
An Intrusion Detection System (IDS) monitors network traffic for unusual or suspicious activity and sends an alert to the administrator. Detection of anomalous activity and reporting it to the network administrator is the primary function; however, some IDS software can take action based on rules when malicious activity is detected, for example, blocking certain incoming traffic.
An IDS software can handle the following pain points in an organization:
- Traditional firewalls may not be able to detect zero-day threats and unauthorized port access
- Ransomware and malware can quickly move laterally across the network, infecting every device in their path
- Many antivirus systems alone are not enough to meet the compliance requirements of standards, resulting in fines
- Identifying breaches can take time, resulting in high damage and costs
- Hackers can repeatedly exploit the same vulnerabilities until they are fixed
Addressing these pain points requires an advanced IDS.
In this guide, we have analyzed hundreds of tools to give you the best 12 that can address the issues that most organizations face today.
Here’s our list of the best Intrusion Detection Systems:
- ManageEngine EventLog Analyzer EDITOR’S CHOICE A log file analyzer that searches for evidence of intrusion and also provides log management. Use this system for compliance management as well as for threat hunting. Get a 30-day free trial.
- ManageEngine Log360 (FREE TRIAL) This SIEM package uses UEBA to establish a baseline of normal activity and then looks for deviations from that norm. This large bundle of multiple ManageEngine modules also gives you user activity tracking for insider threat defense and log management. Runs on Windows Server. Start a 30-day free trial.
- ESET Protect (FREE TRIAL) This multi-level threat detection and response package starts with an on-device anti-virus system and is enhanced by a coordinating unit on the cloud that adds additional threat hunting. The package also has vulnerability management and cloud-based sandboxing options. Runs on Windows, macOS, Linux, iOS, and Android. Start a 30-day free trial.
- Snort Provided by Cisco Systems and free to use, this leading network-based intrusion detection system (IDS) software provides opportunities for automated and manual threat hunting. It works on packet searches and includes a packet sniffer, which can also store traffic for later analysis. Runs on Windows, Linux, and Docker.
- SolarWinds Security Event Manager Analyzes logs from Windows, Unix, Linux, and macOS systems. It manages data collected by Snort, including real-time data. SEM is also an intrusion prevention system, shipping with over 700 rules to shut down malicious activity.
- OSSEC This is an excellent host-based intrusion detection system that is free to use and can be extended by a network activity feed to create a full SIEM for free. This tool is undergoing a lot of changes right now with a better free version called OSSEC+ available and a paid version called Atomic OSSEC. Runs on Linux.
- Gatewatcher AIonIQ This network detection and response (NDR) package is delivered as a network device or virtual appliance. It gathers data from your network through a packet sniffer and can forward its discoveries to SIEMs and other security tools.
- CrowdSec This HIDS/IPS package, available in free and paid versions, collects log files from your site and uploads them to a cloud server for threat detection. The collector is available for Linux, Unix, Windows, and Docker.
- Suricata Network-based IDS software that operates at the application layer for greater visibility.
- Zeek Network monitor and network-based intrusion prevention system.
- Security Onion Network monitoring and security tool made up of elements pulled in from other free tools.
- AIDE The Advanced Intrusion Detection Environment is a HIDS for Unix, Linux, and Mac OS
Key Points To Consider While Choosing the Best IDS Software
Selecting the right IDS software is critical to improving the security of your network and infrastructure. However, this is also the most difficult process, given the vast advancements that have taken place in this space in the last few years. To navigate this maze, below are some key points to consider:
- Accuracy and scope: You want an IDS that will go beyond known threats and signature-based detection to also identify unknown threats and fileless malware using behavioral and anomaly detection strategies.
- Deployment: The tool you choose must have multiple deployment options, like Network IDS, Host-based IDS, and cloud, for greater flexibility.
- Integration: The tool you choose must integrate well with your tech stack.
- Real-time alerts: Make sure the IDS you select offers real-time alerts with detailed logs and recommended actions, so you can isolate and fix the problem at the earliest.
- Performance: The selected IDS should be able to handle large workloads and scale seamlessly to grow with your business.
- Compliance: Pick a tool that comes with pre-built reporting templates to meet the requirements of different compliance standards.
How to Calculate the ROI of IDS Software?
A key aspect of selecting an IDS is the Return on Investment (ROI) because you’d want the tool to add value to your operations and decrease your costs. But, how do you calculate the ROI of each tool? We have come up with a structured approach that you can follow, or customize to suit your needs.
Step 1: Identify the Metrics
The first step is to identify the metrics based on the current state of your network and the pain points that you want the IDS to address. Some possible metrics to consider are:
- Number of intrusion attempts
- Average time taken to detect a breach
- The average time taken to investigate false positives
- Cost of data breaches. You can take estimates or historical figures, where appropriate
- Revenue loss due to breaches and downtime
- Compliance fines
Step 2: Calculate the Total Costs
Next, calculate the total costs of the software you choose. This can include:
- Licensing or subscription fees
- Hardware costs, if applicable
- Cost of installation, including technical expertise required for integration
- Training costs
- Maintenance and customer support costs
Step 3: Calculate the Benefits
In this step, estimate the likely benefits that your organization can get when you use the selected IDS tool. The savings that you can look for are:
- Reduced response time
- Fewer intrusion events
- Avoided downtime and business interruption
- Reduced or avoided compliance penalties
- Faster rate of detection
Step 4: Put It All Together
Now, put all the above metrics together to calculate the ROI:
- Annual Cost Savings = (Time saved in incident response × Cost per hour of security staff) + (Reduced downtime hours × Cost per hour of downtime) + (Avoided breach costs + Avoided fines + External tool cost savings)
- Total Investment = All the costs identified in Step 2
- ROI = ((Annual Cost Savings – Total Investment) ÷ Total Investment) × 100
The best intrusion detection systems software and tools
Features Comparison Table
We found the following characteristics for the products we tested.
| Features/IDS | ManageEngine EventLog Analyzer | ManageEngine Log360 | ESET Protect | Snort | SolarWinds Security Event Manager | OSSEC | Gatewatcher AIonIQ | CrowdSec | Suricata | Zeek | Security Onion | AIDE |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Real-time Monitoring | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Log Management | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No |
| Signature-based Detection | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No |
| Anomaly-based Detection | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Open Source | No | No | No | Yes | No | Yes | No | Yes | Yes | Yes | Yes | Yes |
| Cloud Integration | Yes | Yes | Yes | No | Yes | No | Yes | Yes | No | No | No | No |
| Free Version Available | No | No | No | Yes | No | Yes | No | Yes | Yes | Yes | Yes | Yes |
Now you have seen a quick rundown of host-based intrusion detection systems and network-based intrusion detection systems by operating system. In this list, we go deeper into the details of each of the best IDS.
1. ManageEngine EventLog Analyzer (FREE TRIAL)
Best for: In-depth log analysis and management
Relevant for: Security teams and IT administrators
Price: Subscription costs depend on the number of devices. For 10 Syslog devices, the cost is $595
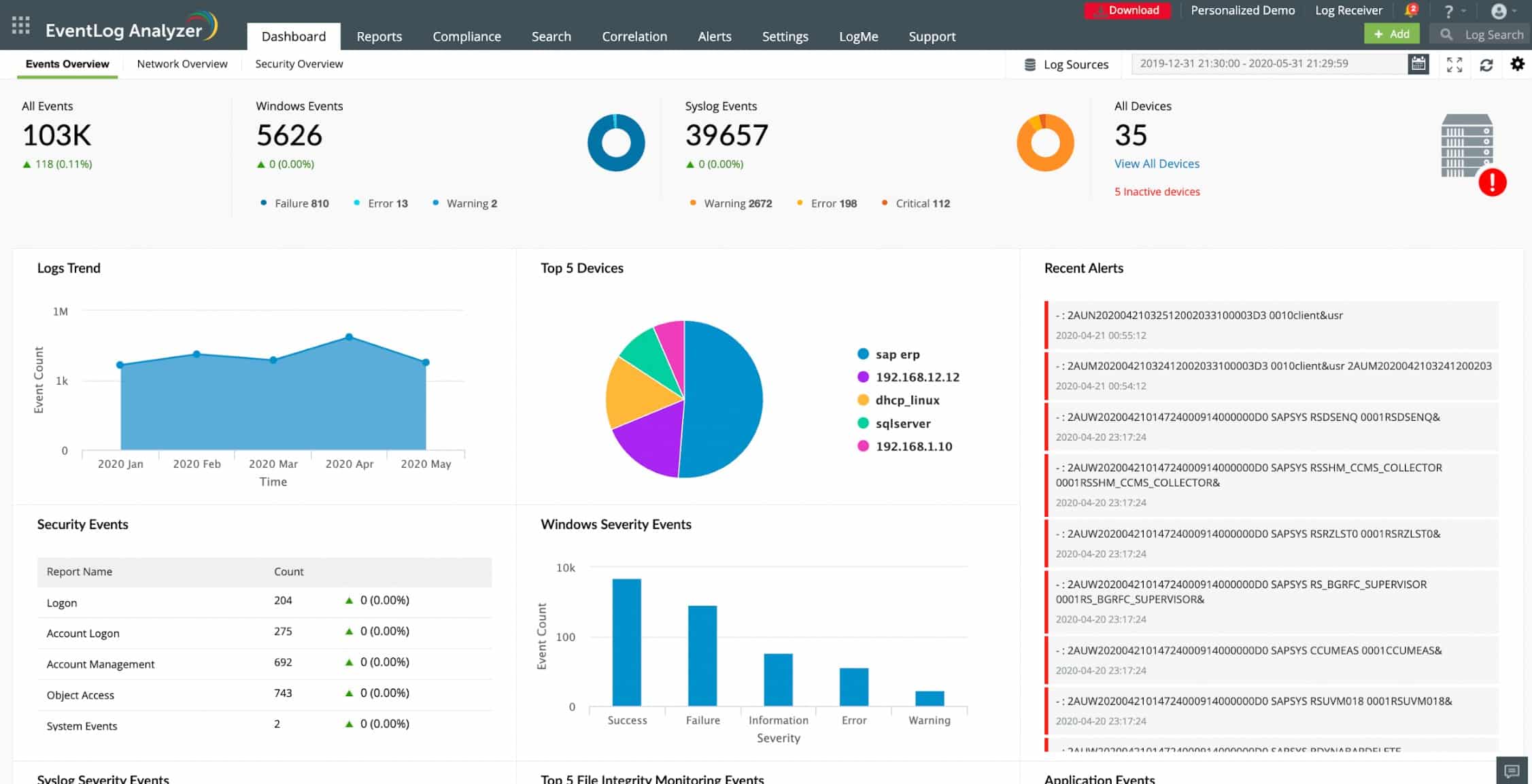
ManageEngine is a leading producer of IT network infrastructure monitoring and management solutions. EventLog Analyzer is part of the company’s security products. This is a HIDS that focuses on managing and analyzing log files generated by standard applications and operating systems. The tool installs on Windows Server or Linux. It gathers data from those operating systems and also from Mac OS, IBM AIX, HP UX, and Solaris systems. The logs from Windows systems include sources from Windows Server Windows Vista and above and the Windows DHCP Server.
ManageEngine EventLog Analyzer’s Key Features:
- Manages and Analyzes Log Files: EventLog Analyzer is designed to effectively manage and analyze log files, providing insights into system activities and potential security events.
- Auditing for Data Protection Standards Compliance: The tool includes auditing capabilities to ensure compliance with data protection standards, such as HIPAA, PCI, and FISMA.
- Supports Various Hardware Devices: Supports dozens of different hardware switches, routers, firewalls, and access points. This broad support ensures compatibility with a wide range of network devices.
- Monitoring User Permissions for Compliance Standards: Monitors user permissions to ensure compliance with standards like HIPAA, PCI, and FISMA.
- Advanced Log Correlation: Automatically correlates data from multiple sources to identify complex attack patterns.
Unique Business Proposition
A unified platform that integrates log management, compliance reporting, and threat detection to provide complete visibility into your operations. It also collects and analyzes logs from diverse sources to proactively monitor security events.
Feature-in-Focus: Real-Time Event Correlation
Continuously analyzes log data to correlate events and send alerts if needed. Due to this continuous analysis, alerts happen in real time and reduce the risk of burden.
Comparitech SupportScore – 9.3
ManageEngine is a solid company with an extensive product suite catering to different areas in networking, monitoring, and management. Due to this diversified product suite, it is financially stable, and has a dedicated support team that promptly handles all questions and concerns. Its self-supporting documentation is also excellent.
Why do we recommend it?
ManageEngine EventLog Analyzer captures, consolidates, and stores log messages from all parts of your system. It then searches through those records for indications of hacker activity or malware. The package includes a compliance reporting module.
Apart from operating systems, the service gathers and consolidates logs from Microsoft SQL Server and Oracle databases. It is also able to channel alerts from a number of antivirus systems, including Microsoft Anti-malware, ESET, Sophos, Norton, Kaspersky, FireEye, Malwarebytes, McAfee, and Symantec. It will gather logs from web servers, firewalls, hypervisors, routers, switches, and network vulnerability scanners.
EventLog Analyzer gathers log messages and operates as a log file server, organizing messages into files and directories by message source and date. Urgent warnings are also forwarded to the EventLog Analyzer dashboard and can be fed through to Help Desk systems as tickets to provoke immediate attention from technicians. The decision over what events constitute a potential security breach is driven by a threat intelligence module that is built into the package.
The service includes automatic log searches and event correlation to compile regular security reports. Among those reports is a format for Privileged User Monitoring and Auditing (PUMA) and a variety of formats needed to demonstrate compliance with PCI DSS, FISMA, ISO 27001, GLBA, HIPAA, SOX, and GDPR.
Who is it recommended for?
This ManageEngine tool is available for Windows Server and Linux, which means it is ideal for any business that has on site servers. The package is available in an edition for a single site and another that covers multiple sites. Small businesses can get a free version of the system that manages logs and includes compliance reporting but doesn’t provide an automated threat detection service.
During our testing, we identified the following pros and cons related to EventLog Analyzer.
Pros:
- Installation Flexibility on Windows or Linux: Offers flexibility by allowing installation on either Windows or Linux operating systems, providing sysadmins with more options to align with their preferences.
- Alert Forwarding from Major Antivirus Brands: The tool supports alert forwarding from major antivirus brands like ESET, Malwarebytes, and Norton. This integration enhances its ability to correlate security events and responses.
- SaaS option available: ManageEngine offers a hosted version on the cloud.
- Automated remediation: Administrators can set up playbooks that will trigger responses.
Cons:
- Best Suited for Larger Networks and Enterprises: The platform is described as highly detailed, suggesting that it may have a steeper learning curve and is best suited for larger networks and enterprises with complex log management needs.
The ManageEngine EventLog Analyzer is available in three editions. The first of these is Free. However, the Free edition is limited to monitoring log messages from five sources, which isn’t really sufficient for any modern business beyond very small enterprises. The two paid editions are Premium and Distributed. The Distributed plan is significantly more expensive than the Premium plan. The Premium system should be sufficient for most single-site enterprises, while the distributed version will cover multiple sites and an unlimited number of log record sources. You can try out the system with a 30-day free trial that has a limit of 2,000 log message sources.
EDITOR'S CHOICE
ManageEngine EventLog Analyzer is our top pick for an intrusion detection systems because this SIEM solution that serves as an effective IDS for organizations. It helps monitor, analyze, and secure network environments by collecting and examining logs from various sources, including servers, firewalls, routers, and other network devices. This enables administrators to identify suspicious activities, detect potential intrusions, and ensure regulatory compliance. As an IDS, EventLog Analyzer excels in real-time log analysis, enabling organizations to monitor network traffic and system activities for signs of malicious behavior or policy violations. It supports a wide range of log sources and can automatically correlate data to highlight abnormal patterns, such as unauthorized access attempts, unusual login times, or unexpected network traffic spikes: common indicators of a security breach. The tool provides detailed reports, dashboards, and real-time alerts to facilitate quick detection and response. It also includes customizable alerting features to notify administrators of potential threats, helping to reduce response time and mitigate damage.The built-in compliance reporting tools ensure that the system adheres to industry standards and regulations, such as GDPR, HIPAA, and PCI DSS.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/products/eventlog/on-prem-cloud-free-trial.html
OS: Windows, Linux, and SaaS
2. ManageEngine Log360 (FREE TRIAL)
Best for: Integrated SIEM and compliance
Relevant for: MSPs, and IT security teams
Price: Depends on the number of devices. For a minimum of two domain controllers, the price is $945
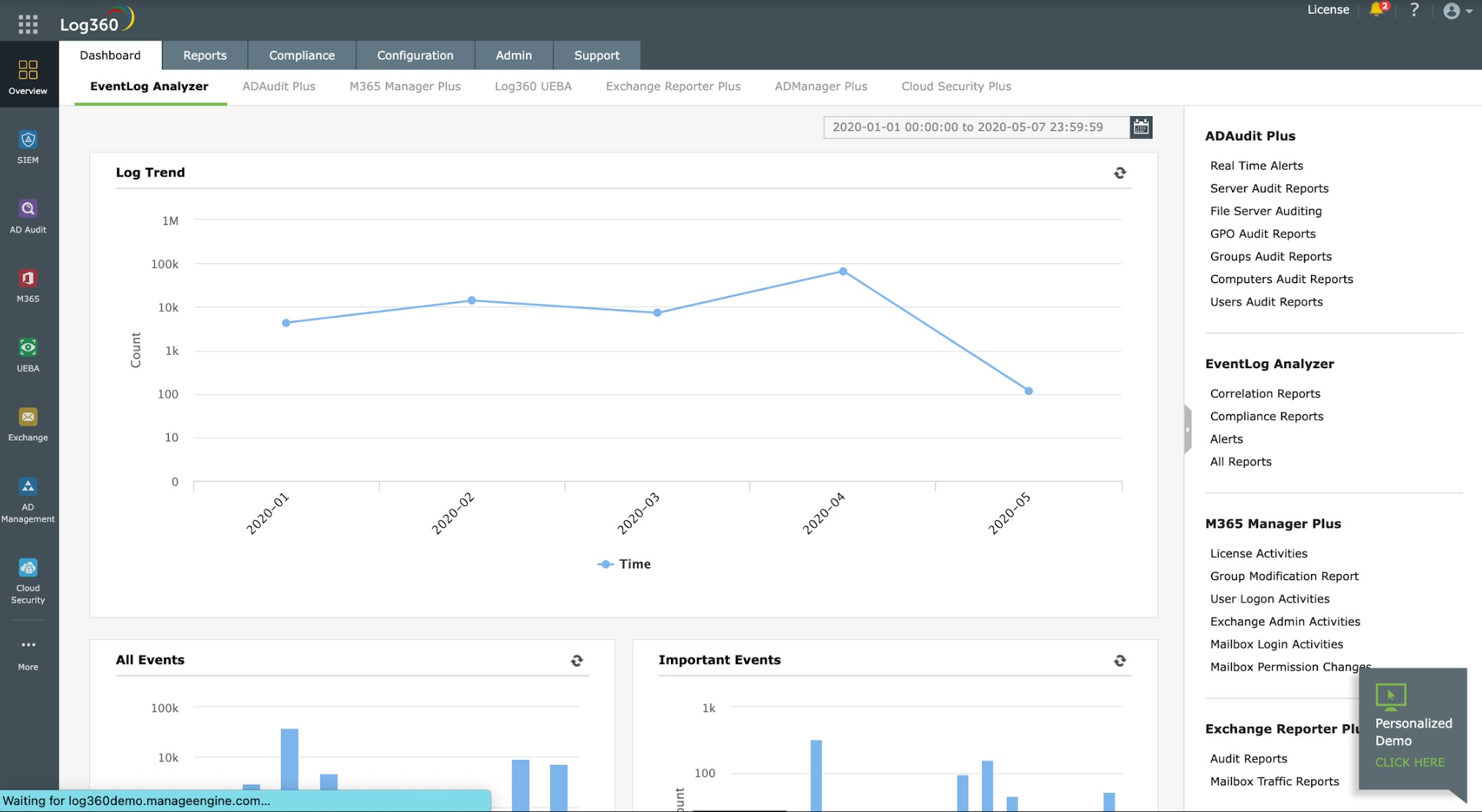
ManageEngine Log360 is a SIEM system. Although usually, SIEMs include both HIDS and NIDS, Log360 is very strongly a host-based intrusion detection system because it is based on a log manager and doesn’t include a feed of network activity as a data source. The Log360 software package runs on Windows Server but is able to collect log messages from other operating systems.
ManageEngine Log360’s Key Features:
- Log Collection and Consolidation: Log360 offers log collection and consolidation capabilities, allowing organizations to gather and centralize logs from various sources.
- Threat Detection: The tool includes threat detection features, enabling the identification and response to potential security threats within the log data.
- Windows Events, Syslog, and Software Logs: Log360 supports the collection and analysis of various log types, including Windows Events, Syslog, and logs from different software applications.
- Anomaly-Based Threat Hunting: Incorporates anomaly-based threat hunting, allowing for the proactive identification of unusual or suspicious activities.
Unique Business Proposition
This is a SIEM solution that combines different events to help you understand the current state of your security. Its centralized console allows organizations to monitor and analyze logs from different sources for better security and compliance.
Feature-in-Focus: Advanced Detection
By combining data from different sources, this tool detects complex attack patterns and anomalies. Its predefined correlation rules and the flexibility to create log rules make it a handy tool for detecting all kinds of threats.
Why do we recommend it?
ManageEngine Log360 is a package of eight ManageEngine services, which includes the EventLog Analyzer. Additional modules provide file integrity monitoring, email protection, and cloud platform threat detection. This system includes user and entity behavior analytics (UEBA) that provides an adjustable baseline of standard activity.
The package collects Windows Events and Syslog messages from operating systems and also interacts with more than 700 software systems to gather logs. When these log files arrive at a central server, their formats are standardized, so that they can be searched and filed together.
The console for Log360 includes a data viewer that offers analysis tools for manual searches and assessment. Records can also be read in from files. The system also performs automated searches for its SIEM threat hunting.
The SIEM uses machine learning to establish a pattern of activity for each user account and device. This is known as user and entity behavior analytics (UEBA). The system then looks for activities that don’t fit into that pattern. When suspicious activity is detected, Log360 raises an alert. You can adjust the thresholds for notifications.
The system shows alerts in the console and you can also set it up to forward notifications as tickets through ManageEngine ServiceDesk Plus, Jira, and Kayoko.
Log360 is a useful tool for compliance with GDPR, GLBA, PCI DSS, FISMA, HIPAA, and SOX. The log management system files log messages in an easy-to-retrieve structure, which makes it suitable for compliance auditing.
Who is it recommended for?
ManageEngine Log360 provides a lot of system management and security services that might be too much for all but the largest businesses. Mid-sized companies could opt for the EventLog Analyzer to get the threat detection element of this package. A Free edition provides log management, compliance reporting, and AD management for small businesses with up to 25 workstations.
During our testing, we identified the following pros and cons related to Log360.
Pros:
- Log Management for Standard Compliance: Log360 is designed to assist with log management for standards compliance, helping organizations meet regulatory requirements.
- Notifications Through Service Desk Systems: Supports notifications through service desk systems, enhancing communication and collaboration within the organization.
Cons:
- Not Offered as a Cloud Service: Log360 is not offered as a cloud service. This means that users may need to deploy and manage the solution on their own infrastructure, potentially requiring additional resources.
There are two versions of ManageEngine Log360: Free and Professional. The Free edition is limited to monitoring 25 endpoints. The Professional edition is available for a 30-day free trial.
3. ESET Protect (FREE TRIAL)
Best for: Multi-layered endpoint security
Relevant for: MSPs and IT teams
Price: Costs $287.72 per year for five devices
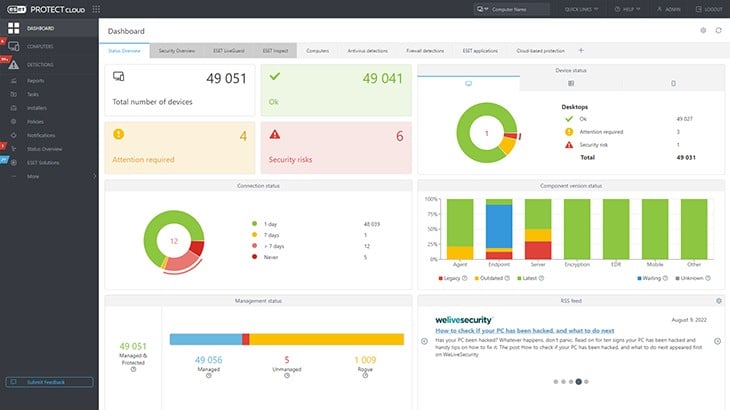
ESET Protect detects intrusion, insider threats, and malware. The system operates on each device and it is available for mobile devices as well as computers. The antimalware system is available for Windows, macOS, Linux, iOS, and Android. Every installed instance of this cybersecurity package reports to a central cloud-based console.
ESET Protect’s Key Features:
- Anomaly-Based Detection: ESET Protect employs anomaly-based detection methods to identify and respond to unusual or abnormal activities that may indicate potential security threats.
- Multi-Level Threat Hunting: The platform provides multi-level threat hunting capabilities, allowing users to investigate and respond to various levels of security threats effectively.
- Private Threat Intelligence Network: ESET Protect operates within a private threat intelligence network, enhancing its ability to gather and share information about emerging threats.
- Local Detection and Response: ESET Protect enables local detection and response mechanisms to continue functioning even if a device is isolated from the network, ensuring continuous protection.
Unique Business Proposition
A cybersecurity platform that offers comprehensive protection against multiple threats. Its support for diverse operating systems makes it ideal for different scenarios and organizations. Its centralized console also provides complete visibility.
Feature-in-Focus: Cloud-Based Console
A highlight of this tool is its cloud-based console that supports centralized management of endpoints. Its real-time visibility and automated incident response reduce the overhead for IT employees, as they can control everything through the console.
Comparitech SupportScore – 9.6
ESET is one of the leading players in cybersecurity and is backed by a large employee base, including a dedicated support team. It has also been seeing good revenue inflows, indicating the company’s stability in the coming years. Its self-supporting documentation is also sufficient.
Why do we recommend it?
ESET Protect is a multi-level threat detection service. Its four editions build up layers of services that include vulnerability management and a threat intelligence feed. The tool looks for identifiers of typical malware and hacker behavior, such as evasion tactics, lateral movement, password cracking, and file manipulation.
The ESET system is offered in four editions and the power of the cloud-based element of the package increases with higher plans. While the lowest plan, ESET Protect Entry just provides a live activity monitor in the console, the next plan up, ESET Protect Advanced implements secondary threat hunting in its cloud system.
The ESET Protect Complete plan provides cover for cloud packages and email systems as well as endpoints. The cloud unit can be set up to implement automated responses. The top plan, ESET Protect Elite, can involve third-party tools in those responses, while the Complete package focuses communication on the ESET on-device software.
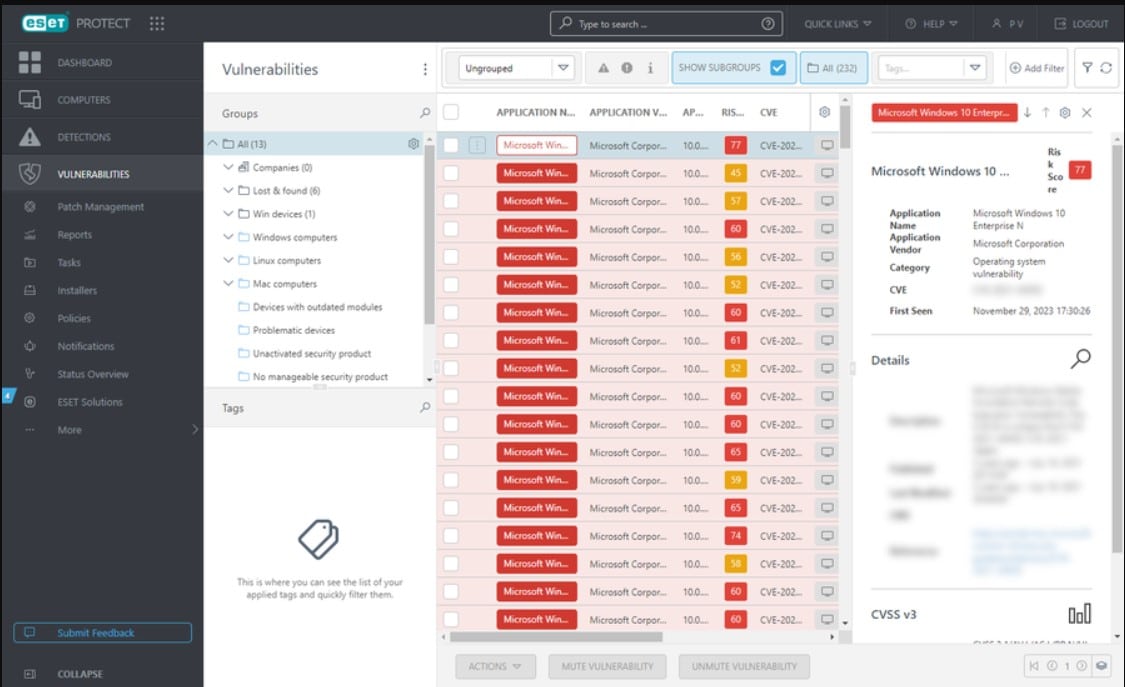
The plans that include cloud-based threat detection also provide software sandboxing on the ESET servers. The top two plans provide system hardening features with a vulnerability scanner and a patch manager. When an attack is discovered on one endpoint, all of the other devices enrolled in the protection are notified. This enables the local units to implement deeper scrutiny of traffic from the suspicious source or the attacked endpoint.
Responses are automated but businesses that use the system are also expected to have their own cybersecurity experts on staff. Those companies that don’t have such expertise on the payroll can opt for the ESET Protect MDR, which provides a Security Operations Center (SOC) team along with the software for remote security management.
Who is it recommended for?
Small businesses with few endpoints to monitor will do well with the Entry edition. The minimum number of endpoints that will be covered by an ESET package is five. All of the editions of ESET Protect are available in a multi-tenant architecture, which is suitable for use by managed service providers.
During our testing, we identified the following pros and cons related to ESET Protect.
Pros:
- Shared Intelligence: ESET Protect utilizes shared intelligence that is coordinated from the cloud, ensuring that threat information is efficiently distributed to all connected endpoints.
- Warnings to All Endpoints in Case of an Attack: The platform is designed to issue warnings to all endpoints if a single device within the network is under attack, promoting swift and unified responses to security incidents.
Cons:
- Requires a Minimum of Five Devices: A potential drawback is that ESET Protect requires a minimum of five devices. This may be a consideration for smaller organizations or those with limited device numbers.
Any business will find that one of the four plans meets its security needs. Packages cover at least five endpoints except for the ESET Protect Elite edition, which is priced for at least 26 devices. ESET Protect is available for a 30-day free trial.
4. Snort
Best for: Customizable IDS
Relevant for: Educational institutions and network administrators
Price: Community edition is free, Subscriptions edition is priced at $29.99 for the Personal plan, and $399/sensor for the Business plan. Both prices are annual subscriptions
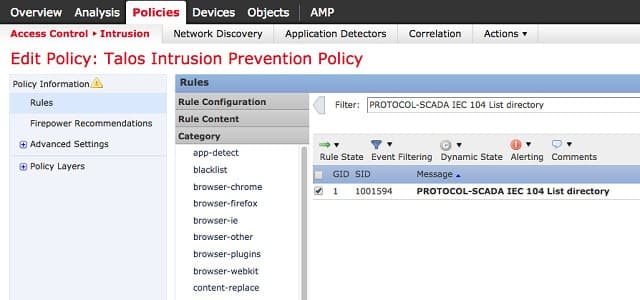
Snort is the industry leader in NIDS, but it is still free to use. This is one of the few IDSs around that can be installed on Windows. It was created by Cisco. The system can be run in three different modes and can implement defense strategies, so it is an intrusion prevention system as well as an intrusion detection system.
The three modes of Snort are:
- Sniffer mode
- Packet logger
- Intrusion detection
You can use snort just as a packet sniffer without turning on its intrusion detection capabilities. In this mode, you get a live readout of packets passing along the network. In packet logging mode, those packet details are written to a file.
Snort’s Key Features:
- Industry-Leading NIDS: Snort is recognized as an industry-leading Network Intrusion Detection System, providing capabilities for monitoring and analyzing network traffic for potential security threats.
- Supported by Cisco Systems: The software is supported by Cisco Systems, adding credibility to its effectiveness in network security.
- Supports Packet Sniffing for Live Traffic Analysis: Snort supports packet sniffing for live traffic analysis, allowing administrators to analyze network packets in real-time alongside log scanning.
Unique Business Proposition
Snort is a free and open-source IDS managed by Cisco. It offers real-time packet logging and traffic analysis that can be customized using different rule sets. It covers a wide range of scenarios and can identify false negatives. Snort is also compatible with multiple environments.
Feature-in-Focus: Rule Engine
A standout feature of this tool is its customizable rule engine. Using this feature, users can write and modify rules to identify emerging threats. This feature can be particularly useful for organizations with unique security requirements, like educational institutions and healthcare companies.
Why do we recommend it?
Snort is a free data-searching tool that specializes in threat detection with network activity data. By accessing paid lists of rules, you can quickly improve threat detection. This is a good system for picking up security tips as well because the user community of Snort is very active and provides advice and innovations.
When you access the intrusion detection functions of Snort, you invoke an analysis module that applies a set of rules to the traffic as it passes by. These rules are called “base policies,” and if you don’t know which rules you need, you can download them from the Snort website. However, once you become confident in the methodologies of Snort, it is possible to write your own. There is a large community base for this IDS and they are very active online on the community pages of the Snort website. You can get tips and help from other users and also download rules that experienced Snort users have developed.
The rules will detect events such as stealth port scans, buffer overflow attacks, CGI attacks, SMB probes, and OS fingerprinting. The detection methods depend on the specific rules being used and they include both signature-based methods and anomaly-based systems.
Who is it recommended for?
Snort requires a level of commitment to get high-quality threat detection working properly, Small business owners with no technical expertise would find setting up this system too time-consuming.
During our testing, we identified the following pros and cons related to Snort.
Pros:
- Completely Free and Open-Source: One of Snort’s significant advantages is that it is completely free and open-source, making it accessible to a broad user base.
- Large Community Support: Snort benefits from a large and active community. This community shares new rule sets and configurations, providing system administrators with a wealth of resources to enhance their security environment.
Cons:
- Highly Complex: Snort is known for its complexity, even with preconfigured rules. Users are required to have deep knowledge of network security concepts to effectively utilize and customize the tool.
- Reliant on Community Support: While the community support is extensive, Snort relies heavily on this community for support.
Snort’s fame has attracted followers in the software developer industry. Several applications that other software houses have created can perform a deeper analysis of the data collected by Snort. These include Snorby, BASE, Squil, and Anaval. Those companion applications help you make up for the fact that the interface for Snort isn’t very user-friendly.
5. SolarWinds Security Event Manager
Best for: SIEM with automation
Relevant for: Mid to large organizations
Price: Starts at $3,292
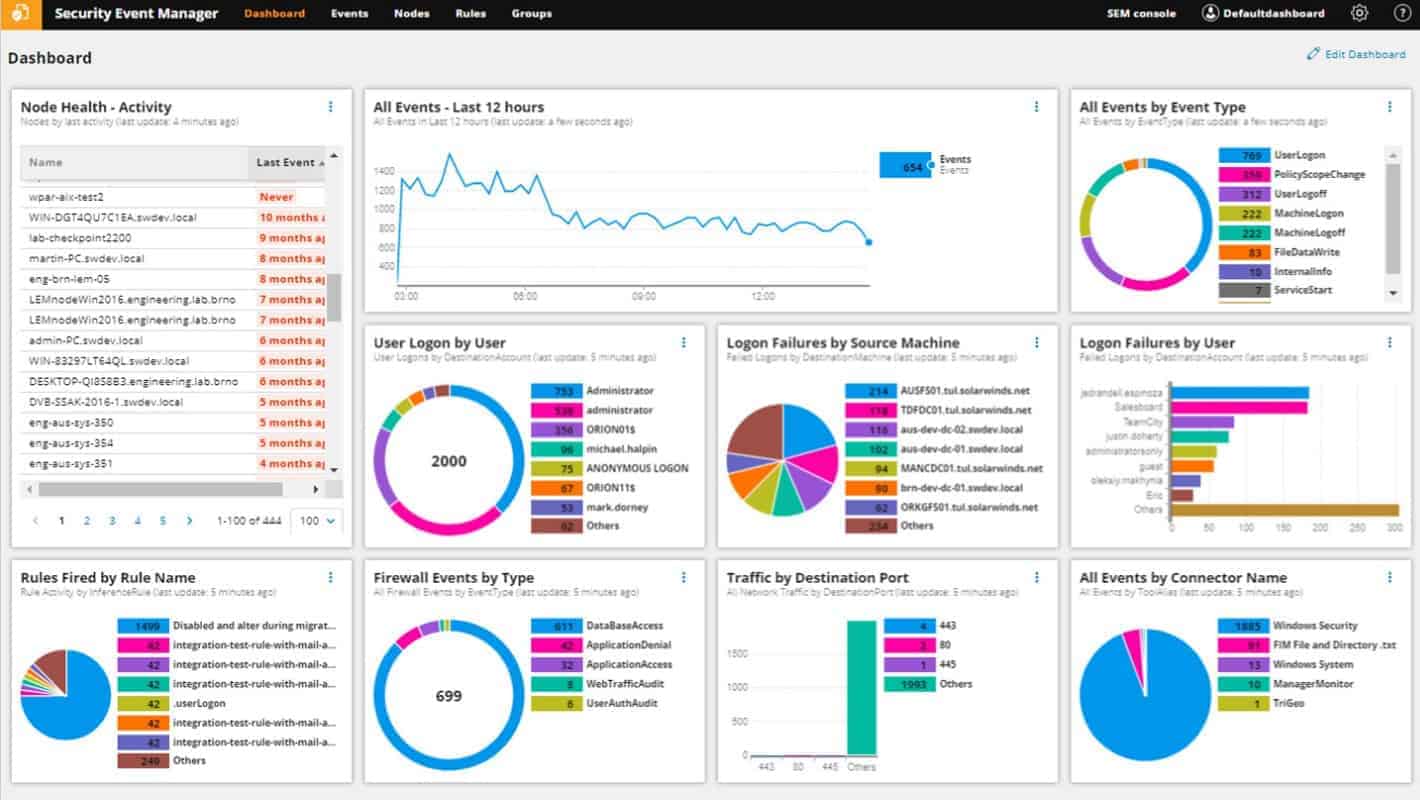
The SolarWinds Security Event Manager (SEM) runs on Windows Server, but it can log messages generated by Unix, Linux, and Mac OS computers as well as Windows PCs.
As a log manager, this is a host-based intrusion detection system because it is concerned with managing files on the system. However, it also manages data collected by Snort, which makes it part of a network-based intrusion detection system.
SolarWinds Security Event manager’s Key Features:
- Analyzes Log Files: SEM is capable of analyzing log files, providing insights into security events and potential threats within a network.
- Can Process Live Data: The tool is designed to process live data, allowing for real-time monitoring and analysis of security events as they occur.
- Compatible with Snort: SEM is compatible with Snort, enhancing its capabilities by integrating with a popular Intrusion Detection System (IDS) tool.
- Automatic Remediation: SEM supports automatic remediation, allowing for automated responses to identified security incidents.
- Built-in Reporting and Dashboard Features: This potentially reduces the need for additional tools for Intrusion Detection System (IDS) purposes.
Unique Business Proposition
SolarWinds SEM is a comprehensive tool that offers advanced features, like real-time threat detection and automated incident response. Its virtual appliance deployment simplifies installation, making it a good choice for organizations with limited technical expertise and resources. It helps with compliance reporting as well.
Feature-in-Focus: Automated Incident Response
The automated incident response feature can be configured to perform specified actions when a threat is detected. These actions can include disabling user access, blocking IP threats, and more. This feature acts as the first line of defense before security teams take over to mitigate the risks.
Comparitech SupportScore – 8.9
SolarWinds is another leader in the networking and monitoring space. However, in the last few years, its employee satisfaction levels have decreased more than we would have liked. Though we don’t anticipate huge drops, there can still be small gaps in the quality of customer support.
Why do we recommend it?
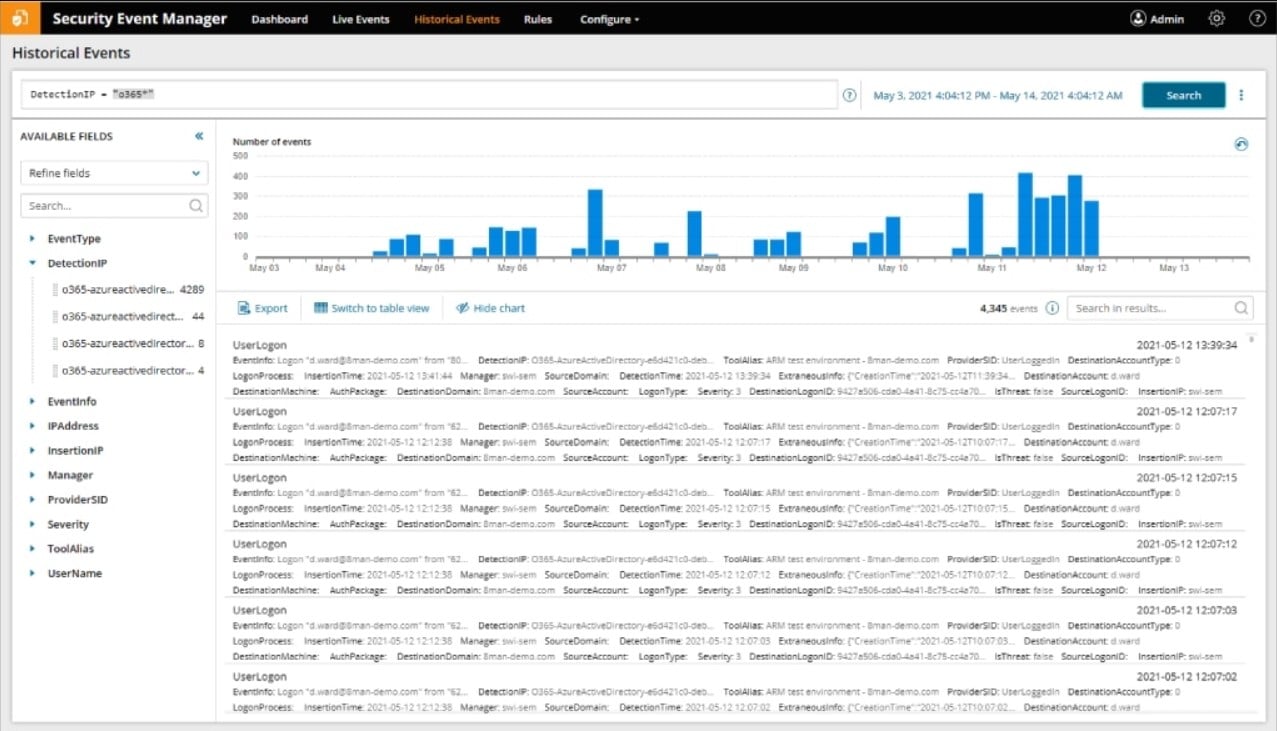
SolarWinds Security Event Manager is an on-premises package that collects and manages log files. It isn’t limited to Windows Events because it can also gather Syslog messages and the logs from applications. The tool also implements threat hunting by searching through collected logs.
Snort is a widely-used packet sniffer created by Cisco Systems (see below). It has a specific data format, which other IDS tool producers integrate into their products. This is the case with the SolarWinds Security Event Manager. Network intrusion detection systems examine traffic data as it circulates on the network. To deploy the NIDS capabilities of the Security Event Manager, you would need to use Snort as a packet capture tool and funnel captured data through to the Security Event Manager for analysis. Although LEM acts as a HIDS tool when it deals with log file creation and integrity, it is capable of receiving real-time network data through Snort, which is a NIDS activity.
The SolarWinds product can act as an intrusion prevention system as well because it can trigger actions on the detection of intrusion. The package ships with more than 700 event correlation rules, which enables it to spot suspicious activities and automatically implement remediation activities. These actions are called Active Responses.
- These Active Responses include:
- Incident alerts via SNMP, screen messages, or email
- USB device isolation
- User account suspension or user expulsion
- IP address blocking
- Processes killing
- System shutdown or restart
- Service shutdown
- Service triggering
The Snort message processing capabilities of the Security Event Manager make it a very comprehensive network security monitor. Malicious activity can be shut down almost instantly thanks to the tool’s ability to combine Snort data with other events on the system. The risk of disrupting the service through the detection of false positives is greatly reduced thanks to the finely-tuned event correlation rules.
Who is it recommended for?
This system performs full log management and also provides SIEM. These are two functions that all companies need. However, the large processing capacity of this SolarWinds tool is more than a small business would need.
During our testing, we identified the following pros and cons related to Security Event Manager.
Pros:
- Built with Enterprise in Mind: SEM is built to cater to enterprise-level needs and can monitor a variety of operating systems, including Windows, Linux, Unix, and Mac.
- Supports Tools Such as Snort: The compatibility with tools like Snort allows SEM to be part of a larger Network Intrusion Detection System (NIDS) strategy, providing a comprehensive security solution.
- Pre-configured Alerts, Correlation Rules, and Detection Templates: It comes with over 700 pre-configured alerts, correlation rules, and detection templates, offering instant insights upon installation and reducing the time needed for configuration.
Cons:
- Feature Dense: The tool is feature-dense, which might require time to fully explore and understand all available features.
You can access this network security system on a 30-day free trial.
6. OSSEC
Best for: Open-source host-based IDS
Relevant for: Security teams and compliance officers
Price: Community edition is free, while the Atomic OSSEC edition has flexible pricing. Contact the support team for a negotiated price
OSSEC stands for Open Source HIDS Security. It is the leading HIDS available and it is entirely free to use. As a host-based intrusion detection system, the program focuses on the log files on the computer where you install it. It monitors the checksum signatures of all your log files to detect possible interference. On Windows, it will keep tabs on any alterations to the registry. On Unix-like systems, it will monitor any attempts to get to the root account. Although OSSEC is an open-source project, it is actually owned by Trend Micro, a prominent security software producer.
OSSEC’s Key Features:
- Log File Analyzer: OSSEC serves as a log file analyzer, actively monitoring and analyzing log files for potential security threats or anomalies.
- Alerting System: OSSEC features an alerting system that notifies administrators of potential security incidents or suspicious activities.
- Utilizes Checksums: The platform utilizes checksums to verify the integrity of logs and files, ensuring that no unauthorized modifications have occurred.
- Supports Root Account Monitoring on Unix/Linux Systems: OSSEC supports the monitoring of the root account on Unix/Linux systems, enhancing security measures for critical system components.
Unique Business Proposition
OSSEC is an open-source host-based IDS that provides extensive security monitoring across multiple environments. It combines log analysis, rootkit detection, and real-time alerting to offer a scalable and secure solution.
Feature-in-Focus: File Integrity Monitoring (FIM)
A highlight of OSSEC is its real-time file integrity monitoring, which continuously monitors the critical files and directories for unauthorized modifications. It sends alerts to administrators as soon as it detects any change, and this helps IT administrators to quickly detect potential breaches.
Comparitech SupportScore – 3.6
OSSEC has always been an open-source platform with limited employees and resources. As per our evaluation, the documentation and support are highly limited.
Why do we recommend it?
OSSEC is a free host-based intrusion detection system. There is a registry tampering detection system built into this tool in addition to its main log file analysis services. The basic package of this tool requires the addition of third-party tools to collect and consolidate log messages and also to provide a front end.
The main monitoring application can cover one computer or several hosts, consolidating data in one console. Although there is a Windows agent that allows Windows computers to be monitored, the main application can only be installed on a Unix-like system, which means Unix, Linux or Mac OS. There is an interface for OSSEC for the main program, but this is installed separately and is no longer supported. Regular users of OSSEC have discovered other applications that work well as a front-end to the data-gathering tool: include Splunk, Kibana, and Graylog.
The log files covered by OSSEC include FTP, mail, and web server data. It also monitors operating system event logs, firewall and antivirus logs and tables, and traffic logs. The behavior of OSSEC is controlled by the policies that you install on it. These can be acquired as add-ons from the large user community that is active for this product. A policy defines an alert condition. Those alerts can be displayed on the console or sent as notifications via email.
Who is it recommended for?
OSSEC is very reliable and highly rated for its threat detection capabilities. However, you need to spend time marrying the tool up with other packages to get proper log management and also displays for the statistics and warnings that OSSEC generates – generally the free ELK system is used for those purposes. If you aren’t interested in working through these adaptation tasks, you would be better off with one of the other tools on this list.
During our testing, we identified the following pros and cons related to OSSEC.
Pros:
- Completely Free and Open-Source: OSSEC is entirely free and open-source, making it accessible to a wide range of users without any cost.
- Free Policies: The platform provides free policies, offering pre-configured settings and rules to assist users in securing their systems.
- Strong Community Support: OSSEC benefits from a strong community, providing ongoing support, templates, and scanning profiles to users.
Cons:
- Reliant on Community Support (Paid Support Available): While the community support is robust, OSSEC relies on the community for support. Paid support options are available for users seeking additional assistance.
- Lacks Advanced Visualization Features: Users may find the platform lacking in advanced reporting and visualization capabilities.
Trend Micro offers support for OSSEC for a fee.
7. Gatewatcher AIonIQ
Best for: Non-intrusive network threat detection
Relevant for: Security Operations Centers (SOCs) and government organizations
Price: Negotiated pricing
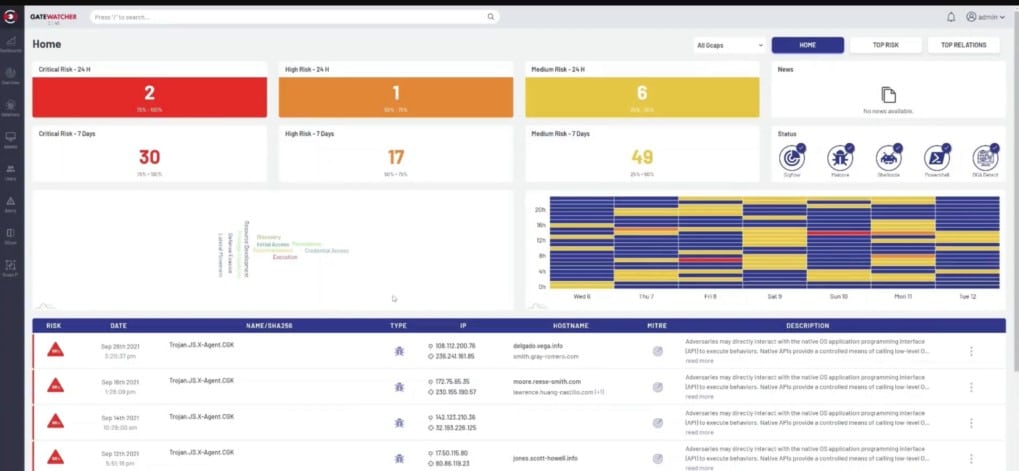
Gatewatcher AIonIQ is a network detection and response (NDR) package that examines the activity on a network and creates a profile of standard behavior for each traffic source. Part of that profile involves the endpoints that the source communicates with regularly. Deviations in a user or endpoint’s standard traffic patterns trigger deeper scrutiny and further indicators will cause the AIonIQ system to raise an alert.
Gatewatcher AlonIQ’s Key Features:
- Scans Network Traffic: Gatewatcher AIonIQ is designed to actively scan network traffic, monitoring data flow for potential security threats and anomalies.
- Generates Activity Profiles: The platform generates activity profiles, providing insights into the normal behavior of network elements and helping to identify deviations from the baseline.
- Watches Out for Malware Activity: AIonIQ focuses on detecting and preventing malware activity within the network, enhancing overall cybersecurity measures.
Unique Business Proposition
AlonIQ is an AI-powered Network Detection and Response (NDR) platform that uses anomaly detection and behavioral analysis to identify emerging threats. Its capability to provide real-time visibility into network activities and encrypted traffic enables organizations to quickly detect and respond to threats. It also integrates well with most systems.
Feature-in-Focus: Asset Mapping
AlonIQ has a unique asset mapping feature, which combines well with behavioral analysis to help understand the connections between assets and users. Consequently, it detects lateral movements and insider threats, while improving the security posture of organizations.
Why do we recommend it?
Gatewatcher AIonIQ is a network monitoring system that tracks activities, looking for anomalous behavior per user on the network or per IP address in the case of external traffic coming in. A sudden change in behavior by a user could indicate an intruder who has taken over an account. The package also looks for typical malware activity.
The package examines the activities of both users and endpoints, recording who connects to which devices and for access to which applications. The tool also looks for standard patterns of activity that are known to be carried out by such formats of malware as ransomware and worms.
As this is an NDR, the tool can be set up to implement automated responses. This is optional, however, because the system has an alternative configuration. This is to pass through activity data to a Security Information and Event Management (SIEM) system or a Security Orchestration, Automation, and Response (SOAR) service, where action can be taken.
The AIonIQ data gets its traffic data from SPAN ports or from TAPs. So, all traffic will flow through the tool, which is delivered as a network device or a virtual appliance. That low-level data will not all be passed to the Gatewatcher cloud server for analysis. Instead, the sniffer selects specific factors from headers and payloads and delivers those summaries.
The name of the tool has “AI” in it and that indicates that the system uses Artificial Intelligence – specifically machine learning – to adjust its behavior baselines and alter its alerting thresholds. This means that the package will reduce false positive reporting over time.
Who is it recommended for?
This package is a sophisticated, AI-based intrusion detection system that will also identify malware that generates network activity, such as ransomware and worms. This isn’t a free product or a service that will appeal to small businesses or startups with tight budgets. It is suitable for mid-sized and large organizations.
During our testing, we identified the following pros and cons related to AIonIQ.
Pros:
- Automatically Adjusted Baselining Managed by Machine Learning: The platform utilizes machine learning to automatically adjust baselining, adapting to changes in network behavior without requiring manual intervention.
- Identifies Intruders and Malware: AIonIQ is capable of identifying both intruders and malware within the network, contributing to proactive threat detection and response.
- Interfaces to SIEM and SOAR Services: The platform provides interfaces to Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) services, facilitating integration into broader security ecosystems.
Cons:
- Need to Inquire for a Price List: One potential drawback is that there is a need to inquire about pricing, as a price list may not be readily available. This lack of transparency can be a consideration for organizations evaluating the solution.
It is available as a hardware unit for networks but increasingly, customers are opting for the virtual appliance version, which runs over a VM or containers, so it isn’t rooted in one specific operating system. Packages include the services of a consultant who will install the system for you. However, you can further your investigations into the AIonIQ service by accessing a demo.
8. CrowdSec
Best for: Collaborative threat intelligence
Relevant for: DevOps teams and SMBs
Price: Community edition is free, SaaS enterprise edition costs $29/month, while the Cyber Threat Intelligence API access costs $200/month for 2,000 queries. If you need local synchronization, that’s priced at $18,000/month
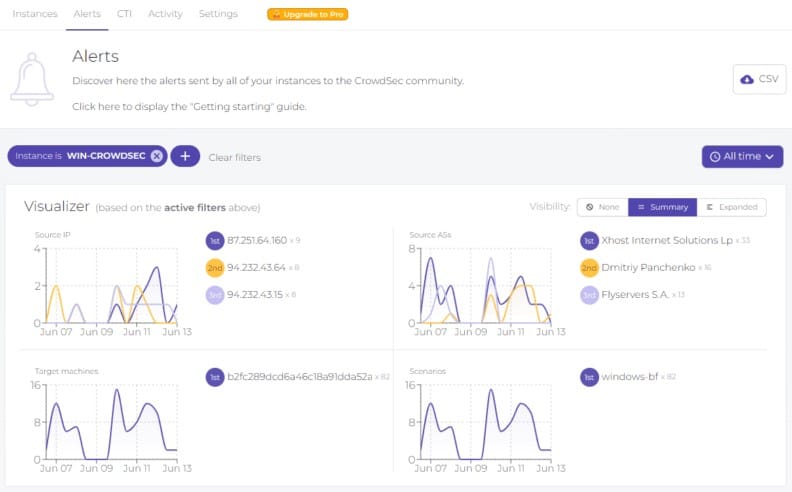
CrowdSec is a hybrid HIDS service with a comprehensive collector for in-site installation, which is called the CrowdSec Security Engine. This unit collects log files from around your network and its endpoints. These are uploaded to the CrowdSec server for threat hunting. You get access to a console on the server, which gives a view of statistics about your data – this is called CrowdSec Console.
CrowdSec’s Key Features:
- Ease of Use: The platform is designed to be user-friendly, making it accessible to a wide range of users with varying levels of technical expertise.
- Firewall Hardening: CrowdSec focuses on enhancing security by hardening firewalls against IP addresses associated with malicious activities. This proactive approach helps prevent potential threats.
Unique Business Proposition
This is a community-driven platform that uses collective intelligence to identify and mitigate threats. CrowdSec analyzes logs and combines them with the shared intelligence of its community to identify and block malicious IPs. Also, its modular infrastructure and integration make it ideal for diverse environments.
Feature-in-Focus: Community Intelligence
Its community-driven threat intelligence is a powerful feature as it can cover a wide range of threats and use cases. Every time a user detects a malicious IP, it is updated in the database. In turn, this protects other users from accessing these IPs. This collective approach works well to block new and existing threats.
Why do we recommend it?
The Community edition of CrowdSec is free to use and it is impressive. This means that you can get a competent IPS for no money and its availability for all of the major operating systems (except macOS) gives it a wide audience. The global blocklist protects your network from hackers before they even get to your site.
You need to install the Security Engine on each endpoint on your network. If you have hardware network firewalls, you can also install the Security Engine there. You then nominate one server on your network as a forwarder. This is called a LAPI. With this in place, all the Security Engine instances will send logs over the local network to the LAPI, which then uploads them through a protected tunnel connection to the CrowdSec server.
The CrowdSec system performs its threat detection and if it detects a problem it registers an alert in the console. It also sends an instruction back to the LAPI, which forwards it to the relevant Security Engines and also to the firewall. This makes CrowdSec an intrusion prevention system.
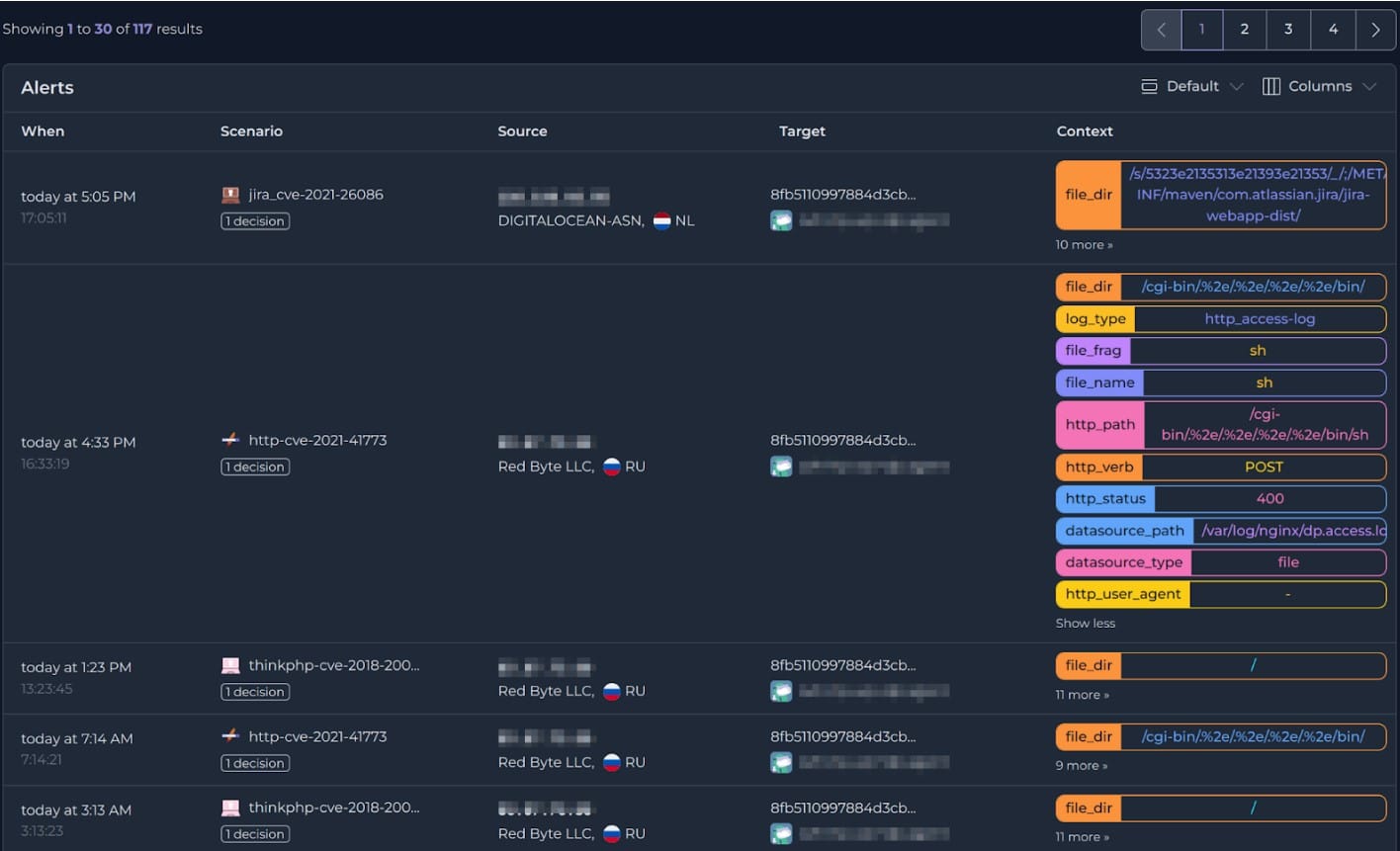
The warning that the threat detection system sends to the site is an IP address that needs to be blocked. The Security Engine on the device that has suspicious activity implements a “bouncer” action, which blocks further communication with that banned address. Simultaneously, the IP address is added to the blacklist of the site’s firewall. Thus, the intruder is blocked from the entire site.
CrowdSec serves many customers on its server simultaneously. When one user account’s threat hunter identifies a malicious action, it registers the IP address of the source in its global blocklist, which is instantly shared among all users. When the Console of one account receives a notification of a new address to block, it immediately sends that instruction to the LAPI.
Who is it recommended for?
Any business would benefit from the CrowdSec system. Its threat intelligence feed that sends your firewall a blocklist of malicious sources is in itself worth a lot. This tool doesn’t deal with insider threats, but, as it is an intrusion detection system, that’s fair enough.
During our testing, we identified the following pros and cons related to CrowdSec.
Pros:
- Firewall IP Blocking Against Hackers: The platform’s ability to automatically block IP addresses associated with malicious activities contributes to a more robust security posture.
- Free Version for Most Businesses: Offers a free version that is considered sufficient for the security needs of most businesses. This can be a cost-effective solution for organizations with budget constraints.
Cons:
- No Version for macOS: Lacks a dedicated version for macOS. This may be a drawback for organizations or individuals using macOS systems.
If all of your endpoints are macOS, you won’t be able to use this tool. If you have at least one computer running Linux, Windows, or Unix, you can at least benefit from the universal threat intelligence feed.
9. Suricata
Best for: High-performance network analysis and threat detection
Relevant for: Private and public organizations that want to protect their assets
Price: Free
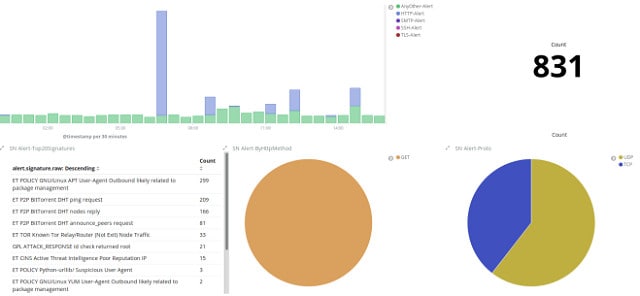
Suricata is probably the main alternative to Snort. There is a crucial advantage that Suricata has over Snort, which is that it collects data at the application layer. This overcomes the blindness that Snort has to have signatures split over several TCP packets. Suricata waits until all of the data in packets is assembled before it moves the information into analysis.
Suricata’s Key Features:
- Efficient Analysis and Reassembly of Protocol Packets: The platform efficiently analyzes and reassembles protocol packets, contributing to effective network traffic analysis.
- Monitors Multiple Protocols: Suricata can monitor multiple protocols and verify the integrity of certificates in TLS, HTTP, and SSL traffic, enhancing security measures.
- Operates on Live Data: The platform is capable of operating on live data, allowing real-time analysis and response to network events.
Unique Business Proposition
Developed by the Open Information Security Foundation (OISF), this is a versatile platform that combines intrusion detection, intrusion prevention, and network security monitoring. It is also compatible with Snort’s rulesets to offer flexible monitoring.
Feature-in-Focus: Multithreaded Architecture
Suricata’s multithreaded architecture allows it to efficiently handle high workloads and throughputs. It can also process traffic concurrently across multiple cores to identify threats as they occur.
Comparitech SupportScore – 3.7
This is an open-source project, where the owners continue to support and manage the tool. Though you can expect a response, it can be delayed. But, its documentation is good and can provide answers to most questions.
Why do we recommend it?
Suricata is a network-based intrusion detection system (NIDS) that examines Application Layer data. This tool is free to use but it is a command line system so you will have to match it up with other applications to see the output of the searches.
Although the system works at the application layer, it can monitor protocol activity at lower levels, such as IP, TLS, ICMP, TCP, and UDP. It examines real-time traffic for different network applications including FTP, HTTP, and SMB. The monitor doesn’t just look at packet structure. It can examine TLS certificates and focus on HTTP requests and DNS calls. A file extraction facility lets you examine and isolate suspicious files with virus infection characteristics.
Suricata is compatible with Snort and you can use the same VRT rules written for that NIDS leader. Those third-party tools, such as Snorby, BASE, Squil, and Anaval that integrate with Snort can also bolt on to Suricata. So, accessing the Snort community for tips and free rules can be a big benefit for Suricata users. A built-in scripting module allows you to combine rules and get a more precise detection profile than Snort can give you. Suricata uses both signature and anomaly detection methodologies.
Suricata has a clever processing architecture that enables hardware acceleration by using many different processors for simultaneous, multi-threaded activity. It can even run partly on your graphics card. This distribution of tasks keeps the load from bearing down on just one host. That’s good because one problem with this NIDS is that it is quite heavy on processing.
Who is it recommended for?
Like the other open-source systems on this list, such as OSSEC, Suricata is great at intrusion detection but not so great at displaying results. So, it needs to be paired with a system, such as Kibana. If you don’t have the confidence to stitch a system together, you shouldn’t opt for Suricata.
During our testing, we identified the following pros and cons related to Suricata.
Pros:
- Collects Data at Application Layers: Suricata excels in collecting data at the application layers, offering unique visibility that extends beyond what products like Snort can provide.
- Compatibility with VRT Rule Format: Suricata is compatible with other tools that use the VRT (Emerging Threats) rule format, promoting interoperability within the security ecosystem.
- Application Layer Operations: Suricata operates at the application layer, providing unique visibility into network traffic at a level that some other tools, like Snort, may not achieve.
Cons:
- Smaller Community Size Compared to Some Tools: While Suricata is free and open-source, it may not have as large of a community as tools like Snort or Zeek.
Suricata has a very slick-looking dashboard that incorporates graphics to make analysis and problem recognition a lot easier. Despite this expensive-looking front-end, Suricata is free of charge.
10. Zeek
Best for: Flexible network security monitoring
Relevant for: Threat hunters and SMBs
Price: Free
Zeek (formerly Bro) is a free NIDS that goes beyond intrusion detection and can provide you with other network monitoring functions as well. The user community of Zeek includes many academic and scientific research institutions.
The Zeek intrusion detection function is fulfilled in two phases: traffic logging and analysis. As with Suricata, Zeek has a major advantage over Snort in that its analysis operates at the application layer. This gives you visibility across packets to get a broader analysis of network protocol activity.
Zeek’s Key Features:
- Signature Detection: Zeek employs signature-based detection methods, allowing it to identify known threats based on predefined patterns or signatures.
- Anomaly Analysis: The platform conducts anomaly analysis, recognizing deviations from established norms or behaviors, which is crucial for identifying unknown or emerging threats.
- Supports Application Layer Traffic Analysis: Zeek supports in-depth analysis of application layer traffic, allowing for a comprehensive understanding of network activities.
- Automation Through Scripting: The platform supports automation through scripting, allowing administrators to script various actions easily. This enhances efficiency and streamlines response efforts.
Unique Business Proposition
This open-source tool is well-known for its deep packet inspection and network traffic analysis. Unlike signature-based firewalls, Zeek monitors the traffic patterns and generates detailed logs that can help with root cause detection.
Feature-in-Focus: Event-Driven Scripting Engine
Its event-driven scripting engine makes it easy to create complex custom scripts that improve the rate of threat detection. Using this feature, security teams can tailor Zeek’s monitoring to suit specific goals and environments.
Why do we recommend it?
Zeek is a NIDS and so it is a rival to Suricata. This tool is open source and free to use as well. Unfortunately, like Suricata, this is a command line system. Zeek has its own programming structure, which makes it very flexible and is great for network professionals who like to code.
Comparitech SupportScore – 4.2
Zeek is one of the oldest products on our list and has made it here because of its decent customer support and well-written documentation. Though it has only a handful of employees, the quality of customer support offered has been satisfactory.
The analysis module of Zeek has two elements that both work on signature detection and anomaly analysis. The first of these analysis tools is the Zeek event engine. This tracks for triggering events, such as a new TCP connection or an HTTP request. Each event is logged, so this part of the system is policy-neutral — it just provides a list of events in which analysis may reveal repetition of actions or suspiciously diverse activity generated by the same user account.
The mining of that event data is performed by policy scripts. An alert condition will provoke an action, so Zeek is an intrusion prevention system as well as a network traffic analyzer. The policy scripts can be customized but they generally run along a standard framework that involves signature matching, anomaly detection, and connection analysis.
You can track HTTP, DNS, and FTP activity with Zeek and also monitor SNMP traffic, enabling you to check on device configuration changes and SNMP Trap conditions. Each policy is a set of rules and you are not limited to the number of active policies or the protocol stack additional layers that you can examine. At lower levels, you can watch out for DDoS syn flood attacks and detect port scanning.
Who is it recommended for?
If you have no technical skills, you shouldn’t consider Zeek. This tool requires programming capabilities as well as the ability to feed data through from one system to another because Zeek doesn’t have its own front end.
During our testing, we identified the following pros and cons related to Zeek.
Pros:
- Highly Customizable: Zeek is highly customizable, catering to the needs of security professionals and providing flexibility in configuring and adapting to specific network environments.
- Utilizes Signature Detection and Anomalous Behavior Scanning: Zeek employs both signature-based detection and anomaly analysis, enabling it to identify both known threats and unknown or emerging security issues.
Cons:
- Only Available for Unix, Linux, and Mac: Zeek is limited to Unix, Linux, and Mac operating systems, potentially excluding users on other platforms.
- Not User-Friendly: Zeek is not considered user-friendly and demands a deep understanding of SIEM, NIDS, IIDS, and related technologies.
- Better Suited for Researchers and Specialists: Due to its complexity and extensive capabilities, Zeek is better suited for researchers and specialists in the field of network security.
Zeek can be installed on Unix, Linux, and Mac OS.
11. Security Onion
Best for: Open-source security monitoring
Relevant for: Government organizations and large enterprises
Price: Community edition is free. To buy the Pro edition, reach out to one of the partners or resellers
For a blend of IDS solutions, you could try the free Security Onion system. Most of the IDS tools in this list are open-source projects. That means that anyone can download the source code and change it.
That’s exactly what the developer of Security Onion did. He took elements from the source code of Snort, Suricata, OSSEC, and Zeek and stitched them together to make this free Linux-based NIDS/HIDS hybrid. Security Onion is written to run on Ubuntu and it also integrates elements from front-end systems and analysis tools including Snorby, Sguil, Squert, Kibana, ELSA, Xplico, and NetworkMiner.
Security Onion’s Key Features:
- HIDS/NIDS Hybrid: Security Onion operates as a Hybrid IDS and NIDS, providing comprehensive coverage for both host-based and network-based security monitoring.
- Log File Tamper Alerts: The platform includes a feature that alerts users to tampering attempts on log files, helping to maintain the integrity of critical security data.
- Built-In Packet Sniffer: Security Onion includes a built-in packet sniffer, enabling real-time analysis of network traffic for immediate threat detection and response.
Unique Business Proposition
Security Onion is a free Linux distribution that’s ideal for enterprise security monitoring, intrusion detection, and log management. It combines signature-based detection and behavioral analysis to allow security teams to efficiently identify and investigate security-related events.
Feature-in-Focus: Integration Capabilities
A notable feature of this tool is its integration with other open-source tools for scalability and extensibility. In particular, it integrates well with Suricata, Zeek, and Elastic Stack to provide deep visibility into network and device activities.
Comparitech SupportScore – 4.5
Security Onion is an open-source tool that does not have a paid version. So, there is no dedicated customer support team, and all queries are answered by a group of volunteers and the community. However, its documentation is comprehensive.
Why do we recommend it?
Security Onion addresses the fact that all of the excellent open-source systems that are available for intrusion detection require to be stitched together in order to make a proper IDS. Each tool, while excellent in its own field, only provides part of the functionality that you get from the paid products on this list from providers such as SolarWinds and ManageEngine.
Although Security Onion is classified as a NIDS, it does include HIDS functions as well. It will monitor your log and config files for suspicious activities and check on the checksums of those files for any unexpected changes. One downside of the Security Onion’s comprehensive approach to network infrastructure monitoring is its complexity. It has several different operating structures and there isn’t really sufficient learning material online or bundled in to help the network administrator get to grips with the full capabilities of the tool.
Network analysis is conducted by a packet sniffer, which can display passing data on a screen and also write to a file. The analysis engine of Security Onion is where things get complicated because there are so many different tools with different operating procedures that you may well end up ignoring most of them. The interface of Kibana provides the dashboard for Security Onion and it does include some nice graphs and charts to ease status recognition.
Who is it recommended for?
Although Security Onion gives you a bundle of all the elements you need for an IDS. It just comes as an installation package that puts all of those different applications on your computer – it doesn’t fit them together for you. Fortunately, Security Onion Solutions offers a tech support service that will set everything up for you. So, rather than paying for the software, you pay for someone to install it for you and make it all work. With this option, anyone can get an excellent IDS without the need of technical expertise or a staff of coders.
During our testing, we identified the following pros and cons related to Security Onion.
Pros:
- Free Open-Source Software: Security Onion is freely available as open-source software, making it accessible to a wide range of users without additional costs.
- Designed for Security Professionals: The platform is designed with security professionals in mind, offering advanced features and capabilities suitable for complex security environments.
Cons:
- Only Available for Linux: Security Onion is limited to Linux operating systems, potentially excluding users on other platforms.
- Uses Kibana for Visualization: The platform employs Kibana for visualization, which may be complex for users unfamiliar with the tool.
- Interface Not User-Friendly: Security Onion’s interface is considered complicated and may not be user-friendly, particularly for those without a background in security or network monitoring.
Both signature-based and anomaly-based alert rules are included in this system. You get information on device status as well as traffic patterns. All of this could really do with some action automation, which Security Onion lacks.
12. AIDE
Best for: Lightweight intrusion detection and file integrity monitoring
Relevant for: Home users and small security teams
Price: Free
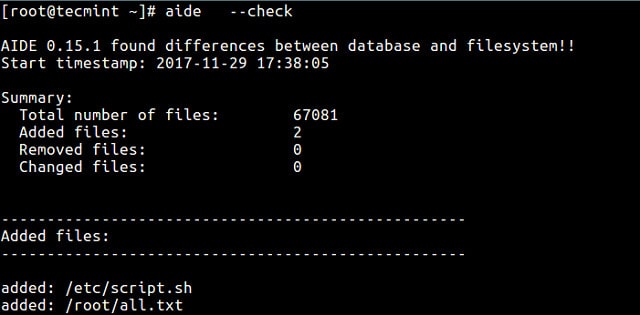
“Advanced Intrusion Detection Environment” is a lot to write, so the developers of this IDS software decided to abbreviate its name to AIDE. This is a free HIDS that focuses on rootkit detection and file signature comparisons for Unix and Unix-like operating systems, so it will work on Mac OS and Linux as well.
When we tested AIDE we found the following key features.
AIDE’s Key Features:
- Creates Configuration Baseline: AIDE establishes a configuration baseline by recording the initial state of files and system settings, providing a reference point for authorized configurations.
- Rolls Back Unauthorized Changes: AIDE can roll back unauthorized changes by comparing the current system state with the established baseline, identifying and addressing unauthorized modifications.
Unique Business Proposition
A free host-based IDS that monitors and detects unauthorized changes to files and directories on Unix-based systems. It is also simple to use and at the same time, highly efficient in environments with limited resources, like legacy systems and gapped networks.
Feature-in-Focus: File Integrity Monitoring
A standout feature is file integrity monitoring, which allows administrators to use regular expressions and store them in a database. When required, these expressions can be applied to files and directories to determine if they have been modified.
Comparitech SupportScore – 0.5
AIDE is another old tool that has been in existence for the last few decades. This is also an open-source project, with little documentation. There is no customer support team.
Why do we recommend it?
AIDE offers far more than scanning log files for specific indicators. It battles rootkit malware and it identifies files containing viruses. So, this IDS is very focused on spotting malware. The service checks on software and hardware configuration files. Backs them up and restores that stored version if unauthorized changes occur. This blocks typical intruder behavior that tries to loosen system security by altering system configurations.
If you have considered Tripwire, you would be better off looking at AIDE instead, because this is a free replacement for that handy tool. Tripwire has a free version, but a lot of the key functions that most people need from an IDS are only available with the paid-for Tripwire, so you get a lot more functionality for free with AIDE.
The system compiles a database of admin data from config files when it is first installed. That creates a baseline and then any changes to configurations can be rolled back whenever changes to system settings are detected. The tool includes both signature and anomaly monitoring methods. System checks are issued on demand and do not run continuously, which is a bit of a shortfall with this HIDS. As this is a command-line function, though, you can schedule it to run periodically with an operating method, such as cron. If you want near real-time data, you could just schedule it to run very frequently.
Who is it recommended for?
While you need technical skills to set up most of the free tools on this list, you need to be a highly skilled programmer to even understand the installation instructions for AIDE. This tool is very obscure and poorly documented and so it is only for the very technically adept.
During our testing, we identified the following pros and cons related to AIDE.
Pros:
- Free Open-Source Software: AIDE is freely available as open-source software, making it accessible to a broad user base without additional costs.
- Designed for Security Professionals: The tool is designed with security professionals in mind, catering to their needs for advanced intrusion detection and system integrity monitoring.
- Extremely Lightweight Deployment: AIDE is known for its lightweight deployment, minimizing resource consumption and impact on system performance.
Cons:
- Only Available for Linux and Unix Operating Systems: AIDE is limited to Linux and Unix operating systems, potentially excluding users on other platforms.
- Not Beginner-Friendly: The tool may not be beginner-friendly, requiring users to have a certain level of expertise in security and system administration.
- Utilizes Command-Line Interface: AIDE primarily uses a command-line interface (CLI) for most actions, which might be less intuitive for users who prefer graphical user interfaces.
AIDE is really just a data comparison tool and it doesn’t include any scripting language, you would have to rely on your shell scripting skills to get data searching and rule implementation functions into this HIDS. Maybe AIDE should be considered more as a configuration management tool rather than as an intrusion detection system.
Types of Intrusion Detection Systems
There are two main types of intrusion detection systems (both are explained in more detail later in this guide):
- Host-based Intrusion Detection System (HIDS) – this system will examine events on a computer on your network rather than the traffic that passes around the system.
- Network-based Intrusion Detection System (NIDS) – this system will examine the traffic on your network.
Network intrusion detection software and systems are now essential for network security. Fortunately, these systems are very easy to use and most of the best IDSs on the market are free to use. In this review, you will read about the ten best intrusion detection system software that you can install now to start protecting your network from attack. We cover tools for Windows, Linux, and Mac.
Host-based Intrusion Detection Systems (HIDS)
Host-based intrusion detection systems, also known as host intrusion detection systems or host-based IDS, examine events on a computer on your network rather than the traffic that passes around the system. This type of intrusion detection system is abbreviated to HIDS and it mainly operates by looking at data in admin files on the computer that it protects. Those files include log files and config files.
A HIDS will back up your config files so you can restore settings should a malicious virus loosen the security of your system by changing the setup of the computer. Another critical element that you want to guard against is root access on Unix-like platforms or registry alterations on Windows systems. A HIDS won’t be able to block these changes, but it should be able to alert you if any such access occurs.
Each host the HIDS monitors must have some software installed on it. You can just get your HIDS to monitor one computer. However, it is more typical to install the HIDS on every device on your network. This is because you don’t want to overlook config changes on any piece of equipment. Naturally, if you have more than one HIDS host on your network, you don’t want to have to login to each one to get feedback. So, a distributed HIDS system needs to include a centralized control module. Look for a system that encrypts communications between host agents and the central monitor.
See also: The Best HIDS
Network-based Intrusion Detection Systems (NIDS)
Network-based intrusion detection, also known as a network intrusion detection system or network IDS, examines the traffic on your network. As such, a typical NIDS has to include a packet sniffer to gather network traffic for analysis.
The analysis engine of a NIDS is typically rule-based and can be modified by adding your own rules. With many NIDS, the provider of the system, or the user community, will make rules available to you and you can just import those into your implementation. Once you become familiar with the rule syntax of your chosen NIDS, you will be able to create your own rules.
Chaining back to traffic collection, you don’t want to dump all of your traffic into files or run the whole lot through a dashboard because you just wouldn’t be able to analyze all of that data. So, the rules that drive analysis in a NIDS also create selective data capture. For example, if you have a rule for a type of worrisome HTTP traffic, your NIDS should only pick up and store HTTP packets that display those characteristics.
Typically, a NIDS is installed on a dedicated piece of hardware. High-end paid-for enterprise solutions come as a piece of network kit with the software pre-loaded onto it. However, you don’t have to pay out big bucks for the specialist hardware. A NIDS does require a sensor module to pick up traffic, so you may be able to load it onto a LAN analyzer, or you may choose to allocate a computer to run the task. However, make sure the piece of equipment that you choose for the task has enough clock speed not to slow down your network.
Related post: Best NIDS Software
HIDS or NIDS?
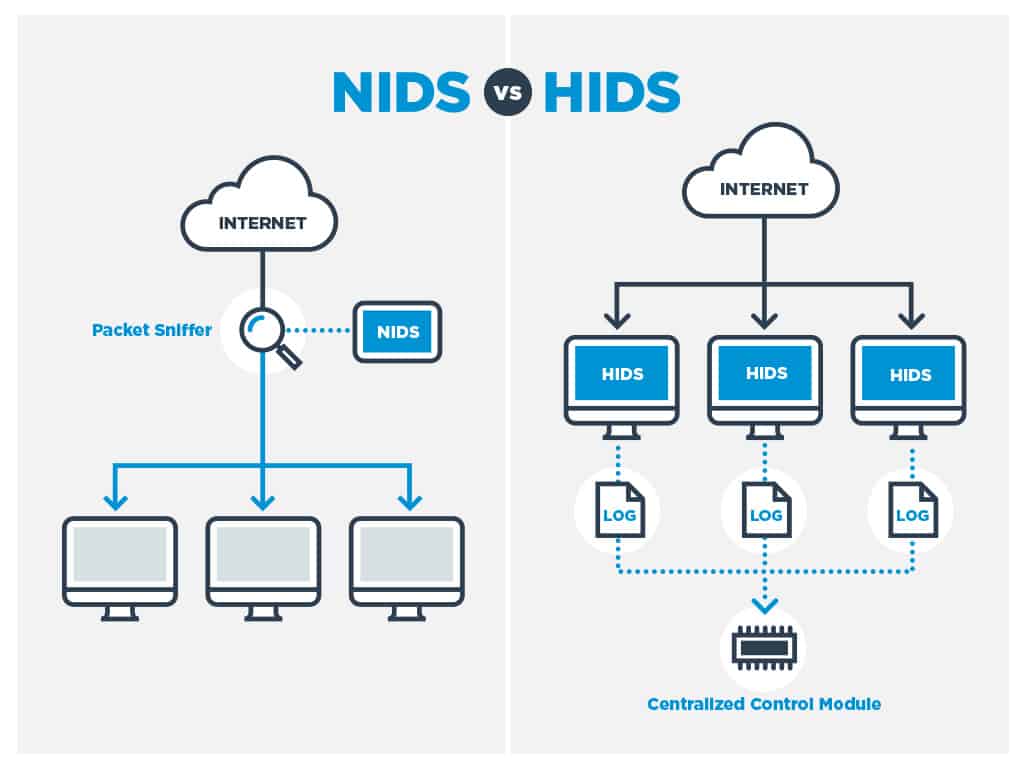
The short answer is both. A NIDS will give you a lot more monitoring power than a HIDS. You can intercept attacks as they happen with a NIDS. In contrast, a HIDS only notices anything is wrong once a file or a setting on a device has already changed. However, just because HIDS don’t have as much activity as NIDSs doesn’t mean that they are less important.
The fact that the NIDS is usually installed on a stand-alone piece of equipment means that it doesn’t drag down the processors of your servers. However, the activity of HIDS is not as aggressive as that of NIDS. A HIDS function can be fulfilled by a lightweight daemon on the computer and shouldn’t burn up too much CPU. Neither system generates extra network traffic.
Detection methods: Signature-based or Anomaly-based IDS
Whether you are looking for a host intrusion detection system or a network intrusion detection system, all IDSs use two modes of operation — some may only use one or the other, but most use both.
Signature-based IDS
Anomaly-based IDS
Signature-based IDS
The signature-based method looks at checksums and message authentication. Signature-based detection methods can be applied just as well by NIDS as by HIDS. A HIDS will look at log and config files for any unexpected rewrites, whereas a NIDS will look at the checksums in captured packets and message authentication integrity of systems such as SHA1.
The NIDS may include a database of signatures that packets known to be sources of malicious activities carry. Fortunately, hackers don’t sit at their computers typing like fury to crack a password or access the root user. Instead, they use automated procedures supplied by well-known hacker tools. These tools tend to generate the same traffic signatures every time because computer programs repeat the same instructions over and over again rather than introducing random variations.
Anomaly-based IDS
Anomaly-based detection looks for unexpected or unusual patterns of activities. This category can also be implemented by both host and network-based intrusion detection systems. In the case of HIDS, an anomaly might be repeated failed login attempts or unusual activity on the ports of a device that signify port scanning.
In the case of NIDS, the anomaly approach requires establishing a baseline of behavior to create a standard situation against which ongoing traffic patterns can be compared. A range of traffic patterns are considered acceptable, and when current real-time traffic moves out of that range, an anomaly alert is provoked.
Choosing an IDS method
Sophisticated NIDSs can build up a record of standard behavior and adjust their boundaries as their service life progresses. Overall, both signature and anomaly analysis are much simpler in operation and easier to set up with HIDS software than with NIDS.
Signature-based methods are much faster than anomaly-based detection. A fully comprehensive anomaly engine touches on the methodologies of AI and can cost a lot of money to develop. However, signature-based methods boil down to the comparison of values. Indeed, in the case of HIDS, pattern matching with file versions can be a very straightforward task that anyone could perform themselves using command-line utilities with regular expressions. So, they don’t cost as much to develop and are more likely to be implemented in free intrusion detection systems.
A comprehensive intrusion detection system needs both signature-based methods and anomaly-based procedures.
Defend the network with an IPS
Now we need to consider intrusion prevention systems (IPSs). IPS software and IDSs are branches of the same technology because you can’t have prevention without detection. Another way to express the difference between these two branches of intrusion tools is to call them passive or active. A straightforward intrusion monitoring and alerting system is sometimes called a “passive” IDS. A system that not only spots an intrusion but takes action to remediate any damage and block further intrusion attempts from a detected source, is also known as a “reactive” IDS.
Reactive IDSs, or IPSs, usually don’t implement solutions directly. Instead, they interact with firewalls and software applications by adjusting settings. A reactive HIDS can interact with a number of networking aides to restore settings on a device, such as SNMP or an installed configuration manager. Attacks on the root user, or admin user in Windows, usually aren’t dealt with automatically as the blocking of an admin user or changing the system password would result in locking the system administrator out of the network and servers.
Many users of IDSs report a flood of false positives when they first install their defense systems, just as IPSs automatically implement defense strategy on detection of an alert condition. Incorrectly calibrated IPSs can cause havoc and bring your legitimate network activity to a standstill.
To minimize the network disruption that can be caused by false alarms, you should introduce your intrusion detection and prevention system in stages. Triggers can be tailored and you can combine warning conditions to create custom alerts. The statement of actions that need to be performed on the detection of potential threats is termed a policy. The interaction of intrusion detection and prevention procedures with firewalls should be particularly fine-tuned to prevent your business’s genuine users from being locked out by over-tight policies.
Intrusion detection systems by type and operating system
The producers of IDS software focus on Unix-like operating systems. Some produce their code according to the POSIX standard. In all of these cases, that means that Windows is excluded. As the Mac OS operating systems of Mac OS X and macOS are based on Unix, these operating systems are much better catered to in the IDS world than in other software categories. The table below explains which IDSs are host-based, which are network-based, and which operating systems each can be installed on.
You may read some reviews that claim that Security Onion can be run on Windows. It can if you first install a virtual machine and run it through that. However, for the definitions in this table, we only count software as being compatible with an operating system if it can be installed directly.
Top Intrusion Detection Software & Tools
| IDS | HIDS/NIDS | Unix | Linux | Windows | Mac OS |
|---|---|---|---|---|---|
| SolarWinds Security Event Manager EDITOR'S CHOICE | Both | No | No | Yes | No |
| ManageEngine EventLog Analyzer FREE TRIAL | HIDS | Yes | Yes | Yes | Yes |
| ManageEngine Log360 FREE TRIAL | NIDS | Yes | Yes | Yes | Yes |
| ESET Protect FREE TRIAL | HIDS | No | Yes | Yes | Yes |
| Snort | NIDS | Yes | Yes | Yes | No |
| OSSEC | HIDS | Yes | Yes | Yes | Yes |
| CrowdSec | HIDS | Yes | Yes | Yes | No |
| Suricata | NIDS | Yes | Yes | Yes | Yes |
| Zeek | NIDS | Yes | Yes | No | Yes |
| Sagan | Both | Yes | Yes | No | Yes |
| Security Onion | Both | No | Yes | No | No |
| AIDE | HIDS | Yes | Yes | No | Yes |
| OpenWIPS-NG | NIDS | No | Yes | No | No |
| Samhain | HIDS | Yes | Yes | No | Yes |
| Fail2Ban | HIDS | Yes | Yes | No | Yes |
Intrusion Detection Systems for Unix
To restate the information in the table above into a Unix-specific list, here are the HIDS and NIDS you can use on the Unix platform.
- Host intrusion detection systems:
- EventLog Analyzer
- OSSEC
- CrowdSec
- Sagan
- AIDE
- Samhain
- Fail2Ban
- Network intrusion detection systems:
- Snort
- Zeek
- Suricata
- Sagan
Intrusion Detection Systems for Linux
Here are lists of the host intrusion detection systems and network intrusion systems that you can run on the Linux platform.
Host intrusion detection systems:
- EventLog Analyzer
- OSSEC
- CrowdSec
- ESET Protect
- Sagan
- Security Onion
- AIDE
- Samhain
- Fail2Ban
- Network intrusion detection systems:
- Snort
- Zeek
- Suricata
- Sagan
- Security Onion
- Open WIPS-NG
Intrusion Detection Systems for Windows
Despite the popularity of Windows Server, the developers of intrusion detection systems don’t seem to be very interested in producing software for the Windows operating system. Here are the few IDSs that run on Windows.
- Host intrusion detection systems:
- SolarWinds Security Event Manager
- EventLog Analyzer
- OSSEC
- ESET Protect
- CroedSec
- Network intrusion detection systems:
- SolarWinds Security Event Manager
- Snort
- Suricata
Intrusion Detection Systems for Mac OS
Mac owners benefit from the fact that Mac OS X and macOS are both based on Unix and so there are far more intrusion detection system options for Mac owners than those who have computers running the Windows operating system.
- Host intrusion detection systems:
- EventLog Analyzer
- OSSEC
- ESET Protect
- AIDE
- Network intrusion detection systems:
- Zeek
- Suricata
How to select IDS software for your network
The hardware requirement of network-based IDS solution may put you off and push you towards a host-based system, which is a lot easier to get up and running. However, don’t overlook the fact that you don’t need specialized hardware for these systems, just a dedicated host.
In truth, you should be looking at getting both a HIDS and a NIDS for your network. This is because you need to watch out for configuration changes and root access on your computers as well as looking at unusual activities in the traffic flows on your network.
The good news is that all of the systems on our list are free of charge or have free trials, so that you could try out a few of them. The user community aspect of these systems may draw you towards one in particular if you already have a colleague that has experience with it. The ability to get tips from other network administrators is a definitive draw to these systems. It makes them even more appealing than paid-for solutions with professional Help Desk support.
If your company is in a sector that requires standard security compliance, such as a PCI, then you really are going to need an IDS solution in place. Also, if you hold personal information on members of the public, your data protection procedures need to be up to scratch to prevent your company from being sued for data leakage.
Although it probably takes all of your working day just to keep on top of your network admin in-tray, don’t put off the decision to install an intrusion detection system. Hopefully, this guide has given you a push in the right direction. If you have any recommendations on your favorite IDS and if you have experience with any of the software mentioned in this guide, leave a note in the comments section below and share your thoughts with the community.
Our Methodology for Choosing the Nest IDS Software
At Comparitech, our goal is to provide honest and unbiased reviews of different tools to help you make an informed decision on which tool will work best for your organization’s needs. To identify these tools, we analyzed the feature set of each tool and combined it with real-world case studies and user reviews. Here is the methodology we followed.
1. Feature Set
One of the first things we looked at was the feature set. We wanted the tool to be as extensive as possible to cover different scenarios, and accordingly, selected tools that had behavioral analysis, anomaly detection, port scanning, and others that can identify known and unknown threats.
2. Business Environments
Along with the features, we also prioritized tools that can fit in different business environments, so they can be extended to cover multiple use cases. Some of our tools work well for organizations of all sizes and come with flexible deployment options.
3. Ease of Use
Usability is one of the key areas of our focus, and keeping in line with this philosophy, the best tools have an intuitive user interface. Initial setup and configuration also require fewer resources.
4. Pricing
Transparency in pricing can help you better evaluate different tools and identify the one that best fits your needs and budget. As much as possible, we have given weightage to tools that display pricing on their website.
5. Support and Documentation
Other key areas for us are support and documentation. We have developed a proprietary score called SupportScore to evaluate these two aspects, and tools with higher scores are featured at the top of our list.
6. Our Broader B2B Methodology
The above-mentioned evaluation criteria align with our broader B2B methodology, where we evaluate every tool based on the relevance of its features, transparency in pricing, usability, and applicability across scenarios. We use a combination of user reviews, real-world use cases, and hands-on testing where possible.
Check out our detailed B2B software methodology page to learn more.
Comparitech SupportScore methodology
We have come up with a proprietary score called the SupportScore that evaluates the quality of customer support offered by vendors. This is a weighted score that takes into account factors like the size of the support team, available documentation and its quality, job satisfaction levels of employees, financial stability, and more. The score will be from 0 to 10, where 10 is the highest.
Check out our detailed B2B software methodology page to learn more.
Why Trust Us?
Our goal is to provide complete information that will help you make the right decisions for your organization. To this end, we take a structured approach that involves multiple components, like use cases, reviews, testing, evaluation, and more. Our reviews are honest and reflect the true state of every tool, so you can trust us to make decisions.
Intrusion Detection Systems FAQs
What is an IDS and IPS?
An IDS is an intrusion detection system and an IPS is an intrusion prevention system. While an IDS works to detect unauthorized access to network and host resources, an IPS does all of that plus implements automated responses to lock the intruder out and protect systems from hijacking or data from theft. An IPS is an IDS with built-in workflows that are triggered by a detected intrusion event.
Explain Snort vs OSSEC
Both Snort and OSSEC are open source IDSs. Snort is a network-based intrusion detection system (NIDS) and OSSEC is a host-based intrusion detection system (HIDS). The key difference between the approaches of Snort and OSSEC is that the NIDS methods of Snort work on data as it passes through the network. The HIDS system of OSSEC examines the log files on computers around the network to look for unexpected events. Both Snort and OSSEC are leading IDSs.
How do host-based intrusion detection systems work?
Host-based Intrusion Detection Systems (HIDS) examine log files to identify unauthorized access or inappropriate use of system resources and data. The main sources for host-based intrusion detection systems are logs generated by Syslog and Windows Events. While some host-based intrusion detection systems expect the log files to be gathered and managed by a separate log server, others have their own log file consolidators built-in and also gather other information, such as network traffic packet captures.
What are active and passive IDS?
Intrusion Detection Systems (IDS) only need to identify unauthorized access to a network or data in order to qualify for the title. A passive IDS will record an intrusion event and generate an alert to draw an operator’s attention. The passive IDS can also store information on each detected intrusion and support analysis. An active IDS is also known as an Intrusion Prevention System (IPS) or an Intrusion Detection and Prevention System (IDPS) because as well as spotting an intrusion, it implements automated actions to block out the intruder and protect resources.
How does the IDS define normal use?
There are two methods that an IDS can use to define normal use – some IDS tools use both. One is to compare events to a database of attack strategies, so the definition of normal use is any activity that does not trigger recognition of an attack. The other method is to use AI-based machine learning to record regular activity. The AI method can take a while to build up its definition of normal use.
What are the best intrusion detection and prevention systems?
Our research ranks the best intrusion detection and prevention systems as SolarWinds Security Event Manager, Snort, OSSEC, and ManageEngine EventLog Analyzer are the leading systems as outlined in this article.
Further Reading
Comparitech networking guides
- Top LAN monitoring tools
- The definitive guide to DHCP
- The definitive guide to SNMP
- The ultimate guide to mobile device management (MDM)
- The best free NetFlow analyzers and collectors for Windows
- Best free network vulnerability scanners and how to use them
- Best packet sniffers and network analyzers
- Best free bandwidth monitoring software and tools to analyze network traffic usage


This is an amazing article. You really should keep this format up. I am trying to do an AoA analysis of alternatives and this is about the only article I’ve found so far that actually has a format that I can easily put into excel. Please keep up writing like this. Having a list of products, a uniform list of what each product offers and what each product can run on. Perfect!
Good research, Im missing AIEngine on the list and probably labrea also
These were all very good and important information for me. I learned much from it.