Are you curious how you can check Group Policy in a fast and easy way? You’re in the right place. In this article, we’ll explore using the GPResult command to check group policy in a few different ways. Let’s get started.
What Is GPResult?
GPResult is a command-line tool used in Microsoft Windows operating systems to display the Resultant Set of Policy (RSoP) for a user or computer. It provides detailed information about the Group Policy settings that have been applied to a specific user or machine, which can be crucial for troubleshooting and managing group policy configurations.
Group Policy is a powerful feature in Windows used by administrators to manage the settings and configurations of users and computers within an Active Directory environment. It includes a wide range of settings, from password policies to security settings and software deployment. However, determining which policies have been successfully applied or diagnosing policy conflicts can be complex, especially in large networks with multiple domains and organizational units (OUs).
GPResult simplifies this process by offering a snapshot of the applied policies. When executed, it shows a summary of both user and computer policy information, including:
- Applied Group Policies: Displays the specific Group Policy Objects (GPOs) applied to the user or computer.
- Inheritance Information: Indicates which GPOs are inherited from higher levels of the Active Directory structure, such as from the domain or organizational unit.
- Resultant Set of Policy (RSoP): Shows the final set of policies that have been applied after considering any conflicting or overridden settings.
- Error Reporting: If there are issues with policy application, GPResult can reveal errors, such as denied access to GPOs or missing policies.
This tool is invaluable for troubleshooting why certain policies aren’t being applied or for verifying that policies are correctly configured on a target system. To run GPResult, administrators simply use the command gpresult /R for a quick report or gpresult /H filename.html for a more detailed HTML report.
Uses of Group Policy
- It may be used to enforce a password policy that allows users to only access/alter services that are defined.
- A group policy can stop an unfamiliar user from connecting to the network from a remote machine.
- It may be used to restrict or enable distant end devices in the network access to specific directories or files.
- It’s used to handle roaming users’ profiles, including folder redirection, offline file access, etc.
This article will teach you how to use the GPresult command-line tool to check which group policy items are applied to a user or computer.
The administrator of the operating system can identify the group policies that have been applied to the machine and the redirected directories and registry settings by using the command gpresult.exe.
GPresult Command
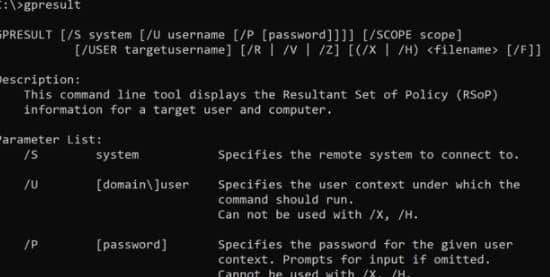
Go to the command prompt and type Gpresult /? to display the GPResult commands.
The description and parameter list of the resultant set of policies (RSoP) for a target user and the machine are shown in the output below.
Enter the following command in the CMD to see the results of the group policy objects settings that have been applied to your PC.
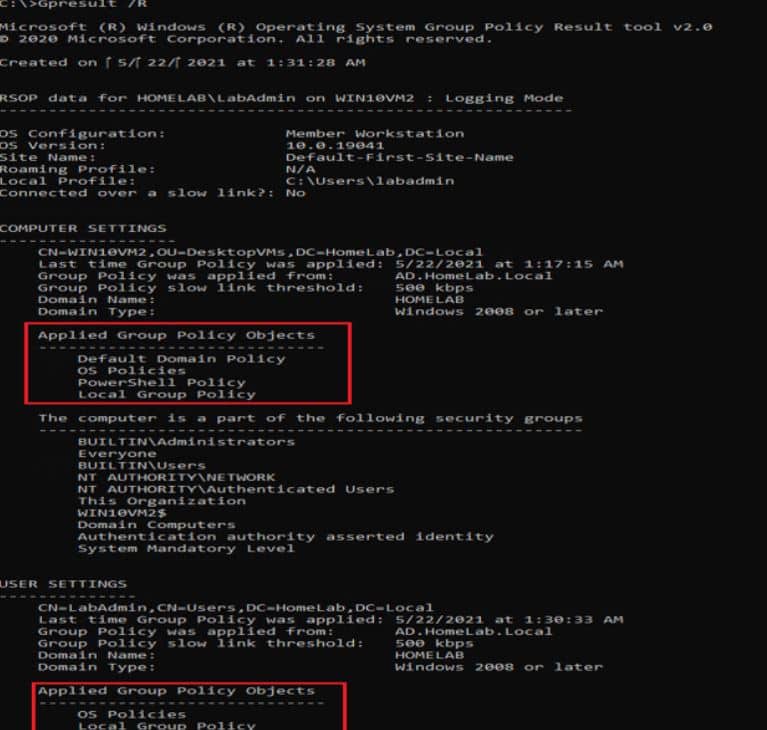
"gpresult /R"
As seen in screenshot 1, the output will provide the consequent set of policies for your desktop and the user account, which includes operating system configuration, OS version, User profile, site name, and link type. In addition, the User profile will detail other policies, such as the last time the policy was implemented, the domain name, domain type, and link threshold value.
Output of gpresult/R
The output for applied GP objects is likewise displayed in screenshot-2 of the GPResult command /R, as you can see. If the OS uses any form of filtering, it will show it together with the security policies applied to the system.
Exporting Gpresult Output
It’s not always enough to just deliver data to the command-line prompt. Perhaps you’ll need to create a report or discuss the findings with others. In such a situation, you’ll need to convert the results to a different format.
GPResult output can be exported in several different ways.
Creating a Text File from the Results
Using the command prompt or PowerShell’s output redirection function is one of the simplest methods to export results to a file. By using the redirection operator > followed by a text file name to “pipe” the command-line results to a file, the text will include precisely what you see in the console.
The command below will return all RSOP data and produce a file named C: \Temp\RSOP.txt that contains the whole GPResult command results.
Gpresult /R > c:\RsopReport.txt
GPResult/S – For remote Computer: The /S command displays the settings and group policy information on a remote machine.
Syntax1
gpresult/s COMPUTERNAME’
This command may also be used to show the remote machine or server’s user and computer settings. We may also observe the remote system’s verbose settings and parameters. We just require the remote end system’s credentials, and the system must be in the same domain as the host system.
Syntax2
gpresult /S system /U username /P password /SCOPE USER /V
The example is shown with the help of a screenshot
The error notice appears because the system is not linked to the remote user.
gpresult /S system /USER targetusername/SCOPE COMPUTER /V is the syntax for seeing the remote computer’s settings.
As a result, the system command combined with the SCOPE command may obtain all essential information from the network’s remote end machine and user.
GPResult/H – To export output to HTML
It is difficult to view the summary data for group policies objects from the command prompt in detail every time. As a result, we may export the data into HTML format to make it more understandable.
In this case, the /H command with the location and file name indicates where the file will be stored, as shown in the image below.
The HTML-formatted output may be seen in a web browser by navigating to the location where it was stored and clicking open with the browser. This is also demonstrated in the screenshot below.
Group Policy For Specific Users
The group policies for a given user or system in the network domain are displayed using this command. You must be aware of the user’s credentials to show the individual user policy summary.
The command is as follows:
gpresult /S system /U username /P password
If you want to examine the policy information and other data for the user “NEHA,” use the command and look at the output in the image below. It will show you all of the user’s settings and OS information.
GPResult Scope Command
The /SCOPE command determines whether or not the network’s user and machine settings should be shown. “USER” or “COMPUTER” is the syntax for this command.
The scope command may also view the remote computers, target users, and target computer’s settings. To access the information, you only need the credentials of the small end-user.
gpresult /R / SCOPE COMPUTER is now the command to display the remote computer settings.
GPResult Force Command
This command instructs the Gpresult to replace any existing filenames supplied by the /H or /X commands.
Gpresult /F /H targetlocationgpresultoutput.Html is the syntax.
The command will replace the content of the target location filename stored at the specified location, as seen in the above picture. The location of the updated file is shown below, and it may be seen using a web browser such as Google Chrome.
Using the Microsoft PowerShell Tool to Configure Group Policy
To configure group policies in Windows Server and Windows clients, use the Windows PowerShell utility with remote server administration tools (RSAT) installed on the client or server.
Many PowerShell commands may extract various OS parameters and examine the resulting set of policies (RSoP) for the remote server and PC. This program may be used to simultaneously set and examine the system parameters of several systems in a network.
Conclusion
We’ve explained what Group Policy Commands are and how to use those using examples and images. However, as previously indicated, numerous sorts of commands may be used to extract the appropriate group set of policies, each with its own set of implications.
When we need to create and test group rules for many devices and users on the network, we utilize the Microsoft Power shell program. The tool’s capabilities are enormous, and we’ll go through them quickly below.