One of the main weaknesses of the traditional approach to security is that it assumes that everything inside an organization’s network can be trusted
Here is our list of the best Zero Trust Security Vendors:
- Check Point’s SASE EDITOR’S CHOICE This advanced internet security platform provides a range of virtual network architectures, including ZTA, SASE, and software-defined WANs. Examine this service with a free demo.
- Twingate (FREE TRIAL) Provides single sign-on access to applications on-site and on the cloud with an option for a software-defined perimeter virtual network.
- NordLayer (GET DEMO) With this system, remote users are allocated access to specific applications, regardless of where those apps are hosted.
- ThreatLocker (GET DEMO) A cloud platform of security modules that lets you assemble a ZTA strategy by implementing execution blocks, micro-segmentation, and application fencing.
- UTunnel (GET DEMO) A business VPN package that offers Zero Trust methods for access controls to applications and other system resources.
- Palo Alto This platform offers a menu of secure virtual network systems that allow you to implement, ZTA or SASE.
- Zscaler Implements Zero Trust Access for all of your applications whether they are cloud services or hosted on your servers.
- Illumio Core & Endpoint Fence your applications with Zero Trust Access or apply cloud-based security to each endpoint.
- Absolute ZTNA Protects traffic from insecure devices with ZTNA and fence applications with ZTA from this platform of virtual network services.
- Appgate Implement a software-defined perimeter, a SASE, or an SD-WAN with the tools offered by this platform that protects applications and devices.
- Cisco Zero Trust Platform This system offers three options to secure remote connections, site-to-site connections, and applications on the cloud or on your servers.
One implication of this assumption is that it keeps us blind to threats that get inside the network, which are then left to freely roam and attack the network wherever they choose.
To overcome this deficiency, organizations must adopt a new approach to protect the modern network infrastructure and fluid network perimeter that extends to the cloud, and the increasing number of mobile or dispersed users. This new approach is called the zero-trust security model or zero-trust network access (ZTNA).
What is Zero Trust Network Access (ZTNA)?
Zero Trust Network Access (ZTNA) is a modern cybersecurity approach that enforces strict access controls based on the principle of “never trust, always verify.” Unlike traditional security models that rely on perimeter defenses, ZTNA assumes that threats can originate from both inside and outside the network. This model verifies every user and device attempting to access resources, ensuring access is granted only to those who have been explicitly authorized.
ZTNA operates by segmenting network resources and applying granular access policies. Instead of broad, unrestricted access, users only gain access to the specific resources they need. Authentication and authorization occur continuously, often relying on multiple factors like user identity, device health, and contextual information such as location or time of access.
One of ZTNA’s key benefits is its ability to support secure remote work. It allows users to connect to applications and data without exposing the broader network, reducing the attack surface and minimizing risks associated with lateral movement by attackers. It’s a cloud-friendly solution, integrating well with distributed environments and hybrid infrastructures.
ZTNA vs. Zero Trust Access (ZTA)
While ZTNA is a subset of Zero Trust principles, Zero Trust Access (ZTA) encompasses a broader framework. ZTNA specifically focuses on secure, granular access to network resources, often addressing remote or application-level access. In contrast, ZTA extends these principles across an organization’s entire IT ecosystem, including endpoints, data, applications, and identities.
ZTA includes components like endpoint security, secure authentication, data encryption, and threat detection, providing a holistic approach to security beyond just network access.
Why ZTNA is Essential
ZTNA addresses the evolving cybersecurity landscape by accommodating the shift to remote work, cloud adoption, and the rise in sophisticated cyber threats. By ensuring that access is continually verified and restricted to the least privilege necessary, ZTNA significantly reduces vulnerabilities. It enhances security while improving user experience by enabling seamless access without compromising safety, making it a cornerstone of modern cybersecurity strategies.
The best Zero Trust Security Vendors
Our methodology for selecting a Zero Trust security tool
We reviewed the market for Zero Trust security systems and assessed their providers based on the following criteria:
- A package that includes an access rights manager or can interface to a local LDAP service
- A hub for user access to corporate facilities
- Standardized process for users on-premises, working from form, or out in the field
- An easy-to-manage system that doesn’t require specialist cybersecurity knowledge
- Nice to have additional vulnerability scanning for system hardening
- An opportunity to test the software without paying either from a free trial or a demo
- Value for money from a price that is fair with respect to the facilities provided
1. Check Point’s SASE (ACCESS FREE DEMO)
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: www.sase.checkpoint.com
Money-back guarantee: 30 DAYS
Check Point’s SASE, formerly Perimeter 81, is on a mission to transform traditional network security technology with one unified Zero Trust Network as a Service (ZTNaS).
Key Features:
- Remote access
- Cloud application protection
- Integrated access rights management
- Cloud-based hub
- Connection protection
Why do we recommend it?
Check Point’s SASE is easy to understand. Imagine a VPN service where the user selects a location and then connects. With this system, the user logs into the client application and after turning the connection on, is able to select from a menu of applications. The credentials used for app access are copied through for application access.
Check Point’s SASE zero trust solution is offered via the following platforms:
- Zero Trust Application Access Helps to ensure zero trust access to web applications and remote network access protocols such as SSH, RDP, VNC, or Telnet, through IPSec tunnels – without an agent.
- Zero Trust Network Access Helps to ensure zero trust access to on-premises and cloud resources with one unified cloud platform.
- Software-Defined Perimeter Helps organizations conceal internal network resources and assets from external entities, whether it is hosted on-premises or in the cloud.
Check Point’s SASE zero trust platforms are a scalable hardware-free solution that helps organizations provide secure access to their network infrastructure and digital assets including local and cloud resources from end-point to data-center to the cloud. It offers network visibility, resource access segmentation, and full integration with major cloud providers, giving organizations peace of mind in the cloud.
Who is it recommended for?
This service is a good choice for any size of organization but it is a particularly good option for small businesses that don’t have their own technicians on the payroll. The system is easy to sign up to, install, and set up. You need at least 10 users to get a plan.
Pros:
- Connection security for remote worker access and links to cloud services
- A cloud-based system that links users to applications
- A location-agnostic service – your users can be scattered across the globe
- Combined security for connections and application access
- Also secures mobile devices
Cons:
- Charges for a minimum of 10 users
It offers flexible payment plans with billing occurring on a yearly or monthly basis. When you sign up with Check Point’s SASE, you get a full management platform where you can build, manage, and secure your network. Get access to a free demo.
BEST ZERO-TRUST SECURITY VENDOR:Check Point's SASE is our top choice! Ideal for SMBs, especially those looking for a modern alternative to traditional corporate VPN systems.
2. Twingate
Apps Available:
- Mac
- IOS
- Android
- Linux
Website: www.twingate.com
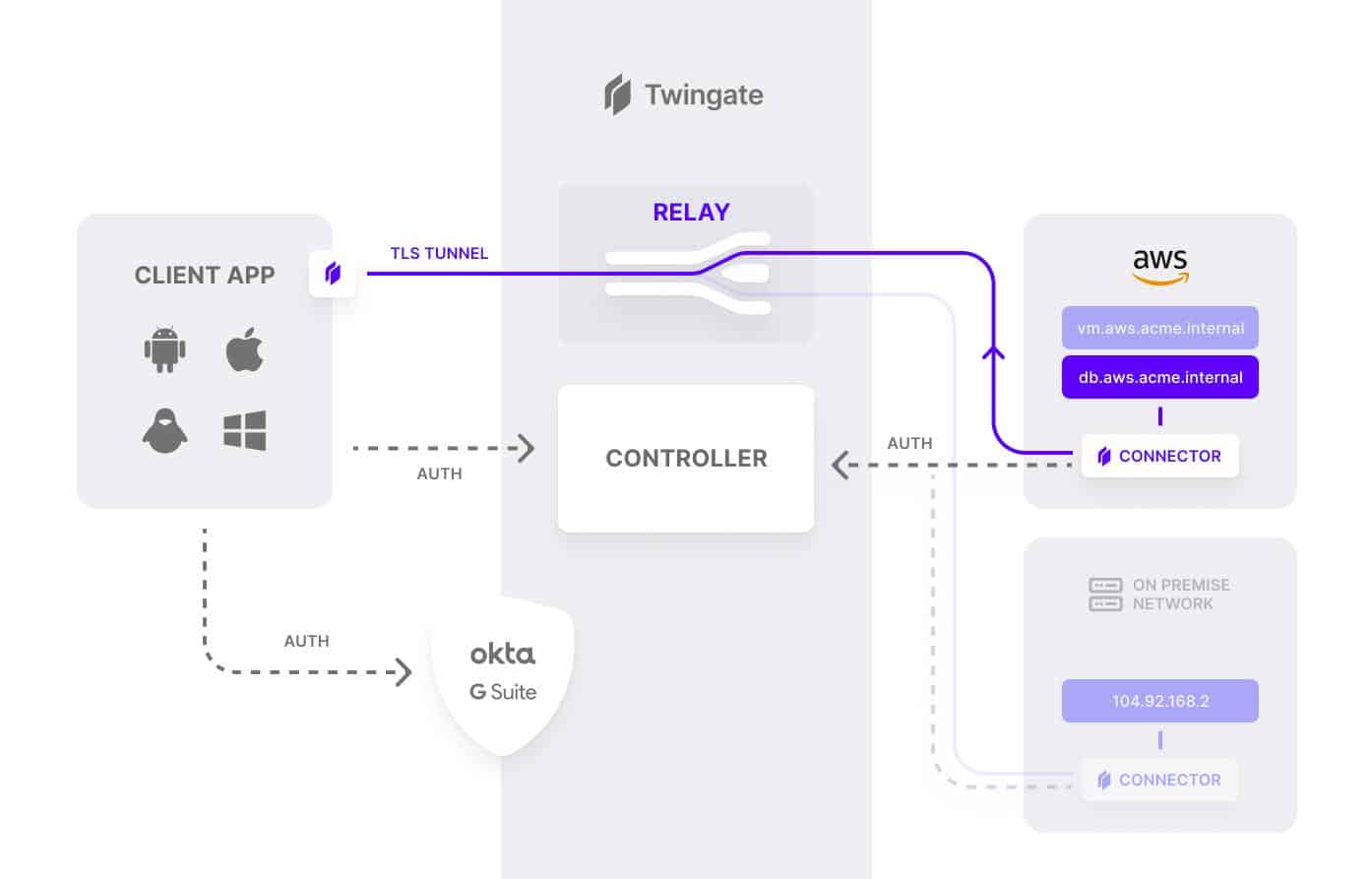
Twingate is a relatively young but fast-rising cloud-based ZTNA service provider. Twingate enables organizations to implement a modern zero-trust network without changing existing infrastructure, and centrally manage user access to company digital assets, whether they are on-premises or in the cloud. Twingate ZTNA solution is offered as an SDP service or an alternative to a traditional VPN. It is delivered as a cloud-based service, and delegates user authentication to a third-party Identity Provider (IdP).
No special technical knowledge is required from end-users other than to download and install the SDP client application and authenticate with an existing identity provider. The controller handles the rest, negotiating encrypted connections between clients and resources. Once everything is confirmed, users are routed to the appropriate resources.
Key Features:
- Hosted in the cloud
- VPN-based
- Free plan
Why do we recommend it?
While Twingate says that its product replaces a VPN, in reality, it is an extended VPN. The extension that it provides is application access controls, which makes this a similar service to NordLayer and Perimeter 81. All user application access goes through the Twingate cloud server for authentication.
The Twingate zero trust architecture relies on four components: Controller, Clients, Connectors, and Relays. These components work in tandem to ensure that only authenticated users gain access to the resources that they have been authorized to access.
Who is it recommended for?
Twingate protects applications running on your premises and in the cloud. Access to all applications is guarded by a menu of services granted to each user. If a user isn’t allowed access to a resource, that software doesn’t even appear in that person’s menu and so, effectively it doesn’t exist for them.
Pros:
- Multi-factor authentication
- Single sign-on environment
- Network access controls
Cons:
- No self-hosting option
ZERO TRUST:Twingate is a ZTNA that allows businesses to manage remote access to apps and other resources. It comes with a 14-day money-back guarantee.
3. NordLayer
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: www.nordlayer.com
Money-back guarantee: 14 DAYS
NordLayer operates like a VPN with integrated access rights management. Each user gets an access app that, thanks to a single sign-on mechanism, flows through login actions to each of the applications to which the user is allocated rights.
Key Features:
- VPN-linked
- Remote access
- Access controls
- Single sign-on
Why do we recommend it?
NordLayer is a similar system to Perimeter 81. This is an expansion of the service offered by NordVPN, building application access controls into the VPN client app. The tool can be deployed on mobile devices as well as computers. When users connect to an application, the request passes through the central NordLayer server for approval.
The user app can be assigned to each user whether they are remote or on site. The users only know about the existence of the applications to which they have been granted access and so have no way of even reaching the login screen of the business’s other services. Access to all company sites is blocked from all access other than connections that arrive through one of the authorized NordLayer tunnels.
NordLayer is a package of modules and you decide on your security strategy, whether it is ZTA or a virtual network configuration, such as a SASE. An anti-virus service, called ThreatBlock is included in all plans and you can get FWaaS by adding on the dedicated IP address option.
Who is it recommended for?
As with the Perimeter 81 package, the NordLayer system is suitable for any size of business but especially small enterprises. The minimum user number of an account with this SaaS package is five, so NordLayer caters to even smaller businesses than those that can get the Perimeter 81 service.
Pros:
- Combines connection security and access controls
- An anti-virus package is included
- All user traffic goes to the NordLayer cloud server and then gets forwarded
- Monthly and yearly payment options
Cons:
- DDoS protection isn’t included in the lowest plan
RELIABLE ALL-ROUNDER:Small Enterprise Favourite NordLayer is offered in three plan levels and the top two of these can implement ZTA. Get a demo to assess the NordLayer system.
4. ThreatLocker (ACCESS FREE DEMO)
ThreatLocker is a SaaS package, based in the cloud. It provides the building blocks of a ZTA network that can be administered from a console that is hosted on the ThreatLocker server. The controller can manage resources and users in multiple locations and it can control application usage and activity on the cloud as well as those hosted on a site.
Key Features:
- Default block on software
- Allowlisting
- Protects data
Why do we recommend it?
ThreatLocker provides you with a method to protect data and control access to applications. All software on an endpoint in disabled and even new packages won’t run. Files are ringfenced so they can only be accessed by specific applications. Users are granted access to those applications and that software is specifically allowed to run. All other software, including malware, continues to be disabled.
Modules include Allowlisting, which blocks all software from running on owned computers. Only those packages that are on the “allow list” will be able to execute. The Application Fencing module implements micro-segmentation, controlling access to specific resources, such as directories or files, and logging all activity. A Network Access Control module checks the security of each device before allowing it to connect to the network and controls which servers that endpoint can access. The Storage Control module blocks USB ports that can be activated for the deployment of a specific memory stick by a specific user. This permission can be revoked and all activity is logged.
Who is it recommended for?
The “allowlisting” strategy of ThreatLocker is very easy to administer and it removes all possibility of administrator forgetfulness allowing malware to get access. All software is blocked from running and it takes a specific permission action by the administrator to allow a package to run. Thus, an oversight in administration results in inconvenience rather than a data breach.
Pros:
- Good for protecting sensitive data
- Easy to set up and administer
- Users can request that a software package is approved – until it is, it won’t work
Cons:
- No price list
All of the logging features in ThreatLocker can be used for threat hunting with a SIEM tool and they are also available for compliance reporting for PCI DSS, HIPAA, and GDPR. One shortfall with the ThreatLocker system is that it doesn’t have its own integrated access rights manager. You can assess ThreatLocker by accessing a demo.
5. UTunnel (FREE DEMO)
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: UTunnel.io
Money-back guarantee: 14 DAYS
UTunnel is a powerful Zero Trust system designed to secure network access by verifying every user and device before granting access. By adopting a Zero Trust Architecture (ZTA), UTunnel ensures businesses can maintain a strict, secure perimeter around their network, safeguarding sensitive data and resources in a modern, distributed workforce.
Key Features:
- Zero Trust Authentication
- Choose between self-hosting or hosted VPN solutions
- AES-256 encryption
Why do we recommend it?
We recommend UTunnel.io because it effectively implements Zero Trust principles, ensuring all access requests are continuously validated. Its flexible hosting options, combined with strong encryption, allow businesses to secure their network without sacrificing control or ease of use, making it ideal for modern enterprises with stringent security needs.
UTunnel.io adopts a Zero Trust Architecture (ZTA). No user or device is trusted by default, regardless of their location or network. Access to company resources is controlled through multi-factor authentication (MFA) and device validation, ensuring that only authorized individuals and devices gain access. UTunnel.io offers self-hosting on premises and on cloud accounts so businesses maintain full control over their systems while adhering to ZTA.
Pros:
- Access managed gateways or set up your own
- Flexible packages priced per user
- Security measures include a kill switch and DNS leak prevention
Cons:
- VPN server self-hosting requires deep technical knowledge
UTunnel offers various pricing plans designed for different business needs, with options for both cloud-hosted and self-hosted VPN solutions. Plans are based on the number of users and additional features, ensuring scalability as businesses grow. Each plan includes the ability to implement Zero Trust principles and access comprehensive security features like encryption, centralized management, and more. Schedule a free demo.
6. Palo Alto
Palo Alto Networks is a well-known American enterprise cybersecurity company that provides network security, cloud security, endpoint protection, and various cloud-delivered security services. Palo Alto Networks was named a Challenger in the 2022 Gartner Magic Quadrant for Security Service Edge (SSE), and a leader in the Forrester New Wave Zero Trust Access.
The Palo Alto Networks Prisma Access is a cloud-delivered platform that consolidates networking and security capabilities into a single platform that enables flexible hybrid work culture for the modern business without compromising security and user experience.
Key Features:
- Strategy options
- WAN management
- Application access management
Why do we recommend it?
The Palo Alto Prisma offers a range of products that are components for different network, data, and application protection strategies. Use the service to create Zero Trust Access application protection system, a software-defined WAN to unify sites, or Secure Access Service Edge (SASE) to add a cloud firewall to your SD-WAN.
Prisma Access security capabilities include the following technologies:
- ZTNA Prisma Access ZTNA provides a secure connection to applications and supports both agent-based and agentless connection methods regardless of a user’s location.
- Next-Gen Cloud Access Security Broker (CASB) Prisma Access CASB provides visibility, real-time data protection, and security for SaaS applications
- Cloud Secure Web Gateway Prisma Access provides cloud secure web gateway (SWG) functionality which is natively integrated with Next-Gen CASB to protect remote users from threats when accessing the web and non-web applications.
- Firewall as a Service (FWaaS) Prisma Access provides FWaaS capabilities with the full functionality of Palo Alto Networks Next-Generation Firewalls (NGFWs).
Who is it recommended for?
This is a high-level package from a major networking and cybersecurity system provider. The package needs to be managed by a technician who has training and experience in creating security strategies. So, this is a system that would be suitable for mid-sized and large organizations with highly trained network specialists on the payroll.
Pros:
- Flexible platform
- Options for Zero Trust application protection
- Protects IoT networks
Cons:
- No free trial
A virtual test drive that aims to give you hands-on experience with Palo Alto Networks Prisma Access is available on request.
7. Zscaler
Zscaler is an American cloud security company and one of the leading providers of ZTNA solutions and services. Zscaler was named a leader in the Gartner 2022 Magic Quadrant for Security Service Edge. Zscaler’s ZTNA products include the Zscaler Zero Trust Exchange, Zscaler Private Access (ZPA), and others.
Key Features:
- Access hub
- Secures remote access
- VPN-based
Why do we recommend it?
Zscaler is a VPN-based service that draws all company traffic to its own hub where it is authenticated and then forwarded. This system operates in the same way as Perimeter 81 and NordLayer – it provides a VPN service mixed with an access rights manager. The tool can be used as a data loss prevention system as well.
The Zscaler Zero Trust Exchange is the platform that powers all Zscaler services to securely connect users, devices, and applications over any network. The platform leverages the zero trust principle of least-privileged access to secure applications, data, and users as they connect to work remotely via the public network (internet).
Who is it recommended for?
This is a good solution for a mid-sized company that is looking for value for money. The platform combines many system security services and a skilled cybersecurity expert can assemble the components in the package to create a bespoke but reliable data, application, and network protection system.
Pros:
- A flexible platform of security tools
- A dedicated IP address option that creates a cloud-based firewall
- Activity monitoring with alerts
Cons:
- No free trial
ZPA is a cloud-based service that provides zero trust access to private applications running on-premise, in the public cloud, or within the data center. ZPA protects applications from the public network (internet), making them invisible to unauthorized users. A free online demo is available on request.
8. Illumio Core & Endpoint
Illumio delivers zero trust micro-segmentation from endpoints to data centers to the cloud to halt cyber-attacks and the spread of ransomware. You can also use Illumio’s zero-trust platform to protect against lateral movements across devices, applications, workloads, servers, and other infrastructure.
Key Features:
- Protection for hybrid networks
- Cloud workload protection
- Servers, cloud platforms, and containers
Why do we recommend it?
Illumio controls the supporting platform for applications and uses that position to block or allow access to applications. The Illumio Core package operates on systems running on your own servers and on the cloud, while Illumio Endpoint, tracks all activity from a specific device.
Illumio zero zero-trust solution is offered via the following platforms:
- Illumio Core (formerly known as Illumio ASP) Delivers visibility and segmentation for workloads and containers in data centers, private clouds, and all public cloud environments.
- Illumio Endpoint (formerly known as Illumio Edge) Brings zero trust to the endpoint and helps prevent the peer-to-peer spread of ransomware and other malware.
Who is it recommended for?
The Illumio services will appeal to different audiences. The Illumio Endpoint service is a little like a User and Entity Behavior analytics service with preventative controls that look a lot like access control lists (ACL) for classic network segmentation. Illumio Core implements network segmentation that extends out across internet connections to cloud services.
Pros:
- Two products that protect access to applications through microsegmentation
- Its access controls are implemented through application-level software rather than network access control lists
- Ringfences applications
Cons:
- Doesn’t implement network segmentation
With capabilities that span micro-segmentation, network visibility, encryption, and vulnerability management, Illumio’s zero-trust platform provides opportunities for organizations to embrace and implement zero-trust strategies. Pricing details can be obtained by directly contacting the vendor. However, the vendor provides a means to obtain a total cost of ownership (TCO) estimate for Illumio Core to help you build a business case for the elimination of unnecessary hardware in your data center. Find out more.
9. Absolute ZTNA
The Absolute zero trust solution combines ZTNA, SDP, and enterprise VPN solutions to provide organizations with secure access to their digital assets and resources. It can be deployed on-premises, or in the cloud (public, private, and hybrid). The easiest way to take advantage of the Absolute platform is to implement it as a service.
Key Features:
- Network segmentation
- IoT access controls
- Application protection
Why do we recommend it?
Absolute ZTNA provides both network security and protection for applications. The tool is particularly useful for securing access for potentially insecure devices, such as IoT devices or BYOD equipment. As well as Zero Trust Network Access, the package implements Zero Trust Access for application access.
The Absolute client installed on user devices acts as the controller, gathering real-time data about the host device, applications, network connections, and analyzing the context of every user request for resources. The data gathered is then used to build a risk profile of each request to determine whether the user can access the resource based on the immediate context. The Absolute gateway which can be installed on-premises or in the cloud ensures that all company resources are protected. If the controller approves users’ access to a resource, traffic is routed to this gateway and directly to the destination requested.
Who is it recommended for?
This package is primarily a network security service and it also implements application security. The tool authenticates the user that wants access to corporate resources and also validates the security of the device that the request comes from. This device security scanning is particularly important for IoT devices that don’t involve the use of access credentials.
Pros:
- Risk assessment for accessing devices
- A self-repairing device client
- Malware scanner option
Cons:
- More network and endpoint protection than application security
You can examine the Absolute ZTNA platform by accessing a demo.
10. Appgate
Appgate ZTNA solution is offered as software-defined perimeter, VPN alternative, secure third party, and DevOps access based on zero trust principles and built to support hybrid IT and a distributed workforce. It is infrastructure agnostic and can be deployed in all environments: on-premises, multi-cloud (AWS, Azure, GPC), virtualized containerized environments, and legacy networks and infrastructure.
Appgate was named a leader in the Forrester Zero Trust New Wave 2021 report. The entire Appgate ZTNA solution is designed to be distributed and to offer high availability, and it can be deployed in physical, cloud, or virtual environments. The Appgate platform integrates seamlessly with third-party applications such as IdPs, LDAP, MFA, and SIEM, among others.
Key Features:
- Network security
- Appliance based
- Software-defined perimeter
Why do we recommend it?
The Appgate system provides a software-defined perimeter, however, it is delivered on an appliance. The appliance implements all of the security management for the network, which is delivered after an assessment of the user trying to get into the system and the device of the user. The device must be free of malware and other security risks and the user must present the right credentials.
With the Appgate ZTNA solution, access can be controlled from any location and to any enterprise resource with centralized policy management for servers, desktops, mobile devices, and cloud infrastructure among others.
The Appgate ZTNA platform consists of three main components:
- Controller The controller manages user authentication and applies access policies assigned to users based on user attributes, roles, and context. It then issues entitlement tokens listing the resources the user is permitted to access.
- Client The Appgate client is software that runs on user devices, and connects with Appgate appliances to receive site-based entitlement tokens after successful authentication.
- Gateway The gateway evaluates user entitlements and opens connections to resources accordingly.
Who is it recommended for?
Appgate is similar to the Absolute ZTNA system because it implements network access controls for potentially insecure devices, such as IoT equipment and BYOD. The service can also be used to control access to applications, in which case, it provides a ZTA service.
Pros:
- Validates devices as well as users
- Good for BYOD
- Secures IoT networks
Cons:
- Requires the purchase of a hardware device
The Appgate SDP (part of its ZTNA solution) is available for a test drive, and the virtual appliances and client software are also available for download.
11. Cisco Zero Trust Platform
Cisco’s zero trust solution helps organizations secure access to applications from device and location.
Key Features:
- Zero Trust Network Access
- Cloud workload protection
- Zero Trust Access
Why do we recommend it?
Cisco is the world leader in internet and network technology. The company provides three options for ZTA and ZTNA. The products include a combination service that implements security checks for both users and devices. The overlap between the three services can be a little confusing.
The Cisco zero-trust approach is broken down into three pillars: workforce, workload, and workplace.
- Zero Trust for the Workforce This pillar ensures that only the right users and devices that meet security requirements can access applications and systems, regardless of location. Zero Trust for the workforce solution is implemented via the Cisco Duo platform. A free version called Duo free, a 30-day free trial as well as the various subscription plans and associated costs and features are all available.
- Zero Trust for workloads This pillar focuses on securing all connections and preventing unauthorized access within application environments across multi-cloud, irrespective of where they are hosted. The Cisco Zero Trust for workload solution is implemented via the Cisco Secure Workload. It can be deployed on-premises (physical or virtual) or as a SaaS application.
- Zero Trust for the workplace This pillar focuses on securing all users and devices (including IoT) access to the enterprise network. The Cisco Zero Trust for the workspace solution is offered via the Cisco Software-Defined Access (SDA) platform. The solution is targeted at medium to large enterprises.
Who is it recommended for?
These tools are better suited for companies that have competent network managers with a strong comprehension of cybersecurity. The Duo Free product is going to interest small businesses with little money to spare.
Pros:
- A range of ZTA and ZTNA products
- Solution for hybrid system protection
- Cloud-only protection product
Cons:
- Not one single product
Choosing the right ZTNA vendor
While ZTNA has many use cases, most organizations choose to use it as a means of access to hybrid and multi-cloud services, an alternative to VPN, and a means to eliminate over-privileged access to resources, among others. These solutions can be deployed as on-premises or standalone service, cloud service, or as a hybrid service, combining cloud and stand-alone offerings. With a variety of Zero Trust vendors out there, choosing the right one for your business and budget can be challenging. In this article, we’re going to review the eight best Zero Trust vendors in the market. Hopefully, this will guide you in the process of choosing the right solution for your business.