Deep Instinct is an advanced cybersecurity solution designed to provide high-level protection for organizations against a wide array of cyber threats, including malware, ransomware, and advanced persistent threats. The deep learning-based approach of Deep Instinct offers one of the most proactive and innovative cybersecurity technologies available today. Traditional security systems rely on signature-based detection methods but Deep Instinct’s deep learning model is capable of analyzing and identifying threats in real-time.
This system identifies threats that were previously unseen by other security solutions. Its ability to predict and prevent attacks before they happen provides organizations with a proactive defense strategy. The solution uses a neural network to analyze files, behaviors, and patterns in data, making it effective in recognizing sophisticated and evolving cyber threats. Its predictive capabilities protect endpoints and extend to mobile and IoT devices, ensuring comprehensive coverage for all devices within an organization’s infrastructure.
With an emphasis on speed and efficiency, Deep Instinct operates without the significant performance impact typically associated with other security software. It offers organizations a lightweight yet powerful defense system that is easy to deploy and manage.
In this review, we will examine deeper into the features, benefits, and limitations of Deep Instinct, exploring how its deep learning-powered threat detection sets it apart from other solutions on the market and why it is gaining attention as an effective cybersecurity tool for businesses of all sizes.
Deep Instinct Prevention Platform Review
Deep Instinct is a cybersecurity company that applies deep learning to cybersecurity, especially in preventing and detecting malware. Deep Instinct is headquartered in New York City, United States, with Israel and United Kingdom operations. Deep Instinct takes a prevention-first approach to deal with zero-day threats and other modern cybersecurity challenges using its revolutionary deep learning framework. Deep Instinct prevents threats at the endpoint without requiring an agent. It also prevents threats beyond the endpoint by scanning the in-transit files of your applications and workflows, as well as local, private, and public cloud storage and web gateways to prevent the upload or download of malicious files while ensuring the integrity of your environment.
Key Features:
- Preventative Approach: Utilizes deep learning to preemptively stop zero-day and other advanced threats across endpoints and cloud environments.
- Low False Positive Rate: Achieves high EPP efficacy with a promise of fewer alerts and the industry’s lowest false positive rate.
- Broad Endpoint Protection: Supports a wide array of operating systems including Windows, macOS, Android, ChromeOS, and Linux, ensuring comprehensive endpoint security.
- Cloud and Application Security: Offers dedicated solutions for cloud storage and critical business applications, preventing malicious uploads and downloads.
- Web Gateway Protection: Integrates with web gateways via ICAP to prevent access to malicious content and reduce malware entry points.
Unlike other tools that often generate an overwhelming volume of alerts and false positives, the Deep Instinct Prevention Platform fulfills the promise of prevention by providing an improved endpoint protection platform (EPP) efficacy and the lowest false positive rate to stop unknown threats. In addition, deep Instinct prevents threats before execution, unlike most endpoint detection and response (EDR) solutions which rely on fundamental machine learning and require the attack to begin executing before it can be detected.
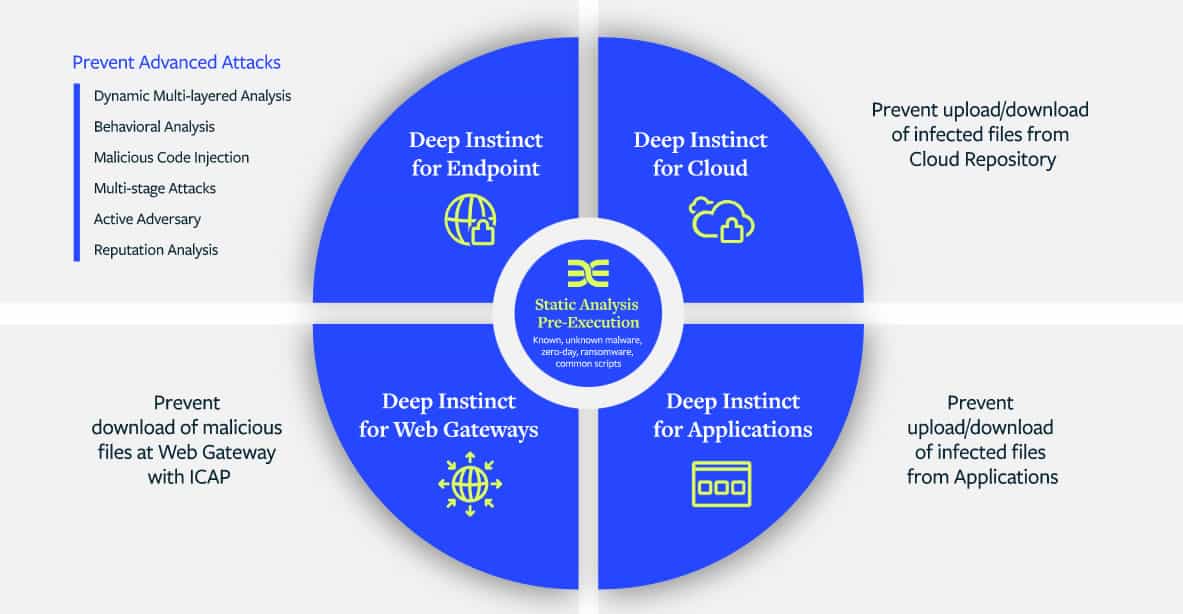
The Deep Instinct Prevention Platform is made up of the following key components:
Deep Instinct for Endpoint: Deep Instinct for Endpoint is a lightweight, agent-based solution that prevents known and unknown malware, including zero-day exploits, ransomware, remote code injection, fileless attacks, script-based attacks, among others. The moment an attacker attempts to infect your endpoint with a malicious payload, Deep Instinct prevents it even before it executes. This helps to improve the effectiveness of your existing security solutions while lowering false positives and your organization’s overall risk.
In addition to prevention, Deep Instinct also employs additional dynamic and behavioral analysis layers to detect and automate responses to identified threats. As a result, your security teams will spend less time responding to benign alerts and more time focusing on higher-value priorities.
Deep Instinct for Endpoint key benefits and capabilities include:
- Supported on Windows, macOS, Android, ChromeOS, and Linux operating systems.
- Increases the security team’s productivity and efficiency to fight threats.
- Lowers TCO and increases ROI of your entire security stack.
- Improves compliance standards for GDPR, PCI, and CCPA.
- Eliminates frequent cloud checks and agent updates.
- Maps to MITRE ATT&CK for faster investigations.
- Guaranteed false positive rate <0.1%.
- Extremely lightweight agent.
Deep Instinct for Cloud: Public cloud providers are responsible for the security of the cloud, but you are responsible for the protection of what is stored in the cloud. Preventing malicious content from entering your cloud storage is critical to lowering the risk that an infected file could spread malware. Deep Instinct for Cloud contains malicious content in your cloud by scanning files uploading to or downloading from your public or private cloud storage while ensuring the integrity of your cloud deployment.
Deep Instinct for Cloud key benefits and capabilities include:
- It prevents malicious files from uploading into public or private cloud storage.
- Keeps malware-infected files from reaching production systems.
- Improves existing security solutions by reducing the burden on the endpoint.
Deep Instinct for Applications: Deep Instinct for Applications is designed to protect your business-critical applications such as ERP, CRM, and others and prevent the introduction of malware into your production environments. When a file is uploaded through an application, a trigger calls Deep Instinct to scan the file. If the file is deemed malicious, the file is blocked, and according to the policy set by the organization, the file will be deleted or sent to a sandbox. This helps to assure that your applications will not be a source of infection for your end-users or customers.
Key features and benefits include:
- Reduces latency associated with traditional AV file scanning.
- Provides consistency of security standards across all applications.
- Scales to the needs of high-volume transaction applications.
Deep Instinct for Web Gateways: Deep Instinct for Web Gateways is designed to protect your network and prevent users from accessing malicious content from the internet with greater accuracy. If you are using a signature-based web proxy, for example, to filter traffic, when user requests from the internet hit the web proxy, Deep Instinct deployed with Internet Content Adaptation Protocol (ICAP) server (a lightweight HTTP-based protocol used to optimize proxy servers) scan files to ensure that malicious content from the internet does not get through.
Key features and benefits include:
- Improves end-user experiences by reducing latency associated with legacy AV solutions.
- Reduces malware at the entry point, reducing the burden on security teams and analysts overwhelmed with alerts.
- Prevents a more significant number of known and unknown threats at the web gateway.
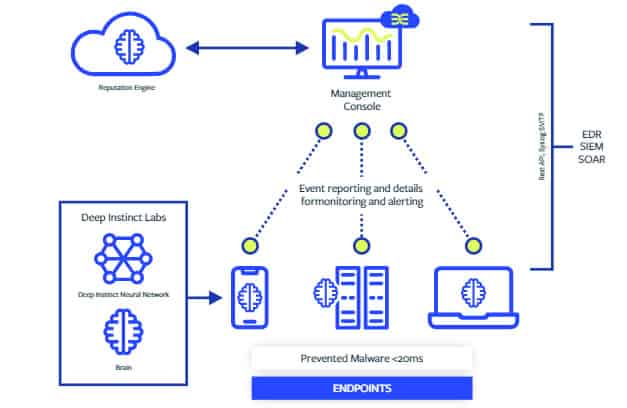
Deep Instinct integrates seamlessly with EDR, SIEM, SOAR, and other tools via REST API, Syslog, or SMTP to improve investigation, remediation, and threat hunting. If you are considering this solution for your network, the system requirement is as follows:
| Parameters | System Requirements |
|---|---|
| Operating System | Windows 7 SP1, 8, 8.1, 10 Windows Server 2008 R2 SP1, 2012, 2012 R2, 2016 |
| .Net Framework | Version 3.5 or higher |
| CPU | Dual-core CPU or higher |
| RAM | 2 GB or higher (recommended 4 GB) |
| Disk Space | 500 MB free disk space |
| Supported Virtual Environment | Amazon Workspaces, Citrix Systems XenServer, XenDesktop, and XenApp. VMware ESX and Horizon, Microsoft Hyper-V, Oracle VirtualBox |
Pros:
- Advanced Deep Learning Technology: Stands out by using deep learning for proactive threat prevention, setting a new standard in cybersecurity effectiveness.
- Cross-Platform Support: Provides extensive coverage, ensuring security across various operating systems and extending protection to mobile and cloud environments.
- Operational Efficiency: Significantly reduces the time security teams spend on false positives, allowing focus on more strategic tasks.
- Compliance Enhancement: Helps in meeting key compliance standards such as GDPR, PCI, and CCPA by bolstering data protection measures.
- Agent Efficiency: Features an extremely lightweight agent that minimizes system impact while eliminating frequent updates and cloud checks.
Cons:
- Learning Curve: The sophistication of deep learning technology might present a learning curve for teams less familiar with such advanced solutions.
- Integration Complexity: While offering comprehensive protection, integrating across diverse environments and platforms could be challenging without adequate technical expertise.
The leading Deep Instinct alternatives
Deep Instinct platform is not a one-size-fits-all solution for everyone. If you figure out that it is not best suited for your needs or environment and you’re considering a suitable alternative, you’ll find lots of them out there. To help you decide between the countless options out there, we’ve put together a list of the ten best Deep Instinct platform alternatives. Hopefully, this will guide you in the process of selecting the right one that meets your needs.
1. CrowdStrike Falcon
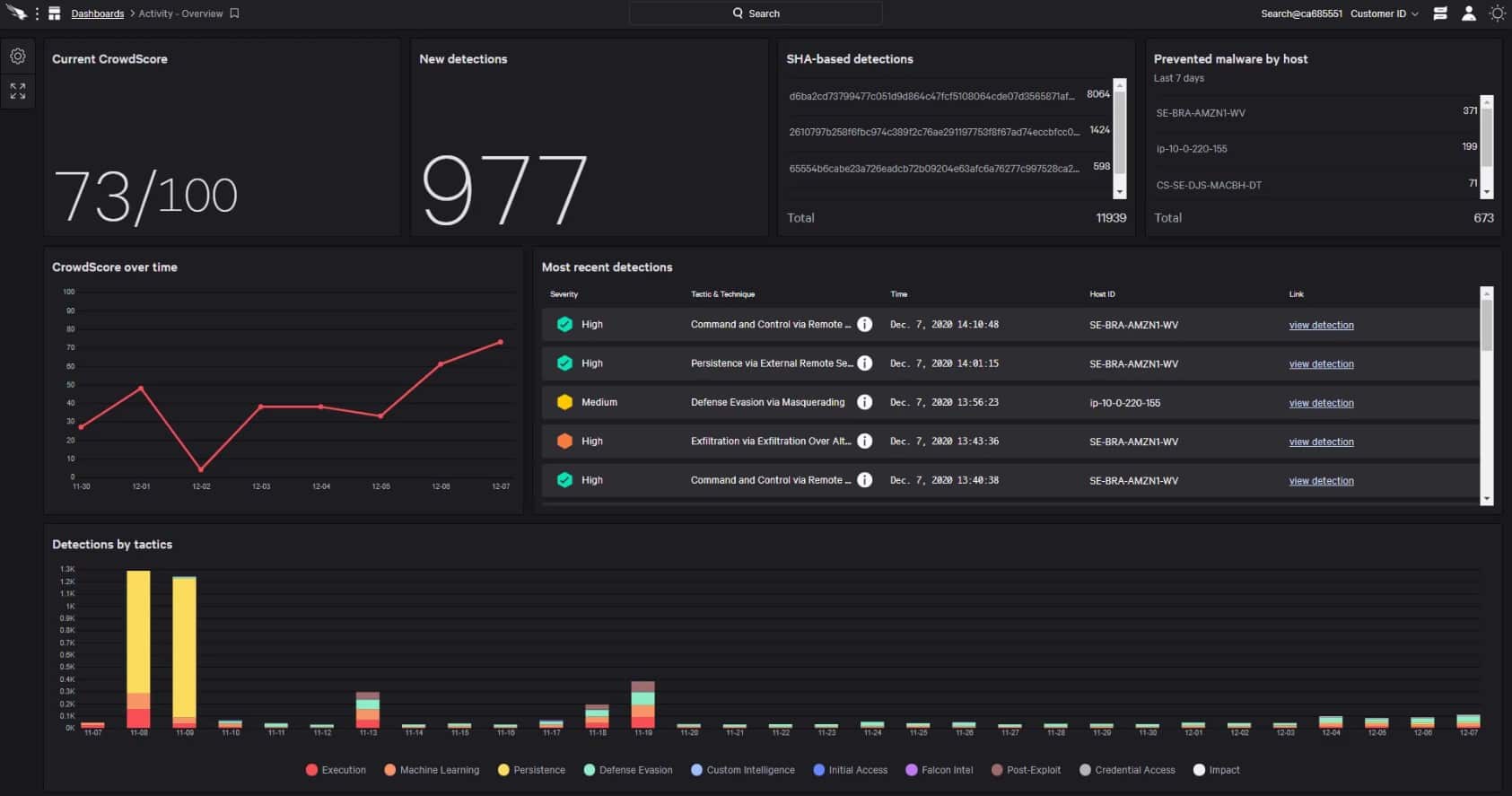
CrowdStrike Falcon is a unified set of cloud-delivered technologies that prevent all types of attacks — including zero-day malware and much more. CrowdStrike Falcon responds to those challenges with a cloud-managed lightweight solution that unifies next-generation antivirus (NGAV), endpoint detection and response (EDR), cyber threat intelligence, managed threat hunting capabilities, and security hygiene.
Key Features:
- Comprehensive Attack Prevention: Integrates various technologies to thwart all attack types, including elusive zero-day threats.
- Unified Cloud Solution: Offers a lightweight, cloud-managed security platform combining NGAV, EDR, and more.
- Extensive Security Suite: Features include Falcon Prevent (NGAV), Falcon Insight (EDR), Falcon Device Control, Falcon Firewall Management, Falcon for Mobile, and Falcon Forensics.
In addition, the CrowdStrike Falcon Platform includes:
- Falcon Prevent Next-Generation Antivirus (NGAV)
- Falcon Insight Endpoint Detection and Response (EDR)
- Falcon Device Control USB Device Control
- Falcon Firewall Management Host Firewall Control
- Falcon For Mobile Mobile Endpoint Detection and Response
- Falcon Forensics Forensic Data Analysis
Pros:
- All-in-One Security Platform: Provides a complete range of security tools from antivirus to forensic analysis within a single framework.
- Leader in Endpoint Protection: Recognized as a Leader in the 2021 Gartner Magic Quadrant for its robust endpoint protection capabilities.
- Cloud-Managed and Lightweight: Ensures efficient operation without heavy on-premise infrastructure, facilitated by cloud management.
- Free Trial Availability: Offers potential users a chance to experience its features firsthand through a free trial request.
Cons:
- Learning Curve: The extensive suite of tools and capabilities may require a significant time investment to fully understand and utilize effectively.
- Cost Consideration for SMEs: While pricing details are not mentioned, the comprehensive nature of the platform might imply a higher cost, which could be a consideration for small to medium enterprises (SMEs).
CrowdStrike was also named a Leader in the 2021 Gartner Magic Quadrant for Endpoint Protection. A free trial is available on request.
2. Microsoft Defender for Endpoint (MDE)
Microsoft Defender for Endpoint is an endpoint security platform designed to prevent, detect and respond to modern threats in enterprise networks. MDE uses a combination of endpoint behavioral sensors embedded in Windows 10, next-generation protection, cloud security analytics from big data, device-learning, etc., and threat intelligence generated by Microsoft hunters and other sources to combat cyberattacks in the enterprise.
Key Features:
- Comprehensive Protection: Combines endpoint behavioral sensors, next-gen protection, cloud analytics, and threat intelligence to counteract cyber threats.
- Cross-Platform Support: Offers robust security solutions for Windows, macOS, Linux, iOS, and Android platforms.
- Advanced Threat Detection: Utilizes big data analytics and machine learning to detect and respond to threats across the enterprise landscape.
Microsoft is also recognized as a Leader in the 2021 Gartner Magic Quadrant for Endpoint Protection Platform. MDE is supported on Windows, macOS, Linux server, iOS, and Android devices.
Pros:
- Integrated Ecosystem: Leverages the broader Microsoft security framework for enhanced protection and seamless integration with other Microsoft products.
- Extensive Device Coverage: Ensures enterprise-wide security across a broad range of devices and operating systems.
- Real-Time Threat Intelligence: Benefits from Microsoft’s vast threat intelligence network, offering timely and effective threat mitigation.
- Flexible Deployment Options: Meets diverse enterprise needs with both cloud-native and on-premise deployment solutions.
- Trial Availability: Allows organizations to evaluate the platform’s capabilities through a free trial request.
Cons:
- Complexity in Management: The extensive features and capabilities may present a steep learning curve for IT teams unfamiliar with Microsoft’s security tools.
- Potential for Overlap: Organizations already using multiple security solutions may need to assess the overlap and integration with existing tools.
Deployment options include On-premise, cloud-native, among others. A free trial is available on request.
3. Trend Micro Apex One
Trend Micro Apex One defends endpoints against fileless malware, ransomware, malicious scripts, and other malware. Trend Micro is recognized as a Leader in the 2021 Gartner Magic Quadrant for Endpoint Protection. Apex One offers threat detection, response, and investigation within a single agent. Its extensive detection and response capabilities (XDR) extend detection and response capabilities with cross-layer detection, threat hunting, and investigation across email, endpoints, servers, cloud workloads, and networks together in one console. Trend Micro provides both SaaS and on-premises deployment options. A 30-day free trial is available on request.
4. Sentinel One Singularity platform
Sentinel One is a cybersecurity startup that uses machine learning for monitoring personal computers, IoT devices, and cloud workloads. It is recognized as a Leader in the 2021 Gartner Magic Quadrant for Endpoint Protection Platform. Sentinel One Singularity is an XDR platform that utilizes its patented heuristic model behavioral AI to prevent, detect, and respond to cyberattacks. Sentinel One Singularity is a one-stop platform for EPP, EDR, NGAV, firewall, device control, cloud workload security, threat intelligence, network visibility, and control; and A free online demo is available on request.
5. McAfee Endpoint Threat Defense and Response
McAfee Endpoint Threat Defense and Response brings together robust threat detection and correction tools such as:
- Real Protect: Applies state-of-the-art machine learning techniques to identify malicious code
- Dynamic Application Containment (DAC): Makes it easy to protect systems from infection without sacrificing productivity
- Active Response: advanced malware hunting and response capabilities that enable analysts to uncover threats anywhere in the environment
McAfee was named a Leader in the 2021 Gartner Magic Quadrant for Endpoint Protection. A free online demo is available on request.
6. Sophos Intercept X Endpoint
Intercept X from Sophos is one of the leading endpoint protection software that combines endpoint detection and response (EDR), extended detection and response (XDR), managed threat response (MTR), deep learning AI capabilities, and more to prevent, detect and respond to modern cyberattacks from a unified console. Sophos is recognized as a Leader in the 2021 Gartner Magic Quadrant for Endpoint Protection Platform. Intercept X is available for devices running on Windows and macOS. Licensing is based on per-user pricing with no upfront infrastructure cost. A free trial and online demo are available on request.
7. VMware Carbon Black Cloud Endpoint
Carbon Black is a cybersecurity company developing cloud-native endpoint security software designed to prevent and detect cyberattacks. Carbon Black leverages the Predictive Security Cloud (PSC)–a big data and analytics cloud platform that analyzes unfiltered user data for threats. VMware Carbon Black Cloud Endpoint Standard combines next-generation antivirus (NGAV), endpoint detection and response (EDR), and behavioral analytics to prevent, detect and respond to modern cyberattacks. A free online personalized demo is available on request.
8. Cylance AI
Cylance is a software company that applies AI and machine learning techniques to cyber security to prevent, rather than reactively detect malware. Cylance is noted for its pioneering role in developing antivirus and other computer security applications that effectively neutralize cyber threats before they can exploit or infiltrate systems. BlackBerry acquired the company in 2019. Cylance AI is now the technology that powers the following leading BlackBerry security applications:
- BlackBerry Protect–an AI-based endpoint protection platform (EPP)
- BlackBerry Optics–an AI-driven endpoint detection and response (EDR) works with BlackBerry Protect
- BlackBerry Persona–an endpoint user and entity behavior analytics (UEBA) solution that uses predictive AI
- BlackBerry Gateway–an AI-driven Zero Trust network access (ZTNA) solution
9. Cybereason Defense Platform
Cybereason is a cybersecurity company that offers a unified endpoint protection platform. Multiple layers of machine learning algorithms power the Cybereason Defense Platform to uncover zero-day and other forms of malware. In addition, the platform provides comprehensive prevention, detection, and response solutions via a single lightweight agent.
Cybereason plans and features include:
- Professional: Prevention-focused protection targeted at SMBS
- Business: Combines threat intelligence, NGAV, EDR, MDR, threat hunting, and more to prevent, detect, and respond to cyberattacks targeted at SMBS
- Enterprise: Advanced prevention, endpoint controls, and critical tools for your SOC needs.
- Ultimate: Comprehensive attack protection including breach protection warranty targeted at enterprises of all sizes
10. Symantec Endpoint Security
Symantec is a well-known brand in endpoint security and has one of the largest market share of any product for endpoint security. Symantec Endpoint Security combines intrusion prevention, firewall, anti-malware, and some DLP features as a single-agent platform designed to protect all your traditional and mobile endpoint devices. It applies machine learning and behavioral analytics to prevent, detect, and respond to malicious activities. Symantec Endpoint Security is a flexible solution deployed on-premise, in the cloud shares, or hybrid. It is typically supported on machines running Windows, Linux, or macOS. With or without Symantec Agent installed, endpoints can leverage the EDR cloud-based portal using a dissolvable agent and on-premises collection server. It is supported on machines running Windows, Linux, or macOS. The product can be purchased via Broadcom authorized distributors and partners in your region or country.