Unrestricted USB ports are a massive security risk for any environment. Whether you’re trying to prevent infection or data theft, reliably locking down USB access without preventing legitimate work can seem impossible.
We tested and reviewed seven of the best USB lockdown software tools to help sysadmin balance security and productivity in their environment. Let’s get started.
Here’s our list of the best USB lockdown tools:
- ThreatLocker Storage Control EDITOR’S CHOICE This cloud-based device control tool implements USB device blocking that can be selectively lifted on request for specific users. Access a demo to assess this service.
- Endpoint Protector by CoSoSys (GET DEMO) Robust enterprise device control solution. Access the free demo.
- ManageEngine Device Control Plus (FREE TRIAL) Offers comprehensive USB lockdown with scalable device control features. Start a 30-day free trial.
- USB Lock RP Uses lightweight agents and supports legacy environments.
- DriveLock Offers device control through a sleek minimalist design with end-user training.
- DeviceLock Offers device control and DLP that can identify advanced data theft by reading text from images.
- Safetica Uses behavioral analysis to identify insider threats while pushing out device control policies.
How does USB lockdown software work?
USB lockdown software (also known as device control) stops unauthorized or unknown devices from interacting with endpoints that contain sensitive data. This approach uses endpoint security agents to monitor the environment, enforce policies, and record what data has been moved, if any.
This management allows the sysadmin to scale their device policies and protect endpoints from insider threats, data theft, and BadUSB. In addition, USB lockdown software often does more than just restrict access to USB ports, which is good news for administrators.
Robust device control solutions will offer USB lockdown software as an option and provide sysadmin with more granular control. Device whitelisting, transfer limits, one-time passwords, and encryption are just a few of the features offered by enterprise device control.
Organizations can leverage this technology to protect themselves from accidental or malicious data loss and build data protection workflows that adhere to specific security standards such as PCI DSS, FISA, or HIPAA.
What is Device Control?
Device Control is the act of controlling what kind of hardware is allowed to interact with your managed endpoints. Device Control encompasses all devices, including USB ports. Many platforms offer USB lockdown as a part of their device control solution so that you may hear the two terms used interchangeably. However, if you’re looking for a specific feature such as timed delay USB access, it’s important to specifically ask the vendor if their device control solution supports it.
What should I look for in USB lockdown software?
Control Features
USB lockdown software should have plenty of options for administrators to restrict access rather than a single on or off switch. In reality, people need to get work done. A USB lockdown software that denies staff access to their work materials won’t last long. Having granular control in place allows administrators to implement layers of security that reduce risk while allowing staff to remain productive.
Options for mandatory encryption, time restrictions, and configurable policies are essential for a successful device control policy. Start with your goal in mind and identify the features you’ll need to carry out that goal. For instance, mandatory encryption can help staff move data protected by compliance regulations, while time restrictions can prevent after-hours data theft and restrict BYOD environments.
Lastly, identify tools that have configurable levels of permissions or groups. For instance, a USB lockdown software that continuously prevents the CEO from accessing files would be frustrating. Instead, by integrating with systems such as Active Directory, sysadmins can use their existing permission architecture to build a solid but flexible USB lockdown policy that suits their needs.
Visibility
Device Control software should give administrators an overview of their protected devices and log what data has been moved and by whom. When the data transfer is authorized, keeping track of who accessed it and where it can be vital to investigate a data theft incident or fraud. Ensure your solution can log these actions in case an investigation requires this information.
Visibility also helps sysadmin understand their environment and how protected each endpoint is. For example, many USB lockdown software tools have centralized consoles that overview compliant machines, whitelisted devices, and possible issues. This visibility helps organizations scale their device control efforts by assigning NOC teams to handle problems or input this data into a SIEM for the historical record.
Integration
While most USB lockdown software works as a standalone solution, having the option to share insights between platforms is essential for long-term success. For instance, having a device control platform with a robust API library allows an organization to scale alerts to a ticket system down the road. Integrations also help keep team members in the loop. For example, a flexible integration may allow instances of confirmed data theft to notify NOC teams and a manager via text immediately.
These same integrations can sometimes also support automated scripting. If the device control platform doesn’t support automated response, often, an integration can enable automatic actions such as locking a user account or quarantining a machine from the network.
Our methodology for selecting a USB lockdown tool:
We reviewed the market for the best USB lockdown tools based on the following criteria:
- Security Features and Effectiveness: We considered the robustness of the security features offered, such as the ability to block all unauthorized USB devices, monitor and log device usage, and enforce strict data transfer policies. Tools that provide granular control over device access and data transfer received higher recommendations due to their effectiveness in preventing data leakage and ensuring compliance with data protection regulations.
- Ease of Use and Management: Tools that feature an intuitive user interface and straightforward management capabilities are prioritized. This includes the simplicity of setting up the software, the ease of configuring policies, and the overall user experience in daily operations.
- Compliance and Auditing Capabilities: For many organizations, particularly those in regulated industries, the ability to comply with legal and regulatory requirements is crucial. USB lockdown tools that provide comprehensive auditing capabilities, such as detailed logs of all device interactions and data movements, help businesses meet stringent compliance standards.
- Flexibility and Customization: The ability to customize the tool according to specific organizational needs is another important factor we considered. This includes customizing which devices are allowed, setting specific user permissions, and tailoring the security measures to fit different scenarios or requirements within the organization.
- Integration with Existing Systems: Compatibility and the ability to integrate seamlessly with existing IT infrastructure, including other security solutions and systems, enhance the value of a USB lockdown tool. Integration helps in creating a cohesive security posture without disrupting existing workflows.
- Scalability: The chosen tools must be able to scale with the organization’s growth. This means they should be capable of handling an increasing number of devices and data traffic without a significant performance drop. This makes them suitable for both small businesses and large enterprises.
- Support and Reliability: Reliable customer support and regular updates from the vendor are essential to ensure that the software continues to protect against the latest threats and operates smoothly. Vendors that provide excellent ongoing support and software updates are often recommended.
The best USB Lockdown software
With these critical features covered, let’s examine some of the best USB lockdown software tools on the market today.
1. ThreatLocker (GET FREE DEMO)
ThreatLocker Storage Control discovers all USB ports on a computer and then blocks them. This system is based in the cloud and you can use the platform to protect endpoints from malware. The Storage Control module is aimed at data loss prevention.
Key Features:
- Blocks by Default: ThreatLocker operates on a default-deny model, meaning it blocks all unauthorized activities by default.
- Administrator Allows Devices: Administrators can allow specific devices, such as USB drives, based on policies and user permissions.
- Identifies USBs by Serial Number: The system can identify USB devices based on their unique serial numbers, enhancing security.
- Implements DLP: ThreatLocker includes Data Loss Prevention features to prevent sensitive data from leaving the organization.
- Application Execution Controls: ThreatLocker includes controls to manage and monitor application execution, enhancing overall security posture.
Why do we recommend it?
ThreatLocker Storage Control takes into account that sometimes administrators can forget to implement controls or that some computers get missed out of a list of systems to secure. This system blocks all USB devices by default. Users can appeal to get a device approved if they find their USB stick has been left off the list.
The full ThreatLocker system blocks all software packages from running on a protected endpoint. The administrator then assembles an allowlist and those permitted applications are then allowed to run. This strategy automatically prevents malware from running and it also blocks users from installing and using their own favorite software on company computers.
The applications that are permitted to execute are further controlled by a system that prevents them from accessing computer resources. The resources to which the administrator decides to grant the application access can then be specified.
The Storage Control module also blocks CDROMs and external disks and then enables an allowlist for these devices. This permission only allows a specific user to use the USB stick and the right can be revoked at any time. This strategy means that users are made aware that the ability to use USB storage is a very rare event.
The ThreatLocker system logs all file access events whether they are on USB, CDROM, or a fixed disk. This is a great feature for auditing and the generated log messages can be channeled through to a SIEM tool.
Who is it recommended for?
This system is part of a wider “allowlisting” strategy of ThreatLocker that is applied to file access. Everything is blocked by default and that stops slip ups from letting data out of the business. This is a lockdown mechanism that is the most effective insurance possible for businesses that manage sensitive data.
Pros:
- Simplified Strategy for Dealing with Malware: Blocking by default and requiring explicit permissions, ThreatLocker simplifies the strategy for dealing with malware and unauthorized access.
- Choice of Scope: Users have the flexibility to define the scope of permissions and restrictions based on their security needs.
- Granular USB Device Permissions: Permission to use a specific USB device is granted only to named users, reducing the risk of unauthorized data transfers.
- File Access Logging: Access to files on disks is logged, providing visibility into file activities and potential security incidents.
- USB Storage Activity Recording: All file movement to and from USB storage is recorded, helping to track data transfers and detect suspicious activities.
Cons:
- No Access Rights Manager: One notable drawback is that ThreatLocker doesn’t include an access rights manager, which could limit the granularity of permissions management in certain scenarios.
You can assess ThreatLocker by accessing a demo.
EDITOR'S CHOICE
ThreatLocker Storage Control is our top pick for a USB lockdown tool because it starts off with a complete ban on any storage device attaching to a port. Once that ban is in effect, it is possible for an administrator to lift that lock for a specific user and the administrator can choose to notify the user that the accessibility of the USB device will only last for a limited time. All file movements on and off the USB device are logged for auditing and threat hunting. It doesn’t matter if the USB stick is infected because another module in the ThreatLocker package blocks any software from running on the protected computer. Only trusted applications can be granted an exception to that ban.
Download: Access FREE Demo
Official Site: https://threatlocker.com/demo-sign-up
OS: Cloud-based
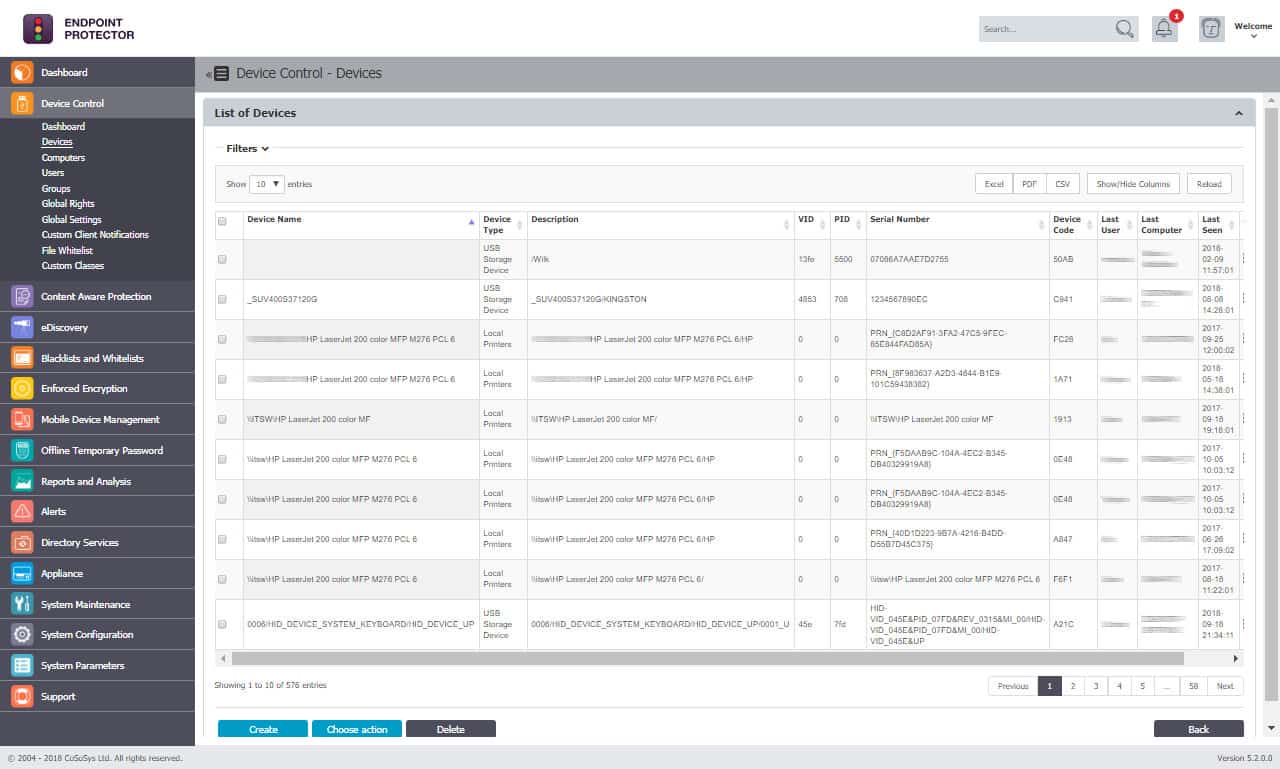
2. Endpoint Protector by CoSoSys (GET DEMO)
Endpoint Protector is an industry-leading DLP platform that provides cross-platform protection. The brand focuses heavily on controlling sensitive data transfer, storage, and recovery with detailed USB lockdown options.
Key Features:
- Blocks All Devices by Default: Endpoint Protector follows a default-deny approach, blocking all devices by default to prevent unauthorized access.
- Controls Bluetooth Devices: In addition to USB and other external devices, Endpoint Protector also provides control over Bluetooth devices, enhancing overall device security.
- Blocks Malware Transfers: The solution is designed to block malware transfers, reducing the risk of malware infections through removable devices.
- DLP Functionality: The solution acts as a Data Loss Prevention (DLP) solution by alerting to improper file access or insider threats, enhancing data protection.
Why do we recommend it?
Endpoint Protector Device Control is an extensive data loss prevention tool that forms part of a wider DLP service. Like the ThreatProtector service, this system blocks all devices and then an administrator approves it by serial number. This service can authorize devices for use by specific users to move specific categories of data.
It can be challenging to start over with a zero-trust policy for device control in large busy environments. Therefore, when taking a whitelist approach, it’s essential to have various options from which to build your trusted list.
Endpoint Protector identities this problem provides sysadmin with numerous ways to lock down, manage and monitor devices across the enterprise. For example, users can create rules and groups via LDAP based on vendor ID, product ID, serial number, and existing permission groups. In addition, the platform takes a unique approach to protect data through content-aware scanning and enforced encryption.
Content-aware protection helps the system understand context based on the action, user, and type of data accessed. This provides a strong starting point for administrators to build additional policies, helping save time during the onboarding process.
Automatic USB encryption ensures that data leaving your environment is encrypted, no matter which device it goes on. Enforced encryption helps keep companies compliant by providing data is encrypted both in transit and while at rest. From an end-user perspective, this procedure is password-based and only adds a single step to their workflow.
Who is it recommended for?
The Device Control service is not a standalone system because it relies on the categorization of data that is implemented in another unit of the Endpoint Protector suite. Therefore, it is an add-on service that not all businesses will need as much as the central sensitive data discovery and classification system.
Pros:
- User-Based Security Policies: Endpoint Protector allows the creation of custom security policies based on users rather than machines, providing flexibility and tailored security controls.
- Compliance: It complies with industry standards such as PCI DSS, HIPAA, NIST, ISO 9001, and GDPR, ensuring data protection and regulatory compliance.
- Automatic Risk Assessment: It automatically assesses risks based on vulnerabilities found on endpoints, helping administrators prioritize security measures.
- Device Control Settings: It prevents data theft and BadUSB attacks through device control settings, mitigating the risk of unauthorized data transfers and malicious activities.
Cons:
- Lack of Trial Version: One potential drawback mentioned is the absence of a trial version for testing, which could be a limitation for organizations evaluating the solution before implementation.
Endpoint Protector’s combination of device controls, DLP options, and encryption settings make it a valuable tool for any business looking to secure their data and prove compliance. You can test out Endpoint Protector by requesting a demo.
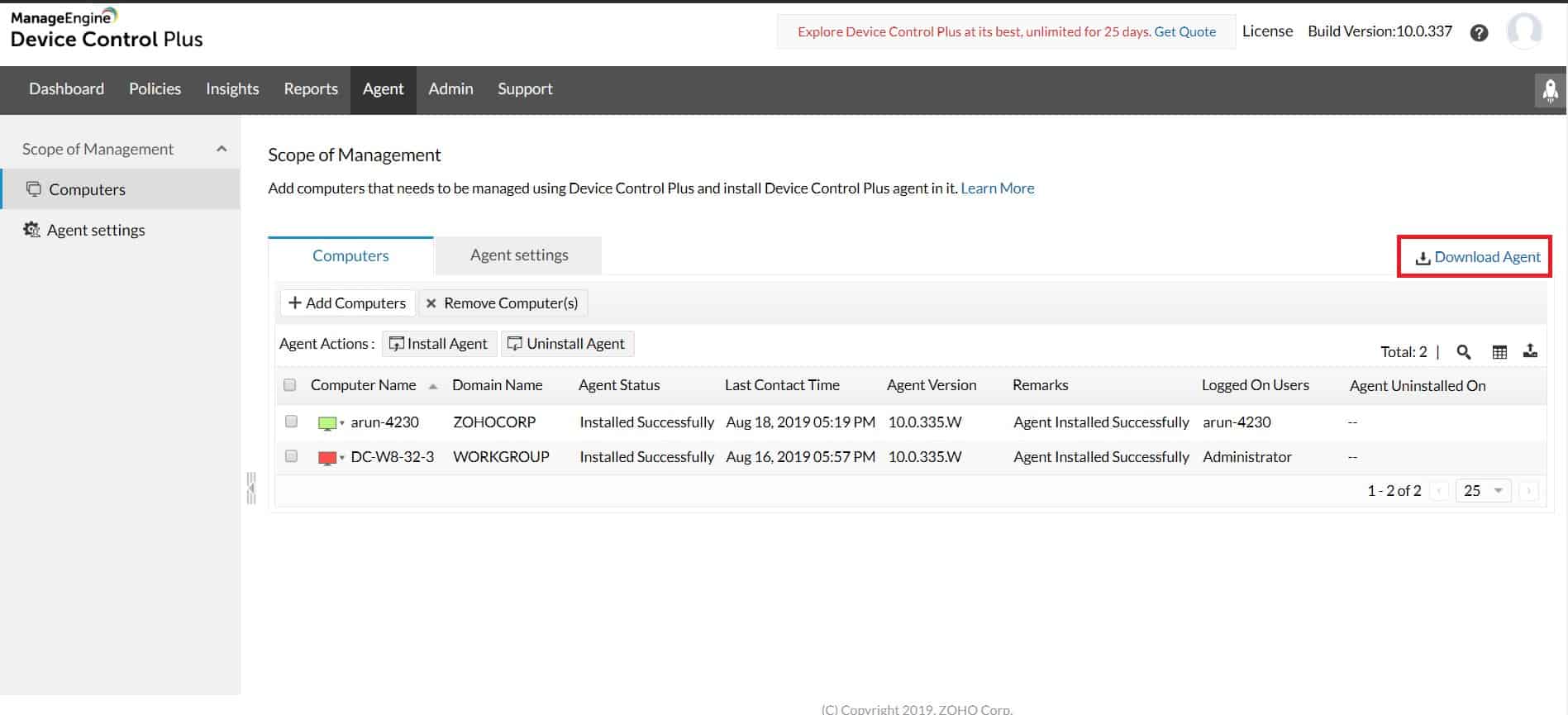
3. ManageEngine Device Control Plus (FREE TRIAL)
ManageEngine Device Control Plus is designed for enterprise control and supports both BYOD and company asset management. The platform offers administrators numerous options for device control while uniquely offering several features out of the box that makes onboarding quick and painless.
Key Features:
- USB Read-Only Mode: Device Control Plus allows administrators to set USB devices to read-only mode, enhancing data security by preventing unauthorized data transfers.
- Default Device Blocking: It blocks all devices by default, ensuring that only approved devices can connect to the network.
- Temporary Approval: There’s an option for temporary approval of devices, providing flexibility while maintaining security standards.
- Integration with ManageEngine Ecosystem: Integrates well with other products in the ManageEngine ecosystem, providing a cohesive management experience across different aspects of IT infrastructure.
Why do we recommend it?
ManageEngine Device Control Plus focuses on tackling the threat of malware getting onto an endpoint through a USB device rather than on data loss prevention. However, the tool does have activity logging features that create an audit trail and can reveal to an investigator that a file has been copied onto a removable storage device.
The platform goes beyond simple USB lockdown software by providing Data Loss Prevention (DLP) features to stop data leakage and detect the early signs of insider attacks. Sysadmins can create zones to set up read-only access, identify devices with overarching privileges, and automatically push out policies to new devices.
Transfer control can be established to identify suspicious file transfers by metrics like size, file type, and location. This helps prevent the theft of data and provides context into why that data was accessed in the first place. Rather than working backward to restrict access, ManageEngine Device Control Plus uses a Zero Trust approach that relies on a trusted device list to allow different access levels.
For situations where staff need special access, one-time access can temporarily be given to that user with privileges that revert after a certain amount of time. The platform also understands user behavior over time to create a baseline of everyday work. It uses this data to identify suspicious activity and highlight possible insider activity when anomalies arise. Threat activity can either launch automated scripts or send an alert notification via integration. This works well for both smaller teams and larger organizations that send alerts to a helpdesk queue.
Lastly, the platform has an intuitive dashboard that makes it easy to view the status of all managed endpoints and track critical alerts historically and in real-time. ManageEngine Device Control Plus offers a comprehensive approach to USB lockdown for both medium and enterprise-sized organizations.
Who is it recommended for?
Any business can choose to disable all USB ports on all endpoints. However, businesses that do need to allow some users to use removable storage will need to use this package or one like it. One problem with this system is that it doesn’t include a virus scanner so you will need to buy that as well.
Pros:
- Quick Setup and Customization: Device Control Plus is designed to work right away, featuring over 200 customizable widgets to build unique dashboards and reports, making it user-friendly and adaptable to various needs.
- Autodiscovery and Device Mapping: It leverages autodiscovery to find, inventory, and map new devices, simplifying device management and visibility.
- Multiple Alerting Channels: Device Control Plus supports email, SMS, and webhook for numerous alerting channels, ensuring timely notifications and response to security incidents.
Cons:
- Learning Curve: As a feature-rich tool, Device Control Plus may require time investment to properly learn and utilize all its functionalities, especially for administrators new to the platform.
You can test out ManageEngine Device Control Plus through a free 30-day trial.
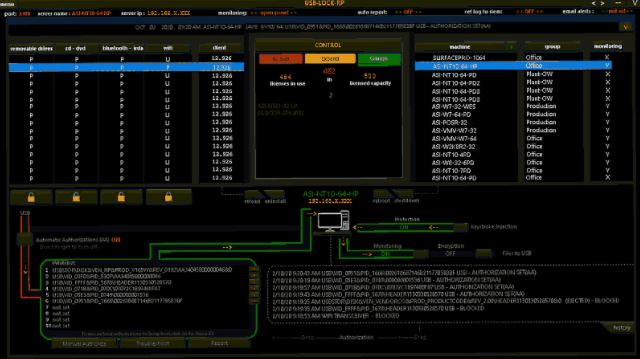
4. USB Lock RP
USB Lock RP is a device control platform with a focus on controlling and locking down USB ports. It provides centralized USB management through a sleek dark-mode dashboard and empowers administrators of any size network to manage their data more effectively.
Key Features:
- Remote USB Port Locking: USB Lock RP allows administrators to remotely lock USB ports, preventing unauthorized access to connected USB devices.
- USB Read-Only Mode: It can make USBs read-only, enhancing data security by restricting write access to USB storage devices.
- File Transfer Encryption: The solution offers file transfer encryption, ensuring that data transferred via USB devices is secure and protected from unauthorized access.
- Centralized USB Management: It centralizes all USB management tasks from a single pane of glass, streamlining administration and improving efficiency.
Why do we recommend it?
USB Lock RP is a package that can control USB ports remotely. This system requires an agent to be installed on each endpoint to communicate with a central controller console and implement the controls on USB ports. That agent will block all ports by default and then implement allowed actions per device.
The platform uses a lightweight agent to control endpoints and push out policy enforcement, making it highly scalable and viable for legacy devices with limited resources. The enforcement automatically detects hardware IDs to allow only specific USB devices without restricting other peripherals like speakers or printers.
Policy enforcement works on the system level to stop unauthorized devices from transmitting or receiving data, ideal for preventing data theft and infection. In addition, automatically blocking unknown devices creates a secure environment by default and helps reduce unnecessary scans of new hardware when plugged in.
The platform can scale to support up to 5000 devices and supports basic logging and data exports in CSV format. In addition, users can add blocking screens complete with their company logo, opening the possibility for MSPs to resell this product as a managed service.
Who is it recommended for?
The endpoint agent for this package is only available for Windows, so you won’t be able to control endpoints running macOS or Linux. The package can operate remotely and the local agent that facilitates that can be installed remotely, so it is a good solution for large organizations and it can also be used by managed service providers.
Pros:
- Excellent Interface: USB Lock RP features an excellent interface that is user-friendly and intuitive, making it easy for administrators to manage USB devices.
- Scalability: It can support up to 5000 endpoints, making it suitable for both small to medium-sized businesses (SMBs) and enterprise networks.
- Flexibility: USB Lock RP is a highly flexible platform, offering customization options and scalability that cater to the needs of SMBs as well as large enterprise environments.
Cons:
- Learning Curve: Like many feature-rich products, USB Lock RP can take time to fully explore and understand its capabilities, especially for new users or administrators.
USB Lock RP is a viable solution for both small and large networks alike. With its lightweight agent and support for legacy systems as old as Windows NT, this tool is both as flexible as it is powerful.
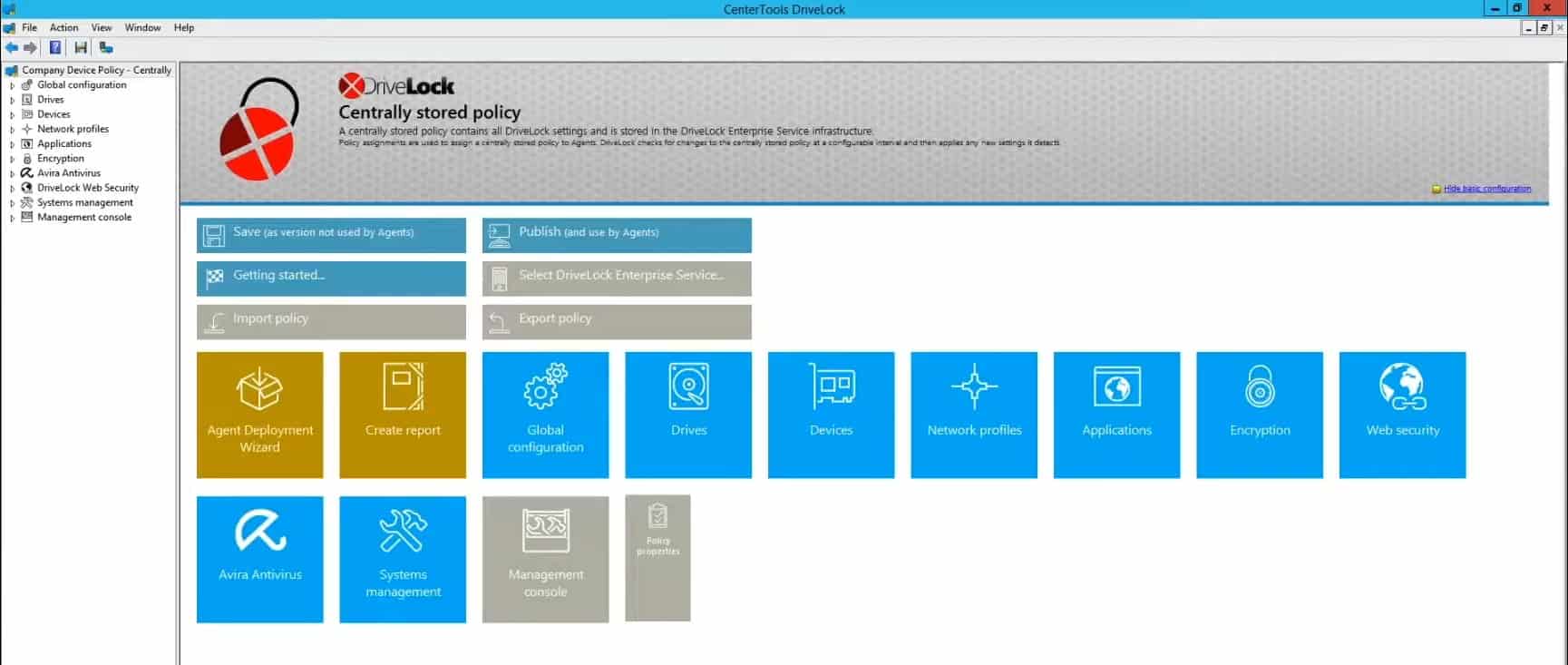
5. DriveLock
DriveLock provides cloud-based endpoint security that follows the Zero Trust model to secure endpoints and different data on the network. In addition, the platform offers numerous other features as separate services such as device encryption, app control, and vulnerability management.
Key Features:
- Default USB Blocking: DriveLock blocks USB devices by default, preventing unauthorized access and data transfers via USB ports.
- Application Control: It includes application control features, allowing administrators to manage and control the execution of applications on endpoints.
- Device Control: DriveLock provides comprehensive device control capabilities, enabling administrators to monitor and manage connected devices effectively.
- Disk Encryption: The solution offers disk encryption features, enhancing data security by encrypting sensitive data stored on endpoints.
Why do we recommend it?
DriveLock isn’t limited to controlling USB devices. It also controls access to applications. In both cases, the tool uses a blocking strategy by default. This is very similar to the ThreatLocker and Endpoint Protector strategies. The system doesn’t include a sensitive data discovery system, so it can only log which files were moved and not what was in them.
DriveLock uses a minimalistic management console to help highlight critical information and key metrics to administrators on the front end. In addition, it leverages color well to help gather information about your environment and is fully customizable through a widget-based system.
The platform offers complete device control, including USB lockdown features to secure multiple types of environments. A part that made DriveLock stand out is its ability to train employees to handle data safely. This feature can identify when inappropriate access is attempted and rectify it through a short instructional lesson. This not only helps train staff to be more security conscious but also provides admins with a record of who attempted to access which files and how many times they tried.
Outside of USB lockdown options, DriveLock also supports controls for both internal devices and BYOD environments, allows users to create flexible policies without eliminating their current device policy. In addition, other forms of media removal such as CDs or DVD burners are also suppressed, a feature some other tools may lack.
Who is it recommended for?
DriveLock stresses the importance of user training, which implies it doesn’t enforce rigid standards. It does log all file movements onto and off USB devices, so it should be used in conjunction with a sensitive data loss prevention service or a file integrity monitor.
Pros:
- Integrated Security Features: DriveLock combines device control with Data Loss Prevention (DLP) and anti-malware features, providing a holistic approach to endpoint security.
- Common Criteria EAL 3+ Certified: It is certified under the Common Criteria Evaluation Assurance Level (EAL) 3+, indicating a high level of security and reliability.
- Scalability: DriveLock is highly scalable, making it suitable for larger environments such as enterprises with extensive IT infrastructure.
- Disk Encryption: The inclusion of disk encryption adds an extra layer of security by protecting data at rest on endpoints.
Cons:
- Complexity for Non-Technical Users: DriveLock may not be ideal for a non-technical audience or organizations without dedicated IT security expertise.
You can test out DriveLock utterly free through a 30-day trial.
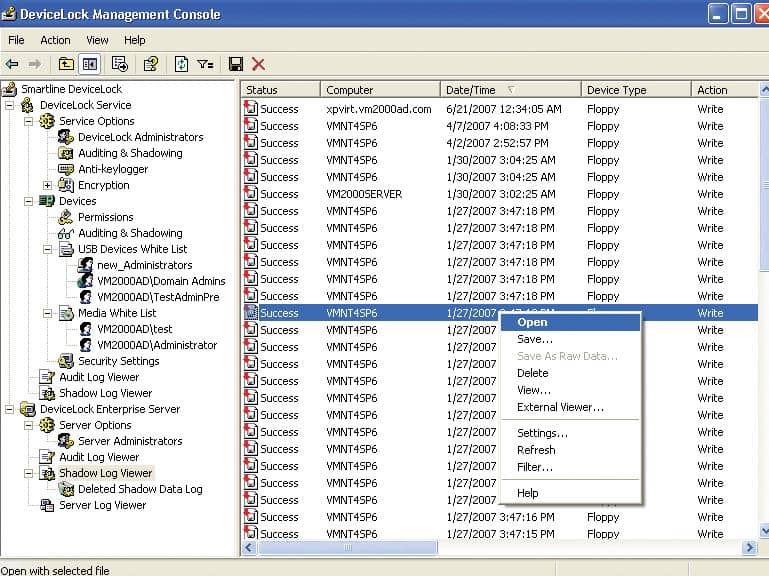
6. DeviceLock
DeviceLock DLP by Acronis offers data loss prevention, device control, and endpoint management. In addition, the platform minimizes insider threats by blocking unauthorized access to sensitive data automatically and logging any attempts to discover or access data out of scope for that user.
Key Features:
- Sensitive Data Protection: DeviceLock focuses on protecting sensitive data, providing controls to prevent unauthorized access and data leaks.
- File Movement Blocks: It includes features to block file movement, ensuring that sensitive files are not transferred to unauthorized locations.
- Data Access Control and Tracking: DeviceLock enables administrators to control and track data access across the network, ensuring visibility and accountability.
- Compliance Management: DeviceLock offers tools for compliance management, helping organizations adhere to regulatory requirements and internal policies.
Why do we recommend it?
Acronis Device Lock is more than a USB port blocker or device control system because it includes a protection system for sensitive data. This package can interface with Active Directory, so you can have your data access rules connected to AD user groups. The system provides activity logging for file access and movements.
As a DLP solution, users have extended visibility into user behavior, devices, and the overall environment. This allows both administrators and the platform to identify patterns and trends that help reduce false positives and provide a more accurate device control solution.
DeviceLock works through a simple agent deployable and offers Active Directory integration and other centralized management console templates to set policies from. One hidden benefit to the platform’s increased visibility is having performance data collected for you. Performance reports allow you to see how well users are following data protection policies and viewing which features of the tool you use, helping you control your costs by eliminating features you don’t need.
Who is it recommended for?
This package will control all file movements, not just those on and off USB storage. The service has a core module for USB controls and then add-ons for controls of data movements by other means. This system can operate through virtual desktops. The software for this package runs on Windows or Windows Server.
Pros:
- Lightweight Tool: DeviceLock is a lightweight tool that uses minimal system resources, ensuring efficient performance without causing system slowdowns.
- User Behavior-Based Threat Identification: It leverages user behavior analysis to identify potential threats, enhancing security by detecting suspicious activities.
- Automated and Manual Detection: The solution supports both automated detection methods, such as rule-based controls, and manual detection methods, providing flexibility in threat detection and response.
Cons:
- Interface Scalability: One drawback mentioned is that the interface of DeviceLock may not scale as well as some other options, potentially impacting user experience, especially in larger deployments.
DeviceLock offers several modular add-ons attractive to smaller budget-conscious organizations looking only to take advantage of a few features rather than pay for an enterprise solution. In addition to USB lockdown, DeviceLock also monitors and controls clipboards, identity image data, and extract text data from images to protect against data theft.
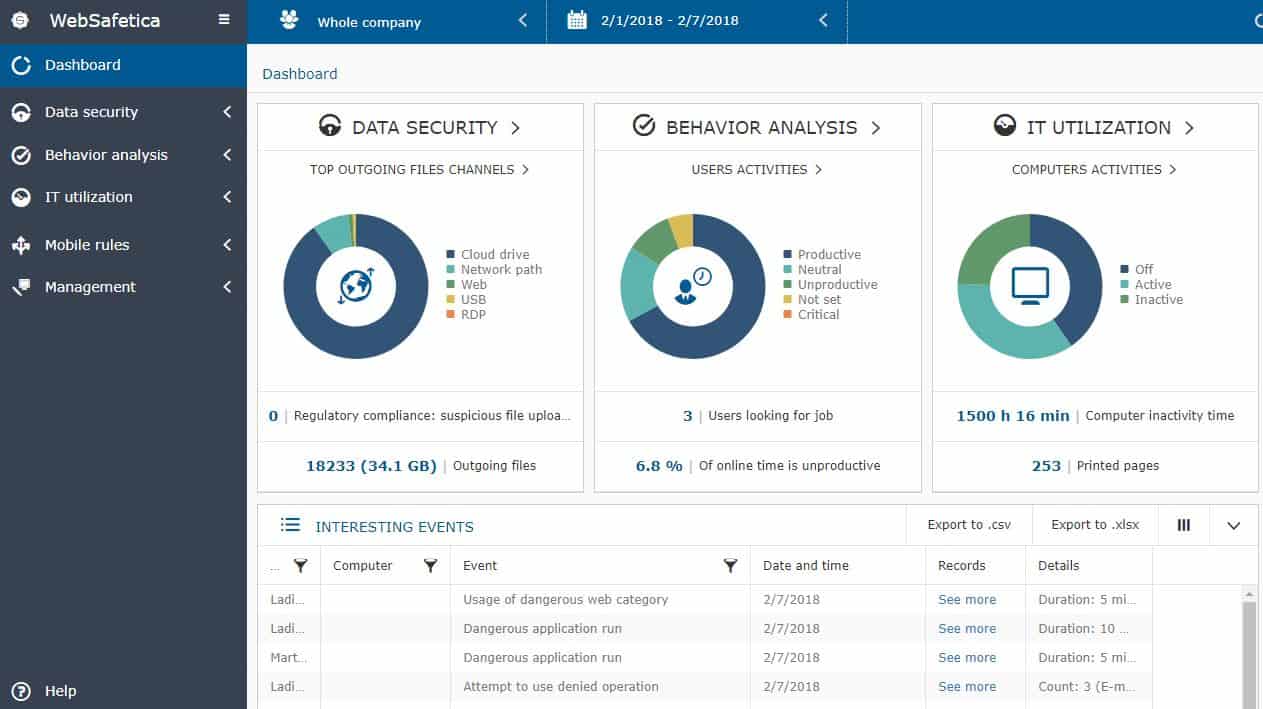
7. Safetica
Safetica focuses on protecting data by implementing DLP, insider threat detection, and regulatory controls for sysadmins. This combination helps keep businesses complaint while protecting them from accidental data loss through deletion and malicious insider data theft.
Key Features:
- USB Lockdown: Safetica can block or restrict the use of USB devices to prevent unauthorized data transfer.
- Content-Aware Protection: The tool offers content-aware protection policies that can control what data can be transferred based on content type, ensuring sensitive information does not leave the organization through any means, including USB drives.
- Device Control: Beyond USBs, Safetica allows for the management and monitoring of other device types, such as CDs, DVDs, and external hard drives.
- Audit and Forensics: Provides detailed logging and tracking of USB usage and file movement, which helps in auditing and forensic investigations to determine the cause and scope of any incidents.
Why do we recommend it?
Safetica is a DLP solution that locates all of your sensitive data and classifies it. The classification process can be easily tailored towards specific data protection standards, including GDPR, HIPAA, and PCI DSS. The tool tracks and logs the movement of data.
Administrators can create flows that not only restrict or lockdown USB ports but define how files can move. These rules provide granular control over how data moves, ensuring it can always go where it needs to, without being leaked elsewhere.
To detect insider threats, holistic behavioral analysis is used to automatically identity malicious behavior based on the baseline of everyday end-user actions. This, when paired with a Zero Trust policy, can see the emerging movement of a rogue employee and automatically restrict their access until a manual review has been completed.
The DLP section prevents data loss through a combination of incremental backups and customizable device control. First, onboarding starts by running an audit for sensitive data, where the system will attempt to highlight sensitive information. Second, users will set their policies based on these zones. Lastly, users create their automated reports and set up real-time alerts for any security threats that may emerge.
Who is it recommended for?
Safetica has two versions. These are Safetica NXT, which is a SaaS platform, and Safetica ONE, which is an on-premises software package for Windows Server. Safetica NXT is recommended for small and mid-sized businesses and the Safetica ONE option is designed for use by large enterprises.
Pros:
- Ease of Management: Comes with a user-friendly interface that simplifies policy implementation and management across the organization, enhancing usability for IT administrators.
- Enhanced Security: By controlling access to USB and other removable devices, Safetica helps prevent potential data leaks and theft, enhancing organizational security.
- Compliance Support: The solution aids compliance with various regulatory requirements by ensuring that data is only transferred through authorized channels and by maintaining detailed logs of data movement.
- Flexibility: Safetica’s policies are highly configurable, allowing organizations to tailor device and data usage rules according to their specific security needs and policies.
Cons:
- Potential for Overblocking: If not properly configured, Safetica’s restrictive policies might block legitimate uses of removable storage, potentially hindering productivity.
Safetica does not have a free trial, but you can test their platform through a free demo.