What is database encryption?
Database encryption is the process of converting sensitive data stored in a database into an unreadable format using cryptographic algorithms. This ensures that even if unauthorized individuals gain access to the database, the data remains protected. Only those with the correct decryption keys can decode and access the encrypted data. Encryption plays a vital role in maintaining data security and privacy, especially in industries like healthcare, finance, and e-commerce that handle large volumes of sensitive or regulated information.
Only have time for a glance at the tools? Here is our summary list of the best database encryption tools:
- IBM Security Guardium Data Protection EDITOR’S CHOICE Provides full visibility while encrypting and decrypting structured or unstructured data with good levels of automation and scalability. Installs on Windows, Linux, Unix, or cloud platforms.
- Vormetric Transparent Encryption Hardware-accelerated encryption solution using data-at-rest encryption with centralized key management, privileged user access control, and more.
- DbDefence for Microsoft SQL With data masking techniques for database tables provides extra protection, bespoke SQL database encryption.
- BitLocker The ‘go-to’ encryption solution for Microsoft Windows-based systems designed to provide powerful encryption to whole volumes.
Database encryption typically involves encrypting specific fields, such as Personally Identifiable Information (PII), financial records, or passwords, or encrypting the entire database file. Common encryption methods include AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), and DES (Data Encryption Standard), each providing varying levels of security.
One of the main purposes of database encryption is to protect data at rest, ensuring that stored data remains secure, even if physical drives are stolen or compromised. Coupled with encryption for data in transit (via SSL/TLS), organizations can establish comprehensive end-to-end data protection.
While encryption is a strong security measure, it is not foolproof. Effective encryption depends on managing keys securely, updating algorithms to resist new threats, and ensuring proper integration into applications. Without secure key management, encrypted data may still be vulnerable to breaches.
Database encryption also helps organizations meet regulatory requirements such as GDPR, HIPAA, and PCI DSS, which mandate strict data protection measures. Compliance ensures that businesses avoid penalties while safeguarding customer trust.
In summary, database encryption is an essential defense mechanism in modern cybersecurity. By securing sensitive data against unauthorized access, it provides a vital layer of protection and supports the organization’s overall data governance strategy.
Why do we need database encryption?
The term “encryption” represents the conversion of data into a secure format that can only be read using a decryption key. The whole purpose is to ensure that only authorized persons or applications can access and work with the data. In a world that has become all too familiar with breaches and hacks, data owners have come to seek ways to keep their data secure. The software industry heeded this call and came up with solutions where their clients’ data is encrypted in three major ways:
- Full-drive encryption – encryption of drives as a whole and where everything that is stored on them is ciphered. Major operating systems like Linux and Windows Server come with features that allow for full-disk encryption that can then only be accessed using a password. This password needs to be entered at boot time so that even the operating system itself can gain access to data on it. Any application that then runs on the server doesn’t require access to the password as the operating system handles its access transparently.
- Partial system encryption – file-system-only encryption that ciphers a specific folder or data file which can then be accessed by only using a password. This method is similar to the previous encryption method as here too, once the operating system confirms the right password, any applications that need to work with the data will do so transparently. The drawback here is that human error could result in sensitive data being stored in unencrypted file storage spaces or systems.
- Database encryption – data security that converts data stored in databases into undecipherable garbage that makes no sense without a password. Here the password need only be inserted when the database is being accessed and not when the whole system starts up. In this case, should there be unauthorized access to the disk – even if it were physically removed – the culprits wouldn’t be able to access the data that is in the encrypted databases.
Since we have mentioned “transparency” a couple of times in the encryption types above, it becomes necessary to look into the definition of the concept in detail:
What is Transparent Database Encryption (TDE)?
Transparent Data encryption (TDE) is an encryption technology that is used by the larger database software companies like Microsoft, IBM, and Oracle. They have made this technology a part of the data security feature for a number of their database solutions. 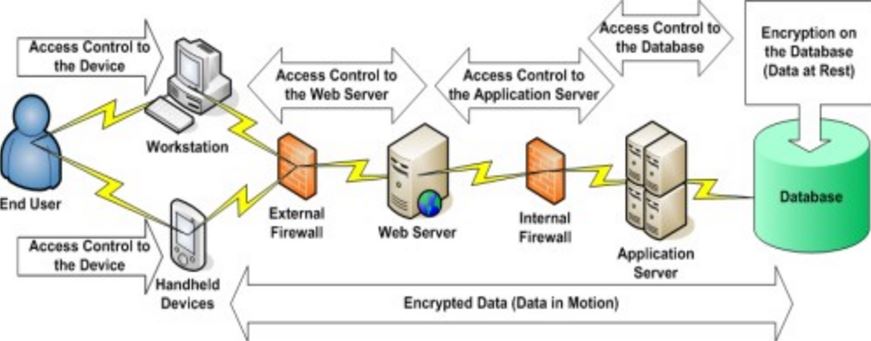
TDE is database-level encryption that works to cipher data at rest – meaning when the data is not being accessed, changed or in motion over a network – by encoding the structure of the database and not the data itself. This way, even if a disk is stolen, the database on it can’t be accessed without the original encryption certificate and master key.
TDE doesn’t require any application changes in code or otherwise when authorized users access the data, hence the “transparent” in the name. Programmers or any applications don’t need to create macros or update complex configurations to use the data. Once they are authorized, the operating system does the decryption and opens up the database for access to data in it.
This also means authorized users and applications don’t need to create auxiliary tables, triggers, or views to decrypt data that is encrypted using TDE.
The Best Database Encryption Tools
Our methodology for selecting a database encryption tool
We reviewed the market for database encryption solutions and analyzed tools based on the following criteria:
- Compatibility with a long list of DBMSs
- Automated, closed-loop encryption and decryption
- Use of a strong encryption cipher
- Integration with access rights management (ARM) systems
- Implementation of Transparent Database Encryption (TDE)
- A free trial or a money-back guarantee for a risk-free assessment period
- Value for money from a comprehensive encryption system at a fair price
With these selection criteria in mind, we derived a list of cost-effective database encryption systems that don’t slow down data access processes.
Ok, so… here is the list of our choices for the best encryption tools and software solutions to use with your data:
1. IBM Security Guardium Data Protection
IBM Security Guardium Data Protection is the answer to businesses that are looking for a database encryption solution that comes from a globally-established technology brand.
Key Features
- Deployment options: Cloud or on-premises for Windows, macOS, or Linux
- Data privacy compliance: PCI DSS, HIPAA, GRPR, CCPA, and SOX
- Security measures: Protects sensitive data
- Activity logging: Tracks user behavior to spot insider threats
- Protects hybrid systems: Monitors files on premises and on cloud platforms
Why do we recommend it?
IBM Security Guardium Data Protection supplies security services for files and databases. It includes a sensitive data discovery service and protects those locations with constant monitoring as well as data encryption. It can operate on DB2, Oracle, Teradata, Sybase, Hadoop NoSQL, and SQL Server databases on your servers or on the major cloud platforms.
With this tool, TDE is implemented with encryption and decryption taking place above data file systems and storage volumes or drives. This way data access is transparent to users, applications, databases, operating systems, and storage management systems. 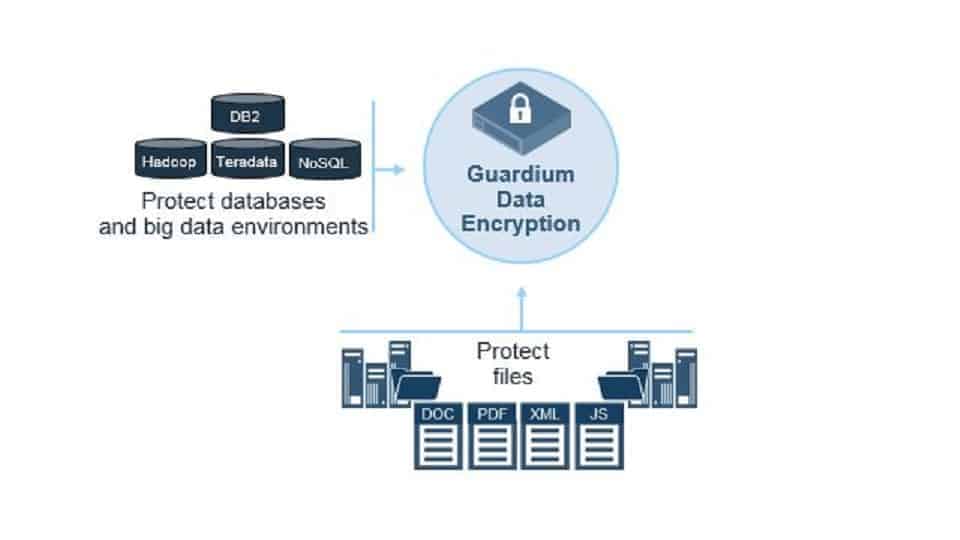
IBM Guardium is used to encrypt both structured and unstructured data sources and can also be scaled to continue covering a business’s security needs even as it continues to grow.
Who is it recommended for?
There are many deployment options for the IBM service but overall, this system is suitable for large organizations. Naturally, it is targeted at businesses that hold sensitive data and those companies that deal with members of the public through their CRM would particularly benefit from this system.
Pros:
- Log forwarding: Feeds logs to SIEM and SOAR tools
- User risk assessment: Gives each user a risk score
- Compliance guide: Provides advice on steps to take to reach compliance
- Database activity monitoring: DB2, Oracle, Teradata, Sybase, Hadoop NoSQL, and SQL Server
- Transparent Data Encryption: Protection for data within the database
Cons:
- No free trial: IBM offers a demo
Finally, IBM Guardium for File and Database Encryption enforces policy-dictated encryptions. It offers centralized encryption key management capability which allows businesses to secure their data while also ensuring they stay GDPR compliant. The policies, meanwhile, are easily defined using a user-friendly management server and can then be rolled out and implemented across a number of operating systems (Windows, Linux, and Unix).
EDITOR'S CHOICE
IBM Guardium is our top pick for a database encryption tool because it offers compliance management, sensitive data discovery, and data access controls for files and databases. The system uses encryption to block all but authorized access, which is controlled through user accounts. The system also logs all access events for compliance auditing. This is a software package that you need to install and manage yourself. However, if you want to use cloud services, you can install it on a cloud account.
OS: Windows, Linux, Unix, Amazon AWS, Google, IBM Cloud, Microsoft Azure, and Oracle OCI
2. Vormetric Transparent Encryption

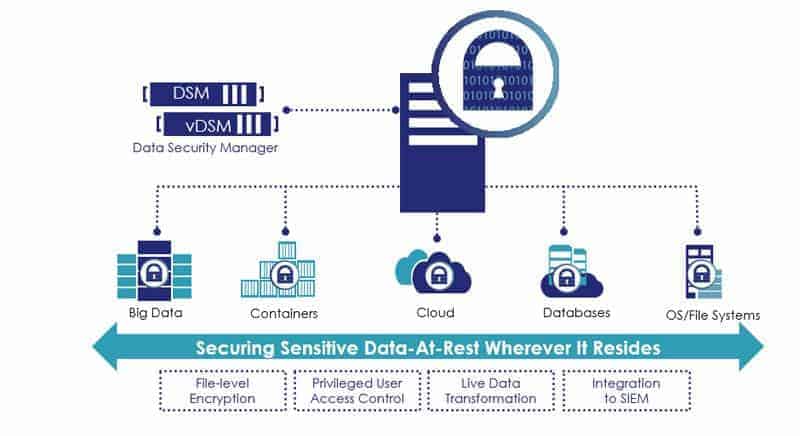
What makes this encryption solution stand out is its ability to secure data where it may be stored – locally, across multiple cloud storage solutions, and in big data. Administrators can opt for operating file system encryption or go for full-disk encryption.
Key Features
- Protects data: Files, big data storage, and databases
- Transparent encryption: Authorized users get instant access through real-time decryption
- Encryption level options: Encrypt each data file/database or the entire drive
- Data privacy standards compliance: PCI DSS, GDPR, and HIPAA
Why do we recommend it?
Vormetric Transparent Encryption provides data protection across platforms – on-premises, cloud, and virtual, but specifically focuses on data at rest. This means it will encrypt files and databases, providing central management of encryption keys, access control, and data usage logging. The service will automatically calibrate to PCI DSS, GDPR, and HIPAA requirements.
The sheer power of Vormetric Transparent Encryption is revealed by simply looking at the data it can cover: it is easily deployable, can be scaled to cover tens of thousands of physical or virtual servers, and works on Windows, Linux, and Unix platforms.
One unique feature that comes with this solution from Thales eSecurity is that no downtime is required for initial data encryption operations. Administrators can simply use the “Live Data Transformation” option where databases and files can be encrypted while the data is in use.
Again, there is no downtime, a fact that can be appreciated when considering some tools may require a clean slate – being installed on new database servers before data can be encrypted.
Who is it recommended for?
The unique selling point of this system is that it centralizes the management of a very large number of data stores that can be spread across the globe. Therefore, this is one of the few data protection tools with sufficient capacity for the largest international conglomerates in the world but a bit over-engineered for everyone else.
Pros:
- Access controls: Only authorized users trigger decryption to view data
- Activity tracking: User activity tracking identifies insider threats and account takeovers
- Suitable for datacenters: Can manage tens of thousands of servers at the same time
- Multiple environments: Protects data on virtual systems as well as physical servers
Cons:
- No price list: Makes assessing suitability difficult
3. DbDefence for Microsoft SQL

Key Features
- Specialized tool: Designed to protect data in SQL Server databases
- Real-time encryption: New records are immediately encrypted
- Transparent decryption: Authorized users see plain data without delay
Why do we recommend it?
DbDefense for Microsoft SQL is a very specialized database security system that seems to have no equal in the market. This system literally operates within the database and can mask individual columns in tables. It is also able to prevent some DBAs from getting sight of table contents.
This TDE tool offers data security solutions without compromising performance speeds. DBAs have full control over what they need to secure and configure DbDefence to work on tables (some or all of them), logins, and applications that access the restricted data.
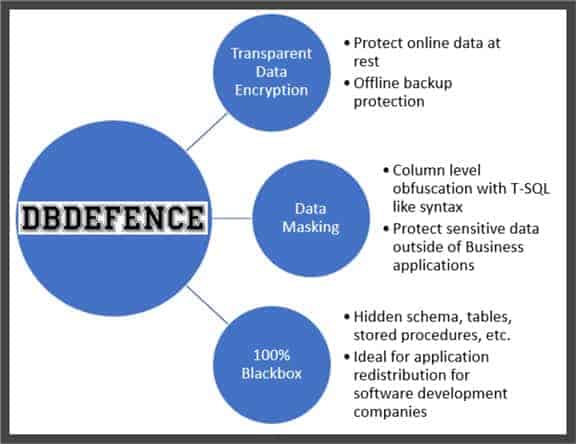
Configuration modes allow three levels of securing database files and data:
- TDE that takes care of encryption while data is at rest
- A “Blackbox” function that locks down databases from being able to browse objects (tables, procedures, and functions) without the proper authorization
- A middle-ground solution known as data masking (PDF) and which allows TDE protection as well as hiding sensitive columns from administrators and other Power Users
Finally, DbDefence is an effective encryption tool that is easy to set up and run; it is simply a lithe, effective SQL database encryption algorithm and yet has a tiny digital footprint.
Who is it recommended for?
This is a very important security tool and any business that holds sensitive data in SQL Server tables should use it. The ability to get right into the database and block access to the data in tables trumps all other security tools that deal with database access through the interfaces that extract and display data.
Pros:
- Data masking: Redact fields during display or printing without losing the original data
- Standards compliance: GDPR, HIPAA, and PCI DSS
- Security measures: Can hide schemas and individual tables
Cons:
- Can’t protect all data: Only operates on SQL Server databases
4. BitLocker

Key Features
- Included for free in Windows: Part of Windows since Windows Vista
- Entire disk encryption: Embedded in the operating system
- Easy to use: Does not require technical expertise
Why do we recommend it?
BitLocker is built into the Windows operating system and so it is free to use (once you have paid for Windows). This provides the tool with a very wide audience and makes it difficult for other encryption services to compete. However, it isn’t an enterprise solution.
BitLocker Drive Encryption, as it is officially known, is a built-in Windows data protection feature that has been available with Windows operating systems right from the early days of Vista. It serves to protect users from data loss or theft that may occur in case a device is stolen, lost, or negligently decommissioned. 
The main concept behind this security tool is to make sure that no unauthorized access is granted to a drive – whether by running software-attack tools or by physically moving a hard disk to a different computer.
An endearing factor of BitLocker is the fact that all it takes to secure a disk and all the data on it is just a few clicks.
Who is it recommended for?
One problem that buyers looking for a database encryption system will have with Bitlocker is that it encrypts drives rather than databases. Also, it works on an endpoint and can’t be centrally controlled, so it isn’t really an enterprise system. Very small businesses and private individuals will choose this tool.
Pros:
- Free system: Makes paying for a rival tool difficult to justify
- Trusted brand: Microsoft, BitLocker, and Windows are all respected brands
- Linked to a physical proof of identity: A USB key or a fingerprint scan to provide infallible identity proof
Cons:
- No central administrator controls: Only suitable for personal use or for owner-managed small businesses
A few words of caution
Now, although all these encryption tools offer a way to secure data, there will always be that one weak point: the administrator. Because should hackers gain access to the administrator password – whether it is due to negligence in keeping the password secure or because they didn’t care enough to use a complex one – nothing will stop them from gaining full access to the data.
Solution: never use default passwords. Also, create complex encryption passwords that can’t be guessed and do not write them down where anyone can find them.
The same applies to any applications that are given the authorization to access disks, file systems or databases; the hackers could exploit any weaknesses in the applications themselves and access the data by exploiting them.
Solution: be careful what roles and permissions you give to every application. Keep up with patches and updates so any exploits are thwarted.
Are there any drawbacks to using database encryption tools?
OK, we have just spent all this time discussing which tools would be a perfect fit for a number of database server setup scenarios. We have also touched on a couple of precautions.
Now, we will have a look at what the cons are when it comes to encrypting a database. Because, although you might be willing to secure your data, there are some aspects you also need to keep an eye out for. They are:
- Forgetting the password – administrators need to use complex passwords to truly secure their databases and, unfortunately, this makes it much easier for them to forget them; if they do, there’s probably no way of accessing that data ever again.
- A false sense of security – while encrypting data using these latest tools secures your data, it doesn’t mean that you should let your guard down; always be on the lookout for new methods of hacking. Make sure you keep your whole digital environment patched and updated.
- Resource hogging – while most database encryption tools aren’t resource-intensive, the case might change as your data grows and when you have a higher number of users or applications that continue to ask for more and more data. This security cost might be offset by increasing resources, but that will also mean convincing management to increase your budget
Looking at these drawbacks, it can safely be said that the advantages outweigh them by far. This leads us to the conclusion: if you have sensitive files and confidential data, you should always consider encrypting it.
Database Encryption FAQs
What is the difference between asymmetric and symmetric encryption?
Symmetric key encryption requires the same key to be used to encrypt and decrypt a text. With asymmetric encryption, a different key is used to decrypt a text to the one used to encrypt it. Symmetric encryption systems require that the key be shared, which is a hazardous process because if anyone intercepts the transmission of the key, the encryption is worthless. With asymmetric encryption, the encryption key needs to be kept private. However, the decryption key can be made public. Therefore, these are called the private key and the public key. It is impossible to work out the private key if you have the public key. Therefore, the recipient of an encrypted text can be sure that the declared sender actually created the encrypted text because the related public key decrypts it. For this reason, asymmetric encryption systems are often used for authentication.
What is the major issue with database encryption?
Database encryption improves data security. However, it does have disadvantages. For a start, encrypted data needs to be decrypted when accessed in order for it to be useful. Therefore, the decryption process slows down access to data. Encrypting the data for storage also slows down the data input phase. There is going to be a point that data extracted from the database will be in a plain text format. This is a point of weakness, particularly with database systems that cache results in memory for rapid, repeated access – this stores the data in an unencrypted format. Another problem is the issue of encryption keys. If the same key is used for the entire database, renewing that key would require all of the database’s contents to be decrypted and re-encrypted, which is a time-consuming task. If the encryption is not periodically renewed, there is a risk that the key could be discovered and all security compromised.
Is MySQL database encrypted?
By default, MySQL databases are not encrypted. However, encryption can be activated on a tablespace through the ALTER TABLESPACE command.






