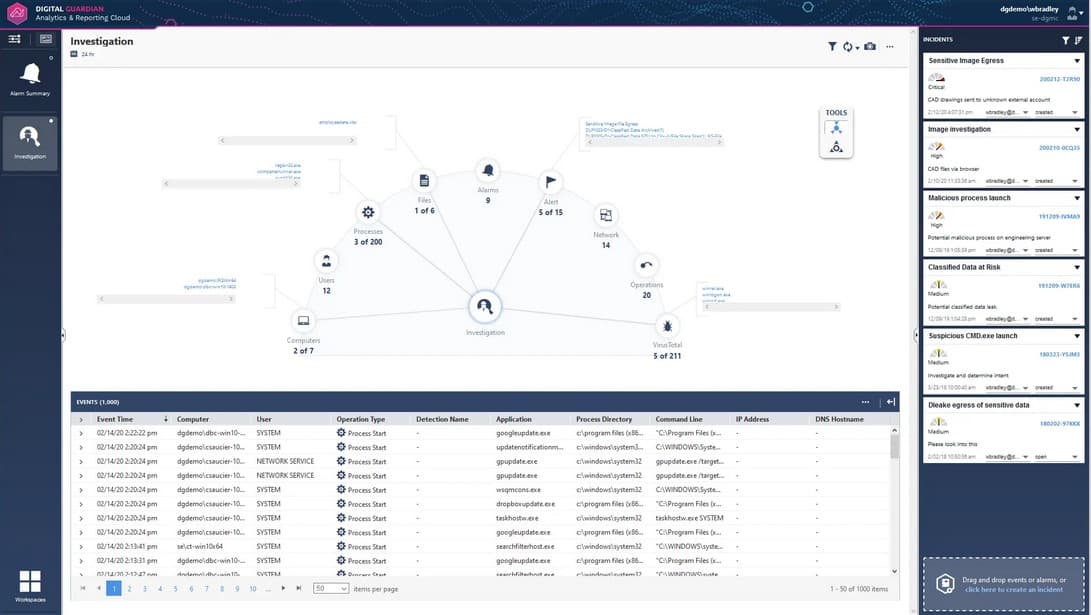
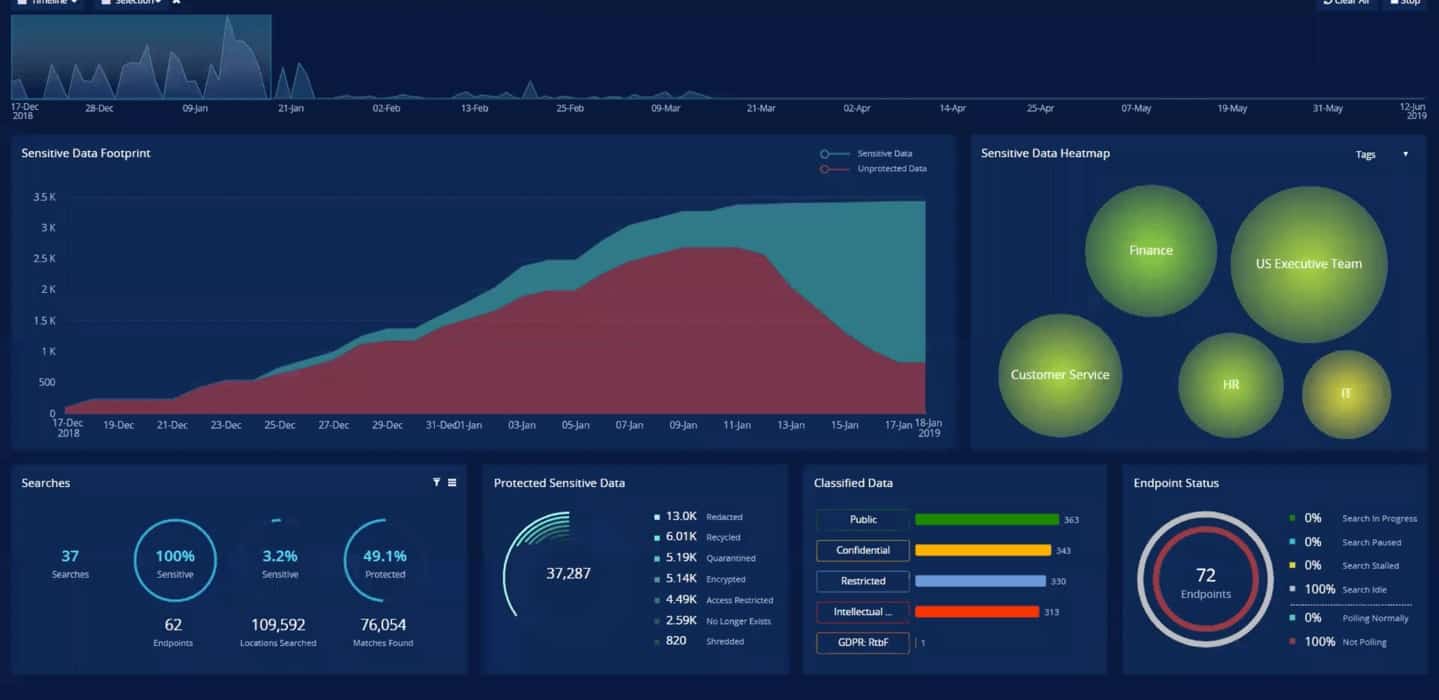
Verdasys started operations in 2003. The company specialized in data protection and fraud detection software. The most successful product of the business was a data loss prevention (DLP) system called Digital Guardian, and in 2010, Verdasys converted this star system into a SaaS platform. However, Digital Guardian continued to grow, dominating its activity, so in August 2014, the company changed its name to Digital Guardian.
What does Digital Guardian DLP do?
The critical service that the Digital Guardian platform offers is its protection services for sensitive data. Companies that hold personally identifiable information (PII) on individuals must now be cautious about managing that data. Legislation around the world imposes fines on businesses that fail to protect this information from misuse or disclosure.
Industry standards for data privacy, such as PCI DSS for the payment card industry and HIPAA for the healthcare sector, are now embedded into business agreements. Part of the legal requirements over PII management includes ensuring that all suppliers and associated businesses comply with the relevant standard. So if your company operates in a sector covered by a data privacy requirement, you just won’t get any business unless it complies with that requirement.
GDPR in the EU and the CCPA in California are two examples of regional standards for PII management that can result in heavy fines for businesses operating in those locations without full compliance.
The Digital Guardian platform provides all of the tools that a business needs to comply with all data protection standards regarding PII. It also helps block the theft of other data held on your systems.
Digital Guardian features
The Digital Guardian platform is composed of modules. Many of these are interlinked and work together to provide complete protection for PII.
Key Features:
- Sensitive Data Tracking: Automatically identifies and locates sensitive information across your network.
- Data Sensitivity Grading: Assigns levels of sensitivity to data, aiding in prioritization and protection efforts.
- Endpoint Protection: Deploys agents on Windows, macOS, and Linux devices to monitor and control data movement.
- Network Surveillance: Monitors data flow across the network and internet, with capabilities to enforce encryption and prevent unauthorized transfers.
- Cloud Security: Extends protection to cloud-stored data, ensuring comprehensive security across all platforms.
- Intrusion Detection: Utilizes analytics and SIEM technology to detect and alert on potential security breaches.
How much does Digital Guardian cost?
Digital Guardian DLP is offered as a self-drive package that is delivered from the cloud. The central server for the system is hosted, and subscribers access their account dashboard through any standard browser.
Businesses that don’t have their in-house cybersecurity teams can opt for the Managed Detection and Response package. This includes all staff to monitor the service, so there is no need to allocate any staff to watch the dashboard.
Digital Guardian doesn’t publish the price of its DLP platform. Instead, you need to contact the Sales Department to get a quote. You can also access a demo system for assessment.
Pros & Cons of Digital Guardian
Digital Guardian is a very effective data loss prevention system. Here are its benefits and drawbacks.
Pros:
- Enhanced Data Management: Efficiently reorganizes access rights and categorizes sensitive data for better control.
- Multi-Platform Endpoint Monitoring: Provides robust monitoring of endpoint activity and manages file access across major operating systems.
- Data Exfiltration Control: Offers thorough management of data exfiltration channels to safeguard against unauthorized data transfers.
- Cloud Platform Integration: Applies stringent control measures for accessing data on cloud platforms, enhancing overall data security.
Cons:
- Opaque Pricing: Lack of transparent pricing information may deter potential customers, requiring direct contact with sales for quotes.
Alternatives to Digital Guardian
Digital Guardian is a very comprehensive system for the protection of sensitive data. However, it is not the only system on the market, and many of its rivals present powerful alternatives.
Our methodology for selecting a Digital Guardian alternative
We reviewed the market for data loss prevention systems and analyzed the options based on the following criteria:
- A system that discovers sensitive data and ranks it
- An auditor for access rights management systems that recommends better controls
- Graded permissions management that takes into account the user’s role and department
- A file integrity monitor
- A system to detect unusual behavior
- A demo system or a free trial for a no-cost assessment
- Value for money that offers complete protection at a competitive price
As well as looking for the key attributes listed in our selection criteria, we made sure to include systems for different operating systems and cloud-based services.
Here is our list of the best alternatives to Digital Guardian:
- SolarWinds Security Event Manager (FREE TRIAL) A SIEM service and a log manager that includes a file integrity monitor and compliance auditing. It runs on Windows Server.
- ManageEngine Endpoint DLP Plus (FREE TRIAL) Use this package to identify sensitive data and then control access to it, how it is transferred, and how the system responds to unauthorized access attempts. Runs on Windows Server.
- ManageEngine DataSecurity Plus (FREE TRIAL) This system provides data loss prevention, risk assessments, and file auditing for on-premises and cloud-stored data. Runs on Windows Server.
- Endpoint Protector This data loss prevention system discovers and classifies PII, audits access rights, watches file activity, and controls all utilities that can be used for moving data. Offered as a hosted service, as an app on cloud platforms, or for installation as a virtual appliance.
- Spirion Sensitive Data Manager This cloud-based service tracks and manages sensitive data on-site, remote locations, and in the cloud by working through agent systems. Agents install on Windows, macOS, Linux, and cloud platforms.
- Azure Information Protection A sensitive data management service from this cloud platform can manage data anywhere, not just on Azure.
- Mage iDiscover A cloud-based data management platform that uses AI techniques to identify and protect sensitive data following GDPR, CCPA, and HIPAA requirements.
You can read more about each of these options in the following sections.
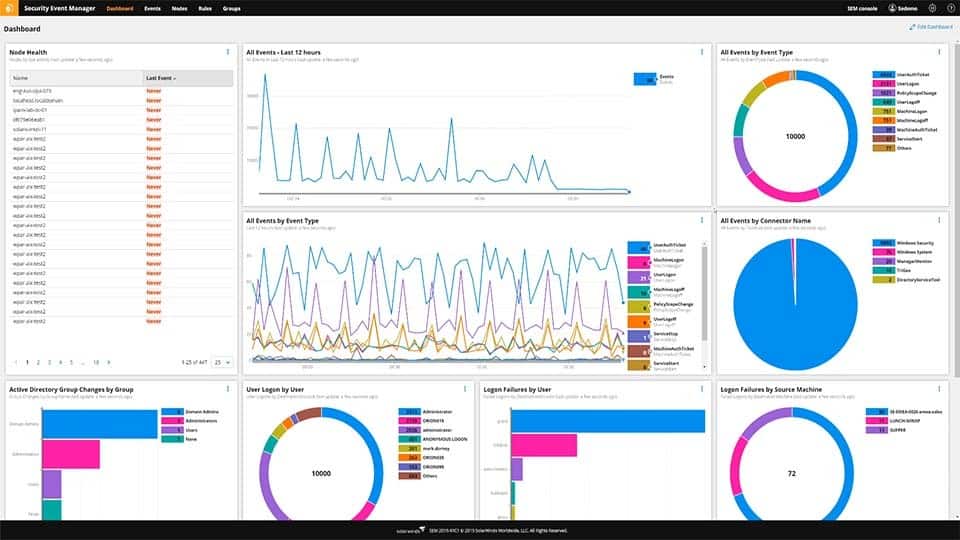
1. SolarWinds Security Event Manager (FREE TRIAL)
SolarWinds Security Event Manager is a SIEM system and log manager that also includes a file integrity monitor. In addition, this package consists of a range of security services, including a vulnerability scanner, as well as system hardening tips and then constant security monitoring with this bundle. This package’s services provide compliance with PCI DSS, GLBA, SOX, NERC CIP, and HIPAA.
Key Features:
- Comprehensive Log Collection: Centralizes log data from across your network for thorough analysis and management.
- On-Premises Solution: Designed specifically for deployment within your own infrastructure, ensuring full control over security data.
- Regulatory Compliance: Supports adherence to key standards like PCI DSS, GLBA, SOX, NERC CIP, and HIPAA, simplifying compliance processes.
- Log File Integrity Monitoring: Safeguards log files against unauthorized changes, enhancing security posture.
- Vulnerability and Risk Assessment: Identifies system vulnerabilities for targeted security enhancements and risk mitigation.
Why do we recommend it?
SolarWinds Security Event Manager is a SIEM system. This tool includes a log manager and the two main elements of the system create effective compliance auditing and reporting functions. By default, this system doesn’t look specifically for actions on data types, but it can be adapted by custom log searches.
The vulnerability manager includes a risk assessment service. This will identify where weaknesses in your system lie, and you can then hone in on specific locations of sensitive data. This system links all actions to your access rights manager and helps block inappropriate actions by authorized users and access attempts by intruders. Sensitive data mismanagement detection is implemented through the SIEM service. Automated file integrity monitoring operates on the log files managed by Security Event Manager.
Who is it recommended for?
This is a solution for large companies that don’t want to use external, cloud-based SIEM systems. The service is implemented as a software package for Windows Server. You can perform all of your security scanning with this tool, not just data loss prevention. This SIEM is particularly good at spotting intrusion.
Pros:
- Integrated File Monitoring: Protects log files and enhances overall security
- Comprehensive Vulnerability Scanning: Identifies and addresses system weaknesses effectively.
- SIEM for Advanced Threat Detection: Detects and responds to suspicious activities targeting sensitive data.
Cons:
- Lacks Data Discovery: Does not provide data discovery or sensitivity classification features, limiting its capacity for identifying and categorizing sensitive data automatically.
SolarWinds Security Event Manager runs on Windows Server, and it is available for a 30-day free trial.
EDITOR'S CHOICE
The Security Event Manager logs all activities performed on monitored files, and those records get sent into a poll and all other system logs. This collection forms the input to the SIEM system. With this service, you will be alerted to unexpected activity. This detects insider threats as well as intruder activity. The SIEM coordinates with firewalls and access rights management systems to block malicious activity. The log manager attached to the SIEM stores logs for compliance auditing.
Download: Download 30-day FREE Trial
Official Site: solarwinds.com/security-event-manager/registration
OS: Windows Server
2. ManageEngine Endpoint DLP Plus (FREE TRIAL)
ManageEngine Endpoint DLP Plus is a package of protection methods for sensitive data. It implements data loss prevention by identifying and classifying sensitive data. This exercise is carried out in the context of data protection standards. You can first set up the package for your specific protection needs and then set it off on its discovery path.
Key Features:
- Automated Data Discovery: Scans and identifies sensitive data across your network to ensure comprehensive protection.
- Precise Data Classification: Classifies data based on sensitivity, aligning with specific data protection standards for enhanced security.
- User Behavior Analysis: Monitors user interactions with sensitive data to prevent unauthorized access or misuse.
- Cloud Compatibility: Extends protection to data stored on cloud platforms, ensuring security across all data environments.
Why do we recommend it?
ManageEngine Endpoint DLP Plus is a strong competitor for Digital Guardian DLP because it performs many similar routines. For example, this package implements data discovery and classification that can be tailored to specific data protection standards. This package covers cloud resources as well as on-premises assets.
The definition of the types of data that you need to protect is all part of security policies. These are available as templates but you can also create your own. Once your sensitive data is located, access rights and data usage permissions are enforced in email systems, cloud platforms, file transfer utilities, and on USB devices.
The service logs all file access events and tracks user activity in relation to sensitive data usage. This enables you to block inappropriate use by authorized users. Access to data is controlled by preventing direct access to the actual data store, such as files and databases. Instead, those data stores can only be mined by authorized applications, which you define. This link puts greater emphasis on the need for tight access rights management.
Who is it recommended for?
Clearly, the main audience for this package will be companies that manage personally identifiable information and other sensitive data. This is an on-premises software package that runs on Windows Server. Ordinarily, large companies are going to be more likely to buy such as system. However, ManageEngine offers a Free edition for SM that covers 25 endpoints.
Pros:
- Robust Data Protection: Offers thorough identification and classification of sensitive data, tailored to meet various protection standards.
- Application-Based Access Control: Restricts data access to approved applications, reducing the risk of unauthorized data breaches.
- Comprehensive Activity Monitoring: Tracks user behavior and data access, providing insights into potential security risks.
- Versatile Data Security: Controls access across USBs, email systems, and file transfer utilities, fortifying data against unauthorized use.
Cons:
- Limited Deployment Options: Only available for on-premises installation, lacking the flexibility of a SaaS deployment model.
The software for ManageEngine Endpoint DLP Plus runs on Windows Server and it is available in free and paid versions. The Free edition is limited to monitoring 25 endpoints. You can access the full, professional system, which can monitor devices on multiple sites, on a 30-day free trial.
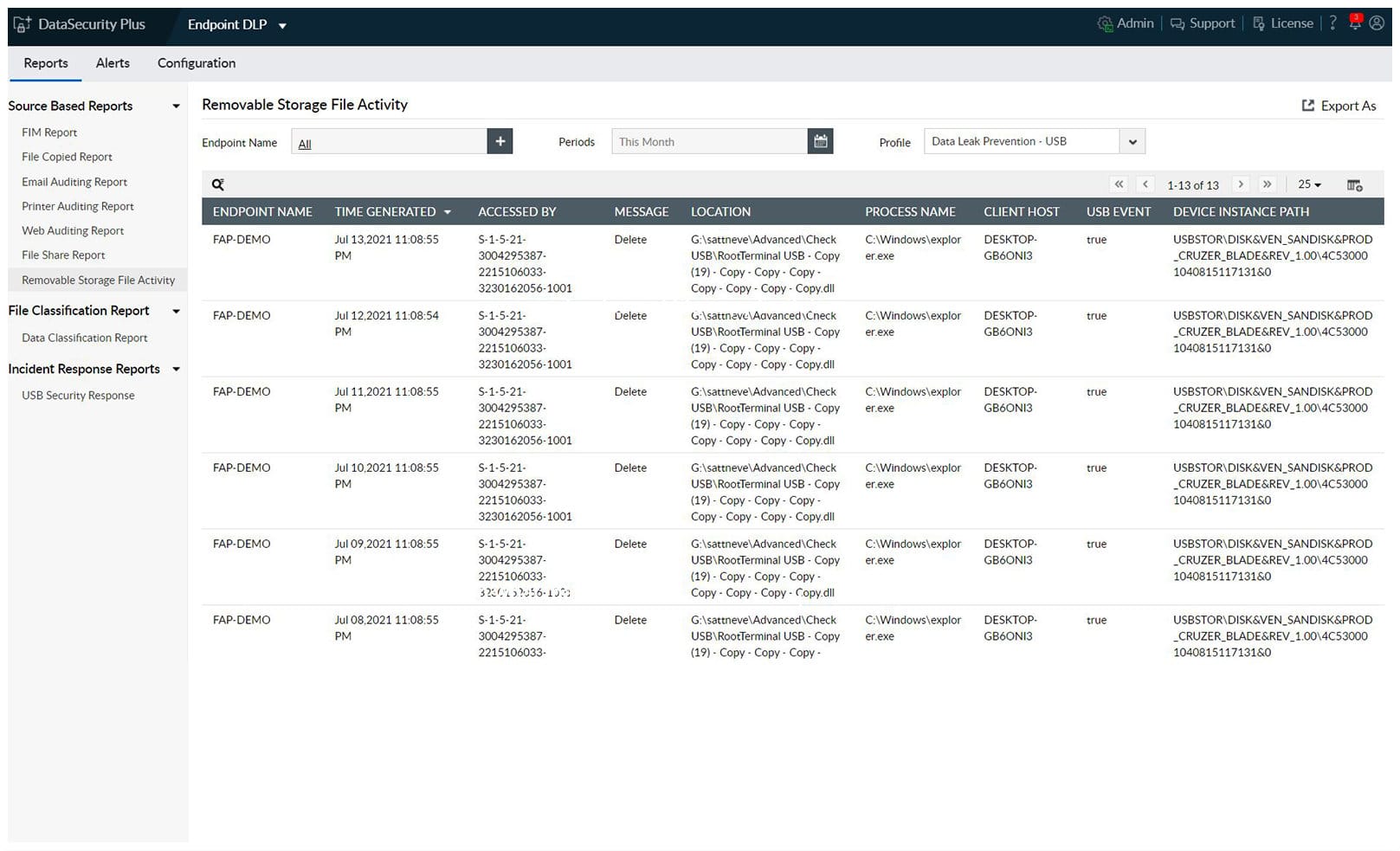
3. ManageEngine DataSecurity Plus (FREE TRIAL)
ManageEngine DataSecurity Plus is a bundle of ManageEngine security and analysis tools, which includes the Endpoint DLP package. The core DLP function provides standards compliance adaptations, which enable it to target specific types of data for protection. Examples of these data types are credit card numbers and email addresses.
Key Features:
- File Integrity Monitoring: Ensures the security and integrity of critical files, alerting on unauthorized changes.
- Sensitive Data Identification: Discovers sensitive information such as credit card numbers and email addresses, safeguarding against breaches.
- Compliance-Focused Management: Tailors data protection strategies to meet various regulatory compliance standards efficiently.
Why do we recommend it?
ManageEngine DataSecurity Plus is the second ManageEngine tool on this list. While Endpoint DLP is classified as an endpoint protection service, ManageEngine categorizes DataSecurity Plus as a security auditing package. As both systems protect data, there is a lot of overlap between them.
The DLP system then scours all of your endpoints for instances of the specified data types and logs their locations. The files that are identified for this process get special access and movement controls applied to them.
DataSecurity Plus provides file server analysis, which identifies temporary and junk files for deletion and provides analysis of file permissions to help tighten data security. The File Auditing function logs all data access events and can be set up to raise an alert if those protected files are touched. The Data Risk Assessment service refines the data discovery process, enabling it to spot adjacent fields or scattered data, which, in combination can identify an individual and therefore qualify a document or data file for special protection.
The Cloud Protection module extends the functions of the DLP to cloud stores and also prevents banned content from loading in the browsers of your users.
Who is it recommended for?
A business looking for a DLP system that decides on ManageEngine as a provider has two systems to choose from. Both of these services are software bundles for Windows Server. The big difference between them is the charging structure with DataSecurity Plus divided into four modules, which are charged for individually.
Pros:
- Advanced Data Risk Analysis: Employs data risk assessments to identify and protect scattered or combined data that could compromise individual identities.
- File Server Optimization: Analyzes file servers to eliminate unnecessary files and tightens file permission controls for enhanced security.
- Sensitive Data Control: Implements strict controls over the use and movement of identified sensitive data, ensuring compliance and security.
- Comprehensive Audit Trails: Maintains detailed records of data access events, facilitating compliance with regulatory standards.
Cons:
- Deployment Limitations: Available only for on-premises deployment on Windows Server, lacking a Software as a Service (SaaS) option.
The pricing structure of DataSecurity Plus is a little complicated as each of the four components in the system has its individual price. The software bundle for DataSecurity Plus runs on Windows Server and you can get it on a 30-day free trial.
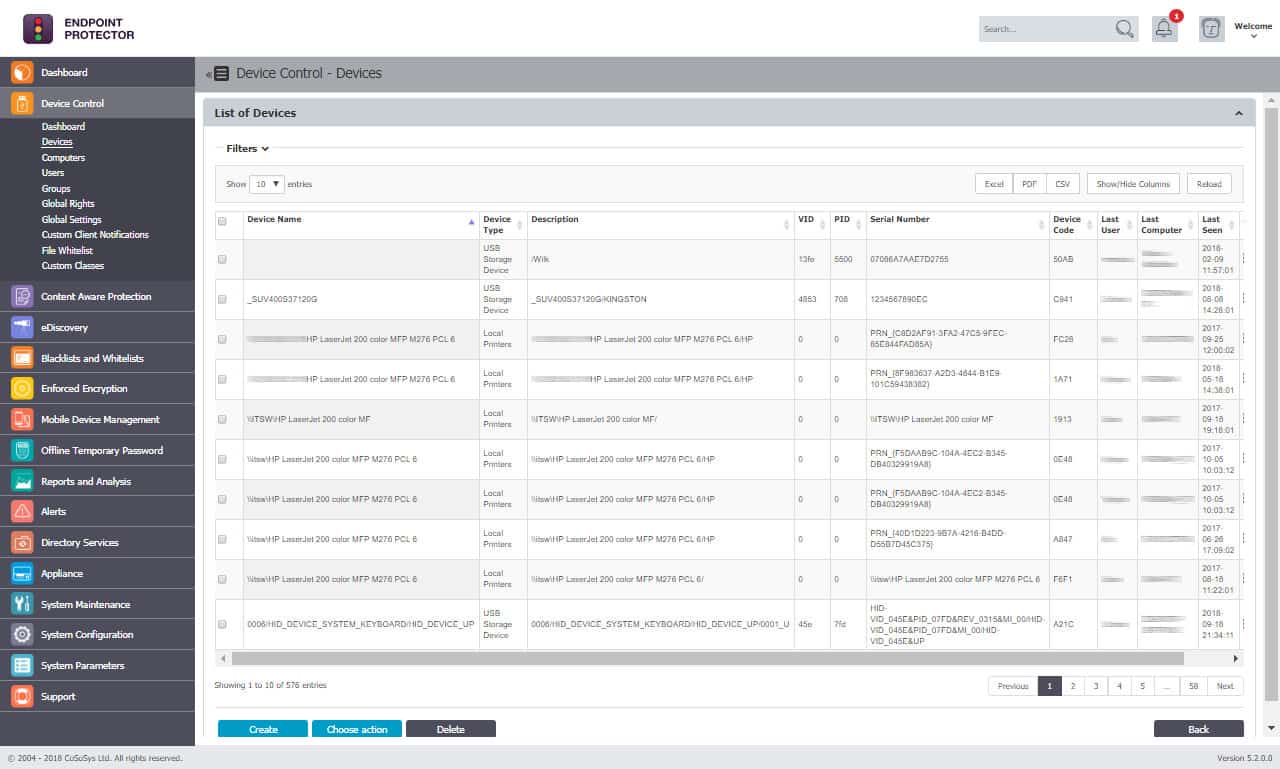
4. Endpoint Protector
Endpoint Protector is a very close match for Data Guardian. This is a data loss prevention system that requires agents to be installed on endpoints. The endpoint modules ensure continuity should those devices get disconnected from the network and cannot communicate with the central module.
Key Features:
- Continuous Data Discovery: Automatically detects and classifies sensitive data across the network, adapting to various security standards.
- File Access Management: Restricts file access based on defined policies, ensuring data is only available to authorized users.
- Peripheral Control: Monitors and controls the use of removable storage devices to prevent unauthorized data transfer.
Why do we recommend it?
Endpoint Protector provides a sensitive data scanner that will categorize discovered data instances according to a given data security standard. This platform containerizes each file and then only allows access according to a built-in access rights manager. This ARM links together rights for a file, for an application, and for a user.
The on-device systems are available for Windows, macOS, and Linux. The profile activities on the device and send reports up to the central server for analysis. These agents also perform sensitive data discovery and classification services. That discovery service works continuously, so new instances of PII are instantly spotted and enrolled in protection. In addition, the agents monitor activity on USB devices, printers, and email clients to enforce the system-wide data security policy.
The central module allows system administrators to set up security policies and then communicates them to endpoint agents. It also audits the access rights management system and gathers information for compliance auditing. The system spots data in motion and optionally blocks it or enforces encryption. It also controls access to files of sensitive data by encrypting them.
Endpoint Protector can protect data on your site, in remote locations, and on the cloud. It is a hosted SaaS platform and accessible as a service on AWS, GCP, and Azure. Additionally, it is possible to install the software on-site over a VM.
Who is it recommended for?
This is a very good system for companies that need to implement data security but can’t afford or find suitable cybersecurity experts for their staff. This is because the Endpoint Protector system, which can also block malware, is incredibly easy to implement. Protected endpoints can be running Windows, macOS, or Linux.
Pros:
- Dynamic Sensitive Data Protection: Offers a robust, continuous scanning and categorization system for sensitive data, ensuring up-to-date protection.
- Comprehensive Endpoint Oversight: Extensively monitors endpoint activities, including USB, email, and printer interactions, aligning with security policies.
- Encryption-Based Security: Employs encryption for both file access and data transmission, bolstering data security across platforms.
- Versatile Auditing and Compliance: Provides detailed auditing and reporting capabilities for meeting regulatory compliance standards effectively.
Cons:
- Limited to DLP Functions: While highly effective for data loss prevention, it falls short of offering the full range of SIEM functionalities.
Endpoint Protector a great choice for a Digital Guardian replacement because its functions match its main rival while being available on a broader range of platforms. The services of Endpoint Protector cover all possible methods that intruders and malicious insiders could use to steal data. In addition, this system includes a high degree of automation, which removes the need to employ security experts.
Get access to a demo: endpointprotector.com/get-demo
5. Spirion Sensitive Data Manager
Spirion Sensitive Data Manager is a cloud-hosted SaaS platform that interacts with the agent modules installed on your sites and cloud data stores. Agents perform continuous data discovery and sensitivity classification. In addition, the central server supplies you with a choice of off-the-shelf security policies tuned to different data privacy standards. You can accept one of these, adapt one, or write your own. This service covers intellectual property as well as PII.
Key Features:
- Automated Data Discovery: Continuously scans for and classifies sensitive data, ensuring comprehensive protection.
- Flexible Deployment: Offers an on-premises solution, catering to businesses preferring to manage their data security internally.
- Cloud Data Protection: Extends its protective measures to data stored on cloud platforms, securing information wherever it resides.
Why do we recommend it?
Spirion Sensitive Data Manager competes in a crowded market because it is an on-premises data loss prevention system. The on-premises delivery model still seems to be the winner for DLP systems. The eDiscovery module in this package is called AnyFind and it operates continuously to register new data instances for protection.
The data classification module is called Watcher. While it assesses data instances, it also scans for system weaknesses, so it is also a vulnerability manager. It examines your access rights system and sets all of your user accounts’ permission levels. Then, it recommends new account permissions and new user groups.
The ongoing file integrity monitoring service in the Sensitive Data Manager is called Spyglass. This implements your security policies. You can apply different approaches to different user groups and business departments; access rights are segmented. So naturally, intruders don’t get a look in.
Who is it recommended for?
This system can scan on-premises files, cloud platforms, including storage services, and cloud SaaS systems, such as Google Workspace and Microsoft 365. This system works a little like a SIEM because all of the processing is implemented centrally with agents on each endpoint and platform. Businesses with hybrid systems will benefit the most.
Pros:
- Intelligent Data Management: Integrates continuous data discovery with classification, providing a robust foundation for data protection.
- Access Rights Optimization: Evaluates and suggests improvements for user permissions, enhancing security and minimizing risks.
- Compliance and Risk Management: Delivers risk assessment and compliance management capabilities, ensuring adherence to various standards.
Cons:
- Lacks Active Security Monitoring: While offering strong data protection and compliance features, it does not include proactive system security monitoring.
The Spirion system includes protection services that comply with data privacy standards such as GDPR, CCPA, HIPAA, and PCI DSS. In addition, you can get a demo of the Spirion Sensitive Data Manager.
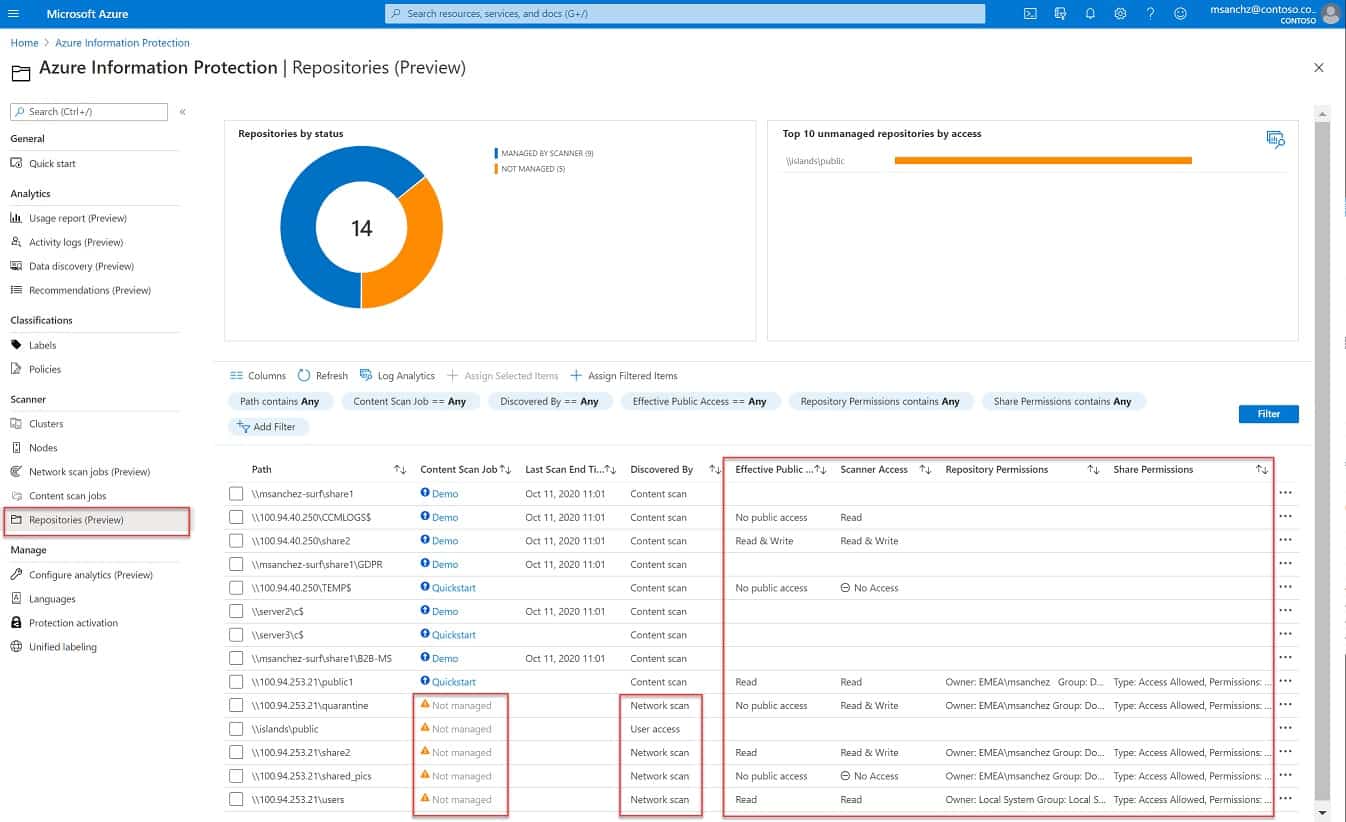
6. Azure Information Protection
Azure Information Protector is a service on the Azure platform that can manage sensitive data wherever it is held. Although you need to set up an Azure account to access this service, you don’t have to use Azure storage space for this system to operate. This system can scan any of your sites and also the cloud resources provided by other platforms.
Key Features:
- Azure-Based: Leverages the Azure platform to offer comprehensive data management and protection services.
- On-Site Data Security: Capable of securing data stored on-premises, ensuring robust protection across all environments.
- Compliance Assurance: Facilitates compliance with various data protection regulations, streamlining management tasks.
Why do we recommend it?
Azure Information Protection is based in the cloud but it can protect data on your on-site endpoints. Ostensibly, this package can interface with any platform anywhere, which would include AWS and GCP. However, the package provides agents for your on-premises endpoints, but an SDK to help you connect to other cloud platforms, which could prove difficult.
To start the data protection service, you have to set up security policies in the Information Protector console based on the Azure servers. Then, you access it through any standard web browser. This policy can be set by applying a template from a library that matches the data privacy standard that you are following. You then need to enroll each of your servers and cloud services into the program. The service then scans for data and classifies it. From this point, the continuous monitoring of access to those data stores is active.
Other services in this package include the electronic watermarking of documents and an identifier that can be embedded in metadata to track copies of distributed files. File controls allow access to viewing and movement; copying or printing can be blocked. It is also possible to encrypt files to control access.
Who is it recommended for?
If you have Azure accounts, you can easily protect the data held in them with this package. So, the types of businesses that will opt for the Azure Information Protection package are those that keep their data on-premises or on Azure.
Pros:
- Versatile Data Protection: Provides sensitive data discovery and classification, extending security measures beyond Azure storage.
- Advanced Document Security: Implements electronic watermarking and metadata embedding for tracking document distribution and usage.
- Restrictive File Controls: Allows fine-tuning of file access, including blocking printing and file movements, enhancing data security.
Cons:
- Lacks Comprehensive Security Monitoring: While effective in data protection and compliance, it does not offer system-wide security monitoring features.
7. Mage Data
Mage Data supports GDPR, CCPA, and HIPAA compliance and includes data discovery and classification. The package also assesses security weaknesses on the servers where detected sensitive data is held. The data discovery system uses AI processes to evaluate the meaning and purpose of data. Its reach extends to databases and unstructured data storage systems. It can examine and protect data on any site and also on cloud platforms.
Key Features:
- AI-Driven Discovery: Utilizes artificial intelligence for thorough data discovery and classification, even in complex datasets.
- Risk Evaluation: Assesses security vulnerabilities within servers holding sensitive data, guiding fortification efforts.
- Extensive Coverage: Capable of analyzing and safeguarding data across both on-premises and cloud environments.
Why do we recommend it?
Mage Data is a data discovery and classification system. It is able to identify adjacent or nearby data fields that individually don’t disclose an identity but do collectively. This system uses AI to achieve this task. The package also tracks user activity and data movements.
This security package will examine the access permissions on each datastore and recommend necessary changes. It will also assess your access rights manager, identify new user account controls, and fine-tune your user groups. It will also evaluate the security settings of the applications that give access to sensitive data.
Who is it recommended for?
This is a solution for a large business that already has a SIEM that they like, and want to enhance it to implement data loss prevention. For example, businesses that have the SolarWinds Security Event Manager could implement DLP by feeding Mage Data into it.
Pros:
- Comprehensive Compliance Support: Offers robust features for adhering to GDPR, CCPA, and HIPAA, ensuring regulatory compliance.
- Intelligent Data Analysis: AI processes enable identification of interconnected data that may collectively reveal identities, enhancing privacy protection.
- Security Optimization Recommendations: Evaluates and suggests enhancements for access permissions and user account controls for improved security posture.
Cons:
- Limited to Data Protection: Focuses exclusively on data discovery, classification, and protection, without encompassing broader system security measures.
Mage Data is a cloud platform, and you can assess by can accessing a demo.