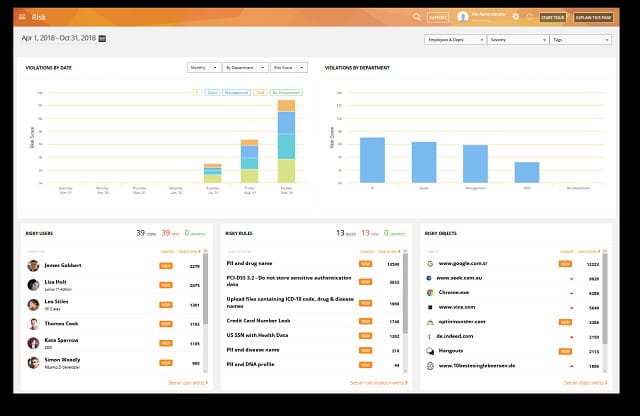
With a focus on behavioral analytics and contextual awareness, Forcepoint DLP offers a reliable solution for mitigating the risks associated with data leaks and loss, while helping organizations comply with industry regulations such as GDPR, HIPAA, and PCI DSS.
Forcepoint is a global cybersecurity company that specializes in data protection and threat intelligence. Headquartered in Austin, Texas, Forcepoint was founded in 1994 as Websense, a company initially focused on web filtering and security solutions. Over the years, the company expanded its portfolio, including cybersecurity products such as endpoint protection, web security, and email security.
In 2015, Websense rebranded as Forcepoint and continued to evolve by integrating advanced security features like behavioral analytics and data loss prevention (DLP). The company was acquired by Raytheon Technologies in 2015, and this acquisition bolstered Forcepoint’s capabilities in securing critical infrastructure for government and enterprise clients. Raytheon sold Forcepoint LLC to Francisco Partners, a private equity firm, since January 2021.
Forcepoint’s Data Loss Prevention (DLP) solution is a key offering in its cybersecurity suite, designed to protect sensitive data from being leaked, stolen, or compromised within an organization. The DLP prevents data breaches by monitoring and controlling data movement. It monitors across channels: email, cloud services, and external storage devices. Advanced machine learning algorithms detect abnormal behavior and policy violations in real-time, ensuring that organizations can prevent both insider and outsider threats.
Today, Forcepoint is recognized as one of the leading providers of cloud security and data protection solutions. Forcepoint DLP is well-suited for organizations with complex, data-heavy environments, providing a flexible, scalable solution to enforce data protection policies across diverse platforms and networks.
What does Forcepoint DLP do?
The services of Forcepoint DLP fall into four categories:
- Data Protection Fundamentals
- Data Protection Unification
- Behavioral Awareness
- Automation & Ecosystem
We will look at the components of these categories.
Data Protection Fundamentals
This category lists the core strategies of the Forcepoint DLP approach.
- Drip DLP This technique tracks all data outflows, recording each bit of data that leaves. It might be permissible and necessary to let individual records in a collection pass out of the system. However, this also allows data thieves to steal a large amount of data over time. The Crip DLP system raises an alert if a specified percentage of a collection has been transferred out by stealth piece by piece.
- Cloud protection expresses the service’s ability to watch over cloud data stores with the same methods applied to on-premises storage locations.
- Native remediation This service can implement orchestration to both detect and block data exfiltration. This means changing firewall rules to block activity from a specific IP address, suspending use accounts in an access rights manager, or using the operating system to kill malicious processes.
- Data discovery across all environments The discovery service is automatic and continuous. It explores the enrolled systems for data storage locations.
- Structured and unstructured data fingerprinting This tracks related fields that individually do not represent a security risk but constitute a serious disclosure if exfiltrated together. The movement of these related fields is then closely tracked.
- Optical Character Recognition (OCR) The Forcepoint system can scan document images for critical pieces of information and index those pieces of data into its data management strategy.
- Cloud app protection Let this automated service scan for cloud-based apps accessed by your users. Make sure only authorized apps are in use and that they are secure.
- Alert prioritization With this system, you can avoid getting bogged down with minor issues while more significant problems lie at the back of the queue. Severity ranking draws attention to the critical issues.
Data Protection Unification
Forcepoint DLP isn’t restricted to monitoring one location.
- On-prem, cloud, and hybrid deployment Cover multiple sites and cloud platforms with one account.
- Uniform policy enforcement Set a security policy for different categories of data and apply it across all platforms and locations.
- Integration across web, email, network, endpoint, and cloud All communication channels are monitored for data movements.
- Converged network and endpoint protection Forcepoint DLP involves both network and host monitoring.
- Single console control across all environments Get live, aggregated activity feedback on the dashboard’s home screen and drill down to individual locations and events.
- Off-network policy enforcement Endpoint agents continue protection even when the device is unreachable over the network.
Behavioral Awareness
- Native, behavioral analytics A user and entity behavior analytics (UEBA) module establishes a baseline of regular activity by profiling the behavior of each user account and the normal processes on each device.
- Risk-adaptive protection This is implemented by Dynamic Data Protection, which was launched as a separate module but is not part of Forcepoint DLP. It pre-sets the detection of your DLP system by your security policy goals.
- Risk-based policy enforcement Closely related to the risk adaptive protection system, this service implements remediation according to your risk-related security policy.
Automation & Ecosystem
- Automated policy enforcement The dashboard includes a policy setting, which you can create from scratch or set up by selecting a pre-set format from a template library.
- Compatibility with classifications vendors You can use a third-party data categorization tool with this system.
- Database support flexibility Protects data stored in databases.
Forcepoint DLP deployment options
Forcepoint DLP is a cloud-based SaaS service, which requires an agent service to be installed on the site or platform that the system is protecting. It is also available as an appliance, and it can be set up as a virtual appliance on a cloud platform, such as Azure or AWS, or your site, running over a VM.
You can access Forcepoint DLP on a 30-day free trial.
Forcepoint DLP Pros and Cons
Pros:
- A data discovery system that locates PII, PHI, and intellectual property
- A cross-platform system
- Protects data on cloud platforms as well as on sites
- Available as a SaaS platform, as a physical appliance, or as a virtual appliance
- Offers pre-set policies for data privacy standards compliance
Cons:
- Relies on third-party tools for data categorization
Alternatives to Forcepoint DLP
Forcepoint DLP is an excellent data protection system, and the flexibility of its deployment options make it even more attractive. However, this is not the only data loss prevention system available, and it is advisable to check out a few options before committing to one particular service.
Our methodology for selecting a Forcepoint DLP alternative
We reviewed the market for data loss prevention systems and analyzed the options based on the following criteria:
- Coverage for multiple sites
- The ability to amalgamate monitoring for on-site and cloud hybrid systems
- Data discovery and classification service for sensitive data
- Options for a hosted SaaS service or a software package for installation
- Built-in data privacy standards compliance
- A free assessment period in the form of a free trial or a demo system
- Value for money, represented by a good deal for the functions offered
With these selection criteria, we select a good range of options.
Here is our list of the best alternatives to Forcepoint DLP:
- ManageEngine Endpoint DLP Plus EDITOR’S CHOICE This on-premises system will search through every endpoint on your site for sensitive data, classify it, and protect the files that contain it. The service can also be implemented to protect data on multiple sites from one server. This system runs on Windows Server and you can get it on a 30-day free trial.
- Symantec Data Loss Prevention An on-premises package includes data discovery and classification for sensitive data and a complete protection system. Available for installation on Windows Server, Linux, or over a VM.
- Endpoint Protector A cloud-based data loss prevention system with endpoint agents for service continuity. This system monitors and controls exfiltration points through modules that run on Windows, macOS, and Linux.
- Digital Guardian DLP This data loss prevention platform monitors endpoints and networks to control and block data movements. This is a cloud-based system with endpoint agents for Windows, macOS, and Linux.
- Teramind DLP A cloud-based data loss prevention system that includes user and entity behavior analytics and insider threat assessments.
You can read more about each of these options in the following sections.
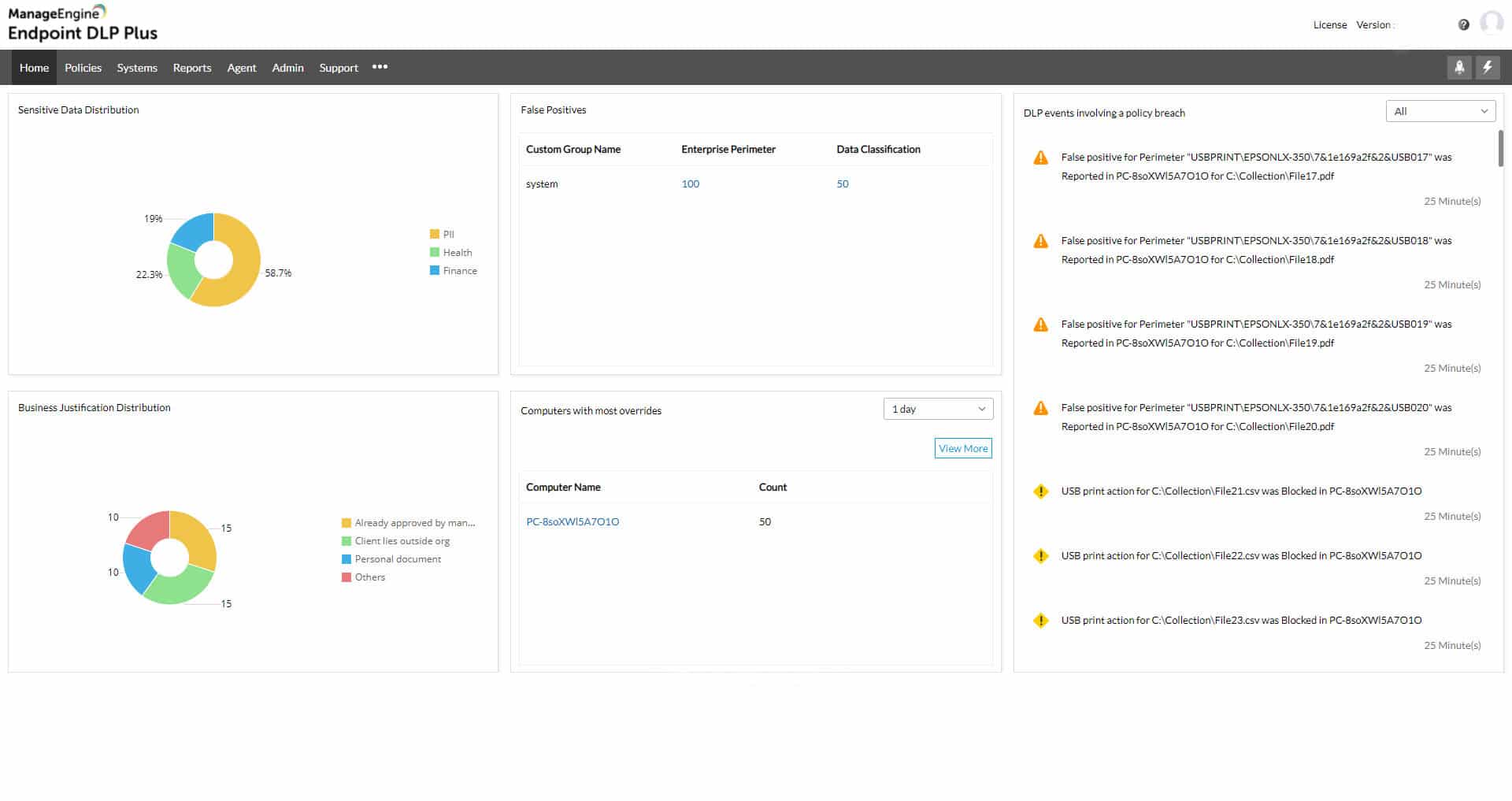
1. ManageEngine Endpoint DLP Plus (FREE TRIAL)
ManageEngine Endpoint DLP Plus operates controls over access to sensitive data at rest, in use, and in motion. This data protection service is set up by applying a template from a library in the Endpoint DLP Plus configuration screens and that modifies its detection and protection routines to match the specifications of PCI DSS, HIPAA, GDPR, and other data protection standards.
Key Features:
- Sensitive data discovery
- Data classification
- File movement controls
- User activity tracking
- Free for 25 computers
Why do we recommend it?
ManageEngine Endpoint DLP Plus identifies sensitive data and categorizes it. The system controls the software that can access the files containing that data. So, ransomware is completely blocked because it is never going to get on the list of authorized software. The next level of protection defines which users can access those files with that approved software.
A key element in the Endpoint DLP Plus system is its data discovery process. This periodically scans all of the endpoints on your system for the presence of the defined sensitive data. Each encountered instance is categorized and the file that contains it is then protected. Data protection takes the form of containerization, which forms a wrapper around the file, blocking all direct access.
When setting up the Endpoint DLP Plus service, you specify a number of software packages that will be designated as trusted applications. The DLP then allows those applications to access files that contain sensitive data. It is assumed that you will only grant the trusted status to systems that have their own tight access controls. While in the application, user access to sensitive data is logged, enabling any destruction or theft to be attributed to a specific account. Data access events that seem inappropriate trigger user activity tracking from that account. This is an insider threat detection system that can also identify account takeover.
Sensitive data monitoring also applies to data movements. This branch of the DLP service allows and logs or blocks the movement of protected files onto USB sticks. It also controls what data can be sent to a printer, attached to an email, or uploaded to a cloud platform.
Who is it recommended for?
As with Forcepoint, this package is aimed at businesses that manage sensitive data. The system also includes a user activity tracker that identifies suspicious activity that could represent an insider threat of an account takeover. Small businesses will be drawn to the Free edition, which will protect 25 endpoints.
Pros:
- Sensitive data discovery and classification
- File containerization to block direct access
- Files locked with access allowed to trusted applications
- Association of trusted applications to facilitate access to controlled data
- Data movement controls
Cons:
- Not a SaaS package
Endpoint DLP Plus installs on Windows Server. There is a Free edition available for small businesses that will monitor up to 25 computers. The paid edition, called Professional is available for a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Endpoint DLP Plus is our top pick for a Forcepoint DLP alternative because it is easy to adapt to the requirements of specific data privacy standards, such as PCI DSS, HIPAA, and GDPR. This system discovers and categorizes sensitive data, identifying the files that need to be protected. Access to those files is only permitted through trusted applications and file movements are logged and controlled. Endpoint DLP Plus can be used to monitor sensitive data on multiple sites from one console.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/endpoint-dlp/download.html
OS: Windows Server
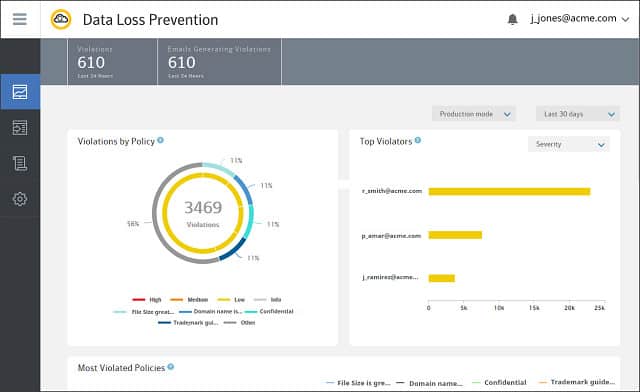
2. Symantec Data Loss Prevention
Symantec Data Loss Prevention monitors endpoints, networks, storage devices, and cloud platforms. In addition, this system includes a discovery and classification service for sensitive data. This is an on-premises package, but it can amalgamate data protection on several sites and cloud platforms.
Key Features:
- Data discovery and classification
- Data on-premises and on the cloud
- Email scanning
- Compliance management
Why do we recommend it?
Symantec Data Loss Prevention has been through a few changes of ownership in recent years and is now a property of Broadcom. This tool provides discovery and classification for sensitive data and it is able to manage data on cloud platforms as well as on servers on the buyer’s site.
The service watches over file servers and databases and monitors file transfer activity, USB ports, printers, faxes, emails, and Web activity to block data exfiltration. It will also monitor cloud syncing services, such as OneDrive or Dropbox.
This system implements data control according to a specified security policy. These can be implemented by setting rules manually or by selecting a format from a library. The Symantec system offers templates for all of the significant data privacy standards. The service can also encrypt files and control access through decrypting user accounts. In these cases, all access is logged.
The Symantec Data Loss Prevention package is available for Windows, Windows Server, macOS, and Linux installation.
Who is it recommended for?
This package is aimed at mid-sized and large organizations that manage several sites and cloud accounts from one central IT management office. The tool is able to set a corporate data protection policy and then apply that everywhere. The system is also strong on compliance management.
Pros:
- Discovery and classification for sensitive data
- Monitors data movements on-site and cloud platforms
- Includes control of cloud services, such as Gmail and Office 365
Cons:
- No free trial
- Needs updating for Windows 10
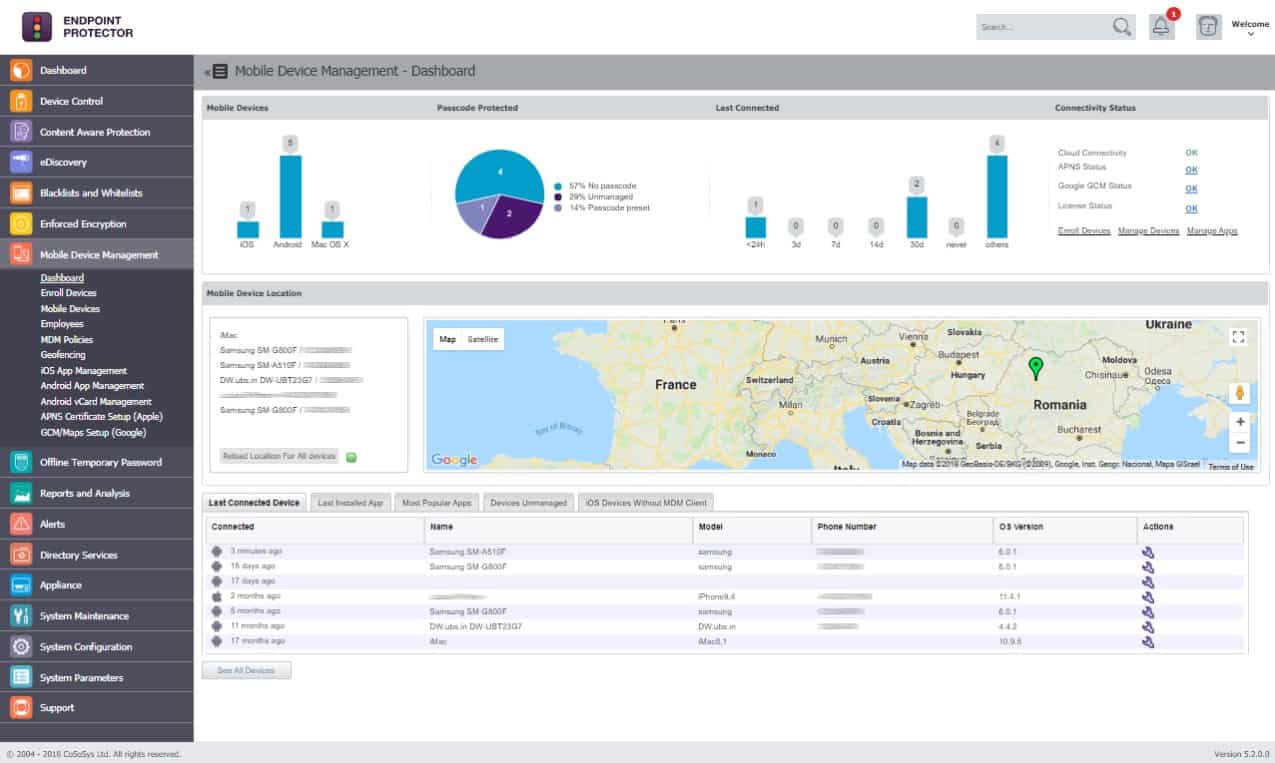
3. Endpoint Protector
Endpoint Protector operates from the cloud but is implemented on endpoints. That means this is a split system with the server and its dashboard offered as a SaaS platform and endpoint agents controlled by that central system. Thus, each endpoint is fully monitored and controlled individually, while detection and response are coordinated throughout the enterprise.
Key Features:
- Allowlisting
- Access rights management
- Device controls
Why do we recommend it?
Endpoint Protector has a very effective way to block malware – it blocks all software from running and then allows only those packages registered on an approved list to activate. That protects your data from ransomware and other automated attacks. A three-level access rights system that only allows specified users to access data through an approved software package enhances data protection.
The server performs an audit on your access rights management system and facilitates your security policy choice. The system then sends instructions to endpoints to discover sensitive data and classify it. The security policies are implemented through the application of specific access rights to particular data locations. For example, endpoint Protector will apply encryption to files to control access to them.
This data loss prevention service performs user and entity behavior analytics (UEBA) to establish standard activity patterns per user account and device. It raises an alert if activity deviates from this standard. The service also controls data movement onto USB memory sticks, printers, and through emails and file transfers.
Endpoint Protector is a good choice for a Forcepoint DLP alternative because it can consolidate data protection for multiple sites and cloud platforms. The wide range of deployment options for this DLP system matches those offered by Forcepoint. In addition, the data classification system of Endpoint Protector is fully integrated into its data discovery tool and is constantly active.
Who is it recommended for?
This tool is suitable for use by any business, not just those that manage sensitive data. The protection strategy is very easy to understand and manage because it blocks everything and everyone by default. So, there is no danger that data will get stolen or damaged due to an administrative oversight.
Pros:
- Includes a discovery and classification service for sensitive data
- Encrypts files to control access
- Scans access rights management systems for weaknesses
- Constantly monitor endpoint, network, and cloud activity
- Controls data movements on printers, emails, and USB ports
Cons:
- Could include a full SIEM
You can choose to subscribe to the hosted SaaS system of Endpoint Protector or activate it as a service on AWS, Google Cloud Platform, or Azure for a fee. It is also possible to get the software and run it on our server as a virtual appliance. The endpoint agents are available for Windows, macOS, and Linux. Access a demo to assess the service.
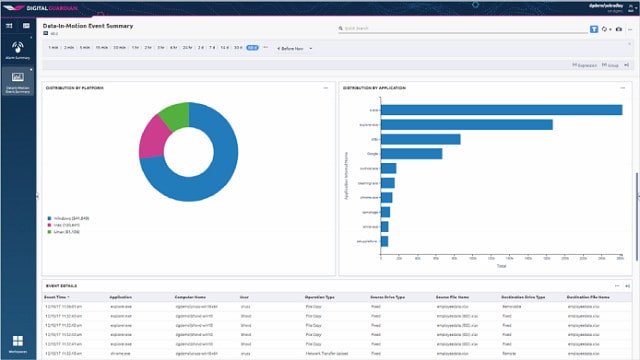
4. Digital Guardian DLP
Digital Guardian DLP is a cloud-based service that uses device agents to collect data and implement data controls. The endpoint systems can also operate independently should the device get disconnected from the network. This service also scans networks and internet transactions.
Key Features:
- Integrates with Active Directory
- Data movement tracking
- Windows, macOS, and Linux
Why do we recommend it?
Fortra’s Digital Guardian DLP package acts as an orchestration system. The package provides endpoint agents and a data collection tool for reporting. The consolidated activity records that the tool generates are forwarded to external threat detection systems, such as SIEMs. The tool can then channel remediation instructions back to the endpoints.
The service will analyze your access rights management system and recommend a better permissions structure. Next, you create security policies that dictate how sensitivity ratings should be controlled for each data type. These policies can be set in one go by applying a template from a library that caters to a specific data privacy standard.
The service sweeps devices and services, looking for data locations. It then classifies each data item by a sensitivity grade. This service protects PII and intellectual property.
The endpoint agents control data exfiltration points, such as USB ports, printers, emails, and file transfer systems. This service doesn’t block all data movements; it controls who can perform those tasks for specific data types.
This service is a threat hunter as well. The endpoint agents, available for Windows, macOS, and Linux, constantly upload logs and activity reports to the central server for threat-hunting analysis. Open a demo account to assess this package.
Who is it recommended for?
This system is implemented as a network device working with agents installed on all endpoints. The tool relies on the presence of third-party tools for threat detection, so this system is suitable for businesses that already have a central SIEM but need a mediator between it and all endpoints.
Pros:
- Includes threat detection as well as data protection
- Controls file access permissions
- Improves the permissions structure
Cons:
- The company doesn’t publish a pricelist
5. Teramind DLP
Teramind DLP is a hosted SaaS platform with onsite modules for data gathering and direct system controls. There are customized versions available for a specific industry. In addition, each account can be modified by using security policies to suit one of the data privacy standards that are prevalent today. There are policy templates available GDPR, HIPAA, ISO 27001, and PCI DSS.
Key Features:
- Employee work pattern analysis
- Identifies data in images
- Compliance with GDPR, HIPAA, and PCI DSS
Why do we recommend it?
The Teramind DLP system focuses on insider threats. It identifies the regular usage of data by each employee through behavior analysis. Sudden changes in activity will indicate a threat, such as an employee who has become bitter or has been manipulated by impersonators. These events could also indicate an account takeover event. The package has routines for checking on the activities of remote workers.
The service scans your enrolled networks for instances of data storage. When it finds data, the scanner classifies each example according to a sensitivity ranking. This scan repeats continuously so that the service will cover all new data instances. In addition, the Teramind DLP system can scan images of documents and identify data in them by using OCR.
Teramind DLP applies a typical intrusion detection system to its data loss prevention strategy; this identifies intruders and insider threats and controls access to data. The system also provides a risk assessment service. It provides a data analyzer that tells you where the largest sensitive data stores are and which user accounts access them with the most significant frequency.
Teramind DLP is available for a 14-day free trial.
Who is it recommended for?
Teramind assumes that its customers already have extensive checks for intrusion defense. However, the most likely channel that outsiders use to get into a system is by capturing user accounts. You will also need a system to provide system-wide activity scanning, such as a SIEM.
Pros:
- Performs threat detection as well as data protection
- Includes a risk assessor
- Automatically adjusts its process to meet data privacy standards
Cons:
- Can generate a lot of analysis data