What is a Secure Web Gateway?
A Secure Web Gateway (SWG) is a cybersecurity solution designed to protect organizations from web-based threats while enabling secure internet access. Acting as an intermediary between users and the internet, an SWG enforces security policies, monitors web traffic, and blocks malicious activities. This ensures that users can browse the web and use cloud-based applications without exposing the organization to risks like malware, phishing attacks, or data breaches.
Here is our list of the best Secure Web Gateways:
- Check Point’s SASE SWG EDITOR’S CHOICE This Web protection system blocks access to suspicious or inappropriate websites and tracks user activity. This is a cloud-based service. Get your free demo.
- NordLayer (FREE DEMO) This VPN-based package provides user, application, and internet security in an easy-to-administer package that offers single sign-on and 2FA. You can get a demo.
- ManageEngine Browser Security Plus (FREE TRIAL) This service catches Web-based attacks by paying close attention to browser add-ons and identifying malicious interfaces. Start a 30-day free trial.
- CleanBrowsing This cloud-based service takes the opportunity of the DNS fetch phase of browsing to check out requested Web pages for malicious content.
- Zscaler Web Security Cloud-based web protection system that includes URL and DNS filtering, a firewall, antivirus, and anti-spam.
- N-able Mail Assure Cloud-based email threat protection system that also scans outbound emails for data loss events.
- Symantec Secure Gateway Hosted web gateway with cloud access security, data loss prevention, advanced threat protection, and email security.
- Forcepoint ONE SWG Cloud-hosted web access gateway with URL filtering, data loss prevention, and advanced malware detection.
- FortiProxy Great for SMEs, this web threat intelligence service includes web filtering, DNS filtering, antivirus, intrusion prevention, and data loss prevention.
- Barracuda Web Security Gateway Remote content filter that blocks malicious code even when it is encrypted.
- Censornet Web Security A content filter with an emphasis on blocking offensive text and images. Can process encrypted transmissions.
- Skyhigh Secure Web Gateway This cloud-based edge service provides content filtering, defense against Web-based threats, and outbound traffic scanning for data loss prevention. This service can be combined with other Skyhigh Security products.
- Sophos Web Gateway This traffic monitor inspects both incoming and outgoing internet transmissions to block threats and prevent data loss.
Secure web gateways combine multiple security features, such as URL filtering, application control, anti-malware scanning, data loss prevention (DLP), and encrypted traffic inspection. These tools help maintain robust security for employees, whether they are working within the corporate network or remotely.
Why Do You Need a Secure Web Gateway?
- Protection Against Web-Based Threats Cyber threats such as malware, ransomware, and phishing campaigns often originate from malicious or compromised websites. An SWG blocks access to these sites in real-time, ensuring users are shielded from dangerous content.
- Data Loss Prevention An SWG can monitor outbound traffic to prevent sensitive information from being accidentally or maliciously leaked. This is critical for industries that handle regulated data, such as healthcare, finance, or retail.
- Control Over Internet Usage With features like URL filtering and application control, an SWG allows organizations to enforce acceptable use policies, restricting access to non-work-related or high-risk websites.
- Inspection of Encrypted Traffic Many threats now hide in encrypted traffic (HTTPS). An SWG decrypts and scans this traffic for threats, maintaining a balance between security and privacy.
- Support for Remote Workforces As remote work becomes the norm, SWGs ensure consistent security for users outside the corporate firewall, reducing the attack surface.
By incorporating a secure web gateway, organizations can proactively safeguard their networks, protect their data, and maintain compliance with industry regulations.
The Best Secure Web Gateways
Our methodology for selecting a Secure Web Gateway
We reviewed the market for network protection systems against Web-based attacks and analyzed tools based on the following criteria:
- Searches for and defense against malware
- Spam filters for email systems
- Blocks on phishing strategies
- Controls over the content that can be displayed on corporate browsers
- Detection of spoofing and impersonation attempts
- A free trial or a demo account for a no-risk assessment period
- Value for money represented by a comprehensive Web defense at a fair price
With these selection criteria in mind, we identified cloud-based network protection services that guard against Web-based threats.
All of the tools mentioned on this list are equipped with advanced threat intelligence capabilities to discover new threats and zero-day malware.
1. Check Point’s SASE Secure Web Gateway (ACCESS FREE DEMO)
The Check Point’s SASE Secure Web Gateway operates a Web filtering system that protects the business’s network and endpoints from malicious infections that can be transmitted through websites.
Key Features:
- An edge service: Hosted in the cloud
- Filters all internet traffic: Checks all internet traffic into and out of a protected business
- Covers multiple sites: Front several sites and home-based workers with one account
- Firewall rules: Blacklist websites by type, name, name element, or IP address
- Activity monitoring: Track the Web access of each user
Why do we recommend it?
Check Point’s SASE Secure Web Gateway is an add-on service on a platform of tools that can be configured to provide a range of system security strategies. You can create a Zero Trust Access system, a SASE, or an SD-WAN by assembling together different utilities in the package.
The automatic site access blocks also extend to the detection of fake websites that impersonate legitimate sites with login screens. These sites are used to reap access credentials from victims. The Secure Web Gateway protects corporate accounts from hacking by making these imposter sites impossible to reach.
The tool also enables system administrators to set up custom filtering rules. These can be used to enforce company policy on Web usage at work. It enables the prevention of company facilities from being used to access inappropriate sites. Attempts to access banned sites are logged.
This system is a cloud platform so the administrator dashboard can be accessed through any standard Web browser. The software isn’t limited to the protection of employees in one location as it can extend its service to the devices of home-based workers.
Who is it recommended for?
The Check Point’s SASE system is very easy to use. It provides you the security you need without imposing a straight-jacket of terminology. The service is cloud hosted and priced with a combination of a rate per user and per gateway, which makes it affordable to even the smallest company.
Pros:
- Part of a wider menu of services: The full Perimeter 81 package offers a range of system protection services
- Protects internal corporate traffic: Creates an SD-WAN or a SASE
- Easy to set up: Each user gets an access app
- Creates a single corporate identity: Get a single IP address to represent multiple sites
- Scans incoming Web page code: Identifies malicious content
Cons:
- No free trial: Offers a demo instead
The system installs a background agent on each protected device. This ensures that protection can be extended to individual devices, not just those on the company network behind a firewall.
The service strengthens protection against types of attacks that most firewalls cannot spot. The system is offered as part of a bundle of services that includes DNS filtering and internet privacy.
Check Point’s SASE presents its services in bundles and there are four plans. The first of these, called Essentials, doesn’t include the SWG service. However, the three other plans do. All plans are protected by a 30-day money-back guarantee and you can get a demo to assess the Check Point’s SASE services.
EDITOR'S CHOICE
Check Point’s SASE is our top pick for a secure Web gateway because it provides this service as part of a framework of hybrid network security systems. The secure Web gateway provides a reverse firewall, examining the outgoing traffic of users and the remote systems that they try to access. The SWG provides an opportunity to implement security policies that block access to unauthorized SaaS packages and websites. This control can be useful for limiting the opportunity to process data, which is an important restriction for data integrity protection. Web page code is checked as it travels through the Check Point’s SASE server to block infections and phishing attempts.
Download: Access Free Demo
Official Site: https://www.sase.checkpoint.com/demo
OS: Cloud-based
2. NordLayer (ACCESS FREE DEMO)
NordLayer is a package that provides connection security and application access controls. This system is based on a package of VPNs that secure the connections between users and applications. Those applications can be hosted on your servers or they can be SaaS packages.
Key Features:
- Cloud-based traffic hub: All your user traffic goes through the NordLayer server
- Application access control: Authentication happens on the NordLayer server
- Deep packet inspection: Incoming Web code is scanned for threats
- Web access controls: Block or filter Web access
Why do we recommend it?
NordLayer evolved from the NordVPN service. Each user gets an app for any device and this looks a lot like a VPN client. This app also presents the user with a lost of applications to access. They aren’t able to see those systems to which they haven’t been given permission.
Each user downloads an access app onto any device that will be used for company business. This could be a company-owned workstation or a home-based computer. The app is available for Windows, Linux, macOS, iOS, and Android.
The system administrator gives each user access to a list of applications and when the user logs in from any computer through the app, that list appears as a menu of services, clicking on a menu entry ripples through the app authentication to the application, so the user only has to log in once to use all allocated systems.
All communication between users and applications is carried through a VPN connection to the NordLayer cloud server from where authorized users are forwarded to the host of the application. Users accessing the Web also have their traffic carried through the NordLayer server. Those requests are made by NordLayer on behalf of the user, so the return address is that of the NordLayer server.
When the code for a requested Web page arrives at the NordLayer server, it is scanned for threats. This is how the Secure Web Gateway service is threaded into the operating procedures of the NordLayer system. Cleared traffic is passed on to the user over a VPN-secured connection.
NordLayer offers a dedicated IP address that acts as a filter. This platform is a cloud server that offers a dedicated IP address, providing a gateway for all traffic coming into a company. The endpoints protected by the gateway can be anywhere: on multiple sites or in the homes of remote workers. The tool can even protect mobile devices. All traffic from the business’s users passes out through the NordLayer server and all returning traffic returns through it. The server scans Web pages coming in and removes any malicious code. Outgoing traffic is scanned for attachments to block data disclosure
Who is it recommended for?
This system is priced per user with a minimum team size of five. This makes the NordLayer service suitable for all sizes of businesses. The SWG service is only available in higher plans, which have an additional charge per company for a dedicated server and IP address, which turns the proxy server into a firewall.
Pros:
- Website blacklisting: Block access to sites by type, keyword, name, or IP address
- Cloud-based firewall: All incoming traffic goes through the NordLayer server for inspection
- Reverse firewall: Inspect all outgoing traffic for data loss prevention
- Activity monitoring: Track the Web activity of each user
Cons:
- No self-hosting option: You can’t run this service yourself
The cheapest plan of NordLayer, called Lite, doesn’t include the full firewall service but it does include the ThreatBlock package, which blocks malicious and infected websites. This is a basic SWG and higher plans get an enhanced version with deep packet inspection capabilities. There isn’t a free trial for NordLayer but you can get a demo.
3. ManageEngine Browser Security Plus (FREE TRIAL)
ManageEngine Browser Security Plus, strictly speaking, isn’t a secure Web gateway. However, it provides a similar service because it blocks attacks on endpoints that can be launched through Web browsers.
Key Features:
- Examines browser plug-ins: Will remove unauthorized utilities
- Compatible with many browser brands: Works with Chrome, Firefox, Microsoft Edge, and others
- Monitors traffic to browsers: Can block infected Web pages
Why do we recommend it?
ManageEngine Browser Security Plus is an interesting alternative to a secure Web browser because it performs endpoint protection from within the network. This is a good option for businesses that don’t like cloud-based services. This tool works on Windows Server and it scans each endpoint to discover its browsers. The service then assesses the plug-ins for each browser, looking for unauthorized systems that could provide gateways for malware or intruders.
This system is compatible with all of the major browser brands, including Firefox, Chrome, Internet Explorer, Microsoft Edge, Yandex, and Brave. The service records browser usage and offers the opportunity to enforce security policies. The tool can be useful as part of a wider data loss prevention strategy. However, that would require the edition of a sensitive data manager.
You can use the Browser Security Plus tool to blacklist sites that are not appropriate for use on your premises. The package also offers browser isolation to guard against infected Web pages. However, that feature is only available for Internet Explorer and Microsoft Edge. It is possible to restrict the browsers that can be used on your endpoints, thus, preventing users from downloading their preferred browsers.
Other security features in the package include a block on downloads, whether initiated by the users or attempted by functions on a Web page. The plug-in controller can also prevent downloaders from being installed within the Web browser.
Who is it recommended for?
This package is suitable for businesses of all sizes and there is a Free edition for small businesses. That version is limited to managing the browsers on 25 computers. Other than that capacity restriction, the Free edition has all of the features of the paid Professional edition.
Pros:
- Easy to use: The console for the tool includes guides and wizards
- Provides browser controls: Prevents downloading and access to inappropriate sites
- Data loss prevention: Can be used to restrict data uploads
Cons:
- No version for Linux: Only available for Windows and Windows Server
Although there is a Free edition for Browser Security Plus, you would be better off starting with the 30-day free trial of the Professional edition. If you decide not to buy at the end of the trial period, the package will impose a 25-computer restriction, turning it into the Free edition.
4. CleanBrowsing
CleanBrowsing offers a different path to Web security within a network. Rather than guarding a network and filtering all traffic, the CleanBrowsing service focuses on the Web pages that are requested from browsers operating within a business.
Key Features:
- Operates as a DNS service: You just need to change your network settings to access the service
- Preset filters: Choose categories of websites to block
- Custom blacklist: Add in your own website bans
Why do we recommend it?
CleanBrowsing is a content filter and URL blocking service that is particularly strong at preventing access to adult content. This system is very easy to set up thanks to its pre-set filters that you turn on to ban thousands of websites at a time.
The ClearBrowsing system operates as a DNS resolver. When a user requests a Web page, the browser first interprets that page’s URL into an internet address. The DNS resolver provides this address by referring to a DNS server. However, before returning the retrieved address, the CleanBrowsing system first checks out that page for infection, malicious content, or impersonation.
Integrating this service involves simply nominating the address of the service for the browser’s default DNS server. However, the redirection can also be set up by changing the settings of the network router, thus applying the DNS service to all devices on the network.
CleanBrowsing operates from data centers located around the world. These distributed locations provide faster response times and also endure constant availability.
Who is it recommended for?
The target market for CleanBrowsing seems to be private individuals rather than companies. However, there is a Business edition. This offers a lot of capacity with an allowance to use the tool on 100 devices. Small businesses can just access the free service and set it up on each managed device, including mobile equipment.
Pros:
- Easy to set up: Guided onboarding
- Efficient processing: Doesn’t slow down internet access
- Activity monitoring: See your business’s traffic and adjust filters
Cons:
- We filtering only: Won’t block P2P activity
CleanBrowsing is available for free. This service is probably better for home use and for small businesses. It will block adult content as well as provide phishing protection. The paid version is available in three editions. These allow you to set up your own filtering rules as well as getting the adult content and phishing blocks.
With the three paid plans you can cover a large number of devices and include endpoints into one monitoring plan no matter where in the world they are located. The system can also be applied to mobile devices. To check out the CleanBrowsing system, access the free version of the tool.
5. Zscaler Web Security
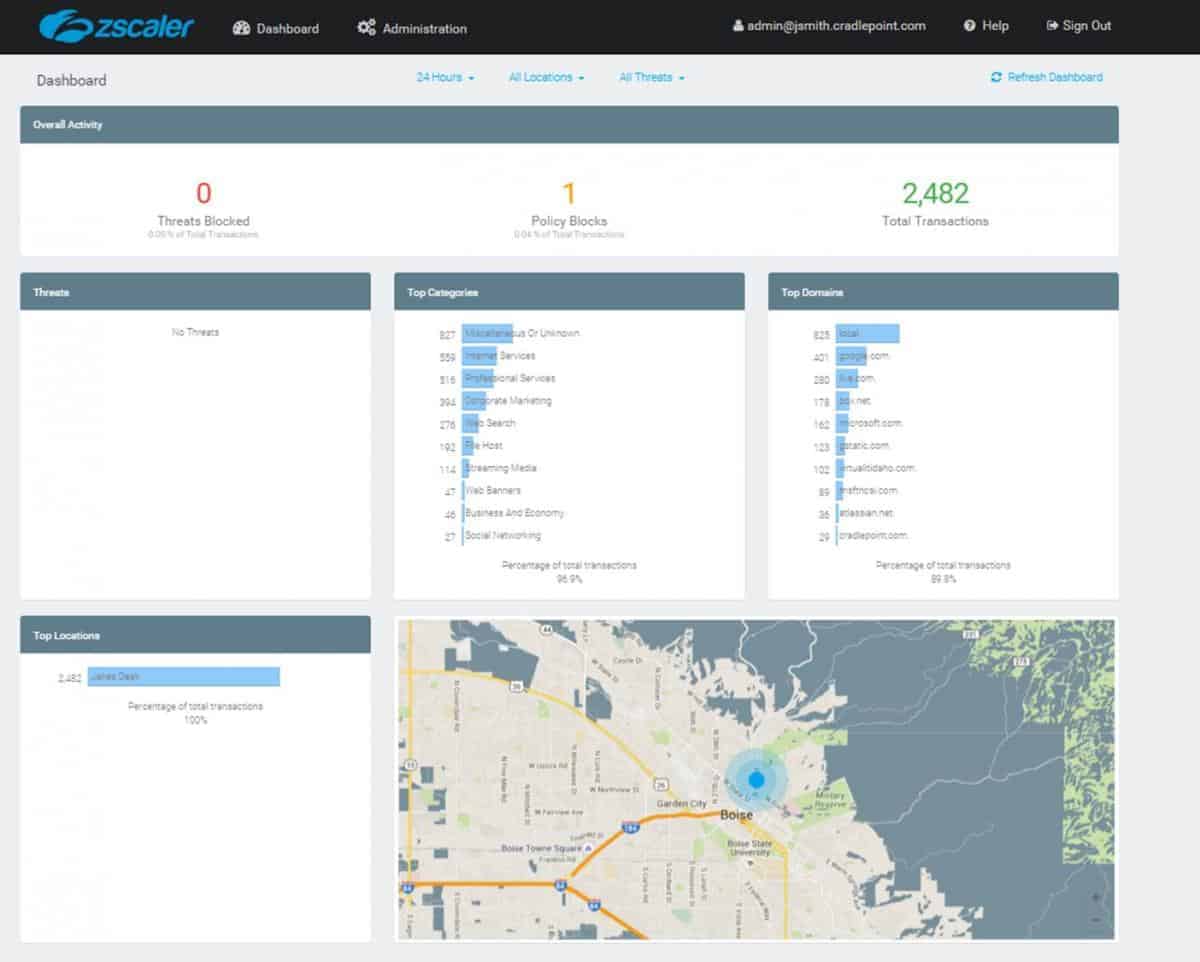
Zscaler Web Security is a cloud-based web security gateway that comes with URL filtering, a firewall, cloud-based application control, antivirus, anti-spam, DNS filtering, and more. One of the perks of being part of the cloud gateway is that any threat detected by any user is automatically blocked for all customers – there are over 120,000 security updates every day to protect against the latest threats. The tool can also inspect SSL traffic that many other platforms struggle to analyze.
Key Features:
- Connects users to applications: Acts as a hub, based on the cloud
- Blocks incoming connection requests: Acts as a firewall
- Examines Web access: Blocks access to a blacklist of sites
Why do we recommend it?
Zscaler Web Security uses AI in its methods to detect and block phishing, Command & Control connections, and malicious website detection. The service keeps confirming that each device has been safeguarded by scanning it for infection. The tool also provides improvements to browser settings and other utilities that connect to the internet.
The antivirus takes signatures from over 60 threat feeds to identify new threats. However, the software isn’t limited to monitoring security events; you can also optimize your network’s performance. The bandwidth control capabilities of Zscaler Web Security can prioritize important applications over less important traffic.
To protect your files against loss or destruction there are a handful of data protection features. Implement Data Loss Prevention to protect user data. There is also a Cloud Application Security Broker to control user access to applications and File Type Controls to determine what files can enter or exit the network.
Who is it recommended for?
Zscaler is a platform of cybersecurity tools and it provides a similar list of security solutions as that offered by Perimeter 81 – SASE, ZTA, and SD-WAN. This platform is not as easy to understand as the Perimeter 81 service. You need cybersecurity knowledge to work out which products to buy and how to set them up.
Pros:
- Scans incoming code: Identifies malicious code in a Web page’s HTML
- Data loss prevention: Acts as a reverse firewall
- Activity tracking: Logs user behavior for insider threat detection
Cons:
- No free trial: You can get a demo
Users can connect to the program through the Zscaler cloud to browse safely from malicious attacks. The platform is scalable so that you aren’t limited by hardware if you need to manage more traffic. To view a quote for Zscaler you will have to contact the company directly. You can request a demo and a quote.
6. N-able Mail Assure
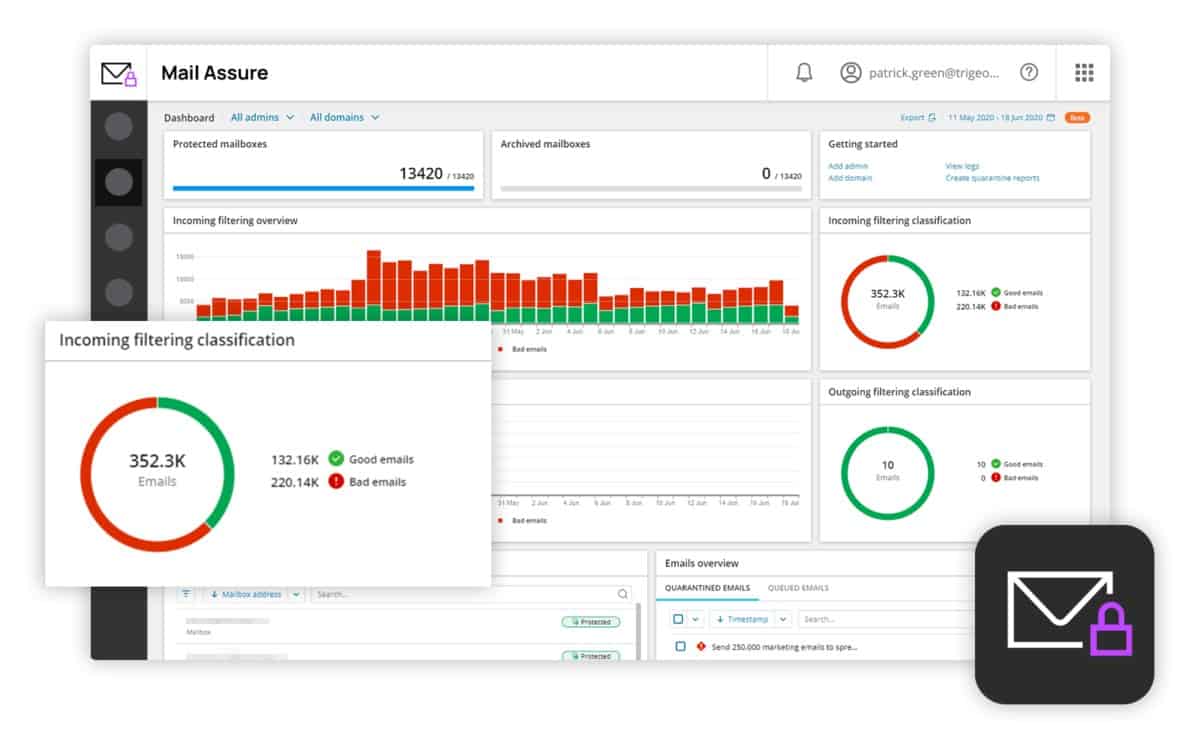
The N-able Mail Assure system is an edge service formerly supplied by SolarWinds MSP. MSPs can offer Mail Assure as an extra service to their clients. The MSP can include the oversight of technicians in its pricing plan when it proposes Mail Assure to its customers. Despite the fact that N-able markets this service to MSPs, there is no reason why in-house IT departments shouldn’t also deploy the Mail Assure system.
Key Features:
- Scans incoming emails for threats: Blocks phishing attempts
- Scans for malware: Looks through attachments
- Spam filter: Blocks tricks, advertising, and lures to fake sites
Why do we recommend it?
N-able Mail Assure is an email protection system that cuts out spam and detects phishing and other types of scams. The tool will block malicious links in emails and quarantine attachments to protect users. The tool also scans outbound emails to provide data loss prevention. A threat intelligence feed sharpens the service.
The Mail Assure system is hosted on N-able servers so all email traffic from the MSP’s clients needs to be channeled through that system via a VPN. Similarly, all incoming emails go to the Mail Assure server first and then travel on to the client’s system through the VPN.
When an email intended for the client arrives at the Mail Assure server, it scans for security threats, including spam, phishing attempts, address spoofing, impersonation, malicious content, and poisoned links.
N-able collates a threat intelligence database from all of the attacks that it encounters while serving all of its customers around the world. This centralized attack profile means that information on any threat identified in one part of the world is instantly available to protect all of the other Mail Assure users.
Apart from referencing the threat intelligence database, Mail Assure checks for typical attack signatures and also refers to a sourced mail address blacklist.
The edge service also provides continuity services and archiving. Encrypted archives of genuine emails are stored automatically and can be restored on demand. The continuity service extends to online mailboxes for all of the accounts on the protected system, which enables all users to continue to access and send emails even when the main email server is unavailable.
N-able Mail Assure is a system that is delivered from the cloud by a reliable provider and it provides business continuity service should your main email system go down. The Mail Assure service maintains a threat database with known spammers and hackers listed by IP address and domain. The tool also spots specific keywords and strategies that indicate phishing or infection attempts regardless of email source.
Who is it recommended for?
N-able is a brand that provides services for MSPs and the Mail Assure system is intended as a pass-through service to protect MSP clients. The system is cloud-hosted and pre-filters emails, passing on safe and disinfected emails to the recipient. IT departments could subscribe to the service as well.
Pros:
- Blacklisting: Maintains a list of known scammer domains and IP addresses
- Behavior detection: Looks for typical phrases known to be in use in fraudulent emails
- Designed for MSPs: Will protect the clients of managed service providers
Cons:
- No price list: You have to request a quote
The Mail Assure service will also protect online Office 365 email servers as well as onsite systems. N-able offers a free trial of Mail Assure.
7. Symantec Secure Gateway
Symantec Secure Gateway is a cloud-based web gateway designed to fit into an enterprise’s security stack. The solution combines a secure web gateway with data loss prevention, advanced threat protection, email security, and a cloud access security broker. As part of Symantec Secure Gateway’s advanced threat detection capabilities, you can authenticate users and inspect encrypted traffic.
Key Features:
- Protects hybrid systems: Examines traffic to on-premises and cloud services
- An edge service: Represents the protected client on the internet
- Filters traffic: Weeds out threats before passing on legitimate Web traffic
Why do we recommend it?
Symantec Secure Gateway manages user activity on the Web. It is an edge service and it mediates all traffic in and out of a site, including emails and social media platforms. The tool includes text and image scanning to spot scams and malware and it also scans outgoing traffic to block data theft.
To make sure that you don’t fall behind emerging risk factors, Symantec Secure Gateway uses real-time threat intelligence from the Symantec Global Intelligence Network. The Symantec Global Intelligence Network uses machine learning and image analysis to detect cyberattacks. The service processes more than 1.2 billion web requests every day with nine Security Operations Centers across the globe.
The Symantec Integrated Cyber Defense Platform that comes with Symantec Secure Gateway allows you to automate threat remediation. For example, identified threats can be blacklisted to minimize the network’s exposure to threats. Automation helps to shut down threats as quickly as possible.
Who is it recommended for?
This is a corporate solution and it is very detailed. The system is a high-end solution that includes AI and sophisticated scanning methods. This might push the service out of the price bracket for small businesses. Mid-sized and large businesses are more likely to be drawn to this system.
Pros:
- A global service: Analyzes traffic to many clients to identify threat patterns
- Protects Web and email: Filters out spam and phishing emails
- Data loss prevention: A reverse firewall that scans outgoing traffic for data movements
Cons:
- You can’t buy it direct: You have to look for a retailer
Symantec Secure Gateway is a good fit for those organizations that are looking for a security solution equipped to manage a hybrid computing environment. For pricing information, you will have to request a quote from the company directly. You can request a quote.
8. Forcepoint ONE SWG
Forcepoint ONE SWG provides a Web interface for all internet access by users. This is part of the Forepoint ONE package that includes protection for cloud services, email systems, Web access, and private apps. Methods used by the secure Web gateway include a remote browser isolation (RBI) service, which hosts the Web pages that users want to access on the Forcepoint server, which the users then view, creating a safety buffer.
Key Features:
- Deploys remote browser isolation: The user accesses a browser that is running on the Forepoint server
- Content Disarm and Reconstruction: Gathers all of the files for a Web page, strips out malicious files, and forwards the rest
- Data loss prevention: Scans outgoing traffic for files
Why do we recommend it?
Forcepoint ONE SWG is part of a platform of security services. Other tools in the plan provide configuration scanning for cloud services and also access controls with ero Trust application fencing. The tool scans downloads and email attachments and also operates in reverse to prevent data theft.
The solution also has a 100% accuracy at detecting attacks through fingerprinting meaning it is equipped against less obvious threats. In the event, an attack does get through or a disaster takes place, Forcepoint ONE SWG has data loss prevention to protect your data. You can effectively manage data loss prevention policies through one centralized console.
The package includes Web content filtering and threat assessments for contents and the sources of the Websites that the users access. This scanning and verification extends to email systems.
Who is it recommended for?
The Forcepoint ONE package is a comprehensive system that takes care of all possible cloud and Web-based threats. Forcepoint doesn’t publish its pricelist, so it is difficult to judge its affordability for small businesses. Companies that use cloud SaaS packages and also handle sensitive data will particularly need this package.
Pros:
- Resident in the cloud: Intercepts traffic before it gets to your system
- Sensitive data protection: Categorizes data and protects sensitive information
- A single point of security: Defend multiple sites and cloud services at one choke point
Cons:
- No free trial: You can get a demo
The Forcepoint ONE system is an edge service that is entirely resident in the cloud, so you don’t need to download any software to use the package. You can access a demo to find out more about the Forcepoint ONE SWG.
9. FortiProxy
FortiProxy is Fortinet’s dedicated Secure Web Gateway solution. FortiProxy offers antivirus, web filtering, a DNS filter, application controls, intrusion prevention systems, data leak prevention, content analysis, traffic shaping, caching, ICAP Client/Server integration, and VPN-access. It integrates into Fortinet’s Security Fabric to leverage sandboxing, zero-trust isolated web browsing and central logging & reporting.
Key Features:
- Part of the Fortinet group solution: Creates a multi-product security system
- Proxy system: Intercepts traffic before it gets to your systems
- Malware blocking: Blocks malicious code in Web traffic
Why do we recommend it?
FortiProxy is a product of Fortinet, which is a leading producer of firewalls. The star of the Fortinet stable is the FortiGuard hardware firewall and the company has copied this successful model by making the FortiProxy an appliance. This is an alternative strategy to the Cloud-based edge services offered by most of the tools on this list.
The Secure Web Gateway can deep-inspect SSL (hardware accelerated) and SSH traffic to reveal hidden threats. The L2/L3 deployment options are versatile for both transparent and explicit modes for Active/Passive clusters for fail-over and Active/Active clusters (scalable to a maximum of 8) with the option for single cache-collaboration storage.
FortiGuard Labs supports FortiGuard Threat Intelligence and there are over 200 researchers in 31 countries dedicated to discovering new threats. For example, over 150,000 websites are blocked every minute by the FortiGuard web filtering service. There is even the potential to blacklist or whitelist particular websites.
Authenticated web application control enables the user to set access policies to restrict user access. For example, the user can restrict access to social websites by user or group. The tool offers support for 3000 apps. Similarly, there is data loss prevention to stop sensitive files falling into the wrong hands (these files can also be watermarked or fingerprinted).
Who is it recommended for?
The hardware requirement for this tool means it has a high upfront cost to implement. The smallest model offered by Fortinet caters to 500 to 5,000 users, so this is not a solution for small businesses. However, Fortinet also offers the FortiProxy as a virtual appliance.
Pros:
- Email protection: looks for spam and phishing emails
- Available as an appliance: Buy a piece of hardware to host this service
- Combines with other Fortinet services: Load extra functions onto your appliance, such as load balancing and caching
Cons:
- No price list: You have to request a quote
FortiProxy aims at a high-end market and is purpose-built to support mid-sized and large companies. Its impressive 18Gbps in a single appliance provides protection against advanced threats without impairing network performance. To view a price for Fortinet you can request a quote from the company directly. You can also request a demo.
10. Barracuda Web Security Gateway
Barracuda Web Security Gateway is a web filtering tool for companies that want to block malware and viruses. The software can inspect SSL-encrypted traffic and remotely filter content on the internet. Barracuda Web Security Gateway uses threat intelligence, antivirus, and anti-spyware to cover a range of online threats.
Key Features:
- SSL offloading: The gateway becomes an encryption endpoint so it can decrypt and inspect content
- Web usage policy enforcement: Block the use of corporate facilities for leisure Web browsing
- Malware protection: Filters out malware before it gets to your users
Why do we recommend it?
Barracuda Web Security Gateway competes directly with FortProxy because this is also a network appliance. Like Fortinet, Barracuda offers a virtual appliance option as well. This tool provides SSL offloading which means that all secure We transmissions can be fully scanned before delivery to users.
For example, Barracuda Advanced Threat Protection (ATP) checks incoming files against a cryptographic hash database and blocks any content with malicious activity. Any files that don’t match are sent to a virtual sandbox where they can be verified at no risk to the wider network.
The platform also offers dashboards where you can not only monitor threats but also monitor user activity. There is also an alert feature so you receive notifications when a security event is kicking off. For post-event follow up there is a reporting feature that you can use to review the aftermath.
Who is it recommended for?
The smallest unit that Barracuda offers caters to 100 users. So, it caters to smaller businesses than the ForiProxy system but it still incurs upfront costs. The virtual appliance version is more accessible and it is also suitable for very large businesses. This system is suitable for companies that prefer to host their own security systems.
Pros:
- Email protection: Blocks spam and phishing attempts
- Global threat intelligence: Threat identification based on analysis of events from all clients
- Attack alerts: Get notified when a threat is detected
Cons:
- No price list: You need to ask for a quote
There are several versions of Barracuda Web Security Gateway to choose from including 210, 310, 410, 610, 810, 910, and 1010. Versions range from 150-250 Mbps throughput and 300-800 concurrent users to 3,000-5,000 Mbps and 15,000-25,000 concurrent users. You need to contact the company directly for pricing information. You can request a free trial version.
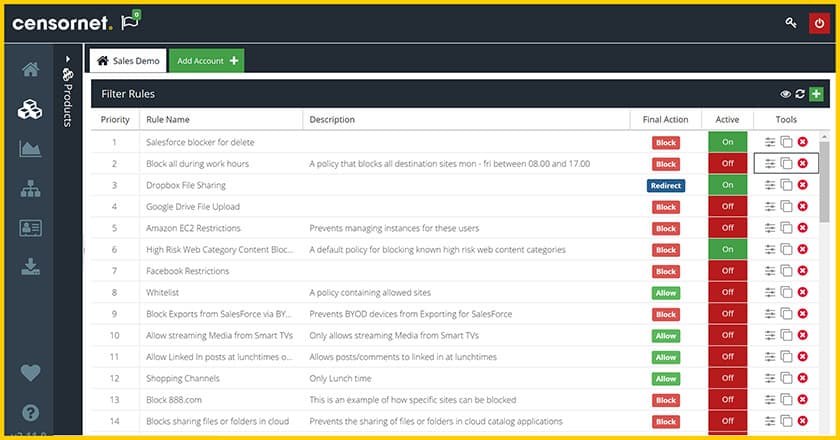
11. Censornet Web Security
Censornet Web Security is a web security cloud service that filters online content. The software blocks offensive content, illegal content, malware, and inappropriate images from being downloaded. The Image Content Analysis (ICA) add-on uses AI and deep learning to identify offensive, extremist, or adult images automatically with minimal false positives.
Key Features:
- Blocks inappropriate content: Anything not suitable for work is filtered out
- Detects malware: Removes malicious code from Web pages and emails
- Easy to use: Suitable for home use as well as for businesses
Why do we recommend it?
Censornet Web Security provides content filtering and threat defense for Web access. The tool is an edge service, so you don’t need to install any software on your servers and you don’t need a network appliance. The package extends protection to office guests that bring in their own devices.
Advanced anti-malware and threat intelligence address more complex threats. In addition, encrypted SSL / TLS traffic can also be processed giving protection against more complex threats. Censornet Web Security has an average response time of 35 ms meaning the end-user experience is highly responsive for employees.
To control security throughout the network, Censornet Web Security has Guest and Captive portals. The user can create policies and apply them to individual devices in the network. Policies can block or allow users to access particular devices by category, group, or keyword.
Who is it recommended for?
Censornet offers email and cloud application security on its platform and combining the three plans gets a discount. The plans are affordable for small businesses and they take care of many of the cybersecurity requirements of any business. So, this is a good choice for owner-managers who don’t have cybersecurity skills.
Pros:
- Supplies an encryption service: Is able to decrypt traffic before it reaches users and inspect for threats
- Controls user access: Restrict users to specific devices
- Email protection: Implements end-to-end encryption
Cons:
- No free trial: Request a demo instead
Censornet Web Security is a viable tool for organizations that want to protect employees from interacting with problematic and malicious content. Plans are priced per user per month. You can access a demo to understand the Censornet system better.
12. Skyhigh Secure Web Gateway
Skyhigh Secure Web Gateway is one of the most recognized web filtering solutions known for its strong anti-malware features. Skyhigh Secure Web Gateway can inspect HTTP, HTTPS, and SSL traffic to identify malicious code. In other words, the tool can detect threats hidden beneath the surface of online content.
Key Features:
- An edge service: Delivered from the cloud
- Web traffic proxy: Receives all outgoing and incoming HTTP/HTTPS messages
- Remote browser isolation: Users view a browser that runs on the Skyhigh server
Why do we recommend it?
Skyhigh Secure Web Gateway is an edge service that controls Web traffic going in and out of a network. It provides remote browser isolation (RBI) so your users view the Web sites that they visit loaded on the Skyhigh server. The SGW will also filter outbound traffic to implement data loss prevention.
The antivirus protection of Skyhigh Secure Web Gateway is also strong. This system was originally developed by McAfee and it inherits a threat intelligence service that is collated from the experiences of all of the systems that Skyhigh protects. The threat intelligence reference lists all of the characteristics of discovered malware. McAfee GTI creates a catalog of online websites, emails, and IP addresses and assigns a reputation score to distinguish entities with the highest risk.
To stop important data being leaked from the network Skyhigh Secure Web Gateway has data loss prevention. Data loss prevention scans outward-bound traffic to protect against the loss of business assets. Similarly, data stored in the cloud is protected by encryption to prevent unauthorized access.
Who is it recommended for?
The Skyhigh platform is comprehensive and it also includes cloud application access controls. The bundle takes care of all internet-based threats to a business. However, the company doesn’t publish a price list, so it is difficult to recommend it to cash-strapped small businesses. This service competes with Censornet and Perimeter 81.
Pros:
- Global threat intelligence: Shared experiences of all businesses using the platform
- Data loss prevention: Examines outgoing traffic for files
- User activity monitoring: Tracks user behavior to detect insider threats
Cons:
- No free trial: Get a demo
Skyhigh Secure Web Gateway is delivered from a platform of edge services that can be combined. Unfortunately, Skyhigh doesn’t publish its price list or detail how the different units on its cloud platform can be combined. However, the list of options includes the full Cloud-Native Application Protection Platform (CNAPP). There isn’t a free trial available for the Secure Web Gateway, but you can access an interactive demo.
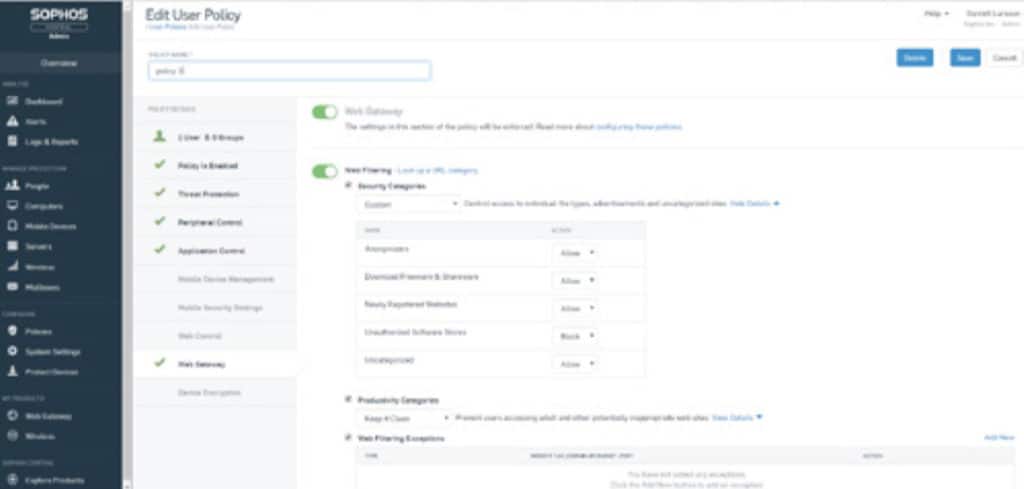
13. Sophos Web Gateway
Sophos Web Gateway is an advanced secure web gateway product. The tool detects zero-day threats and can read HTTP / HTTPS traffic. To detect advanced threats, the program has SophosLabs Threat Intelligence, a team of threat researchers who identify the latest malware threats. There are also features like behavioral analysis to detect malicious behavior and block it.
Key Features:
- Deployment options: A cloud service, a network device, or a virtual appliance
- Intercepts Web traffic: Reads HTTP and HTTPS messages in both directions
- SSL offloading: Acts as the encryption endpoint to enable decryption and content inspection
Why do we recommend it?
Sophos Web Gateway is similar to the Skyhigh platform because it is an edge service that scans inbound and outbound Web traffic. This package has a few extras, which include a threat intelligence feed that adapts the scanner to specific risks. The system has pre-sets to block specific sites or types of content.
Unlike many other web gateways, Sophos Web Gateway has a detailed dashboard function. From the dashboard, you can monitor incoming and outgoing traffic, alongside other performance data. The dashboard gives you a top-down perspective of security events when they occur. For example, you can view graphs on Web Application Usage and Top Web Application Users to see if there are any performance issues you need to address.
You can even create your own security policies in the platform. You have a range of options such as blocking inappropriate content, implementing a bandwidth quota, and setting applications to allow or block. To help with event management there are also over 100 different report templates to help you document security events in detail.
Who is it recommended for?
The Sophos target market for all of its products lies with mid-sized clients and this tool fits that market very well. However, the tool doesn’t require deep technical knowledge, so you don’t need to have a cybersecurity expert on the payroll to get full protection from Web threats with this tool.
Pros:
- Zero-day attack detection: Looks for anomalies
- Threat intelligence: Warns of known malicious domains, IP addresses, and content
- Reverse firewall: Blocks data movements and notes user activities
Cons:
- No prices: You can see the price from AWS and Azure Marketplaces but not for the network device or the virtual appliance – you have to request a quote for those
The advanced threat detection capabilities and ease of use make Sophos Web Gateway a product that meshes nicely in most companies. To get the pricing information for Sophos Web Gateway you will have to contact the company directly. You can start the 30-day free trial.
Top Secure Web Gateways can inspect encrypted traffic
Staying safe online isn’t a question of setting an antivirus solution and hoping for the best. Sophisticated threats are cropping up all over the place; particularly in online traffic. If your employees are connecting to cloud services or applications a web security gateway is vital for finding threats inside encrypted traffic.
A secure web gateway should be a mainstay in any enterprise’s cybersecurity strategy. Content filtering can go a long way towards automating away many risks that employees face online.
Secure Web Gateway FAQs
What is the most Secure Web Gateway?
The most secure Web gateway combines techniques, so systems like N-able Mail Assure, Zscaler Web Security, and Symantec Secure Gateway that add a threat database reference to transmission encryption are the systems to look for.
What is an SWG?
SWG stands for Secure Web Gateway. This service receives all traffic traveling from the internet to a private gateway and blocks malicious activity.
Is a firewall a Secure Web Gateway?
Yes, a firewall is a security gateway because it searches traffic traveling into a system and roots out malicious activity.
What is the function of a Secure Web Gateway?
The security gateway is a service that searches through traffic coming into a network and removes malicious packets. This service is near-live to ensure that users on the protected system don’t experience a significant slow down in their internet service.