CrowdStrike is a prominent cybersecurity provider and Zscaler is creating innovative cloud-based virtualization solutions for security. Each offers its systems from a cloud platform and both have moved to the cutting edge of corporate security.
Both companies keep extending their stables of tools and, starting from different core activities, the two providers compete in the same markets for some of their menu of services.
CrowdStrike originally offered endpoint protection but has branched out into cloud and internet protection. Zscaler is primarily a “cloud-first” security service that doesn’t offer much to protect on-premises systems.
About CrowdStrike
CrowdStrike started operations in 2011 and was originally a cybersecurity consultancy. The business developed its system protection platform, called Falcon, and started marketing this in 2013.
The company gained brand recognition through its research arm, which got a great deal of publicity in its discovery of the Sony Pictures data breach in 2015 and the Democratic National Committee (DNC) email hacks in 2015 – 2016.
CrowdStrike Holdings, Inc. floated on NASDAQ in 2019 and by April 2022 grew to a market capitalization of $50.647 billion. The company’s headquarters moved from Sunnyvale, California to Austin, Texas in December 2021 and it had 3,394 employees by the end of 2021.
The core product of CrowdStrike, Falcon Prevent, is a next-generation anti-virus service. This is an on-device system but all the other tools in the Falcon suite are cloud-based and use the Prevent software as a local agent.
The company’s main method of expansion has been through acquisition. It entered the Zero Trust Access market in September 2020 with the purchase of Preempt Security. It added to this product by buying Secure Circle in November 2021.
Most of the company’s products are tagged with the name CrowdStrike Falcon. The company still offers consultancy services and also runs a managed security service branch, which provides the technicians to run a security system for clients as well as the software.
About Zscaler
Zscaler is a little older than CrowdStrike. The company was originally called SafeChanel, Inc. and began operations in 2007. Its first security product hit the market in 2008. The business focuses on Zero Trust Access (ZTA). This is a cloud-based security solution that emulates a business network over the Internet and protects applications rather than physical systems, such as servers or networks.
The issues of security for cloud workloads are relatively new and the mechanisms they employ are difficult for system administrators to conceptualize because they don’t map directly onto the methods used to protect networks and endpoints. This conceptual leap explains why Zscaler was a little slower in its growth than CrowdStrike.
Zscaler’s growth began in 2012 when it started to attract the attention of venture capitalists. The company embarked on a series of acquisitions in 2018 – all the purchases related to zero trust access systems and cloud workload protection.
Zscaler, Inc. launched on NASDAQ in December 2021 and currently has a market capitalization of $33.664 billion. The business is headquartered in San Jose, California, and at the end of 2021 had more than 4,000 employees.
Business Comparison
CrowdStrike is a larger company than Zscaler and it offers more products. However, Zscaler has a longer history in the innovative field of cloud protection and that is an area that CrowdStrike is currently trying to break into.
Zscaler doesn’t compete with CrowdStrike on endpoint protection. Both companies operate from cloud platforms but the CrowdStrike Falcon Prevent module that installs on endpoints is a crucial feature that protects networks from inside. Zscaler’s strategy is to protect networks from the edge while focusing on security for cloud assets as its main area of operations.
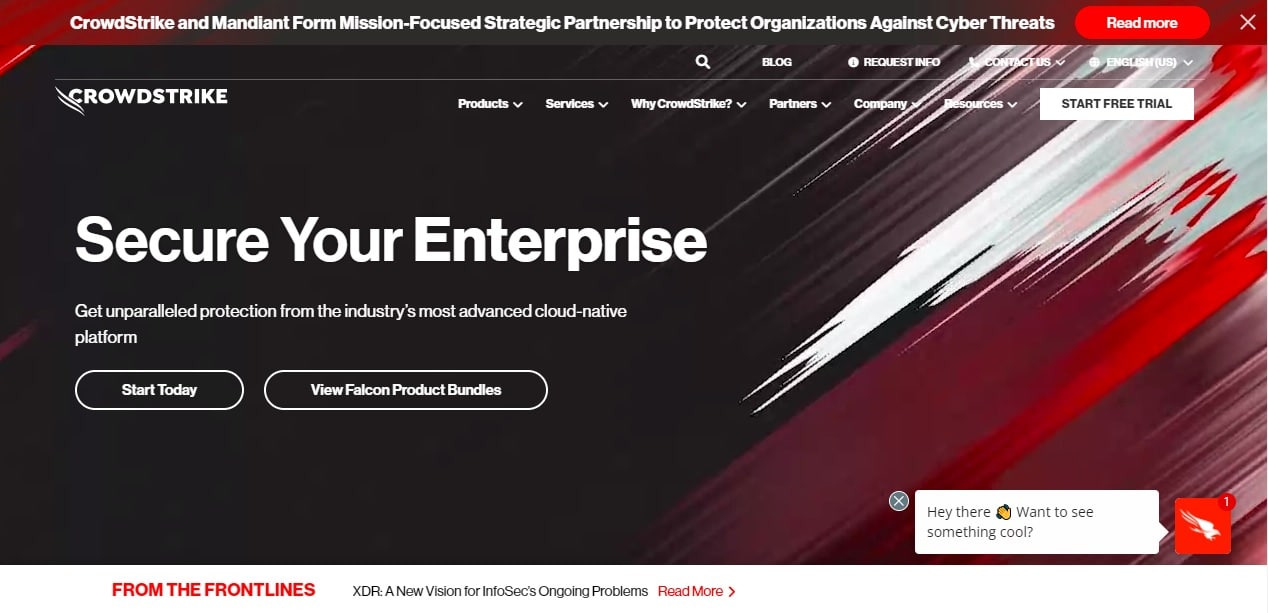
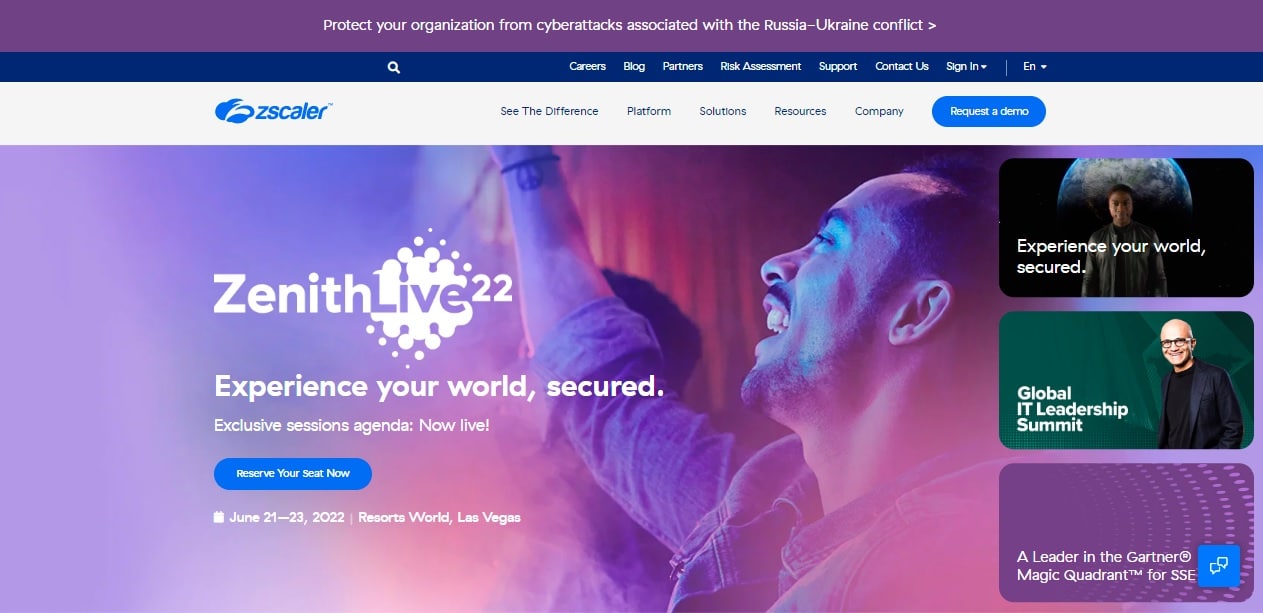
A look at the Home page of each company’s website shows the emphasis that each places on its key area of specialization.
The CrowdStrike page headlines its protection for endpoints and emphasizes that vision through its Home page. Other services, such as protection for cloud assets, are mentioned further down.
Zscaler is promoting its upcoming annual user conference in the initial view of its Home page. In that, you can see the mention of cloud security and nothing about protection for endpoints or other on-premises systems.
A direct comparison between the two companies, CrowdStrike and Zscaler, is difficult because each specializes in different areas of cybersecurity. Although CrowdStrike has entered the area of business in which Zscaler operates, the company hasn’t built up enough experience in the area of Zero Trust Access to fully compete with Zscaler. Zscaler hasn’t even tried to enter the market in which CrowdStrike excels – endpoint protection – because that is outside the Zscaler business model.
CrowdStrike vs Zscaler: Head to Head
The intersection between the services of CrowdStirke and Zscaler covers the areas of Cloud Workload Protection (CWP) and Cloud Security Posture Management (CSPM). These functions are covered by CrowdStrike with three modules and by Zscaler with one product that includes four modules.
CrowdStrike Cloud Security
The three systems that CrowdStirke offers in its Cloud Security division are:
- Falcon Horizon CSPM
- Falcon Cloud Workload Protection
- Container Security
Zscaler Cloud Protection
Zscaler Cloud Protection is a package of four modules that directly compete with the above-mentioned services of CrowdStrike. Its modules are:
- Zero Trust Exchange
- Workload Segmentation
- Zscaler Workload Posture
- Zscaler Workload Communications
Of the cloud security areas covered by both only the CSPM modules can be fairly compared head-to-head. The CWP strategies of the two companies are completely different.
CrowdStrike Falcon Cloud Workload Protection
CrowdStrike recently acquired two businesses that specialize in Zero Trust Access and it is still integrating these new divisions and formulating a ZTA module because it doesn’t yet implement the strategy.
The CrowdStrike CWP is a cloud platform version of its Falcon Prevent system. There are versions of this agent for AWS, GCP, and Azure. Essentially, you activate an agent on your cloud platform account that performs AV services, communicating with the CrowdStrike platform.
The CrowdStrike strategy requires a separate agent to be installed on each cloud platform account. The advantage of this system is that it plugs those cloud accounts into the Falcon Insight system, which is a cloud-coordinated EDR. The Insight service coordinates the actions of Falcon Prevent on endpoints and it will also include cloud platforms with the installation of the Cloud Workload Protection module.
Zscaler Workload Segmentation and Zero Trust Exchange
Zscaler implements CWP through a system that is called micro-segmentation. This is a virtualization approach that is at the heart of ZTA technology – which CrowdStrike is just learning.
Zscaler Workload Segmentation identifies the application dependencies of cloud-resident software and their supporting microservices. It then secures the links between them, creating a virtual network over the internet. It adds a firewall mechanism around these bundles of services to create a black-box virtual application that can be managed as a single entity.
The Zero Trust Exchange is what cybersecurity professionals call a CASB – Cloud Access Security Broker. Zscaler calls its CASB agents Trust Brokers. Think of Zero Trust Exchange as operating like Active Directory. The tool has a list of services that were created as virtual packages by the Workload Segmentation system and then the administrator sets up user accounts in the Zero Trust Exchange registry, allocating access rights to a list of packages for each.
Zscaler also has a module called Zscaler Workload Communications. This acts as a user interface to the whole Zero Trust Exchange system and also a connection security system that locks each user into only being able to contact the Zscaler server. Think of this as a cloud version of a virtualized desktop, such as the VM systems offered by Hyper-V and VMware.
CrowdStrike vs Zscaler for Workload Protection
CrowdStrike ported its endpoint AV system to cloud platforms. This is the type of product that execs can understand. It models familiar approaches to new technology. CrowdStrike’s strategy has won it more customers and a higher company valuation because it is duplicating a credible cybersecurity model.
Zscaler has been operating for longer but was too far ahead of the mindset of its potential customers. The Zero Trust strategy is a better model for protecting cloud-based systems that seem to be floating somewhere far away and not anchored to a thing in the office, such as a desktop PC or a network switch.
After a decade of trying to explain its strategy to potential investors, Zscaler is finally gathering a reputation that has attracted funds. It is now able to educate the market and it is getting cut-through.
CrowdStrike is applying yesterday’s solutions to new platforms, while Zscaler set up tomorrow’s solutions to a hosting platform that, at the time, hadn’t taken off. CrowdStrike is a better solution for hybrid environments because it covers both on-premises and cloud-based assets. Zscaler’s creators’ uncompromising “cloud-first” strategy has meant that it had to tread water while reality caught up with their vision. They aren’t interested in protecting on-premises systems because they don’t believe that they will be around for much longer. Zscaler is a better solution for the protection of all-cloud systems.
CrowdStrike Falcon Horizon CSPM
Cloud security posture management systems are the equivalent of the vulnerability scanners that you use to identify security weaknesses in the settings and software on your on-premises assets. This tool will also scan access rights management systems for poor account security
The CrowdStrike service will scan assets hosted on Google Cloud Platform, AWS, and Azure. The system looks for known weaknesses in configurations and identifies potential attack vectors. From the starting point of your account details, the CrowdStrike system will trace all supporting services, including those that are hosted elsewhere. This autodiscovery process loops so its application dependency map is constantly updated.
An additional service that is built into the CrowdStrike package is a threat intelligence feed that comes from the CrowdStrike team of cybersecurity researchers. The CrowdStrike Threat Intelligence system means once one of the service’s customers gets hit by a new hacker trick, all of the CrowdStrike Horizon CSPM implementations know about it.
The scan results that the CSPM tool produces include guides on what to do to fix the detected problem. It is also possible to get advice from a CrowdStrike analyst.
Zscaler Workload Posture
Zscaler Workload Posture is that platform’s CSPM. It operates on GCP, Azure, AWS, and Kubernetes. This tool performs an autodiscovery function, which repeats to keep its application dependency map up to date.
The CSPM checks on the links between modules and their coupling processes as well as the actual configuration of each service. You also get access to rights manager auditing and that includes the performance on the Zscaler Zero Trust Exchange system.
The result of a CSPM scan is a report that assigns each weakness a risk rating and orders results with the most urgent problems first. This system also produces resolution recommendations.
A feature that Zscaler has that isn’t included in the CrowdStrike Horizon CSPM is a data loss prevention module (DLP). This scans data stores and classifies data by a sensitivity rating. It can also enforce your Trust Brokers to tighten access to that information.
CrowdStrike vs Zscaler for Cloud Security Posture Management
Both CrowdStrike and Zscaler built compliance reporting into their CSPM systems. Both of these systems are good options. You get threat intelligence with CrowdStirke and DLP with Zscaler. Apart from those differences, the core of the CSPM in both cases has application dependency mapping, continuous scanning, and recommendations on security tightening.
As Zscaler Workload Posture is part of the Zscaler Cloud Protection platform, your choice over whether to use this CSPM would be governed by your interest in the complete ZTA environment offered by Zscaler.
Find out more
Neither CrowdStrike nor Zscaler offers a free trial for their cloud security systems, nor do they publish prices. To find out more about Zscaler, you can request a demo of the Cloud Protection system. You can read about CrowdStrike Cloud Security products at the CrowdStrike website.