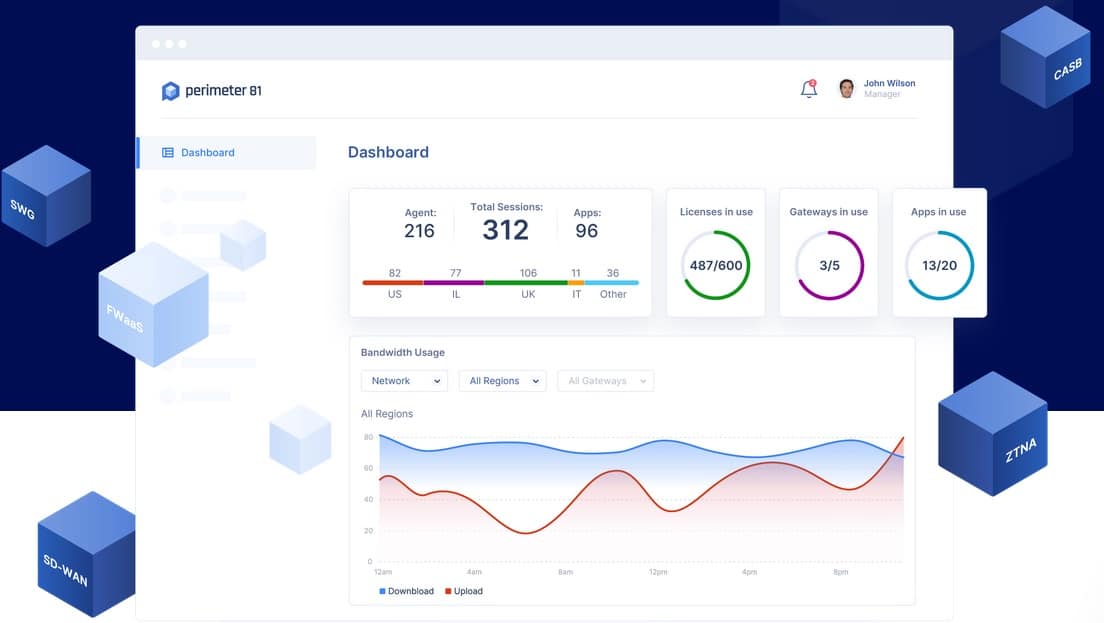
SASE stands for “Secure Access Service Edge”. It is a method of creating secure connections between sites over the internet. It is like turning the space between company networks into a single private system, enabling the network manager to treat a fragmented network as a secure whole.
Here is our list of the best SASE tools (read on for the full review of each):
- Check Point’s SASE EDITOR’S CHOICE Platform offers a flexible and user-centric network solution with features like Zero Trust application and network access, flexible VPN options, and standards compliance, allowing users to tailor services to their needs. This easy-to-use system ensures secure connections to cloud and on-premises applications, offers a customizable mix of services for various architectures, and operates primarily in the cloud with simple pricing, making it suitable for businesses of all sizes. Gain access to the free demo.
- Twingate (FREE TRIAL) This software package implements Zero Trust Access, which provides a method to deal with access controls to resources on hybrid systems. Available for Linux, AWS, and Azure. Start a 14-day free trial.
- NordLayer (GET DEMO) This cloud hub provides secure connections over the internet between sites and remote users and it also provides application security. Access the free demo.
- Cloudflare One A package of pre-existing Cloudflare products that create secure virtualized networks and services.
- Zscaler SASE A comprehensive platform of services that work through centralizing applications or data.
- Open Systems SASE An appealing contender provider with the option for on-site deployment.
SD-WAN and SASE
Understanding SASE and SD-WAN
Several related technologies help to compose a SASE system. Understanding the overlapping concepts emerging for WAN security helps better define the meaning of SASE and its purpose.
The Evolution of SD-WAN
A SASE is a refinement of the SD-WAN concept. SD-WAN stands for “software-defined wide area network”. In this technology, the network management software overlays an IP address structure over private network links that are not fixed but supplied by intermittent connections across the internet.
The Virtual Office Strategy
Taking the SD-WAN concept a little further, it is possible to do away with the internal network altogether. This idea would be of particular interest to businesses that run virtual offices. With the virtual office strategy, no one sits in the company office. Instead, they work from home or are permanently out in the field.
The Role of Cloud Telephone Exchange
The corporate telephone number can be hosted on a cloud-based exchange and map internal extension to the actual telephones, possibly mobile devices, owned by each worker. Similarly, the corporate network is a series of ad-hoc connections forged across the internet on an as-needed basis.
The Illusion of a Unified Network
Just as the Cloud telephone exchange makes it seem to the outside world that they are dealing with a group of people housed in one location, the SD-WAN makes those workers feel as though they are connected to a company network and can communicate with each other just as easily as if they were all in the same building.
Managing Networks with SD-WAN Software
In the meantime, the SD-WAN software presents an overview of a network structure, which is just a series of pointers to people instead. For example, consider endpoints on a network. Consider that a device at one IP address could be a tablet rather than a desktop. As the sales rep that uses that device moves around the country, its location within the network appears to stay in the same place.
The mediation of the SD-WAN software means that the network manager doesn’t need to know where each node is; the system can be managed from an imaginary structure rather than getting concerned with the actual physical underlying infrastructure.
SASE Systems: Cloud-hosted SD-WAN
With a SASE system, the SD-WAN software is hosted in the cloud and offered as a SaaS platform; the network administrator doesn’t need to be in the same place to access the system dashboard, which is available through a Web browser.
Adapting to Business Expansion with SASE
Being in a state of expansion, the company can switch office locations regularly and even add on temporary locations and operate pop-up outlets. In addition, the network administrator can integrate short-term contract consultants into the team without remapping any of the networks. In short, it doesn’t matter where anyone is in reality or what actual physical hardware connects them to the network.
CASB and SASE
CASB stands for “cloud access security broker.” The abbreviation is pronounced “cass-be”. It enforces security policies between the users of cloud services and the cloud resources. To operate, the CASB needs to get a look at all of the virtual network traffic. Therefore, all traffic passes through the CASB server. While it is traveling through, the CASB gets to implement security procedures and extract information for security reporting.
As SASE combines SD-WAN technology with security processes, it needs a CASB node to fulfill its purpose. Therefore, CASB is the engine that implements SASE on an SD-WAN.
The CASB is an authentication server. It is like the Active Directory for your imaginary network that the SD-WAN created. While it is operating its authentication process, the CASB system can also log which user accessed which resource and for how long. This is a crucial audit trail information for data privacy standards compliance.
SWG, FWaaS, and SASE
SWG stands for “secure Web gateway”. This is, to all intents and purposes, a firewall. The SWG will check on outgoing traffic as well as incoming traffic. The standard firewall function blocks malicious actors from gaining access and filters out malware. The reverse firewall inspects all outgoing transmission, which enables it to prevent data theft.
The SWG can be implemented on-premises on a network appliance or as an edge service on a remote server. The SWG is termed “firewall as a service” (FWaaS) in the edge service scenario.
As the SASE implements network security along with network virtualization, it needs to perform FWaaS functions. This service can be implemented as an SWG on each site or as an FWaaS operating as a proxy. If the firewall for each of your sites is a pre-filtering proxy-based somewhere out in the cloud, it isn’t too much of an intellectual leap to realize that the firewall function for all sites can be performed from the same service and controlled from a single dashboard.
VPN and SASE
If the network’s firewall is not on site but is provided by a SaaS server somewhere else, there is a security gap between that firewall and the physical network boundary. A VPN secures the gap.
The VPN is a “virtual private network”. That means software processes create the same level of privacy for internet transmissions as packets traveling over a private network experience. Not only can no one outside get into the traffic, but they can’t read the packet headers to identify the actual source and destination of the packet. Encrypting the body of a packet creates security, encryption the header of a packet creates privacy.
The SASE creates a hub, which is an edge service. This is like a very busy network switch, linking together all of the subnets of the network. For example, one virtual cable leading out of the switch might go to a single device that could be on the desk of a telecommuter in a home somewhere. Another virtual cable led to a mobile device in New York yesterday and is in Tulsa today. Another virtual cable leads to an entire office network serving a hundred desktops and printers.
When the network administrator looks at the network topology map, each cable leads to one device with one IP address, and all connections are both secure and private.
Converging virtualization and security
After looking at all of these elements of edge services: network virtualization, access rights management, system security, data loss prevention, connection protection, network performance monitoring, security monitoring, and standards compliance, you can see that all of these functions can be centralized. This is the SASE.
An FWaaS needs to get all traffic in and out of a site routed through it. As has already been explained, the firewalls for all sites can be merged into one, which creates a central point for all corporate traffic, both for traffic that circulates internally and for traffic that communicates with external locations.
As all traffic passes through the merged edge service firewall, CASB functions can all be performed in that exact location. Monitoring software can also record metrics simultaneously, and VPNs protect all connections to all locations.
Implementing SASE
As SASE is an edge service, you can expect to get a single provider’s entire network virtualization and system security package. Therefore, substantial organizations might prefer to set up their SASE by renting space on a cloud server and installing all of the necessary software elements on it. However, it is more usual to take out a subscription to an existing SaaS platform that provides a SASE package.
Our methodology for selecting a SASE platform
We reviewed the market for SASE systems and analyzed the options based on the following criteria:
- A secure package with solid encryption for connections
- Account security to prevent the central hub and data store from being broken into
- Included cloud storage space for activity logs
- A service that is compliant with data security standards
- A fast and easy-to-use network management system
- A free assessment period or demo system
- A comprehensive package that has no set-up fees or lock-in period
Using this set of criteria, we looked for a range of scalable SASE systems to be suitable for businesses of all sizes and provide flexibility for rapidly-growing startups.
The best SASE tools
1. Check Point’s SASE (FREE DEMO)
Tested on: Cloud/SaaS with VPN Client installed on each internet gateway/endpoint.
The Check Point’s SASE platform offers all of the elements of a SASE, such as Firewall as a Service, edge services for application access or network access, user-centric network architecture, and VPNs so you can create a SASE by taking out subscriptions to all of the services or just pick the parts that suit you.
Key Features:
- Zero Trust Application Access: Enhances security by verifying every access request, ensuring only authorized users can access critical applications.
- Zero Trust Networking: Strengthens network defense by continuously authenticating and authorizing every network connection, reducing the risk of breaches.
- Flexible VPN Implementations (e.g., Split Tunneling): Allows customizable VPN configurations, improving efficiency by routing only necessary data through the VPN.
- Integration of User-Owned Devices: Facilitates secure BYOD (Bring Your Own Device) practices, offering flexibility and convenience for users working remotely.
- Standards Compliance: Ensures adherence to industry standards, providing users with a secure and reliable network environment that meets regulatory requirements.
Why do we recommend it?
Check Point’s SASE is an easy-to-use network and application security system. It applies a VPN service for all users to connect safely to cloud applications and also software hosted on premises. The VPN client interface includes a menu of services, so the user is only able to access the applications that the system administrator allows.
This is the ultimate flexibility because you aren’t limited to one imposed architecture – you can pick and mix to create your system. For example, I placed gateway clients at the perimeter of my home network and I placed them on each endpoint in a virtual office to implement full virtualization with embedded security for our distributed team.
All of the operations for this SASE platform are based in the cloud, but you need to install a VPN client on each internet gateway, which could mean on each endpoint. This agent also acted as an SD-WAN addressing interpreter to fully integrate all of my sites into one network.
Who is it recommended for?
This is a flexible package that constructs a Zero Trust Access system and can be extended into a SASE through a dedicated IP address, which channels external incoming traffic through the Check Point’s SASE cloud server, creating a cloud-based firewall. Businesses with many remote workers benefit from using this system.
Pros:
- Choose to protect networks with an SD-WAN approach or implement secure application delivery from a central cloud server
- Segment users into groups regardless of their location
- Alter the layout of your network with subnets and DMZs without regard to the actual location of endpoints
- Use the facility to create a central, secure, and closely monitored primary datastore
- Integrate user-owned devices allowing private use in parallel with corporate activity without compromising network security
- Next-Gen Secure VPN service
Cons:
- Requires thorough planning to create a simplification of your service delivery with guarantee because the platform is very flexible, but worthwhile to implement
Pricing is calculated with a mix of per user and gateway charges. It can be paid per month or year, making the service accessible to small businesses, start-ups, and large organizations. You can request a demo to assess Perimeter 81 SASE.
EDITOR'S CHOICE
Check Point’s SASE is our top pick because it is so flexible. You don’t get a one-size-fits-all solution but rather have the option to decide how far you want to go with your network virtualization, choosing whether to remap the delivery of data, applications, or the entire network. In addition, scalable per-user pricing is very appealing to small businesses.
Download: Gain Access to FREE Demo
Official Site: https://www.sase.checkpoint.com/demo
OS: Cloud based SaaS
2. Twingate (FREE TRIAL)
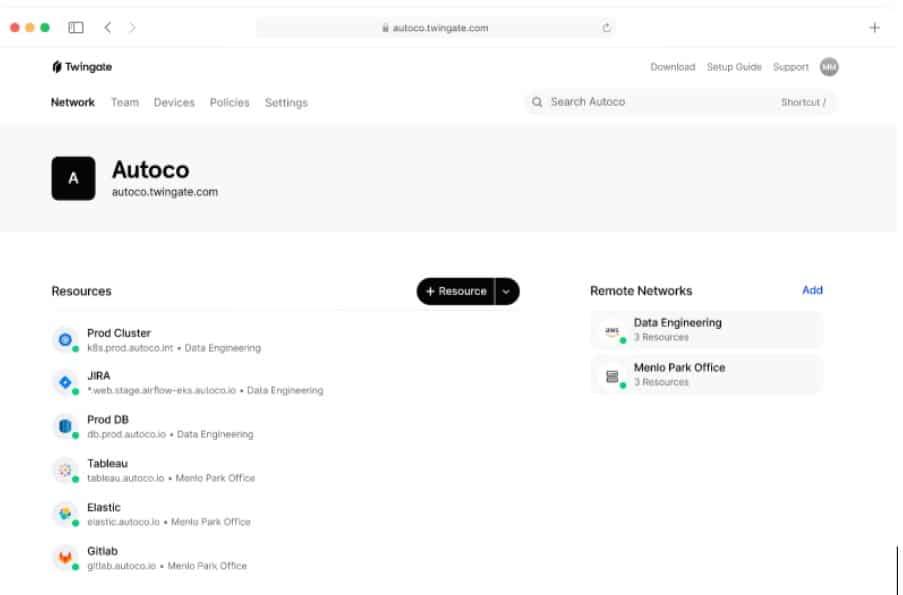
Twingate offers a self-hosted option for access controls. Although SASE systems are usually SaaS packages, not everyone is comfortable with the loss of control that these hosted systems involve. With Twingate, you can choose to host the software on your own AWS or Azure account if you want to base the system in the cloud.
Key Features:
- Self-hosted: This feature gives you the freedom to host the software on your own AWS or Azure account. It’s like having your own security system that you can control and manage according to your preferences.
- User Access App: Twingate provides an application for user access, making it easy for authorized users to connect securely. It’s like having a secure key to your online resources that fits right in your pocket.
- Microsegmentation: This feature allows you to divide your network into secure sections, enhancing your network’s security. It’s like having separate, secure compartments in a ship; if one is breached, the others remain unaffected.
- Suitable for Hybrid Systems: Twingate is adaptable and can be used with both on-premises and cloud-based systems. It’s like having a versatile security solution that fits different environments.
Why do we recommend it?
The Twingate strategy of an expanded VPN service is similar to the systems provided by NordLayer and Perimeter 81. Strictly speaking, this is a ZTA solution and not a SASE because it doesn’t include an edge firewall to define the perimeter of the virtual private network.
The Twingate strategy for system protection is based on Zero Trust Access (ZTA). This operates in a similar manner to Active Directory, requiring the system administrator to create a list of resources and another list of user accounts. You allocate a resource to each user account – this process can be eased by creating user groups.
The underlying infrastructure of Twingate is similar to a VPN service. Each user gets an access app, which is just like a VPN interface. Signing into the app gets the user validated by the authentication system in the Twingate package. This passes the user through to authorization, which checks against the defined resources to which the user is allowed access.
The access rights management service in Twingate populates a menu of services in the user app. Therefore, each user only sees a limited list of all the business’s resources. The user then gets access to a specific application by clicking on its menu entry. A single sign-on mechanism flows through the authentication used to approve the user’s login to the app so the ZTA re-authentication requirements are taken care of automatically without the user having to sign in again.
Who is it recommended for?
Twingate offers three plans, which expand its potential client base. The first plan, Starter is free and will cater to up to 10 users. This is just a group VPN service with a central administrator console. The middle plan, called Teams, provides application access controls along with connection security. The top plan adds on SSO.
Pros:
- Application-level protection
- Control access to any resource whether it is on your servers or on the cloud
- Easy-to-use access rights management interface
- Adds a list of authorized applications to the user access interface
Cons:
- Doesn’t include cloud storage space like most SASE packages
You can download Twingate software onto Linux and then run it from the operating system or through Helm or Docker containerization. You can also run the software on AWS or Azure. Access the Twingate system with a 14-day free trial.
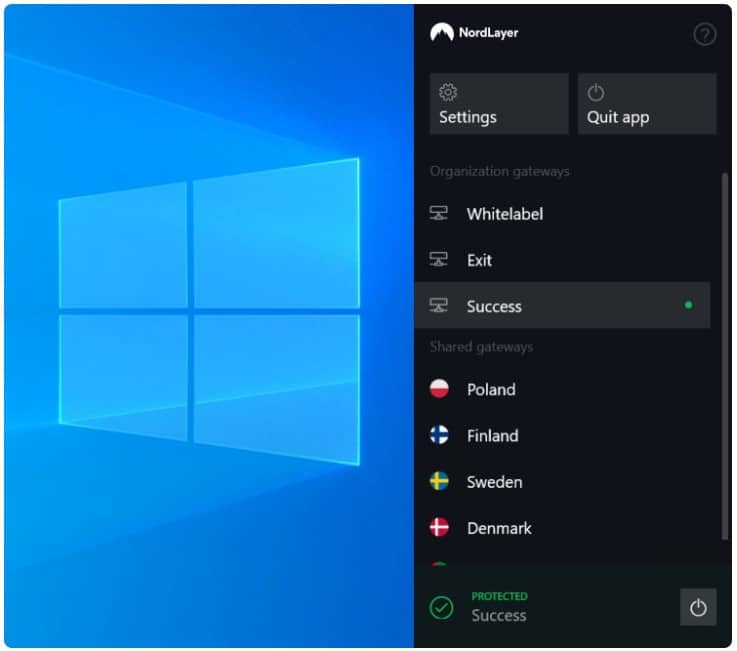
3. NordLayer (GET DEMO)
NordLayer is an innovative security solution that provides site-to-site VPNs and remote access VPNs to create a private network across internet connections. This package can also provide application access control on premises and for SaaS platforms.
Key Features:
- Zero Trust Access (ZTA): This feature ensures that every user and device is verified before granting access, enhancing the security of your network.
- Secure Connections: NordLayer provides encrypted connections, safeguarding your data from prying eyes.
- Network Security: This feature protects your entire network from threats, creating a virtual fortress around your internet connection.
- Microsegmentation: This allows you to divide your network into secure sections.
Why do we recommend it?
NordLayer is very similar to Perimeter 81. The service extends the VPN services of NordVPN, adding on access controls. The VPN client for each user includes a list of permitted applications. Again, add on the dedicated IP address service to get a cloud-based firewall and turn this ZTA solution into a SASE.
The NordLayer system is primarily a Zero Trust Access package. However, this cloud-controlled package is really a collection of tools that can be configured in different ways to provide a range of secure configurations, that include a SASE. You can create a secure virtual network with an arrangement of VPNs. The two higher plans provide a dedicated IP address. That is, essentially, a front for your virtual network and all external traffic will pass into the network through it.
Behind the dedicated server, your own traffic passes between sites and remote users over the internet. Traffic out to external sites passes through the NordLayer server. This gateway server acts as a cloud-based firewall.
That secure virtual network with a cloud firewall fronting it gives you your SASE. Once that is constructed, you can add in application control. The NordLayer system was created by the same company behind NordVPN. That VPN system provides users with an app that they can connect to the VPN with. In the NordLayer version, this only allows access to the virtual network. The system administrator can set up a list of allowed applications for each user and a single sign-on mechanism flow through the login action for the app to all of those permitted applications.
The applications to which each user has access can be on-premises or on the cloud. All users get the same portal whether they are in the office or working remotely. The tools in the NordLayer package can be used to implement Zero Trust Access without the configuration of a SASE network.
This platform offers a method to unify several sites and cloud platforms and also enables remote workers to connect to the corporate network. The NordLayer system acts as a hub, checking the authorization of users as their connections pass through to services and applications. The whole virtual network can be fronted by a dedicated IP address that is hosted on the NordLayer server. This gives a multi-site business or an enterprise that operates a virtual office a single identity on the internet. All traffic that is intended for company users and resources travels over the NordLayer VPNs; communications with the outside world pass through the NordLayer server, which provides security by filtering out traffic floods and malware.
Who is it recommended for?
NordLayer competes directly with Perimeter 81. However, the subscription rate for this service is a little simpler because Perimeter 81’s charge rate is calculated as a combination of the number of users and gateways. While the minimum team size for Perimeter 81 is 10, you can get NordLayer with a 5-user license.
Pros:
- Creates a protected private network over the internet
- Connects sites and remote users for little cost
- Integrates access rights management
- Provides a single IP address identity for multiple locations
Cons:
- No free trial
NordLayer user apps are available for Windows, Linux, macOS, Linux, Android, and iOS. There isn’t a free trial for this system but you can get a demo to examine the NordLayer system.
4. Cloudflare One
Cloudflare One is a SASE product from a well-known security provider that recently expanded its edge services menu. The Cloudflare One platform neatly stitches together all of the edge services offered by the business into an off-the-shelf package. As all contributing technologies are available individually, you don’t have to go the entire route if just parts of the concept interest you.
Key Features:
- A complete package or a menu of services
- Protect the network, applications, or data
- An established leader in edge services
Why do we recommend it?
Cloudflare One is an edge package that provides connection security between users and sites and also between users and applications. Essentially, the Cloudflare server becomes a hub for a subscribing company’s internet traffic between remote users and sites. This is a full SASE package because it includes a cloud-based firewall.
The elements in this platform are WARP, which offers network optimization through user-centric networking; Magic Transit, an SD-WAN solution, and Cloudflare Network Interconnect (CNI), a data center fabric, use the Argo service for routing.
The Cloudflare One package gives you a Zero Trust network access (ZTNA) system and DPI for traffic implementing FWaaS and data loss prevention. You can use the Cloudflare CDN to protect access to data or deliver all of your applications from a cloud server, controlling access there, thus filtering data access through the related software. Integrate network into the service with a secure Web gateway (SWG) and benefit from the standard Cloudflare DDoS protection.
Cloudflare is very good at offering free versions or free trials to its services but, as Cloudflare One is a new service and so flexible, it doesn’t even provide an automated demo account for this package. So instead, you have to request a consultation to get started on your buyer’s journey.
Who is it recommended for?
Cloudflare is good at catching startups and growing businesses by offering many of its services for free for small volumes. The company provides SSL certificates and a CDN for free and markets those services through Web hosting providers. There is a Free plan of the SASE that covers up to 50 users.
Pros:
- Flexible services that enable you to choose how to virtualize
- A well-established and trusted brand
- Plugs in established Cloudflare services, such as the CDN or DDoS protection
Cons:
- No free trial or demo account
5. Zscaler SASE
ZScaler offers a range of services that let you implement SASE in different ways. For example, choose to host all of your applications on the Zscaler server and let it implement access controls or install a gateway program on your network and let Zscaler marshal traffic across the internet by providing an IP overlay. You can also opt to centralize data storage and protect access to that or implement all of the above combinations.
Key Features:
- Virtualize the whole network or integrate remote workers
- Centralize controls on applications or data
- Offers 150 data center locations
Why do we recommend it?
Zscaler SASE is built up by three services, which are a private virtual network system, a cloud-based firewall, and a site-site VPN service. The result of combining these systems creates a virtual network over the internet to link your sites and remote users together and then control user access to applications.
Protect individual endpoints, including mobile devices, by integrating them into your home network or virtualizing everything and everyone. The Zsacaler system implements threat detection, access controls, and activity logging for compliance auditing, which every security strategy you implement.
Zscaler doesn’t publish a price list. However, you can request a demo to get a view of its services.
Who is it recommended for?
The Zscaler package is a reliable service and would be a good choice for any type or size of business. However, the company is going to find competing with the free plan of Cloudflare One a bit of a struggle, so the Zscaler SASE market is more likely to lie with mid-sized businesses.
Pros:
- Offers a choice of security focus and access models
- All cloud-based services
- Integrate an entire network with the deployment of an agent as a gateway
Cons:
- No free trial
6. Open Systems SASE
Open Systems gives you a hybrid solution that hides the underlying platform of your resources, so you can combine cloud services and on-site servers into a unified system for your users. This SASE solution pulls together SD-WAN, network monitoring, and delivery security to form a SASE.
Key Features:
- Includes SWG, SD-WAN, NGFW, CASB, and IPS
- Integrates auditing and monitoring
- Offers threat detection and data protection
Why do we recommend it?
Open Systems SASE is one of two levels of service from this managed service provider. The other level is an SD-WAN, which lacks the edge security services that are included in the SASE version. Open Systems will set up and run your SASE or SD-WAN for you.
Unlike the other tools in this list, Open System offers an on-premises deployment option for this SASE, so you can choose to run it yourself instead of using a SaaS platform. However, the SaaS route is also available.
Open Systems offers three plan levels, which means you don’t have to pay for all of the service elements if you choose a virtualization strategy that only needs specific services. The service is scalable and would be suitable for small businesses and start-ups, in addition, as well as large multinationals. The company doesn’t publish a price list or offer a demo. Instead, you need to request a quote to find an entry point into the purchase process.
Who is it recommended for?
A managed service for a SASE is a very good idea for businesses that do not have any technicians on the payroll. That would imply that this option is ideal for small companies. However, the company doesn’t publish its price list, which makes comparison on price difficult to assess.
Pros:
- Flexible options provided by three service plans to suit different virtualization strategies
- A competent service offered by a trusted brand
- On-site deployment option
Cons:
- ZTNA and CASB are add-on services
- No free trial or demo
SASE FAQs
What means SASE?
SASE stands for Secure Access Service Edge. This is a framework that expanded the network boundary so that it includes internet links across to remote sites and cloud-resident applications. SASE bundles together several technologies that include Zero Trust Access (ZTA), Firewall as a Service (FWaaS), and Software-defined WANs (SD-WANs). The concept is that your secure network is kept private by VPNs between sites, remote workers, and cloud platforms. While authorized users can get into the system, outsiders are held at bay be boundary security, which is implemented as an edge service and delivered from the cloud.
What is SASE and how does it work?
Secure Access Service Edge (SASE) combines sites, remote, workers, and cloud platforms into an extended private network that includes both on site and internet connections. Users access services through a cloud-based hub, which acts as an authentication service. Communication with the world outside the virtual network is mediated by a cloud-resident Firewall as a Service (FWaaS).
Who invented SASE?
The concept of the Secure Access Service Edge (SASE) was first outlined by Neil McDonald and Joe Skorupa who work for the management consultancy, Gartner, Inc. The term first appeared in Hype Cycle for Enterprise Networking, 2019.