Email security is important for the protection an organization’s sensitive data and preventing cyber threats such as phishing, malware, and spam. As one of the most commonly used communication channels in business, email is often the target of cyberattacks. Without proper protection, malicious actors can exploit vulnerabilities in email systems to gain unauthorized access to systems, compromise data, and disrupt business operations.
Here is our list of the best email security software packages:
- TitanHQ Email Security EDITOR’S CHOICE This cloud-based system can protect SaaS email services, such as Exchange Server/Outlook and Gmail with a spam and malware protection module and an anti-phishing service. Access a free demo.
- Trustifi Inbound Shield This cloud-based system blocks spam, phishing attempts, and malware by pre-processing all incoming emails before they get to the protected email server.
- N-able Mail Assure A cloud-based system that is designed for managed service providers to offer email protection to their clients.
- Proofpoint Essentials A cloud-based email security system for small and middle-sized enterprises that also performs protection for social media accounts.
- Trend Micro Email Security A comprehensive email protection system that is delivered from the cloud and includes continuity services as well as blocking malicious emails.
- Barracuda Email Security Gateway A physical appliance that coordinates with email client plug-ins delivers this email security package that blocks attacks in emails and scans both internal and external emails.
- Hornetsecurity Spam and Malware Protection A cloud-based system that has a great deal of success in blocking spam, malware, phishing attempts, and access to infected websites.
- Fortinet FortiMail Part of the Fortinet Security Fabric, this email security system blocks spam, phishing, and malware. Delivered as an appliance or a SaaS package.
You can read more about each of these solutions in the following sections.
Email security software also plays a vital role in compliance management. Many industries are subject to strict regulations, such as HIPAA, GDPR, and PCI DSS, which mandate the protection of sensitive information shared via email. These tools can help ensure compliance by offering secure email encryption, auditing capabilities, and secure data storage, all while helping businesses avoid hefty fines associated with data breaches and non-compliance.
Key features of email security software include spam filtering, malware detection, phishing prevention, and email encryption. By implementing these tools, organizations can significantly reduce the risk of email-borne threats, ensuring that both employees and customers remain protected from potential security breaches. These solutions offer a range of features designed to detect and block threats before they can reach users’ inboxes.
Our guide provides a detailed overview of the best tools available for safeguarding email communications. We will also cover the importance of automated threat detection and advanced filtering capabilities. Email security software can automatically identify suspicious attachments, links, and email content, allowing organizations to prevent potentially harmful emails from reaching end users. This proactive approach to security reduces the burden on IT teams and improves overall organizational resilience.
By using the right email security software, businesses can protect against a wide range of email-based threats, maintain regulatory compliance, and preserve the confidentiality and integrity of sensitive communications.
Con artists use emails to trick your employees into diverting funds, this is called Business Email Compromise (BEC). Emails can also be used by hackers to extract system access credentials, which is called account takeover and it is implemented through a scam called phishing.
Busy workers don’t always scrutinize the origin of an email, they don’t spot impersonating domains and they really can’t be expected to examine the headers of emails to extract the IP address of origin. You need to put automated systems in place to check all of these factors.
Email attachments are widely used by hackers to hide Trojans that get them into a system. So, you need to put attachment scanning and sandboxing routines in place.
There are many security procedures that you need to put in place in order to protect your business from email-bound threats. This responsibility can be a little overwhelming. However, there are many software systems that offer complete protection for all aspects of your email system.
The Best Email Security Software
Good email security systems are available and there are specialized packages for different types and sizes of businesses. In fact, there are probably too many systems that you should consider. This guide will help you identify the best system for your business by focusing on the top email security systems available today.
Our methodology for selecting email security software
We reviewed the market for email security software and analyzed tools based on the following criteria:
- A cloud service or a network appliance that catches bad emails before they get to the server
- A spammer blacklist
- Attachment isolation and scanning
- Phishing and impersonation detection
- Malicious link detection
- A free trial or demo system for a commitment-free assessment opportunity
- Value for money represented by strong and comprehensive email security at a fair price
With these selection criteria in mind, we identified some outstanding email security software systems that are suitable for all types and sizes of business.
1. TitanHQ Email Security (GET FREE DEMO)
TitanHQ is a cloud-based security platform that offers a range of email security tools. The email protection system is split between two modules: Email Security and Anti-Phishing Protection. You can buy just one of these or both. Email Security provides protection from automated attacks and PhishTitan guards against confidence tricksters.
Key Features:
- Cloud-based
- Spam detection and blocking
- Malware detection
- Detects and blocks BEC, phishing, and whaling
- Quarantining on the cloud
TitanHQ offers Email Security to guard against spam and malware and Anti-Phishing Protection to detect and block impersonation attempts and credentials theft campaigns. The combination of these two units provides complete protection for SaaS email systems – principally Exchange Server/Outlook and Gmail.
Both email security units use machine learning techniques as part of their threat detection routines. This improves over time and can require training by example. The tool quarantines suspicious emails instead of deleting them and the administrator can examine those suspended emails and allow them through.
The scanner learns from the administrator’s decision and will allow through emails from sources that the administrator has approved.
The system’s administrator console is based in the cloud and accessed with any standard Web browser. It is possible to set up a blocklist and an allowlist to enhance the automated spam filtering processes.
Pros:
- Integrates with Microsoft 365 and Google Workspace
- Priced according to the number of users
- Analytical reports
- Web-based administration console
- The administrator can set up a block list or an allow-list
Cons:
- Minimum user count of 25
Email Security and Anti-Phishing Protection are priced separately and there is no joint package. However, as the two systems are run on the same platform, they can be administrated through a single console. You can assess the system by requesting a demo.
EDITOR'S CHOICE
TitanHQ is our top pick for email security software because this platform hosts all of the security systems you need to protect your email accounts. You don’t need to download or host any software to run this package. The service can easily integrate with Microsoft 365 and Google Workspace to catch the emails headed for the Exchange Server or Gmail mail servers. Good emails get passed through to your email server and suspicious mails get quarantined. The tool uses a range of techniques to detect spam and phishing attempts and it is possible for an administrator to set up a block list and/or an allow-list to add extra screening services. The TitanHQ platform also offers email encryption, email archiving, and website protection services in other modules.
Download: Access a FREE Demo
Official Site: https://www.titanhq.com/complete-360-security/
OS: Cloud-based
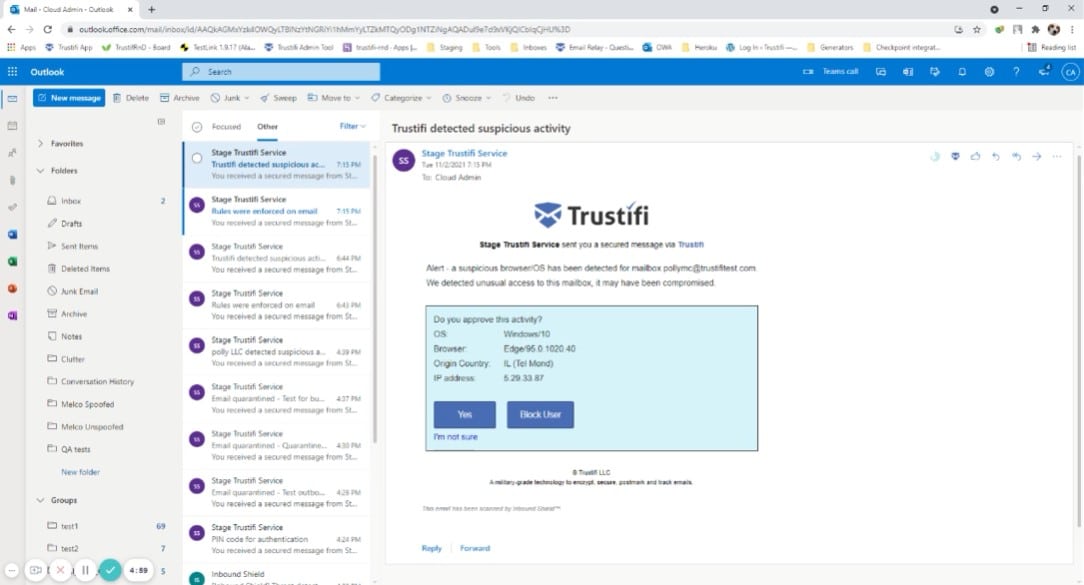
2. Trustifi Inbound Shield
Trustifi Inbound Shield is part of a SaaS package that protects business email systems and the data that they carry. The platform also includes Outbound Shield, which performs email security functions and implements data loss prevention for sensitive data.
Key Features:
- Cloud-based
- Filters out malware
- Scans for phishing
- Identifies malicious links
- Validates attachments
The cloud email security system is a proxy and it catches all incoming emails on the way into your server. This enables the service to fish out all malware before it even gets to your system, making it impossible for ransomware and other malicious processes to even get started causing damage.
The Trustifi system operates from the cloud and you integrate it pre-scans all incoming emails before passing on validated mails. The service can also be integrated into Google Workspace and Microsoft 365 email systems. The tool takes only minutes to set up.
Trustifi uses AI processes to spot spam and impersonation. This process looks at the header of an email and checks that the explicit address is in keeping with its source IP address.
The system scans all links in email bodies and identifies infected or fake Web pages. The system also scans through attachments and quarantines them if suspicious content is detected.
Trustifi Inbound Shield blocks any suspicious email and prevents them from even getting onto your email server. The system integrates into your email system through an API and there are also plug-ins for the cloud-based Microsoft 365 and Google Workspace email systems. This service is also bundled in with Outbound Shield, which operates a data loss prevention service and account takeover detection services.
Pros:
- Easy to set up
- Compatible with Microsoft 365 and Google Workspace
- Spots phishing and impersonation
- Clears links in emails
- Isolates infected attachments
Cons:
- No free trial
The Trustifi platform also includes Outbound Shield. That service classifies sensitive data and scans outgoing emails for incidences of it. This will act in different ways according to the security policies that you set up regarding email user accounts and their permissions over data usage. The tool also includes account takeover detection.
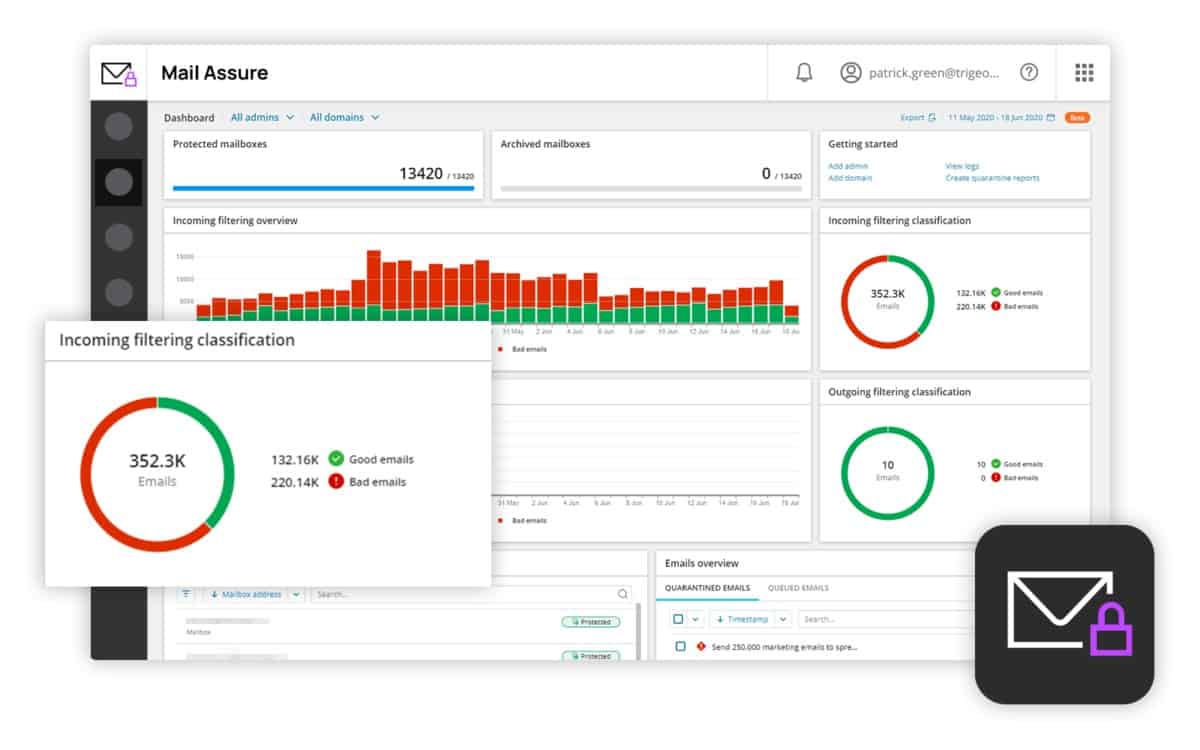
3. N-able Mail Assure
N-able Mail Assure uses blacklists and AI techniques to block phishing and malware in inbound emails. This is a cloud-based service and it is particularly aimed at managed service providers (MSPs), which is the target market for the N-able brand. The system is intended for use by the MSPs to offer extra service to their customers. The system can also be used by the centralized in-house system monitoring team of a multi-site business.
Key Features:
- Cloud-based
- Multi-tenant system
- Continuity service
- Protection from malicious activity
Among the indicators that Mail Assure searches for in inbound emails include signs of spam, phishing, impersonation, spoofing, and malware.
As well as scanning incoming emails for malicious content, this tool implements threat detection routines on both inbound and outbound emails. The entire system can be applied to Microsoft 365 by the application of a plug-in.
The Mail Assure system offers user accounts on its portal. This also makes emails that pass through the service available through the portal. If a protected business loses the use of its primary email service, its users can access their emails and also send and receive new mails there until the email server comes back online. When the primary server becomes available again, Mail Assure syncs missed emails onto it.
One more service offered by the Mail Assure system is an archiving function. This compresses and encrypts emails. These archives can be queried.
Pros:
- Scans incoming emails for phishing, impersonation, and spoofing
- Continuity service
- Email archiving
- Integrates with Microsoft 365
Cons:
- The multi-tenanted architecture is difficult to set up
N-able Mail Assure is available for a 30-day free trial.
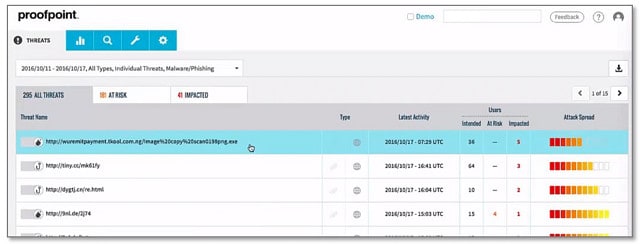
4. Proofpoint Essentials
Proofpoint Essentials is a cloud-based service that is tailored to use by small and middle-sized businesses. The system protects social media accounts as well as email systems.
Key Features:
- Email and social media protection
- Continuity service
- Email archiving
Other benefits of this package include a continuity service and an archiving system. It can help you recover from accidental or intentional damage to your email system. Archiving can store emails for up to 10 years, which will help you towards data security standards compliance.
The Proofpoint system acts as a front-end to your own email server. The tool receives all of your company’s emails first. After processing those emails to check for security issues, it will either hold them back or send them through to your own mail server, depending on the outcomes of its investigations.
Withheld emails are kept in storage on the cloud server and systems administrators can log into the Proofpoint dashboard to check on them. The dashboard displays assessments of each suspicious email and also has screens for overall email throughput and processing performance monitoring.
The security procedures implemented by Proofpoint Essentials include searches for signs of spam, phishing, and malware. The tool will also validate all links in emails to check for fake or infected targets.
Outbound emails also get scanned. You can define security policies that apply encryption to specific email types and the service also implements data loss prevention.
Pros:
- Security scans for incoming email
- Data loss prevention
- Enforced encryption for outgoing emails containing sensitive data
Cons:
- No on-premises option
Proofpoint Essentials is available for a 30-day free trial.
5. Trend Micro Email Security
Trend Micro Email Security is delivered from the cloud and uses AI techniques to scan for malicious content in emails.
Key Features:
- Spam and phishing detection
- URL verification
- Attachment sandboxing
The Trend Micro system diverts all of your email traffic to its own mail server for filtering. The tool looks for spam, phishing, impersonation, and malware in the emails. It also scans attachments for malware. Both emails and attachments are examined for links and each discovered target is scanned for infection or impersonation.
The AI strategy built into the detection rules is based on machine learning. Their purpose is to identify zero-day attracts by establishing a baseline of normal activity and flagging exceptions.
There are two plans offered for Trend Micro Email Security: Standard and Advanced. Extra features in the Advanced plan include a continuity service that allows your users to access their mail on the Trend Micro server if your main email server goes down. The plan also offers protection for Microsoft 365 and Google Workspace. The Advanced system analyzes the authorship signatures of email texts and maintains a 60-day analysis window to find repeated attempts and persistent threats.
Pros:
- Includes a threat intelligence feed garnered from customer-base experience
- Blocks malware, phishing, spam, and impersonation
- Offers an email continuity service
Cons:
- No on-premises version
Trend Micro Email Security is available on a 30-day free trial.
6. Barracuda Email Security Gateway
Barracuda Email Security Gateway is a network appliance that manages all email transmissions in and out of your mail server. Barracuda provides a threat intelligence feed and frequent software updates to keep each implementation of the Gateway up to date with the latest developments in email attack strategies.
Key Features:
- Spam, phishing, and malware detection
- Link validation
- Attachment scanning
The Barracuda Email Security system doesn’t just patrol the connection point between a network and the internet. It also communicates with plug-ins installed on all email clients operating within the business. This part of the service is designed to spot security threats transmitted through internal emails.
The benefit of having the email security delivered in an appliance means there is no danger of any infection ever getting onto your own servers. By weeding out spam emails and other email-based attacks, this tool considerably reduces the amount of traffic that your network and email server need to deal with.
The device will hold back emails that are detected to contain malicious content. This filtering extends to attachments. The system also provides a continuity service because if the main email server goes down, the client plug-ins automatically switch to interfacing with the Barracuda appliance instead.
The service also scans through outgoing emails plus those sent out from clients to other addresses within the business. This system implements sensitive data protection as part of a data loss prevention strategy. The module also includes data security standards compliance assurance. The outbound email management system also optionally enforces email encryption.
Pros:
- Protection for external and internal email
- Data loss prevention
- Email continuity
Cons:
- Not offered as a software package
Barracuda Email Security Gateway is available on a 14-day free trial.
7. Hornetsecurity Spam and Malware Protection
Hornetsecurity’s Spam and Malware Protection is a SaaS package that is able to block 99.9 percent of all spam. As well as filtering out the great burden of processing spam, this service will also absorb DDoS attacks aimed at email servers. This combination radically cuts down a lot of the volume that your network and email servers have to cope with.
Key Features:
- Spam filter
- Malware blocking
- Cloud service
The Hornetsecurity system stops malware sneaking through to your system by hiding in emails and their attachments. This includes the blocking of Trojans, spyware, and ransomware. The success of Hornetsecurity at blocking malware is even higher than its spam blocking success rate – it is at 99.99 percent.
Pros:
- Easy to implement
- URL checking
- Protection from infected websites
Cons:
- No free trial
One of the main problems companies face with emails is the danger of phishing. The Hornetsecurity system addresses this by scanning all URLs in emails – most phishing successes are implemented through fake websites. The link verification service also blocks sites that contain malware download mechanisms.
8. Fortinet FortiMail
Fortinet FortiMail is part of the Fortinet Security Fabric. This system is a framework that fits together with a range of tools to provide a complete corporate security package. You don’t have to implement every element of the Security Fabric. However, the central product is the FortiGate firewall. If you implement FortiMail, it is most likely that you will do so as a supplement to FortiGate.
Key Features:
- No load on your servers
- Blocks spam and phishing
- Detects malware
Fortinet products are delivered on an appliance or as a SaaS package. You can reduce cost overhead and make Fortinet products more affordable by hosting FortiMail on the same device as FortiGate.
The FortiMail system catches all incoming and outgoing emails, giving it the chance to examine emails for threats in both directions. The information extracted during these servers can also be fed into the FortiSIEM security monitoring service if you also subscribe to that system.
Inbound emails are scanned for spam and impersonation attempts. It can also block phishing attempts through URL scanning. Outbound emails are assessed for data loss prevention. The DLP service enforces compliance with PCI DSS, HIPAA, and GDPR.
Pros:
- Reduces load on email servers
- Blocks spam, BEC, impersonation, phishing, and malware
- Deployment options
Cons:
- No free trial
FortiMail is also available as a virtual appliance or as a service on AWS or Azure. Access a free demo of Fortinet FortiMail.