Password management is a crucial aspect of maintaining a secure and well-organized IT environment. In Active Directory (AD), ensuring that users adhere to password policies, such as regular password changes, is vital for minimizing security risks. One common administrative task is monitoring password expiration to prevent users from being locked out or, worse, relying on weak, outdated passwords.
For system administrators, knowing when passwords are set to expire can help proactively manage user accounts. This not only enhances security but also improves user experience by preventing unexpected disruptions. Active Directory stores password expiration information, but extracting and interpreting this data requires the right tools and techniques.
This guide will walk you through various methods to find password expiration details for AD users. Whether you prefer graphical tools like an Active Directory management package or command-line tools such as PowerShell, we’ll cover step-by-step instructions to suit your workflow. You’ll learn how to query individual accounts, generate reports for multiple users, and even automate the process for ongoing monitoring.
By the end of this guide, you’ll have the skills to efficiently manage password expiration in Active Directory, ensuring your organization stays secure and compliant. Let’s dive in and explore the best practices for managing this essential aspect of AD user accounts.
About Password Expiration in Active Directory
Before looking at how to extract password expiration dates from Active Directory, it is worth noting what that factor means. When the password expiration date is reached, the account isn’t blocked. Instead, the user is prompted to enter a new password.
The password expiration date enforces password rotation policies, so it is not a bad thing. Users will still access their accounts, but they will just have to reset their passwords. Therefore, don’t panic if you see that many accounts have a password expiration date coming up – there is nothing that you need to do about it. Just let the users get prompted for a new password.
Looking for password expiration dates
To get a list of AD user password expiration dates, open a Command Prompt window. You can do this in several ways. One is to press the Windows key and R together, entering cmd in the Run box that appears, and then hitting RETURN or pressing the OK button. You can also get the Command Prompt window by entering Command in the Start menu search field and selecting the Command Prompt from the results list.
You should use the net user utility to see the password expiration date for a user. The format of this command is:
NET USER
[username [password | *] [options]] [/DOMAIN]
username {password | *} /ADD [options] [/DOMAIN]
username [/DELETE] [/DOMAIN]
username [/TIMES:{times | ALL}]
username [/ACTIVE: {YES | NO}]
Here is an example run of this utility. In this case, the command fetches details about the user Test01 on the local domain.
The password expiration date is shown on the ninth line of the report on the user account and is labeled Password expires.
Use PowerShell to get a list of AD user account expiry dates
The net user just calls the details of one user account. To extract a list of all account expiry dates, you will need to use PowerShell. You need to be sure that you have the supporting PowerShell AD libraries available before running your search for user password expiry dates.
The Active Directory PowerShell Module is pre-installed on Windows Server. If you are running this search on Windows 10, you need to access the page about these PowerShell routines at Microsoft. You will also need to install the Remote Server Administration Tools for Windows 10.
Open a PowerShell window by pressing the Windows key and R together to get the Run box, entering powershell, and then hitting RETURN or clicking the OK button. Alternatively, you can enter powershell in the Start search field and selecting PowerShell from the results.
Get the password expiration date for one user with the PowerShell code:
Get-ADUser -Identity UserName -Properties msDS-UserPasswordExpiryTimeComputed).'msDS-UserPasswordExpiryTimeComputed'You would need to enter a user ID instead of the token UserName shown in the code above. You can format the output by piping the results through to a SELECT statement:
SELECT Name, {[datetime]::FromFileTime($_.”msDS-UserPasswordExpiryTimeComputed”)}
Giving a total command of:
Get-ADUser -Identity UserName -Properties msDS-UserPasswordExpiryTimeComputed).'msDS-UserPasswordExpiryTimeComputed' |
SELECT Name, {[datetime]::FromFileTime($_.”msDS-UserPasswordExpiryTimeComputed”)}An alteration to this command will give you all users registered within your Active Directory instance.
Get-ADUser -filter {Enabled -eq $True -and PasswordNeverExpires -eq $False} –Properties "DisplayName", "msDS-UserPasswordExpiryTimeComputed" |
Select-Object -Property "Displayname",@{Name="ExpiryDate";Expression={[datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed")}}This code will display the output to the screen. If you need the output to a file, you should just pipe the results of the code.
Utilities to get Active Directory user information
If you don’t want to create your code to get the expiration dates for AD users, you can install an Active Directory management tool instead. The password expiration date is one of the attributes that these utilities will give you.
Our methodology for selecting an Active Directory management tool
We reviewed the market for tools that will get you the user password expiration dated from AD and analyzed the options based on the following criteria:
- A system with a GUI interface that presents AD contents in an acceptable format
- A service that can show a range of user account attributes
- A manager that will show the user groups and user group membership from AD
- Nice to have an interface to update values in AD
- A monitoring system that warns of replication errors
- A free tool or a system that offers a free trial for a no-cost assessment
- A paid tool that provides value for money or a free tool that is worth installing
Given that Active Directory is only available for Windows systems, we looked for packages to access Windows or Windows Server. In addition, systems that can access the Azure AD service were also of interest.
Here is our list of the best tools to find password expiration for Active Directory users:
- ManageEngine ADSelfService Plus (FREE TRIAL) A user portal that implements a single sign-on environment through AD and allows users to reset their own passwords. Runs on Windows Server.
- Lepide Data Security Platform This cloud-based service offers a range of security enforcement tools, including the Password Manager, that is able to list and supervise password expiry dates for both on-site and cloud-located assets.
- ManageEngine ADManager Plus this tool acts as a front-end for Active Directory and enables you to plan and organize user account features. Available in free and paid editions and offered for download on Windows or as a cloud service.
You can read more about each of these options in the following sections.
1. ManageEngine ADSelfService Plus (FREE TRIAL)
ManageEngine ADSelfService Plus is a user portal that enables administrators to present a menu of available services to each user. The system interacts with Active Directory to discover the systems to which that user has access and then generates a page containing access to them. Once the user has authenticated to enter the portal page, all access logins are rippled through, creating a single sign-on environment.
Key Features:
- User portal
- Self-service password reset
- Single sign-on
- Create a menu of authorized applications
Why do we recommend it?
ManageEngine ADSelfService Plus is an interesting option for businesses with a large user community when dealing with password management. Rather than leaving the technical support team to handle all password-related issues, this tool lets the users access their own AD record and update it. So, password expiration ceases to be your problem.
The portal enables the implementation of 2FA strategies and it also presents the user with an option to reset a password. The portal can be accessed through a Web delivery system or a mobile app, making systems available through multiple devices. This creates a flexible cross-device environment for the modern roaming work schedule.
Who is it recommended for?
This is a good tool for mid-sized and large organizations. Small businesses won’t need such a service because the few user accounts that such businesses have are easy to manage. According to Garner, up to 40 percent of Help Desk calls relate to password issues, so the ManageEngine system is a great cost saver.
Pros:
- Universally available access portal
- 2FA possible
- User password reset function
- Single sign-on
Cons:
- Doesn’t handle LDAP
ManageEngine ADSelfService Plus is an on-premises package that runs on Windows Server. The system can be added to a cloud account through AWS Marketplace or Azure Marketplace. There are three editions of the systems: Free, Standard, and Professional. The Free edition is limited to managing 50 users. You can get a 30-day free trial of the Professional edition of ADSelfService Plus.
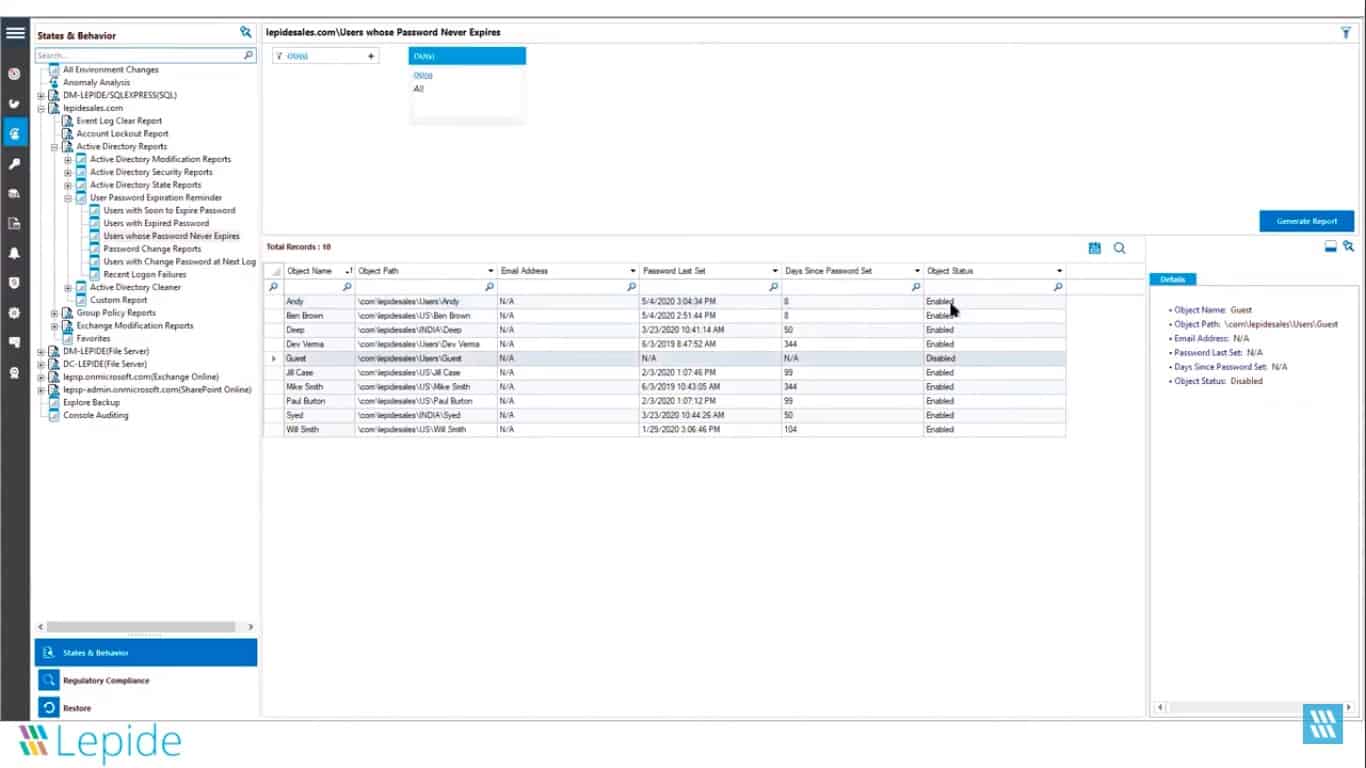
2. Lepide Data Security Platform
Lepide Data Security Platform is a SaaS system that offers several security protection services and includes a Password Manager. This service can explore data in Active Directory and display single factors. One of those focuses is on password expiration dates.
Key Features:
- Password manager
- Expiration data analysis
- SaaS package
Why do we recommend it?
The Lepide Data Security Platform offers a range of system scanning and compliance management tools. The package includes the Password Management system. This service ensures that passwords have expiration dates on them and it will send out reminders to users as the expiry date approaches. Administrators get a daily summary.
The issue of password expiration dates in AD is not just one of knowing when users will be told to reset their passwords. For example, you might have taken over a system from an administrator who prioritized ease of management over security. In such a case, many, or even all, accounts in AD may have passwords that never expire. An effective way to implement that is to set expiry dates so far into the future that they never become an issue. Lepide helps you identify this error, and you can use the interface to adjust expiry dates so that they follow a meaningful password rotation policy.
Lepide Data Security Platform is resident in the cloud, and it can cover applications that are based in the cloud and services that you have operating on your site. Password management activity in Lepide Data Security Platform extends to databases and productivity suites and general system access.
Who is it recommended for?
The Lepide system is suitable for mid-sized businesses and large organizations. It identifies open-ended passwords and ensures that administrators put expiry dates on all of them. It also lets you set up a series of advisory emails to users, so they don’t get a bland system-generated message.
Pros:
- Covers access rights for a range of applications
- Includes analyzers for password expiration dates
- Offers a range of tools to manage user accounts
Cons:
- It would be nice to have a longer free trial period.
You can access a 15-day free trial of Lepide Data Security Platform to assess its password management tools for yourself.
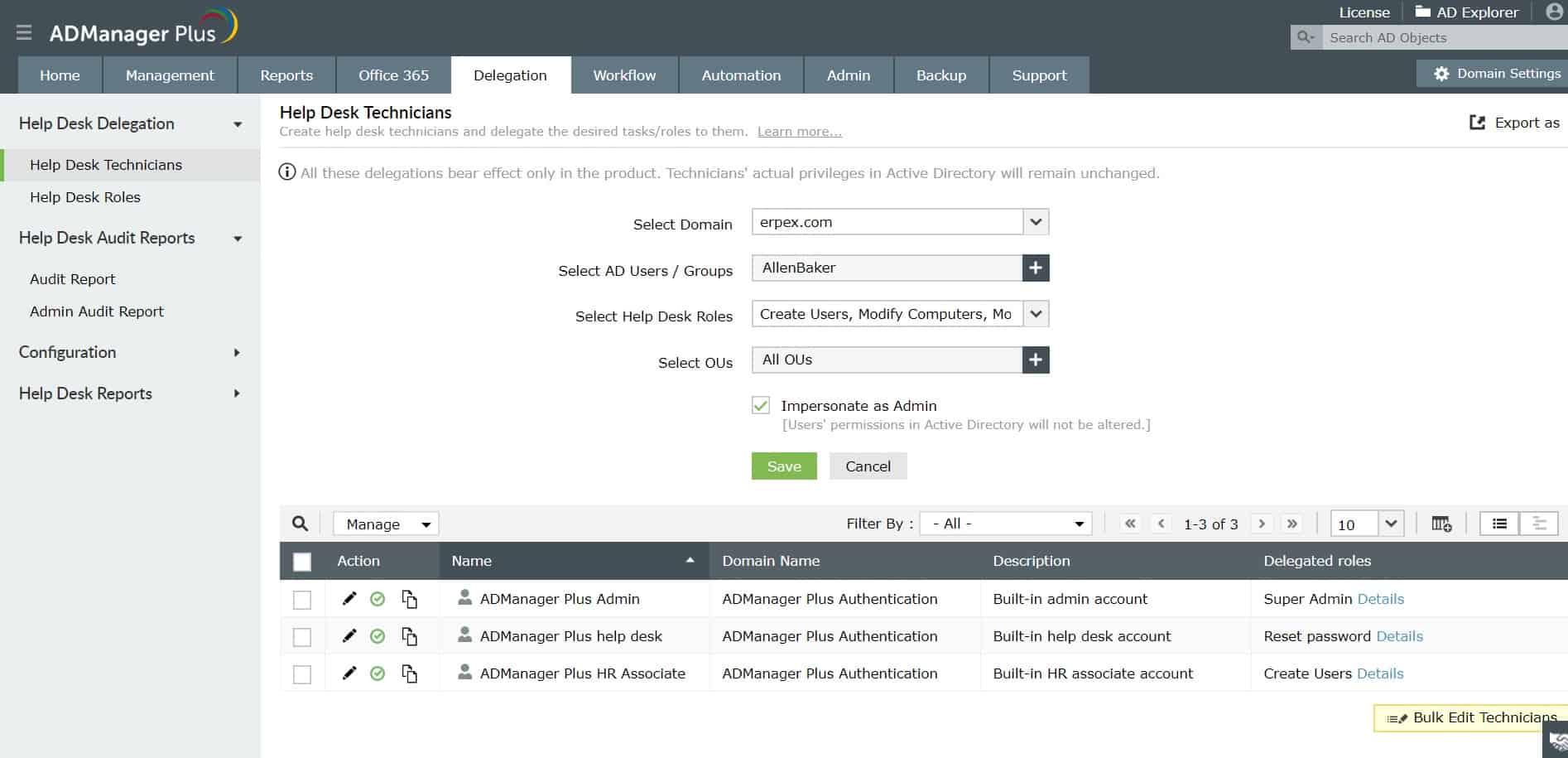
3. ManageEngine ADManager Plus
ManageEngine ADManager Plus gives you extra user account management and reporting functions that you just don’t get from the regular AD interface. This is an essential tool for those who need to comply with data privacy standards because it will audit your user accounts and generate all of the reports you need for compliance.
Key Features:
- A pack of 6 AD tools
- AD frontend
- Password management
Why do we recommend it?
ManageEngine ADManager Plus is a similar system to SolarWinds Access Rights Manager because it offers a front end for multiple domain controllers and can cross platforms and applications as long as the access rights system is Active Directory. The tool will manage replication to ensure that all domain controllers are properly coordinated.
The tool unifies the management of account information for a typical Microsoft environment because it can control AD instances for Microsoft 365, SharePoint, Microsoft Exchange, and general system access domains. In addition, the tool includes account analysis functions that will spot abandoned accounts and show you password expiry dates.
This system offers a rules base for account creation, automatically imposing the access controls needed by any data privacy standard. You can set up a standard control policy and then roll that out to all of your domains and ensure that those standards create all future user accounts.
ManageEngine ADManager Plus installs on Windows and Windows Server, and it is also possible to add it as a service to your Azure or AWS account.
Who is it recommended for?
There is a Free edition of ADManager Plus, which is limited to managing 100 domain objects – that’s big enough for many small businesses. The paid system is available in two editions. This tool is particularly useful to mid-sized and large businesses. ManageEngine also includes ADManager Plus in the bundle package called AD360.
Pros:
- Complete control over all AD instances
- Standards compliance reporting
- On-site and cloud deployment options
Cons:
- It doesn’t cover any other access rights management systems apart from AD.
There is a Free version of the tool, which is limited to managing 100 objects in AD. The paid version is offered in two editions, which are available on a 30-day free trial.
Active Directory password management FAQs
Where is password expiration set in Active Directory?
To find the password expiration date for a user account in Active Directory, open Active Directory Users and Computers and enable Advanced options. Locate the user account and access properties -> Attribute Editor -> Attributes -> pwdLastSet. This will be a date and time value. To instantly expire the account, highlight the pwdLastSet field and click Edit. Enter 0 for the value and press OK.
Can you see user passwords in Active Directory?
It is not possible to see the password for a user account in the Active Directory Users and Computers system, or anywhere else. Even if you have domain admin rights.
What is PwdLastSet attribute Active Directory?
PwdLastSet gives the date and time that the user account password was last changed. You can see this in the Properties of the user account in Active Directory Users and Computers uber the Attribute Editor tab.