devices from over 170 vendors in one location. Devices supported by SOTI MobiControl include Windows XP, Windows CE, Mac OS, iOS, and Android.
Key features:
- Remote viewing
- Remote control
- Integrations with Apple DEP, Android zero-touch enrolment, Samsung KME, Windows Autopilot, and Zebra StageNow
- Use scripts to execute management actions
Unique feature:
Remote viewing and remote control features in this package compete strongly with the technician tools in Scalefusion, which is the only competitor that comes close to this system for mobile device support capabilities.
Why do we recommend it?
SOTI MobiControl is able to support IoT devices and desktops as well as mobile devices and it is focused on enforcing security on corporate-owned devices.
When monitoring devices users can choose between remote viewing or remote control to take control of devices for a more hands-on approach to performance issues. There is also a chat that enables the administrator to communicate with the end-user of the device.
The software can also be used for mobile content management to secure files and web content. Through the SOTI Hub app, you can upload Microsoft Office files and determine which users have access to the resources. The application is very useful for managing access to files to ensure that only relevant employees can view sensitive information.
The application management capabilities of SOTI MobiControl are also very useful. Administrators can control what applications are permitted through blacklists and whitelists. Blacklisting non-work applications help ensure that teams stay productive.
Who is it recommended for?
This system aims to manage corporate-owned devices with strong security and data transfer performance optimization. It is a good choice if you often have problems connecting to devices in areas with poor signal quality.
During our testing, we identified the following pros and cons related to SOTI MobiControl.
Pros:
- Supports over 170 different vendor devices
- Allows technicians to manage devices and even remotely control them
- Supports access auditing
Cons:
- Best suited for MSPs and larger networks
SOTI MobiControl is recommended for teams looking for MDM solutions with clear connected visibility with remote control capabilities. However, you must request pricing information from the company directly. You can start the 30-day free trial.
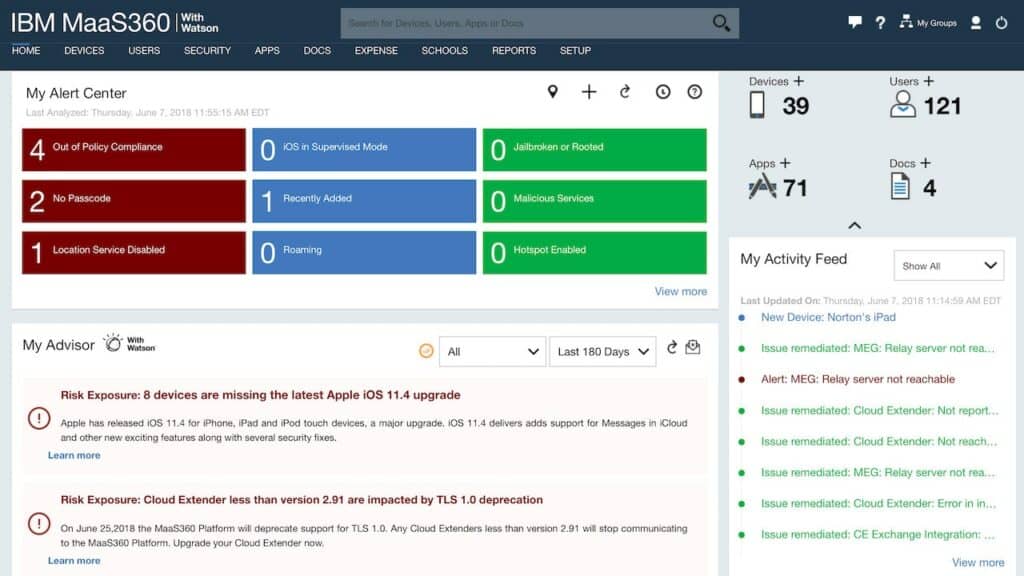
13. IBM MaaS360
IBM MaaS360 is an enterprise mobility management solution that supports Windows, Mac OS, Android, and iOS devices. With IBM MaaS360 you can monitor the data usage of devices in real-time and deploy updates to mobile applications from one centralized location. Application updates can be deployed to Windows and Mac OS devices for apps like Java, Adobe, Flash, Apple iTunes, and more.
When we tested IBM MaaS360 we found the following key features.
Key features:
- Real-time data usage monitoring
- Malware detection and remediation
- 24/7/365 customer support
- Single sign-on to web and cloud apps
Unique feature:
IBM has evolved its MaaS360 brand to be a security package. It manages both owner and BYOD mobile devices, plus endpoints and IoT devices.
Why do we recommend it?
IBM MaaS360 is a thorough enterprise UEM package with very strong security measures that includes malware scanning.
The device security features included with IBM MaaS360 are one of its greatest assets. The device platform can detect and remediate malware on endpoints. Being able to detect malware on devices provides you with an extra layer of mobile security that helps prevent endpoints from being compromised and putting your data at risk.
If you’re looking to monitor IoT devices then IBM MaaS360 is a natural choice. The platform can monitor Google Android, Android Things, Microsoft Windows 10, and Windows IoT devices to deploy security policies to protect the devices from causing security risks.
Who is it recommended for?
The capabilities of MaaS360 with its ability to monitor and protect just about every device type that a business can use makes it a good choice for large and complex corporations. However, it provides per-device pricing, which makes it accessible to small businesses.
Pros:
- Built with enterprises in mind
- Good fit for those looking to monitor IoT devices
- Can detect and defend against malware
Cons:
- Best suited for MSPs and larger networks
IBM MaaS360 is one of the easiest to use tools on this list, with a high-quality console for managing devices that would suit the needs of enterprises of all sizes. IBM MaaS360 pricing starts at $4 (£3.25) per device per month and $8 (£6.50) per user per month. You can start the 30-day free trial.
14. Cisco Meraki
Cisco Meraki covers the management of laptops and desktops as well as smartphones and tablets. This management console of this system is very attractive and includes a map showing the locations of all of your company’s managed devices. However, it can’t manage IoT or WiFi-enabled office equipment, such as printers. It will communicate with devices running Windows, macOS, Windows Phone, iOS, Android, Chrome OS and Samsung Knox.
When we tested Cisco Meraki we found the following key features.
Key features:
- Simple console for such a sophisticated system
- User self enrollment of devices
- Tracks mobile plan usage
Unique feature:
Cisco Meraki enables you to create a unified network from multiple sites and cloud resources through SD-WAN and SASE configurations. The tool enables you to include mobile and IoT devices into that network.
Why do we recommend it?
Cisco Meraki is a very sophisticated virtual network system that, despite its underlying complexity, presents a simple network in your management console. You can assign IP addresses in a single address space across your enterprise’s many sites and treat mobile devices as part of that structure.
Underpinning the MDM is a secure communication channel that is encrypted by AES with a 256-bit key. The app communication is protected by a VPN, which is applied on a per-app basis.
Configuration can be varied according to device type, user profile, or ownership model. These groups of devices can be configured in bulk, but there is always the possibility of individual configuration. Users with their own devices can enroll to get included in the network. The delivery method for apps and data files is called Backpack. The central administrator creates a bundle of files and then sends out access permissions to groups, individuals, or the entire network. These bundles will go out to user-owned devices once they have enrolled and been included in a user group.
Lost or stolen mobile phones can have all of their rights revoked and can be locked or wiped remotely. Meraki automatically tracks mobile plan usage, so excessive activity can be identified from live reports and stolen devices can be cut off from the phone and data services immediately.
Who is it recommended for?
Large multi-site businesses would get the most out of the Cisco Meraki service. It is also a good tool for securing the inclusion of user-owned devices by delivering apps and data outside of the secure network in containers.
Pros:
- Protects communications with AES-256 bit encryption
- Supports BYOD enrollment
- Supports remote wipes for stolen devices
Cons:
- Would like to see better data visualizations
- Does not support IoT devices
Related post: Best Cisco Network Monitoring Tools
15. Jamf Now
Jamf Now is a mobile device management system that only controls iOS devices. This is a cloud-based system that is priced per device. The service is free for the first three devices.
Unique feature:
Jamf Now is a great service for iOS device management. It provides processes for managing owned devices and other routines of dealing with BYOD. Both ownership models can be managed from the same console.
Why do we recommend it?
Jamf Now is equally competent at managing corporate-owned devices and BYOD. The service is a good choice because of its ability to secure devices and prevent lost or misplaced mobiles from risking data disclosure.
The setup process for devices revolves around “blueprints.” Each blueprint represents a standard configuration. You can create groups of devices and allocate a different blueprint to each. Configuration of those groups of devices can then be commanded, setting up all of them in bulk.
An alternative method for device inclusion is the enrolment process. This requires a device owner to create an account for the network by accessing a custom enrollment page. Once signup is complete, the configuration of the device initiates, giving user-owned devices the same level of security accorded to business-owned devices.
Remote monitoring of devices can be automated, giving you alerts when risk conditions occur, such as jailbreaking or the installation of unauthorized software. It is possible to display a full inventory of devices on your network in the dashboard. Details include spare storage capacity, a list of installed apps, and the serial number of the device.
Each device can be given a passcode centrally, and it is possible to use two-factor authentication with Jamf Now. You can activate a lost mode, which will lock the device and cause it to signal you its location. You can also wipe devices remotely.
Who is it recommended for?
The big restriction in the Jamf Now service is that it only manages iOS. If you are prepared to have multiple device management tools running in parallel, you could integrate Jamf Now into your toolset. However, that strategy doesn’t make sense when there are other competent tools available that offer more operating systems.
Pros:
- Leverages a sleek and intuitive dashboard interface
- Uses playbooks and blueprints to templatize device policies
- Can recover lost devices and secure them from data theft
Cons:
- Only supports iOS devices
Jamf Now is an interesting system and the free service for three devices is very tempting for sole traders, partnerships, and startups on a tight budget. The limitation of the service to just iOS devices may make this option too limited for your business.
























HI
You forget to mention biggest MDM market share players: Knox Manage, Xenmobile and Mobile Iron
Thanks for the reminder that I should be aware of the compatibility to different kinds of operating systems when it comes to getting a mobile device management consulting service
The best MDM I used was MobiVisor in the past. If you look for a really flexible Choice, you can check it out.
The Team can also implement new functions if you want.
Soti, 42Gears, VMware, ManageEngine… So many solutions considered leaders in the Mobile Device Management market, present in all MDM software comparisons and always in the first Google advertising results when you are looking for a solution to manage your fleet of professional mobile devices. But don’t be fooled by first appearances and do your research further. Because if these giants are ubiquitous on the web and continuously listed in the “Top 10” or “Best mobile management solutions” for a successful mobile strategy… It’s because they have an equally huge budget to inject in advertising, marketing, and paid articles highlighting their product.
Check out new key players in the MDM market, like TinyMDM: MDM solutions dedicated to small and medium enterprises combine security and ease of use. In addition to requiring no special knowledge and no training at all, all the functionalities are available in a single package, accessible to all.
Hi, VLavie,
In many respects you are right. However, there is a very good reason that I usually prefer the big providers and that is reliability. It is true that these systems have big marketing budgets, but that doesn’t mean that they win through visibility over effectiveness. Being a big player is a circuitous achievement because overhyped rubbish soon gets a lot of bad reviews. A huge advantage that the established services have over challenger systems is that they have been extensively used and so very well tested in the field. These recommended systems from large corporations also have well-funded support teams who regularly update the code — and that technical budget makes a big difference. What most commercial buyers need above all else is dependability.
Thanks for your input,
Stephen
Thanks for the reminder that I should be aware of the compatibility to different kinds of operating systems when it comes to getting a mobile device management consulting service. I’d like to know more about such things because I’m thinking about opening a business that offers a delivery service soon. I think that the drivers I will be hiring will appreciate getting their own mobile devices for this kind of work.
Good to see this list, albeit short. The majority of these MDMs are appropriate for managing employee-owned devices. We are in the logistics and transportation business and we use SureMDM (from 42Gears) for remote management of company-owned tablets and rugged devices. Works like a charm. Hope this helps anyone with similar requirements.
Hi Stephen,
Thanks for great infos and I like LiteManager for free remote management. Great another alternative for administration!
The information here is incorrect. Jamf Now supports iOS, tvOS and macOS devices, not just iOS. The larger EMM tool Jamf Pro is also omitted from the list.
Thank you for listing the MDM providers. However, our favorite Apptec360 is missing from the list when it came to efficiency, feature selection and price guidance.
Hi David, we also use Apptec software and are surprised why they are not listed.
Hi Stephen,
Thanks for providing such Best MDM Solutions. But consider MobiLock Pro as well in the list. It offers all the features that above are giving.
Thanks
You forget to mention biggest MDM market share players: Knox Manage, Xenmobile and Mobile Iron (ivanti)!