Ping and Traceroute are great utilities for making a quick check on network connection statuses. However, you can’t sit and issue those commands repeatedly. Automated tools perform monitoring tasks around the clock – they don’t sleep or need bathroom breaks.
Here is our list of the best network automation tools:
- ManageEngine OpManager EDITOR’S CHOICE This tool excels in network automation capabilities, integrating comprehensive network, server, and application management into a single, user-friendly interface. Download a 30-day free trial.
- Site24x7 Network Configuration Management (FREE TRIAL) This package provides firmware vulnerability scanning, configuration image storage, and protection against device tampering. This is a cloud-based system. Start a 30-day free trial.
- ManageEngine Network Configuration Manager A full network device management package that includes configuration backup and centralized control of all device settings.
- SolarWinds Network Configuration Manager Able to create a standard setup, backup that configuration, and roll it out to all other devices of the same make and model.
- TrueSight Network Automation A network automation system that includes workflows to manage network devices.
- rConfig A free, open-source package that manages network configurations.
- Progress WhatsUp Gold Network Configuration Management A device configuration system add-on for a network monitoring package.
There are so many tasks that technicians need to perform every day in order to keep a network running smoothly and just about all of them can be automated.
What’s more, most automation tools can perform their services over a network and across the internet, which means that they enable the centralization of IT management.
Benefits of network automation
Key areas where network monitoring is improved by automation include:
- Device health monitoring
- Traffic flows and network capacity checks
- Connection efficiency
- Security monitoring
As well as launching searches and tests repetitively, automation tools have a big advantage over manual implementation because they eliminate human error.
Network management automation
Just as standard monitoring methods can be performed with greater dexterity through automation, management tasks can also benefit by implementing them through automated tools. Examples in the management category include on-boarding of equipment and users, patch management, capacity management through the clearing of temporary resource holders, such as temporary files and abandoned processes, and the management of IP address allocation.
Key areas of network management that are improved by automation include:
- Access rights management
- Capacity planning
- Incident response
- Continuity management
- Configuration management
- IP address management
- System maintenance
Network automation tools can repeat the same task over and over again, rippling out changes to many devices, updating cross-references in different systems. An example of where automation helps in network management lies with Device configuration management. Most networks have all of their nodes run by the same make and model of the device. There is an optimal setup for any device and having to log into the management console of each switch or router and go through all of its settings is laborious.
A technician working on setting up a network device can get distracted or interrupted, sometimes leaving the configuration incomplete, or clicking on the wrong option while trying to perform several tasks simultaneously.
Manual efforts to perform these tasks can result in half-completed rollouts, due to the technician responsible being interrupted in mid-task. Human error can result in transposition mistakes and paper-based notes can easily get destroyed or misplaced. Automated processes instantly update records and databases to reflect each change, creating a closed-loop system that greatly improves on the hazard-prone manual workflows.
The best network automation tools
Looking after network devices requires setup standardization, performance optimization, operation monitoring, and security enforcement. Automating all of those tasks introduces a greater level of coordination between tasks and responsibilities than a human mind can track. Automating device management tasks is a very worthwhile move.
Our methodology for selecting a network automation tool
We reviewed the market for network systems and analyzed tools based on the following criteria:
- A management tool for network devices
- Automated process to rollout device configurations
- A constantly-updating asset inventory
- Alerts for device problems or unexpected configuration changes
- Automatic settings restoration
- A free trial or a demo system that creates the opportunity for a no-obligation assessment
- A good price for a tool that provides several functions
With these selection criteria in mind, we identified some great network automation tools that will reduce your network management workload.
You can find out more about each of these tools in the following sections.
1. ManageEngine OpManager (FREE TRIAL)
ManageEngine OpManager stands out for its robust network automation capabilities, simplifying network management and enhancing operational efficiency. It offers automatic network discovery, auditing devices across various vendors and operating systems by specifying an IP range. OpManager’s advanced discovery engine includes features like Discovery profiles, schedules, and custom rule setups, ensuring all devices are monitored effectively.
Key Features:
- Automated Configuration Management: Simplifies network configuration tasks and reduces manual errors.
- Security Event Monitoring: Detects and alerts on critical security events like failed logons and account lockouts.
- Application & System Monitoring: Monitors logs for crucial applications such as IIS, Exchange, SQL, and ISA servers.
- Custom Rule Creation: Allows for the creation of custom monitoring rules to enforce specific security policies and monitor any application.
- Integrated Solution: Combines event log monitoring with overall network, server, and application management, eliminating the need for additional consoles.
- Predefined Rules: Offers numerous out-of-the-box rules for monitoring various applications and services, enhancing usability.
Why do we recommend it?
OpManager is recommended for its superior network automation capabilities, which streamline configuration management and routine network tasks, enhancing overall efficiency and reducing manual workload.
Automated network mapping provides complete visibility of the network infrastructure, helping administrators quickly identify and troubleshoot issues. Additionally, OpManager’s proactive alarm escalation and workflow automation streamline network management, making it easier to maintain optimal performance and address issues before they escalate.
Who is it recommended for?
OpManager is ideal for IT administrators and network managers seeking a comprehensive monitoring solution with advanced network automation features, particularly those managing complex and large-scale network environments.
Pros:
- Network Automation: Automates network configurations and routine tasks, improving efficiency and reducing manual errors.
- Comprehensive Security Monitoring: Automatically detects and alerts on critical security events, enhancing network security.
- Extensive Application Support: Provides thorough monitoring for essential applications like IIS, Exchange, and SQL servers.
- Customizable Rules: Users can create and customize monitoring rules to suit their specific security and operational needs.
- Unified Management Console: Integrates event log monitoring with network and server management, streamlining operations.
- User-Friendly: Designed to be accessible for users without extensive technical expertise, making it easy to deploy and manage.
Cons:
- Learning Curve: New users might need time to familiarize themselves with the extensive features and customization options.
Download a 30-day free trial.
EDITOR'S CHOICE
ManageEngine OpManager is our top network automation tool because it excels in network automation capabilities, significantly simplifying network management tasks. This tool integrates network, server, and application management into a single console, reducing the need for multiple interfaces. It offers robust security event log monitoring, automatically detecting critical events such as failed logons and account lockouts, which enhances security without requiring expert intervention.
OpManager also supports extensive monitoring of application and system logs for services like IIS, Exchange, and SQL servers, with the flexibility to create custom rules. Its ability to automate network configurations and routine tasks boosts operational efficiency and minimizes downtime.
Download: Access the 30-day FREE Trial
Official Site: https://www.manageengine.com/network-monitoring/network-automation.html
OS: Windows, Linux, Cloud-based
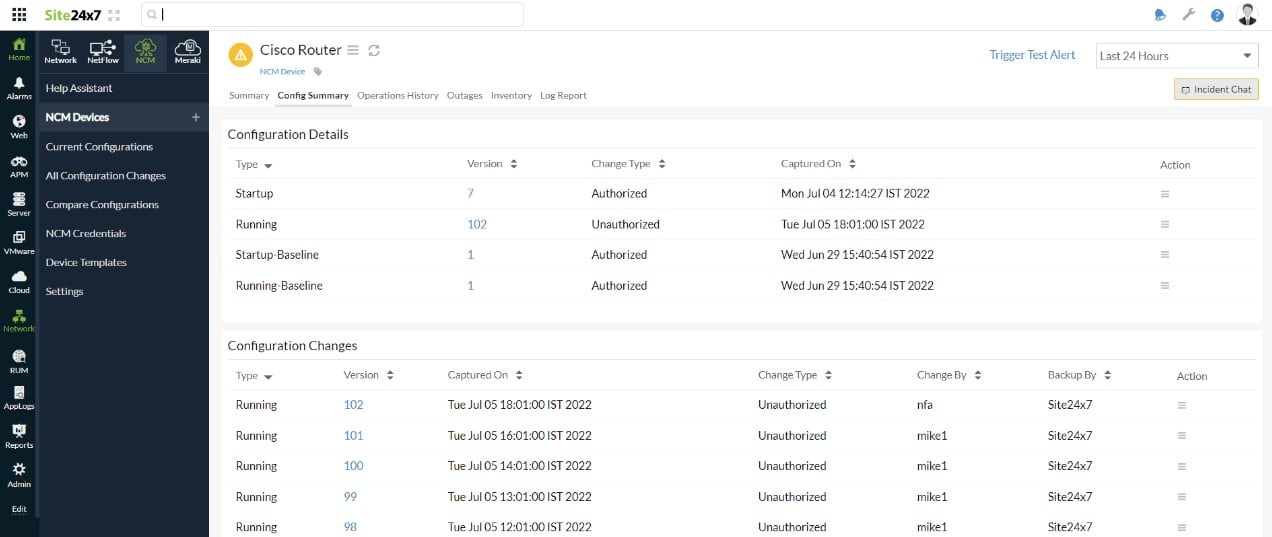
2. Site24x7 Network Configuration Management (FREE TRIAL)
Site24x7 Network Configuration Management is offered on a platform of system monitoring and management services that include a network discovery routine. That unit creates a network inventory, which provides the Network Configuration Management module with a list of the equipment that it needs to manage.
Key Features:
- Comprehensive Network Inventory: Automatically discovers and catalogs network devices, creating a detailed inventory for management.
- Firmware Vulnerability Scanning: Identifies outdated firmware on network devices and updates them to mitigate security vulnerabilities.
- Configuration Backup and Restore: Saves configurations of network devices and automatically restores them if unauthorized changes are detected.
Why do we recommend it?
The Site24x7 Network Configuration Management service provides protection for your system by blocking unauthorized changes to network devices and also preserving all of your hard work in setting up all systems by storing configurations for instant recovery if hardware gets damaged by an environmental disaster. The package includes firmware vulnerability scanning.
The Network Configuration Management tool scans each device in the network inventory and records its firmware version. The system will then check whether there is a newer version available and, if so, update the device. Once the device has been validated, the network configuration management package takes an image of the device’s settings and stores it. The tool periodically compares the current settings of each device to its stored image. If there is a difference, the package restores the stored configuration. Thus, many attempts by hackers to alter the settings of your network will be automatically wiped out.
This service automates an essential security monitoring task. Without it, the network manager would need to manually command a backup of the configuration and then remember to check the difference between the current and stored versions regularly. This would take up time that would be better spent on other admin tasks.
Who is it recommended for?
This package is suitable for any business that has a network. It can manage switches, routers, firewalls, and wireless APs. The tool is able to connect to devices provided by Cisco, Fortinet, SonicWall, Aruba, and other manufacturers. Per-unit pricing makes the 24×7 package very scalable.
Pros:
- Integrated Monitoring Platform: Part of a broader suite of system monitoring and management tools, offering a holistic approach to IT infrastructure oversight.
- Cloud-Based Management Console: Enables remote access to network management tools via any standard web browser, enhancing flexibility and convenience.
- Security and Compliance: Regularly scans for and corrects unauthorized configuration changes, ensuring network security and compliance with policies.
- Rapid Hardware Deployment: Facilitates quick integration of new or replacement hardware by applying stored configurations, minimizing downtime.
- Scalability: Offers per-unit pricing, making it a versatile solution for businesses of all sizes, from small operations to large enterprises.
Cons:
- Limited Base Package Inclusion: The initial packages may only cover configuration management for a single device, potentially requiring additional purchases for comprehensive network coverage.
The Site24x7 platform is a subscription service with a large number of plans. All of them include the Network Configuration Management service with coverage for one device. You pay extra for each additional device. The base package for the MSP edition includes coverage for five devices. Assess the Site24x7 platform with a 30-day free trial.
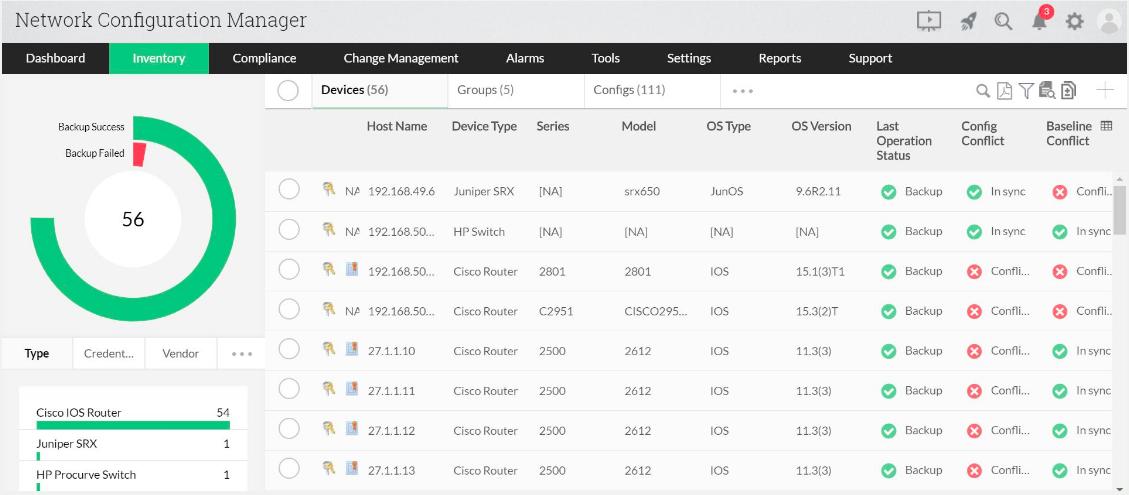
3. ManageEngine Network Configuration Manager
ManageEngine Network Configuration Manager has a similar set of automated functions to those in the SolarWinds tool. It manages configurations for switches, routers, and firewalls. This tool backs up the settings of a device as an image. These backups can be restored on-demand or automatically, according to a trigger event.
Key Features:
- Multi-Platform Support: Compatible with Windows Server, Linux, and AWS, facilitating versatile deployment options.
- Configuration Backup and Restoration: Automatically backs up device configurations, offering the ability to restore settings on-demand or in response to specific triggers.
- Tampering Monitoring: Actively watches for unauthorized changes to device configurations, ensuring the integrity of network settings.
Why do we recommend it?
ManageEngine Network Configuration Manager is a very similar package to the SolarWinds Network Configuration Manager. It creates an image of each device’s settings and stores it in a library. The tool will sweep the network comparing current settings with the stored version for each device and restore the original if changes are detected.
The main trigger is an unexpected change. When the network administrator wants to alter the settings of a device, the process is managed through the Network Configuration Manager dashboard. Changes by any other route get wiped out.
Once an image has been stored, it can be applied to any device and even in bulk to a large number of devices. This automation is a great time saver for large networks.
Who is it recommended for?
This system is suitable for mid-sized and large organizations. There is a Free edition for small businesses that has a limit of managing two devices. The two paid editions cater to a single site or multiple sites. The software will install on Windows Server, Linux, or AWS.
Pros:
- Automated Device Management: Simplifies the process of managing device configurations, making it easy to standardize settings across switches, routers, and firewalls.
- Change Management Control: Integrates changes through a centralized dashboard, maintaining control over authorized adjustments and negating unsanctioned modifications.
- Bulk Configuration Capabilities: Enables the application of configurations to multiple devices simultaneously, significantly reducing manual workload for network administrators.
- Comprehensive Alerting System: Notifies administrators of inventory changes or unauthorized configuration modifications, enhancing security and compliance.
- Scalable Solutions: Offers editions tailored to different organizational sizes, from a Free version for small businesses to more advanced options for multi-site enterprises.
- Cross-Platform Compatibility: Supports a broad range of operating systems, ensuring functionality across diverse IT environments.
Cons:
- Complexity: As a full-featured monitoring platform, new users may find it challenging to navigate and utilize all available options effectively.
ManageEngine created the Network Configuration Manager following the Network Change, Configuration, and Compliance Management (NCCCM) standards. The software for the system installs on Windows Server and Linux. It is available for a 30-day free trial.
4. TrueSight Network Automation
TrueSight Network Automation from BMC Software provides automated processes for the on-boarding, management, and security of network devices. A key feature of this network automation tool is its design that coordinates with the compliance requirements of a long list of data security standards.
Key Features
- Automated Network Device Onboarding: Streamlines the integration of new network devices into the management system, ensuring they are immediately brought under control.
- Centralized Fleet Management: Offers a unified platform for overseeing the configurations and compliance of all network devices.
- Compliance Reporting: Aligns with numerous data security standards, including PCI-DSS, NIST, HIPAA, CIS, and SOX, providing tailored compliance reporting.
Why do we recommend it?
TrueSight Network Automation is another network configuration manager. This system also looks at the firmware of network devices and updates it when necessary. That process can disrupt the manual configuration options, so it will then reapply your settings if they were wiped out by the update.
Network managers can select a set of policies from the TrueSight setup menu that specifies the security to follow. Once this setting has been specified, the TrueSight system adapts to fully comply with that standard. The available standards in the settings list of TrueSight Network Automation include PCI-DSS, NIST, HIPAA, CIS, and SOX.
Once set, the standards compliance module recommends the settings for each network device. On starting service, the tool scans the network for all devices and logs them. Once listed, those devices can be reconfigured automatically by TrueSight Network Automation according to the selected standard.
The network discovery process continues throughout the service life of the tool. This sweep looks for new devices and also checks on the settings of devices already enrolled in TrueSight management. If any of the settings are detected as changed, TrueSight automatically rolls it back to the standardized setting, logging the change as it removes the unauthorized change.
TrueSight can be set to automatically rollout any patches and updates to the firmware of all monitored devices. It is also possible to specify a required manual approval and individual on-demand updates can also be applied through the system.
BMC Software TrueSight Network Automation installs on Windows Server, RHEL, and Ubuntu Linux.
Who is it recommended for?
This system is suitable for mid-sized and large companies. The service offers automatic reconfiguring of devices for specific data protection standards. You can select a template from a library that applies requirements for HIPAA, PCI DSS, NIST, and SOX. this is an on premises package for Windows Server or Linux.
Pros:
- Compliance-Focused Configuration: Automatically adapts device configurations to meet selected data protection standards, simplifying compliance efforts.
- Continuous Network Discovery: Regularly scans the network for new devices and unauthorized configuration changes, maintaining security and consistency.
- Firmware Management: Includes capabilities for updating device firmware while preserving manual configurations, reducing operational disruptions.
- Automated Configuration Rollback: Automatically reverts unauthorized changes, keeping device configurations in line with policy standards.
- Pre-configured Workflows: Offers a range of ready-to-use workflows, facilitating immediate benefits from automation.
Cons:
- Complexity for Small Networks: The depth and breadth of features may overwhelm smaller networks or organizations with simpler infrastructure needs.
5. SolarWinds Network Configuration Manager
SolarWinds Network Configuration Manager provides a series of task automation workflows for managing network devices. The software includes a system that enables a standard setup for a specific device make and model to be saved. This is stored as an image. It can then be applied to all other devices of the same model automatically – those currently on the network and any new devices added.
Key Features
- Standardized Device Configuration: Enables the creation and storage of standard setup images for network devices, ensuring uniformity across the network.
- Automated Device Setup: Facilitates the automatic configuration of new devices to conform to established standards, streamlining network expansions.
- Unauthorized Change Detection: Monitors for and instantly reverses unauthorized configuration changes, maintaining network integrity and security.
Why do we recommend it?
SolarWinds Network Configuration Manager will store an image of each network device’s settings and then check for unauthorized changes on those devices. This process will restore the stored settings if it detects changes. You can also use this system to standardize device settings and apply the stored image to any new device.
The Network Configuration Manager monitors the settings of each of the devices enrolled in the system. If any unauthorized changes occur, the service reapplies the original image. This is a vital security service because altering device settings can weaken network security, making it easier for intruders to move around the network undetected.
An unauthorized change in the configuration of a device also raises an alert. This makes the network manager aware of the alteration even though the threat already gets locked down by the configuration reset. The knowledge of an unauthorized change and the log of what happened enables the event to be investigated further.
Those configuration change logs contribute towards a document base to show data security standard compliance. The Network Configuration Manager receives security feeds from the National Vulnerability Database. This enables network managers to close down exploits in network devices as soon as they are discovered. Thanks to process automation, any configuration changes can be applied in bulk to all devices from one central location.
Who is it recommended for?
This tool is a very competent network automation service for large businesses. Once you have standardized your switch and router settings and stored images, you don’t need to do anything further. The Network Configuration Manager will constantly sweep the network and ensure device security. This software installs on Windows Server.
Pros:
- Enhanced Security Measures: Actively watches for configuration tampering, restoring original settings to lock down security breaches promptly.
- Compliance Documentation: Generates change logs to support compliance with data security standards, providing evidence of proactive network management.
- Vulnerability Database Integration: Receives updates from the National Vulnerability Database, enabling quick response to newly discovered exploits.
Cons:
- Enterprise Focus: Tailored for large business environments, making it less suitable for smaller networks or non-professional users.
The SolarWinds Network Configuration Manager installs on Windows Server. You can access it on a 30-day free trial.
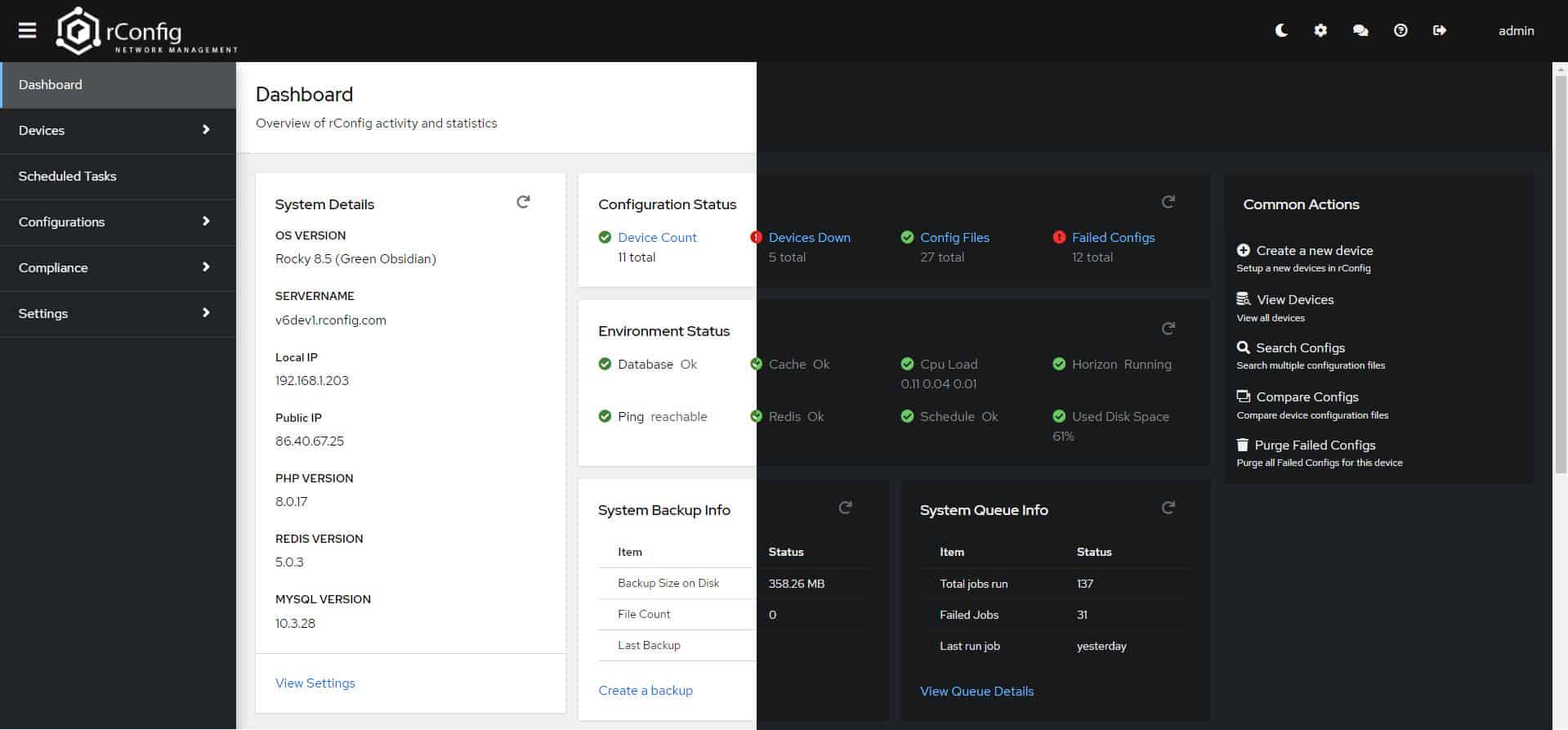
6. rConfig
The rConfig system is a free, open-source network configuration manager. Despite not having a commercially funded development team behind it, rConfig has many key network automation features found in its fully-funded rivals.
Key Features
- Open-Source Solution: Provides a cost-free network configuration management tool, making it accessible for any budget.
- Automatic Device Discovery: Continuously scans the network for devices, ensuring all components are accounted for in the management system.
- Automated Configuration Management: Enables backup, standardization, and deployment of device settings to maintain consistent network configurations.
Why do we recommend it?
Those looking for a free network automation tool should consider rConfig. This open-source software package will discover all network devices and record them in a hardware inventory. This is a network configuration manager that has compliance management capabilities. The system allows you to examine the stored configurations.
This automation tool includes network discovery. This process is continuous, which means that the software detects all devices when it is first installed and then continues to detect changes to the network infrastructure. Each discovered network device is logged in an inventory and then its automated management can begin.
The tool is able to back up all the settings of all devices. It is also possible, through rCongif, to create a standard-setting on one device, back it up, and then apply it to all devices of the same make and model.
With each successive network sweep, rConfig retakes an image of each device. The network manager can set up a script to compare each snapshot to the standardized backup. Although this process is not fully automated within the rConfig environment, it is sufficient to detect unauthorized changes.
The rConfig dashboard includes the Configuration Compliance Manager, which stores data security standards requirements and highlights differences in the ideal settings for compliance and the configurations of devices running the network.
The software for rConfig installs on CentOS and RHEL Linux.
Who is it recommended for?
There are three editions of rConfig and the first of these is free to use. The standard version is suitable for mid-sized and large companies and that edition includes compliance management and the option to store rollback points. The tool is also available in a version for managed service providers.
Pros:
- Cost-Effective Network Management: As a free, open-source tool, rConfig offers significant cost savings while still delivering essential network automation features.
- Continuous Monitoring: Offers autodiscovery and continuous monitoring capabilities, ensuring new devices and hosts are promptly integrated into the network management strategy.
- Configuration Flexibility: Allows for the easy push of new configurations and backups of existing device settings, facilitating efficient network management.
Cons:
- Limited Support: Being open-source, rConfig does not come with the paid support options available with commercial products, potentially impacting troubleshooting and issue resolution.
- Linux Dependency: Requires installation on CentOS or RHEL Linux, which may limit its applicability in environments not using these operating systems.
7. Progress WhatsUp Gold Network Configuration Management
WhatsUp Gold, from Progress Software Corporation, is a network monitoring and monitoring package that can be enhanced through add-on modules. One of the add-ons available for WhatsUp Gold is Network Configuration Management.
Key Features
- Configuration Standardization: Saves standardized device configurations to ensure uniformity across network devices like switches, routers, and firewalls.
- Tampering Detection: Monitors network devices for unauthorized configuration changes, alerting network managers to potential security risks.
- Automatic Configuration Restoration: Offers the ability to automatically revert devices back to their approved settings in the event of unauthorized changes.
Why do we recommend it?
Progress WhatsUp Gold Network Configuration Management is an add-on unit for the WhatsUp Gold system. The core package provides network device monitoring, based on SNMP. The Network Configuration Manager addition backs up the configurations of switches, routers, and firewalls. It will alert on the detection of settings changes.
The Network Configuration Management module performs network scans at regular intervals. Each identifies all devices currently operating on the network and logs them in an inventory. The discovery service then documents all of the settings on each device, making them visible in the system dashboard.
The network manager can create a standard setup for each category of device and model and then automatically roll that out to all devices of the same type. Once a standardized configuration has been stored and implemented on all devices, successive system sweeps identify any divergence from that standard setup. This identifies unauthorized changes and the network manager gets notified of such an incident by an alert. The manager then has the option of rolling back the changes on demand. Alternatively, the Network Configuration management system can be set up to cancel unexpected changes automatically.
The Network Configuration Manager also facilitates updates and patches to network devices. The system can be set to roll out updates automatically or list new updates for approval. Patches can also be applied manually through the system.
All actions concerning device configurations are logged, providing an audit trail. These logs are needed for any data security standards compliance audits.
WhatsUp Gold is a network performance monitor. This operates by querying device statuses through the Simple Network Management Protocol (SNMP). So, network operations get automatically and recursively tested by the main system of WhatsUp Gold, while the Network Configuration management add-on repeatedly checks on the configurations of network devices. The combination of these two services provides full automation of network device management and monitoring.
Who is it recommended for?
This system requires the pre-installation of the WhatsUp Gold base package, which is marketed at mid-sized businesses. The addition for network configuration management provides compliance management as well, with auditing and reporting functions. The software for all of the WhatsUp Gold suite runs on Windows Server.
Pros:
- Integrated Network Management: As an extension of the WhatsUp Gold platform, it complements network performance monitoring with configuration management for a holistic network oversight.
- Automated Device Updates: Facilitates the deployment of patches and updates, either automatically or under manual supervision, enhancing network security and compliance.
- Comprehensive Auditing: Logs all configuration-related activities, providing an essential audit trail for compliance verification and security audits.
Cons:
- Dependency on Core Package: Requires the foundational WhatsUp Gold system, potentially adding to the total cost for businesses not already using the platform.
- Modular Upgrade Considerations: While modular pricing offers flexibility, businesses requiring a full suite of features may find the cumulative cost of add-ons significant.
The WhatsUp Gold system installs on Windows Server. You can get a 30-day free trial of WhatsUp Gold and the Configuration Management module.
Choosing a Network Automation Tool
Suppliers of network tools are both inventive and competitive. This means that just about every aspect of network management is now supported by the availability of a suitable tool. Also, as soon as one network management tool provider thinks of a new field to support, every other player in the market comes up with its own version of that utility.
So, there are a lot of different automation tools that cater to different aspects of network management and lots of competitors vying to supply a utility to perform each function. In order to make this list of recommended automation tools more manageable, we have narrowed down the requirements to tools that enable the automated management of network devices.
Network automation FAQs
What is network automation in CCNA?
Network automation is implemented by software and it manages network devices. Tasks such as configuration, management, updating, and testing of devices can be implemented by systems that run either on a schedule periodically or loop continually. Automation processes can be attached to network monitoring systems so that a detected shortfall or fault can be immediately corrected without manual intervention. Other automation scenarios include scripts that implement a series of tasks in a workflow, such as onboarding a new device by inserting settings and security features at the launch of one command.