Organizations are expanding their digital presence, and this creates a wider surface area for attacks. A deep analysis of every attack shows that it all started with a single vulnerability. Had the vulnerability been identified and remediated, the cyberattack could have been thwarted.
Given the multiple endpoints and applications, it is not possible to manually identify every vulnerability. This is where automated software platforms help. A vulnerability manager performs automated checks on system weaknesses for any computer system. At the bare minimum, these tools identify vulnerabilities, so the IT teams can fix them before they are exploited by hackers.
Additionally, vulnerability management tools address the following pain points in organizations.
- Manually tracking every asset across the entire network can be close to impossible.
- Ad hoc scans are unreliable as they do not provide a comprehensive picture of vulnerabilities.
- IT teams may find it hard to prioritize issues, and this can impact their resolution.
- The patching process can be slow and unfragmented, opening security vulnerabilities.
- It can be difficult to understand the business impact of vulnerabilities.
- Standalone processes can add to overheads and may even create data silos that benefit no one.
Vulnerability management tools address the above pain points to provide organizations with comprehensive visibility into the vulnerabilities in their infrastructure. Many of them even apply remediation processes automatically to prevent anyone from exploiting them. In this guide, we will explore the best tools that offer extensive protection.
Our list of the best software deployment tools
Based on our independent research, selection requirements, and rating methodologies, these are the best best vulnerability managers available on the market today:
- NinjaOne Vulnerability Manager EDITOR’S CHOICE This cloud-based system is part of a remote monitoring and management package and it focuses on software vulnerabilities with an automated patch manager. Get a 14-day free trial.
- Invicti (FREE DEMO) This system focuses on securing applications developed in-house and is mainly concerned with code destined to operate online. Access the free demo.
- Acunetix (ACCESS FREE DEMO) This security package has a lot of options. It can be used as an automated penetration testing tool, and there is also a version that operates as a full vulnerability scanner. Use it as a cloud service or install it onsite on Windows, macOS, or Linux.
- Intruder (FREE TRIAL) A cloud platform that offers a range of security management services, including a monthly vulnerability scan.
- ManageEngine Vulnerability Manager Plus (FREE TRIAL) This package includes a vulnerability scanner and all of the tools you need to act on the discovered weaknesses. Available for Windows and Windows Server.
- ESET Protect MDR This managed security service includes a choice of software plans that provide endpoint protection, email security, vulnerability scanning, patch management, and threat detection. Endpoint agents for Windows, macOS, Linux, iOS, and Android.
- SecPod SanerNow This platform includes a vulnerability manager, a patch manager, and a compliance manager that operates on Windows, macOS, Linux, and cloud platforms. Delivered from the cloud.
- OpenVAS This security system is free to use, and its full name is the Open Vulnerability Assessment System. Written for Linux but will run on Windows over a VM.
Vulnerability management and pen testing
You might wonder, if vulnerability managers and pen testing perform the same task, when would you use each? As it is a software package, a vulnerability manager is cheaper than pen testers. On the other hand, the white hat hackers that perform pen-testing are highly skilled, and there aren’t many of them, so their rates are very high.
Given that vulnerability, managers are so much cheaper than pen testers; why bother with penetration testing? Although vulnerability managers have all of the techniques of hackers built into them, they don’t have intelligence. The vulnerability just looks for the system weaknesses that would let a hacker in. A pen tester can make instant decisions and take rough guesses that can shortcut procedural instructions.
The difference between vulnerability testing and penetration testing is that a vulnerability manager is organized, but a penetration tester is ingenious. You need both system checking strategies. Given the costs involved in penetration testing, it is conducted much less frequently than vulnerability scanning. Even vulnerability scanning doesn’t need to run continuously. A typical schedule for a vulnerability scan is once a month. You can then order an outside consultancy to perform penetration tests on your system once every six months or once a year.
The actual requirements for system security checks vary according to the system. For example, a very stable network with few innovations and a low rate of added software won’t need checks very often. On the other hand, a system that is constantly being expanded by an in-house development team will need more frequent inspections constantly expanding system.
Key Aspects to Consider While Choosing the Best Vulnerability Management Tools
At its core, vulnerability management must scan your infrastructure to identify existing vulnerabilities. However, it’s better to have a tool that goes beyond just scanning and proves the context, criticality, and the underlying cause to speed the remediation process.
That said, here are some key aspects to consider while choosing a vulnerability management platform that best meets your needs.
- Coverage and Visibility: Two core aspects to look for are coverage and visibility. The tool must detect vulnerabilities across all environments, and it must present them in a way that you can understand. Without these features, your vulnerabilities will continue to be blind spots.
- Context and Prioritization: Going beyond risk identification, the tool you select must also prioritize the vulnerabilities so you can allocate resources accordingly. Also, it helps to get the context for faster remediation.
- Automation: Another must-have feature, as this can save time and effort. Also, it reduces manual errors and opens up the possibility for streamlined workflows.
- Integration: Ideally, the tool you select must integrate well with your existing systems for smooth operations and data workflows.
- Scalability: The tool you select must scale with your growth, and it must be able to take on more endpoints, without requiring too many changes in deployment.
- Reporting and Compliance: It’s good to select a tool that can generate reports for internal decision-making and audit trails for meeting compliance requirements.
The Best Vulnerability Managers
There are many vulnerability managers on the market today because it is a service that is very heavily in demand. Unfortunately, while some excellent tools are available, there are others that don’t cut the mustard, so you could get stuck with a vulnerability scan that is less than the best.
As well as taking into account these selection criteria, we made sure to find vulnerability managers that businesses that are all Windows or Linux-only can use.
1. NinjaOne Vulnerability Manager (FREE TRIAL)
Best for: Automated vulnerability remediation.
Relevant for: IT teams responsible for patch management and endpoint security, and MSPs.
Price: Negotiated pricing
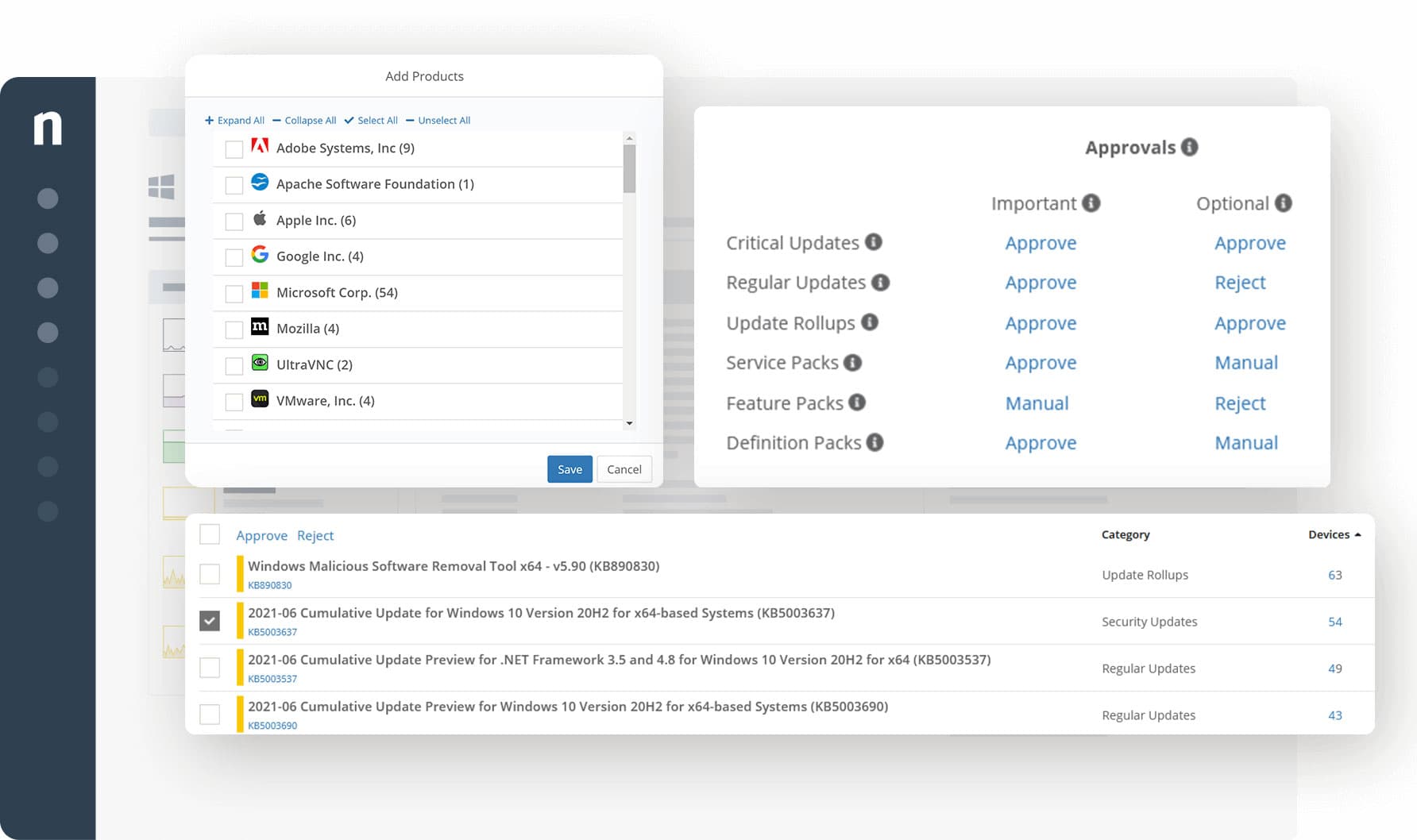
NinjaOne Vulnerability Management is part of a remote monitoring and management (RMM) package that focuses on software vulnerabilities. The RMM provides a discovery service that will compile a software inventory for each endpoint. Continuous scanning of each protected endpoint identifies when new software is installed, keeping the inventory up to date. G2’s track record of recognizing NinjaOne, 11 times consecutively, accentuates its proficiency in Endpoint Management.
Key Features:
- Endpoint Software Management: Provides comprehensive monitoring and management of software on all endpoints.
- SaaS Platform: Delivers vulnerability management as a cloud-based service for ease of access and management.
- Automated Patching: Ensures operating systems and applications are up-to-date across Windows, macOS, and Linux devices.
- Compliance Tracking: Offers an audit trail for compliance purposes, detailing patch management activities.
Unique buying proposition
NinjaOne consolidates vulnerability detection, risk prioritization, and remediation into a single platform. It utilizes automated workflows to perform real-time scanning, CVE data import, and policy enforcement, enabling you to handle the entire lifecycle, from discovery to remediation.
Feature in Focus: Zero-touch Patch Automation
The zero-touch patch automation feature automatically identifies missing patches across applications and operating systems, and deploys them based on predefined policies. It also offers auto-reboots and real-time status updates, without requiring manual intervention.
Why do we recommend it?
NinjaOne lets you set up a central configuration policy for endpoints and enforce that by applying those settings to every device. The tool then scans for software and ensures that those packages and the operating systems of all endpoints are kept up to date. Automated patching serves a large number of endpoints without the need for manual intervention.
The vulnerability scanner looks at the version numbers of all of the installed operating systems and software packages. This number indicates the patch status of each piece of software and gets updated each time a patch is applied.
Although the RMM allows technicians to set up a standard configuration for endpoints and apply it to all devices. The tool doesn’t scan for changes, and so it doesn’t cover the configuration aspect of vulnerability management.
This system will automatically monitor all network and server activity, looking for performance issues, while it also scans for new software to record in the inventory, and polls for updates from software suppliers.
If a patch becomes available for one of the software systems listed in the inventory, NinjaOne copies over the installer and queues it up for rollout at the next available maintenance window. Patches are applied out of office hours when endpoints are not in use, so the patch manager will wake up, reboot, and turn off computers when necessary.
Who is it recommended for?
The NinjaOne platform is a complete system monitoring and management package, so if you already have a monitoring system that you like and you only want a vulnerability manager, this package probably isn’t for you. The RM is ideal for managed service providers and in-house IT departments.
Pros:
- Centralized Configuration Policy: Allows for the standardized setup of endpoint configurations, ensuring uniform security practices.
- Continuous Software Scanning: Keeps software inventory current by detecting new installations and available updates.
- Efficient Patch Management: Automates the patching process, significantly reducing the workload on IT staff.
- Integrated Backup and Recovery: Includes data protection services to mitigate the impact of security breaches.
- License and Log Management: Facilitates software license oversight and stores activity logs in cloud storage for easy retrieval.
Cons:
- Lacks Transparent Pricing: Requires potential users to contact sales for a customized pricing plan, which may delay decision-making.
NinjaOne doesn’t publish a price list, but you can register for a quote to match your needs..The tool is a SaaS platform and you sign up for the service at the company’s website. You can get a 14-day free trial to fully assess the RMM package.
2. Invicti (ACCESS FREE DEMO)
Best for: Web apps vulnerability management
Relevant for: DevOps and DevSecOps teams.
Price: Invicti offers three plans – Essentials, Professional, and Ultimate. Check the support team for negotiated pricing.
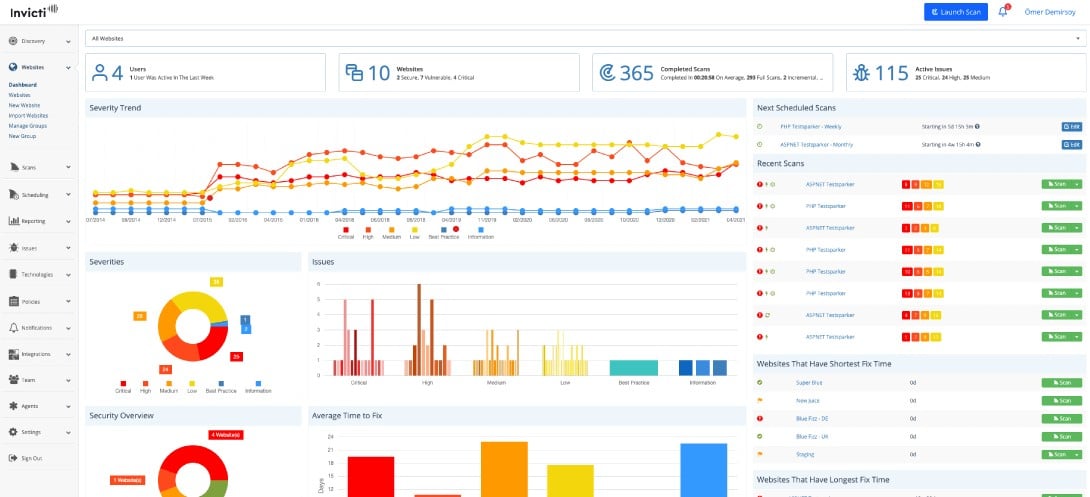
Invicti is probably the best vulnerability management tool available for DevOps environments. This is mainly a good choice for the developers of Web applications. The Invicti tool can offer security advice at every stage of the CI/CD pipeline. The package includes Dynamic Application Security Testing (DAST) and Interactive Application Security Testing (IAST). It is suitable for developers during the build phase, by acceptance testers, when pushing through new development, and by the operations team to check on live systems.
Key Features:
- Continuous & On-Demand Testing: Enables regular and ad-hoc security scans throughout the development lifecycle.
- CI/CD Pipeline Integration: Seamlessly fits into continuous integration and delivery workflows for real-time security feedback.
- Comprehensive DAST & IAST: Offers dynamic and interactive application security testing to identify vulnerabilities in web applications.
- Flexible Deployment: Available as a cloud service or an on-premises solution, catering to different organizational needs.
Unique buying proposition
Invicti automates the complete vulnerability management lifecycle for web apps and APIs. It has a proprietary scanning technology for identifying vulnerabilities and, accordingly, creates and assigns tickets to developers based on predetermined workflows and rules. It also integrates well with ticketing systems and trackers to provide complete visibility into the status of identified vulnerabilities.
Feature in Focus: Proof-based Scanning
Invicti uses a proprietary technology called Proof-based scanning for validating the identified vulnerabilities. It safely exploits them in read-only mode to ensure that every vulnerability is valid, thereby reducing false positives. According to the company’s website, this technology ensures an accuracy rate of 99.98%
Why do we recommend it?
Invicti is a Web application security tester that can be used to scan applications under development, at the point of acceptance testing, and during operations. In its operations phase usage, the service acts as a vulnerability scanner. This system tests third-party services and APIs in conjunction with assets developed by the customer.
Vulnerability scans by Invicti work through the Common Vulnerabilities and Exposures (CVE) list produced by The Mitre Corporation. As Invicti is geared towards developers of Web applications, these reported exploits are not enough. The system also has its method of heuristics that examines code under development for possible pitfalls and security glitches.
For an idea of what this service assesses, think of the coupling between functions and how data exchanges can be manipulated. With code under development, these weaknesses are not necessarily “known exploits” and would pass checks that just look for specific CVEs. However, the connections between modules are known to provide gaps that hackers will gladly squeeze into if it gives them a way in, so Invicti can spot those potential hazards before too much work has gone into developing the function.
Integration testing and acceptance testing need to look further at how the new code fits into the existing structure of a Web application or site. So, this offers another point in the pipeline where Invicti can help. It is even possible to automate the code movement through the testing phase by utilizing the integrations available in Invicti.
At the point of sandboxing a new application, Invicti will assess the required system settings that support the software. In addition, it will be looking at how the code uses system resources and examining whether the requirements for the software introduced system security vulnerabilities.
Once the code goes live, Invicti will continue to scan it, examining whether the live environment intrudes new vulnerabilities in the package or whether the new code weakens the security of an existing application.
As it is very focused on in-house development, Invicti is not so hot on patch management. When the software developers are in the back office, there is no point in looking to the supplier for a patch. However, the Invicti system can orchestrate responses to weaknesses with other security tools already operating on the network, particularly for the third-party software that the business uses.
Who is it recommended for?
This system can be used by businesses that are the consumers of Web applications, but the main market for the system lies with the developers and managers of Web services, such as SaaS platforms. The package is useful to screen third-party components before choosing them as parts of a development.
Pros:
- CI/CD Pipeline Support: Specifically designed to enhance security within DevOps environments, providing valuable insights at every stage.
- Versatile Integration: Easily integrates with various project management tools, streamlining vulnerability management processes.
- Advanced Testing Techniques: Utilizes both DAST and IAST for thorough examination of applications, catching vulnerabilities early in the development phase.
- Operational Vulnerability Scanning: Continues to monitor applications post-deployment, ensuring ongoing security.
- CVE and Custom Vulnerability Detection: Monitors for known vulnerabilities while also identifying potential security risks unique to the application’s code.
- SaaS and On-Premises Options: Offers flexibility in deployment, allowing businesses to choose the model that best fits their infrastructure.
Cons:
- Lacks Patch Management: Does not include features for managing software patches, which may require additional tools for complete vulnerability management.
Invicti is available as a cloud platform, and it is also possible to get the system as a software package for installation. The on-premises version runs on Windows and Windows Server. In addition, you can access a demo to assess Invicti.
3. Acunetix (ACCESS FREE DEMO)
Best for: Web vulnerability scanning.
Relevant for: DevSecOps and web application engineers who want to build security into CI/CD pipelines.
Price: Negotiated pricing.
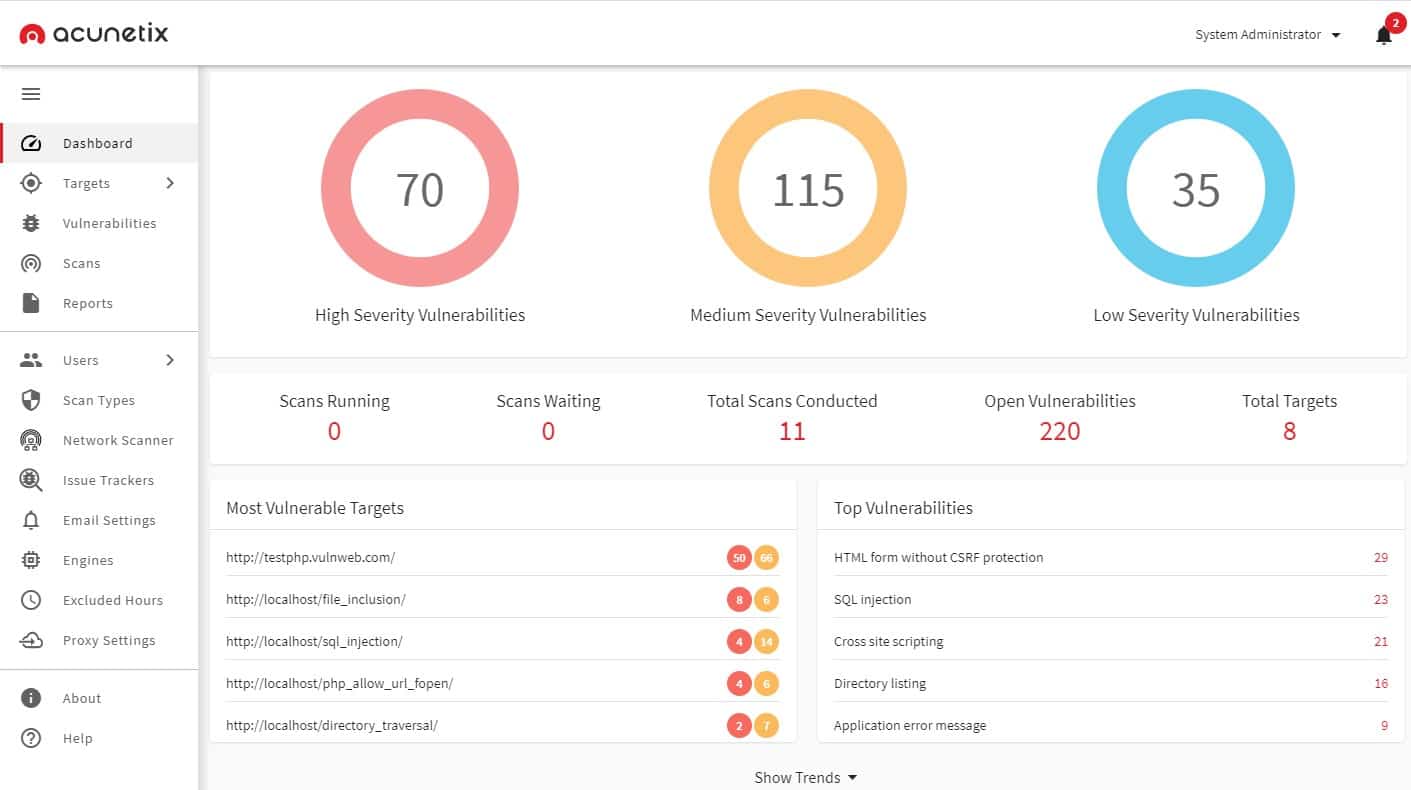
Acunetix is a very flexible service because it is offered in three versions, each with different levels of automation, so depending on which edition you go for, you get an automated penetration testing tool or a vulnerability scanner.
Key Features:
- Versatile Scanning Options: Offers both web and network vulnerability scanning, with a focus on continuous testing.
- Compliance Support: Helps businesses meet standards like PCI DSS, HIPAA, and ISO 27001 through thorough security assessments.
- Advanced Testing Tools: Includes tools like AcuSensor for IAST, Deep Scan for comprehensive crawling, and Out-of-Band Vulnerability Tester.
Unique buying proposition
Acunetix can quickly and thoroughly scan your web application and APIs to discover open and hidden vulnerabilities. Moreover, it integrates seamlessly into any CI/CD pipeline to scan web apps before deployment. It also compares the current values against predefined thresholds and sends alerts when there are deviations. Its scan reports and recommendations for remediation come in handy as well.
Feature in Focus: CI/CD Pipeline Integration
Acunetix automates vulnerability management for web apps by integrating with popular CI/CD pipelines like Jenkins, Azure DevOps, Bamboo, and more. As a result of this integration, every build or commit is scanned thoroughly for deviations from the predefined thresholds. This approach ensures that vulnerabilities are identified early and remediated quickly before they cause a wide impact.
Why do we recommend it?
Acunetix is a Web application security tester that can drill through third-party APIs and framework functions to discover all of the supporting microservices. The system tests these systems to authorize them for use in development and also in conjunction with the newly created modules during acceptance testing and through its service life.
This is primarily a Web application scanner. It looks for the OWASP Top 10 in Web applications. These are known tricks that hackers use, such as SQL injection and cross-site scripting. The tool will also scan through look services that support APIs, looking at microservices and serverless systems. In total, Acunetix scans for more than 7,000 Web vulnerabilities – that facility is included in all editions of the product.
Other services in the Acunetix bundle include an Interactive Applications Security Tester (IAST), called AcuSensor, the Acunetix Deep Scan crawler, and the Acunetix Out-of-Band Vulnerability Tester. These tools are available in all editions and can be run on demand. The plans also include a Web application discovery module that chains all services from a starting point in a user-facing system, such as a Web page. In addition, the local services vulnerability scanner will read through code written in JavaScript, .NET framework, and PHP.
The three different versions lend themselves to different deployment scenarios. For example, the Standard edition performs scans on-demand so that penetration testers would use this version. The two higher versions, called Premium and Acunetix 360, offer continuous automated vulnerability scanning.
Those two higher versions are both suitable for businesses that follow data privacy standards. They count towards compliance with PCI DSS, HIPAA, and ISO 27001. The Premium plan is ideal for IT operations departments because it also scans the internal network and internet-accessed Web applications. This network vulnerability scanner looks for more than 50,000 known vulnerabilities.
Both of the higher versions can be used for DevSecOps environments. However, the Acunetix 360 edition is more suitable for the CI/CD pipeline operating scenario because it includes a workflow creation and management system. In addition, constantly expanding system Acunetix offers static, dynamic, and interactive application testing features. These plans also include integrations for orchestrated development management, connecting through to tools such as GitLab, Jira, Jenkins, and Bugzilla.
One of the shortfalls of Acunetix is that it doesn’t include an associated patch manager or configuration manager to fix the problems that it discovers automatically. However, this package is more aimed at Web applications than standard third-party software packages, and that operating environment doesn’t usually produce software updates. However, if you opt for the Premium edition to secure your network, you can connect Acunetix results to a third-party patch manager.
Who is it recommended for?
You would use Acunetix as part of your development environment for the creation of Web applications. You can also extend this system to provide network vulnerability scanning by integrating the free OpenVAS system (see below). Like Invicti, this package is available as a SaaS package or for on-premises installation.
Pros:
- Flexible Deployment: Available in versions that cater to different needs, from manual penetration testing to automated vulnerability scanning.
- Broad Vulnerability Coverage: Scans for over 7,000 web vulnerabilities, including the OWASP Top 10, ensuring a wide range of security threats are addressed.
- DevSecOps Integration: Supports CI/CD pipelines with integrations for key development and project management tools, facilitating seamless security testing in development workflows.
- Network and Web Application Scanning: Premium and 360 editions offer extended scanning capabilities, including internal network scanning and compliance with major security standards.
Cons:
- Lacks Patch Management: While highly effective in identifying vulnerabilities, it does not include a patch management feature to automatically remediate found issues, requiring integration with third-party solutions for comprehensive vulnerability management.
Acunetix is offered on the Software-as-a-Service model from a cloud host. However, you can also opt to install the software on your host. The package will run on Windows, macOS, and Linux. You can assess Acunetix by accessing the demo system.
4. Intruder (FREE TRIAL)
Best for: Continuous scanning of cloud resources
Relevant for: Security teams managing hybrid environments.
Price: Intruder offers four plans (All prices are per month for five infrastructure licenses):
- Essential: $99
- Cloud: $180
- Pro: $240
- Enterprise: Custom
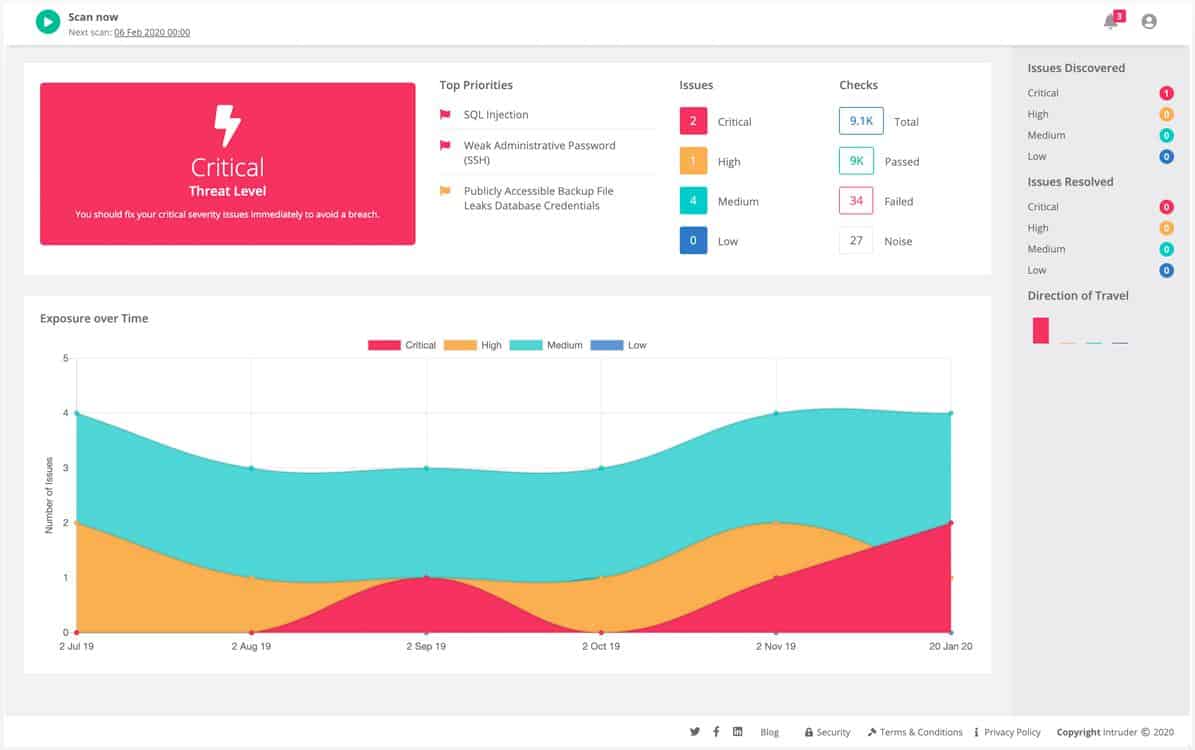
Intruder offers a range of plans from its cloud platform. Services from this provider start with a unlimited ad-hoc vulnerability scans. These vulnerability scans check websites for known exploits and also examine your network’s external profile. Once your vulnerability to outsiders has been assessed, the system conducts tests from within the network. In total, Intruder has a database of over 10,000 vulnerabilities to look for and conducts over 11,000 professional and open-source checks depending on what plan you are on.
Key Features:
- Extensive Vulnerability Database: Searches for over 10,000 vulnerabilities, offering comprehensive scans based on a vast range of known exploits.
- Flexible Scanning Options: Provides on-demand vulnerability scans, allowing for timely assessments of security posture.
- Penetration Testing Service: Available as a premium option, delivering expert human-led testing for deeper security insights.
Unique buying proposition
Intruder’s always-on vulnerability scanner gets triggered automatically when there’s a new asset on the Internet, in your cloud account, or even within your internal network. With this automatic detection, you are always on top of intruder attacks, unauthorized access, hacking bots, and more.
Feature in Focus: Smart Recon
A highlight of Intruder is its Smart Recon feature, which scans only when there’s a change in your infrastructure. Besides saving resources, this feature kicks in automatically. It can also be extended to cover misconfigurations and web vulnerabilities.
Why do we recommend it?
The Intruder system is an external attack surface assessor that is available in plans that also provide internal vulnerability scanning. The price difference between the three plans is very big and so buyers of the service would be attracted to a specific plan – either external scans or frequent network scans.
The entry-level vulnerability scanning service is called the Essential edition. You can add on the ability to launch vulnerability scans on demand, automatic emerging threat scans, cloud account integration and API & developer integrations by choosing the higher Pro edition. This service also monitors possible problems with SSL/TLS certificates and gives you access to the network view. The Pro plan also releases research data on emerging threats to look out for.
The top-tier plan of Intruder is called the Vanguard edition. This gives you all of the vulnerability scanning features of the Pro edition plus the services of a human penetration testing team and extended vulnerability discovery.
Who is it recommended for?
The three plans of Intruder have different audiences. The lowest plan has a broad appeal for all businesses that want to ensure that hackers can’t get into their systems. The top plan is almost five times the price of the lowest plan and is probably too expensive for SMBs.
Pros:
- Tailored Service Plans: Offers varying levels of service, from basic external scans to advanced internal network assessments, catering to different security needs.
- Comprehensive Security Checks: Performs over 11,000 checks, utilizing both professional and open-source methods to ensure detailed coverage.
- Emerging Threats Monitoring: Pro edition includes automatic scans for new vulnerabilities and integrations for enhanced cloud security.
- SSL/TLS Certificate Monitoring: Proactively identifies potential issues with SSL/TLS certificates, aiding in maintaining secure communications.
- Human Penetration Testing: The Vanguard edition includes expert penetration testing services for an added layer of security analysis.
Cons:
- Lack of Automated Patch Management: Does not include a feature for automatic patch application, requiring manual intervention for vulnerability remediation.
Plans start from $101/month when billed yearly. You can get a 14-day free trial of their Pro edition. All plans feature online chat support and detailed vulnerability assessment reports.
5. ManageEngine Vulnerability Manager Plus (FREE TRIAL)
Best for: Endpoint vulnerability lifecycle management.
Relevant for: MSPs handling multiple clients and IT security teams that require unified visibility across all endpoints.
Price: The annual subscription costs $1,195 for 100 workstations and $2,987 for a perpetual license.
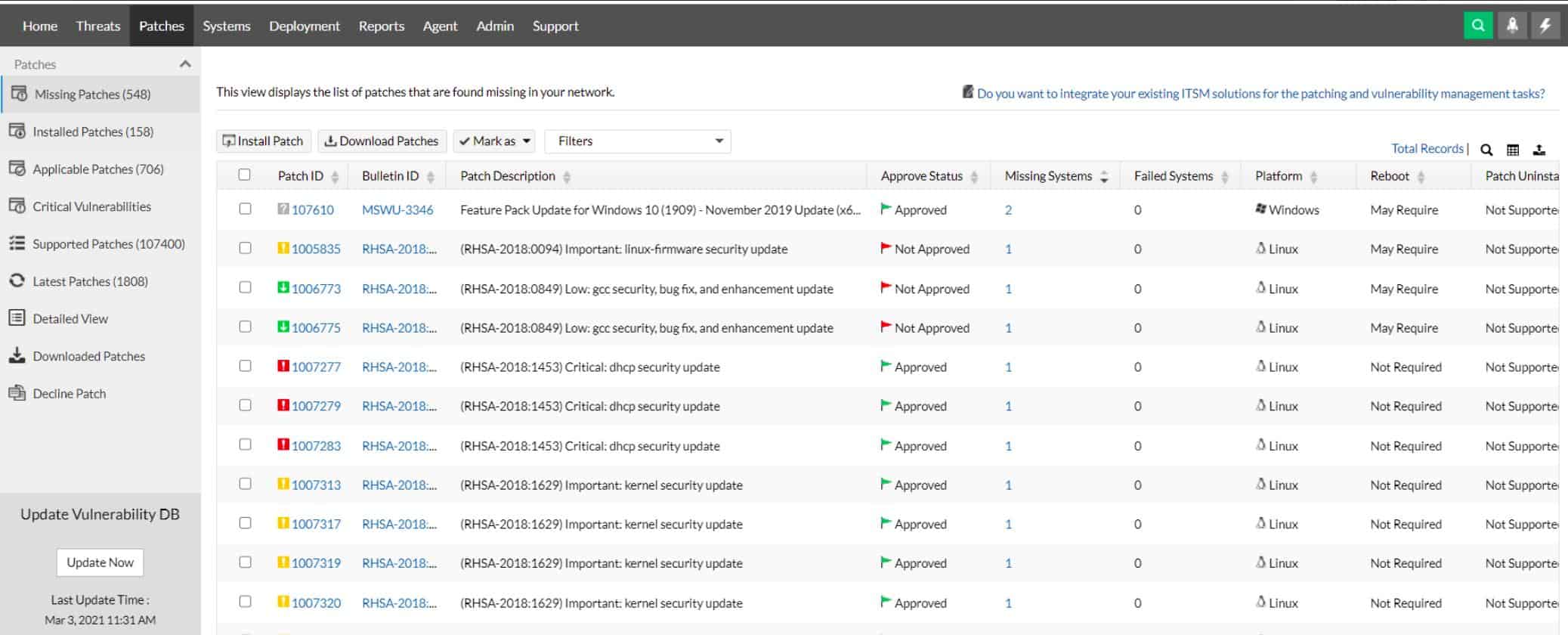
ManageEngine Vulnerability Manager Plus is the ultimate vulnerability management tool because it doesn’t just discover system security weaknesses; it fixes them. While it is common for a vulnerability management package to include both a vulnerability scanner and a patch manager, Vulnerability Manager Plus has many more utilities that act on the vulnerability scan results.
Key Features:
- Integrated Vulnerability and Patch Management: Combines a powerful vulnerability scanner with an efficient patch manager for comprehensive security oversight.
- Zero-Day Vulnerability Protection: Identifies potential vulnerabilities that could be exploited in zero-day attacks, enhancing preemptive defense capabilities.
- Frequent Scans: Conducts scans every 90 minutes, ensuring timely detection and management of vulnerabilities.
Unique buying proposition
This tool automates the entire vulnerability lifecycle, from discovering vulnerabilities to remediating them. It comes with many features like patch management, risk-based scanning, configuration management, and more through a single agent-based console. Also, this tool supports over 50,000 endpoints and integrates well with popular tools.
Feature in Focus: Continuous Agent-based Scanning
A highlight of this tool is that it uses lightweight agents to scan endpoints every 90 minutes to discover new vulnerabilities, missing patches, misconfigurations, open ports, and zero-day attacks. It correlates the findings and provides appropriate recommendations to remediate them.
Why do we recommend it?
ManageEngine Vulnerability Manager Plus is an on-premises scanner that operates within the network. It checks out endpoints running Windows and Linux and also network devices. The top package includes a patch manager, which also applies to devices running macOS. The service focuses on system misconfigurations and can automatically fix them.
The vulnerability scanner in the Vulnerability Manager Plus bundle scans operating systems, software, and system settings, looking for loopholes known as entry points for hackers. In addition to these standard checks, this scanner assesses other issues not yet listed as known hacker exploits that could be used for attacks. This protects your system against zero-day attacks, which are new strategies that no one has tried yet.
While many vulnerability management services give your system a scan once a month, the ManageEngine system runs every 90 minutes. First, it checks the network for all devices, so it can enroll new devices that you add between scans – you don’t have to set up that new device in the scanner dashboard. Next, the scanner ranks all of the system weaknesses and displays them all in a list ordered by priority.
If you gave the system permission, Vulnerability Management Plus would automatically trigger other modules to fix the problems that it discovers. But, first, it will run the automated Patch Manager. This service is included in the ManageEngine bundle, but it isn’t tied to the vulnerability manager. You can also use it yourself outside of the processes of Vulnerability Manager Plus.
The Patch Manager checks for patch availability, store the downloaders for them and then schedules them for installation. That schedule will work on a series of windows that you specify so that installation doesn’t disrupt normal office activities. It also orders patches accounting for any patch dependencies. Finally, if there is no patch available for the discovered vulnerability, Vulnerability Manager Plus provides a script that will implement a workaround.
Many system weaknesses are due to poorly managed device settings. Vulnerability Manager Plus includes a Configuration Manager that will reorganize those settings and then prevent changes to them. It will also examine all ports and ensure that those not in use are closed. Those that need to be opened will be password protected where possible.
The vulnerability scanner also produces a risk assessment of all of the software that it discovers. In some cases, it will show that a package makes the entire system vulnerable to attack and should be removed.
Who is it recommended for?
ManageEngine provides the Free edition of Vulnerability Manager Plus for small businesses with up to 25 endpoints. This delivers all of the functions available in the Professional edition, which includes the configuration scanning and repair functions. The Enterprise plan adds on the patch manager and compliance reporting.
Comprehensive Endpoint Coverage: Scans endpoints running Windows, Linux, and, with the top package, devices running macOS, for a wide range of vulnerabilities.
Pros:
- Automatic Problem Resolution: Capable of fixing system misconfigurations and applying necessary patches automatically, reducing the administrative burden.
- Dynamic Device Discovery: Automatically identifies new devices on the network, facilitating seamless security management without manual device registration.
- Prioritized Vulnerability Reporting: Ranks vulnerabilities by severity, allowing IT teams to focus on the most critical issues first.
- Configuration Management: Includes tools to adjust and lock down device configurations, preventing unauthorized changes and closing unused ports.
- Customizable Automation: Gives administrators the flexibility to select which repair actions are automated, tailoring the system’s response to the organization’s policies.
Cons:
- Lacks Cloud-Based Option: Available only as an on-premises solution, which may not suit organizations looking for cloud-based vulnerability management services.
Vulnerability Manager Plus installs on Windows and Windows Server. It is available in three editions: Free, Professional, and Enterprise. The Free version is limited to managing 25 devices. The Professional edition is suitable for handling a LAN, and the Enterprise edition will cover multiple sites. You can get a 30-day free trial of the Professional edition.
6. ESET Protect MDR (FREE TRIAL)
Best for: Automated detection and remediation of vulnerabilities
Relevant for: MSPs and security teams in mid to large-sized organizations.
Price: The Premium version costs $69.99/year for three devices, while the Protect Complete version costs $287.72/year for five devices.
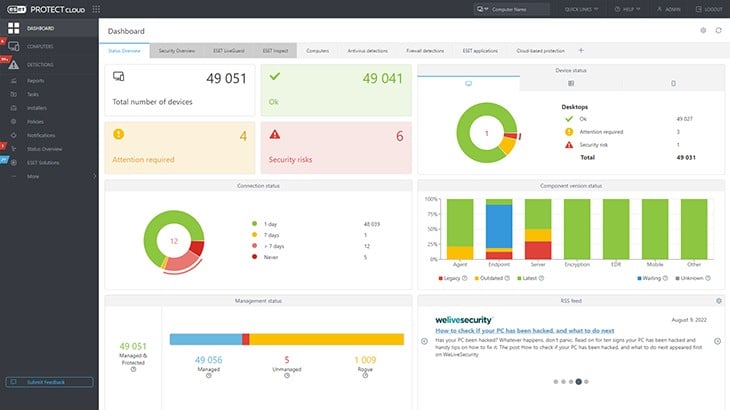
ESET Protect MDR is a managed detection and response service that adds the services of security technicians to a range of endpoint protection and cloud security systems. The options on this menu of services include a vulnerability scanner that has an automatic patch manager associated with it.
Key Features:
- Comprehensive Vulnerability Search: Targets a broad range of vulnerabilities, searching for over 35,000 potential security issues.
- Automated Software Updates: Includes an automatic patch manager to update out-of-date software, reducing vulnerabilities.
- Prioritization of Threats: Organizes discovered vulnerabilities by severity, enabling focused and efficient remediation efforts.
Unique buying proposition
ESET combines vulnerability tracking with managed detection and response to offer comprehensive monitoring of your endpoints. It automatically identifies vulnerabilities and prioritizes them. Moreover, it integrates threat response and patching to provide active threat mitigation.
Feature in Focus: Dynamic Patch Automation
The dynamic patch automation feature uses agent-based scanning to detect missing patches and outdated software. More importantly, it groups similar software with missing patches and uses policy-driven tasks to deploy them.
Why do we recommend it?
ESET Protect MDR provides the services of a team of cybersecurity experts as a managed service. The security operations center uses ESET software to provide security monitoring. This package includes a vulnerability scanner and a patch manager to resolve out-of-date software. The cybersecurity team will produce solutions for all other discovered weaknesses.
The vulnerability scanner can be run on demand or set up to run regularly on a schedule. The console for the service is based in the cloud and end clients are able to see there the discovered vulnerabilities. This console is central to the ESET Protect system and is available for those customers who prefer to buy the software without the managed service.
The weaknesses that the vulnerability scanner discovers are ordered by priority, with the most severe problems appearing first. This enables the technicians to tackle the biggest issues first.
Managed service providers can use this system to service their clients without the need for the ESET SOC team. This is because the cloud-based console that centralizes all of the functions of the ESET package is available in a multi-tenant architecture. This keeps the data of MSP clients separate.
The ESET Protect software includes endpoint protection software that identifies malware and intruders. This endpoint unit will also implement responses to shut down detected threats. Higher plans of the ESET Protect package add on a central, cloud-based threat hunting system. This can also be set up to automatically implement responses. These solutions are communicated to the ESET endpoint agent and also to third-party security tools.
The endpoint unit in the ESET Protect package is available for mobile devices as well as for computers. It will run on Windows, Linux, macOS, iOS, and Android.
Who is it recommended for?
The MDR package is suitable for businesses that don’t have cybersecurity specialists on staff. It is also a cost-effective solution because the managed security service provider is able to benefit from efficiencies by using the same staff to monitor multiple clients. The ESET Protect software is also available without the MDR service for companies to use themselves and for MSPs for security monitoring for their clients.
Pros:
- Managed Detection and Response: Offers expert cybersecurity services, adding human expertise to sophisticated software solutions.
- Versatile Endpoint Protection: Provides robust security for a variety of platforms including Windows, Linux, macOS, iOS, and Android.
- Cloud-Based Central Console: Features a unified, cloud-based management dashboard accessible for both direct customers and MSPs.
- Integrated Threat Hunting: Higher tiers include advanced threat hunting capabilities with automated response options to swiftly address detected issues.
- MSP-Friendly Architecture: Supports multi-tenant configurations, allowing MSPs to securely manage multiple client environments.
Cons:
- Limited Trial Options: Does not offer a free trial, potentially hindering initial evaluation for prospective users.
The MDR service can be combined with any of the editions of ESET Protect and so there is no free trial for the entire package. However, once you have decided on the level of service you require, a 30-day free trial is available for that edition. The starting point for your investigation is to contact ESET
7. SecPod SanerNow
Best for: End-to-end automation remediation.
Relevant for: MSPs and IT teams in large enterprises.
Price: Negotiated price, based on the number of endpoints used.

SecPod SanerNow is a SaaS package that is hosted in the cloud and performs security protection for networks, endpoints, and cloud platforms. The system requires agents to be installed on the protected endpoints and cloud platforms. These gather information that is uploaded to the SanerNow server to create hardware and software inventories.
Key Features:
- Extensive Vulnerability Coverage: Scans for over 160,000 weaknesses, with daily updates to the vulnerability database.
- Rapid Deployment and Scanning: Utilizes endpoint agents for quick installation and simultaneous scanning, reducing system impact.
- Integrated Patch Management: Automatically manages patches for identified software vulnerabilities, streamlining the remediation process.
Unique buying proposition
SanerNow is a comprehensive cloud console that offers vulnerability scanning, prioritization of risks, patching, and configuration management. Such a unified approach is cost-effective and reduces tool sprawl. At the same time, it automates the complete vulnerability management lifecycle.
Feature in Focus: Integrated Security Controls
SanerNow comes with built-in security controls that can harden configurations by applying controls in real-time. Essentially, it maps the detected risks to NIST and CIS benchmarks, and based on the provided recommendations, it applies the appropriate controls.
Why do we recommend it?
The SecPod SanerNow vulnerability manager is a cloud-based system but it is able to provide internal network scanning through the installation of an agent. It can scan network devices and also endpoints running Windows, macOS, and Linux. The tool can also scan cloud platforms. The package includes a patch manager.
Endpoint agents are available for Windows, macOS, and Linux. All installed agents run in parallel when operating in vulnerability scanner mode. This simultaneous operation means that a standard system scan takes only five minutes to execute. One agent is nominated as a network vulnerability scanner. A Continuous Posture Anomaly Management unit in the platform performs vulnerability scanning for cloud services.
The vulnerability manager works from a list of weaknesses that is maintained on the SecPod server. This has a total of 160,000 conditions to look out for and it is revised daily to account for newly discovered threats. Scanning can be run continuously.
The discoveries of the scanners are uploaded to the SecPod cloud server where they are assessed. The console for the SanerNow system displays a summary of vulnerability scan results that groups discovered weaknesses by severity. This provides a prioritized list of problems that need to be dealt with.
Each vulnerability list entry suggests solutions when the issue is caused by lax device configurations. As the administrator fixes these weaknesses, the rerun of the vulnerability scan will update the console report and show a reduced number of vulnerabilities.
Security weaknesses that are caused by outdated software or operating systems can be dealt with automatically by the patch manager that is included in the platform. The SecPod server regularly checks the producers of operating systems and software packages for patches. When they are available, the server copies over the installers, verifies them, and then stores them in a library.
The patch manager instance running for an account holder analyzes the version numbers of discover software to identify which can be patched. In these cases, the patch is scheduled in the account patch management console and then rolled out to the relevant endpoints as soon as possible. The patch manager relies on a maintenance calendar that the account holder needs to set up.
Who is it recommended for?
SecPod provides per-device pricing for SanerNow, which makes it accessible for businesses of all sizes. The package is run in the cloud as a SaaS package with no upfront installation costs. This is a suitable service for all types and sizes of businesses and it provides an option for continuous vulnerability scanning.
Pros:
- Cloud-Based Efficiency: Delivers a comprehensive security solution as a cloud service, facilitating easy setup and management.
- Cross-Platform Support: Offers agent-based protection for Windows, macOS, and Linux, ensuring broad endpoint coverage.
- Prioritized Problem Resolution: Generates reports that categorize vulnerabilities by severity, aiding in efficient risk management.
- Continuous Monitoring: Provides the option for ongoing scanning, ensuring that systems remain secure against new and evolving threats.
- Compliance Assistance: Includes features for compliance reporting, helping businesses adhere to regulatory standards.
Cons:
- Selective Patching: Applies patches to a predetermined list of 400 software titles, which may not cover all applications used by an organization.
All of the activities of the vulnerability scanner and the patch manager are logged. These records are stored and will provide compliance reporting for HIPAA, PCI DSS, NIST 800-53, NIST 800-171, and ISO. You can assess the SanerNow system with a 30-day free trial.
8. OpenVAS
Best for: Script-driven vulnerability detection and remediation.
Relevant for: Security engineers integrating automatic scans into CI/CD pipelines.
Price: Free
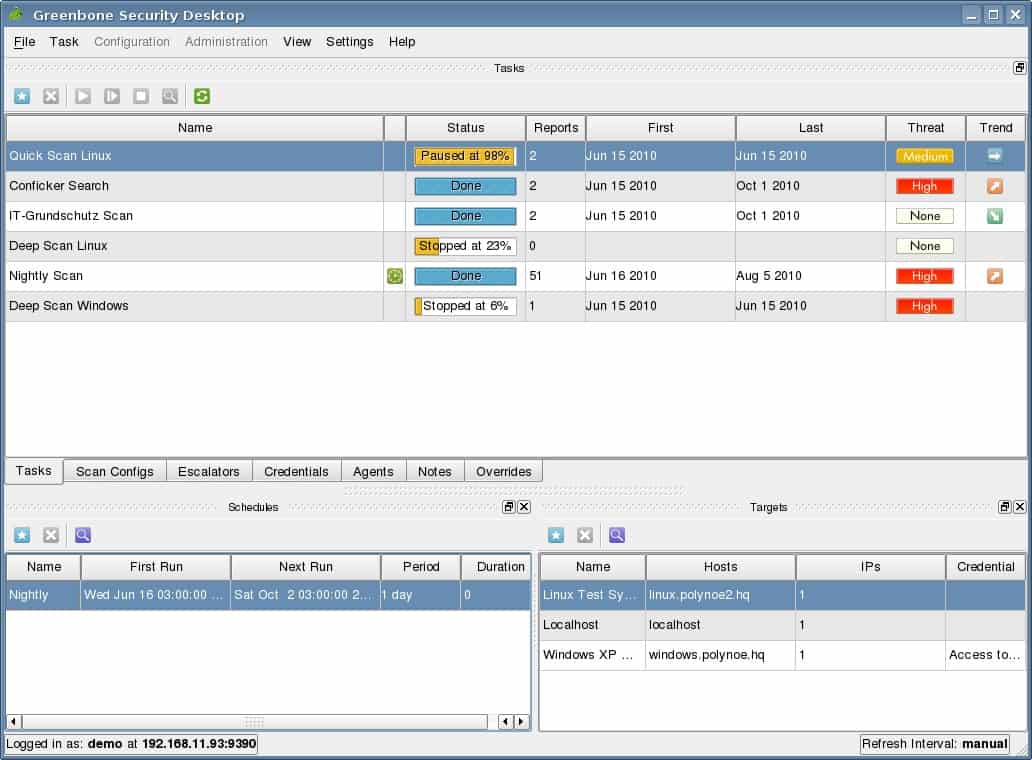
The full name of OpenVAS is the Open Vulnerability Assessment System. This is an open-source project, which means it is free to use. You might not jump straight to this option because some businesses have a policy of only using software that is professionally supported. OpenVAS doesn’t have that feature. However, as it is free, you could install it and use it as a benchmark to judge the other vulnerability management tools you test. It isn’t unreasonable to expect that a paid product should be better than this free scanner.
Key Features:
- Open Source Accessibility: Offers a robust vulnerability scanning solution without any cost, encouraging widespread use and customization.
- Extensive Vulnerability Coverage: Features a comprehensive database of over 50,000 network vulnerabilities for thorough security assessments.
- Community Support: Benefits from an active user community for advice, tips, and shared network vulnerability tests (NVTs).
Unique buying proposition
This is a free vulnerability engine that offers detailed scanning using an extensive plugin library. It combines both authenticated and unauthenticated scans with custom configurations, which means you can customize the tool to meet your specific requirements. It also supports automation through CLI and API.
Feature in Focus: API-driven Task Management
OpenVAS’s API and CLI-based automation is its strength. Many tasks, like creating targets, configuring scan profiles, and generating detailed reports, can be done through Python scripts. The advantage is that you can customize the workflows for your needs.
Why do we recommend it?
OpenVAS is a highly respected free, open-source vulnerability scanner. Like many successful open-source tools, this package is maintained by a for-profit business. Greenbone tends to use OpenVAS as a marketing tool for its paid systems. So, you will be pushed to buy the Greenbone Enterprise Appliance instead.
The active community that uses OpenVAS is contactable through a community message board. That can be a good source of guidance on using the tool and vulnerability assessments in general. In addition, the vulnerability database is composed of network vulnerability tests (NVTs). Other users of OpenVAS supply these, and the list includes more than 50,000 conditions.
There is a paid version of OpenVAS, which is called Greenbone Vulnerability Management. That has a commercially gathered NVT database and also provides professional support. However, that product is challenging to acquire because Greenbone doesn’t sell its products direct.
OpenVAS installs on Linux, and it is integrated into Kali Linux. Therefore, it is possible to run it on Windows over a VM. This system has a GUI interface and can also be used as a command-line utility.
Who is it recommended for?
OpenVAS is referred to by its supplier as the Greenbone Community Edition because the company is trying to gain brand recognition from its investment in the free tool. OpenVAS is relatively easy to use and it doesn’t take much training to understand how to set up a scan.
Pros:
- Cost-Effective Security Tool: Provides a free alternative to commercial vulnerability scanners, making it accessible for businesses of all sizes.
- Adaptable and Expandable: As an open-source project, it allows for modifications and enhancements to meet specific user needs.
- Integrated into Security Platforms: Available as part of Kali Linux, offering a streamlined setup for security professionals.
- Dual Interface Options: Supports both graphical and command-line interfaces, catering to different user preferences.
- Benchmarking Capability: Can be used to evaluate the effectiveness of other vulnerability management tools, setting a standard for comparison.
Cons:
- Lacks Professional Support: As a free tool, it does not come with the professional support services often available with paid solutions.
- No Built-in Patch Management: While it identifies vulnerabilities, it does not include features for automated patch application, requiring additional processes for remediation.
The vulnerability scanner is integrated into Greenbone Security Manager as the trial version, which you can download for free.
Our Methodology in Choosing the Best Vulnerability Management Tools
We strive to provide the most accurate information to help you make informed decisions that will positively impact your operations. To achieve this goal, we do an in-depth analysis of the features and test the tools hands-on, where possible. Additionally, we combine user reviews and applicability across use cases to provide a detailed review of each tool. Our methodology for selecting the best vulnerability management tools involves the following:
- Breadth of Coverage – One of the first things we looked at was the breadth of coverage. Ideally, the tools we recommend must cover every endpoint, operating system, and environment to provide the flexibility you need to use them across multiple real-world scenarios.
- Technical Capabilities – Can the tool accurately identify the vulnerabilities? Does it provide the context and prioritization that can speed the resolution process? We evaluated the technical capabilities of different tools against such questions to identify the most technically capable ones.
- Automation – Another core aspect we looked into was automation, as we want the tool to reduce human interference in vulnerability management.
- List of features – We prioritized tools that combine multiple features like patch management, configuration management, report generation, ticketing, and more to reduce tool sprawl.
- Vendor Support – We looked for vendors that have dedicated customer support teams and well-developed documentation, so you can get the timely support required for using the tool.
- Usability – We picked tools that have a user-friendly interface and are intuitive to use for most people.
Our Broader B2B Software Methodology
The above factors align with our broader B2B software methodology, where we evaluate the features of every platform to ensure they align with the common requirements of most organizations. Moreover, we look at factors like scalability, applicability across multiple environments, usability, and more.
Learn more about B2B software methodology.
Why Trust Us?
Comparitech is known for its unbiased reviews, as our goal is to provide all the facts to help you make the right decision. We lay down the methodology we use and the factors we consider while selecting tools, so you can better align our methodology with your requirements. Due to this transparency, millions of B2B decision makers trust our reviews.
Vulnerability Management FAQs
What is a vulnerability management tool?
A vulnerability management tool scans a system, looking through every operating system and software package for known weaknesses that hackers can exploit. Many weaknesses are already known by software producers and they can be fixed by applying a patch. Other weaknesses relate to system settings, which can be corrected to tighten security.
How do you manage vulnerability management?
The management process for vulnerability management involves five phases:
- Scoping
- Definition of roles and responsibilities
- Select tools for the task
- Draw up project requirements and service level agreements
- Conext assessment
Why do we need vulnerability management?
Vulnerability management ensures that all of your IT assets are hardened against attacks. You should be careful not to make hacker and malware attacks easy to implement. If your system is secure, it is less likely to be damaged by malicious activity.




