HUMAN (formerly PerimeterX) provides cloud-based platform-agnostic application security solutions that leverage machine learning and behavior-based analytics to protect online businesses while preserving user experience. HUMAN Security products detect and block automated bot attacks and client-side threats before they affect your web and mobile applications or APIs. This helps to reduce your risk, protect users and partners, and safeguards proprietary content.
Overview of HUMAN Platform
HUMAN platform includes the following essential products:
- HUMAN Bot Defender A behavior-based bot management solution protecting your websites, mobile applications, and APIs from automated attacks. It combines intelligent fingerprinting, behavioral signals, and predictive analysis to detect bots on web and mobile applications and API endpoints.
- HUMAN Code Defender A client-side application security solution that protects websites from digital skimming, formjacking, and Magecart attacks, Code Defender detects suspicious script behavior by automatically inventorying and baselining the conduct of all client-side JavaScript on your website.
- HUMAN Page Defender Preserves the intended online shopper experience by blocking unwanted coupon extensions and ad injections that steal your users and redirects them to competitors. Eliminating these pop-ups means you can prevent your site visitors from getting redirected to competitors, hide unauthorized content from being shown on your site, take back control of the shoppers’ experience and keep them on the path to purchase.
The HUMAN platform provides other services and tools such as behavior-based predictive analytics, machine learning models, sensors, detectors, and enforcers. It also features a user-friendly portal with advanced analysis and reporting capabilities that give you actionable insights. Although HUMAN does not offer a free trial, a free online product demo is available on request.
Here is our list of the best Human alternatives:
- Qualys Cloud Platform This system includes agents that need to be installed on the systems that host the applications that are going to be tested and it will continuously scan applications for security weaknesses.
- Barracuda Web Application Firewall This service implements vulnerability scanning and then applies the same checks during live operations. A free scanner is available.
- Invicti This scanner can be set up for continuous testing on a CI/CD pipeline for web application developers. Delivered as a SaaS platform or software for Windows Server.
- Acunetix This package implements dynamic application security testing (DAST) for DevOps teams. Available for Windows, macOS, and Linux.
- Akamai Bot Manager A cloud platform that identifies and blocks all forms of automated attacks, such as DDoS and click fraud.
- Imperva Bot Protection This protection system against automated attacks is delivered from the cloud.
- Signal Sciences A cloud platform that provides a mix of detection services to block threats to websites, web applications, and APIs.
- DataDome The bot-blocking cloud platform stops DDoS attacks and payment frauds.
You can read more about each of these solutions in the following sections.
If you’re considering a suitable alternative, like HUMAN, you will find lots of them. However, you want to ensure you get the same functionality from an alternative tool. So, we’ve compiled a list of the eight best HUMAN options. Hopefully, this will guide you in the process of selecting the right one for your environment.
Our methodology for selecting the best HUMAN alternatives
We’ve broken down our analysis for you based on these key criteria:
- Comprehensive Security Features: Evaluating the breadth and depth of security measures each tool offers, such as DDoS protection, vulnerability scanning, and bot management.
- User Experience: Considering the ease of use, interface intuitiveness, and customization options to ensure the tools are accessible for a range of users.
- Integration Capabilities: Assessing how well each tool integrates with other systems and platforms, such as cloud services and DevOps pipelines, to ensure seamless operation within diverse environments.
- Performance Impact: Examining the tools’ impact on application and network performance to ensure they provide security without significant performance degradation.
- Scalability and Flexibility: Looking at the ability of the tools to scale with growing needs and their flexibility to adapt to different organizational requirements and sizes.
The best HUMAN alternatives
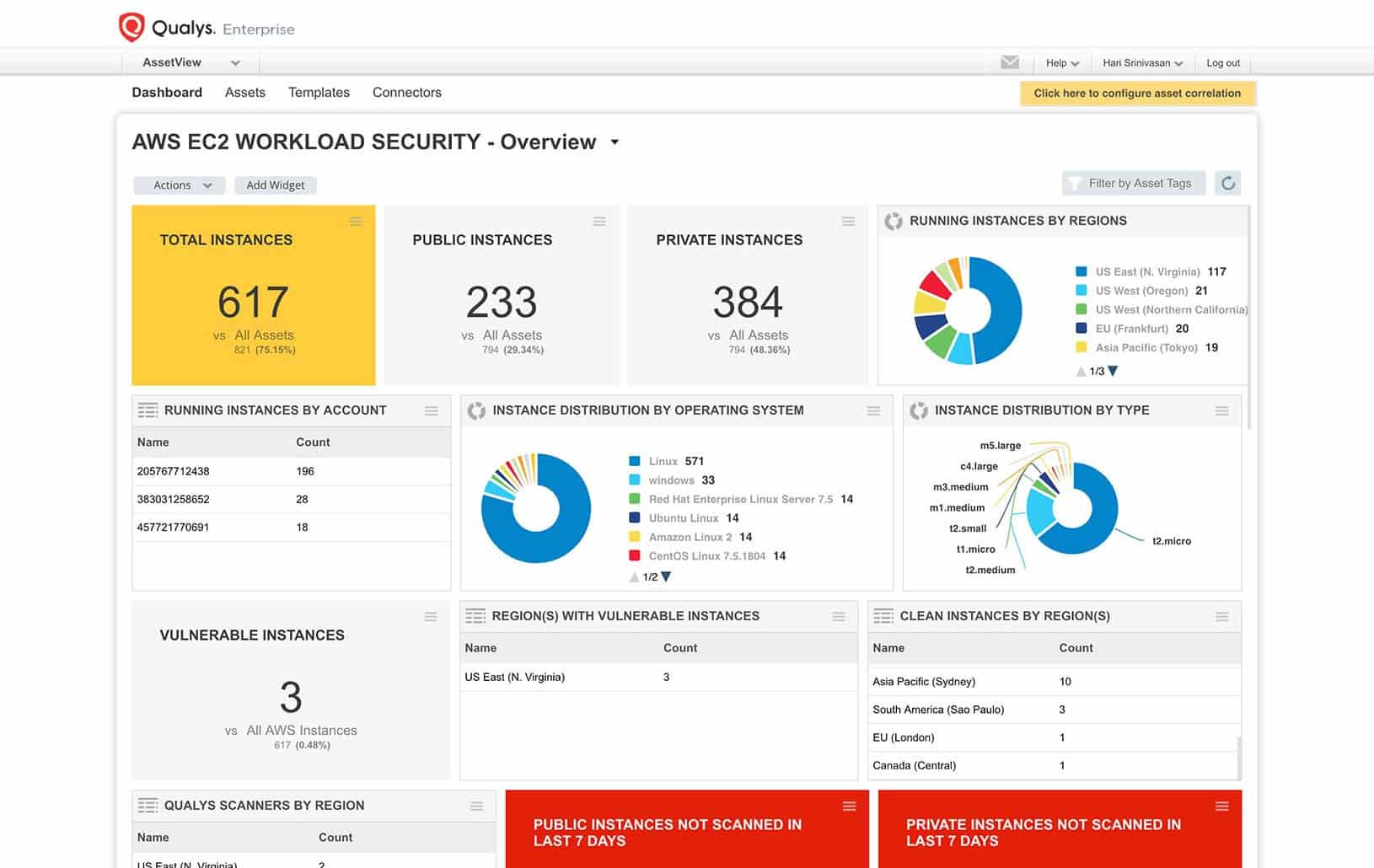
1. Qualys Cloud Platform
Qualys is one of the first cloud-based information security and compliance solutions providers. Qualys security services include vulnerability management, detection & response, threat protection, patch management, endpoint detection & response, cloud security assessment, web app scanning, and a firewall.
Key Features:
- Vulnerability Scanning: Identifies and reports on system vulnerabilities.
- Attack Surface Management: Manages and reduces potential attack surfaces.
- Risk Assessment: Evaluates and prioritizes security risks.
- Compliance Management: Ensures adherence to data protection standards.
- Cross-Platform Monitoring: Monitors security across various platforms.
Why do we recommend it?
Qualys Cloud Platform provides agents that need to be installed on each server or cloud platform in your IT system. It then scans each for configuration problems and looks through each of your software systems for weaknesses. The platform also provides external scans of your system from its own location.
The Qualys Cloud Platform, combined with its lightweight Cloud Agents, Virtual Scanners, and Network Analysis capabilities, brings together all four critical elements of effective vulnerability management into a single app. As a result, Qualys vulnerability management helps organizations discover every asset in their environment, assesses these assets for the latest vulnerabilities, and automatically deploys remediation.
Who is it recommended for?
Qualys is a classic vulnerability scanner with both internal and external scans. Although the service stresses its risk assessment, this is an automated attack vulnerability tester rather than a business risk assessor. The platform produces compliance reporting, so this is a suitable package for companies that need to comply with a data protection standard.
Pros:
- Continuous Vulnerability Monitoring: Provides ongoing scanning and detection of system vulnerabilities.
- Lightweight Operation: Functions efficiently as an online service with minimal impact.
- Automated Threat Remediation: Automatically addresses identified threats.
- User-Friendly Interface: Features an intuitive and accessible user interface.
Cons:
- Not Ideal for Small Networks: May be too robust for smaller network environments.
Qualys Web Application Scanning (WAS) provides automated crawling and testing of web applications and APIs to find and fix security vulnerabilities, including cross-site scripting (XSS) and SQL injection. A free 30-day trial of the Qualys Platform is available on request.
EDITOR'S CHOICE
Qualys Cloud Platform is our top choice for information security and compliance because it offers comprehensive vulnerability management and threat protection. Its lightweight Cloud Agents, Virtual Scanners, and Network Analysis capabilities integrate seamlessly to provide continuous monitoring and automated remediation. The platform’s ability to discover every asset in an environment, assess vulnerabilities, and ensure compliance makes it invaluable.
We found the user interface particularly intuitive, making it easy to navigate and configure. The cross-platform monitoring ensures that both internal and external threats are addressed efficiently. Qualys stands out for its robust feature set, making it the best option for enterprises needing extensive security solutions.
Download: Download a 30-Day Free Trial
Official Site: https://www.qualys.com/enterprise-trurisk-platform/
OS: Cloud-Based
2. Barracuda Web Application Firewall
Barracuda Networks is a leading provider of networking, storage, and security products. The company’s security products cut across network security, data and email protection, and application security. Barracuda’s application security solution is the Barracuda Web Application Firewall.
Key Features:
- Comprehensive Protection: Safeguards websites, web applications, and APIs.
- Web Application Firewall: Provides robust defense against application attacks.
- Managed Service Option: Offers a managed service for ease of use.
- AI-Based Security: Utilizes AI for enhanced threat detection and prevention.
Why do we recommend it?
The Barracuda Web Application Firewall provides protection from bot attacks in the form of DDoS surges and click fraud. This system uses both live scanning that can implement zero-day protection and a threat intelligence feed that acts as a blacklist of traffic source addresses.
This solution protects your websites, mobile and web applications, and APIs against various application attacks, including OWASP Top 10, client-side attacks, DDoS, and bot attacks that use scraping, denial of inventory, and credential stuffing. It is an integrated platform that brings together a set of security tools to ensure the complete protection of your critical application. It supports applications deployed on-premises, in the cloud, or a hybrid. As well as protecting web applications and websites, the WAF has a feature to protect APIs. The package includes a security policy automation service and a bot protection system.
Barracuda Bot Protection scans incoming application traffic to identify and stop bots from scraping confidential data, skewing web analytics, and impairing website performance. It combines threat intelligence with machine learning to identify and detect bots and other advanced attackers.
Who is it recommended for?
This product is designed for businesses that either manage or rely on web applications. So, that includes businesses that run an eCommerce model or those that provide access to their services through mobile apps. The company also offers an email protection plan to block automated email attacks, such as spam and phishing.
Pros:
- User-Friendly Interface: Easy-to-use interface that scales well for complex networks.
- Built-In IDS: Includes an Intrusion Detection System for early threat detection.
- Enterprise-Friendly: Ideal for large networks and enterprises requiring advanced security features.
- Customizable Dashboard: The NexGen Admin dashboard is highly customizable for detailed insights and reporting.
Cons:
- Complex for Smaller Networks: Many features may be excessive for smaller networks.
- No Immediate Free Trial: Requires a manual request for an evaluation version from the sales team.
Barracuda provides a free web application vulnerability scanner to find and fix hidden security flaws. A free trial of the Barracuda application security solution is also available on request.
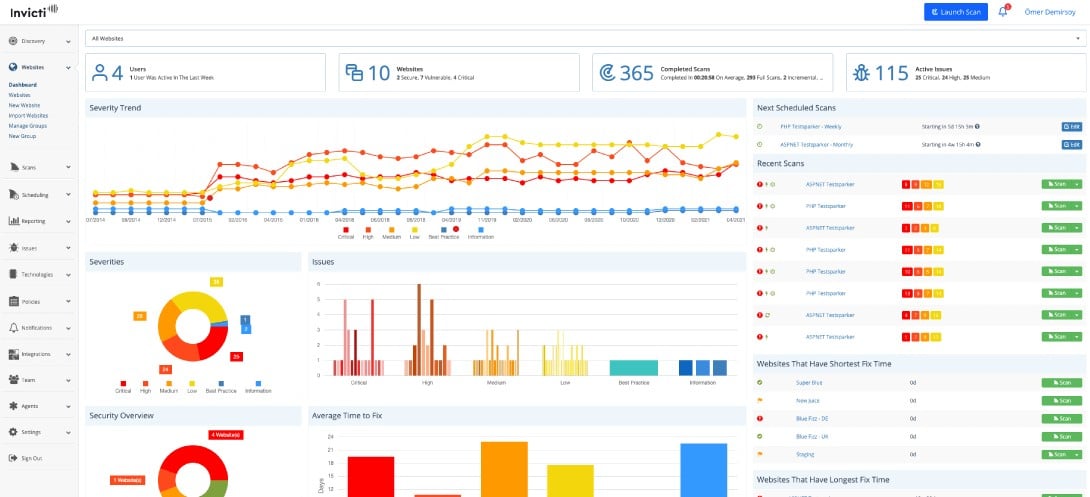
3. Invicti
Invicti, formerly known as Netsparker, is an easy-to-use application security solution that enables you to scan web applications, websites, and services for security flaws. It uses a heuristic-based approach to detect vulnerabilities, making it easier to identify zero-day vulnerabilities in web applications.
Key Features:
- Vulnerability Scanning: Detects security flaws in web applications, websites, and services.
- Attack Surface Management: Identifies and manages potential attack vectors.
- Continuous Testing: Provides ongoing testing throughout the development lifecycle.
Why do we recommend it?
Invicti is a DevOps tool. That is, it can be used both for checking on web applications under development and by operations teams that support live web applications. The tool implements dynamic application security testing, which means that it runs an application with a range of inputs and notes what happens.
Invicti also uses a proprietary technology called Proof-Based Scanning to safely exploit identified vulnerabilities and automatically create a proof-of-exploit to show that it’s not a false positive. With Proof-Based Scanning technology, you can build DAST into your software development lifecycle (SDLC) to eliminate vulnerabilities before they can reach production.
Who is it recommended for?
The system can be set up as a vulnerability scanner with plan option for on-demand and monthly scans or a more frequent scanning cycle. Development teams use the tool for continuous testing in a CI/CD pipeline. The use of the tool depends on its plan. It can also be used for penetration testing.
Pros:
- Intuitive Admin Dashboard: Features a user-friendly and insightful dashboard.
- Framework-Agnostic Support: Compatible with any web application, web service, or API framework.
- Streamlined Reporting: Offers detailed reports with prioritized vulnerabilities and remediation steps.
- Proof-Based Scanning: Eliminates false positives by safely validating vulnerabilities.
- DevOps Integration: Integrates smoothly into DevOps workflows, offering quick feedback for bug prevention.
Cons:
- Limited Trial Availability: Offers a demo instead of a full trial period for testing.
The vulnerabilities Invicti scans for are listed in the Top 10 list of most critical security risks. It’s targeted at small and medium businesses and doesn’t require deep IT security knowledge to use. The product is available in three editions: Standard, Team, and Enterprise. In addition, a free online demo is available.
4. Acunetix
Acunetix is an automated web application security testing tool designed to help small and mid-size organizations find and fix exploitable vulnerabilities that put their web applications at risk of attack. Acunetix automatically discovers and creates a list of your websites, web applications, and APIs and scans them for security holes. Acunetix comprises the following key components:
- AcuSensor Technology An optional component of Acunetix, which you can use for free with all product licenses.
- AcuMonitor A service that allows the scanner to detect out-of-band vulnerabilities. This service is automatically used by out-of-band checks and requires no installation or configuration, only simple registration for on-premises versions.
- DeepScan Technology Acunetix DeepScan technology enables it to crawl and scan even the most complex website or web application to find all possible entry points.
Key Features:
- External Attack Surface Assessments: Evaluates vulnerabilities from an external perspective.
- Internal Scanning: Conducts in-depth scans within the network.
- Application Security Testing: Tests the security of web applications, websites, and APIs.
Why do we recommend it?
Acunetix is a similar product to Invicti. In fact, both systems are owned by the same company. However, they have different histories, coming to the company’s ownership by different routes. A big distinction of Acunetix is that it can plug in OpenVAS, a free vulnerability scanner.
Who is it recommended for?
The OpenVAS extension of Acunetix makes this package interesting to system administrators who want to assess network vulnerabilities. However, that system is available for free separately for anyone, so it can be used alongside any vulnerability scanner or web application security tester. The core of Acunnetix has the same DevOps market as Inviciti.
Pros:
- Application Security Focus: Specifically designed for identifying and addressing web application vulnerabilities.
- Tool Integration: Integrates seamlessly with various tools, including OpenVAS.
- Misconfiguration Alerts: Detects and alerts on system misconfigurations.
- Automated Threat Response: Uses automation to stop threats and escalate issues based on severity.
Cons:
- Limited Trial Availability: Does not offer a full trial version for testing purposes.
The product is available in three editions: Standard, Premium, and Acunetix 360, designed to meet the needs of a specific segment of end-users. All three editions can scan for the OWASP Top 10, and are particularly strong at detecting web application security issues such as cross-site scripting, SQL injection, reflected XSS, CSRF attacks, and directory traversal, among others. A free demo is available on request.
5. Akamai Bot Manager
Akamai Bot Manager is designed to help organizations manage the impact of bots across their entire digital environment, including websites, mobile applications, and web APIs. It helps organizations detect bots interacting with their web application or website and categorize them based on their role or value. It also gives you the flexibility to apply different management actions based on the category a bot belongs to.
Key Features:
- Good and Bad Bot Identification: Differentiates between beneficial and malicious bots.
- Automated Attack Blocking: Prevents various types of automated attacks.
- Web Usage Statistics Cleaning: Ensures accurate web analytics by filtering bot traffic.
Why do we recommend it?
Akamai Bot Manager provides an assessment for each request for access to web applications, particularly websites. The platform is set up as a referral service that is accessed by a web server through a plug-in. The system presents a score, which can be used to selectively block or allow a request.
Akamai Bot Manager employs a variety of detection techniques such as pre-defined signatures, bot reputation, and real-time detections capabilities to identify unknown bots as they attempt to access protected websites, including:
- Behavior anomaly analysis Collects telemetry from client input devices, such as mouse movements and keyboard strokes, to identify abnormal behavior that distinguishes between human and bot
- Browser fingerprinting Collects identifying client browser information and analyzes them to identify anomalies that indicate an automated bot
- HTTP anomaly detection Employs a risk-scoring model to inspect HTTP requests for patterns and anomalies that indicate they were generated by an automated bot attempting to disguise itself as a legitimate bot
- Rate-based and session activity Looks for differences in the behavior of a web client to that of human users
- Workflow validation Allows an organization to define a workflow for its website that a human user would follow and take action on clients that deviate from the specified workflow
Who is it recommended for?
This service will interest any business that runs a website. Although bot assessments can be applied to web applications in general and mobile apps as well, websites are more vulnerable to bot activity because they have addresses that can be targeted. Bot activity can be used by a competitor to mislead a web-based business of the relative success of pages and features.
Pros:
- Comprehensive DDoS Protection: Blocks multiple types of DDoS attacks, including SYN, UDP, and POST floods.
- Post-Attack Insights: Provides advanced insights after an attack to enhance future security measures.
- Proactive Attack Surface Reduction: Automatically reduces potential attack surfaces before an attack occurs.
Cons:
- No Free Trial: Does not offer a free downloadable trial for testing.
- Complex Features for Small Networks: Smaller networks may not fully utilize features like hybrid cloud protection.
Bot Manager is deployed at the network edge (Akamai Intelligent Edge Platform) to enable you to detect and mitigate bot traffic before it hits valuable targets. It also integrates visualization and reporting of bot traffic into Akamai Security Center, which displays overall bot traffic statistics and other types of attack traffic. A live demo with simulated attacks is available on request.
6. Imperva Bot Protection
Imperva is a cyber security software and services company protecting enterprise data and applications in the cloud or on-premise. The Imperva application security platform gives organizations visibility and control over human and malicious bot traffic, including the ability to detect and mitigate OWASP Top 10 vulnerabilities without imposing friction on legitimate users.
Key Features:
- Application Security: Protects web applications from OWASP Top 10 vulnerabilities and other threats.
- Network Security: Defends against network intrusions and DDoS attacks.
- Data Security: Safeguards sensitive data from theft and breaches.
Why do we recommend it?
Imperva uses threat detection procedures to block application attacks, network intrusion, and data theft. All of these areas of competence involve bot detection. However, it is a bigger element in the Application Security category. The typical bot threat to applications are DDoS attacks on websites. The tool focuses on a range of fraud attacks.
Imperva’s Advanced Bot Protection protects websites, mobile apps, and APIs from automated threats. This includes web scraping, account takeover, transaction fraud, denial of service, competitive data mining, unauthorized vulnerability scans, spam, click fraud, and web and mobile API abuse. All without impacting application performance or user experience.
In addition, it checks that each browser has the correct JavaScript engine, is formatted correctly, and all components perform as they should. This helps to distinguish between browser automation tools and legitimate users.
Who is it recommended for?
This system is particularly strong at protecting websites and it is part of an armory of protection systems that are contained in the Imperva WAF. The tool looks for bad bots that are engaged in click fraud, payment fraud, and credentials cracking as well DDoS.
Pros:
- Comprehensive Audits and Compliance: Offers in-depth compliance audits and breach detection, ideal for enterprises.
- Flexible Deployment Options: Available as both a cloud product and an on-premise solution.
- Effective Fraud Detection: Identifies and mitigates click fraud, payment fraud, and credential cracking.
Cons:
- Not Ideal for Smaller Organizations: Many features are tailored for larger enterprises with extensive compliance needs.
| Deployment Model | Integrated within Imperva’s Cloud Application Security | Connectors |
|---|---|---|
| Ideal For | Companies seeking a single stack security solution offering CDN, WAF, DDoS, and Advanced Bot Protection | Companies that want Advanced Bot Protection to integrate with already deployed popular technologies. Available Connectors: AWS, Cloudflare, F5, NGINX, Fastly |
Table 1.0 | Imperva’s Advanced Bot Protection deployment options
Table 1.0 above describes the available deployment options. In addition, a personalized online demo and a free trial are available on request.
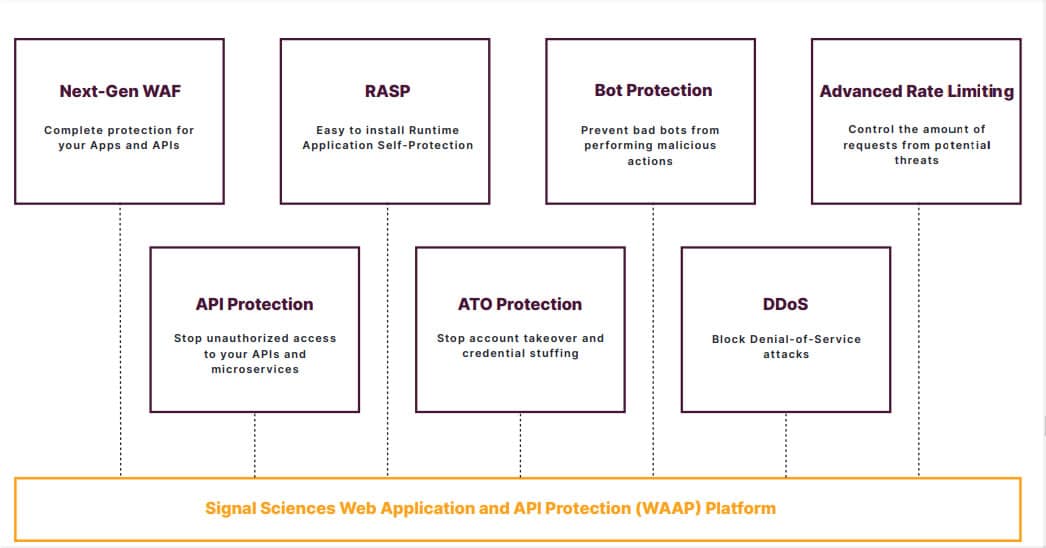
7. Signal Sciences
Signal Sciences is a SaaS-based security technology company that provides a Web Application and API Protection (WAAP) Platform. Signal Sciences was named a 2021 Gartner Peer Insights Customers’ Choice for WAF.
Some of the critical application security tools included in the platform are:
- Web Application Firewall (WAF) Signal Sciences next-generation WAF creates a protective shield between your web app and the internet to help mitigate many common attacks.
- Bot Protection Signal Sciences monitors web application and API traffic to detect and block automated malicious bots, including bots that engage in message spamming, content scraping, credit card, and inventory abuse, among others.
- Runtime Application Self-Protection (RASP) Designed to provide personalized protection to your applications using runtime instrumentation to detect and block attacks by taking advantage of information from inside your application in real-time.
- Account Takeover (ATO) Protection Detects and blocks credential stuffing and account takeovers attempt
- Rate Limiting Controls the number of requests from potential threats to prevent abusive behavior at the application layer that negatively impacts website and API performance.
- DDoS protection Signal Sciences Cloud DDoS protection blocks network and application layer DDoS attacks to keep your web apps and APIs available for customers.
Key Features:
- Edge Service: Enhances security by operating at the network edge.
- Run-Time Security: Provides real-time protection using runtime instrumentation.
- Bot Protection: Detects and blocks malicious bots whilst allowing good bots through.
Why do we recommend it?
The Signal Science platform provides a list of modules that combine to protect web applications as they operate. The WAF blocks hacker attacks and malware while the Bot Protection module identifies automated attacks. The system blocks bad bots while letting good bots, such as search engine crawlers, through.
Who is it recommended for?
This package is suitable for businesses that run websites. It is particularly good at spotting fraud attempts, particularly payment fraud. However, it also provides protection against account takeover, scraping, and click fraud. Attacks from rivals, such as inventory hoarding and message spamming are also blocked.
Pros:
- User-Friendly Interface: Features a sleek, easy-to-use interface.
- Simplifies RASP: Effectively simplifies complex Runtime Application Self-Protection environments.
- Lightweight Performance: Protects without significantly impacting application performance.
- Comprehensive Threat Detection: Identifies API abuse, account takeover attempts, and other threats.
Cons:
- Steep Learning Curve: Can take time to fully explore and utilize all available options.
Signal Sciences can be deployed in containers, on-premises, or the cloud and allows you to gain one unified view across your entire application. A free online demo is available on request.
8. DataDome
DataDome provides cloud-based online fraud and bot management services that protect mobile apps, websites, and APIs from web scraping, scalping, credential stuffing, account takeover, Layer 7 DDoS attacks, and carding fraud. DataDome’s mission is to free the web from fraudulent traffic so that sensitive data remains safe and online platforms can perform at optimum speed.
Key Features:
- Online Fraud Protection: Protects against various types of online fraud.
- Scraping Prevention: Blocks web scraping attempts.
- Click Fraud Combat: Detects and mitigates click fraud.
Why do we recommend it?
Data Dome is a bot management system that identifies and blocks automated attacks. The tool will automatically present a CAPTCHA challenge if a visitor’s actions raise alarms while leaving the majority of visitors unmolested. This is a useful service for companies that find web visitors are deterred by a CAPTCHA challenge that is applied automatically.
DataDome uses AI and machine learning to determine whether a traffic or user account is a human or a bot by analyzing billions of events. Once a bot-driven fraud attempt is detected, DataDome blocks it right away without impacting business operations.
The rules used by DataDome to protect your applications from threats are ordered into the following four different categories:
- Signature-Based Detection They leverage fingerprinting, such as browser fingerprint, HTTP header, and TLS fingerprint, to identify malicious traffic
- Behavioral detection Detects threats based on behavior not linked to human activity, such as too many login attempts.
- Reputational detection Detecting threats based on requests originating from an IP with a poor reputation or IP that recently acted maliciously.
- Vulnerability Scanner detection Detects threats by finding possible internal weaknesses and security vulnerabilities.
Who is it recommended for?
This package is particularly useful for websites and mobile apps that deploy user accounts. It’s detection methods track user activities and so it can identify fake users before they get to the point of trying to buy. The system can also spot account takeover.
Pros:
- User-Friendly Interface: Simple and intuitive, allowing for extensive customization.
- Fully Cloud-Based: Provides flexibility and ease of deployment.
- Dual Detection Methods: Utilizes both signature and behavioral detection for comprehensive protection.
- Automated and Manual Scans: Supports both automated and manual scanning options.
Cons:
- Learning Curve: Can take time to fully explore and utilize all available features.
DataDome provides a tool to check your site for bad bots slowing down your website performance and impacting the customer experience. A personalized online demo and a free 30-day trial are available on request.