Developers love writing code – they have to. Otherwise, they wouldn’t have chosen their profession. But, if there is one thing that can make their lives miserable, it is an error message throwing their new applications into chaos. And nothing is more frustrating to them than not being able to track the cause of the bugs
Here is our list of the best static code analysis tools:
- Checkmarx SAST Another popular enterprise-grade tool, flexible, and accurate static analysis tool that can identify security vulnerabilities in any code early in the development process.
- Synopsys Coverity A SAST tool to quickly find and fix bugs like critical defects, vulnerabilities, and lapses in compliance standards; it is easy to use, accurate, scalable, and integrates well into development environments.
- SonarQube A popular static code analysis tool that can be used for error identification and security testing. This is an open-source package that is available in free and paid versions.
- Micro Focus Fortify Static Code Analyzer (SCA) A static code analysis tool that locates the root causes of vulnerabilities, and prioritizes issues by severity, providing detailed resolution guides. It also offers dynamic application testing as well as source code analysis.
- Aikido This cloud-based offers free and paid SaaS plans that provide static application security testing for DevOps teams. This package is going to provide more value during the development phase and it can be set up as a continuous tester for the release process in a CI/CD pipeline.
- Veracode Static Analysis A static code analysis tool that scans deployments thoroughly before they are released and gives automated feedback and guidance on resolving issues; it can cut mistakes made by half and has a small digital footprint and scans.
- Snyk Code A quick and effective static code analysis tool that boasts high scan speeds and uses semantic analysis to find bugs and vulnerabilities; it is a free tool for individual developers and small teams.
What is static code analysis?
Let’s define static code analysis:
Developers use static code analysis tools to find and fix vulnerabilities, bugs, and security risks in their new applications while the source code is in its ‘static’ state – meaning when it is not being run.
This process helps reduce exposure to internal and external security risks, allows developers to create applications quickly, and lets businesses see where they stand concerning compliance to industry security standards.
Note: To find out more about SAST, you can refer to “What is SAST (Static Application Security Testing)?” – This is a post that gives a comprehensive insight into the technology itself.
This is all in contrast to Dynamic Application Security Testing or DAST, where the analysis occurs while the application is running.
The Best Static Code Analysis Tools
Our Methodology for selecting a static code tool:
Businesses and developers should consider the following factors when comparing and choosing static code analysis tools:
- Low false-positive rates – a question is what volume of false positives users of a product encounter. Their tool should help them save time, not waste it chasing issues that don’t exist. Also, the tool should make it easy to manage false positives, regardless of how low the rate of occurrence, when they do (inevitably) encounter them.
- IDE Integration – users should be able to integrate their tools into their existing developer environments. This is critical in measuring how early in the software development life cycle (SDLC) the tools can be used; the earlier it can be used, the more effective it becomes.
- The extent of automation – they should also ask to what extent the static testing can be automated within the development environment. Incidentally, SAST has traditionally been considered one of the more manually-driven security testing methods. Any level of automation improves efficiency.
- Detailed reporting capabilities – developers should be able to figure out where they have gone wrong quickly and then fix the issues without resorting to more research. A good tool will not only highlight errors but also provide ample documentation and training for better understanding and directly contributing to the resolution of issues.
- The price – the price of a SAST should be worth the tool’s performance and its features. After all, why pay for any product when there is a better alternative on the market for free?
Feature Comparison Table
| Tool/Features | Checkmarx | Synopsys Coverity | SonarQube | Micro Focus Fortify SCA | Aikido | Veracode Static Analysis | Snyk Code |
|---|---|---|---|---|---|---|---|
| Language Support | Multiple | Multiple | Multiple | Multiple | Multiple | Multiple | Multiple |
| Integrations | Various IDEs, CI/CD | Various IDEs, CI/CD | Various IDEs, CI/CD | Various IDEs, CI/CD | Various IDEs, CI/CD | Various IDEs, CI/CD | Various IDEs, CI/CD |
| Free Trial | Yes | No | Yes | Yes | Yes | Yes | Yes |
| On-Premises/Cloud | Both | Both | Both | Both | Cloud | Both | Cloud |
| Automated Scans | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Compliance Reporting | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Vulnerability Database | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Real-Time Feedback | Yes | No | Yes | No | Yes | No | Yes |
1. Checkmarx SAST

With Checkmarx, we have another leading player in the static code analysis tool market. Its product is an enterprise-grade, flexible, and accurate static analysis tool.
It can identify hundreds of security vulnerabilities in any code. It is used by DevOps and security teams to scan code early in the SDLC to spot vulnerabilities, compliance issues, and business logic problems – and also offers advice on how to solve them.
When we tested Checkmarx we found the following key features.
Key Features:
- Static Code Analysis: Performs static analysis of source code to identify security vulnerabilities, such as SQL injection, Cross-Site Scripting (XSS), and insecure authentication mechanisms.
- Wide Language Support: Supports a wide range of programming languages including Java, C#, C/C++, JavaScript, Python, PHP, Swift, and more, enabling it to analyze code across diverse technology stacks.
- Vulnerability Detection: Detects a variety of security vulnerabilities and coding flaws, including OWASP Top 10 vulnerabilities, compliance violations, and industry-specific security standards.
- Integration with CI/CD Pipelines: Integrates with CI/CD pipelines and development environments, allowing for automated scanning of code as part of the build and deployment process.
- Customizable Rulesets: Allows users to customize rulesets and policies based on organizational security requirements and coding standards.
- Detailed Reports and Remediation Guidance: Generates detailed reports with identified vulnerabilities, including risk severity, location in code, and remediation recommendations.
Why do we recommend it?
Checkmarx SAST is part of a platform of automated testing tools that also offers dynamic testing methods, so it is possible to combine them both. The tool will integrate into code repositories and bug trackers, so it is possible to set the tester to launch as part of the commitment process for code.
Who is it recommended for?
Checkmarx is a cloud-based SaaS package, so, those who want a hosted application testing package instead of one that needs to be self-managed would prefer Checkmarx over SonarQube. Apart from their deployment models, these two packages are very similar.
During our testing, we identified the following pros and cons related to Checkmarx.
Pros:
- Comprehensive Security Coverage: Provides comprehensive coverage of security vulnerabilities and coding flaws, enabling organizations to identify and remediate security risks throughout the software development lifecycle.
- Accuracy and False Positive Reduction: Employs advanced static analysis techniques to minimize false positives and false negatives, reducing the likelihood of overlooking critical security issues
- Integration with Development Environments: Seamless integration into development environments enhances workflow efficiency.
- Incremental Scans: The ability to perform incremental scans saves time and resources.
- Best Fix Location Feature: The Best Fix Location feature simplifies the process of identifying and resolving multiple vulnerabilities.
Cons:
- No Free Trial: This may limit the opportunity for users to explore the tool before committing to a subscription or purchase.
Request a Checkmarx SAST demo for FREE.
2. Synopsys Coverity
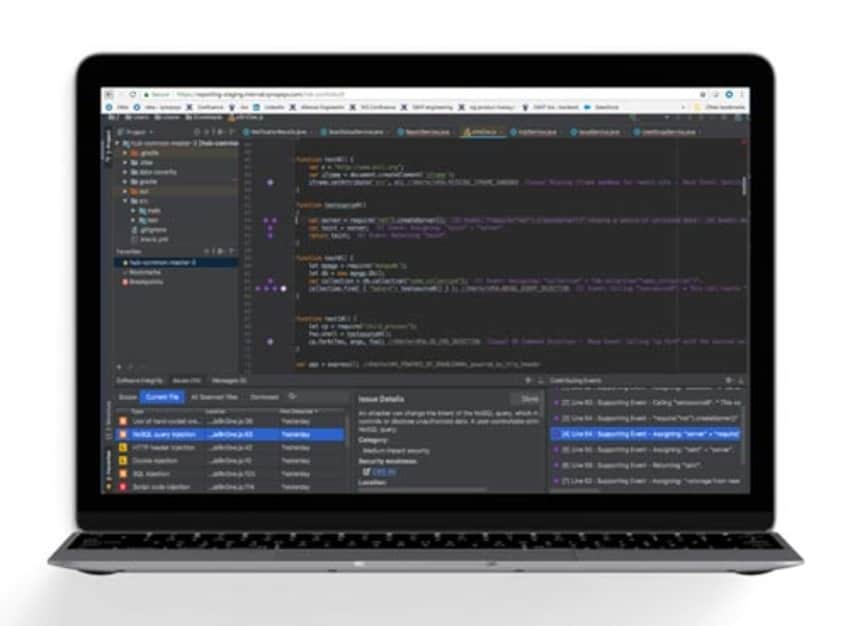
With Synopsys Coverity Static Analysis, developers can look forward to quickly finding and fixing bugs in their code. Coverity identifies critical software quality defects and security vulnerabilities in code and any lapses in industry compliance standards. It is an easy-to-use, accurate, and scalable tool that irons out bugs in the early stages of an SDLC.
When we tested Coverity Static Analysis we found the following key features.
Key Features:
- Out-of-the-Box Bug Spotting: Coverity can immediately start spotting and fixing bugs without requiring extensive tuning.
- Integration with DevOps Pipelines: Integrates well into Continuous Integration (CI) and Software Configuration Management (SCM) pipelines via REST APIs, enhancing DevOps workflows.
- Centralized Risk Profile: Offers a centralized aggregated risk profile of entire application portfolios, with APIs for exporting results to other risk reporting tools.
- Vulnerability Management: Developers can filter identified vulnerabilities, prioritize based on criticality, and manage security policy compliance across teams and projects.
- Code Sight IDE Plugin: Allows developers to find and fix security or quality issues in real-time as they write code within their Integrated Development Environments (IDEs).
- Real-Time and Incremental Analyses: Provides developers with real-time, accurate, and incremental analyses that run seamlessly in the background, helping them fix issues and secure their code.
- Trend Reports and Compliance Proof: Provides trend reports and severity level reports over time for analyzing project security status, which can be exported as proof of compliance during audits.
Why do we recommend it?
Synopsys Coverity integrates into development management systems, so you don’t have to launch the package manually. It will trigger automatically when developers move their new modules into the project repository for release.
Who is it recommended for?
As with the other tools on this list, Synopsys is intended for use in the Dev part of DevOps rather than by operations teams. This tool competes with the self-hosted SonarQube because it can be installed on Windows, macOS, and Linux. It also competes with Checkmarx because you can get the services on a subscription through the Synopsys SaaS platform.
During our testing, we identified the following pros and cons related to Coverity Static Analysis.
Pros:
- CI/CD and SCM Support: Useful for CI/CD pipelines and software configuration management, enhancing development workflows.
- Bug Spotter: Helps developers identify and fix bugs in development environments, improving code quality and security.
- Performance Analysis Reports: Offers performance analysis reports to monitor code performance and identify bottlenecks.
Cons:
- No Free Trial: The absence of a free trial may limit opportunities for users to evaluate the tool before committing to a subscription or purchase.
Schedule a Synopsys Coverity demo for FREE.
3. SonarQube
Tested on: Docker over Windows, macOS, Linux, and Azure

SonarQube is one of the more popular static code analysis tools out there. It is an open-source platform for continuous inspection of code quality and performs automatic reviews via static code analysis. In addition, it can detect and report bugs, code smells, and numerous other security vulnerabilities.
When we tested SonarQube we found the following key features.
Key Features:
- Integration with Multiple Platforms: SonarQube integrates seamlessly with various platforms, including GitHub, Azure DevOps, Bitbucket, GitLab, Docker Support, and coding IDEs like Eclipse, Visual Studio, Visual Studio Code, and IntelliJ IDEA.
- Support for Multiple Programming Languages: It supports over 25 programming languages, such as C#, Python, Cobol, PHP, and Java.
- Comprehensive Code Analysis: SonarQube helps developers identify and address bugs, security vulnerabilities, and code quality issues by providing insights into code errors, breaches, code updates, and adherence to coding standards.
- Classification of Issues: The tool classifies issues by severity, maps them to secure coding standards, and offers detailed documentation to facilitate the implementation of best practices.
- Reporting Features: SonarQube generates reports on duplicate code, coding standards violations, unit tests, code coverage, code complexity, and code comments, offering a comprehensive overview of code quality.

Why do we recommend it?
SonarQube provides a great deal of flexibility because you decide where to host the testing software. You can run it on Windows, macOS, or Linux and it is also possible to run it through Docker or on an Azure account. It is also able to integrate with a number of development platforms. Integration with bug trackers lets the tool return failed code for rework.
Who is it recommended for?
Like all of the static code testers on this list, SonarQube is intended for use by development teams and specifically for the development of Web applications. The ability to integrate the tool into code repository systems enables it to be positioned as a testing gatekeeper for verified program stores.
During our testing, we identified the following pros and cons related to SonarQube.
Pros:
- Self-Hosted Deployment Options: SonarQube can be deployed on-premises or on Azure, providing flexibility in hosting options.
- Effective Error Detection: It is highly effective in spotting coding errors, security vulnerabilities, and ensuring code quality.
- Continuous Testing: SonarQube can run as a continuous tester in CI/CD pipelines, enabling continuous code analysis and improvement.
- Application Security Testing: Offers Static Application Security Testing (SAST) capabilities to enhance application security.
Cons:
- Lack of Price Information: One potential drawback is the absence of clear pricing information, which may impact decision-making for organizations considering paid versions with enhanced features.
You can start a 14-day free trial.
4. Micro Focus Fortify Static Code Analyzer
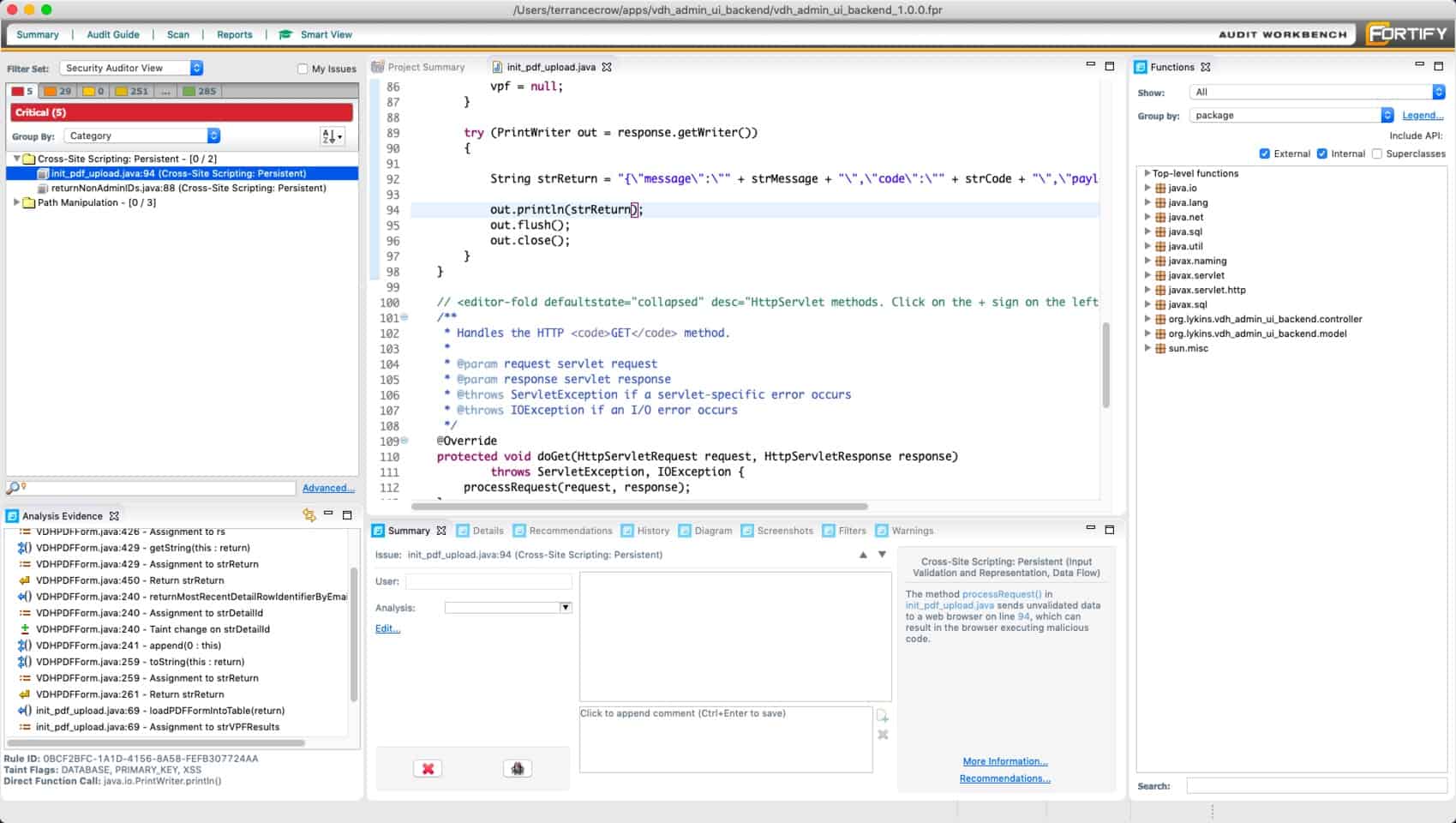
Micro Focus Fortify Static Code Analyzer (SCA) is a static code analysis tool that locates the root causes of security vulnerabilities in source code, prioritizes issues by severity, and provides detailed resolution guides on how to fix them.
This tool offers dynamic (DAST) application testing as well as source code analysis (SAST).
When we tested Fortify Static Code Analyzer we found the following key features.
Key Features:
- Real-Time Detection: Integrates into IDEs like Eclipse or Visual Studio to help developers find and fix security defects in real-time while they code.
- Secure Coding Training: Provides game-like training to help developers enhance their secure coding skills.
- Wide Language and Framework Support: Supports over 25 major programming languages and frameworks, ensuring compatibility with diverse development environments.
- Agile Updates: Offers agile updates backed by an in-house security research team to stay up-to-date with the latest security trends and vulnerabilities.
- Integration Capabilities: Integrates well with various solutions and platforms, including Visual Studio, Bamboo, GitHub, Jira, Slack, and SAP.
- Comprehensive Vulnerability Coverage: Covers over 800 vulnerability categories to help users comply with standards like CWE, DISA STIG, and PCI DSS.
- Detailed Analysis Results: Provides comprehensive analysis results that allow developers to drill into source code details and pinpoint complex security issues quickly.
- High Accuracy and Machine Learning: Achieves high accuracy rates and employs machine learning-assisted auditing to improve the effectiveness of security audits.
- Flexible Deployment Options: Offers multiple deployment modes, including on-premises, SaaS, or hybrid methods, to meet different business needs.
- Customization: Enables users to write custom rules, use templates, and create in-house report formats for better integration and meeting unique demands.
Why do we recommend it?
Micro Focus Fortify Static Code Analyzer is part of a platform of security testing services under the Fortify brand. The platform also offers a Static Code Analysis module and a DAST package. The service can be integrated into your CI/CD pipeline by API connectors into repository systems and bug trackers.
Who is it recommended for?
If you worry a little about the quality of your development team’s skills, you should prioritize the Fortify platform. It includes developer training services and also gives detailed fix instructions when the SAST tester routes programs back to coders for rework. This SaaS platform is a strong competitor for Checkmarx SAST.
During our testing, we identified the following pros and cons related to Fortify Static Code Analyzer.
Pros:
- Dynamic Analysis Tool Integration: Partners with a dynamic analysis tool for comprehensive security testing.
- Live Coding Advice: Provides live coding advice during development to help developers address security issues in real-time.
- Integration with Project Management Tools: Integrates seamlessly into project management tools and code repositories, enhancing workflow efficiency.
Cons:
- No Price List: The lack of a published price list may make it challenging for potential users to assess the cost of adopting the tool.
Try Micro Focus Fortify Static Code Analyzer (SCA) – FREE for 15 days.
5. Aikido
Tested on: Cloud

Aikido is a static application security testing (SAST) system. It is able to scan through any code as long as you own the program – it can’t scan compiled programs. This platform offers a range of security tools, not just SAST. It provides software composition analysis (SCA) and will operate as a cloud security posture management (CSPM) service for live systems.
Key Features:
- Code scanning that looks for Common Vulnerabilities and Exposures (CVEs): Checks through plain text code
- A risk score: An easy to understand score that is illustrated by a traffic-light-coded dial
- A risk assessment summary: Called the TL;DR
- A description of the error or risk: Explains how it will aid attacks
- An explanation of how to fix each discovered problem: A guide on what to recode

Why do we recommend it?
Aikido is a coding assurance system that uses a number of techniques to ensure that the systems that you developed in-house are not going to provide an open door for hackers. The service also looks for the use of open source packages that come from other locations and possibly act as a call to systems that are run on other servers.
This system is a code analyzer, so it isn’t going to be able to assess functions that are provided by third parties. This is a particular problem when frameworks, APIs, or third-party plug-ins are used. However, the service can ensure that the management team knows of the presence of these potential security loopholes.
The package will merge errors when they have the same source. So, for example, if a function with weak security is called several times in a program, Aikido sees that and doesn’t shove out a warning every time. Instead, it will generate one notification and list all of the locations where the weakness is present.
Some problems can be fixed automatically. Those that can’t will be described in notifications that can be sent to your development project management tool. The tester triggers a repeated scan of a given repository. So, when an update is saved, the tester will run automatically. This will examine whether the problem has been fixed. If a program is error-free, it is flagged for release.
Who is it recommended for?
The Aikido package works well for automated development testing. It kicks in automatically and scans any code that is checked into the repository that you register with the service. The functions of the package can be used for live Web applications. However, this tool excels when used for DevOps scenarios.
Pros:
- CI/CD pipeline automation: The tester will run automatically when new code is stored in a repository
- Vigilance for multiple repositories: The Free edition allows 10 repos and the top plan has no limits
- Software Composition Analysis (SCA): Looks for open-source content and details its risks
- Scans container images: Two for the Free plan and no limit for the top edition
Cons:
- Doesn’t assess third-party functions: Can only test the systems of which it can access the code
Aikido offers one free edition and three paid plans. The main difference between these packages is the volume of systems that the plan will test. There are some extra features in successively higher plans, such as the opportunities to customize tests and greater opportunities for analysis. However, all of the core functions, such as SCA, SAST, and integration with development project management systems are present in all plans. You can try it for free.
6. Veracode Static Analysis
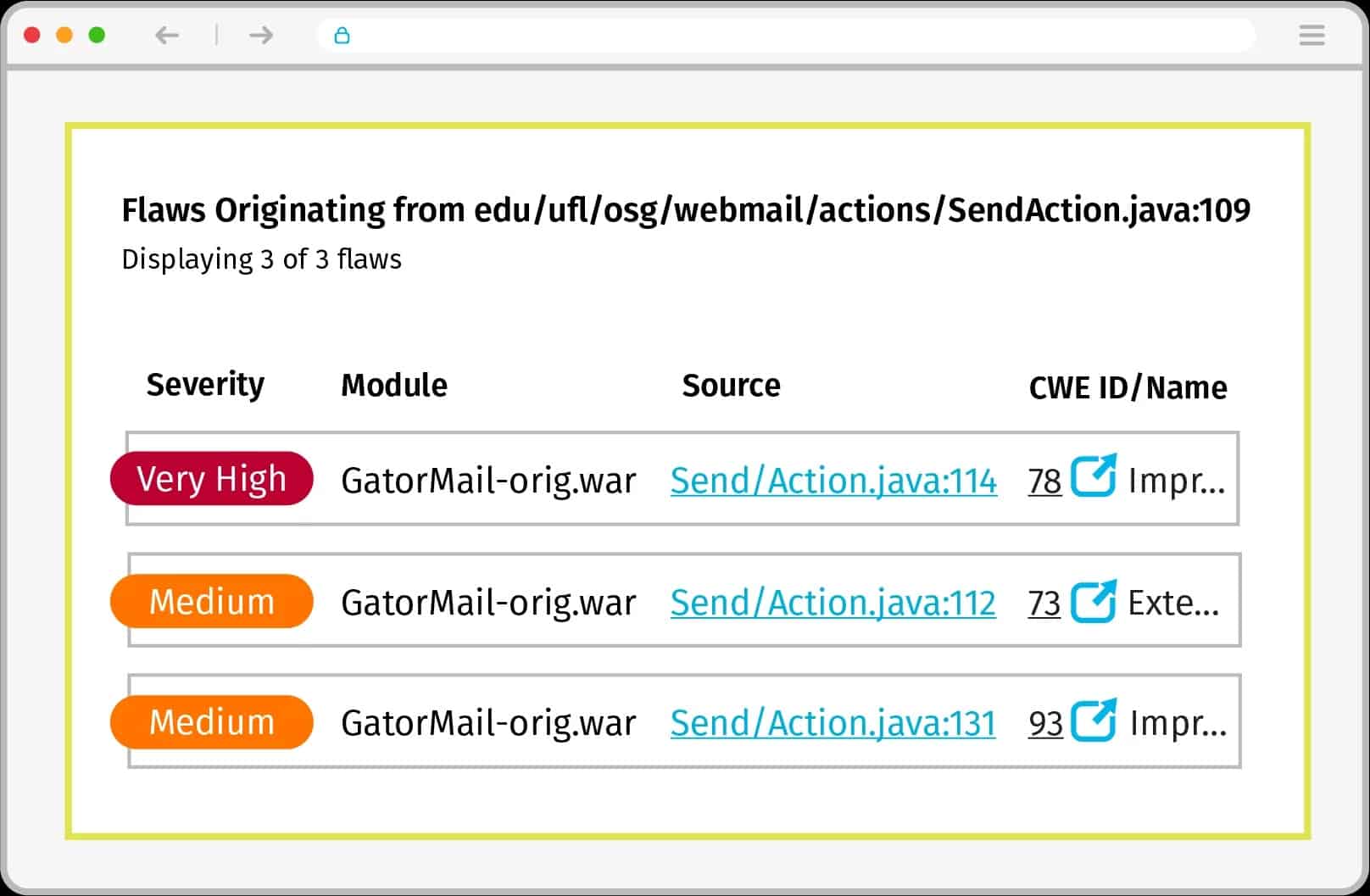
As its name suggests, Veracode Static Analysis is also a static code analysis tool that scans deployments thoroughly before they are released for production. In addition, it gives automated security feedback and guidance on resolving issues, so developers stay on top of their work and fix vulnerabilities quickly.
When we tested Veracode Static Analysis we found the following key features.
Key Features:
- Broad Language Coverage: Scans over 100 programming languages and frameworks, ensuring comprehensive analysis across your codebase.
- Fast and Accurate Scans: Leverages advanced algorithms to deliver quick and precise vulnerability detection with minimal false positives.
- Binary Code Analysis: Analyzes not just source code but also compiled binaries, offering a more complete security picture.
- Real-Time Feedback: Provides developers with immediate feedback on vulnerabilities within their IDEs, promoting early detection and remediation.
- Continuous Learning: Offers just-in-time training to developers for solving code bugs and improving coding practices.
- Efficient and Lightweight: Operates quickly with a light digital footprint, seamlessly integrating into development workflows without disrupting schedules.
- Integration Capabilities: Integrates seamlessly with IDEs, developer tools, and DevOps environments, offering over 30 out-of-the-box integrations and APIs for continuous scanning.
- Risk Assessment Reports: Generates comprehensive reports on the risk landscape with one click, suitable for analysis, audit, and compliance purposes.
Why do we recommend it?
Veracode Static Analysis is a SAST package for development teams. A distinctive feature of this tool is that it isn’t just available as a continuous tester for CI/CD pipelines but it is also accessible as an on demand tester. This enables the tool to be used in many other ways. For example, developers can test their own code as they go along and project managers can scan APIs and plug-ins for security weaknesses before adopting them for inclusion in the new code.
Who is it recommended for?
Veracode is a true DevOps tool. It is provided as a SaaS platform and it can scan code on demand, which means that it can be used as a vulnerability scanner by operations teams as well as providing continuous testing during code release.
During our testing, we identified the following pros and cons related to Veracode Static Analysis.
Pros:
- Reduced False Positives: Focuses on delivering accurate results, minimizing wasted time investigating non-existent threats.
- Faster Development Security: Enables early detection and fixing of vulnerabilities, saving time and resources in the long run.
- Complete Code Analysis: Scans both source and compiled code, providing a more thorough security assessment.
- Improved Developer Workflow: Integrates with developer tools and provides real-time feedback, fostering a security-conscious development environment
Cons:
- No Free Trial: The absence of a free trial may limit the ability of potential users to experience and evaluate the tool before making a purchase decision.
Schedule a Veracode Static Analysis demo for FREE.
7. Snyk Code
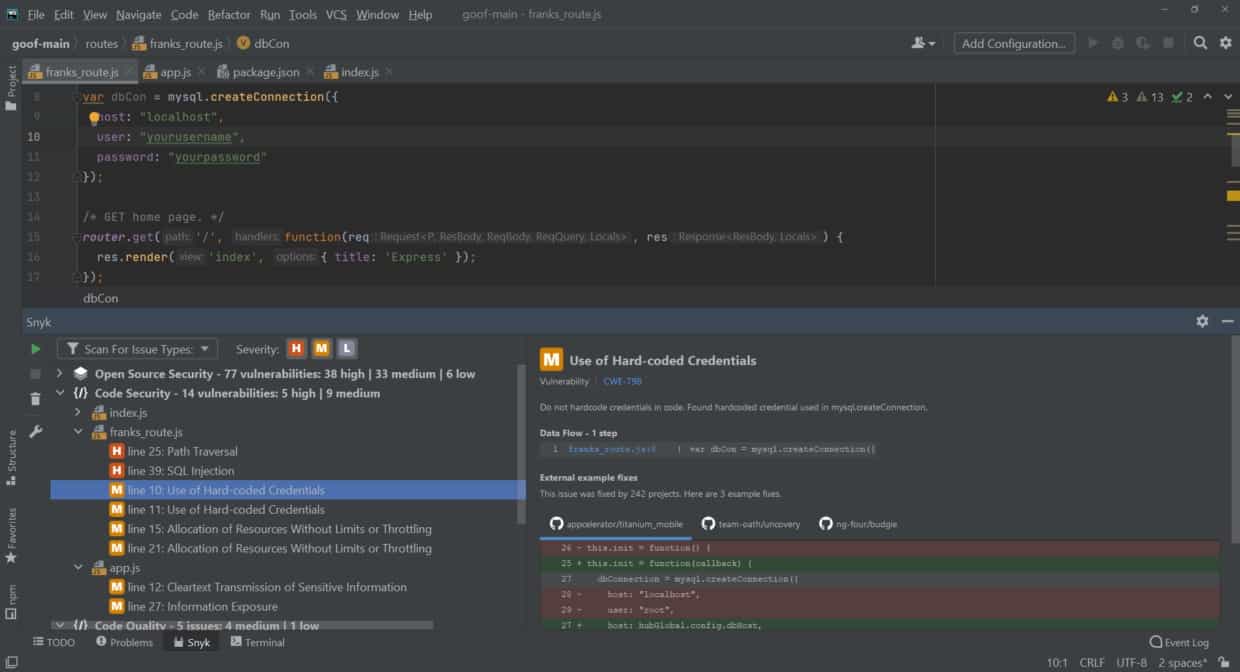
Snyk Code is a static code analysis tool that developers will find to be quick and effective. It boasts high scan speeds and uses semantic analysis to find more bugs and vulnerabilities – a combination that makes this tool very likable. It’s also FREE “for individual developers and small teams to secure while they build.”
When we tested SNYK Code we found the following key features.
Key Features:
- Static Code Analysis: Snyk Code performs static analysis of source code to identify security vulnerabilities, code smells, anti-patterns, and potential bugs across multiple programming languages.
- Language Support: Snyk Code supports a variety of programming languages including JavaScript, TypeScript, Python, Java, Go, Ruby, and more.
- Advanced AI and Machine Learning: Snyk Code leverages advanced AI and machine learning algorithms to analyze code patterns, detect vulnerabilities, and provide actionable insights into potential security risks and coding issues.
- Cloud Environment Compatibility: Snyk Code is designed for businesses and developers working in cloud computing environments and platforms like code, containers, Kubernetes, and Terraform.
- Integration and Compatibility: Easily integrates with popular applications, IDEs, programming languages, and platforms such as Visual Studio Code, Python, GitHub, JavaScript, and Docker
- Real-Time Scan Results: Provides scan results in real-time, boasting faster scanning times compared to similar solutions, making it efficient for developers.
Why do we recommend it?
Snyk Code is firmly identifiable as a development testing tool. It will integrate into IDEs so it can be launched by coders periodically during the creation of a new program. The system will also integrate into CI/CD pipelines in continuous testing mode. In both cases, the system provides detailed explanations of the security weaknesses that it discovers, providing tips for fixes.
Who is it recommended for?
Snyk Code is a close competitor for Veracode Static Analysis in its use for developers because of the detailed information that the testing results provide for programmers. Unlike Veracode, however, Snyk Code doesn’t support security testing for operations teams.
During our testing, we identified the following pros and cons related to Snyk Code.
Pros:
- Improved Security for Open-source Reliance: Offers robust open-source security analysis, crucial in today’s development landscape.
- Free Version Available: Offers a free version, allowing users to experience its capabilities before committing to a paid plan.
- Semantic Detection Methods: Utilizes semantic detection methods for effective vulnerability identification and mitigation.
- Container Inspection: Can examine inside containers to detect inappropriate use of environments, enhancing security in containerized environments.
Cons:
- No Self-Hosted Option: Lacks a self-hosted option, which may be a limitation for organizations preferring to host security solutions internally.
- Newer Player: While growing in popularity, Snyk Code may not have the same track record and extensive features as some established SAST solutions.
Try Snyk Code for FREE.
Advantages of using a static code analysis tool
We have just had a look at the six best static code analysis tools. Let’s now see why developers and businesses should adopt these solutions:
- With the help of SAST solutions, the development of applications becomes faster while applications become more secure and reliable.
- Businesses have their applications up and running in the shortest amount of time; they save time and money – and release more secure code on time – all factors that help their processes become more efficient.
- These tools help create better developers who develop code quickly and do it without making security risks or deviating from industry best practices.
- They also don’t waste time by having to retro-fit security into old code – they do it while it is being built; they have code insights before execution.
- SAST tools execute scans quickly when compared with dynamic analysis (DAST), for example.
- The search for bugs and code quality maintenance is automated, which quickly eliminates human error due to manual debugging.
Static vs. Dynamic code analysis
A point that needs to be addressed is why developers prefer to choose static code analysis tools (SAST) over dynamic (DAST).
For one, SAST tools debug the code as it is being created and before it is built. This makes it quicker and easier to clean the code. They also give developers educational feedback and the chance to fix the code themselves; this can serve as hands-on training.
DAST tools, on the other hand, fix the code by giving security teams quickly delivered improvements. But, unfortunately, they are comparatively resource-intensive and require more expertise to run.
Static code analysis tools are a must
Businesses and their developers should always have static code analysis tools integrated into their development process. It is the best way to turn code into applications that contribute to business processes without creating any risk.
Have you used any code analysis tool? Do you think we have missed one? Let us know; leave us a comment.
Static code analysis FAQs
What is static code analysis tools?
Static analysis scans through source code looking for coding errors or potential security weaknesses. The practice is also known as source code analysis. Traditionally, source code checking is the responsibility of the coder – it is expected that such mistakes should be corrected in order to sign off the coding job as complete. While testing is traditionally performed by running a program, source code analysis can be performed before a program has been completed, giving it the advantage of catching errors early. The use of static analysis for security weakness detection increased the importance of this field of QA and implementing the practice through automated tools removes human oversight and maximizes the efficiency of expensive human resources.
What do static analysis tools analyze?
Static analysis tools are useful for catching coding errors early. They can operate before unit testing is possible. Automated tools do not need to be limited to looking at the program in isolation but can highlight potential security issues that might arise once the code is implemented on specific operating systems or integrated into other applications.
Who typically uses static analysis tools?
Static analysis tools are used to identify coding errors and so they are particularly useful to programmers during the creation of a program
Unit testing and acceptance testing can identify procedural errors with programs by running them. However, using static analysis first with an automated tool can spot common errors quickly and recycle programs for correction before time-consuming system testing occurs.
Not every organization is security-conscious and a new application can gather sales despite the presence of security weaknesses. The use of static analysis tools during the assessment of a software bundle for acquisition can be a useful way to identify insecure systems before a business commits to buying it.
New vulnerabilities arise all the time and so a function that passed security testing at acquisition could provide weaknesses later, particularly when applied in new suites and environments. Static code integrated into operation procedures, such as within a vulnerability scanner, can spot new vulnerabilities in old code.