Protecting sensitive data and preventing unauthorized access to critical systems is paramount for businesses. One of the most vulnerable entry points for cyber threats is often through physical devices such as USB drives. These portable storage devices can carry malware, facilitate data theft, or introduce viruses into secure environments. As a result, organizations are adopting endpoint security solutions to manage and secure USB ports and devices, preventing potential breaches and ensuring data integrity.
Our comparison of GiliSoft USB Lock and Endpoint Protector offers a detailed look at two popular software solutions designed to safeguard against USB-related security risks. Both tools provide organizations with powerful features to control and manage USB device usage, but they do so in different ways, each offering unique advantages depending on a business’s specific needs.
GiliSoft USB Lock is a software solution focused on restricting USB ports, blocking unauthorized USB device access, and preventing data leaks. It allows administrators to set policies that control which devices can connect to a computer or network, offering customizable access levels based on user roles or device types. GiliSoft also features additional options such as restricting the use of CD/DVD drives and other peripherals, ensuring that users are limited to only approved devices.
On the other hand, Endpoint Protector provides a more comprehensive suite of tools for endpoint security, with a strong emphasis on data loss prevention (DLP). It supports a wider array of devices beyond USB drives, including mobile phones, external hard drives, and network shares. Endpoint Protector not only restricts access to these devices but also tracks and monitors device activity, providing organizations with real-time insights into potential threats.
In this guide, we explore the strengths and weaknesses of both solutions, helping businesses choose the right tool for their USB and endpoint security needs.
The need for USB locking software
Today, a USB or flash drive is a marvel of technology that we take for granted. Not too long ago, and before everyone had access to gigabytes and terabytes of storage capacity, data was stored on rewritable CDs and DVDs when portability was required. Needless to say, they were cumbersome, fragile, and very limited in storage capabilities.
But, although the USB drive made life easier, it came with its drawbacks: it was soon accessible to everyone – including hackers and malicious users, it became a medium of choice for infectious code for exploitation or stealing of data, and the device of choice for employees stealing or leaking data.
This weak security point created the need for software solutions like Gilisoft USB Lock and Endpoint Protector.
Gilisoft USB Lock Product highlights
Gilisoft USB Lock is a data leak prevention (DLP) tool that stops the unauthorized outflow of confidential data by blocking the copying of it to storage devices like USB drives, phones (Android or iOS), optical disks (CDs or DVDs), external drives or any other portable data storage device.
Once installed, USB Lock can be configured to block all such drives and devices that do not belong to the organization. USB Lock can also stop the hacking or leaking of data from shared folders or drives when configured correctly.
Gilisoft is also a command-line application to make it easier to deploy or integrate into enterprise environments.
Key Information
- Gilisoft USB disables reading from and writing to USB drives, SD drives, and non-system drive partitions. Of course, administrators can create whitelists to allow specifically approved devices – the tool will then block all devices except those on the whitelist.
- It can also restrict read/write access to removable media devices like DVDs, CDs, and SD card readers. It also can be used to disable access or connection to phones, printers, modems, COM LPT ports, infrared, blue-tooth, 1394 ports.
- It can also serve as a proxy to block access to prohibited websites. For example, organizations can prevent their users from accessing sites they deem are unsafe or those that can be used to store data (Box, Dropbox, Google Drive, Microsoft One Drive, etc.) or for any other reason. When users try to access such pages, they are forwarded to a blank page – or one with a custom message indicating it is prohibited to access the site – and not the intended site itself.
- This tool can protect itself – first, no one can uninstall it without the administrator’s password. Second, should they try to do so, an alert is triggered after five failed attempts, and an email is sent to predefined email addresses while the errant account is temporarily banned.
Endpoint Protector Product highlights
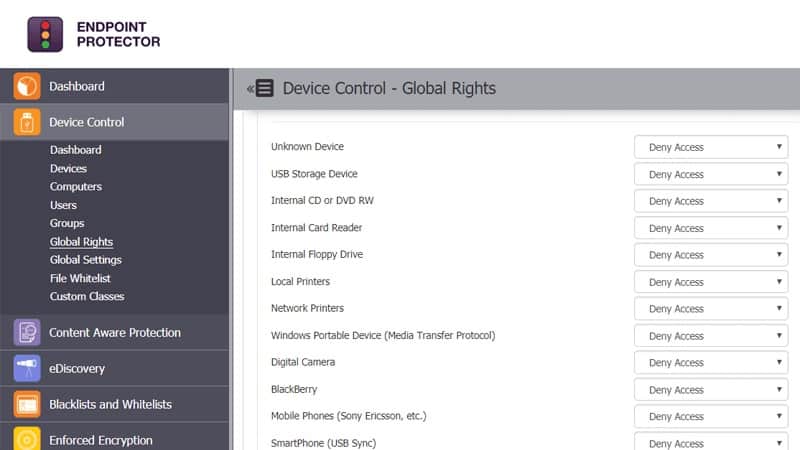
Endpoint Protector offers USB and peripheral port control; it can lock them down or be used to monitor and manage connected devices. It can also be used for granular control based on vendor IDs, product IDs, serial numbers, and other unique identifiers.
Apart from the devices mentioned above, the Endpoint DLP Suite helps to lock USB ports, make DVD and CD burners read-only. In addition, it can block prohibited websites, prevent particular programs from running, and be used to disable more devices.
It also offers enforced encryption and automatic USB encryption capabilities to encrypt, manage, and secure USB storage devices by safeguarding data as it transits to and from them. The configuration is easy to set, efficient, and password-protected.
Endpoint Protector scans data at rest to discover, encrypt, and delete sensitive data. This is further enhanced with detailed content and context inspection that can be done through manual or automatic scans.
Key Information
- Endpoint Protector is easy to install and use – remote deployment takes minutes, and management is a breeze; once done, it is ready to encrypt, manage, and secure USB storage devices by safeguarding data in transit.
- It forces users only to use authorized USB or other storage devices when they transfer confidential data; it can also force data encryption as it is stored on and retrieved from portable and USB storage devices. Thanks to this, password-protected and encrypted area ensures data remains safe even if the storage device is lost or stolen.
- Administrators get complete control of all the USB ports and connected storage devices on their network – they can uniquely identify all USB-connected devices, block unauthorized device use or enforce data encryption remotely.
- Endpoint Protector discovers, encrypts, and deletes sensitive data; it can be configured to perform explicit content and context scans to find confidential data.
Feature Comparison
| Gilisoft USB Lock | Endpoint Protector | |
| Operating Systems | Windows 2000, Windows 2003, Windows XP, Windows Vista, Windows 7, Windows 8, and Windows 10 | Cloud, SaaS, Web-Based, Windows, macOS, Linux, thin client systems |
| Features, Devices covered, and encryption capabilities |
|
|
| Ease of use | Very easy to install and use | Easy to install and easy to use |
| Dashboard UI | Highly interactive, easy to navigate and understand, clear and precise functionality - no mistakes can be made | Despite it being an enterprise-level tool, it is pretty easy to install and use. Administering it is excellent too - dashboards and menu are easy to navigate and command |
| Price | Free trial version available; they offer a fair-priced full version | Demo version available; the price for the full, premium solution is more fit for corporate users |
Gilisoft USB Lock vs. Endpoint Protector head-to-head
Ok, we have just looked at the tools individually. Now, let’s compare them feature-to-feature:
Installation
Gilisoft USB Lock is easy to install and just takes a few minutes to have it up and to run. Incidentally, this tool has a self-protection mode that prevents uninstalling by anyone other than the administrator. So, the installation remains until the administrator says it should go.
Endpoint Protector too is an easy-to-install solution that only takes a few minutes and a few steps to deploy and start using. Moreover, the solution’s package can be installed in smaller populations, while third-party tools can install it on more prominent people. Either way, it can be up and running in a matter of minutes.
Ease of use
Administrators will quickly love how easy it is to start using and master Gilisoft USB Lock. All actions can be executed from menus that are clear, concise, and straightforward.
With Endpoint Protector, the menus and features are also designed to make it easy to navigate and use. In addition, the modern design helps with making sure even novices can start securing their devices immediately after installation.
Dashboard and UI
One of the reasons Gilisoft USB Lock is easy to use is the design of the user interface (UI). Anyone – even a first-time user – would be able to perform most of the required administrative jobs like locking a USB drive, for example. In addition, the graphics and design are futuristic and fun – guaranteed to not bore anyone soon.
The dashboard for Endpoint Protector is designed to make the life of the user easier. Apart from its abundant features grouped into descriptive menus, it offers insights and real-time data automatically updated thanks to its auto-refresh capabilities. Overall, the graphical user interface (GUI) is interactive and easily discernible for navigation.
Operating system compatibility
Gilisoft USB Lock is compatible with most versions of Windows: Windows 2000, Windows 2003, Windows XP, Windows Vista, Windows 7, Windows 8, and Windows 10.
Meanwhile, Endpoint Protector can be deployed on any architecture as it supports cloud, SaaS, web-based deployments and is compatible with Windows, macOS, and Linux operating systems. In addition, it is so versatile it can be used on thin client installations.
Data securing capabilities
As we have seen, Gilisoft USB Lock is an excellent tool for protecting data from being copied to USB drives – one of the most common and accessible storage devices today. But, Gilisoft extends its security capabilities even further by covering other storage devices, websites, and even programs in its attempts to stop confidential or copyrighted data from being leaked using such storage devices or even printers.
Endpoint Protector is a suite of tools that can secure a wide range of devices, including USBs and peripherals, by encrypting and decrypting data as it goes back and forth; meanwhile, it also scans data at rest or in motion to ensure no sensitive information is being transferred illegally. In addition, it can auto-detect sensitive data, which can then be encrypted or deleted depending on the need.
Reporting
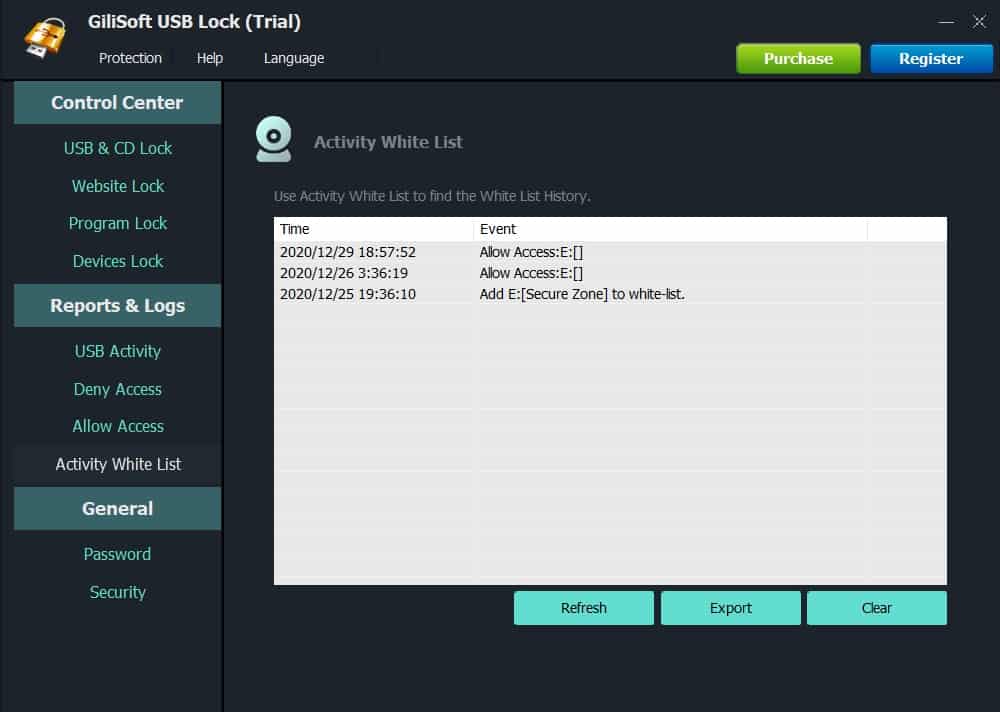
Gilisoft USB Logs comes with reports and logs that give deep insights into activities like:
- USB Activity to monitor file operation (like creating or deleting of files) on all USB disks
- Deny and Allow Access History – to see who accessed or was denied access to what
- Activity White List – tracking of the activity on devices that have been allowed to connect as well as store data
Endpoint Protector, on the other hand, offers file tracing and file shadowing to monitor data traffic. Administrators also have access to device logs where they can see the activity of each permitted device. In addition, they can manage all the users in the system – create users, import users, access user rights on specific devices, and view usage history. Finally, the tool also offers Compliance Tracking to see how well the organization is adhering to expected security standards.
Support
The Gilisoft website has a section dedicated to “How To” manuals for all their products, not just Gilisoft USB Lock. Apart from that, clients also get support via Skype, email, and text chat.
Endpoint Protector offers support via phone, email, or their help desk. In addition, they have FAQ pages and forums and a knowledge base for research into and in-depth understanding of their product.
Gilisoft USB Lock vs. Endpoint: Pros & Cons
Gilisoft USB Lock
Pros:
- Great user interface
- Blocks both USB ports as well as disk drives
- Offers password protection as well as full USB denial
- Can also block websites
Cons:
- Better suited for larger environments
Endpoint Protector
Pros:
- Custom security policies can be based on the user rather than the machine
- Automatically assesses risk based on vulnerabilities found on the endpoint
- Can alert to improper file access or insider threats (Acts as a DLP solution)
- Prevents data theft and BadUSB attacks through device control settings
Cons:
- Would like to see a trial version available for testing
Gilisoft USB Lock vs. Endpoint: Pricing
You can get a trial version of Gilisoft USB Lock for FREE. Alternatively, you can buy the full version of the software.
Endpoint Protector has a Demo version available upon request, but the price for the full, premium solution is more of a fit for corporate users.
The verdict
We have just gone through the head-to-head comparison of these two DLP and USB locking solutions. So, let us go ahead and get to the final verdict:
Gilisoft USB Lock offers a lot more than its name has to suggest as it protects different devices ranging from USB drives to printers, stops programs, and blocks websites that are deemed unnecessary to the users. Furthermore, it performs all of its functions quickly and without putting heavy loads on the endpoint processor or slowing down the system’s performance.
Endpoint Protector is an ideal tool for the corporate networking environment where they can even have cloud architectures as part of their infrastructure. It performs well in a larger environment where there are many endpoints to monitor and keep track of. Using it in anything but such an environment would be overkill and a waste of resources.
So, we suggest that SMB or personal users opt for Gilisoft USB Lock while businesses and corporate networks can be the ideal clients for Endpoint Protector. Apart from that, we can safely assume that these two tools perform well, as expected – they just do so in different network sizes.
Let us know what you think; leave us a comment below.





