Paros Proxy was once a popular open-source web security testing tool used by penetration testers and security professionals to analyze web applications and identify security vulnerabilities. Developed in the early 2000s, it gained attention for its ability to intercept and manipulate HTTP/HTTPS traffic, making it useful for testing web applications for issues like cross-site scripting (XSS), SQL injection, and other common vulnerabilities.
However, in recent years, Paros Proxy has become outdated and is no longer actively maintained. The last significant update to Paros was made around 2007, and the tool has not seen substantial development or security updates since then. As a result, it has fallen behind in terms of compatibility with modern web technologies, security standards, and features that are necessary for effective vulnerability testing.
Security and Compatibility Issues
The fact that Paros Proxy is no longer maintained presents several security and functionality risks for users. Without regular updates, the tool lacks patches for known security vulnerabilities, making it potentially insecure for use in testing environments.
The software is not equipped to handle newer web application protocols, security features, or evolving attack techniques that have become common in modern applications. This includes limited support for advanced encryption methods like TLS 1.2 or TLS 1.3, which are critical for secure web communication today.
Moreover, many modern web applications now use frameworks and technologies that Paros Proxy cannot adequately analyze, such as AJAX-heavy applications, web sockets, and more complex authentication methods. The lack of updates also means that Paros does not have integrated support for newer web vulnerabilities or techniques for modern web application security testing.
Look for an alternative
Given its outdated status and the lack of security updates, Paros Proxy should not be considered a secure or reliable tool for web application security testing today. Security professionals are encouraged to use more up-to-date, actively maintained tools. There are a number of other Web application testing services that are closely related to Paros Proxy, are free to use, and are still being maintained. Other paid tools are also available to substitute for Paros Proxy.
Here is our list of the best Paros Proxy alternatives:
- ZAP EDITOR’S CHOICE A fork of Paros Proxy, so if you are looking for the latest Paros Proxy version, look here. This web security system is supported by the Open Web Application Security Project and is maintained by a coordinated team of volunteers.
- Wapiti Looks for XSS, file and backup disclosure, and many other security weaknesses on websites.
- Skipfish Crawls every page on a site and scans each for security weaknesses by using heuristic techniques.
- Ratproxy This website vulnerability checker includes SSL man-in-the-middle attack protection along an encrypted connection.
- SQLMap This free pen-testing tool specializes in spotting SQL injection attacks on a website, covering six typical database attack methods.
- Wfuzz A pen-testing tool for hardening web applications against cookie fuzzing, SQL injection, XSS, and authentication forcing.
- Vega A free web application vulnerability pen tester to spot XSS, SQL injection, directory listing, and file inclusion tricks among other possible attacks.
- W3af This is an attack audit framework that identifies SQL injection, XSS, and a total of 200 other possible vulnerabilities.
Do you need Paros Proxy?
Paros Proxy operates as a traffic interceptor between the server and a browser. This is an excellent way to scan for site vulnerabilities. However, there are other pen testing configurations that can be considered as good replacements for the tool. We didn’t just look at proxies as alternatives.
The processes of Paros Proxy show the requests sent by the browser and the responses sent by the web server in order to see the many data exchanges that occur in order to compose a web page. This identifies the different web servers involved in providing code for the page. Another feature in Paros Proxy is a crawler that will list all of the pages on a site.
Paros Proxy is useful when looking for possible vulnerabilities to hacker attacks, such as cross-site scripting (XSS) or SQL injection. However, given its age, the service is incapable of discovering new attack vectors.
When looking for alternatives to Paros Proxy, we focused on searching through free open-source software. As the main download site for Paros Proxy is SourceForge, we also prioritized other web application security solutions that are available on that code repository and looked at GitHub and the Google code repository as well.
The Best Paros Proxy Alternatives
Our methodology for selecting Paros Proxy alternatives
We reviewed the market for Paros Proxy replacements and assessed the options based on the following criteria:
- A packet sniffer for Web traffic
- A tool that can identify exchanges in the delivery of a Web page
- A system that can identify contributing components hosted on other servers
- Detection of malicious data entry
- A Web crawler to document all of the pages on a site
- A free trial or a demo that provides an opportunity to assess the system before buying
- Value for money from a Web traffic sniffer that can identify attacks at a reasonable price
You can read more about each of our solid recommendations for Paros Proxy alternatives in the following sections.
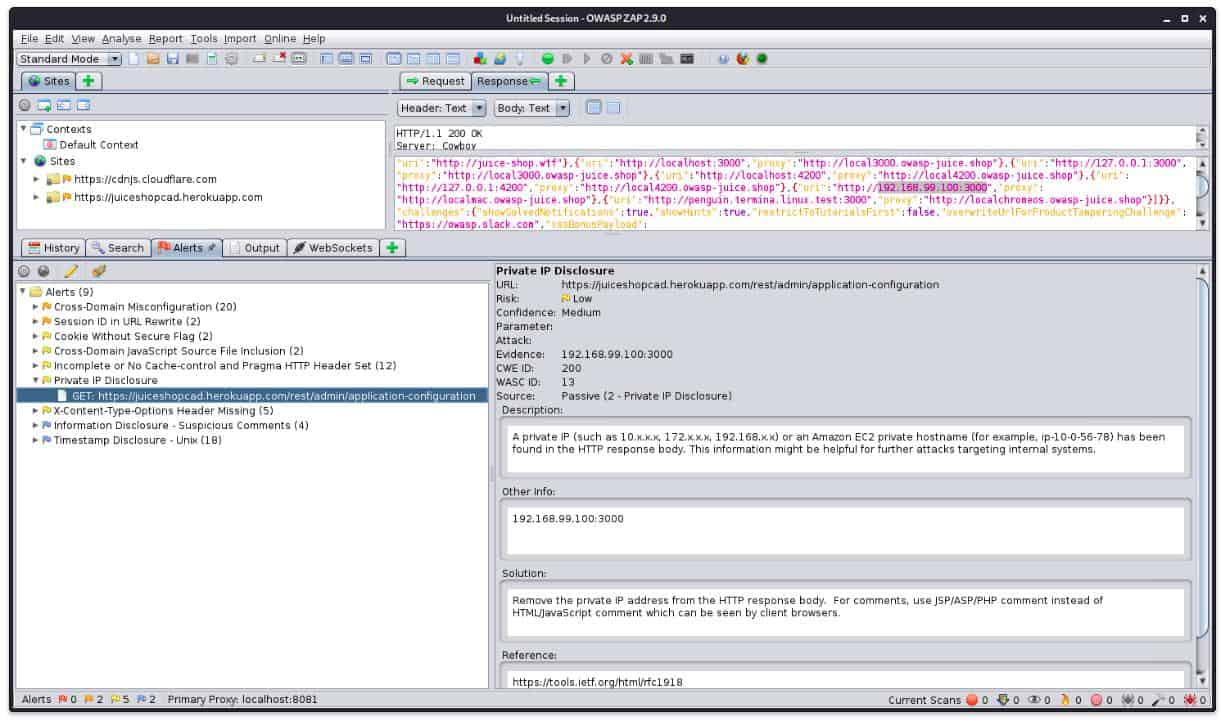
1. ZAP
ZAP stands for the Zed Attack Proxy. It is a fork of Paros Proxy and is still being refined and advanced by a well-organized community team. The open source project is under the management of the Open Web Application Security Project (OWASP).
Key Features:
- Fork of Paros Proxy: As close as you can get to Paros Proxy without actually being Paros Proxy
- Fully Managed Development: Previously run by OWASP, now run by The Software Security Project
- Open-Source: Anyone can download the source code and change it
- Site Crawler: Operates like a search engine
- Free to Use: Costs nothing
Why do we recommend it?
ZAP has two main recommendations as an alternative to Paros Poxy. The first is that it is based on Paros Proxy and the second is that The Software Security Project is the definitive organization for identifying security threats. This tool is useful for reconnaissance.
The Zed Attack Proxy starts its testing process by crawling the site to be tested to log all accessible pages. It then lists those pages, giving the user the opportunity to command analysis of a specific page. The tool will look for SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), security misconfiguration, broken authentication and session management, ineffective access control, sensitive data exposure, unprotected APIs, and components with known vulnerabilities. In general, each scan highlights insufficient attack protection on a web server and outdated code on a page.
New users have a steep learning curve in order to get the best out of the tool because there are a lot of plug-ins available that allow the tool to be expanded and tailored. All of those adaptations are developed by the user community and so have been created to meet a specific need that many other ZAP users might need. The tool and all add-ons are free.
ZAP works in exactly the same way as Paros Proxy in that it operates as a proxy between the web server and a browser. You don’t need to host it on a remote server, though, it will run on the same computer that runs the browser. The code for the tool installs on Windows, Mac OS, Linux, and BSD Unix.
Who is it recommended for?
This tool is suitable for use by penetration testers. The tool is free to use and so anyone can download it, which means, if you are a system administrator you can use it yourself to check on Web application security and save your company the cost of hiring security consultants.
Pros:
- This is a Proxy: It intercepts traffic between a Web server hosting the site being tested and the browser that displays it
- Generates List of Pages in the Site: The user can then focus on specific pages
- Offers Numerous Plugins: These extend usability
- Assesses Specific Pages: Produces a prioritized list of vulnerabilities
- On-Premises Software Package: Available for Windows, Mac OS, Linux, and BSD Unix
Cons:
- Not User-Friendly: You need training in order to use the tool
EDITOR’S CHOICE
OWASP ZAP is our number one recommendation as a replacement of Paros Proxy because it is a fork of that vulnerability scanner. The ZAP project is properly managed and so the code is regularly overhauled, keeping it up to date with cybersecurity threats and free from vulnerabilities in its own procedures.
Operating System: Windows, Mac OS, Linux, and BSD Unix.
2. Wapiti
Wapiti has its own page at SourceForge.io and it is free to use, although the developers ask for donations. This tool crawls a site, identifying all accessible pages and the tests for vulnerabilities by launching a series of attacks to see whether they succeed. It doesn’t examine source code.
Key Features:
- Probes File Access Weaknesses: Looks for typical Web application security vulnerabilities
- Attempts Code Attacks: Tries SQL injections, cross-site scripting, and many other techniques
- Command-Line Tool: No GUI interface
- Free to Use: Available from GitHub and SourceForge
Why do we recommend it?
Wapiti is a competent Web application and website security scanner that is still being maintained – the latest update to the code occurred in January 2023. Wapiti is highly automated but it is a command line tool with a lot of options that take a long time to learn.
The vulnerability tests of Wapiti include file disclosure scans, database injection, CRLF injection, XSS, command execution possibilities, XML External Entity (XXE) injection, server-side request forgery (SSRF), Shellshock, and open redirects. It will search for the backup files containing sensitive information, look for known dangerous files on the webserver, check for .htaccess weaknesses, and try uncommon HTTP attacks.
Wapiti is a library of utilities that are launched at the command line – there is no GUI frontend for it. The code will install on Windows and Linux.
Who is it recommended for?
Once you have studied the command line options, you will find Wapiti very easy to use. The next challenge is interpreting the results. As the output writes about specific types of attacks, you will need to read up on application security if you aren’t already a trained penetration tester.
Pros:
- Discovers all Pages on a Site: Operates reconnaissance as a crawler
- Launches Attacks to Determine if they Succeed: More reliable than proof of concept
- Supports Black Box Scans: Doesn’t scan code
- Downloadable Software Package: Available for Windows and Linux
Cons:
- No GUI: Targeted more towards security specialists
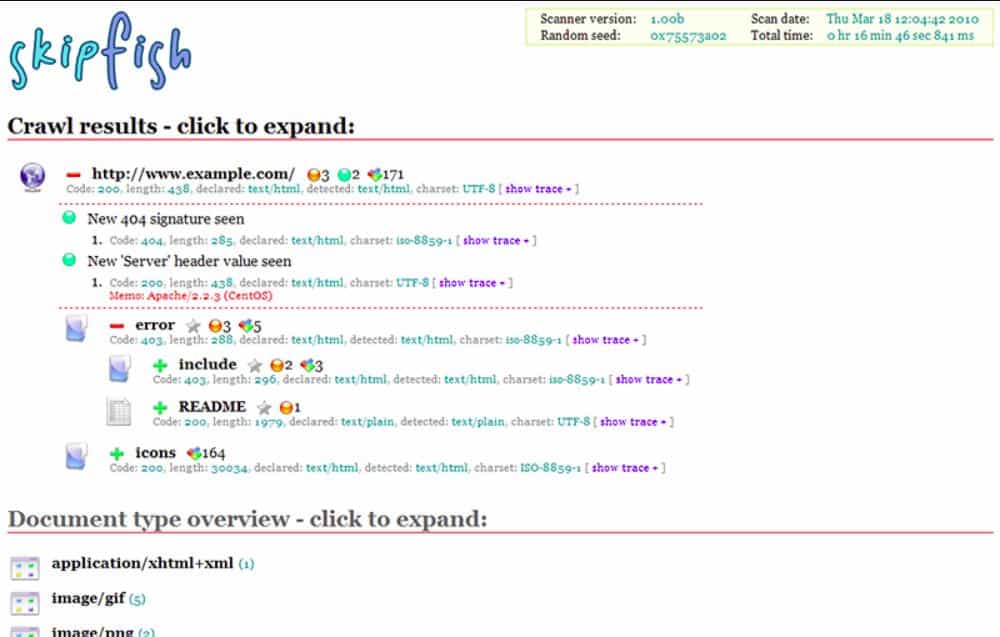
3. Skipfish
Skipfish uses a web crawler strategy to identify all accessible pages on a site and then automatically cycles through them, scanning for vulnerabilities. The report of results maps out the structure of the site’s file storage and lists any potential problems with each file.
Key Features:
- Operates as a Web Crawler: Scans through all linked pages on a site
- Shows File Hierarchy: Indicates files that have security weaknesses
- Free to Use: Open source
Why do we recommend it?
Skipfish is an interesting tool that discovers all pages on a website and then scans each for security weaknesses. Just the crawl is a useful feature because it could expose pages and directories that you thought were hidden. Such secret pages can often be used by hackers as a way in.
The vulnerability probes check for SQL and PHP injection, server-side shell command injection, server-side XML injection, XSS, CSS inclusion problems, directory and redirection bypasses, and many other attack vectors.
Skipfish is free to use and it installs on Windows, Linux, Mac OS, and Free BSD. The code is available from a Google archive.
Who is it recommended for?
This is a great little tool and better still, it is free to use. One problem is that after a lot of development activity in 2010 and 2011, the software hasn’t been updated since December 2012. That could mean that it is perfect and can’t be improved or maybe it is effectively abandoned.
Pros:
- Lightweight Tool with a Simple GUI: Doesn’t look very presentable
- Maps Site Structure: Reports vulnerabilities as a simple report
- On-Premises Software: Available for Windows, Linux, Mac OS, and Freebsd
Cons:
- Old Code: Hasn’t been updated since 2012
4. Ratproxy
Ratproxy is very similar to Paros Proxy. However, its latest release is a little dated. It operates between the web server and a browser and its unique selling point is that it also checks SSL session establishment to look for man-in-the-middle attack vulnerabilities. A nice feature of this vulnerability scanner is that it is lightweight and doesn’t place too much load on its host.
Key Features:
- Checks Transmission Security: Operates as a proxy
- Examines SSL Certificates: Tries man-in-the-middle attacks
- Free to Use: Available from a Google Code archive
Why do we recommend it?
Ratproxy is a scanner, which automates reconnaissance for security weaknesses in websites. As well as scanning the code of a site, the tool can record the events of a user and identify triggered weaknesses. The system looks for typical attack strategies, such as XSS and SQL injection.
The Ratproxy checks examine scripting and content vulnerabilities as well as file space security weaknesses and transmission security flaws. The service produces a report on each scanned web page, leaving it up to the user to find ways to close down any detected vulnerabilities.
Ratproxy is stored on a Google code archive and is free to use. It will install on Windows, Mac OS, Linux, and FreeBSD.
Who is it recommended for?
Like many widely-used pen testing tools, Ratproxy is free to use and old. Penetration testers don’t seem to be too worried that the software they used hasn’t been updated for a long time. The current version of Ratproxy was created in 2009. So, this code is even older than Skipfish.
Pros:
- Scans for a List of Weaknesses: Searches for content, scripting, and protocol vulnerabilities
- Relies on a Simple Lightweight Interface: A similar look to that of Skipfish
- Downloadable Software Package: Runs on Windows, macOS, Linux, and Unix
Cons:
- Outdated: The last update was in 2009
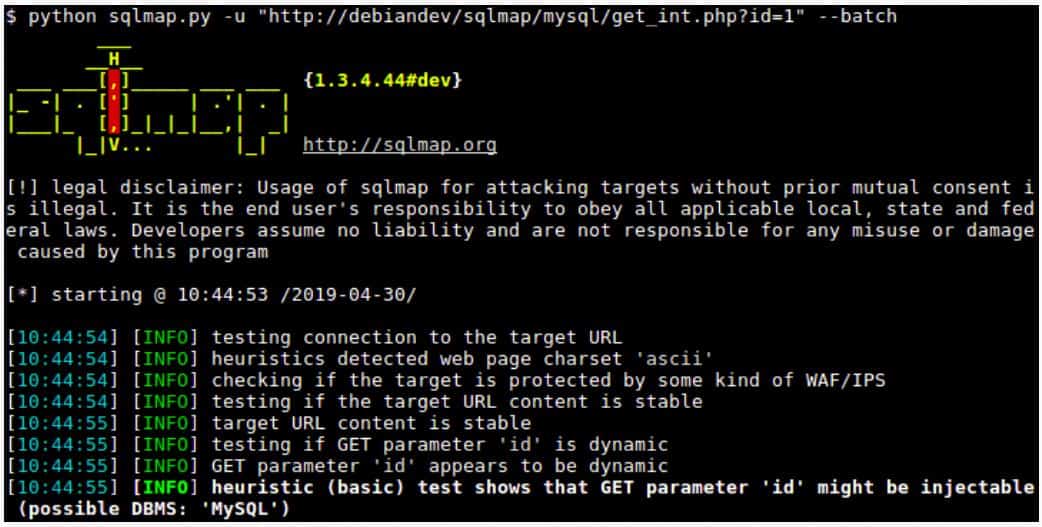
5. sqlmap
sqlmap is a free open source project with its code available on GitHub. As its name suggests, sqlmap focuses on SQL injection and database attacks.
Key Features:
- SQL Security: A very powerful tool
- Database Management Tools: One command with a long list of options
- Free to Use: Download it as a compressed file
Why do we recommend it?
The sqlmap is an unassuming command line tool. It has one command: sqlmap. However, the tool is brilliant and a very competent research system. It can reveal account credentials and technology details. This is another old program but it is regularly updated. Its many options take a long time to explore.
The tool is capable of probing a long list of DBMSs including MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, Informix, and MariaDB. As well as attempting a range of attacks to test for vulnerabilities, the tool has a range of database management utilities, such as password security and access rights checks.
sqlmap is written in Python and it will install on Windows, Linux, Mac OS, and FreeBSD.
Who is it recommended for?
This tool is free to use and very effective, so it is a good choice for any security consultant or penetration tester. It is also a good research tool for hackers. The utility is implemented y one command that has a long list of options. These take time to learn.
Pros:
- Useful Reconnaissance Services: Can discover database access credentials
- Hacker Tool: Compatible with a long list of DBMSs
- Multiple Platforms: Available for Windows, Linux, Mac OS, Free BSD
Cons:
- Command Line Tool: No GUI
6. Wfuzz
$ wfuzz -w wordlist/general/common.txt --hc 404 http://testphp.vulnweb.com/FUZZ ******************************************************** * Wfuzz 2.2 - The Web Bruteforcer * ******************************************************** Target: http://testphp.vulnweb.com/FUZZ Total requests: 950 ================================================================== ID Response Lines Word Chars Request ================================================================== 00022: C=301 7 L 12 W 184 Ch "admin" 00130: C=403 10 L 29 W 263 Ch "cgi-bin" 00378: C=301 7 L 12 W 184 Ch "images" 00690: C=301 7 L 12 W 184 Ch "secured" 00938: C=301 7 L 12 W 184 Ch "CVS" Total time: 5.519253 Processed Requests: 950 Filtered Requests: 945 Requests/sec.: 172.1247
>>> for r in wfuzz.get_payload(range(100)).fuzz(hl=[97], url="http://testphp.vulnweb.com/listproducts.php?cat=FUZZ"): ... print r ... 00125: C=200 102 L 434 W 7011 Ch "1" 00126: C=200 99 L 302 W 4442 Ch "2"
Wfuzz examines web traffic for site vulnerabilities. It will spot possibilities for XSS and SQL injection as well as LDAP access weaknesses and authentication loopholes. This testing tool is a “fuzzer”.
Key Features:
- A Suite of Command Line Tools: Additional utilities included with the main Wfuzz program
- Web Application Security Tester: Looks for weaknesses in web pages
- Free to Use: Get the code from GitHub
Why do we recommend it?
Strictly speaking, Wfuzz is more of a brute force values cracker for account credentials and other system properties of Web applications rather than a fuzzer. Fuzzing intentionally feeds in incorrect data to observe system responses, this tool hopes to hit the correct value by cycling through a word list.
Fuzzing involves giving a program an unexpected, random, or invalid input in order to test whether it will fall over or hang because the programmer didn’t include a routine to deal with such responses. Fuzzing is a typical hacking technique, so Wfuzz tries all of those strategies that the website might face and highlights attacks that the web applications currently can’t handle.
$ wfpayload -z range,0-5 0 1 2 3 4 5
Wfuzz is a command-line utility, so it isn’t very attractive. Calls to this command can be built into scripts for test automation, enabling savvy users to build more comprehensive reports out of it. The utility is free to use and it will install on Windows, Mac OS, Linux, and FreeBSD. Wfuzz supports Python 3.
$ wfencode -e md5 test 098f6bcd4621d373cade4e832627b4f6
Who is it recommended for?
You could use this system for fuzzing by looking at the failed attempts rather than those that succeed. The package also includes a word list generator but you can also find your own dictionary to provide inputs. Like all of the other systems on the list, this free tool takes time to learn.
Pros:
- Can be Called From Scripts: Automates testing
- A Fuzzer: Tests systems using random inputs and packet injection
- Multiple Platforms: Runs on Windows, macOS, Linux, and FreeBSD
Cons:
- Only Available as a Command-Line Tool: No data visualization
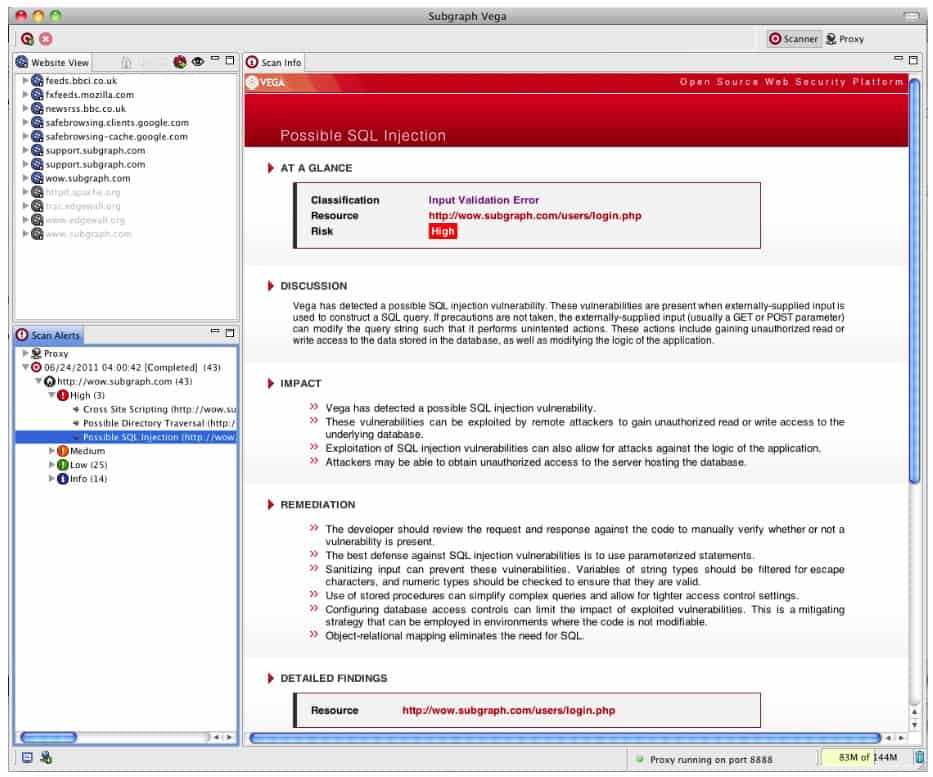
7. Vega
Vega is a bundle of vulnerability scanning services, which includes a proxy. There are three elements in this suite: Vega Scanner, Vega Proxy, and Proxy Scanner – each has its own capabilities for testing different aspects of a website’s delivery. The package has an attractive GUI interface, which makes this the easiest to use of all the Paros Proxy replacements on this list.
Key Features:
- GUI Interface: Presentable screens
- Proxy Configuration: Intercepts Web page code transfers to browsers
- Free-to-Use: Open source
Why do we recommend it?
Vega has a few advantages over most of the other tools on this list. First of all, it has a GUI interface, which is a lot easier to use than command line systems, such as sqlmap and Wapiti. Another attraction that this system holds is its choice of modes. You can use it as an automated scanner or as a proxy for penetration testing.
The proxy allows the use of Firefox or Chrome for testing and can assist in the assessment of SSL certificate validity as well as checking for vulnerabilities and loopholes in the web applications system.
The tool will check for susceptibility to XSS and SQL injection as well as examining access to directories and backups. Vega installs on Windows, Linux, and Mac OS and it is free to use. The software is very extensively documented with complete instructions available on how to download, install, adapt, and run the utility.
Who is it recommended for?
Vega has a wider audience than many of the other tools on this list. It is free to use, which is an appealing feature for penetration testers. Vega is also a good alternative to the commercial vulnerability scanners that are available on the market, so it could be a money saver for system administrators.
Pros:
- Scanner Mode: Provides a vulnerability scanner
- Can Validate SSL Certificates: Also checks on TLS procedures during HTTPS session establishment
- Multiple Platforms: Available for Windows, macOS, and Linux
Cons:
- Can Take Time to Fully Explore the Platform: Fortunately, there is a comprehensive guide available
8. w3af
w3af is available from a GitHub repository. It is a widely used free web vulnerability testing platform. The name “W3af” is an abbreviation of Web Application Attack and Audit Framework. The code for the platform can also be downloaded from the W3af website, which also has an extensive and well-presented documentation library.
Key Features:
- Well-Known Tool: Widely used by penetration testers
- Extendable: A library of plug-ins
- Free to Use: Available on GitHub
Why do we recommend it?
W3af is a highly respected and free vulnerability scanner. Its GUI presentation should make it accessible to system administrators who are not cybersecurity specialists, except that the system of loading in plug-ins to get functions added to the tool makes using the package complicated.
The vulnerability detection strategies of W3af are dictated by plug-ins. Like the app itself, plugins are free and can be downloaded from the W3af website. The tool has a useful GUI interface, which makes operating the system and checking through results a very simple task.
The scanner will look for 200 vulnerabilities in a site, which include SQL injection, XSS, unprotected resources, and loose authentication systems.
A community forum at the W3af website gives access to tips and tricks from other users and the site also has a blog, which explains the current state of cybersecurity and alerts to new threats.
W3af installs on Linux, Mac OS, and BSD Unix.
Who is it recommended for?
You would need to dedicate time to learn how to use W3af and the purpose of each of the 200 plug-ins to get the best out of this system. That means the system is not quite as “out-of-the-box” as commercial vulnerability scanners. Therefore, you would be more likely to use W3af if you are a cybersecurity professional.
Pros:
- Features a Simple GUI Interface: More presentable than command line tools
- Can Scan for Over 200 Vulnerabilities: Tries SQL and XSS attacks among other tests
- Multiple Platforms: Runs on Linux, macOS, FreeBSD, and OpenBSD
Cons:
- Development is Slow: Updates are infrequent
Replace Paros Proxy
Although you might be very pleased with Paros Proxy, it is time to move on. Even the developers behind the tool have given up on it. This guide has given you some really attractive replacements to Paros Proxy and even includes the utility’s heir, the OWASP ZAP system.
Take a look at the attractive GUI interfaces that W3af and Vega have to offer. These consoles make vulnerability scanning a lot easier and they have search and filtering utilities to make diagnoses of the results into a straightforward task.
Paros Proxy FAQs
What is Paros proxy used for?
Paros Proxy is a penetration testing tool that intercepts traffic between a Web server and a proxy browser to see all of the transactions that take place in order to deliver the code for a page. This tool lets a tester see live activity as the Web page is used, which includes the transport of the data that users enter into fields in the page.
What is the port used for internal SSL handling in Paros?
Paros Proxy uses port 8443 for internal SSL handling. All other traffic, for example for the proxy connection, goes to port 8080.
Replacement for paros proxy?
Good alternatives for Paros Proxy are:
- OWASP ZAP
- Grabber
- Wapiti
- Skipfish
- Ratproxy
- SQLMap
- Wfuzz
- Vega
- W3af