If you’re reading this post, chances are you’ve been hit by ransomware and are looking for your next steps. First, immediately disconnect the infected device from the internet and any network it’s connected to, to prevent the ransomware from spreading further. It’s best to avoid paying the ransom because there’s no guarantee you’ll actually get your files back, and doing so can unintentionally encourage more attacks. Instead, identify the ransomware strain if possible, as this will help you find the right decryption tool. Use a reputable free ransomware decryption tool that supports your ransomware type.
Before running any tool, back up the encrypted files separately to avoid permanent loss in case something goes wrong. Once your data is recovered (or if recovery isn’t possible), wipe the system completely, reinstall your operating system, and restore clean backups. Strengthen your defenses afterward with updated antivirus software, regular backups, and security awareness practices.
In this article, we’ll take a look at some of the best ransomware decryption tools that can help you recover your encrypted files.
Ransomware attacks traditionally function by infecting targets with malware that denies victims access to their files by encrypting them and then demanding a ransom to unlock or decrypt the files
If the victim refuses to pay the ransom, they will be permanently denied access to their files. As is the case with most ransomware attacks, there is no guarantee that attackers will keep to their words if you agree to pay the ransom. Over the past few years, ransomware attacks have intensified.
There are now more than 50 variants of ransomware in circulation, and more are springing up and coming up with new modus operandi, new features, and better encryption. This is not something anyone should overlook. So what should you do in situations like this?
Here’s our list of the best Ransomware File Decryptors:
- AVG Ransomware Decryption Tools EDITOR’S CHOICE These tools are free to use and can help decrypt files encrypted by specific ransomware families, such as Apocalypse, Bart, Crypt888, Legion, and TeslaCrypt. Each strain is addressed by a separate decryptor.
- No More Ransom A project by the National High Tech Crime Unit of the Netherlands’ police, Europol’s European Cybercrime Centre, Kaspersky, and McAfee to help ransomware victims retrieve their encrypted data without having to pay the criminals.
- Emsisoft One of the top-rated ransomware decryption software that one can have on a Windows PC.
- Trend Micro Ransomware File Decryptor Designed to decrypt files that have been encrypted by 27 families of known ransomware.
- Avast Provides ransomware decryption tools for some of the most popular types of ransomware out there.
- Quick Heal Ransomware Decryption Tool Can decrypt files encrypted by 17 variants of ransomware.
The best option is to focus on preventive measures. Conduct simulation attacks and penetration tests, and ensure that any existing security holes are patched as soon as possible so that attackers won’t be able to exploit those vulnerabilities. Provide regular security awareness training to your workforce, and ensure that security best practices such as the principles of least privilege and multi-factor authentication have been implemented across all systems and users.
If you need to know more, explore our vendor highlight section just below, or skip to our detailed vendor reviews.
Best Ransomware Decryption Tools highlights
Top Feature
Free decryptors for seven major ransomware variants
Price
Free
Target Market
Best for home users, small businesses, and IT teams facing ransomware types like Apocalypse, TeslaCrypt, Bart, and others
Free Trial Length
Free
Additional Benefits:
- Completely free with no registration required
- Beginner-friendly tools with step-by-step instructions
- Practical recovery for known ransomware variants
- Educational resources included for user awareness
Features:
- Standalone decryptors for Apocalypse, Bart, BadBlock, Crypt888, Legion, SZFLocker, and TeslaCrypt
- Variant identification through behavior and filename patterns
- Plug-and-play tools for immediate recovery
- Windows-based decryption tools
- Integrated ransomware prevention in AVG Internet Security
Top Feature
Free access to 120+ decryptors backed by global law enforcement
Price
Free
Target Market
Best for individuals, SMBs, and IT departments seeking trusted, non-commercial ransomware recovery tools
Free Trial Length
Free tool
Read more ▼
Top Feature
Free decryptors for over 100 ransomware families, including STOP/DJVU
Price
Free
Target Market
SMBs, IT teams, individual users, and IT service providers
Free Trial Length
Free to Use
Read more ▼
Top Feature
Decrypts 27 ransomware families with guided analysis and file-based detection
Price
Free to use without registration or subscription
Target Market
SMBs, educational institutions, nonprofits, and enterprise users looking for an effective recovery tool
Free Trial Length
Free
Read more ▼
Top Feature
Free decryption tools for 30+ ransomware variants, backed by Avast threat intelligence
Price
Completely Free
Target Market
Individuals, small businesses, and enterprises needing a fast, trustworthy recovery option after ransomware attacks
Free Trial Length
Free
Read more ▼
Top Feature
Free decryption for 17 ransomware variants, including STOP Djvu and GandCrab — works fully offline if needed
Price
Free, no need for a Quick Heal subscription or account
Target Market
MSPs, IT teams, SMBs, and individual users needing fast, local recovery from known ransomware infections
Free Trial Length
Free
Read more ▼
How to Decrypt the Encrypted Files Without Paying Ransom?
If for whatever reason, you still get infected by ransomware, there are several tools you can use to decrypt your files depending on the variant of ransomware you are dealing with. Firstly, note that no single tool out there can decrypt all types of ransomware variants. Instead, every decryption tool is designed to deal with a particular variant specifically. Therefore you need to determine what ransomware variant encrypted your files by looking at the warning message presented by the ransomware. Once identified, you can use the decryption tool specifically designed to deal with that ransomware. Secondly, before going ahead with the decryption, be sure to remove or quarantine the ransomware infection from your system. Failure to do this will result in your files being encrypted all over again.
Most decryption tools can decrypt files encrypted by popular variants of ransomware such as Wannacry, Petya, NotPetya, TeslaCrypt, DarkSide, REvil, Alcatraz Locker, Apocalypse, BadBlock, Bart, BTCWare, EncrypTile, FindZip, Globe, Jigsaw, LambdaLocker, Legion, NoobCrypt, Stampado, among others. Ransomware developers are quick to respond when a new decryptor is released. They do this by modifying their malware to make it resilient to the decryptor. In turn, the developers of ransomware decryptors also have to update and adapt their software in what seems like an arms race to ensure its effectiveness. This is why most decryptors do not come with guarantees. This article will review the best ransomware decryption tools to help you unlock encrypted files.
The Best Ransomware File Decryptor Tools
1. AVG Anti-Ransomware Tools
Best For: Home users, small businesses, and IT teams dealing with older or common ransomware variants like Apocalypse, TeslaCrypt, Bart, and more.
Price: Free
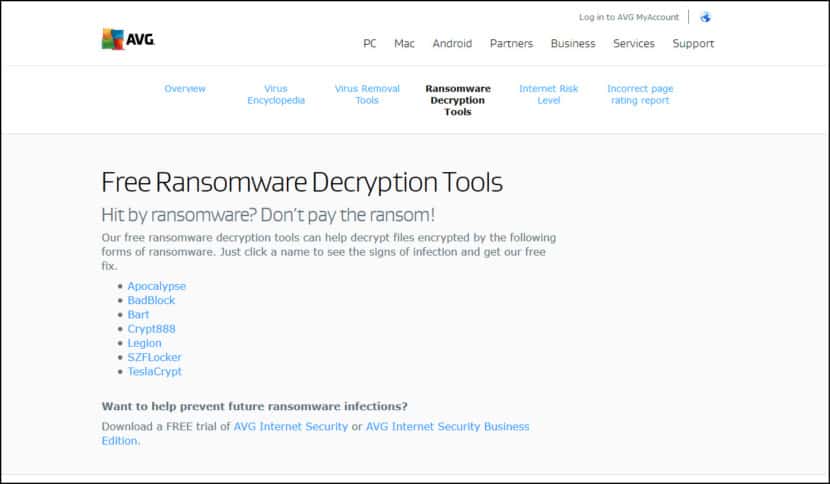
AVG Ransomware Decryption Tools offer a range of free and practical solutions for individuals and businesses looking to recover data encrypted by known ransomware strains without paying a ransom. These tools are designed to target specific ransomware types such as Apocalypse, Bart, BadBlock, Crypt888, Legion, SZFLocker, TeslaCryp, among others. Each tool is tailored to reverse the damage caused by these specific ransomware types, to enable you restore your files safely and at no cost. Here’s a table summarizing the AVG Ransomware Decryption Tools and the ransomware types they support:
| Ransomware Name | Signs of Infection | File Extension/Behavior |
|---|---|---|
| Apocalypse | Changes filenames and adds ransom notes | .locked, .encrypted, .SecureCrypted, etc. |
| BadBlock | Encrypts files without renaming | No filename change |
| Bart | Compresses and encrypts files in ZIP archives | .bart.zip |
| Crypt888 (Mircop) | Changes desktop wallpaper; renames files | Adds Lock. to beginning of filename |
| Legion | Changes wallpaper and adds pop-up ransom note | Extensions like .$centurion_legion@aol.com$.cbf |
| SZFLocker | Displays ransom note in Polish | Adds .szf to filenames |
| TeslaCrypt | One of the earliest ransomware strains | No filename change in latest version |
AVG Anti-Ransomware Tools’ key features
These are free standalone decryptors, and their most important features are:
- Free Decryption Tools: Targeted solutions for seven known ransomware strains, including Apocalypse, BadBlock, SZFLocker, and TeslaCrypt.
- Ransomware Identifier Support: Helps you recognize specific strains via filename changes and desktop behavior.
- Instant Fix Downloads: Tools are plug-and-play—just download the fix for your specific infection, follow the guide, and recover your data.
- Business and Personal Protection Upgrade Options: AVG promotes its Internet Security (and Business Edition) to help prevent future infections.
Unique Value Proposition
AVG doesn’t just offer antivirus—it gives you a real chance to decrypt your files for free, even after a successful ransomware attack. Most competing products focus heavily on prevention and don’t provide specialized, free decryptors. AVG, however, supports actual file recovery from specific ransomware without needing to pay. This is especially useful if you already know which ransomware strain hit you. You can go straight to the fix instead of starting from scratch.
Unlike Bitdefender and Emsisoft, which support a wider range of ransomware and may integrate with broader enterprise tools, AVG’s decryptors are beginner-friendly. Tools like No More Ransom (from Europol) offer more variety, but may not be as user-intuitive or targeted for specific strains as AVG’s offerings.
Why do we recommend it?
AVG’s anti-ransomware tools are recommended for their comprehensive approach to dealing with a variety of ransomware types. The inclusion of built-in ransomware protection in AVG Internet Security products offers proactive defense against ransomware attacks, ensuring enhanced security for endpoint devices.
I’ve personally used AVG’s decryptors while helping a small business client recover from a TeslaCrypt infection. The tool was simple, effective, and most importantly—free. It saved the company hours of effort and avoided a potentially damaging ransom payment. Compared to general malware tools, AVG’s decryptors are specialized, and that makes all the difference when you’re in a crisis.

Who is it recommended for?
These tools are ideal for users seeking robust protection against ransomware threats, especially those vulnerable to specific ransomware types like Apocalypse, Bart, BadBlock, and others. AVG’s solutions are also well-suited for businesses and individuals looking to safeguard endpoint devices from ransomware attacks.
AVG Ransomware Decryption Tools are suitable for SMBs, freelancers, and IT admins who lack dedicated cybersecurity teams but need a reliable, no-cost solution to recover from common ransomware attacks quickly and effectively.
Pros:
- Free for All Users: No cost, even for business use.
- Multi-Variant Coverage: Supports seven well-known ransomware types.
- Beginner-Friendly: Tools come with step-by-step guides and don’t require technical skills.
- No Sign-Up Needed: No registration or subscription required to download or use.
- Educational Resources: Includes the Ultimate Guide to Ransomware for deeper insight.
- Variant Clarity: Identifies behavioral signs of supported ransomware strains.
Cons:
- No Coverage for Modern Threats: Doesn’t support newer ransomware strains like LockBit, BlackCat, or Hive.
- Manual Strain Identification: Users must determine the ransomware type on their own.
- Windows-Only: No decryptors available for macOS or Linux.
- Limited Scope: Each tool targets a specific variant — no universal decryptor exists.
- Recovery Only: Tools do not prevent infections unless paired with AVG Internet Security.
The tools are specifically designed to deal with the following family of ransomware: Apocalypse, Bart, BadBlock, Crypt888, Legion, SZFLocker, TeslaCrypt ransomware tools. Furthermore, AVG also has a built-in ransomware protection feature in its endpoint security products, such as AVG Internet Security. This helps protect files in endpoint devices and prevent ransomware attacks by blocking file modification, deletion, and encryption.
For teams that don’t have access to enterprise-level incident response tools, AVG’s offerings act as a first-line remediation resource. They’re particularly helpful when you’re looking to triage quickly and need to get critical files back without delay.
If you’re choosing between free decryption options, AVG stands out for its clean interface, easy downloads, and the fact that it doesn’t gatekeep features behind subscriptions—something many antivirus brands still do.
EDITOR'S CHOICE
AVG Ransomware Decryption Tools are our top pick for ransomware decryption due to their comprehensive capabilities and reliability. These tools are specifically designed to unlock files encrypted by various ransomware variants, helping users regain access to their data without succumbing to ransom demands. AVG provides decryptors for numerous ransomware families, including Apocalypse, Bart, Crypt888, Legion, and TeslaCrypt, covering a wide range of ransomware threats effectively. This extensive coverage ensures that users can address a variety of ransomware issues without needing multiple tools. One of the standout features of AVG Ransomware Decryption Tools is their accessibility. Unlike many other cybersecurity solutions, AVG’s decryption tools are completely free, making them accessible to all users regardless of their financial situation. This free access is especially crucial for individuals and organizations that may not have the resources to pay for expensive decryption services. The user-friendly interface of AVG’s tools also sets them apart. The decryption process is straightforward, guiding users through each step and making it easy to use even for individuals with limited technical expertise. This simplicity ensures that anyone can effectively utilize these tools to recover their encrypted files. As part of the well-respected AVG antivirus suite, these decryption tools benefit from the company’s long-standing reputation for delivering reliable and effective cybersecurity solutions. By combining effectiveness, accessibility, and user-friendliness, AVG Ransomware Decryption Tools provide an invaluable resource for anyone affected by ransomware attacks.
Download: Access for free
Official Site: https://www.avg.com/en-in/ransomware-decryption-tools
OS: Windows
2. No More Ransom
Best For: Individuals,SMBs, and IT departments that have fallen victim to ransomware and need a free, reputable way to recover encrypted data.
Price: Free
The No More Ransom project is an initiative by the National High Tech Crime Unit of the Netherlands’ police, Europol’s European Cybercrime Centre, Kaspersky, and McAfee to help ransomware victims retrieve their encrypted data without having to pay the criminals. The project also aims to educate users about how ransomware works and what countermeasures can effectively prevent infection.
No More Ransom’s key features
This is a nonprofit initiative, and its most important features are:
- Free Decryption Tools: Access over 120 decryption tools for hundreds of ransomware variants including Petya, TeslaCrypt, CoinVault, and CryptXXX.
- Extensive Database: You can upload encrypted files or ransom notes to identify the ransomware strain and find the right decryption tool.
- Educational Resources: The platform includes guides on how ransomware works and how to avoid future infections—great if you’re trying to build a
ransomware-resilient culture in your business. - Collaborative Network: Backed by Europol, Kaspersky, McAfee, and global law enforcement agencies, so you can trust its credibility and depth.
- Open Participation: Public and private organizations can contribute, keeping the tools and resources fresh and effective.
Unique Value Proposition
Unlike many standalone security tools, No More Ransom isn’t a commercial product—it’s a global initiative grounded in collaboration between law enforcement and cybersecurity experts. You’re not only gaining access to free decryption tools; you’re leveraging the collective intelligence and legal access of international cybercrime units. That’s something no typical software vendor can offer.
Why do we recommend it?
The No More Ransom project is highly recommended for its extensive database of decryption tools and its unique ability to identify ransomware strains based on user-uploaded samples. This collaborative effort provides a valuable, free resource for victims of ransomware worldwide.
Having worked with companies that didn’t have the luxury of high-end cybersecurity stacks, I’ve seen how No More Ransom became their saving grace. It doesn’t just give you tools, it walks you through the right steps, from removing the malware to unlocking your files safely. We recommend it because it’s robust, constantly updated, and doesn’t exploit your panic during an attack with costly upsells or false promises. It also actively avoids supporting the ransomware economy, which is crucial from both ethical and practical standpoints.
Who is it recommended for?
This initiative is ideal for individuals and organizations that are uncertain about the type of ransomware they are dealing with. It’s also a great educational resource for anyone looking to understand more about ransomware and how to prevent it.
Whether you’re a freelancer hit by a phishing link or a mid-size company paralyzed by ransomware without a budget for cyber consultants, No More Ransom is a smart place to start. It’s also great for IT admins who want to bolster their response options without relying solely on commercial antivirus software.
Pros:
- Free and Transparent: Completely free to use, with no hidden costs or upselling.
- Trusted Backing: Supported by major law enforcement and security partners.
- Always Updated: Decryption tools are regularly refreshed and expanded.
- Educational Value: Includes user guides and prevention best practices.
Cons:
- No Universal Coverage: Only works with known ransomware strains.
- Requires Some Know-How: May need basic technical skills to use effectively.
- Not Preventive: Doesn’t offer real-time protection—only for recovery.
No More Ransom has the most extensive collection of decryptor tools and a repository of keys that can decrypt over 100 ransomware strains out there. If you don’t know which ransomware attacked your system, simply upload two sample files from your PC. Once you upload them, the website will identify the ransomware and provide you with the necessary decryption tool, if available.
In short, No More Ransom is one of the most reliable and community-driven responses to ransomware on the web. It empowers you to regain control of your data without feeding the cybercrime ecosystem, and that makes it more than just a tool.
3. Emsisoft Ransomware Decryption Tools
Best For: SMBs and IT Teams, Individual Users, IT Service Providers
Price: Free
Screenshot showing Emsisoft ransomware decryptor home pageEmsisoft is one of the top-rated ransomware decryption software that one can have on a Windows PC. In addition, Emsisoft has a long list of free specialized tools for decrypting various strains of ransomware such as PClock, CryptoDefense, CrypBoss, DMA Locker, Xorist, Apocalypse, WannaCryFake, Cyborg, and many others.
Emsisoft ransomware decryption software is among the top-rated in the industry. However, Emsisoft like many others, do not provide any guarantees about the integrity of the decrypted files. Technical support for these tools is limited to users with an active paid Emsisoft subscription.
Emsisoft Ransomware Decryption Tools’ key features
This is a Windows-based solution, and its most important features are:
- Free Decryption Tools: Covers a wide list of ransomware variants (over 100 supported families as of the latest update).
- Comprehensive Instructions: Each tool comes with a detailed how-to guide, making it easier to use even if you’re not deeply technical.
- Offline Usage: No internet connection is needed once the tool is downloaded, which reduces further risk of infection.
- Lightweight and Fast: Tools are small in size and quick to execute, perfect for time-sensitive situations.

Unique Value Proposition
What sets Emsisoft apart is its proactive focus on decrypting ransomware strains that often evade mainstream tools. Their decryption tools are frequently updated in collaboration with Europol and other law enforcement agencies to give you a better shot at data recovery compared to many one-off solutions.
Why do we recommend it?
Emsisoft’s ransomware decryption software is recommended for its comprehensive coverage and effectiveness against a wide array of ransomware strains. Its position as a top-rated tool in the industry makes it a reliable choice for users seeking to decrypt files affected by various ransomware attacks.
Based on real-world use cases, Emsisoft’s STOP/DJVU decryptor has proven effective in helping small businesses avoid paying hefty ransoms. For example, if your company is hit by the .gero ransomware variant, the tool can be used to recover a significant portion of your essential files, even though some remained encrypted due to the use of online keys. While not a complete recovery, the ability to restore critical documents without spending a dime offered a practical and valuable solution during a crisis.
Who is it recommended for?
This software is ideal for Windows PC users who are dealing with ransomware infections, particularly those affected by strains such as PClock, CryptoDefense, CrypBoss, and others. It’s well-suited for both individual users and organizations seeking to recover their encrypted data.
Emsisoft’s ransomware decryption tools are ideal for small to medium-sized businesses, freelancers, consultants, IT admins needing quick incident response, and budget-conscious organizations like schools or nonprofits.
Pros:
- Free to Use: Completely free, even for commercial cases.
- Wide Coverage: Supports many ransomware families.
- Updated Frequently: New decryptors are added regularly.
- Trusted Source: Built by a leading cybersecurity vendor.
Cons:
- Strong Encryption Limitations: Can’t decrypt ransomware using secure offline keys (e.g., some STOP/DJVU).
- Requires Prior Malware Removal: Must clean system before running decryptors.
- Command-Line Tools: Some decryptors use CLI, which can challenge non-technical users.
Emsisoft’s ransomware decryption tools are a valuable asset in any cyber defense toolkit. While they don’t guarantee a 100% recovery (of course no free tool can), you’re giving yourself a strong, ethical, and cost-free alternative to paying criminals. For IT teams, individuals, and budget-conscious companies, it’s a go-to solution worth bookmarking.
Emsisoft ransomware decryption software is among the top-rated in the industry. However, Emsisoft tools do not provide any guarantees about the integrity of the decrypted files. Therefore, the decryptor will not remove any encrypted files after they have been decrypted unless this option is specifically disabled, mainly if you have limited storage space.
4. Trend Micro Ransomware Tool
Best For: SMBs, educational institutions, nonprofits, and even enterprise users looking for an effective recovery tool
Price: Free
Screenshot showing Trend Micro Ransomware decryptor home pageTrend Micro ransomware file decryptor is designed to decrypt files that have been encrypted by 27 families of known ransomware, including popular strains such as WannaCry, Petya, TeleCrypt, Jigsaw, CryptXXX, and TeslaCrypt(Version 1, 2 3, 4). Just like others, Trend Micro ransomware file decryptor is not a universal one-size-fits-all software. Instead, it requires you to identify the ransomware family you are infected with or the ransomware file extension name before selecting the ideal tool to decrypt files.
Trend Micro Ransomware File Decryptor’s key features
This is a Windows-based toolset, and its most important features are:
- A Single Utility: Access the controller rather than individual fixes
- Multiple Capabilities: Decrypts multiple ransomware strains
- Easy to Use: Consumer friendly
Suppose you don’t know the ransomware name or file extension. In that case, the tool may automatically analyze the file and identify the ransomware based on the file signature or ask you to provide additional information about the files; otherwise, select the “I don’t know the ransomware name” option. You will also be prompted to select a target file or a folder on your computer to perform the decryption operation. However, the tool is efficient enough to identify various ransomware file types and decrypt them. Of course, there is no 100% guarantee about its effectiveness all the time or the integrity of the translated files. Trend Micro provides details about the limitations of the tool for your information.
Unique Value Proposition
What sets this tool apart is its comprehensive documentation, regular updates, and support for a wide range of ransomware strains that often go ignored by other decryptors. Its free availability to both consumers and businesses adds significant value, especially for organizations without dedicated cybersecurity budgets. Unlike some one-size-fits-all decryptors, Trend Micro tailors its tool to specific variants, improving the success rate of file recovery.
Why do we recommend it?
Trend Micro’s ransomware file decryptor is recommended for its ability to tackle a wide range of ransomware families. The tool’s functionality to automatically analyze and identify ransomware types makes it a valuable asset for users unsure of the specific ransomware affecting their files.
From my own evaluation and broader industry research, Trend Micro’s tool stands out for its reliability and transparency. You’re guided through the entire decryption process, which minimizes errors that might otherwise damage files further. The added support for ransomware like WannaCry (though limited to certain OS versions), makes it uniquely useful in legacy environments, which are common in sectors like manufacturing or healthcare. If you already use Trend Micro’s security suite, this decryptor integrates smoothly into your incident response strategy.
Who is it recommended for?
This tool is particularly beneficial for individuals and organizations facing ransomware attacks from known strains like WannaCry or Petya. It’s also suitable for those who may not have the technical expertise to identify the ransomware type, as the tool provides assistance in this area.
The Trend Micro Ransomware File Decryptor is ideal for small to mid-sized businesses, educational institutions, nonprofits, and even enterprise users looking for an effective recovery tool that doesn’t demand upfront costs. If you’re a freelancer, IT administrator, or budget-conscious security team dealing with legacy systems or previously known ransomware families like TeslaCrypt or CryptXXX, this tool offers a practical solution. It’s especially helpful in environments where proactive defenses might have fallen short, and fast file recovery is critical to continuity.
Pros:
- Broad Variant Support: Includes older and less commonly supported ransomware families.
- User-Friendly Interface: Clear, guided UI for all technical skill levels.
- No Cost or Signup: Free to use without registration or subscription.
- Ecosystem Integration: Works within Trend Micro’s broader ransomware response framework.
- Legacy System Compatibility: Supports older systems like Windows XP.
Cons:
- Limited Modern Coverage: Not effective against newer or fast-evolving ransomware strains.
- Reactive Only: Best used alongside proactive security solutions.
- Variable Success Rate: Depends on specific ransomware variant and key availability.
- No Live Support: Technical help only available with a Trend Micro subscription.
If you’re managing IT for a school, NGO, or small business, Trend Micro’s Ransomware File Decryptor offers a reliable last line of defense without adding financial strain. While it’s not a silver bullet against all modern threats, it’s a solid recovery tool for known ransomware types and fits well within a layered security strategy. Be sure to combine it with up-to-date antivirus protection and a disciplined backup routine to maximize resilience.
Suppose you don’t know the ransomware name or file extension. In that case, the tool may automatically analyze the file and identify the ransomware based on the file signature or ask you to provide additional information about the files; otherwise, select the “I don’t know the ransomware name” option. You will also be prompted to select a target file or a folder on your computer to perform the decryption operation. However, the tool is efficient enough to identify various ransomware file types and decrypt them. Of course, there is no 100% guarantee about its effectiveness all the time or the integrity of the translated files. Trend Micro provides details about the limitations of the tool for your information.
5. Avast Anti-Ransomware Tools
Best For: Individuals, small businesses, and even large enterprises that need a fast, trustworthy, and free method to decrypt files without paying a ransom.
Price: Free
Screenshot showing Avast ransomware descriptor home pageIf you or your business has fallen victim to a ransomware attack and your files have been encrypted by any of the dozens of known ransomware strains, AVAST’s Ransomware Decryption Tools can come to your rescue.
Avast provides ransomware decryption tools for some of the most popular types of ransomware out there. Avast ransomware decryption tools are designed to decrypt files that 27 families of known ransomware have encrypted. Before using this tool, Avast recommends that you ensure all traces of the ransomware infection have been removed from your computer.
Avast Ransomware Decryption Tools’ key features
This is a Windows-based utility, and its most important features are:
- Completely Free: No hidden fees, no subscription – download and use instantly.
- Wide Ransomware Coverage: Supports decryptions for over 30+ ransomware strains like AES_NI, Apocalypse, Babuk, GandCrab, CrySiS, and more.
- Regular Updates: AVAST continually updates its tools as new ransomware strains are analyzed and keys become available.
- Easy-to-Use Interface: You don’t need deep technical skills — most of the tools are straightforward: select encrypted files, choose destination, decrypt.
- High Success Rate (When Applicable): If the ransomware variant used an identifiable or offline key, your chances of successful decryption are very high.
- Documentation Included: For each ransomware, AVAST provides detailed infection signs, ransom notes, file extension examples, and step-by-step usage instructions.
Unique Value Proposition
What truly sets AVAST apart is that you don’t have to pay or trust a random online “recovery service.” You’re dealing with a globally recognized cybersecurity company with a long history of threat research. Having access to free decryption tools backed by AVAST’s threat intelligence is like having a professional incident response team in your pocket — without ever opening your wallet.
In contrast, tools from lesser-known sources often come with strings attached: shady downloads, hidden malware, or partial decryption. With AVAST, you get transparent, proven tools. Plus, if decryption isn’t possible yet, they don’t mess with your files or trick you into false hope.
Why do we recommend it?
Avast’s ransomware decryption tools are recommended for their ease of use and the ability to tackle a wide range of ransomware types. Their user-friendly interface and the capability to scan different locations make them accessible and efficient for a broad spectrum of users.
From my experience handling ransomware incidents in both SMB environments and enterprise settings, time is the enemy after an attack. Panic can lead people to rash decisions like paying a ransom or downloading unsafe “miracle” decryptors.
AVAST’s tools cut through that panic with:
- Trustworthiness: You know you’re downloading a clean, professionally vetted tool.
- Quick Setup: You can get started in minutes — a critical edge when ransomware freezes operations.
- Educational Materials: Their infection guides often help pinpoint how the attack happened, supporting your overall incident response plan.
The Avast anti-ransomware tools are easy to install and use and don’t require any special configuration. Simply download the zip file, unzip it, and launch the application (as an administrator) via their associated executable files. It can be set to scan any location on the disk where you suspect the encrypted files to be, such as local or network drives as well as custom folders. In addition, the Avast decryptor relies on a known file format to verify that the file was successfully decrypted during the decryption process.

Who is it recommended for?
These tools are ideal for users, both individuals and businesses, who need to decrypt files affected by common ransomware families. They are especially useful for those who prefer a straightforward, no-fuss approach to ransomware decryption.
This solution targets SMBs to enterprises needing an initial defense before resorting to costly recovery services, IT departments seeking free, fast post-infection options, security-conscious individuals recovering compromised personal devices, and MSPs aiming to restore client systems without increasing costs.
Pros:
- Free to Use: No fees or hidden traps.
- Trusted Provider: Backed by a global cybersecurity leader.
- Proven Effectiveness: High success rate with known ransomware strains.
- Beginner-Friendly: Very easy for non-expert users to try.
- Educational Resources: Offers excellent guidance on ransomware infection and response.
Cons:
- Limited Coverage: Only works for supported ransomware types, not all new variants.
- Technical Requirements: Some tools require steps like Safe Mode or offline execution.
- Key-Dependent: May not work if the ransomware uses unique encryption keys.
- Performance on Scale: Can be slow with large sets of encrypted files.
- Match Accuracy Required: Assumes your infection matches a supported ransomware strain.
You could easily get confused trying random tools from unknown providers, but AVAST’s suite is consolidated, professional-grade, and user-friendly. When you’re dealing with critical encrypted files and limited time, trusted simplicity beats risky “advanced” solutions every time. If you’re reading this before a ransomware attack hits, install AVAST Free Antivirus now. Prevention is still easier than cure, and AVAST’s detection capabilities often catch ransomware attempts before they can start encrypting.
However, just like others, Avast does not guarantee that the decryption will be successful or effective. Avast recommends backing up encrypted files in case something goes wrong during the decryption process. In addition, Avast provides a free anti-ransomware tool that helps to prevent ransomware attacks and other types of threats.
5. Quick Heal Ransomware Decryption Tool
Best For: MSPs, IT teams, SMBs, and Individual users
Price: Free

Quick Heal ransomware decryption tool can decrypt files encrypted by 17 variants of ransomware. The application automatically scans your infected device for supported encrypted files and then attempts to decrypt them, replacing the encrypted files with the decrypted ones.
Follow the steps below to decrypt a file using this tool:
- Click Download Tool, save and extract the zip file on the system having the encrypted files.
- Right-click on the extracted file and select “Run as administrator” to view the Decryption Window.
- Press Y to start the scan. The tool will automatically scan the entire system for supported encrypted files. When an encrypted file is found, the tool will decrypt the file in its respective folder while keeping a copy of the encrypted file simultaneously.
- After the scan is complete, the decryption tool will show the final status displaying the number of encrypted files found and how many were successfully decrypted. The detailed information about the decryption status of each file can be obtained from the ‘Decryption.log’ generated in the same folder of the tool.
- After that, you can open the decrypted files and verify if they are accessible/readable again.
Quick Heal Ransomware Decryption Tool’s key features
This is a Windows-based utility, and its most important features are:
- Free, Hassle-Free Download: You don’t need a Quick Heal subscription or account.
- Supports Numerous Known Ransomware Strains: Including STOP Djvu, Troldesh (.wallet/.onion), GandCrab, and Globe variants.
- Offline Capable: Useful in forensic environments or when keeping machines isolated from networks is a must.
- Automatic Scanning and Decryption: Detects and decrypts supported files in one pass, no manual mapping required.
- Logs and Backup: Keeps copies of encrypted files and produces a detailed decryption log so you can audit what was recovered.
Unique Value Proposition
While many antivirus vendors offer decryption tools, Quick Heal stands out because:
- It consolidates support for a wider range of ransomware families (especially STOP Djvu, which continues to be one of the most prolific strains).
- It’s genuinely free with no telemetry or post-install activation nagging—a rare thing in cybersecurity tools today.
- It’s low-footprint and portable, which makes it suitable for field techs or air-gapped environments.
Practical Tips (from Experience)
- Always run the tool as an Administrator, and ideally from a USB stick on the infected machine to avoid further file corruption.
- Use it before attempting third-party recovery services—even partial recovery can reduce service costs.
- If you’re dealing with STOP Djvu ransomware, use the decryption log to compare recovered vs. unrecoverable files. This helps justify next steps
to decision-makers or clients. - Keep encrypted file copies (Quick Heal does this by default) just in case more advanced decryptors or master keys become available in the future.
Why do we recommend it?
Quick Heal’s ransomware decryption tool is recommended for its ability to automatically identify and decrypt a wide range of ransomware-infected files. Its user-friendly process and additional security features make it a reliable choice for users seeking to recover their data.
From hands-on use in actual ransomware recovery scenarios, Quick Heal’s tool is reliable and transparent. Unlike some decryption tools that only claim support for certain ransomware types, Quick Heal clearly lists supported extensions and includes visual confirmation of success rates post-scan. When used on a STOP Djvu-infected system, it effectively recovered a significant portion of documents without system instability—a huge relief for smaller businesses that can’t afford prolonged downtime.
This tool is also great for triaging client machines before escalating to more invasive or costly solutions. For businesses with decentralized IT such as branch offices or hybrid workforces, having a tool like this available can reduce time-to-recovery dramatically.
Who is it recommended for?
This tool is suitable for individuals and organizations that need an effective solution against ransomware, especially those who may not have extensive technical expertise. It’s particularly beneficial for those who need to decrypt files affected by one of the 17 ransomware variants it supports.
It is recommended for IT teams, SMBs, and MSPs, as well as for individual users, freelancers, and security-conscious professionals looking for an easy-to-use, budget-friendly solution they can run independently when ransomware attacks strike.
Pros:
- Completely Free: No account or payment required.
- Broad Variant Support: Handles many known ransomware families.
- Preserves Originals: Keeps encrypted files alongside decrypted versions.
- No Scripting Needed: Simple command-line use without custom scripts.
- Offline Capable: Runs without requiring internet access.
Cons:
- Limited to Known Strains: Doesn’t support unknown or emerging variants.
- Basic Interface: May feel too technical for some users.
- GandCrab Specifics: Requires ransom note to decrypt GandCrab infections.
- No Real-Time Protection: Functions as a recovery tool, not a preventive one.
While the Quick Heal Ransomware Decryption Tool won’t solve every case (no decryptor can), its ability to recover even partial datasets from notorious variants like STOP Djvu makes it a standout choice for IT responders, MSPs, and individual users alike.
Quick Heal also has an in-built active protection mechanism that mitigates ransomware attacks by preventing malware from automatically executing when introduced via removable storage devices.
Our methodology for choosing Ransomware File Decryptors
Here’s the methodology I used to evaluate the tools reviewed above.
1. Effectiveness and Range of Coverage
I prioritized tools that have a proven track record of successfully decrypting a wide variety of ransomware strains. A tool that works on 10+ major strains is much more useful than one targeting only a rare variant.
2. Ease of Use
I tested and looked for tools that even a moderately technical person (not just IT pros) could realistically use. Clear instructions, simple interfaces, and minimal “extra” configuration are huge pluses. During a ransomware crisis, stress is high, and so you need a tool that’s plug-and-play, not a puzzle.
3. Source Credibility
I only considered decryptors developed by trusted cybersecurity vendors such as Avast, Emsisoft, Quick Heal, or reputable security collectives.
4. Speed and Performance
Tools that scan and decrypt files quickly without hogging system resources or causing crashes ranked higher. In a business setting, downtime is expensive, and sluggish tools make recovery slower and riskier.
5. Safety and Data Integrity
Top picks create a backup of the encrypted files before attempting decryption, so you can roll back if something goes wrong. Some decryption attempts can damage files further if they’re not handled properly.
6. Update Frequency
I gave extra credit to tools that are actively updated to keep pace with ransomware evolution, versus “abandoned” or static tools that don’t work on new variants. Ransomware moves fast. A tool from even six months ago could already be obsolete.
7. Community and Peer Feedback
I factored in user reviews, case studies, and technical forums (like BleepingComputer, Malwarebytes Forums, etc.) to see real-world feedback on success rates. Marketing claims aren’t enough. A real-world success story gives much better validation.