In Active Directory (AD), FSMO (Flexible Single Master Operations) roles are critical functions that are assigned to specific domain controllers to ensure proper AD replication and operations across the network. These roles are vital for managing the database and ensuring consistency and integrity within an AD environment. There are five FSMO roles, divided across different domain controllers:
- Schema Master – Controls changes to the AD schema.
- Domain Naming Master – Manages domain and trust relationships.
- RID Master – Allocates RID pools to domain controllers.
- PDC Emulator – Acts as a primary time server and handles password changes.
- Infrastructure Master – Updates cross-domain references.
To query FSMO roles in Active Directory, you can use several methods. The most common are using PowerShell or the ntdsutil tool. These commands can help identify which domain controllers hold the FSMO roles, which is important for troubleshooting, migrations, or domain controller planning. Querying FSMO roles can also help in confirming the operational state of critical AD infrastructure.
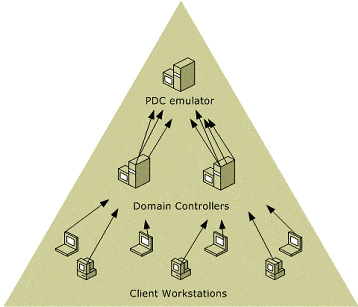
FSMO in the AD Architecture
The AD structure is organized into domains, forests, and trees, each playing a key role in the logical organization and management of resources across the network. These components are important when querying FSMO roles, as they determine how AD objects are organized and how FSMO roles are distributed.
- Domain: A domain is the fundamental unit of Active Directory’s logical structure. It represents a collection of objects (like users, computers, and groups) that share a common directory database and security policies. Each domain is identified by a unique name, such as example.com. Domains are also the primary boundary for applying Group Policy settings and managing permissions.
- Tree: A tree is a collection of one or more domains that share a contiguous namespace. Domains within a tree are connected in a hierarchical relationship, with the root domain at the top. The domains in a tree trust each other by default, allowing users in one domain to access resources in another without needing separate credentials.
- Forest: A forest is the highest level of AD’s logical structure and represents a collection of one or more trees. A forest can include multiple trees, which may or may not share a common namespace. Forests establish the trust relationships between all domains within them, ensuring global access to objects and services. The forest also defines the schema and global catalog for the directory.
When querying FSMO roles, the domain controller holding each FSMO role will be part of a specific domain, and that domain might belong to a tree or forest. The configuration of these components is crucial for understanding where and how FSMO roles are assigned, as some roles, such as the Schema Master and Domain Naming Master, apply across the entire forest, while others, such as the RID Master and PDC Emulator, are domain-specific.
Understanding Multi-master and Single-master Model
There are two standard models used for database update and replication in Active Directory:
- Multi-master replication
- Single-master replication
A multi-master enabled database, such as the Active Directory, provides the flexibility of allowing changes to occur at any DC in the enterprise. The multi-master database model will allow data to be stored by multiple DCs, and updated by any. All members are responsible for client data queries, propagating each member’s data modifications to the rest of the group, and resolving any conflicts between concurrent changes made by different members. However, there are times when conflicts become too difficult to determine. In such cases, it’s best to prevent the war from happening rather than attempt to resolve it after the fact.
The Active Directory performs updates to particular objects using the single-master approach to prevent conflicting updates in Windows. This is referred to as the single-master model. In this model, one DC acts as the master (authoritative source) and controls one or more synchronized to it. Only one DC in the entire directory is allowed to process updates. Active Directory extends the single-master model to include multiple roles and transfer roles to any DC in the enterprise.
Since Active Directory roles are not tied to a single DC, such a model offers a lot of flexibility. This is referred to as Flexible Single Master Operation (FSMO) Roles.
Understanding FSMO Role Assignment
Before discussing how to query FSMO roles in AD, let’s first examine each FSMO role and its relation to the Active Directory. For example, in Windows, there are five FSMO roles, which are described in detail below:
- Schema master: The Schema master is a forest-specific FSMO role located in the forest root domain. The purpose of this role is to replicate schema changes to all other domain controllers in the forest. The schema master FSMO role holder is the DC responsible for performing updates to the directory schema. This DC is the only one that can process updates to the directory schema. Once the Schema update is complete, it’s replicated from the schema master to all other DCs in the directory.
NOTE: Thus, there’s only one schema master per directory.
NOTE:Failure of this role to function correctly can prevent the addition of a new child domain or new domain tree.
NOTE: There’s one RID master per domain in a directory.
- A domain SID that’s the same for all SIDs created in a domain.
- A relative ID (RID) that’s unique for each security principal SID created in a domain.
NOTE: PDC emulator: The PDC emulator is another domain-specific FSMO role, and there is one PDC emulator for each domain in a forest.
- Password changes done by other DCs in the domain are replicated preferentially to the PDC emulator.
- When authentication failures occur at a given DC because of an incorrect password, the losses are forwarded to the PDC emulator before a wrong password failure message is reported to the user.
- Account lockout is processed on the PDC emulator.
- In a multi-domain forest, the PDC emulator in each domain synchronizes to the forest root PDC emulator. All other domain member computers synchronize to their respective domain controllers.
[/ctech_content_w_bk]
Those are the various FSMO roles in Active Directory as described above. It is best practice to have the FSMO parts divided so that standby DCs can be ready to take over each role. The PDC emulator and the RID master should be on the same DC, if possible. The Schema Master and Domain Naming Master should also be on the same DC. When an FSMO role is transferred to a different DC, the original FSMO holder and the new FSMO holder communicate to ensure no data is lost during the transfer. If the original FSMO holder experienced an unrecoverable failure, another DC could be made to take over (seize) the lost roles. This prevents the domain controller from hosting that FSMO role again, except for the PDC Emulator and Infrastructure Master Operation roles.
How to Query FSMO Roles
As a domain administrator, it’s essential to know where the roles are installed in your AD environment. This prepares you to respond better when a disaster occurs. In this article, we will show you two simple methods for querying FSMO roles. The first method uses the Netdom query tool, and the second uses Windows PowerShell.
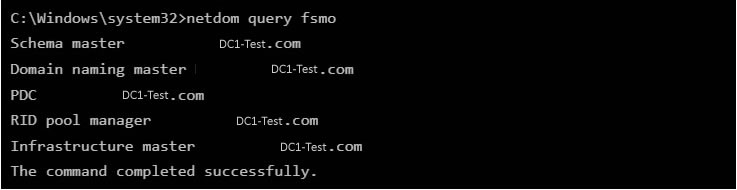
Method 1— Netdom query FSMO command-line tool: Netdom is a command-line tool that allows management of Windows domains and trust relationships. The tool has been built into Windows Server OS since 2003. It is available if you have the Active Directory Domain Services (AD DS) server role installed. We are going to use the Netdom tool to check the FSMO roles. The steps are as follows:
- Open and run the command prompt as admin on your domain controller.
- Enter the command: netdom query fsmo
- The output will show all of the FSMO roles and which domain controller holds them.
Method 2— PowerShell Get FSMO Roles: The PowerShell method for getting FSMO roles requires you to check the domain-wide and forest-wide roles separately. This involves two lines of commands, one to return the forest roles and another to produce the domain roles as shown below:
- Open and run PowerShell as admin on your domain controller
- Enter the command below to return the forest FSMO roles:
Get-ADForest domainname | Format-Table SchemaMaster,DomainNamingMaster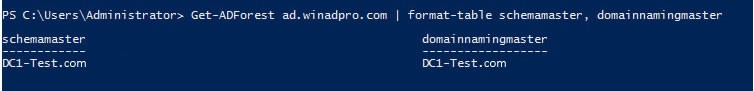
- For the other roles, open and run PowerShell as admin on your domain controller
- Enter the command below to return the domain FSMO roles:
Get-ADDomain yourdomain | format-table PDCEmulator, RIDMaster,InfrastructureMaster
This will return the rest of the FSMO roles and their holder as shown in the output screenshot below: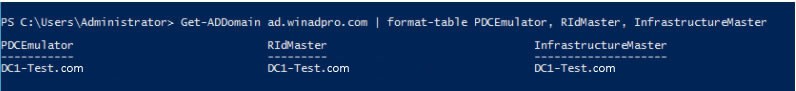
Conclusion
As you can see, FSMO roles prevent conflicts in an Active Directory and, at the same time, give you the flexibility to handle different operations within the Active Directory.
As noted earlier, it’s essential that you know which domain controllers hold which roles in your environment. What these roles are, and the DC’s that hold them in case a disaster occurs or you have a specific reason to move them.
FSMO Roles in Active Directory FAQs
Can I move FSMO roles to a different domain controller?
Yes, FSMO roles can be transferred to a different domain controller for load balancing or as part of a decommissioning process. You can use tools like the Active Directory Schema Management Console or PowerShell cmdlets like “Move-ADDirectoryServerOperationMasterRole” to perform this transfer.
What happens if a domain controller holding FSMO roles fails?
If a domain controller holding FSMO roles fails, some operations that rely on those specific roles may be impacted. It may be necessary to seize the roles onto another domain controller if the original server is permanently offline, using tools like “ntdsutil.
Can I have multiple servers holding the same FSMO role?
No, each FSMO role can be held by only one domain controller at a time within the scope that the role applies (either forest-wide or domain-wide).
What are the considerations for placing FSMO roles?
Considerations for placing FSMO roles include network reliability, domain controller hardware capability, the geographical distribution of users, and the specific functions of each role. Thoughtful planning ensures optimal performance and availability.
How do FSMO roles relate to Global Catalog servers?
The relationship between FSMO roles and Global Catalog servers is mainly concerning the Infrastructure Master role. If all domain controllers are Global Catalog servers, the Infrastructure Master role has no work to do. Otherwise, it is recommended not to place the Infrastructure Master role on a Global Catalog server, as this can cause phantom object issues.
Is it safe to have all FSMO roles on a single domain controller?
While it is technically possible to have all FSMO roles on a single domain controller, best practices often recommend distributing these roles across different domain controllers. This approach provides redundancy and load balancing.
What is a phantom object?
According to Microsoft: “Phantom objects are low-level database objects that Active Directory uses for internal management operations. Two common instances of phantom objects are as follows: An object that has been deleted. The tombstone lifetime has passed, but references to the object are still present in the directory database.”




