Runtime Application Self-Protection (RASP) keeps your applications safe by proactively blocking malicious requests
But how do you know which RASP vendor is right for your environment? In this article, we’ll review the nine best RASP vendors on the market that can help you protect your most critical applications.
Here is our list of the best RASP vendors:
- Imperva RASP EDITOR’S CHOICE This protection service is cloud-hosted but integrates into your Web applications through a plug-in. Imperva delivers an installer that forms part of your CI/CD release pipeline, inserting the plug-in automatically at the point that the Web application is released into production.
- JSDefender Offers application traffic analysis and JavaScript obfuscation.
- Datadog Application Security Management Until recently, this was an independent system, called Sqreen and it provides threat detection and reporting for live Web applications.
- Signal Sciences Focuses heavily on integrating with the DevOps toolchain and reducing its impact on the application.
- New Relic Vulnerability Management This module is integrated into the New Relic platform and also uses the platform’s Open Telemetry data gathering engine and its Interactive Application Security Testing (IAST) unit.
- OpenRASP A highly flexible open-source RASP solution.
- Veracode Runtime Protection Offers a RASP solution paired with vulnerability remediation tools, ideal for larger organizations.
What exactly does a RASP vendor or tool do?
Runtime Application Self-Protection (RASP) is an advanced security technology designed to protect applications in real-time by detecting and blocking threats as they occur. Unlike traditional perimeter security measures, such as firewalls and intrusion prevention systems, RASP operates within the application itself, enabling it to identify and mitigate vulnerabilities directly in the runtime environment.
RASP integrates seamlessly with an application’s code and continuously monitors its behavior and context during execution. This proximity allows it to detect abnormal patterns, malicious inputs, or unexpected interactions that may signal an attack. Common threats addressed by RASP include SQL injection, cross-site scripting (XSS), remote code execution, and privilege escalation attempts.
One of the standout features of RASP is its ability to differentiate between legitimate application activities and potential threats. For example, it can distinguish between a user input that matches a known attack pattern and normal user behavior. This precision minimizes false positives, which are common in other security solutions, and ensures uninterrupted user experience.
Another advantage of RASP is its adaptability. Because it operates within the application, it provides protection regardless of the deployment environment, whether on-premises, in the cloud, or within containerized systems. This makes it a valuable tool for securing modern, distributed applications.
RASP enhances application visibility by providing detailed logs and analytics about detected threats. This data helps developers and security teams better understand vulnerabilities and improve application security during the development lifecycle.
In summary, RASP represents a proactive approach to application security, combining real-time threat detection, precise intervention, and comprehensive insights. As cyber threats grow increasingly sophisticated, RASP is becoming an essential component of application security strategies for organizations aiming to safeguard sensitive data and maintain operational integrity.
How is RASP different from a Web Access Firewall (WAF)?
RASP vendors differ from WAFs primarily because RASP vendors can understand how the app will process the data. In short, the RASP tools have a closer relationship and understanding to a specific application and provide better protection for businesses that use the continuous deployment model. RASP vendors block or filter traffic based on the information collected in the traffic and how your application will handle that traffic.
In a WAF environment, all HTTP requests are analyzed for malicious behavior, abnormal behavior, and odd patterns. Depending on the configuration, the WAF will block or filter this traffic from reaching the application environment. However, the WAF has little visibility into the application and lacks an understanding of how the application will process traffic. This oversight can cause WAFs to produce a more significant number of false positives.
RASP vendors provide businesses with more controls and better accuracy on a per-application basis. In addition, RASP tools can be adapted to any programming language or app environment and continuously learn to stop attacks while preventing false positives.
What should I look for in a RASP vendor?
Ease Of Use
RASP is designed to be heavily automated and run with little to no human interaction. However, that isn’t to say some tools aren’t more straightforward to install than others. Instead, look for a RASP took that installs easily and offers out-of-the-box security templates to get started.
A cluttered dashboard can make NOC monitoring challenges and steepen the learning curve for new users. Instead, consider spending some time trialing your RASP vendor solution and getting a feel for how easy it is to create new workflows, implement rule sets, and navigate through the UI.
Reporting
Depending on your type of business, reporting might be a critical factor in choosing a RASP vendor. Good RASP tools will have customizable reporting tools that aren’t difficult to use. In addition, organizations that adhere to standards such as PCI DSS or HIPAA will want to know they can easily prove compliance with their RASP tool.
Protection
While most RASP tools offer the same baseline layer of protection, look for tools that go beyond the Top 20 OWASP vulnerabilities. Many RASP vendors try to differentiate themselves from competitors by offering patented detection techniques that analyze factors like grammar, geolocation, and machine learning to provide enhanced protection. Good RASP products detect and prevent all attacks, from maliciously crafted packets and DDoS attacks to script kiddie tools.
Consider if your RASP product can scale with you. For example, will your origination only have one or two apps, or do you plan to develop more soon. In addition, enterprise RASP tools can often monitor multiple applications and generate consolidated insights in a single dashboard. Lastly, ensure your RASP vendor supports various types of environments. With multi-cloud and hybrid cloud environments becoming increasingly more popular, be sure that your RASP vendor fits in your current environment and can support your plans to grow in the future.
With the basics out of the way, let’s explore the top 9 best RASP vendors.
The best RASP Vendors
Our methodology for selecting RASP systems
We reviewed the market for Runtime Application Self-Protection solutions and analyzed the options based on the following criteria:
- A cloud-based system
- Application-centric firewalling
- Instant blocks on access to prevent harmful inputs
- Scanning for OWASP Top 10 vulnerabilities
- Possible integration with other edge services
- A free trial or a live demonstration to enable an assessment of this new technology before buying
- Value for money from an automated RASP service that provides effective security protection for a reasonable price
1. Imperva RASP
Imperva is a leading cybersecurity brand with a suite of different protection solutions. Their RASP product is designed to quickly stop online threats and automatically provide a customizable front end for sysadmin and NOC teams.
Key Features:
- Self-Installing Plug-in: Operates as a continuous tester for development pipelines
- Options for Monitoring or Protection: Identifies online threats
- Can be Packaged with other Services: Hosted on an edge server
- Machine Learning: Reduces over-zealous alerting
- Attack Blocking: Operates live
Why do we recommend it?
The Imperva RASP gets embedded with your Web applications at the point that the code passes its security testing in a CI/CD pipeline. So, you make sure that the application is secure and then wrap the RASP in with it. The package doesn’t need to be coded into your application.
Imperva RASP starts by understanding how your application works, interprets traffic, and processes commands to protect it from abuse better. Then, Imperva can detect various attacks ranging from clickjacking and packet tampering to injection attacks and zero-day exploits.
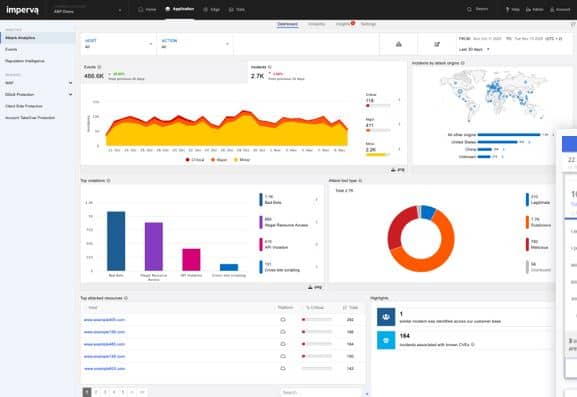
Visually Imperva’s dashboard is sleek and easy to navigate. In addition, the brand uses color very well to help accent key insights and bring critical information to the forefront. Out of the box, Imperva onboards very quickly compared to other RASP products and begins protecting your application with minimal configuration needed on the user’s end.
Who is it recommended for?
Imperva RASP provides an easy way to integrate ongoing protection into your Web applications because it forms a package with your code that will always accompany it, thanks to an installer that makes sure that your code won’t be implemented without its security companion.
Pros:
- Compliance Management: In-depth audits and compliance tests
- Breach Detection Features: Live vulnerability scanning
- DevOps Tool: Use during development and when systems are live
- Deployment Options: Available both as a cloud product or on-premise solution
- Creates a Wrapper: The RASP is bound around the application
Cons:
- Provides Compliance Monitoring: Not all businesses need that compliance features
You can test out Imperva RASP through a free trial.
EDITOR'S CHOICE
Imperva RASP is a cloud-based service that integrates into your own Web applications at the point that they are released into production. This tool pairs well with the Imperva WAF. While the WAF blocks traffic-based attacks such as DDoS, the RASP scans user input before it is posted and prevents code-based attacks, such as cross-site scripting or SQL injection. The tool also identifies and blocks behavioral misuse of a website, such as clickjacking, path traversal, and authentication hijacking. The service also scans the code and add-ons of the Web application to spot insecure cookies, weak encryption or authentication, and hard-coded credential disclosure.
OS: Cloud based
2. JSDefender
JSDefender by Preemptive is designed to obfuscate application traffic and provide end-to-end application protection. Numerous tamper detection methods are used to protect the application, while traffic obfuscation hides your traffic from intruders. JSDefender supports all major frameworks, including JavaScript, Angular, Node, React, React Native, and Webpack.
Key Features:
- Containerizes Java Code: Creates a wrapper
- Obscures Scripts: Prevents code from being legible
- Creates an Interface for the Protected Code: Provides a runtime interpreter
- Runs on the Cloud: Leaves your Web applications on your servers
Why do we recommend it?
JSDefender’s main tactic is to obscure JavaScript, which could otherwise be read by anyone because it runs in plain text. The protected code is packaged in a container and the system includes tampering detection and reporting. The system also speeds up code execution.
JSDefender is an excellent choice for an environment that heavily relies on JavaScript to power its applications and products. Unfortunately, JavaScript applications are delivered in source form, meaning that your code is visible to anyone with access to the browser or app front end. Attackers can exploit this inherent insecurity in JavaScript to sift through the running code and find vulnerabilities to exploit.
Who is it recommended for?
This is a clever solution to the perennial problem of the code for a Web-based system being visible. That visibility is great for security tools that perform code profiling but it also assists hackers. Operations staff will need to work out which monitoring system can receive JSDefender’s reporting messages.
Pros:
- Blocks Reconnaissance: Hackers can’t see script
- Obfuscation: Provides a number of options
- Supports a Wide Range of Frameworks: But only cloaks Java
- Interface is Easy to Use: Better than some API options
Cons:
- Java Only: Not ideal for businesses that don’t heavily rely on JS
JavaScript obfuscation makes it considerably more difficult for attackers to analyze, exploit, or reverse engineer your code. There are also some added benefits to scrambling code, such as minification, which shrinks the size of your code, allowing it to run more efficiently. This unique feature combined with essential RASP protection makes JSDefender an easy choice for anyone that heavily relies on JavaScript applications.
3. Datadog Application Security Management
Datadog Application Security Management provides vulnerability scanning for preventative measures and also a live threat tracker that looks for those well-known attack strategies that are listed by OWASP. The Web application vulnerability scanner is called the Vulnerability Management unit and the scanner for live systems is called Threat Management.
Key Features:
- OWASP Attack Detection: Live scanning
- Blocks Threats: Automated responses
- Scans Adjacent Modules: Examines coupling and cohesion
Why do we recommend it?
Datadog Application Security Management Threat Management. Rather than being built into the Web application, this system operates as a focused attack scanner. It looks for known hacker actions and scans connected modules. It will block suspicious actions and blacklist the IP address of the source of detected hacker activity.
The service was originally called Sqreen and was bought by Datadog. The tool has now been integrated into the Datadog platform. The Vulnerability Management and Threat Management units are charged for separately and you don’t have to subscribe to both. Datadog offers an AWS Fargate monitoring plug-in, which can be added to the Threat Management package for serverless monitoring. The package includes storage space for recorded metrics, which are saved for 90 days.
Who is it recommended for?
The Datadog platform offers a lot of monitoring modules that cover different technologies and the most likely buyer of the Threat Management unit will be customers who are already using or interested in subscribing to many of the other Datadog products, For example, the Threat Management service works very well alongside the Datadog APM.
Pros:
- Implements RASP Through a WAF Mechanism: Operates as a proxy server
- Will Scan all Modules that are Linked to the Threatened Unit: Looks at threat spread
- Provides cloaking for plain text code: Also generates reporting messages for telemetry
Cons:
- Only Available as a SaaS Package: Not available for self-hosting
Your Web applications are probably hosted on serverless cloud platforms and the Threat Management system can collect data from invocations wherever the modules are resident. You can sample the entire Datadog platform, including the Application Security Management Threat Management service with a 14-day free trial.
4. Signal Science
Signal Sciences offers numerous cybersecurity solutions, including WAFs, DDoS protection, and now RASP. The platform focuses on being a simple solution to the complex task of protecting your application and DevOps team from compromise.
Key Features:
- Cloud-Hosted Engine: Operates through an agent in the web server
- Code Inserted into Web Application: Not a wrapper
- A DevOps Tool: Operates through development and out into operations
Why do we recommend it?
The Signal Science RASP has a low impact on the execution of Web applications. Slow response times can deter the public from using a Web application. There is constant pressure on the developers and managers of mobile apps and websites to make them fast, so the low overhead of this package is very appealing.
Signal Sciences uses a streamlined installation process paired with numerous out-of-the-box features that make it easy to hit the ground running and see benefits immediately. This focus on simplicity and powerful protection helps it stand out from competitors and secure its place on our best RASP vendors list.
The platform has carefully designed its product not to impact application performance, claiming that similar tools affect app performance by 100 to 200%. This attention to detail and careful integration into existing DevOps toolchains make it a solid choice for any sizeable DevOp environment that cannot afford downtime.
Who is it recommended for?
This service covers all bases. It protects containers, microservices, and scans through APIs as well. The system can identify authentication cheats, DDoS floods, and database attacks. The module works alongside a module within a wrapper rather than being inserted into the code and it sends reporting messages outside the container.
Pros:
- Easy to Use: Does a good job of simplifying complex RASP environments
- Lightweight: Carefully avoids impacting app performance
- Can Detect a Range of Threats: API abuse, account takeover, and external threats
Cons:
- Requires Training to Implement: Despite its ease of use
Uniquely, Signal Sciences can detect some threats that other RASP tools miss. For example, attacks such as account takeover, API abuse, bad bots are all thwarted under their platform. In addition, the tool is highly flexible and supports legacy, app native, and serverless environments.
5. New Relic Vulnerability Management
New Relic is a complete application observability platform. You can’t subscribe to just one of the modules on the system, you get the lot in one bundle. The many units in the platform include the Vulnerability Management service, which is implemented by an Interactive Application Security Tester (IAST). That tester was originally created by a separate company, called K2 Cyber Security, which New Relic bought in 2022.
Key Features:
- Part of an APM: Useful integrations of service
- Gathers Application Signals: Through telemetry
- Identifies Live Vulnerabilities: Reporting and Response
Why do we recommend it?
The multi-discipline nature of the New Relic platform tends to blur the divisions between modules. So, the system performs its core task of distributed tracing and then also allows its security scanning features to operate on that collected activity data. That maximizes the value of a single source of data.
The RASP function is formed by stringing together two units of the New Relic suite. The APM gathers all data on Web applications as they run, through the use of OpenTelemetry. These log messages are then processed by the Vulnerability Manager to look for signs of attack.
As all running microservices are being monitored simultaneously, the system can spot attacks that use one service as a tool to attack another. The IAST package looks for signs that these movements are underway and then the APM shuts down the invocation to block the attack.
Who is it recommended for?
The full New Relic platform is able to monitor all types of IT assets, not just Web applications. However, it is the Web application observability function that draws customers to New Relic. If you run Web systems, you will need to watch over their performance and security and you get both with this package.
Pros:
- Adds Value to a Distributed Tracing Observability Service: Provides detailed messages
- Spots Attacks: Uses IAST techniques
- Records Suspicious Activity: Also kills affected processes
Cons:
- Is More of a WAF: It operates externally to the application
This security function is just one feature of the New Relic platform, which has 16 units for full-stack observability that includes network monitoring. You will need to be prepared to take on the entire New Relic system in order to get the RASP. You can access the Free tier of New Relic which will process 100 GB of data per month.
6. OpenRASP
OpenRASP, developed by Baidu, is, you guessed it, completely open-source. The protection engine integrates with the application server to track different events, requests, queries, and network traffic.
Key Features:
- Web Server Plug-in: Host it yourself
- Logs Attacks: Doesn’t block them
- Free to Use: An open-source service
Why do we recommend it?
OpenRASP is an open-source package that implements an observability strategy, similar to that of New Relix. The plug-in receives activity messages from Web applications and sorts through them for signs of attack. This is a natural stance to take because it exploits existing telemetry mechanisms.
For an open-source product, OpenRASP leverages numerous out-of-the-box features to protect applications. For example, by examining different inputs and outputs, the product understands the context behind other behavior and stops the malicious activity. In addition, intelligent alerts only notify users when an attack is successful by default, which helps reduce false positives and helps improve the DevOps overall detect rate.
Who is it recommended for?
OpenRASP was developed by Baidu and so all of its documentation is written in Chinese. All of that system can be interpreted by Google’s translate function, you would do better to get into the large user community if you have a Mandarin speaker on staff.
Pros:
- Provides Activity Tracking: Records requests and invocations
- Offers a Variety Out-of-Box Features: Get started quickly
- Has a Large Dedicated Community: Provides support and advice
Cons:
- Lacks Enterprise Support: You have to rely on the community for help
Thanks to its dedicated community, OpenRASP supports a wide variety of integrations into different alert monitoring templates, ticketing systems, and SIEM products. Overall, if your organization wants to dedicate time and workforce to an open-source RASP solution, OpenRASP has you covered.
7. Veracode Runtime Protection
Veracode Runtime Protection is designed to protect applications without interfering or touching their code. This approach helps keep development environments easier to manage and avoids slowness while scanning for threats.
Key Features:
- More of an IAST: Scans and exercises code
- Spots Vulnerabilities: Runs during development
- Recommends Rewrites: Bug tracking
Why do we recommend it?
Veracode is a platform of Web application security testing services. However, its IAST tool can be set to run continuously both for acceptance testing before a module goes live and for ongoing vulnerability scanning. The system also has an automated remediation module, which makes it a defense mechanism.
Veracode does an excellent job at increasing visibility into data flow, application logic, and executed instructions. This allows teams to make changes based on their security goals while automated RASP features work hard in the background to prevent attacks and the exposure of sensitive data.
Monitoring these threats across the application layer can prevent attacks while newly discovered vulnerabilities are highlighted, ranked, and queued for remediation. In addition, this approach helps stimulate a continuous development lifecycle and gives organizations protection from inception to production.
Who is it recommended for?
DevOps teams will like the Veracode solution because they can use the same tool all the way through development through to operations. However, there are a few directions to this approach because the package doesn’t have user activity tracking, rather it is a vulnerability scanner when applied to live system.
Pros:
- Offers Simple Scheduled Scans: Can run periodically
- Controls: Stop, pause and resume scans
- Web Application Protection: Integrates directly into the DevOps lifecycle
Cons:
- No Price List: Must contact sales for pricing
Veracode positions itself as a critical component to application security and has features that can easily integrate within current DevOps teams and remediation workflows. The product has many integrations and a robust API to support SIEM tools and other products in your ecosystem. In addition, Veracode is a strong RASP product ideal for larger organizations capable of processing and remediating their vulnerabilities.
Conclusion
If you’re a large or small DevOps team, any size organization can benefit from a strong RASP vendor. RASP vendors are an essential part of application development that promotes strong security and helps increase the efficiency of the development lifecycle.
How do you protect your applications? Do you use a WAF, RASP, or different technology? Let us know in the comments below.