Endpoint protection is a security solution that addresses endpoint security issues, securing and protecting endpoints against zero-day exploits, attacks, and inadvertent data leakage resulting from human error.
Here is our list of the best endpoint protection solutions and software:
- Guardz EDITOR’S CHOICE This cloud-hosted application and data security platform can protect both on-premises and cloud-based software through external attack surface scanning, risk assessment, live activity monitoring, and Dark Web scanning. Get a 14-day free trial.
- ThreatLocker (GET FREE DEMO) This cloud-based service prevents unauthorized software, such as malware, from running on an endpoint by blocking all execution other than by specifically authorized software that is registered in a whitelist. Available for integration into all the major RMM tools or as a standalone product. Access a free demo.
- ManageEngine Vulnerability Manager Plus (FREE TRIAL) An endpoint security system that is bundled into a unified endpoint management service. Installs on Windows and Windows Server.
- ManageEngine Log360 (FREE TRIAL) Endpoint agents gather logs activity data that is sent to a central server for SIEM threat hunting. Runs on Windows Server.
- NinjaOne Endpoint Security (FREE TRIAL) This cloud-based package is part of a platform of tools that are designed for use by managed service providers, enabling them to protect the systems of their clients.
- ESET Endpoint Security (FREE TRIAL) Endpoint protection that includes network protection tools.
- Bitdefender Gravity Zone Endpoint Security Protection for devices that can be combined with network protection.
- CrowdStrike Falcon A cloud-based endpoint protection platform that combines a next-generation AV, a threat intelligence feed, a UEBA, and firewall management to coordinate full system security.
- Barracuda XDR A managed security service that MSPs can pass on to their clients. This is a SaaS package.
- CoSoSys Endpoint Protector Cloud-based data loss prevention software that also available as a virtual appliance. It helps towards HIPAA, GDPR, and PCI DSS.
- Sophos Intercept X Endpoint An AI-based security system.
- Trend Micro Apex One A blend of traditional and innovative protection techniques.
- N-able EDR A combined endpoint and network protection solution.
- Check Point Harmony Endpoint Includes threat detection and remediation, phishing protection, and a ransomware immunizer.
- Symantec Endpoint Detection and Response Cutting-edge malware and intrusion protection
- Panda Endpoint Protection Protection for networked computers, managed from the cloud.
- CounterTack GoSecure ESL Predictive, AI-driven endpoint protection.
- Malwarebytes Endpoint Protection Cloud-based protection for computers on a network.
- Cylance Protect AI threat protection for endpoints.
Are endpoint protection solutions better than using antivirus software?
As soon as antivirus producers develop a solution to a piece of malware, hackers discover another attack strategy. New viruses, for which an antidote has not yet been created, are called “zero-day” attacks. Hackers can continue to cause damage to the computers of businesses and the general public by keeping a virus production pipeline running.
Knowing that there is always going to be another virus on the horizon to deal with, cybersecurity companies have chosen a new approach. Rather than trying to identify individual viruses and work on blocks for them, companies now focus on spotting anomalous behavior and locking down key services on computers and computerized devices to prevent tampering.
This new strategy is broader than the antivirus or anti-malware approach of one application to defend a computer. Many no longer include a virus database, which, by some industry definitions, means that they do not qualify for the label “antivirus.” A new buzzword emerging in the field is “replacement” technology. These new cybersecurity suites replace antivirus systems entirely with a new AI-based baseline and deviation detection systems.
What is an Endpoint Protection solution?
The umbrella term applied to all cybersecurity efforts to protect a device connected to a network, as opposed to the network itself, is “endpoint protection”. This review will look at the leaders in the field of endpoint protection and how each of those cybersecurity providers approaches the task of protecting user devices.
There isn’t a single solution format for replacement technology. The defining feature of endpoint protection is that it is based on the device that the user accesses. In some cases, that solution is delivered from an external source, but its priority is to protect individual devices, not an entire system of network-connected devices.
Firewalls aren’t regarded as part of endpoint protection. This is because they are designed to protect networks. In many domestic implementations, firewalls run on a computer and operate to protect just one computer. However, firewalls are designed to block traffic, whereas endpoint protection looks at the processes running on a computer.
There are some types of cybersecurity strategies that fall both into the network protection and endpoint protection categories. An example of these is cyber defense which focuses on analyzing log file messages to spot malicious activity – that strategy can be applied to both network and endpoint protection.
The best endpoint protection solutions and software
Although attacks on privately-owned devices are of serious concern, the main focus of the cybersecurity industry is on solutions to defend businesses. Corporate buyers need protection for all of their equipment, including networks and endpoints. So, many endpoint protection systems form part of a suite of programs that cover the entire technology infrastructure. In this guide, we will detail only those modules that protect endpoints.
Our methodology for selecting an endpoint protection solution
We reviewed the market for endpoint protection solutions and analyzed tools based on the following criteria:
- Behavior tracking for baselining
- Asset identification
- Anomaly detection to combat zero-day attacks
- A range of system protection measures for a multi-strategy approach
- Automated responses
- A free trial or a demo for a risk-free assessment opportunity
- Value for money from a reliable protection system that is offered at a fair price
With these selection criteria in mind, we identified the outstanding EPPs that provide universal protection strategies. You can read more about these options in the following sections.
1. Guardz (FREE TRIAL)
Guardz covers endpoints, cloud data storage, and email systems. Its endpoint protection unit looks for malware and intruders. The service is hosted in the cloud and is intended for use by managed service providers to look after the systems of their clients.
Key Features:
- Cloud-Based Operation: Ensures comprehensive monitoring and protection from the cloud, eliminating the need for on-site hardware.
- Malware Detection: Actively searches for and neutralizes various forms of malware, safeguarding your digital environment.
- Advanced Threat Surveillance: Monitors for sophisticated cyber threats, ensuring early detection and response.
- Multi-Device Support: Compatible with various operating systems, including Windows, macOS, and mobile devices.
- Real-Time Monitoring: Continuous monitoring of devices to detect and respond to threats swiftly.
Why do we recommend it?
Guardz is a cloud-based system and it protects endpoints from automated and manual attacks. The full platform also protects the cloud suites of Microsoft 365 and Google Workspace. The service also offers a library of security awareness training courses to help users spot cons.
This system provides a high degree of automation, which maximizes the value of expensive technicians – an important feature for MSPs that need to cut costs wherever possible to beat the competition on price.
One of the main channels used by hackers is by email. So, the Guardz system focuses a lot of attention on scanning incoming emails. The tool looks for spam, phishing, impersonations, and malware – these could all get onto your endpoints and cause havoc. The tool quarantines suspicious emails without the user even seeing those mails.
If a hacker steals account credentials you could have an unwelcome guest on your network without knowing it. This is called an advanced persistent threat (APT) and has been a major cause of data theft events suffered by large organizations. APT is difficult to spot, but Guardz looks for anomalous behavior that indicates that the regular user of that account is not behind current activity.
Automated attacks involve a variety of malware and Guardz spots them all. These include spyware, ransomware, Trojans, adware, keyloggers, viruses, and fileless malware.
Who is it recommended for?
This package is a good option for businesses that don’t have cybersecurity staff on the payroll. The system is only available through managed security services and Guardz also offers a managed security service itself. The platform also includes a library of security awareness courses for users, so it is an ideal package for businesses that know nothing about security procedures.
Pros:
- Automated Protection: Provides robust security measures against both automated and manual cyber attacks, including sophisticated email threats.
- Email Security: Enhances email systems’ defenses, identifying and isolating phishing, spam, and malicious software before they reach the inbox.
- Cybersecurity Training: Includes a variety of security awareness courses, educating users on potential cyber threats and best practices.
- Compliance Management: Assists organizations in maintaining compliance with industry regulations.
Cons:
- MSP Requirement: Access to the platform is exclusively through managed service providers, which may limit direct control for some businesses.
The Guardz platform has a subscription rate per user per month and there is no lower limit to team size, so the package is suitable for all sizes of businesses. You can examine the Guardz platform with a 14-day free trial.
EDITOR'S CHOICE
Guardz is our top pick for an endpoint protection solution because it is designed to safeguard devices against a wide range of cyber threats. Its security suite includes antivirus and anti-malware features, ensuring real-time protection against known and emerging threats. One of the important features of Guardz is its automated backup capability, which protects critical data from ransomware attacks and other forms of data loss, providing peace of mind for users. The user-friendly dashboard makes it easy for both IT professionals and non-technical users to monitor their security status and manage settings effectively. Guardz includes web filtering to block access to malicious websites, further enhancing user safety. Its email security features protect against phishing attacks, addressing one of the most common entry points for cyber threats. Guardz also supports multiple devices across various operating systems, including Windows, macOS, and mobile platforms, making it a versatile choice for organizations with diverse environments. Guardz stands is an effective endpoint protection solution, combining essential security measures with user-friendly management, making it ideal for businesses aiming to bolster their cybersecurity defenses..
Download: Start a 14-day FREE Trial
Official Site: https://app.eu.guardz.com/signup
OS: Cloud-based
2. ThreatLocker (ACCESS FREE DEMO)
Tested on: Cloud-based
ThreatLocker takes a different approach to endpoint protection. Rather than scanning constantly for malicious programs that could start running and cause damage, the ThreatLocker system blocks all software from being able to run. This default block is then modified by Allowlisting specific software. Thus, anything that is not on the list will be unable to launch. Any new software, including malware, will be similarly disabled and so does not present a threat.
Key Features:
- Zero Trust Security: Adopts a stringent approach by defaulting to block all software, only permitting operations from a pre-approved allowlist.
- Execution Control: Grants permission solely to vetted applications, ensuring only trusted software runs on your systems.
- Peripheral Management: Offers rigorous control over external devices, such as USBs, to prevent unauthorized access and data exfiltration.
Why do we recommend it?
ThreatLocker uses the Allowlisting strategy to block malicious software. This disables the mechanism that runs software and makes it check on a whitelist of systems. The operating system will allow those programs to run. The system also blocks USB ports from accepting any devices that are not on another whitelist.
The ThreatLocker system operates a Learning Mode for its allowlisting. This takes about a week and it records the software that is regularly used on each endpoint, creating a candidate list of software that could be allowed to continue to operate once the learning phase ends and lockdown starts.
USB memory devices present a number of problems for cybersecurity managers. The first of these is that they can be used to introduce malware to an endpoint but that isn’t an issue with ThreatLocker-guarded computers. However, those memory sticks can also be used to steal data. So, ThreatLocker blocks them from attaching to the operating system. Users have to request permission to use a USB device, and that permission can be withdrawn at any time.
Other features on the ThreatLocker platform include an application fencing service, which restricts which drives and files a software package is allowed to access. There is also a network access control (NAC) service. This relates to devices rather than to users and it is implemented through the Access Control Lists (ACL) that any administrator familiar with router-based network security will understand.
ThreatLocker provides a complete block on unauthorized software, which includes user-installed utilities and malware. It doesn’t matter if a damaging program gets onto your endpoint because it is a dead file if it can’t trigger and run. This straightforward solution simplifies the administration of endpoints because you set up a whitelist of approved software for endpoints, and so regular scans of each device identify unauthorized systems that will be removed automatically, in between scans, those as-yet-unnoticed malicious programs can do no harm.
Who is it recommended for?
This strategy is very easy to understand, so you don’t need to be a cybersecurity expert to master the ThreatLocker protection system. Any size of business would benefit from this package. ThreatLocker produces a multi-tenant edition for use by managed service providers.
Pros:
- Quick Setup: Allows for rapid deployment and configuration, minimizing downtime and operational disruption.
- Rigorous Access Control: Implements a comprehensive zero trust framework, enhancing security by verifying every access request.
- Comprehensive Cloud Protection: Safeguards both on-premises and cloud-based assets, providing a unified security posture across environments.
Cons:
- Limited User Permissions Management: While strong on software and device control, it lacks an extensive user access management feature.
ThreatLocker is a cloud service and during the onboarding process, you will be guided by the setup system to download and install agents on all of your devices and that gets the ThreatLocker package active. Register for access to the demo to learn more about ThreatLocker.
3. ManageEngine Vulnerability Manager Plus (FREE TRIAL)
ManageEngine Vulnerability Manager Plus offers protection for endpoints running Windows, Windows Server, macOS, and Linux – the console for this package of security services installs on Windows Server and each enrolled device requires an agent program installed in it.
Key Features
- Automated Scanning: Conducts comprehensive scans automatically to detect vulnerabilities across your network.
- Patch Deployment: Manages and applies necessary software updates to mitigate vulnerabilities swiftly.
- Security Configuration: Implements system hardening techniques to strengthen the overall security posture.
Why do we recommend it?
ManageEngine Vulnerability Manager Plus is a preventative protection package. This is a comprehensive service that identifies system settings and statuses that will enable malware and intruders to access or damage the system. The bundle also checks on unauthorized software and out-of-date system. It will automatically fix discovered problems.
The endpoint protection system is actually a bundle of tools. Central to the whole package is a vulnerability scanner. When starting its service, the system searches the network for all endpoints and installs an agent on each. Then it does a full scan, looking for vulnerabilities.
The vulnerability scanner receives an update feed whenever a new vulnerability is discovered. This could be a loophole in a piece of software or a combination of system settings that makes life easier for hackers. A new problem to look out for triggers a new scan of the entire system. The agents on each endpoint also perform a scan automatically every 90 minutes – this catches any new software that might be installed and also picks up on system configuration changes.
Vulnerability Manager Plus polls for new software updates – this is often the main solution to shut down loopholes. The system can implement problem remediation automatically. This will install patches and reconfigure devices to tighten up security. Alternatively, you can set the system to notify you of problems and suggest solutions, so you can investigate and launch the repairs yourself.
Who is it recommended for?
ManageEngine is good at catering to small businesses. The company provides a free edition that has all of the features of the paid options but it is limited to covering 25 endpoints. All sizes of enterprises can benefit from using this package. Use this service to protect devices running Windows, macOS, and Linux.
Pros:
- Proactive Protection: Focuses on identifying and rectifying potential security weaknesses before they are exploited.
- Detailed Reporting: Offers in-depth reports that demonstrate security improvements and pinpoint areas requiring attention.
- Scalability: Designed to accommodate large networks, ensuring protection as your business grows.
- Versatile Platform Compatibility: Supports a wide range of operating systems, including Windows, macOS, and Linux, offering flexibility in deployment.
Cons:
- Complex Ecosystem: Navigating through the extensive features and tools within the ManageEngine suite may require a significant learning curve.
Vulnerability Manager Plus is offered in three editions: Free, Professional, and Enterprise. The free version is limited to monitoring 25 computers. The Professional edition covers one site and the Enterprise edition covers WANs. Both paid systems are offered on a 30-day free trial.
4. ManageEngine Log360 (FREE TRIAL)
ManageEngine Log360 is a SIEM system that collects log data from endpoints to identify whether one is under attack. The security offered by this system also covers cloud platforms. The endpoint hosts an agent that gathers data to be sent to the log server and SIEM for analysis.
Key Features:
- Unified Threat Management: Offers a comprehensive view of security threats across the network, centralizing detection efforts.
- Agent-Based Data Collection: Utilizes on-device agents to gather detailed log data for analysis.
- Integrated SIEM System: Analyzes log data to identify security threats, enhancing overall protection.
Why do we recommend it?
ManageEngine Log360 is a very large package that bundles together many ManageEngine systems, including ADAudit Plus, EventLog Analyzer, M365 Manager Plus, Exchange Reporter Plus, and Cloud Security Plus. Features include a SIEM, data loss prevention, and user activity tracking. The service also lays down an audit trail for compliance reporting.
The agent collects Windows Events and Syslog messages from operating systems and also interacts with more than 700 software packages. When logs arrive at the log server, they are converted to a neutral format so that they can be stored and searched together.
The SIEM looks through these records in a threat hunting process that is enhanced by a threat intelligence feed. If suspicious activity is identified, the system raises an alert. This appears in the dashboard of Log360 and can also be forwarded as a notification, fed through a service desk system, such as ManageEngine ServiceDesk Plus, Jira, and Kayoko.
Logs are stored for compliance auditing and the Log360 system also includes a compliance reporting module for HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA.
Responses for endpoint protection require manual intervention or the participation of an external SOAR service.
Who is it recommended for?
This package is aimed at large businesses. It provides a lot of functions and not every buyer will need all of them. The SIEM core of this service is relevant to endpoint protection and it is available as a standalone service with the EventLog Analyzer package.
Pros:
- Rapid Threat Detection: Enables swift identification of suspicious activities, facilitating immediate response to protect endpoints.
- Extensive Integration Options: Seamlessly works with various service desk systems for efficient incident management.
- Cloud Security Coverage: Extends protection to cloud platforms, ensuring a secure cloud computing environment.
- Regulatory Compliance Support: Includes tools for compliance reporting across multiple standards, aiding in audit preparation.
Cons:
- Limited Server Support: Does not offer server software compatible with Linux, potentially restricting its use in Linux-based environments.
The server for ManageEngine Log360 runs on Windows Server. You can assess the package with a 30-day free trial.
5. NinjaOne Endpoint Security (FREE TRIAL)
NinjaOne is a remote monitoring and management (RMM) system that is designed for use by managed service providers (MSPs). This cloud platform includes an endpoint security service, which can be used by MSPs as an add-on to the RMM system.
Key Features:
- MSP-Oriented Design: Tailored specifically for managed service providers to offer comprehensive endpoint security services.
- Managed Antivirus: Features robust antivirus solutions, managed centrally for enhanced endpoint protection.
- Endpoint Drive Encryption: Ensures data is encrypted on endpoints, adding an extra layer of security.
Why do we recommend it?
NinjaOne Endpoint Security is a cloud-based system that is available from a platform of tools that implement remote monitoring and management (RMM). So, this is a hybrid security service for endpoints that is guided from a central administrator console in the cloud. It is a repackaging of BitDefender and Webroot AV software.
The NinjaOne security system has several layers and the most important endpoint protection feature in the package is an antivirus system. This is a managed service, which means that the MSP technicians can remotely access the AV unit that is installed on each protected endpoint and also get activity data sent to the technician console.
Functions that the AV service enable include a record of the devices on which the AV has been installed and which endpoint still has the AV running. This will tell you that possibly the device’s user has uninstalled the software or there is a problem with that device’s network connection. Lone computers of remote, home-based workers can be included in a client’s MSP service plan and so in some cases, the MSP technicians might be dealing with user-owned devices.
The AV available in the NinjaOne package is supplied by Bitdefender. This package needs to be installed on each device but it is also provided with a cloud-based coordinating console. An alternative AV system offered by NinjaOne is provided by Webroot. This also has on-device elements and a cloud-based console. So, you can either choose yourself or offer a choice to your clients which AV your MSP offers for endpoint security.
Who is it recommended for?
The NinjaOne platform was originally designed for use by managed service providers but it is now also marketed to IT departments for in-house system monitoring and management. The main package on the platform is the NinjaOne RMM and the most likely customers of the Endpoint Protect service are existing RMM buyers.
Pros:
- Antivirus Selection: Offers a choice between leading antivirus solutions from Bitdefender and Webroot, managed centrally for ease of use.
- Compliance and Reporting: Provides detailed reporting on antivirus coverage and compliance across client endpoints.
- Simplified Deployment: Automates the installation and updates of antivirus software, streamlining endpoint security management.
Cons:
- RMM Package Requirement: Endpoint security services are only available as part of the broader NinjaOne RMM suite, limiting standalone purchase options.
You can access a 14-day free trial to assess the platform and find out more about pricing.
6. ESET Endpoint Security (FREE TRIAL)
ESET Endpoint Security protects your company’s computers from malicious activity that might enter over your network. It also blocks any malicious software from connecting to your network. This is termed a “two-way firewall” and it is the second line of defense. The first line of defense is a Host-Based Intrusion Prevention System (HIPS) that monitors event messages in the log files on your computers.
Key Features
- Proactive HIPS: Utilizes Host-Based Intrusion Prevention System (HIPS) technology for early detection of malicious activities.
- Botnet Protection: Specifically targets and neutralizes botnet threats to prevent DDoS attacks and other risks.
- Flexible Deployment: Offers options for both cloud-based and on-premises installations, catering to diverse IT environments.
The HIPS methodology looks for patterns of malicious behavior. The responses to any discovery can be automated so that damage will not continue during the times that the security system’s dashboard is unattended. Some of the actions that the detection system looks for are botnet messages that generate DDoS attacks on other computers and ransomware.
This security service runs on-site and it can be installed on Windows and Linux. A cloud-based version is available. ESET also produces network attack protection software.
Pros:
- Advanced Monitoring Dashboard: Provides a highly customizable interface with visual analytics for comprehensive monitoring.
- Behavioral Detection: Employs HIPS to detect threats based on behavior, offering protection beyond traditional signature-based methods.
- Comprehensive Network Defense: Equipped to prevent botnet propagation and identify command and control communications effectively.
- Deployment Versatility: Available in both cloud-based SaaS and on-premise versions to suit various organizational needs.
Cons:
- Complexity for Smaller Networks: While powerful, some features may be overly comprehensive for smaller or home networks, leading to underutilization.
Try out the ESET PROTECT platform in action with a 30-day FREE trial.
7. Bitdefender GravityZone Business Security
Bitdefender has been an antivirus (AV) producer since it started up in 2001. More recently, the company has shifted its defense systems from the traditional antivirus model to comprehensive system defense packages. The company produces network defense systems as well as endpoint protection.
Key Features:
- Traditional and Behavioral Detection: Integrates signature-based AV with anomaly-based threat detection for comprehensive security.
- USB Device Management: Employs controls to manage and monitor USB device access, enhancing data security.
- Versatile Protection Methods: Offers a combination of intrusion detection, web-threat protection, and device encryption for robust defense.
Why do we recommend it?
Bitdefender GravityZone Business Security is a multi-license package of a solid AV system. The GravityZone package also includes a backup and recovery plan, which is essential for mitigating the damage caused by ransomware. The bundle also provides a vulnerability manager for system hardening.
GravityZone includes a signature detection database, which is similar to the traditional method of looking through a list of virus characteristics. Another similarity to traditional AV performance is that GravityZone terminates virus processes and removes the program. GravityZone adds on intrusion detection procedures to that layer of AV actions.
The tool monitors for attempts to access the device and blocks those communication sources that display malicious intent. It also tracks regular activities on the device to establish a baseline of typical behavior. Anomalous activity that deviates from that baseline provokes defense measures. The measures include tracking apparent exploit activity that characterizes “zero-day” attacks.
On top of threat resolution, the security suite will strengthen the defenses of your device. This module of the suite includes a patch manager to automatically install updates to the software. It also encrypts all of your disks to make data unreadable to intruders. The package also includes web-threat protection, USB checks, and application monitors. The package also includes a firewall.
Who is it recommended for?
The main shopping cart for Bitdefender GravityZone Business Security lets you choose between three and 100 licenses in your purchase. So, this gives you an idea of the size of businesses that this package is aimed at. Companies with more than 100 endpoints can get a custom quote.
Pros:
- Intuitive Interface: Features a user-friendly dashboard that simplifies navigation and accelerates the learning process.
- Dual Detection Mechanisms: Utilizes both signature recognition and behavioral analysis to accurately identify a wide range of threats.
- Enhanced Data Security: Provides disk encryption to safeguard data, even in the event of unauthorized access.
- Comprehensive Device Control: Includes robust options for managing USB port access to prevent potential security breaches.
Cons:
- Documentation Gaps: Could benefit from more extensive guidance and resources to help new users optimize their use of the platform.
Bitdefender offers a free trial of GravityZone.
8. CrowdStrike Falcon
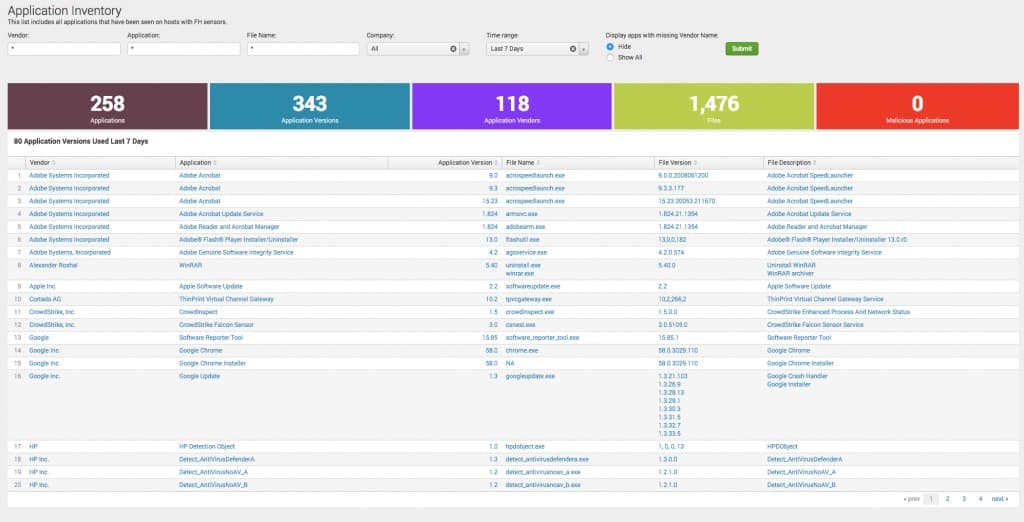
CrowdStrike Falcon is a cloud-based endpoint protection platform (EPP). The system includes AV, threat protection, and device control. This multi-vector approach creates a very thorough endpoint protection system that deploys AI techniques and threat intelligence to block any damaging events that would harm your enterprise.
Key Features:
- AI-Powered Monitoring: Utilizes artificial intelligence to establish normal behavior patterns and detect anomalies.
- Reduction in False Positives: Sophisticated algorithms aim to minimize incorrect threat alerts, improving operational efficiency.
- Modular Approach: Offers a flexible, scalable solution that adapts to various security needs through a selection of modules.
- Enhanced Firewall Integration: Works in conjunction with existing firewall setups to streamline policy management and enforcement.
- Comprehensive Coverage: Provides protection across both cloud and on-premises environments, ensuring a broad defense perimeter.
Why do we recommend it?
CrowdStrike Falcon is a product range that is built upon one product; an endpoint-resident unit, called Falcon Prevent. All of the other packages in the CrowdStrike Falcon product family rely on Prevent for local data gathering and response. Prevent can coordinate with cloud controllers and it can also operate independently if the endpoint is offline.
The platform is composed of modules and all operate both in the cloud and on-site. The on-premises element of the EPP is implemented with an agent that you need to install on your system. This agent ensures that endpoint protection keeps running even if you lose your internet connection.
The key endpoint protection module of Falcon is called Falcon Prevent. This is the AV replacement that combats malware. The system uses machine learning to monitor the regular activities on a device and then identify anomalous actions. The advantage of this AI approach is that it can cat malicious activity that hijacks authorized programs to implement attacks. An example of this type of attack is fileless malware, which traditional AV systems could not spot.
The CrowdStrike Falcon platform is offered in four editions: Pro, Enterprise, Premium, and Complete. The Complete package is a managed service, which removes the need for you or your staff to monitor the service to spot problems and act on them – the CrowdStrike staff does that for you. The Pro edition is the entry-level package that includes Falcon Protect plus Falcon Intelligence, which is a threat intelligence system. The Pro package also includes Falcon Device Control, which lets you block or manage access to USB devices. Another module in the Falcon Pro bundle is Falcon Firewall Management. This doesn’t replace your firewall, but it interfaces to it, making policy creation a lot easier.
Who is it recommended for?
The Falcon range is a little pricey and many small businesses are probably going to prefer cheaper options, such as Bitdefender. This system is suitable for mid-sized and large businesses. It can operate a site-wide security monitoring service and also centralize security protection for multiple sites.
Pros:
- Advanced Detection Capabilities: Employs both AI and process scanning to promptly identify and mitigate threats without solely relying on log analysis.
- Unified HIDS and EPP: Combines the functions of a Host-Based Intrusion Detection System and endpoint protection in a single solution.
- Continuous Improvement: The system’s ability to detect anomalous behavior enhances with prolonged network observation, offering improved security over time.
- Flexible Deployment: Compatible with both cloud and on-site architectures, with lightweight agents that minimize impact on system performance.
Cons:
- Trial Period Limitations: A longer trial could offer potential users a better opportunity to evaluate the platform’s full capabilities.
CrowdStrike offers a free trial of Falcon Pro.
9. Barracuda XDR

Barracuda XDR is a managed security service. That means that the XDR is not only a SaaS package but it also comes with a team of cybersecurity experts to run the system for you. The XDR is marketed to managed service providers. The proposal is that MSPs offer the Barracuda XDR to their clients and Barracuda does all of the work.
Key Features
- Comprehensive Network Defense: Offers robust protection across networks, ensuring secure operations and data flow.
- Cloud Protection: Safeguards cloud-based assets against a wide range of cyber threats, enhancing cloud security.
- Advanced Email Security: Protects against email-borne threats, including phishing, spam, and malware.
Why do we recommend it?
Barracuda XDR is a tool from a leading and highly respected cybersecurity brand. This is one of several hybrid solutions on the list here. The benefit of this approach is that every endpoint is scanned and the cumulative experience of the whole fleet is mined for threats as a central data pool in the cloud.
The Barracuda XDR proposal provides a Security Operations Center (SOC) for MSP clients. The full menu of services included in each package can be customized. Options include network, cloud, email, endpoint, and server security monitoring.
The XDR installs an agent on the client’s system and then gathers log messages. These are uploaded to the Barracuda cloud server where they are consolidated and searched for threats. If a threat is detected, the service can implement automated responses, such as suspending a user account or blocking communication from a suspicious IP address. The security experts examine these actions and decide whether further action is needed.
The threat-hunting service works by anomaly detection. This uses machine learning to establish a pattern of regular activity per user and per device. Deviations from this standard provoke an alert. The Barracuda SOC is operational around the clock, so protection is never lacking at any time of the day or night.
Who is it recommended for?
The XDR approach is very similar to the SIEM strategy. The Barracuda system is a high-end package that is suitable for use by large enterprises and mid-sized businesses that are growing quickly. Small businesses that operate a virtual office with a geographically dispersed workforce would need this system.
Pros:
- Continuous Monitoring: Employs around-the-clock surveillance by cybersecurity professionals, ensuring constant protection.
- AI-Driven Anomaly Detection: Utilizes artificial intelligence to identify unusual activities, providing early warning of potential threats.
- Hassle-Free Management: Designed for MSPs to offer to their clients, with Barracuda handling all operational aspects.
Cons:
- Potential Customer Data Concerns: MSPs might be wary of sharing their client information with an external provider like Barracuda.
Barracuda offers a demo of their XDR service.
10. CoSoSys Endpoint Protector

Endpoint Protector is a data loss prevention system that uses traffic monitoring and encryption enforcement to protect data. The service examines traffic to block intruder data theft and insider threats.
Key Features:
- Cloud-Enabled Security: Leverages a cloud-based edge service for scalable and flexible data protection.
- Comprehensive DLP: Offers data loss prevention capabilities to secure sensitive information from unauthorized access or theft.
- Agent-Driven Endpoint Safeguards: Enhances security with agents on Windows, Linux, and macOS devices, enforcing data policies and encryption.
- Device and Port Management: Provides USB and port control to manage data transfer and prevent leaks or malware intrusion.
- Sensitive Data Identification: Includes a feature for discovering and managing personally identifiable information (PII) across the network.
Why do we recommend it?
CoSoSys Endpoint Protector can guard devices running Windows, Linux, or macOS. This service also includes a device control module, which reduces the opportunities for malware to get onto your system or for users to steal data. This package provides a great combination of system virus protection and data loss prevention.
The Endpoint Protector system is an edge service and it can be implemented through a SaaS system hosted by CoSoSys, the creators of the protection service. Customers can also get the system as software to be installed on an AWS, Azure, or Google Cloud Platform account. Another option is to install the software onsite as a virtual machine. In all cases, the Endpoint Protector system is charged for by subscription.
Agents on devices add further protection for Windows, macOS, and Linux endpoints. These services implement USB and port control to block data from being transferred onto portable storage devices. Not all devices will be blocked because some businesses rely on attached storage devices. Where transfers to devices are allowed, the Endpoint Protector system automatically encrypts data as it passes to the device.
One big problem that many organizations have is that they don’t properly categorize all of their data and don’t know where all of the PII that they manage is actually held. This becomes a headache when the business starts to implement a data security standard, such as HIPAA or PCI DSS.
Endpoint Protector has an eDiscovery module that scans all devices and identifies the locations of all PII. This search enables PII to be protected with encryption and gives the system administrator the option of planning a central data store for PII, which can be monitored and protected more easily than ad-hoc distributed data stores.
Who is it recommended for?
This is a competent and reliable service for businesses that need to prove data protection compliance as well as block malware and intruders. The discovery module to locate and categorize sensitive data is a big plus for companies that need to get a grip on their data spread.
Pros:
- User-Centric Policies: Enables the creation of security policies tailored to individual user behaviors and needs, enhancing protection.
- Proactive Risk Assessment: Evaluates and alerts about vulnerabilities on endpoints, aiding in preemptive threat mitigation.
- Insider Threat Detection: Monitors for unauthorized file access, acting as an effective data loss prevention mechanism.
- Device Control and Encryption: Offers robust controls against data theft and secures data on permitted devices through encryption.
Cons:
- Lack of Trial Option: A demo or trial version for hands-on testing before purchase would be beneficial for potential users to assess its suitability
You can evaluate the online version via a free demo.
11. Sophos Intercept X
Sophos is one of the leading implementers of AI-methods in the cybersecurity industry. Intercept X uses machine learning to establish a baseline of regular activity on a device and then generates alerts when it detects events that do not fit into regular work patterns. That element of the security system detects malware and malicious intrusion. A second element automates responses to detected problems.
Key Features:
- AI-Driven Behavior Analysis: Employs artificial intelligence to monitor standard operations and identify deviations signaling potential threats.
- Protection Against Fileless Malware: Specifically designed to detect and neutralize malware that operates without downloading files to the system.
- Automated Incident Response: Facilitates prompt action against detected threats, reducing the need for manual intervention.
Why do we recommend it?
Sophos Intercept X is an XDR, so it competes with the CrowdStrike and Barracuda tools on this list. This system focuses on blocking malware in all its forms and that includes fileless systems that download from websites and ransomware. Multiple endpoint installations are coordinated by a central threat hunting package.
Other elements in the Intercept X package focus on specific threat types. For example, CryptoGuard is a ransomware-blocking system. Other tools in the pack prevent malware from sneaking onto your device through a browser. This system blocks the methods used by fileless malware, which leaks onto a computer from infected web pages. Another tool checks downloads for viruses and will block the downloads from completing if a virus is sniffed in the file as it downloads. Similarly, the software scans all directories for malware and will also verify any USB memory sticks when they are attached.
Who is it recommended for?
The Intercept X brand is actually a group of products and so, there are options to suit many different types of businesses. However, Sophos is particularly successful in selling to mid-sized businesses. There is also a managed security service option available.
Pros:
- Advanced Threat Detection: Utilizes machine learning to adaptively recognize and thwart emerging cybersecurity threats.
- Comprehensive Ransomware Defense: Features specialized tools like CryptoGuard to actively block ransomware attacks.
- Proactive Automation: Enables automated threat response capabilities, allowing for quick containment and resolution of security incidents.
- Peripheral Security Scanning: Automatically examines external devices upon connection, safeguarding against malware transmission via USBs and other peripherals.
Cons:
- Optimized for Specific Business Sizes: While highly effective, it may offer optimal benefits primarily to small and medium-sized enterprises, potentially limiting its appeal to larger organizations.
12. Trend Micro Apex One
Trend Micro is a prominent AV producer that has crossed over into more sophisticated endpoint protection solutions. Apex One is a blend of old and new. It still has a traditional anti-malware system at its heart, but that threat database lists system vulnerabilities rather than virus signatures. Apex One has added behavior monitoring to improve defenses against zero-day attacks.
Key Features:
- Web Attack Prevention: Shields against threats originating from the internet, including malicious websites and downloads.
- Behavioral Analytics: Utilizes user behavior assessments to detect anomalies that may indicate a cybersecurity threat.
- Automated Mitigation: Implements automatic responses to neutralize detected threats efficiently.
Why do we recommend it?
Trend Micro Apex One is another hybrid solution. In this service, the endpoint unit is an agent with the vast majority of the detection work being performed on the Trend Micro cloud servers. This lightens the burden on endpoint processors but it does mean that full protection is dependent on a functioning internet connection.
The threat-hunting element of this package is a host-based intrusion detection system with automated defense actions. The tool will identify malicious processes. It kills that program and isolates the program that started it. The company calls this “virtual patching”. It will suspend the capabilities of the problematic program until a patch is available for it to close the exploit. That process automatically removes malware, because those malicious programs will never get an update to remove the troublesome behavior.
Apex One provides defense against crypto mining, ransomware, and fileless malware, as well as the traditional Trojans and viruses. This is a cloud-based service, but you will need to install an agent on your computer for it to monitor the system. This runs on Windows and Windows Server.
Who is it recommended for?
Trend Micro is one the leaders in cybersecurity, so you are guaranteed that this is a reliable service. This is probably the closest rival on the list to the Sophos Intercept X XDR option. The solution is probably going to appeal most to mid-sized businesses. A big problem is that this service doesn’t protect devices running Linux or macOS.
Pros:
- Comprehensive Threat Detection: Identifies vulnerabilities and abnormal behaviors, offering protection against a wide array of threats.
- Integrated HIDS: Features host-based intrusion detection capabilities, enhancing overall system security.
- Virtual Patching: Temporarily restricts the functions of potentially compromised programs, reducing the risk of exploitation.
- Browser Security: Provides robust defenses against web-based dangers like crypto mining and malicious scripts.
Cons:
- Cloud-Dependency: Full functionality relies on continuous internet access, which may pose a challenge in environments with unstable connections.
13. N-able EDR
The N-able Endpoint Detection and Response is a good example of the evolution in endpoint security to a full suite of attack protection. This is part of an overall system security service, which is managed from the cloud. The tool uses log analysis and protection methods that derive from SIEM (System Information and Event Management).
Key Features:
- Proactive HIDS: Implements a host-based intrusion prevention system to actively prevent unauthorized access and activities.
- Behavioral Surveillance: Monitors for unusual behavior patterns as indicators of potential security threats.
- Immediate Threat Neutralization: Offers automated responses to detected threats, minimizing the risk of damage.
Why do we recommend it?
N-able EDR is recommended for its comprehensive approach to endpoint and network security, leveraging both host-based intrusion prevention systems and behavior monitoring to identify and mitigate threats. Its ability to scale and provide detailed insights into anomalous activities makes it a formidable tool for protecting large enterprise networks from a variety of cyber threats, including insider risks.
The main module of the Threat Monitor examines log files for warning signs. Just about every action that takes place on your computer and on your network generates a log message. These log messages are not collected automatically. Many businesses just ignore this amazing source of system information that will highlight the anomalous activity that is caused by malicious programs or unauthorized access.
The EDR isn’t just endpoint security because it covers networks as well. The service gathers all of those event messages and stores them to files for analysis. The tool is an Intrusion Protection System (IPS) which can generate standard signs that something is not right on your system. Traditional malware protection will warn you of dangerous processes. The IPS goes one step further than just blocking processes or removing a piece of software because it can block malicious users as well.
Who is it recommended for?
This solution is ideally suited for large enterprises seeking robust endpoint detection and response capabilities. Its integration with SolarWinds’ other security tools, like the Security Event Manager and Patch Manager, makes N-able EDR a powerful component of a holistic security strategy, especially for organizations that prioritize proactive threat detection and automated responses to secure their IT environment against sophisticated cyber attacks.
Pros:
- Scalable Endpoint Defense: Excellently designed to secure extensive networks, making it suitable for large organizational use.
- Advanced Threat Detection: Utilizes behavior analysis to pinpoint and alert on unusual activities, enhancing threat detection.
- Insider Threat Protection: Equipped with intrusion prevention capabilities, it safeguards against both external and internal threats.
- Seamless Integration: Integrates effectively with SolarWinds’ Security Event Manager and Patch Manager for comprehensive security management.
Cons:
- Extended Trial Desired: A longer trial period would be beneficial for thorough evaluation and testing of its capabilities.
You can register for a demo.
14. Check Point Harmony Endpoint
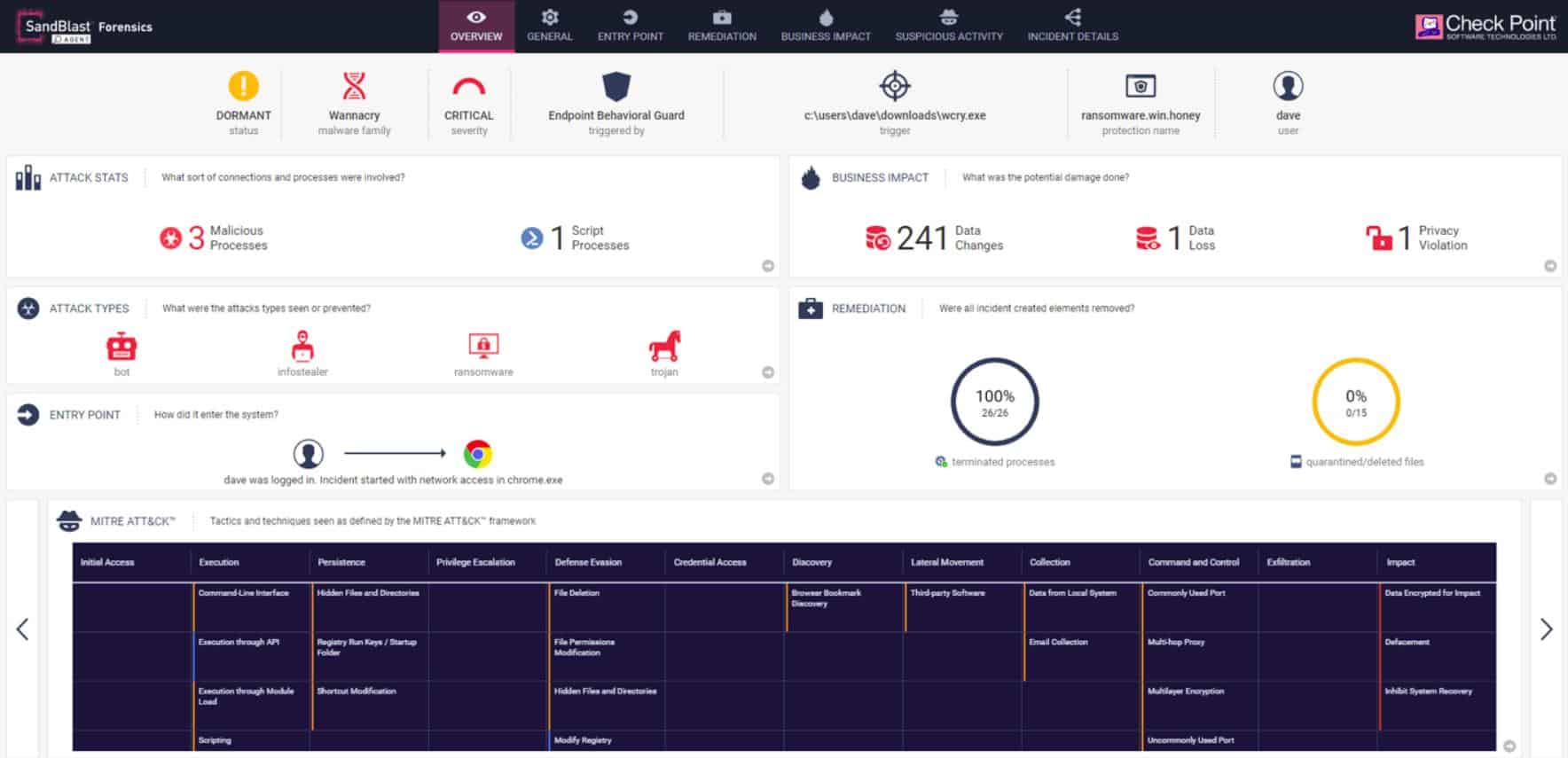
Harmony Endpoint is an endpoint protection (EPP) and endpoint detection and response (EDR) solution from Check Point. This software has AI procedures built into it and includes a range of defense strategies. The package is intended to address the risks to the computers of remote workers and the possibility that portable storage devices can spread viruses.
Key Features:
- AI-Driven Security: Utilizes artificial intelligence to establish baseline behaviors and detect anomalies.
- Credential Defense: Enhances security measures to protect user credentials from theft and misuse.
- Unified Threat Management: Coordinates defense mechanisms across the system for comprehensive protection.
Why do we recommend it?
Check Point Harmony Endpoint is recommended for its advanced AI-driven threat detection and broad spectrum of defense strategies, making it highly effective at protecting against a wide array of cyber threats. Its top performance in industry assessments and its comprehensive approach to endpoint security, including innovative features like anti-bot systems and forensic analysis, make it a leading choice for safeguarding IT environments.
NSS Labs encountered a threat catch rate of 99.12 percent from Harmony Endpoint during the 2020 edition of its Advanced Endpoint Protection industry assessment tests. That was the highest score of all the security software products that were examined in the comparison. Thus, the test awarded Harmony Endpoint its highest rating: AA.
Harmony Endpoint deploys a number of strategies to protect endpoints from attack. One of these is its anti-bot system, which blocks the protected computer from communicating with a command and control center. If the computer has been infected to become part of DDoS attacks, the anti-bot will prevent it from part of an attack.
The Harmony Endpoint system isolates files in a virtual sandbox for inspection so that they can’t operate on the computer until they have been fully assessed. The virus and threat detection module of Harmony Endpoint uses AI techniques to spot anomalous behavior and raise an alert. Remedial action can be automated so that Harmony Endpoint becomes a threat prevention system.
The Check Point ThreatCloud threat database provides constantly updated threat intelligence to the Harmony Endpoint EPP. When viruses are detected, Harmony Endpoint Forensics documents the attack, identifying its entry point and its actions. These reports give technicians indicators on the weak points of the endpoint, allowing for vulnerabilities to be closed off.
Anti-Ransomware features in the Harmony Endpoint package includes automatic file restoration in case its immunizer doesn’t prevent the threatened action from taking place. Other modules include Zero-Phishing, which prevents credential theft and fraud and also blocks access to suspicious sites.
Who is it recommended for?
Harmony Endpoint is suitable for businesses of all sizes that prioritize robust cybersecurity, especially those with remote workers or those utilizing portable storage devices which could introduce vulnerabilities. Its ability to scale, combined with a suite of features designed to protect against the latest cyber threats, makes it an ideal solution for organizations seeking to enhance their endpoint security posture in an increasingly complex digital landscape.
Pros:
- High Detection Accuracy: Achieved a 99.12% threat detection rate in NSS Labs tests, reflecting exceptional effectiveness.
- Bot Communication Blocker: Employs anti-bot technology to prevent compromised devices from participating in DDoS attacks.
- Automated Remediation: Features capabilities for immediate threat neutralization, minimizing the potential impact of attacks.
- Forensic Analysis: Offers detailed forensic insights into attacks, including points of entry and behavior, to inform security improvements.
- Multi-Faceted Ransomware Protection: Includes features for both preventing ransomware attacks and mitigating their effects should they occur.
Cons:
- Complex Configuration: The depth of features and customization options may require a significant investment of time to navigate and optimize.
Check Point offers a free trial of Harmony Endpoint .
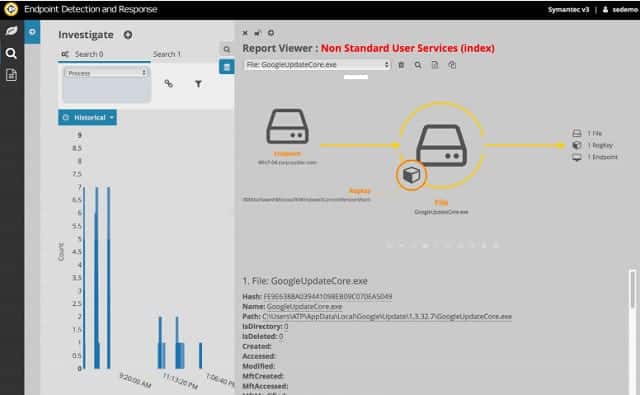
15. Symantec Endpoint Detection and Response
Symantec’s Endpoint Detection and Response employs AI methods to track down malicious activity – this is called “threat hunting.” The system is available as a software module, as an appliance, and as a cloud-based service. If you opt for the cloud version, you still have to install agent software on your site. This runs on Windows and Windows Server. The on-premises software runs on Windows, Windows Server, Mac OS, and Linux. Endpoint Protection and Response is an upgrade to the Symantec basic Endpoint Protection service.
Key Features:
- System-Wide Coordination: Implements a unified approach to defend against threats across all networked systems.
- Intelligent Baseline Monitoring: Utilizes artificial intelligence to recognize normal operations and detect deviations.
- Advanced Memory Inspection: Continually scans system memory for signs of malicious activity, offering another layer of protection.
Why do we recommend it?
Symantec Endpoint Detection and Response is recommended for its sophisticated AI-driven approach to threat hunting and its ability to perform deep memory scans. Its utilization of SIEM technology to consolidate information from across the network makes it highly effective at identifying threats early. The flexibility of deployment options ensures that it fits within any organizational infrastructure, whether cloud-based or on-premises.
The system implements SIEM procedures to check for worrying events written in log files. It also establishes a pattern of normal behavior on the device and raises an alert when processes on the computer deviate from this record. The threat hunter also continuously scans memory for malicious activity. It keeps a record of all activity patterns for long-term analysis. As well as raising alerts, the system can also trigger automated actions to shut down malicious processes as soon as they are spotted. You can get the Endpoint Detection and Response system on a free trial.
Who is it recommended for?
This solution is ideal for businesses looking for a forensic-level security approach that integrates seamlessly with existing network structures. Its suitability for both on-premise and cloud deployments makes it a versatile choice for organizations of all sizes, especially those requiring detailed documentation of security incidents and proactive threat mitigation strategies.
Pros:
- Forensic Analysis Capability: Employs a detailed approach to identifying, neutralizing, and documenting cybersecurity threats.
- Deployment Versatility: Available as both an on-premises solution and a cloud-based service, catering to diverse IT infrastructure needs.
- Comprehensive SIEM Integration: Leverages SIEM technology to analyze data across the network, enhancing threat detection accuracy.
Cons:
- Limited Visualization Tools: The platform would benefit from enhanced data visualization features to simplify threat analysis and reporting.
Related post: Symantec Endpoint Protection: Full Review & Rival Comparison
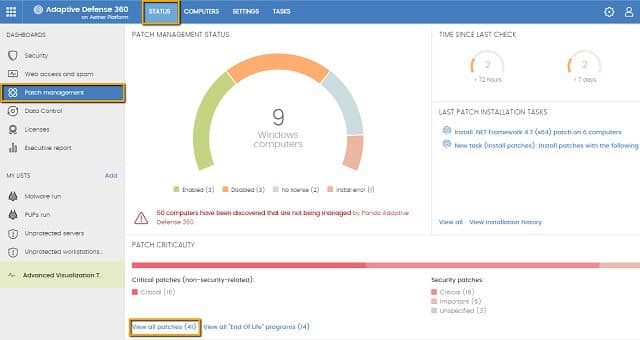
16. Panda Endpoint Protection
Endpoint Protection from Panda Security centralizes the protection of all of the computers connected to your network. That is, you can see all security events on all of the computers on your network on one single console, which is provided from the cloud. The protection operates on desktop computers, laptops, mobile devices, and servers; those protected endpoints can be running Windows, Windows Server, Mac OS, Linux, or Android. The company calls this “collective intelligence”.
Key Features:
- Centralized Network Security: Offers a unified platform for monitoring all network-connected devices, providing a comprehensive security overview.
- Cross-Platform Compatibility: Ensures compatibility with a wide range of operating systems, including Windows, macOS, Linux, and Android, for versatile endpoint protection.
- Peripheral Monitoring: Extends security measures to peripheral devices, enhancing overall network defense.
Why do we recommend it?
Panda Endpoint Protection is recommended for its effective use of collective intelligence to secure devices across a network. Its cloud-based, centralized console allows for easy monitoring and management of security across various platforms, making it an ideal solution for small to medium-sized businesses. The system’s ability to automatically assess and protect new devices and peripherals adds a layer of proactive security that is valuable for maintaining network integrity.
The system will check on the statuses of peripherals as well as the directly-connected devices. It establishes a policy baseline and then automatically drops processes that don’t conform to the profile.
Who is it recommended for?
This security solution is particularly suitable for small to medium-sized businesses looking for a straightforward, effective way to manage endpoint security across multiple platforms. Its ease of use and comprehensive protection make it a solid choice for organizations that require a reliable security system without the need for extensive customization or advanced features tailored to large enterprise environments.
Pros:
- Ideal for SMEs: Excellently suits the security needs of small to medium-sized enterprises with its centralized, cloud-based console.
- Versatile Endpoint Agents: Features agents that seamlessly work across different platforms, ensuring uniform protection for desktops, laptops, servers, and mobile devices.
- Proactive Device Assessment: Automatically evaluates new devices and peripherals for threats as soon as they connect to the network, maintaining security integrity.
Cons:
- Limited for Larger Enterprises: May not offer the depth of customization and advanced features required by larger organizations or complex networks.
17. CounterTack GoSecure ESL
GoSecure is the main brand of cybersecurity startup, CounterTack. ESL stands for Endpoint Security Lifestyle. This is a vulnerability monitor and it doesn’t include any antivirus modules. However, it will monitor any third-party AV system running on your network-attached endpoints.
Key Features:
- Comprehensive Asset Discovery: Automatically identifies all network-attached endpoints, creating a detailed inventory for management.
- Proactive Patch Management: Ensures that all software across endpoints is kept up-to-date, minimizing vulnerabilities.
- AV System Oversight: Monitors the performance and status of third-party antivirus solutions installed on the network.
- Configuration Management: Maintains optimal system settings across devices to fortify security postures.
- Vulnerability Assessment: Conducts thorough scans to identify and address potential security weaknesses before they can be exploited.
Why do we recommend it?
GoSecure ESL by CounterTack is recommended for its focus on maintaining a tight security posture through proactive vulnerability management and patching. Its capability to oversee third-party antivirus systems, combined with comprehensive asset discovery and vulnerability assessments, provides a solid foundation for safeguarding against threats. The user-friendly interface ensures that managing security doesn’t have to be complex, making it accessible for businesses with limited IT resources.
The premise of this tool is that you just need to keep your system tight with all software up-to-date in order to protect against malware. This service is delivered from the cloud.
Who is it recommended for?
This solution is particularly recommended for small to medium-sized businesses looking for a cloud-based security platform that emphasizes vulnerability management over direct threat removal. It’s ideal for organizations that already have antivirus solutions in place and are looking to enhance their security posture through improved asset management, patching strategies, and vulnerability assessments.
Pros:
- Intuitive Interface: Designed with simplicity and clarity in mind, facilitating ease of use and understanding.
- Vulnerability-Focused: Prioritizes the detection and resolution of security vulnerabilities over traditional antivirus functions.
- Suitable for SMEs: Its features and cloud-based delivery model make it an excellent choice for small to medium-sized businesses seeking to strengthen their security infrastructure.
Cons:
- Cloud-Only Deployment: Limits options for businesses looking for on-premises solutions.
- Lacks Built-In AV: While it can manage existing AV software, the lack of an integrated antivirus feature might require additional investments in third-party security products.
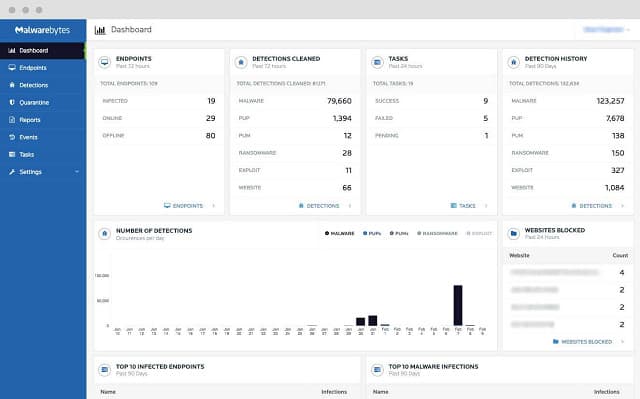
18. Malwarebytes Endpoint Protection
The Malwarebytes Endpoint Protection security system will protect endpoints running Windows and Mac OS. This is a cloud-based system, so it will need access to your network through your firewall.
Key Features:
- Cross-Platform Support: Designed to safeguard endpoints operating on both Windows and macOS, ensuring broad compatibility.
- Cloud-Based Management: Facilitates security management through a cloud platform, requiring minimal on-premise infrastructure.
- Behavioral Monitoring: Employs continuous surveillance of active processes and their behaviors to detect anomalies indicative of malicious activity.
- Comprehensive Threat Defense: Combines traditional antivirus threat databases with advanced detection techniques for holistic protection.
Why do we recommend it?
Malwarebytes Endpoint Protection is recommended for its innovative approach to endpoint security, which combines traditional and behavioral-based detection methods for a thorough defense mechanism. Its cloud-based management system simplifies the process of overseeing the security of Windows and macOS devices, making it an ideal choice for businesses looking for efficient and effective cybersecurity solutions.
The remote system communicates with an agent installed on one of your servers. The agent searches the computers on your system to read through lists of active processes, logging activity. It then keeps a check on any unusual activity that doesn’t conform to this pattern of normal behavior. The malware detection system also relies on the traditional AV method of a threat database that stores the characteristic behavior of known viruses.
Responses to detected threats are launched automatically. The protection extends to the blocking of botnet activity and the refusal to allow browsers to load infected web pages.
Who is it recommended for?
This solution is particularly suited for businesses of all sizes that require a reliable and comprehensive endpoint security system capable of protecting against a wide range of threats. Its cross-platform support ensures that organizations with a diverse array of devices can maintain a high level of security across their entire network.
Pros:
- Network-Wide Security Insights: Offers a panoramic view of threats and the health status of devices across the network, enabling informed security decisions.
- Advanced Malicious Activity Detection: Capable of identifying harmful processes and behaviors, providing an added layer of security.
- Botnet and Web Protection: Includes capabilities to block botnet communications and prevent access to malicious web content, enhancing online safety.
Cons:
- Extended Trial Desired: A more lengthy trial period would be beneficial for a thorough evaluation and testing of its comprehensive features.
Malwarebytes offers a free trial of Endpoint Protection.
19. Cylance Protect
Cylance Protect is an AI-based endpoint protection system that does away with the need for a threat database. You have a choice of getting the Cylance Protect software to install on your own server, or accessing it as a cloud-based service with an agent program installed on one of your sites.
Key Features:
- AI-Driven Protection: Utilizes artificial intelligence to proactively prevent malware installations and unauthorized activities without relying on traditional threat databases.
- Versatile Deployment Options: Available as both a cloud-based service and an on-premise solution, offering flexibility in implementation.
- Advanced Monitoring: Keeps a close eye on file operations and memory activities, effectively combating fileless malware.
- Immediate Threat Remediation: Employs rapid response measures to neutralize threats by blocking suspicious traffic, ejecting intruders, and terminating harmful processes.
Why do we recommend it?
Cylance Protect is recommended for its innovative use of AI technology to offer preemptive protection against a wide array of cybersecurity threats, including the ever-elusive fileless malware and zero-day attacks. Its ability to operate without a traditional threat database sets it apart, offering a forward-thinking approach to endpoint security that’s both efficient and effective.
The service monitors file operations on your computers, blocking the installation of malicious programs. It will also scan memory for unauthorized activity, which will block off the operations of fileless malware. All in all, the Cylance strategy is designed to prevent zero-day attacks by preventing the need for malware analysis and threat response distribution.
Threat remediation occurs immediately. This takes the form of blocking incoming traffic from a suspicious address, booting off intruders, and killing malicious processes.
Who is it recommended for?
This security solution is ideally suited for organizations of all sizes that prioritize advanced, AI-based threat detection and prevention. Its versatility in deployment options makes it a suitable choice for businesses seeking either cloud-based flexibility or on-premise control. The automated remediation capabilities and intuitive dashboards make it accessible for both technical and non-technical users, streamlining security operations and ensuring a high level of protection.
Pros:
- Cutting-Edge Threat Prevention: Leverages AI to consistently block emerging threats, providing robust protection against zero-day attacks.
- Deployment Flexibility: Accommodates varying IT environments with options for cloud-based or on-premise installation.
- Intuitive Management Interface: Features user-friendly dashboards that facilitate monitoring and management, suitable for individual users or Network Operations Centers.
- Automated Attack Mitigation: Supports automated responses to threats, enhancing operational efficiency and reducing the time to remediation.
Cons:
- Need for More User Guides: The platform would benefit from additional documentation to assist new users in navigating and maximizing its features.
Endpoint protection in context
As a business user, you will be managing many endpoints within your offices and also remote computers owned by telecommuting freelancers and home-based employees. An open network that includes remote and user-owned devices is vulnerable to greater risk than a contained office LAN.
Endpoint protection is certainly necessary. However, this shouldn’t be your only line of defense against malware and intruders. You should consider your IT infrastructure as a whole when implementing security measures and make sure that your network is protected by strong security as well as by introducing endpoint protection.
Endpoint Protection FAQs
What does endpoint protection mean?
Endpoint protection is a system that prevents cyber threats from activating on an endpoint. The threats can be malware or manual intrusion. Traditionally, an endpoint is considered to be a desktop workstation. However, the term also applies to laptops, smartphones, and tablets.
Is endpoint protection same as antivirus?
Endpoint protection is a wider task than antivirus. An antivirus system protects an endpoint against malicious software, which can get onto a computer in a range of formats. Endpoint protection covers malware detection and removal but it also deals with manual intrusion and even inappropriate use by authorized users.
Why do we need endpoint protection?
Endpoint protection is important because these devices can be used as gateways into the entire system. Endpoints are the devices that users access and so human negligence or gullibility can provide hackers with a way to coopt authorized users into compromising a system. This makes endpoints far more vulnerable than servers or network devices.









wher is the kaspersky endpoind security ??????