Networks carry vast amounts of sensitive data and so understanding and managing network traffic is essential for ensuring security, performance, and compliance. Deep Packet Inspection (DPI) has emerged as a powerful tool for achieving this. Unlike basic packet filtering, which examines only the header information of a data packet, DPI dives deeper, analyzing the actual content of the packet to make more informed decisions about how to handle it.
What is Deep Packet Inspection?
Deep Packet Inspection is a sophisticated method of network traffic analysis that examines packets at the Application layer of the OSI model. By inspecting both the packet header and its payload, DPI provides insights into the nature, purpose, and potential risks of the traffic traversing a network. This makes it an invaluable technology for managing modern networks, where threats are often concealed in encrypted or seemingly benign traffic.
Why is DPI Important?
DPI serves multiple critical functions across different domains:
- Network Security: Identifying and blocking malware, ransomware, and other malicious traffic.
- Traffic Management: Prioritizing bandwidth for critical applications and reducing congestion caused by non-essential traffic.
- Compliance: Ensuring that data traffic adheres to regulatory standards by monitoring and filtering sensitive content.
What This Guide Offers
This comprehensive guide will demystify Deep Packet Inspection, explaining how it works, its advantages, and the challenges it presents. We will also explore its applications in cybersecurity, internet service provisioning, and enterprise network management. Whether you’re a network administrator, security professional, or IT enthusiast, this guide will equip you with the knowledge needed to understand and leverage DPI effectively.
Dive in to explore how DPI is reshaping network management and fortifying digital defenses in today’s complex IT landscape.
Here is our list of the best Deep Packet Inspection and Analysis tools:
- ManageEngine DataSecurity Plus EDITOR’S CHOICE This package is primarily concerned with protecting data on site and in the cloud but it also performs DPI to impose content controls on Web pages requested on company browsers. Start 30-day free trial.
- ManageEngine NetFlow Analyzer (FREE TRIAL) This package provides a range of methods to examine and record packet details including flow protocols and DPI. Runs on Windows Server, Linux, and AWS. Start a 30-day free trial.
- Site24x7 Network Monitoring (FREE TRIAL) This cloud-based system includes packet header examination for protocol analysis and top talkers definitions. Start a 30-day free trial.
- Paessler Packet Sniffing with PRTG The PRTG system is an infrastructure monitoring tool and it includes a packet sensor.
- SolarWinds Network Performance Monitor This network monitoring tool includes deep packet inspection to identify the source and destination applications and endpoints on network traffic. Runs on Windows Server.
- nDPI This tool inspects packets at the application layer, which means that you need to buffer traffic for inspection.
- Netifyd An adaption of nDPI that captures packets for inspection by other services.
- AppNeta A Cloud-based network monitoring system that includes offline traffic analysis.
SPI Vs DPI
Advancements on gateways that examine the IP header are “stateful” firewalls. They employ Stateful Packet Inspection (SPI). This methodology examines the TCP or UDP headers, which are enclosed within the IP packet. Stateful packet inspection is also known as shallow packet inspection. Deep Packet Inspection (DPI) looks at the data payload of the packet.
SPI examines individual packets as they are processed by the gateway, and selectively drops outgoing requests or incoming data packets that don’t comply with the network security policy. The “stateful” part of the name refers to connection data. The firewall records header information relating to the TCP connection, which enables it to follow a stream of packets. The type of stateful header data that the firewall collects includes the sequence number of packets.
A stateful firewall typically stores this connection information in memory, enabling it to pick out streams of related packets as they pass through the interface. Connection data is held in a dynamic table. Once a connection is closed, that information is wiped from the table to free up memory. The stateful firewall is more likely to block connections while they are in progress. Stateful packet inspection analysis only focuses on live data.
DPI collects packets to be examined as a group, so regular traffic continues on its way while copies are harvested for analysis. This is why DPI is often referred to as “deep packet analysis“. DPI takes longer to produce actionable intel than SPI.
Benefits of deep packet inspection and analysis
Intrusion detection systems look for “signatures” in data traffic to identify irregular activity. One trick hackers use to get around these attack signature detection systems is to split up packets into smaller segments. This spreads the patterns that shallow packet analysis looks for, so no single packet contains that signature and the attack gets through. DPI analysis reassembles streams of packets from the same source, so the attack signatures can be detected even when spread over several incoming packets.
When DPI analysis is part of an intrusion prevention system, the ongoing analysis results generate and apply actions to automatically defend the system. Such action may include blocking all packets arriving from a particular source IP address or even a range of addresses.
Attack detection
The collection of packets enables DPI to identify types of service attacks that stateful analysis would miss. Examples of these are the irregular use of standard network utilities, such as PowerShell or WMI, and directed volume overloads, such as buffer overflow attacks. The use of regular system utilities in virus infection or spyware operations means that a ban on the applications known to be used by hackers cannot be enforced. This is because those system utilities are essential for the delivery of applications and service to legitimate users. Thus, deep packet inspection and analysis steps in to examine the usage patterns of those system services and selectively roots out the traffic that displays suspicious behavior. Thus, malicious activity can be identified even though it initially seems to be legitimate traffic.
Data leak prevention
Data leak prevention is another use for deep packet analysis. This takes a whitelisting approach. The company can set a policy that no one should be allowed to copy data onto a memory stick or send email attachments. But there are legitimate instances where such actions are necessary. In this case, the DPI would be notified to allow through what would otherwise be treated as an unauthorized activity. That user shouldn’t be allowed to send out any file, and so the DPI function keeps monitoring activities to block file transfers other than the authorized attachment.
The best deep packet inspection and analysis tools
Sophisticated network monitoring systems now include deep packet analysis routines. So, you can get this facility as part of your general network management software. Some software providers produce network defense software that incorporates deep packet analysis.
Our methodology for selecting a deep packet inspection tool
We reviewed the market for DPI systems and analyzed the options based on the following criteria:
- Packet scanner that can read headers
- Nice to have SSL offloading on a private network to read payload
- A system that performed live monitoring of network devices
- The option to use SPI instead of DPI
- Guidance to dereference packet header codes
- A free trial or a demo service to assess the software without paying
- Value for money from a system that provides a useful service at a fair price or for free
1. ManageEngine DataSecurity Plus (FREE TRIAL)
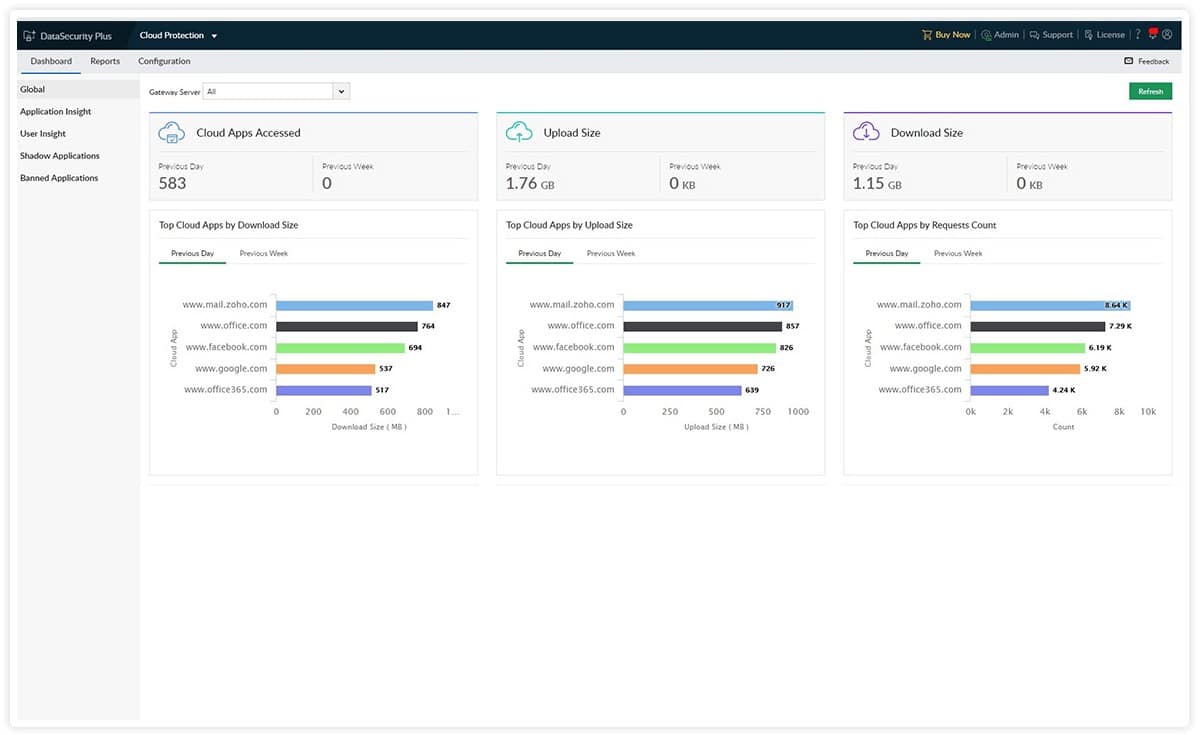
ManageEngine DataSecurity Plus is a very large package of data protection systems. It includes a Cloud Protection module that operates on internet traffic through deep packet inspection. This tool looks at transfers between your site and your cloud accounts and also provides policy enforcement to block inappropriate or offensive Web content from loading into the browsers in your company.
Key Features:
- Data transfer controls
- Web content filtering
- Infected site detection
- Trusted application list
Why do we recommend it?
ManageEngine DataSecurity Plus is a good choice for businesses that want to host all of their monitoring and management systems on their own servers. This package runs on Windows Server. The package is a collection of four modules, which are priced separately, so you don’t have to take the whole bundle.
This module provides a diverse list of services in addition to the sensitive data discovery and protection services of the main DataSecurity Plus package. The entire system is able to enforce compliance with SOX, HIPAA, FISMA, GDPR, PCI, and GLBA.
Who is it recommended for?
This system is particularly geared towards data loss prevention and so it will be of interest to businesses that handle sensitive data. The package includes an application allow-listing system, which is a handy way to block all malware from running and discourage users from installing their own favorite tools.
Pros:
- Blocks phishing and malware sites
- Enforces Web usage policies
- Identifies and protects sensitive data
- Controls data movements
- Enforces data protection compliance and provides reporting
Cons:
- No SaaS version
The DataSecurity Plus system is really a bundle of ManageEngine units and each module has an individual price, so calculating the cost of the entire package can be complicated. The software for the bundle runs on Windows Server and you can get it on a 30-day free trial.
EDITOR'S CHOICE
ManageEngine DataSecurity Plus is our top pick for a Deep Packet Inspection (DPI) tool because of its comprehensive capabilities in monitoring, analyzing, and securing network traffic. It offers detailed insights into network packets, providing a thorough analysis of data flows. This helps detect potential security threats, anomalies, and performance issues. By inspecting data at a granular level, DataSecurity Plus enables IT teams to identify malicious activities such as unauthorized access, malware, and data exfiltration attempts. This level of visibility is crucial for ensuring strong network security, particularly in environments handling sensitive or regulated data. In addition to its powerful DPI capabilities, DataSecurity Plus provides a user-friendly interface that simplifies the process of managing and interpreting packet data. It supports the inspection of both inbound and outbound network traffic, ensuring that all potential threats, whether internal or external, are detected. The tool also integrates with other security systems and monitoring tools, providing a unified view of the network’s health and performance. Real-time alerts and automated responses allow IT teams to act swiftly when a threat is identified, minimizing potential damage. ManageEngine DataSecurity Plus offers detailed reporting and analysis features, making it an excellent choice for compliance-heavy industries such as finance and healthcare. The tool supports auditing and ensures that organizations can maintain full visibility of network traffic, meet regulatory requirements, and protect their data.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/data-security/download.html
OS: Windows Server
2. ManageEngine NetFlow Analyzer (FREE TRIAL)
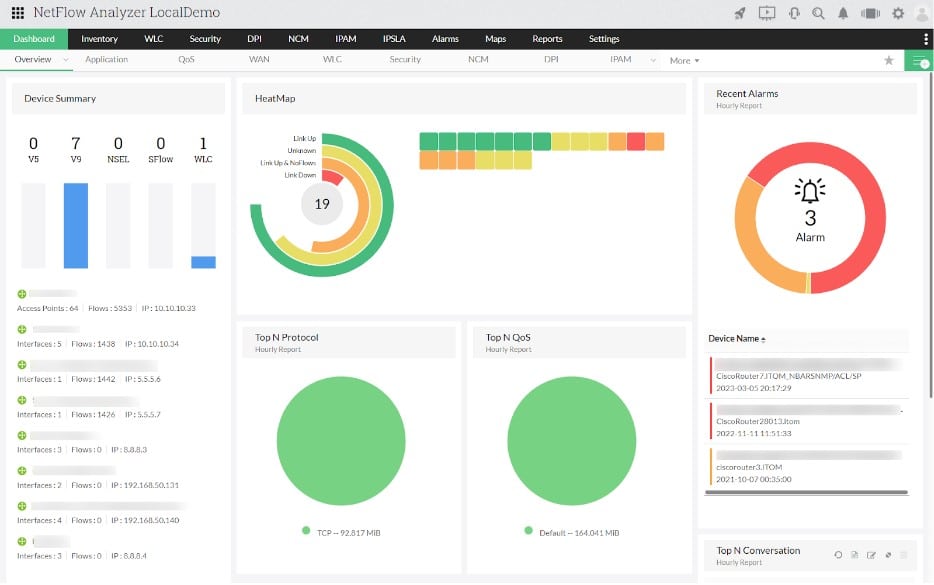
ManageEngine NetFlow Analyzer is a package of traffic monitoring tools and it includes a DPI tool, which is called the Network Packet Sensor. This tool will read the contents of packet headers and payload. However, be aware that is the payload is encrypted, you won’t get any meaningful information out of it.
The packet header data above all gives you a protocol analyzer because it can see the port number in the header of each packet and derive statistics from accumulating counts. So, the dashboard can show you top talkers per endpoint, external IP address, or protocol – which also means application.
Key Features:
- Protocol analyzer
- VoIP Quality of Service sores
- Bottleneck identification
- Device overload monitoring
Why do we recommend it?
The design aim of NetFlow Analyzer is to spot the build-up of traffic in one part of the network and the overloading of individual network devices. If a switch or router can’t handle all of the traffic that arrives at it, packets get dropped – they just disappear because the device can’t pass it on to the next link in the route.
Session control features TCP will record the non-arrival of a packet in a stream, resulting in it being resent, All of this puts extra load on a network by increasing the number of tries that it takes to send each packet, so it is better to intervene and prevent overloading because the traditional problem resolution processes of TCP just makes traffic load a whole lot worse.
You can set up traffic volume alerts so that they are at a percentage of device capacity – say, 80 percent. This will trigger an alert and also generate a log message. Each traffic surge can be dealt with by replanning the network or by implementing traffic shaping measures, such as queuing. Analysis of protocol and endpoint traffic from the DPI feature lets technicians see where all of the traffic is coming from. With this, a focus on specific types of traffic can introduce procedural solutions, such as shifting administrative tasks to overnight hours.
Who is it recommended for?
No one likes overspending on network equipment, so this tool is suitable for businesses of all sizes. The package probably wouldn’t add too much value to small businesses. Mid-sized and large companies need to know capacity demands not just by overall volumes but traffic generator data by protocol and source. You also need to be able to see differences in volumes per link.
Pros:
- Network capacity planning assistance
- Historical time-series graphs
- VoIP traffic analysis
- Alerts for device overloading
Cons:
- The Free edition only covers two interfaces
The NetFlow Analyzer installs on Windows Server or Linux. You can also get it as a service on AWS Marketplace. There is a Free edition but that only monitors two interfaces, which isn’t much use for any business. The paid versions are the Professional edition for a LAN and the Enterprise edition for a WAN. You can get the Professional Edition on a 30-day free trial.
3. Site24x7 Network Monitoring (FREE TRIAL)
Site24x7 Network Monitoring provides network device status monitoring and traffic analysis. The traffic monitoring part of the system extracts throughput data with flow protocols. These include NetFlow, IPFIX, sFlow, J-Flow, cFlow, AppFlow, and NetStream. These protocols are embedded in switches and routers and they read the headers of packets as they pass through.
Key Features:
- Network flow protocols
- Packet header data
- Traffic analysis
Why do we recommend it?
Site24x7 Network Monitoring cuts out the task of reading packet headers by extracting the data that switches accumulate by reading that data themselves. Thus, as this information is stored within network devices, using a suitable language to copy that information prevents the need to repeat the effort.
The packet header data gives Site24x7 information on traffic volumes per source and destination and by protocol. The network traffic analysis dashboard in the Site24x7 console shows traffic data overall and segmented by protocol, source, and destination. It is possible to see traffic throughput rates per link.
Performance expectation thresholds in the Site24x7 package will trigger alerts if crossed. This could be because traffic is approaching the full capacity of a switch or because traffic throughput has suddenly dropped.
The Site24x7 system will also raise alerts if its network device monitoring service detects a component failure that could shut the device down. There are also performance alerts built into the companion modules on the platform that monitor servers and applications.
Who is it recommended for?
This package is suitable for businesses of all sizes and is particularly useful for those companies that need to squeeze the best value out of existing network hardware. By examining the generators of traffic on the network, an administrator can work out how to reduce peaks in demand by implementing queueing or moving batch jobs to run out of office hours.
Pros:
- Uses packet header data to analyze traffic
- Identifies the top generators of network traffic
- Provides data on traffic throughput per link and also across the internet
Cons:
- No on-premises hosting option
You can’t get the Network Monitoring service from Site24x7 by itself. The platform provides plans that bundle all of the modules on the platform together. So you pay a monthly fee to access the whole platform of system monitoring and management tools. There is a special edition available for managed service providers. You can try out Site24x7 with a 30-day free trial.
4. Paessler Packet Sniffing with PRTG
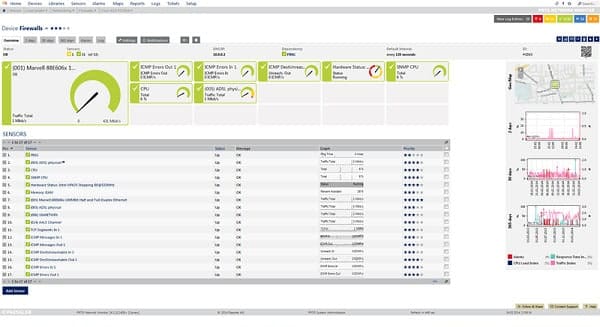
Paessler Packet sniffing with PRTG is a comprehensive network monitoring tool that includes DPI in its data gathering procedures. The Packet sniffer of PRTG analyzes specific traffic types to monitor for resource usage and irregular activity. The monitor reports on those traffic types and their throughput including web traffic, mail server activity, and file transfers. These controls can be very useful for imposing mail and data security policies, and they will enable you to spot surges in traffic that could be indications of intrusion or cyber-attacks.
Key Features:
- Traffic statistics per application
- Data presented in graphs and charts
- Network monitoring
- Alerts for performance problems
Why do we recommend it?
Paessler PRTG provides packet sniffing as one of its many sensors. Each sensor is an individual monitoring service. The packet sniffing tool can be supplemented by other tools to track traffic, which include NetFlow, J-Flow, sFlow, and IPFIX monitors. You can identify the port in each packet header to assess traffic patterns.
If you are particularly interested in using deep packet analysis for security, then the information that you will get on DHCP, DNS, and ICMP traffic should be of particular use to you.
The packet sensor page in the PRTG dashboard features dials and graphs to help you make sense of traffic data quickly.
Who is it recommended for?
This tool is available in a free version, which is limited to 100 sensors. This is a good choice for small businesses and is enough to activate the network discovery and packet sniffing features of the bundle. Mid-sized and large enterprises would probably need to activate more sensors.
Pros:
- Uses a combination of deep packet analysis, WMI, and SNMP to report network performance data
- Can monitor baselines and automatically alert to abnormalities.
- Drag and drop editor makes it easy to build custom views and reports
- Supports a wide range of alert mediums such as SMS, email, and third-party integrations into platforms like Slack
- Each sensor is specifically designed to monitor each application, for example, there are pre-built sensors whose specific purpose is to capture and monitor VoIP activity
- Supports a freeware version
Cons:
- Is a very comprehensive platform, not designed for home use hobbyist use.
Paessler PRTG can be installed on Windows and there is a free version for small networks. This will cover 100 sensors on your network. A sensor is a monitoring point on a network, such as a port or a condition like free disk space. You can download the software for a free trial here.
5. SolarWinds Network Performance Monitor
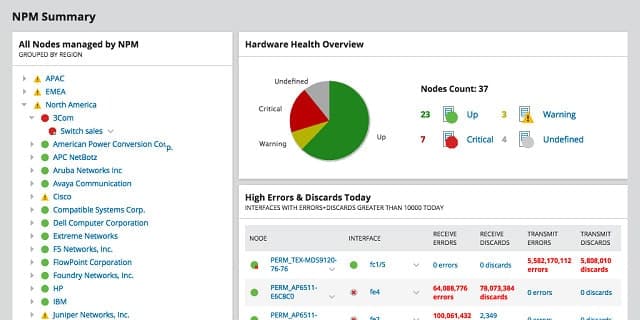
The SolarWinds Deep Packet Inspection and Analysis with NPM uses a range of techniques to monitor and manage network traffic. The main element uses the SNMP messaging system that is native to the firmware of network equipment. However, the analysis sections of the monitor use deep packet inspection (DPI) as part of the tool’s network behavior visibility services.
Key Features:
- Protocol analysis
- Traffic categorization
- Network discovery
- Device performance tracking
- Alerts for traffic issues
Why do we recommend it?
SolarWinds Network Performance Monitor is an on-premises package for Windows Server that uses SNMP to discover all devices on a network, compile a network inventory, create a network topology map, and then perform constant device monitoring. This is one of the leading network monitoring services available.
The purpose of DPI in the SolarWinds tool satisfies two aims of network administrators. The first is to identify the types of traffic that use up most of the system’s resources. Excessive load on the network makes the working environment difficult for everyone and it is important to find out exactly where all of that demand originates. DPI provides this data, and once the resource hoggers have been identified, it is easier for the network administrator to decide what to do about them.
Deep packet inspection also gives the Network Performance Monitor security functions. DPI techniques will identify specific user behavior and applications that cause surges in traffic and display erratic behavior. Those peaks in demand could be caused by hacker attacks, however, they could also be caused by business requirements, such as end-of-the-month account processing. DPI lets you see whether those surges are generated by legitimate business activities. Irregular behavior can be blocked.
You can extend your monitoring capabilities for networks by adding on the NetFlow Traffic Analyzer, which extracts activity data from network devices, including switches, routers, and firewall devices. The combination of the Network Performance Monitor and the NetFlow Traffic Analyzer is called the Network Bandwidth Analyzer Pack and you can get that bundle on a 30-day free trial.
User tracking may highlight unusual activity. For example, one user account could have been compromised, leading that user to access services that don’t tie in with his usual activities. Logins from disparate physical locations within short periods can also identify a user account that has been compromised.
The employment of deep packet analysis by SolarWinds in the Network Performance Monitor shows this technique is not just of use to security specialists. SolarWinds does include deep packet analysis for intrusion detection, but it also uses the system to help shape regular traffic and examine the categories of application traffic that overload the system. The use of DPI to support legitimate business activities points the way forward for all network monitoring systems. The sophisticated methods of DPI are now becoming mainstream and will become a central part of all network traffic monitoring systems in the future.
Who is it recommended for?
This package is comprehensive and is suitable for large businesses. Mid-sized businesses could also use this system. However, its functions are probably a little too extensive for the needs of small businesses. The service provides automated network device monitoring but it requires an add-on package to track traffic patterns.
Pros:
- Built with scale and enterprise in mind, can support thousands of devices across multiple LANs
- Can identify user-specific behavior and automate remediation actions
- Can support WAN environments and multiple VPN configurations
- Dashboard configuration uses simple drag-and-drop widgets for easy customization
- Alerts allow sysadmins to manage their LAN more proactively than most other products
Cons:
- This is an enterprise tool and can take time to fully explore and all of its features and options
The Network Performance Monitor is not free. The price for this system starts at $2,955. However, you can get a free trial for 30 days. The SolarWinds Network Performance Monitor can only be installed on Windows Server operating systems.
6. nDPI
OpenDPI is an open-source project of deep packet analysis tools. An open source project allows anyone to see the source code of an application. That assures users that there are no hidden tricks or damaging malware procedures buried inside. nDPI from Ntop is based on the OpenDPI code and expands its functionality. The source code for nDPI is also available.
Key Features:
- Free to use
- Partners with ntop
- SSL certificate analysis
Why do we recommend it?
nDPI is an open-source project that provides deep packet inspection in a library of functions. This package’s code can be viewed and amended. Thus, you can call the functions, change their parameters, alter their data types, or rewrite large sections as you please. This package doesn’t provide a full monitoring system.
This open-source model gives you the option of installing it as is or modifying the system to suit your business’s needs. Modification of open source code is very common and many people who create enhancements for such systems also make those new features available to the community. In some cases, the organization that manages the source code will accept those changes into the core version. Ntop keeps nDPI separate from the original OpenDPI, so you have two open source options.
nDPI operates at the Application Layer. That means it unifies packets before examining their contents. The headers of the packets tell the analysis engine which protocol the transmission is using and which port the traffic came from and went to. That info identifies any mismatch between applications sending data on the networks and the ports that each uses, as opposed to the ports that the application should be using for the protocol that it follows.
The nDPI system is able to identify encrypted packets by looking at the SSL security certificate that specified the encryption key for the transmission. This is a clever insight and gets around the difficulties that encryption presents to deep packet analysis.
Who is it recommended for?
The nDPI package is suitable for use by programmers when developing a monitoring system. The nDPI functions provide packet inspection capabilities. The benefit of using these functions out-of-the-box rather than adapting them is that these utilities have been tested and then used in the real world again and again, which provides excellent bug spotting.
Pros:
- Opens source project allows for additional customization
- Can report data back regarding encrypted communications (Certificate date, signing authority, etc)
- Takes advantage of NetFlow, making it a solid option for networks heavily using Cisco products
- Completely free
Cons:
- Has a higher learning curve than some paid solutions
- No paid support option, must rely on the community for updates/fixes
- Only support application layer scanning
The nDPI software can be installed on Windows, Linux, and MacOS. The DPI module supports other Ntop products like nProbe and Ntop-NG. nProbe is a traffic monitoring system that collects NetFlow messages. NetFlow is a signaling standard used by Cisco Systems for its network equipment products. This system is available for a small fee and it runs on Linux and Windows. Ntop-NG is a traffic analyzer for networks. This is an alternative network monitoring system that employs SNMP messages. Ntop-NG is available for Windows, Unix, Linux, and Mac OS. It is available in three versions, one of which, the Community Edition, is free.
7. Netifyd
Despite being a fork of OpenDPI, nDPI is becoming a standard all of its own and is the basis for a number of other adaptations. Netifyd is one of these. This makes Netifyd and adaptation of an adaptation of OpenDPI. Like its ancestors, Netifyd is an open-source product and you can see the code that makes up the program, compile it, and use it. Alternatively, you could adapt the code yourself and end up with an adaptation of an adaptation of an adaptation of OpenDPI.
Key Features:
- Packet analysis tool
- Partners with a network monitor
- Displays packets
Why do we recommend it?
Netifyd is a free packet collection system that can compile statistics on packets according to protocol. It is a data collection agent rather than a full packet analysis tool. You could choose to file the records that Netfyd collects and forward them to a data analysis system.
Netifyd will capture packets, but it does not include analysis functions to interpret data or take actions to shape traffic or block protocols. You would need to import the Netifyd data into another application for those functions.
Who is it recommended for?
This package is only likely to appeal to a developer. It is possible to use this agent to gather input data for a customized tool or assemble a pre-written search and display feature in a data analysis system, such as Prometheus or the ELK stack.
Pros:
- Transparent open-source project
- The dashboard is minimalistic and good for smaller network deployments
- Paid version if affordable, even for smaller labs
Cons:
- Another fork of OpenDPI can be a con if you’re not a fan of that framework
- No packet analysis functionality
- Only supports application layer scanning
This system is available from the community pages of the Egloo website. The main product of Egloo is the Netify network monitor that is based on Netifyd but has many more features and is not free. This tool offers you the visualization and sorting capabilities needed in order to properly understand the information that arises out of deep packet inspection. The starter package of Netify is priced at $25 per site per month. That edition allows you to monitor data from up to 25 devices and the service will store your data for two days. Higher packages give you a longer time horizon for historical data.
8. AppNeta
AppNeta is a cloud-based network monitoring system. It is particularly aimed at companies that operate WANs and extend their capabilities into the cloud. The software uses a proprietary network traffic analysis methodology called TruPath, which is a little like Traceroute with added performance reporting.
Key Features:
- Cloud-based
- Path analysis
- Protocol analyzer
Why do we recommend it?
AppNeta excels at monitoring connections across the internet between sites. This system is based in the cloud, which gives it an ideal viewpoint for tracking long-distance connections. The monitor performs protocol analysis, which requires deep packet inspection. The information extracted by this monitor can be used to accelerate specific types of traffic.
After TruPath collects information, the system adds on traffic details gleaned through deep packet inspection. The DPI module works to segment traffic metrics by application. As AppNeta is aimed at businesses that use the internet intensely for all company traffic. It conducts all packet inspection offsite, reducing the strain that excessive reporting procedures can put on networks.
Information that the DPI module gathers is sent to the cloud data center. The analysis engine is hosted remotely and not on any of your equipment. This makes the dashboards and reports available from any location, not just in your HQ. The location neutrality of this configuration makes the control panel for the system available from anywhere over the web. Data is stored on the AppNeta servers for 90 days, which gives you ample opportunity to analyze trends and plan capacity. Demand on apps covers both the cloud services accessed by your company as well as online services that your business provides to others.
The AppNeta presentation focuses on monitoring the delivery performance for applications. It includes alerts on traffic volumes per application. Those traffic warnings could act as a security monitor because sudden surges in internet traffic may indicate an attack. The utility includes user activity analysis, which would come in handy to track suspicious activity and identify compromised accounts. However, AppNeta isn’t positioned as a security tool.
AppNeta covers all communication between your sites and its data center with encryption. The package doesn’t use data analysis tools and you are recommended by the company to use a third-party tool, such as Wireshark.
Who is it recommended for?
AppNeta is particularly necessary for businesses that run virtual networks, such as SD-WANs or SASE configurations. In these circumstances, internet connections between sites, or to remote workers, or cloud platforms rae protected by VPNs. The AppNeta system is able to work around these connection encryption systems.
Pros:
- Operates as a cloud-based SaaS making it flexible and easy to deploy
- Utilizes a proprietary traffic analysis method that provides detailed reports based on each network hop
- A great option for companies that rely on many public-facing applications to conduct business (DMZs, SaaS tools, cloud services)
- Pairs DPI with application performance, allowing users to correlate attacks and uptime easily
Cons:
- Must contact sale for an undetermined free trial period
- Could use more security features to stop threats as they’re identified
- More expensive than similar DPI tools
This monitoring system is not free. The service is priced at $199 per application per location. You can request a free trial of the system, but the company does not offer this for a fixed time period. You may negotiate a trial period with a sales representative upon request.
How to choose DPI and analysis software
Deep packet inspection management and analysis doesn’t have to be performed by a standalone tool. You can get DPI functionality integrated into many of the industry’s top network monitoring systems. If you have a small network and don’t want to shell out for network management systems, then look into the free versions of those big-name network monitors. If you just want a separate system to perform deep packet analysis and don’t want those tasks interfering with your regular monitoring, then you will find some very suitable tools on our list.
Be careful about installing deep packet analysis tools because they extract the data that is carried across your network. Deep packet inspection might compromise the privacy of the data exchanged across your organization. You should check with your company’s legal advisor first before installing any network tool that will enable you to capture data as it crosses the network. Data privacy and access control could be compromised by giving access to network administrator staff. In some cases, the company must pledge to limit access to the personal information of members of the public held on the business’s assets. So, make sure that you aren’t breaching those obligations by installing DPI tools.
The ability to check on packet-level traffic is certainly helpful when you encounter network performance issues. Deep packet analysis goes one step further and reads the contents of each packet. You must reassure yourself and your board of directors, that you really need that level of information in order to protect the network before installing DPI systems.
Do you currently use deep packet inspection techniques to keep your network running well? Have you encountered legal problems over the issue of data privacy while using DPI tools? Let the community learn from your experience by leaving a message in the comments section below.
Deep Packet Inspection FAQs
What is a stateless firewall?
A stateless firewall examines the information in the header of each individual packet when applying its rules of admission. The opposite of stateless is the stateful firewall, which looks at conditions that require the examination of several packets.
Does deep packet inspection block VPNs?
Deep packet inspection will only perform the checks that the firewall’s owners have specified. However, DPI can be used to detect patterns in encrypted packets that are typical of VPN processing. The Chinese government uses this and VPNs deploy stealth tactics to try and evade detection.
What are the deep packet inspection techniques used today?
The most commonly used method deployed for deep packet inspection is signature-based detection. This looks for a specific pattern of characters within the packet. Usually, DPI systems focus their pattern searches on the headers of packets because it is assumed that the body will be encrypted.