USBs are incredibly convenient for portable storage, but they aren’t very secure. To tackle this, we’ll be reviewing the best USB encryption software tools on the market today. Let’s get started.
Here’s a quick rundown of our top picks for the best USB encryption software tools:
- VeraCrypt EDITOR’S CHOICE This service encrypts USB devices, entire hard drives, and virtual containers and it provides a very strong encryption cipher. The greatest attribute of this system is that it is free to use and it lets the USB attach to Windows, macOS, Linux, and Unix.
- Endpoint Protector by CoSoSys Offers a unique way for administrators to manage and secure USB devices and ensure that encrypted data is protected during transit
- Microsoft BitLocker To Go The tool allows users to quickly encrypt both USB devices and standard hard drives with operating systems installed
- Sophos SafeGuard Encryption Drive encryption across the network, securing both flash drives and desktop machines through the same platform
- Rohos Mini Drive A lightweight USB encryption tool that can protect both flash drives and entire or single partitions
- SecurStick Αllows users to encrypt and hide data on USB drives through a unique browser-based interface
What does encryption do?
At a high level, encryption secures your data by scrambling in an unreadable way to anyone who doesn’t possess the private key (password).In addition, robust encryption algorithms protect the data from being brute-forced. This is where an attacker tries thousands of different passwords each minute to guess the right one.
Even with the worlds fastest supercomputers cracking strong encryption like AES-256 would take 2.29*10^32 years (over one billion years!). As you can imagine, this is incredibly valuable for those who need to protect important data such as financial records, password vaults, and identity information.
Encryption can protect our traffic over the internet and our computer hard drives and portable USB drives. We often don’t think about protecting our USB drives, but losing one having one stolen could prove disastrous depending on what it contained.
Some encryption methods also offer a recovery phrase or key. This is often a password or long string of random words that you can input to retrieve your password. If this recovery key is lost, you may be locked out of your data for good. Since encryption mathematically secures data, it can be impossible to break back into an encrypted drive.
Now what we know a little bit about how encryption works and its benefits, let’s explore exactly what you should look for in a USB encryption software tool.
What should I look for in USB encryption software?
The benefits of USB encryption are pretty straightforward, but what are the exact features you should keep an eye out for? First, let’s briefly go over some key features.
Encryption Strength
The type of encryption used is arguably the most critical aspect of a secure USB encryption software tool. Over time, encryption strength has evolved to keep data secure. Unfortunately, older, less complicated encryption algorithms can be cracked by modern-day machines, making them less safe.
Some encryption algorithms such as SHA-1, MD2, MD4, MD5, and DES/3DES are all examples of depreciated encryption methods. Programs using these methods for encryption present a severe security risk to your data. In some cases, modern processing can crack weak encryption, while some algorithms have inherent flaws that make them vulnerable.
All encryption software tools on this list use only robust encryption methods.
Ease Of Use
Good USB encryption software should be easy to use for both technical and non-technical users. However, complex tools sometimes require administrative rights, decompiling, or a steep learning curve to encrypt your drive.
The tools we chose on this list reflect a solid middle ground, allowing non-technical users to quickly understand the software without neglecting technical users who want to customize their encryption process.
Availability
Not all tools are designed for every operating system. Make a note of what operating systems you use, and make sure the tool you pick is compatible with your environment. For example, BitLocker is a USB encryption software tool but only works on a Windows operating system. Users who work off of multiple operating systems will likely want a USB encryption tool that is cross-platform.
It’s also important to note that your USB encryption software should come from a trusted source or is part of an open-source project. This gives you peace of mind that there are no backdoors created during your encryption process.
With that said, let’s look at our top picks for the best USB encryption software tools.
The Best USB Encryption Tools
Our methodology for selecting USB encryption tools
We reviewed the market for security systems that encrypt USB drives and analyzed the options based on the following criteria:
- Strong encryption
- Password protection that automatically decrypts the encryption protecting the device
- An encryption system that allows the USB to attach to many operating systems
- A system that anyone can understand and use
- A portable package that will be resident on the USB device
- A free trial or a demo that enables a no-cost assessment or a free tool
- Value for money from a reliable USB encryption service that is offered at a fair price
1. VeraCrypt
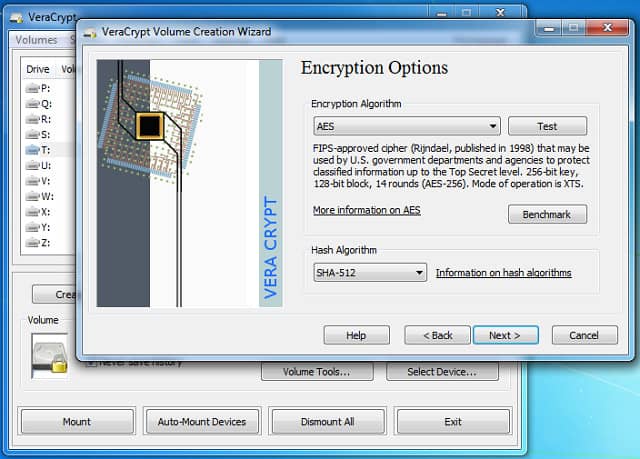
VeraCrypt is the successor to the once-popular TrueCrypt and offers flexible encryption options in an easy-to-use interface. While other tools only offer USB encryption, VeraCrypt can encrypt USB devices, entire hard drives, and virtual containers.
Key Features:
- Free to use: No charge
- Multiple OSs: Available for Windows, macOS, and Linux
- Secure vault: creates a file on the device for the encrypted vault
- Full drive or partial: Encrypt an entire USB stick or just part of the space
- Virtualization: The vault acts like a backup – it is a virtual disk but you can access it to see individual files
Why do we recommend it?
VeraCrypt can create an encrypted vault for files on a hard disk or it can encrypt an entire USB drive. Users don’t have to move files in and out of the vault. To the user, files appear as though they are not encrypted but outsiders can’t access them.
VeryaCrypt uses multiple robust encryption methods that you can choose from, including Serpent, Twofish, Camellia, and AES. This is paired with various strong hashing algorithms such as SHA-256/512, Whirlpool, Streebog, and RIPEMD-160.
Mounting and unmounting volumes are straightforward and require little to no training. In addition, users can quickly encrypt multiple flash drives in a short amount of time if needed for the various staff or entire departments.
A unique feature that I enjoy in VertaCrypt is its “plausibility deniability” options. These options allow you to create hidden volumes within a volume that you can access with a specific password.
For example, an extortionist forces you to unlock your encrypted drive. With the hidden volume function, you can comply and enter your password into a “dummy” container with bogus files and information. A similar secret operating system feature allows you to do the same, only for an entire operating system.
VeraCrypt is available in multiple language packs and works cross-platform for operating systems such as Linux, Windows, FreeBSD, and macOS. Security professionals can verify the integrity of VeraCrypt by examining its source code and checking its PGP signature.
It’s not often that you get a USB encryption tool that blends ease of use with as many powerful features that VeraCrypt does.
Who is it recommended for?
VeraCrypt is a free tool and it is a good choice for home use. One problem for businesses is that the tool has to be installed on each computer that will access the encrypted USB. However, small businesses could use it. The software installs on Windows, macOS, Linux, Unix, and Raspberry Pi.
Pros:
- Hidden vault: Provides an option to hide the vault
- Live operations: Access files directly from the vault without having to decompress or copy them
- Saves updates: Make changes to files in the vault and the tool will update the stored file
- Containerization: The vault acts like a container
- Password protection: Requires a password to verify authorization to access the vault
Cons:
- Requires a management console: You can only access the files in the USB vault through a utility that needs to be installed on an endpoint
EDITOR'S CHOICE
VeraCrypt is our top pick for a USB encryption tool because as an open-source encryption solution, VeraCrypt is freely available and continuously audited by the security community, ensuring transparency and trust. It offers strong encryption algorithms, including AES, Serpent, and Twofish, providing top-tier protection for your sensitive data. One of the key reasons for selecting VeraCrypt is its full disk encryption capabilities, which allow users to encrypt entire USB drives or create secure, encrypted volumes within the drive. This provides an added layer of security, ensuring that your data remains protected even if the USB drive is lost or stolen. Additionally, VeraCrypt allows for hidden volumes within the encrypted container, offering plausible deniability in case of forced disclosure. VeraCrypt also offers cross-platform support for Windows, macOS, and Linux, making it a versatile tool for users across different operating systems. The user-friendly interface and detailed step-by-step setup guide make it easy for both beginners and experienced users to encrypt USB drives without requiring advanced technical knowledge. The software also supports automated encryption/decryption and integrates seamlessly with your USB device, meaning encryption won’t interfere with regular usage. Combined with its strong encryption standards and zero-cost offering, VeraCrypt is the best choice for securing USB drives, ensuring your data remains safe wherever it goes.
OS: Windows, Linux, macOS, and Unix
2. Endpoint Protector by CoSoSys
Endpoint Protector by CoSoSys offers a unique way for administrators to manage and secure USB devices and ensure that encrypted data is protected during transit. For sysadmins looking for a way to quickly enforce USB encryption across the network, Endpoint Protector is the answer.
Key Features:
- Allowlisting: Blocks all software from running on an endpoint except those that have been authorized
- File protection: Creates an encrypted container around each file
- Access rights management: Set up ARM records that only allow specific access permissions to named users through a particular application
- Link file access to applications: Set up an associated so only specific applications can break through the encryption protection for a specific file
Why do we recommend it?
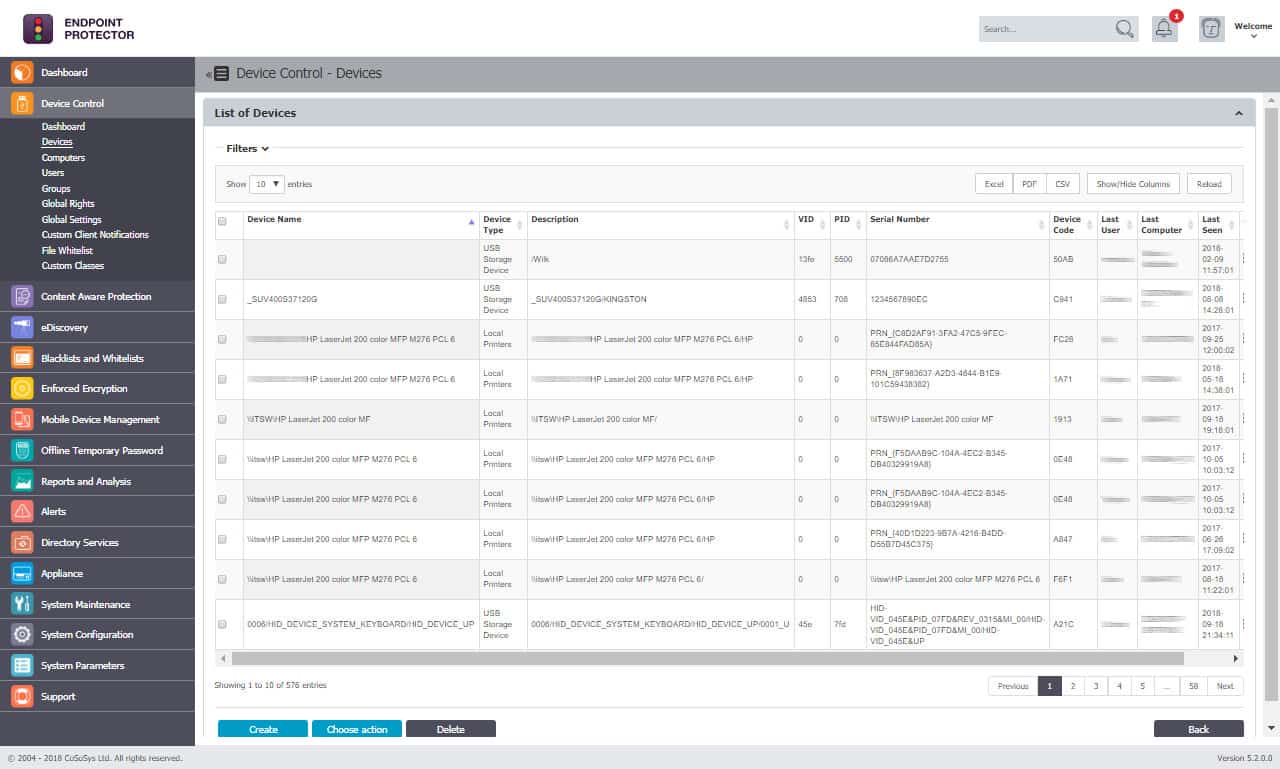
Endpoint Protector by CoSoSys is an endpoint protection system that includes an extension for USB management. This service blocks all USB ports by default. An administrator can access all devices on the network from a central console and approve specific USB devices for use. The tool will also encrypt USB devices.
You can think of Endpoint Protector as an extended device control policy with an emphasis on enforcing encryption. The configurable policies allow you to ensure that any confidential data is only moved to storage devices containing adequate protection. In addition, data transferred from the network is automatically encrypted by default, ensuring that the information is secure while in transit and at rest.
For those looking to integrate USB encryption with a Data Loss Prevention (DLP) solution, Endpoint Protector is a clear winner. Unlike other solutions that require you to purchase specific USB hardware, the platform allows admins to push out “EasyLock” to any USB devices that need encryption.
Endpoint Protector is great for teams that are looking to maintain compliance while moving data. Forcing encryption across portable devices makes it easy to comply with HIPAA, PCI DSS, and SOX standards. In addition, endpoint Protector is cross-platform, allowing it to be used across Windows, Linux, and Mac operating systems.
Pricing for Endpoint Protector depends on your organization’s size. However, you can request a demo to see it in action for yourself.
Who is it recommended for?
This system installs on each endpoint but communicates with a ventral controller. Therefore, it is a good choice for mid-sized and large organizations that operate a central IT asset management department for all hardware. The system can also operate across the internet to manage devices on multiple sites.
Pros:
- Enforces data security standards: PCI DSS, SOX, HIPAA
- Multiple OSs: Windows, macOS, and Linux
- Enforced encryption: Encrypts and password protects USB devices
- USB approval: Only specifically approved USB sticks can connect to endpoints in the company
Cons:
- Limited functionality for Linux: Endpoints running Linux can’t be used to implement USB encryption
3. Microsoft BitLocker To Go
For Windows users, USB encryption might already be a part of your operating system. The tool allows users to quickly encrypt both USB devices and standard hard drives with operating systems installed. For example, BitLocker is already installed and available for Pro, Enterprise, and Education editions of Windows 10 and the Pro and Enterprise versions of Windows 8/8.1.
Key Features:
- Free to use: Supplied by Microsoft
- Encrypts attached device: Secures USB sticks, SD cards, and external hard drives
- Password protection: Only those with the password can get into the encrypted device
Why do we recommend it?
Microsoft BitLocker To Go is able to encrypt USB drives, SD cards, and external hard disks. This service is free and included in the Windows operating system. It doesn’t have a remote operation facility, so the encryption mechanism has to be operated locally on the computer into which the USB device is inserted.
Bitlocker is very easy to use. Simply choose a drive, set a password, and your drive will be encrypted in a few seconds. USB devices can be secured through AES-256 encryption and offer both a GUI and PowerShell option to perform the encryption.
For companies that use smart cards for security or compliance, Bitlocker supports intelligent card technology. Simply insert the smart card during the encryption process and enter your pin to access the drive. In addition, Microsoft BitLocker To Go is an excellent option for Windows users who want to install or pay for additional software.
Bitlocker passwords can be recovered through an automatically generated key if you forget your password. This recovery key can be saved to a file or synced with your Microsoft account.
For those who live in the MacOS world, FileVault is the equivalent of Bitlocker. FileVault offers similar USB drive encryption built directly into the operating system with no additional downloads or installs needed.
Who is it recommended for?
This tool is a good option for home users and small businesses. The lack of a remote management option means that it wouldn’t work well for businesses that operate central IT support departments. The service has a few security weaknesses if outsiders can access the hosting computer.
Pros:
- Transactional encryption management: The encryption process is invisible to the user and files are accessed in the same way as though they were not encrypted
- Strong encryption: Uses 256-bit AES encryption
- Provides a recovery key: Provides forgotten passwords
Cons:
- Windows only: Not available for macOS or Linux
4. Sophos SafeGuard Encryption
Sophos SafeGuard Encryption takes a business-focused approach to drive encryption, compliance, and secure file sharing. Administrators can deploy drive encryption across the network, securing both flash drives and desktop machines through the same platform.
Key Features:
- Centrally managed: A networked solution
- Disk encryption: For Windows, macOS, and USB sticks
- Self-service password recovery: Users don’t need to bother the Help Desk
Why do we recommend it?
Sophos SafeGuard Encryption is a USB device security system that can be managed centrally by an administrator. This tool is also suitable for encrypting endpoint disks for devices running Windows and macOS. Although the encryption is centrally managed, users can recover passwords through a self-service portal.
The centralized dashboard allows users to manage encrypted devices and provides visibility into which devices are or aren’t encrypted. This same visibility also makes it easy to run built-in reports to prove compliance with standards such as HIPPA or PCI-DSS.
A notable feature that will save sysadmins a ton of time is their self-service portal. This allows users to regain access to their devices if they forget a password. In addition, by authenticating each user, the staff member can retrieve a recovery key and decrypt their USB or computer without putting in a helpdesk ticket.
For desktops, the platform leverages Bitlocker for Windows and FileVault for Mac to perform full disk encryption. This may be a problem for companies running the standard version of Windows. All in all, Sophos SafeGuard Encryption provides a convenient way to encrypt USB drives, manage compliance reporting, and allow users to recover their passwords.
You can test out SafeGuard Encryption through a free trial.
Who is it recommended for?
Sophos targets its products at mid-sized businesses but this product would also be a good choice for large organizations. Small businesses with few endpoints might not need such as sophisticated tool and could try this tool or opt for a free USB encryption system. The cloud-based package interacts with BitLocker on Windows and FileVault on macOS.
Pros:
- Data protection standard compliance: For HIPAA and PCI DSS
- Windows and macOS encryption: Users BitLocker for Windows and FileVault for macOS
- File protection: Option to protect individual files as well as entire drives
Cons:
- Windows and macOS: Not available for Linux
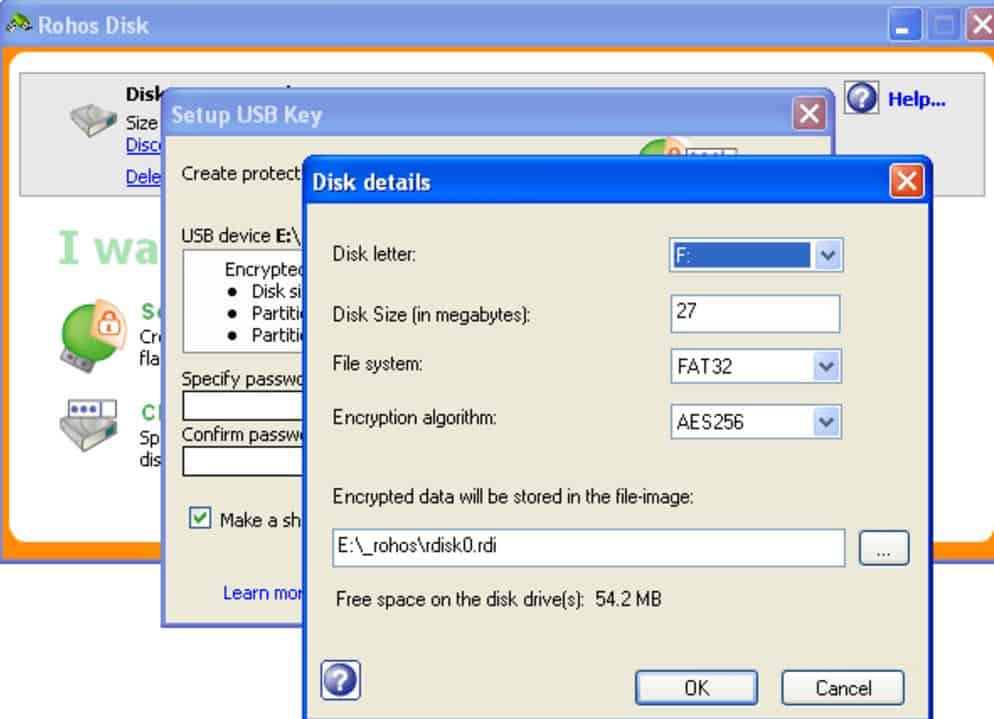
5. Rohos Mini Drive
Rohos Mini Drive is a lightweight USB encryption tool that can protect both flash drives and entire or single partitions. The tool is easy to use and comes with numerous quality-of-life features great for non-technical users.
Key Features:
- Strong encryption: Applies 256-bit AES encryption
- Access interface: Comes with an access interface that is styled like Windows Explorer
- Password protection: A user would need a password to access the USB
Why do we recommend it?
Rohos Mini Drive is available in a version for Windows, which encrypts USB drives, and a portable edition to encrypt a drive on a Windows PC. When this program is running on your PC, it will detect the presence of a new USB and prompt you to enter a password. That grants access or sets up a new device.
Simply plug in the USB drive you’re looking to encrypt, and Rohos Mini Drive will automatically detect it and suggest the best settings. This is great for users who aren’t sure which encryption method they want to use or how big their encrypted volume should be. Of course, all settings are customizable, but seeing how Rohos automatically chooses for you makes it a good product for casual use.
The tool is highly visual and allows you to create backups easily, encrypt USB drives, and set up authentication keys through easy-to-follow wizards. A notable feature of Rohos is its ability to obfuscate encrypted containers within other formats. For example, you can hide your encrypted container in media formats such as Mp4 or Mp3. While this might seem like a feature only needed for the paranoid, this helps protect your files if a virus actively seeks out known encrypted file formats to steal in hopes of opening them.
Who is it recommended for?
This tool is freeware. It is great for home use and for small businesses. There is no central control for USB devices, so this wouldn’t be a good choice for large companies, in fact, it could facilitate the theft of data by employees.
Pros:
- Invisible operations: Once unblocked, the vault acts like any normal drive
- Instant access: You don’t need to unzip files to access them
- Steganography: Hide the vault as an image format file
Cons:
- Only available for Windows: Won’t run on macOS or Linux
Rohos Mini Drive is free to use and you can download the executable for Windows.
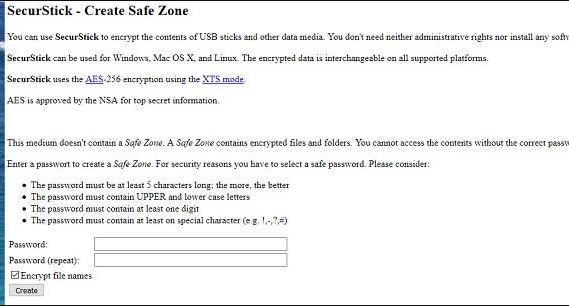
6. SecurStick
SecurStick allows users to encrypt and hide data on USB drives through a unique browser-based interface. In addition, SecurStick is highly portable and doesn’t require administrator rights, making it great for accessing files on machines other than your own.
Key Features:
- Free tool: Not a free trial
- Password-protected vault: Doesn’t need to occupy the entire drive
- Multiple OS: Available for Windows and macOS
Why do we recommend it?
SecurStick is a free tool that will encrypt USB drives from its installation on Windows, macOS, or Linux. The service is straightforward and has a small footprint. However, it is able to implement AES-256 encryption, which is the strongest cipher available. The tool doesn’t have a user guide.
Simply run the program from the USB stick and enter your password to access your files and encryption options. Then, copy and paste the files you wish to protect over to your flash drive, and they are automatically encrypted. Since SecurStick doesn’t require installation, it can run on virtually any operating system.
SecurStick is simple but limits what you can customize about the program. For example, the program creates “zones” to move files to and from, with safe zones representing the encrypted drive. From a usability perspective, SecurStick is rough around the edges. For example, it uses rudimentary HTML to display your password field and other options to interact with your data.
While it might not be as sleek as some competing tools, its versatility, portability, and low free price secure its place on our list.
You can download SecurStick for free.
Who is it recommended for?
This system is good for home use and small businesses. It isn’t possible to install or manage this tool from a remote location, so it wouldn’t be suitable for large businesses with central IT support departments. There also isn’t any central control over whether to allow USB devices to attach.
Pros:
- Creates a hidden folder: Outsiders won’t know the vault is there
- Portable: The encryptor installs an access interface on the USB stick
- Strong encryption: Uses 256-bit AES encryption
Cons:
- A bit clunky: Difficult to work out how to use because there is no user guide
Conclusion
We covered some of the best USB encryption software tools, but which is best for you? VeraCrypt will offer the best balance of usability and customizable features to satisfy both casual and technical users in almost all cases.
Sysadmin looking to encrypt USBs and enforce their encryption will find Endpoint Protector to be the best tool for the job. Endpoint Protector ensures drives are automatically encrypted and protects data in transit, and provides compliance reporting.
Do you encrypt your flash drives? If so, what programs do you use? Let us know in the comments down below.