It is impossible to imagine a business without an email solution – at least if it wants to remain in business for long. However, it is also unimaginable to be lenient with the security of email and gateways, especially when it remains one of the top ways hackers use to gain access to networks and steal data.
Here is our list of the best secure email gateways:
- TitanHQ Email Security EDITOR’S CHOICE Αn easy to set up, deploy, manage, and use email gateways solution; has features like blacklisting, whitelisting, and even offers antivirus protection. Get a 14-day free trial.
- Cisco Secure Email This service scans incoming emails and blocks any emails that contain business email compromise, phishing attempts, spam, and malware.
- Microsoft Defender for Office 365 Α native Microsoft solution that is cloud-based and helps reduce the cost of ownership of all Office 365 applications, including Outlook; it protects clients on collaboration sites using real-time reports and automatic threat mitigation responses.
- Avanan Αn email gateway that uses AI to protect against sophisticated attacks; it is an ideal solution for Office 365 and Google Workspace users and can also protect any email environment.
- Proofpoint Email Protection Αn industry-leading solution that uses AI to defend against BEC; it has numerous features that learn and adapt to new threats, which keeps a safe business well into the future as it keeps evolving.
- Mimecast Α cloud-based secure email gateway that is ideal for larger organizations; it offers many features, including defense against malware, credential harvesting, impersonation attacks, and zero-day attacks.
- Forcepoint Email Security Solution Τhis tool has features that help defend against threats from high-risk or disgruntled internal users; a rather interesting part is its OCR capabilities that allow it to scan images for sensitive data.
The email security challenges
Email is one of the most widely used communication tools, but it also presents significant security challenges. Cybercriminals frequently target email as a vector for various types of attacks, exploiting vulnerabilities to gain unauthorized access to sensitive information. Understanding these challenges is crucial for both businesses and individuals to protect their systems and data.
Here are some of the main security challenges associated with email:
- Phishing Attacks: Fraudulent emails that appear to be from legitimate sources, designed to trick recipients into revealing personal information such as login credentials or financial details.
- Spear Phishing: A more targeted attack, where cybercriminals tailor emails based on their victim’s personal or professional information for a higher success rate.
- Malware Distribution: Cybercriminals often use email to distribute malicious attachments or links that deliver malware, such as ransomware, spyware, or viruses.
- Email Spoofing: Attackers forge the sender’s email address to make it appear as though the message is from a trusted source. Spoofed emails trick employees into compromising security.
- Data Breaches: Sensitive information sent through email can be intercepted if not properly encrypted. Weak passwords or inadequate authentication methods leave email accounts vulnerable to unauthorized access.
To address these email security challenges, organizations should adopt automated measures such as:
- Implementing advanced spam filters and anti-phishing software.
- Using multi-factor authentication (MFA) for added protection.
- Encrypting sensitive email content.
- Educating employees through training on recognizing email threats.
These proactive strategies help mitigate the risks associated with email communication and enhance overall security.
What is an email gateway?
An email gateway is a type of server that protects email servers; it acts as a “gateway” through which all emails – incoming and outgoing – pass through. And as it is passing through, each email is scanned for malicious content or harmful links, as well as any attached documents containing proprietary or confidential information that shouldn’t leave a business’ perimeter.
A gateway could be installed on-premises or run as a SaaS in the cloud. It doesn’t itself host any user email accounts or inboxes. Instead, it sits in the DMZ of a network to inspect and analyze all mail traffic before letting them through.
Only after the email gateway has done preliminary checks does a message leave it to go to the actual email server. These checks include finding out if there are any phishing links or if the email itself is spam.
Now, depending on its type, an email gateway can respond to malicious emails in some ways. Examples include:
- Changing links in suspicious emails to ensure safety.
- Using a whitelist or blacklist to decide which emails are permitted to reach the mail server and which ones aren’t.
- Running an antivirus or DLP to clean the email and its attachments or ensure no data is being leaked.
- Routing emails to the correct domain to ensure outgoing messages reach the right network and intended recipients.
It should be noted here that although an email gateway does have its methods of securing email, it is a secure email gateway (SEG) that does a more complete and in-depth job.
What is a secure email gateway?
A Secure Email Gateway is also a software or hardware gateway that works like a firewall to stop malicious or spammy emails from entering the network. But, in this case, it takes the security measures in the standard email gateway and amps it up to protect against more severe and complex issues and attacks.
Secure email gateways stop unwanted emails with spam, phishing links, attached malware, or fraudulent content. These emails can be quarantined, ignored, deleted, or simply bounced back with an error message.
They also scan outgoing messages and perform analyses to prevent sensitive data from leaving the business network. Alternatively, they can automatically encrypt emails containing sensitive information, rendering them useless to the malicious user.
Depending on requirements, secure email gateways can be deployed as a SaaS, as an on-premises appliance, or on Office365 and Google Workplace.
Our methodology for selecting a secure email gateway
Features and capabilities to look for in reliable, secure email gateways include:
- Scanning capabilities It should be able to scan emails on the go and identify threats.
- The ability to defend against multiple threats Should protect against most threats like phishing, malware, and malicious links.
- Advanced threat identification It should have AI technology that teaches it about evolving threat delivery methods and identify them.
- Deployment options Businesses should be able to deploy the solutions on any network architecture.
- Reporting Reports from these tools should give insight into present security health and serve as proof of compliance or audits.
- Additional features A good solution should integrate well into a network’s security and support it with its other Good examples could be encryption, archiving, and reports.
- Price The ROI should always be worth it.
We have sought these features in the best secure email gateway solutions that we will see next.
The Best Secure Email Gateways
It’s now time to have a look at the best secure email gateways in detail:
1. TitanHQ Email Security (FREE TRIAL)
TitanHQ Email Security is a solution built on a powerful spam filtering platform that boasts a market-leading catch-rate of 99.99 percent and a false positive rate of 0.0003 percent.
Key Features:
- Dual Threat Defense: Combines spam filtering with malware protection for double security.
- Customizable Controls: Allows for precise management of whitelists, blacklists, and email policies.
- Machine Learning Security: Employs machine learning for advanced threat anticipation and protection.
- Protects cloud-based email systems: Exchange Server and Gmail
- Cloud-hosted system: you don’t need to provide server space for it
Why do we recommend it?
Email Security from TitanHQ is one of the leading spam filters on the market. The company also provides phishing and malware protection in its secure email gateway solution. The service performs checks on the domain and IP addresses of inbound emails, referring to a blacklist, and it scans content and attachments.
Email Security is easy to set up, deploy, manage, and use, and yet, it offers antivirus protection on top of the spam blocking to create an environment that is twice as secure. Administrators can use whitelists and blacklists to handle permissions, recipient verification to curb spamming, and monitoring of email flow for malicious content.
Allows whitelisting and blacklisting, advanced reporting, recipient verification, and outbound scanning of email; the tool itself comes with specialist Real-Time Blacklists (RBLs) and email content filtering to create rules depending on security requirements.
Meanwhile, the tool also makes sure the business’ IP address isn’t blacklisted because it is mistaken for a spamming domain by scanning all outgoing emails. Administrators can create custom policies to create block lists at the user, domain, domain group, and total system levels.
Email Security offers security against infected attachments by blocking specific attachment types like .exe .bat files – and by domain, if need be. It uses predictive technology to anticipate new attack methods and also offers advanced threat protection using an inbuilt Bayesian
A secure solution for email needs the ability to anticipate new attacks using predictive technology; it also offers Advanced Threat Protection – an inbuilt Bayesian machine learning and heuristics.
Email Security also has powerful data leak prevention (DLP) rules to prevent internal data loss on top of the ability to prevent whaling and spear-phishing by scanning all inbound emails in real-time.
This tool protects businesses by blocking spam, viruses, malware, ransomware, and links to malicious websites.
Who is it recommended for?
Email Security is a proxy that you can get as a cloud-based system or as an on-premises appliance. Either way, it pre-filters inbound emails for threats and scans the contents of outbound emails for data loss prevention. There is also a version for managed service providers that will protect their clients.
Pros:
- Per-user pricing: A scaleable system for all sizes of businesses
- Suitable for managed service providers: An MSP edition is available
Cons:
- Not for very small businesses: The minimum account size is for 25 users
You can start with a 14-day free trial.
EDITOR'S CHOICE
TitanHQ Email Security is our top pick for a secure email gateway because this platform provides full AI-based scans of email contents, embedded links, and attachments. As well as protecting against spam, this package scans for malware, which makes it very good value for money. The system integrates with Microsoft 365 and Google Workspace, protecting email accounts in Exchange Server/Outlook or Gmail. The cloud-based service provides a quarantine area on the TitanHQ server, to which the scam and malware scanners send all blocked emails. This gives the administrator the opportunity to review those emails and possibly override the automated decision to block them. The machine learning algorithm in the detection system of TitanHQ automatically adjusts according to these decisions.
Download: Access a demo
Official Site: https://www.titanhq.com/complete-360-security/
OS: Cloud-based
2. Cisco Secure Email
Cisco Secure Email (formerly Email Security) – a product from a leading network security company that was selected as Top Player in Radicati’s Secure Email Gateway – Market Quadrant 2020. The tool is a cloud service that acts as a proxy, filtering all of your incoming emails and can also scan outgoing emails for data loss prevention.
Key Features:
- Advanced Spam Filtering: Efficiently identifies and blocks spam emails, enhancing inbox security.
- Phishing Defense: Actively blocks phishing attempts to safeguard sensitive information.
- Malware Protection: Scans and removes malware from attachments to prevent infections.
- Data Security: Implements data loss prevention strategies to protect confidential information.
- Cloud Integration: Utilizes a cloud-based approach for flexible email security management.
Why do we recommend it?
Cisco Secure Email is a cloud-based service and part of the Cisco XDR suite of system protection tools. This package provides inbound filtering with the Cisco Secure Email Threat Defense. It is able to spot a range of attacks, including phishing, BEC, and infected attachments. It performs a range of checks that include source domain verification.
This email gateway protects businesses and users against attacks using methods like phishing, business email compromise (BEC), malware attachments, and ransomware – it boasts industry-leading threat intelligence used to combat malicious links.
It can be used to comply – or audit compliance – to government and industry regulations thanks to its robust data loss prevention capabilities and encryption capabilities that ensure data is safe at all times.
Integration with SecureX – Cisco’s integration platform – gives enhanced visibility and automation across a range of the company’s security products; this ensures full-stack security coverage. It can spot fake email addresses using dynamic threat intelligence and stay up to date to tackle the latest BEC, phishing, malware, and domain spoofing attacks.
Cisco Secure Email monitors inbound emails continuously to protect users from risky files no matter when they may get infected; it is immediately isolated once a threat is identified. This solution offers maximum flexibility to be deployed on-premises, in the cloud, virtually, or in hybrid architectures. Along with the tool, Cisco offers Secure Awareness Training to help businesses cover their weakest links – their users.
Cisco Secure Email has an extensive battery of tests that scan emails in little time to block threats. The service looks for known fraud tests within the body of the email, scans for malware in attachments, and identifies fake email addresses. This tool can also be used for data protection compliance in a reverse proxy format by implementing data loss prevention
Who is it recommended for?
Cisco merges all of its protection systems into one through its XDR package and the Secure Email Threat Defense service feeds event data into that for improved detection of system-wide attacks. Companies interested in that XDR package are the most likely buyers of the Secure Email system.
Pros:
- Versatile Deployment: Adaptable to various environments, including cloud, on-premises, and hybrid setups.
- Comprehensive Threat Intelligence: Utilizes cutting-edge intelligence to detect and neutralize evolving threats.
- Seamless Integration: Works harmoniously with Cisco SecureX for enhanced security visibility.
Cons:
- Complex for Small Setups: May be overly intricate for smaller business environments.
Try Cisco Secure Email (including SecureX) FREE for 45 days.
3. Microsoft Defender for Office 365
Microsoft Defender for Office 365 dashboard showing its abundant featuresOur second choice is Microsoft Defender for Office 365 (formerly ATP) – another product from a leading tech company that is also a leader in the Email Security market. This is primarily a good choice as it offers native protection for Office 365, including the popular Microsoft Outlook.
Key Features:
- Cloud Compatibility: Designed for seamless integration with cloud services.
- Exchange Server Integration: Integrates smoothly with Exchange Server for enhanced email security.
- Advanced Threat Protection: Blocks sophisticated BEC, phishing, and malware threats effectively.
- Insightful Reporting: Provides detailed threat analysis reports for informed decision-making.
Why do we recommend it?
Microsoft Defender for Office 365 takes the familiar Windows Defender up into the Microsoft 365 platform. Ironically, this product has become available while Microsoft has deprecated the Defender name on Windows in favor of the name Windows Security. This service will also protect Teams.
This is a cloud-based email filtering service; it helps businesses protect themselves from attacks across the cyber kill chain and allows for collaboration and, hence, quicker issue resolutions.
It protects Office 365 against advanced threats like BEC, phishing, zero-day malware attacks emanating from malicious email messages, links (URLs), and collaboration tools; it automatically investigates and remediates attacks with no manual intervention required.
This solution has rich reporting and URL trace capabilities that give administrators in-depth insights into the kind of attacks – in real-time; they gain visibility into the threat landscape and can leverage the actionable insights to mitigate threats immediately.
It can identify and block malicious files in collaboration sites and document libraries like SharePoint, OneDrive, and Microsoft Teams.
Defender is intelligent – its anti-phishing protection is powered by machine learning and advanced algorithms that can detect attempts to impersonate users or domain spoofing.
It allows administrators to be more proactive in defending their users – they can run simulations of realistic attack scenarios to identify vulnerabilities.
Its Threat Explorer is a real-time report that helps identify and analyze threats manually. At the same time, Defender’s Automated Incident Response (AIR) capabilities automatically tackle them, saving security operations teams’ time and effort.
As this tool is built into Office 365, it cuts investments required to integrate third-party security tools; and with it being native, it doesn’t diminish the user experience at the endpoints.
Microsoft offers Defender to help its users boost productivity, simplify administration, and lower overall costs-of-ownership with its homegrown protection solution.
Who is it recommended for?
The Microsoft Defender system protects all features in the Office 365 package, not just its Exchange/Outlook email system. It will identify BEC, phishing, and malicious attachments and it operates as a SIEM and XDR across your group account. As the protected system ruins on the same platform, you don’t have to host anything.
Pros:
- Native Office 365 Protection: Offers built-in security specifically for Office 365 applications.
- Automated Incident Response: Streamlines attack investigation and remediation with automation.
- User Training Tools: Features simulation tools for identifying and improving security vulnerabilities.
Cons:
- Limited Integration Flexibility: Offers minimal options for integrating external security tools.
- Platform-Specific: Primarily beneficial for environments fully invested in Microsoft 365.
Try Microsoft Defender for Office 365 for FREE.
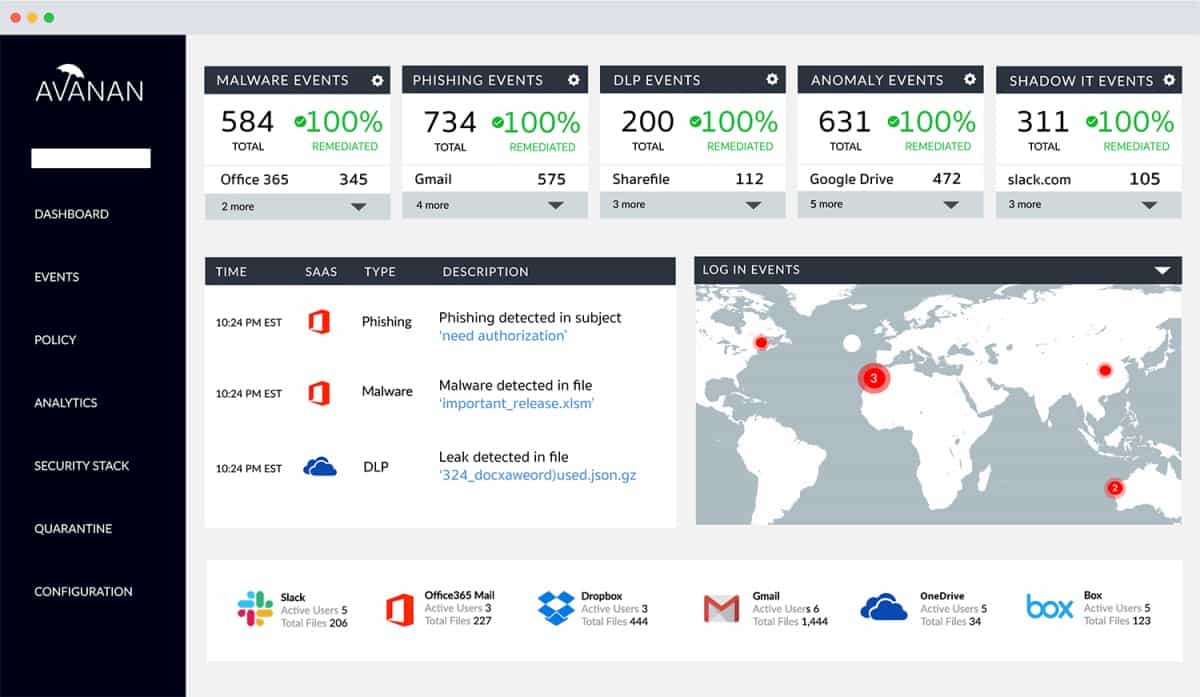
4. Avanan
When it comes to Avanan, the keyword is “advanced AI”. This API-Based email security solution is powered by True AI, trained on comprehensive data sets to stop the most sophisticated phishing attacks before they reach the inbox.
Key Features:
- Cloud-First Approach: Provides comprehensive email security for cloud-based systems.
- Versatile Email Protection: Guards against BEC, phishing, and other email threats across platforms.
Why do we recommend it?
Avanan will protect all of your email systems whether they are hosted on your own servers and accessed on your business’s endpoints or hosted on the cloud and accessed by employees on their own mobile devices. This tool is a proxy and it will integrate with Gmail, Micorosft 365, and other hosted email systems.
Being a cloud-based email security solution means Avanan can help protect inboxes in applications like Outlook and Gmail – for users of Office 365 and Google Workspace; but, it goes beyond that to implement security for applications for Microsoft Teams.
Its advanced AI means businesses implement an accurate machine learning technology to stay on top of the latest, sophisticated attacks in real-time.
These sophisticated attacks include email threats like phishing, malware, account compromise, and data loss.
It is easy to deploy, and once done, it sits inside the email environment without requiring any MX record changes. In addition, because it is API-based, it integrates well into the environment allowing it to analyze archived emails that detect impersonators and fraudsters.
What’s more, it covers multiple layers. For example, this tool offers threat protection inside the email inbox, and it can also monitor and secure incoming, outgoing, and internal emails as they are in transit.
Machine learning technology allows it to identify zero-day phishing attacks using more than 300 indicators of compromise like sent time, location, and domain name – to flag suspicious emails.
Meanwhile, machine learning algorithms allow Avanan to detect BEC by flagging logins made from unusual locations or pointing administrators towards any unusual behaviors that indicate accounts having been taken over. Then there is protection against malicious attachments and URLs that link to harmful content.
Avanan offers advanced reporting for all inbound, outbound, and internal emails while providing real-time and historical visibility into all users and email threats.
This technology allows it to protect inboxes better and even identify threats that other similar solutions might miss.
Who is it recommended for?
Avanan has wide capabilities, which makes it ideal for businesses that didn’t settle on one email system across the company. For example, it can scan your company email system while also protecting side accounts in systems, such as Gmail. The administrator gets to see where in the world those suspicious emails came from.
Pros:
- Advanced AI Detection: Utilizes AI for pinpoint accuracy in identifying sophisticated email threats.
- Easy Deployment: API-based solution for straightforward implementation without MX record changes.
- Broad Coverage: Monitors and secures email traffic in all directions—incoming, outgoing, and internal.
Cons:
- Additional Costs for Extras: Some advanced protection features require separate purchase.
- Short Trial Period: Limited time for evaluating the full capabilities of the service.
Schedule an Avanan demo for FREE.
5. Proofpoint Email Protection
Proofpoint Email Protection is an industry-leading email gateway security solution that can be deployed on-premises or as a cloud service. It is powered by Nexus A.I. – an advanced machine learning technology platform – which makes it powerful enough to identify both known and unknown threats that other security solutions can’t even sense.
Key Features:
- BEC Safeguards: Implements advanced defenses against Business Email Compromise using AI.
- Efficient Spam Control: Utilizes robust algorithms to block spam emails effectively.
- AI-Driven Detection: Employs artificial intelligence for identifying emerging threats.
Why do we recommend it?
Proofpoint Email Protection is another cloud-based service that scans through inbound emails before they reach your email server. The system looks for impersonation, spoofing, phishing, and malware. The system allows administrators to tag emails and then pass them through with a warning message for user awareness.
Proofpoint offers the Advanced BEC Defense – backed by Nexus A.I. – that can classify various types of email accurately and stop a wide variety of email fraud, including payment redirects and supplier invoicing fraud.
This threat detection engine is specifically designed to identify BEC attacks by analyzing metadata like message header data, sender’s IP address – including the origin and reputation analysis – and scanning the message body for keywords, phrases, etc.
It can detect various BEC tactics, including reply-to pivots, malicious IPs, and domain spoofing; suspicious emails can be automatically tagged with clearly legible warnings to reduce the chances of compromise due to end-users not being aware of threats.
Proofpoint’s AI means it offers dynamic protection that continues to evolve and defend against new malware, threats, and other malicious technology; it can also perform reputation and content analysis.
It can help reduce IT overhead by identifying graymail – like newsletters, bulk mail, and other low-priority emails – and filtering them out to help recipients bring them under control and deal with them as they deem fit.
Administrators can use the log data to help with troubleshooting – searches are made easier with the help of dozens of search criteria.
Who is it recommended for?
This system is suitable for mid-sized and large organizations. Proofpoint doesn’t publish a price list, which will put small businesses off enquiring about it. The system will archive all emails, which is a requirement for data protection standards compliance. The email store includes a search utility for analysis and email retrieval.
Pros:
- Unified Archiving & Security: Integrates email security with archiving for comprehensive compliance.
- Long-Term Email Retention: Capable of preserving emails for up to a decade, aiding in regulatory compliance.
- Phishing Defense: Enhances security with URL validation to thwart phishing efforts.
Cons:
- Limited Customizability: Could benefit from more flexible customization options for diverse needs.
Request a 30-day trial of Proofpoint Email Protection for FREE.
6. Mimecast
Mimecast is a cloud-based secure email gateway. It offers a high level of threat protection and granular admin policies that fit a corporate environment.
Key Features:
- Impersonation Defense: Protects against BEC and impersonation with sophisticated AI.
- Scam Detection: Utilizes AI for early detection of scams and fraudulent activities.
- DNS Authentication: Employs DNS-based techniques for authenticating email sources.
Why do we recommend it?
The Mimecast system uses a number of advanced techniques to identify threats. These include DNS analysis to identify spoofing and impersonation. The service also uses machine learning to identify business email compromise (BEC) and payment fraud. The system also detects phishing attempts and malware in attachments.
This is a versatile tool – it stops malware, credential harvesting, impersonation attacks, performs deep inspection for zero-day attack protection, performs DNS-based authentication, and includes DMAARC, SPF and DKIM
It uses machine learning technology to protect against BEC and targeted attacks from outside and inside the organizations.
Administrators can set policies and scan for keywords indicating malicious attachments trying to bypass security or proprietary content that shouldn’t be leaving the business’ confines; Mimecast DLP can detect and block emails containing personal information.
They can also automatically encrypt authorized messages sent to confirmed recipients and contain some of these keywords to ensure the safety of sensitive data without requiring the users to log into a new portal or use encryption keys.
Mimecast also offers Secure Messaging, which can respond to triggered alerts by encrypting messages as they go out and then recalling or expire emails to prevent recipients from reading them after they have been sent.
Mimecast is as powerful as customizable to accommodate specific needs in unique environments – making it strong protection against email threats.
Who is it recommended for?
This package is designed for use by large organizations with a lot of emails to manage. It can extend its protection to Microsoft 365 email components and Gmail. It also provides an archiving service that includes a search utility. This is a very close competitor to Proofpoint Email Protection.
Pros:
- Comprehensive Email Gateway: Acts as a complete solution for email security with advanced threat detection.
- Innovative Threat Detection: Leverages pattern recognition and behavioral analysis for identifying novel threats.
- DNS Security Enforcement: Assists in ensuring proper use of DNS security protocols like DKIM, SPF, and DMARC.
Cons:
- Cloud-Only Offering: Limits options for organizations preferring on-premises or hybrid solutions.
Request a Mimecast demo for FREE.
7. Forcepoint Email Security Solution
Finally, we have Forcepoint Email Security Solution – a secure email gateway that helps identify and prevent targeted attacks, high-risk users, and insider threats. It also empowers remote and mobile workers by allowing the safe integration of third-party cloud technologies like Office 365 and Box Enterprise.
Key Features:
- OCR Capabilities: Features OCR scanning to identify threats within image-based documents.
- Macro Threat Analysis: Detects malicious macros in documents to prevent targeted attacks.
- Data Protection: Offers comprehensive data loss prevention to secure sensitive information.
Why do we recommend it?
Forcepoint Email Security provides all of the standard email protection services from its cloud base. It detects, phishing, spoofing, BEC, and malware. A unique feature of the Forcepoint threat detection system is that it can scan images of documents with OCR. Thus, even threats embedded in digital documents can be identified.
Forcepoint has Optical Character Recognition (OCR) scanning to help spot sensitive data hidden in images like scanned documents or screen grabs; it has advanced capabilities to detect data leaks using images or custom-encrypted files – even when attempting to transmit them using small amounts, spread over time to evade detection.
It has encrypted file detection to recognize custom encrypted files intended to bypass identification screening and offers advanced analysis of macros embedded in MS Office files.
Conditional security access – it curbs full access to sensitive email attachments on risky mobile devices, for example, while allowing them to be still accessible on more secured devices.
Reports can be generated for auditing proposes to assess current overall security status, check for vulnerable systems, infected devices, and those showing suspicious behavior – including “disgruntled employee” activities.
Forcepoint can be deployed in the cloud, with pre-filtering services to conserve bandwidth, in addition to being installed on-premise as a local threat protection tool. There is no compromise on performance necessary.
Who is it recommended for?
This is a solution for large businesses. It is a proxy service that stores all intercepted emails on the cloud. It also integrates with cloud email systems, such as Microsoft 365, and cloud drives, such as Box. Outbound email scanning provides data loss prevention.
Pros:
- Advanced Malware Defense: Utilizes AI for proactive detection of zero-day and sophisticated malware attacks.
- Traffic Inspection: Capable of swiftly analyzing high volumes of email traffic for potential threats.
- Cloud Data Monitoring: Monitors and reports on cloud data usage for enterprise-wide visibility.
Cons:
- Not Suited for Small Networks: May not be the optimal choice for smaller organizational networks due to its extensive capabilities.
Request a customized Forcepoint Email Security Solution demo for FREE.
Where can email gateways be installed?
Ok, we have just seen the best secure email gateways. Now, let’s briefly look at where they can be installed. There are several setup options to choose from:
They can be installed on specific servers; they can, for example, be solutions dedicated to Exchange servers only.
As an on-premises hardware device – a dedicated hardware appliance sitting on the organization’s network; all email traffic, inbound or outbound, is routed through it for analysis and filtering.
As an on-premises VM – a virtual appliance for email security that could be part of a private cloud controlled by the business; alternatively, it can run on on-premises servers without necessarily being part of the cloud architecture.
On public cloud platforms – there are email security gateways that are available as public cloud-based services.
A hybrid setup involves combining a public cloud setup with an on-site presence; this is a typical hybrid deployment that combines public cloud-based service with an on-premises deployed hardware or VM.
Regardless, it is up to the business to find the ideal configuration that works well with their network architecture.
Every business needs secure email gateways
Apart from the fact that emails are the most commonly exploited business process, there are a few more reasons for installing secure email gateways, including:
They protect employees from email threats like spam, viruses, and phishing attacks, which protects businesses.
Secure email gateways allow businesses to improve security for employees by blocking malicious emails and stopping phishing attacks – factors that could affect their productivity.
Secure email gateways also allow businesses to meet compliance requirements – companies that need to handle specific data will always need to install secure email gateways.
Many secure email gateways offer email archiving capabilities – this helps businesses secure their confidential data; archiving, along with encryption, also helps with meeting compliance requirements as copies of emails may need to be stored for legal reasons.
The bottom line is: businesses can dramatically reduce their vulnerabilities, exposures, and threat levels by installing one of the best secure email gateways we have seen above.
We would like to hear what you think. So please, leave us a comment below.
Secure email gateway FAQs
What is secure email gateway?
A secure email gateway (SEG) operates as a proxy system and all of your email traffic passes through the service before reaching your email servers. This traffic diversion gives the ESG the opportunity to scan all emails and drop all malicious communications. Genuine emails are passed on to your email server. SEGs can also be set up to scan outgoing emails to prevent data theft.
Why use a secure email gateway?
Many email systems now have spam filters included in them. However, fraud attempts are harder to identify and so you would use a secure email gateway (SEG) for more comprehensive protection. SEGs use text scanning and can even examine images for texts that indicate BEC or other types of email-based fraud attempts.
Do I need an email gateway?
A secure email gateway (SEG) is a good choice for businesses of all sizes because these services are cloud based and charged for by subscription. This means that you don’t need to manage the security software yourself or even find server space to host them. The charging structure of SEGs makes them affordable to the smallest businesses and they offer important protection from fraud attempts and credentials theft.