Rohos Disk Encryption is designed to protect sensitive data by encrypting entire disks or individual files on Windows and macOS devices. As cyber threats continue to escalate, data encryption has become a critical aspect of maintaining privacy and safeguarding valuable information. Rohos Disk Encryption provides strong protection but users don’t need to be technical experts in order to operate the system. Rohos software is packaged to appeal to both individuals and businesses seeking to secure their data.
This system can encrypt entire drives or create encrypted virtual drives, providing an extra layer of protection for sensitive files and data. With a simple setup process, users can easily set up encrypted volumes. This is a vault system where the encrypted folder is implemented as a virtual disk. Once the user unlocks the drive, access is as easy as browsing a folder in Windows Explorer. Files can be copied in and out of the vault. This ensures both accessibility and confidentiality.
In addition to disk encryption, Rohos offers features such as strong password protection, two-factor authentication, and self-decrypting drives, which provide further layers of security. The software also allows for removable media encryption, ensuring that USB drives and external hard drives are protected from unauthorized access. Rohos Disk Encryption also supports full disk encryption and provides the ability to encrypt operating system partitions, ensuring that all aspects of a device’s data are secured.
In this review, we explore the key features, benefits, and performance of Rohos Disk Encryption, helping you determine if it is the right solution for securing your sensitive data.
Rohos Disk Encryption Solution
There are lots of organizations out there that develop free and commercial disk encryption software. One of such is a Moldova (Eastern Europe) based IT security solutions company called Rohos. Rohos is an on-the-fly disk encryption software that uses a 256-bit AES encryption algorithm. Rohos Mini Drive and Rohos Disk Encryption are two easy-to-use Windows-based (Windows 7/8/10) disk encryption software from Rohos. Both applications are intended to secure your private data on your hard drive or USB flash drive.
The Rohos Mini Drive is a free disk encryption tool that aims to secure the confidential files you have on your USB flash drives. It does this by creating a hidden (virtual) and encrypted partition on the USB flash drive. So, if you are concerned about the security of the confidential files you carry around on your USB drive and want to keep them secret, you can protect them with a password and strong encryption using Rohos Mini Drive. It also offers a portable encryption tool for working with an encrypted partition on any PC. Rohos Mini Drive consists of the following key components:
- Rohos Mini Drive desktop Creates an encrypted partition on a USB drive and makes it look like a regular disk drive.
- Rohos Mini.exe Connects an encrypted USB drive partition as a disk drive on any PC (requires administrator privileges).
- Rohos Disk Browser Makes it possible to open and work with an encrypted partition (open or save any file). It also allows creating virtual disk containers and hidden encrypted containers with a USB drive partition or media file. Administrator privileges are not required.
- Rohos Mini Drive Portable (portable utility) Allows the use of an encrypted partition on any PC without Administrator privileges or installing additional software. Rohos Mini Drive Portable with Administrator privileges can create a Real Hidden Partition on a USB drive.
- File Virtualization Prevents confidential data from leaking outside an encrypted disk in temporary files and folders, the registry, the Recent Documents list, etc.
- Secured virtual keyboard Protect an encrypted disk password from a keylogger.
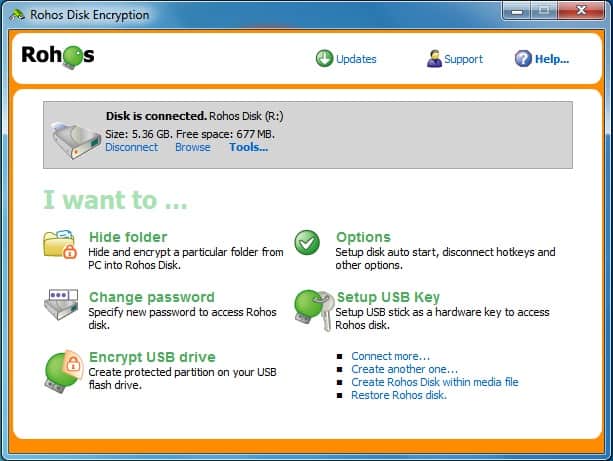
Rohos Disk Encryption is the full feature software that contains all the features of Rohos Mini Drive and much more. It creates hidden and encrypted partitions on the computer or USB flash drive and can also be used to encrypt cloud storage drives such as GoogleDrive, OneDrive, and others. It protects/locks access to encrypted partitions with a hardware key which replaces the use of passwords. The application can be deployed on a Windows platform and requires administrative rights. Some of the key features and capabilities of Rohos Disk Encryption software are as follows:
- Hide Folder With this feature, your protected items can be quickly and easily rendered inaccessible to other users but are instantly accessible when you turn on your Rohos disk. This is particularly useful in situations where you share your computer with other users. In addition, with the Rohos encryption program, you can easily hide your private data, including application folders (C:\Program Files\Firefox), Skype chat, browsing history, saved passwords, contacts, and other important confidential information from other users.
- Steganography In computing, steganography is the practice of concealing a message, file, image, or video within another message, file, image, or video. With this feature, you can easily hide your sensitive files in a media container such as AVI, MP3, OGG, WMA, etc. It also provides plausible deniability–the ability to deny any involvement or responsibility for transmitting a hidden file.
- USB key for access control This allows you to use a USB key such as a USB flash drive, YubiKey OTP token, Aladdin eToken, Swekey, and other USB dongles to access one or many secured Rohos volumes. If you set up the USB key as an access key for the Rohos Disk, you don’t need to enter the disk password manually to access your encrypted files. You are automatically logged in when you insert your USB key into the computer.
- Integrated File-Shredder Rohos Disk contains a File-shredder, which can be used to move any file and folder to your secret Rohos disk. After the files are moved, they’re erased by the File-shredder and deleted. This tool helps you delete files reliably, and nobody can recover it after it has been deleted. File-Shredder is integrated into the Windows Explorer Send-To menu.
- No risk of data loss With Rohos Disk Encryption, there is no risk of data loss. The partition password reset option allows you to recover forgotten passwords to your Rohos disk if you lost your password or USB key.
- There is no need for Admin rights: The Rohos Disk program allows you to access your portable partition, USB flash drive, or portable USB hard drive on a PC without admin privileges. In addition, you can open and edit data on your encrypted secret partition on any computer without administrative rights on a guest PC.
| Features | Rohus Mini | Rohus Disk |
|---|---|---|
| License type | Free | Commercial |
| Create an encrypted partition on a USB flash drive | Yes | Yes |
| Encryption capacity | 8 GB limit | Unlimited |
| Virtual keyboard. Protect your encrypted disk password from a keylogger. | Yes | Yes |
| Open (read-write) encrypted partition on a guest PC via Rohos Disk Browser | Yes | Yes |
| Create password reset file | Yes | Yes |
| Hide Folder or application into the encrypted container. | Yes | Yes |
| Create an encrypted partition on Computer HDD | No | Yes |
| Encrypt folders on PC/Google Drive/Dropbox | No | Yes |
| File-shredder to erase the content of folders and files | No | Yes |
| Steganography | No | Yes |
| Increase encrypted partition size. | No | Yes |
| Set up the hardware security key for disk access without entering a password | No | Yes |
Table 1.0 | Comparison of Rohos Mini Drive and Rohos Disk Encryption Software
The Best Rohos Encryption Software Alternatives
Rohos encryption software is not a one-size-fits-all solution for every organization. If you figure out that it is not best suited for your needs or environment and you’re considering a suitable alternative, you’ll find lots of them out there. To help you decide between the countless options out there, we’ve put together a list of the ten best Rohos encryption software alternatives. Hopefully, this will guide you in the process of selecting the right one that meets your needs.
- ManageEngine Endpoint Central EDITOR’S CHOICE The BitLocker Management feature of Endpoint Central safeguards sensitive data through encryption. Along with seamless key rotations to stream encryption, it also enables the deployment of granular custom policies for targeted applications. These policies can be automatically deployed to multiple users without manual intervention. These features are backed by extensive monitoring through an intuitive dashboard where you can consolidate audit data into detailed reports for informed decision-making. Get a 30-day free trial.
- BitLocker Drive Encryption Α free, easy-to-use, complete disk encryption application embedded in Microsoft Windows versions starting with Windows Vista. BitLocker uses the AES encryption algorithm with a 128-bit or 256-bit key. Unfortunately, it only works on the C: drive, so that it won’t help with external disks or USB tokens. And it can’t be used to make encrypted zip files.
- Endpoint Protector Enforced Encryption The Endpoint Protector USB Flash Enforced Encryption is a cross-platform tool within Endpoint Protector DLP application that ensures data is copied or transferred to USB storage devices is automatically encrypted. It will automatically push an AES-256 bits encryption algorithm called EasyLock to connected USB devices if the Endpoint Protector agent is installed on the computer. EasyLock can secure your files on a local HDD folder, on a USB device, Dropbox, iCloud, or it can be burned to CDs and DVDs. If you are looking to try it out, a free demo is available on request.
- FileVault Α full disk encryption program included in Mac OS versions starting with Mac OS X Panther (10.3). It performs on-the-fly encryption with volumes on Mac computers. An upgraded version—FileVault2, embedded in Mac OS X Lion (10.7) and other later versions provides encryption for the entire OS X startup volume and the home directory using XTS-AES-128 encryption with a 256-bit key.
- Symantec Endpoint Encryption Οffers two encryption products: Symantec Endpoint Encryption and PGP Encryption Solutions. Depending on the scenarios, both can help you secure your sensitive data, including computers, tablets, hard drives, removable media (USB drives, external hard drives, and DVDs), email systems, and cloud-based applications. In addition, Symantec Endpoint Encryption can help you manage BitLocker and Filevault-protected devices. At the same time, PGP Encryption supports file and folder encryption (zipped archives or individual files) and file share encryption (NTFS/CIFS shares). The products are available via Broadcom authorized distributors and partners in your region or country.
- McAfee Drive Encryption Α software component available in McAfee Complete Data Protection suites. It provides full disk on-the-fly drive encryption for data at rest on Microsoft Windows tablets, laptops, and desktop PCs; and files and folders encryption for data at rest on network files and folders on PCs and Macs, removable media (USB drives and CD/DVDs), email attachments, and cloud storage.
- Check Point Full Disk Encryption This is a complete disk encryption application that automatically encrypts all information on the hard drive—including user data, the operating system, temporary files, and erased files. The application is integrated into the Checkpoint Endpoint Security Software Blades such as Check Point endpoint security. A free trial of the endpoint security suite is available on request.
- Trend Micro Endpoint Encryption An entire disk and file/folder encryption software for data at rest on PCs and Macs, laptops and desktops, USB drives, and other removable media. It uses the AES encryption algorithm with a 128-bit or 256-bit key, and it’s fully supported on Windows (7, 8, 8.1, 10) and Mac OS (10.8, 10.9, 10.10, 10.11, 10.12, 10.13, 10.14). Some of the key features include:
- Ability to manage BitLocker and Filevault protected devices
- Active Directory integration
- Pre-boot authentication
- Reporting and auditing
- VeraCrypt A free open source on-the-fly disk encryption software for Windows, Mac OSX, and Linux. VeraCrypt is a fork of the discontinued TrueCrypt project but with many improvements that address concerns with the original TrueCrypt code. In addition, the software supports plausible deniability and pre-boot authentication. Other key features include:
- Ability to encrypts an entire partition or storage device such as USB flash drive or hard drive
- Ability to create a virtual encrypted disk within a file and mount it as an actual disk
- Ability to encrypt a partition or drive where Windows is installed
- Cryptomator Α free, open-source disk encryption software for encrypting files stored in the cloud. Cryptomator works with any cloud provider that can be synchronized with a folder in your local file system. However, most cloud providers encrypt data only during transmission (data in transit). With Cryptomator, you can create vaults that are hosted on a virtual drive. The data stored in the vault is then encrypted before being transferred or synced to your cloud storage providers, such as Dropbox, OneDrive, Google Drive, or other cloud providers. It uses the AES encryption algorithm with a 256-bit key.
- Boxcryptor Αn encryption software used for encrypting your sensitive files and folders in Dropbox, Google Drive, OneDrive, and other cloud storage providers. You can use Boxcryptor to encrypt your data right on your device before transferring or syncing it to your cloud storage provider. Boxcryptor encrypts files with AES-256 and RSA-4096 encryption algorithms, and it’s supported on Windows, Mac, iOS, Android, and Linux (though with the Boxcryptor Portable and limited functionality). The product is targeted at both individuals (free version) and businesses (commercial version).
Conclusion
Full disk encryption only protects your computer while it’s turned off. This means that anyone who gains access to your computer while you are still logged in may still be able to access your data. It also doesn’t protect systems from being attacked by hackers or provide any protection for data while it’s transmitted across the internet. For that, you’ll need a VPN application.
To deal with these and other similar threats, you should minimize the amount of sensitive data you carry on your laptop. But, of course, the best protection against data loss is not to carry the data in the first place.
Rohos Disk Encryption FAQs
How do you use Rohos encryption?
Rohos Disk Encryption will protect a USB drive. To use the Roho encryption system, floor these steps:
- Insert your USB device.
- Open Rohos Disk Encryption – the USB device will be shown in the Home screen.
- Click on Encrypt USB drive in the Rohos screen.
- In the Encrypt USB drive pop-up, make sure that the inserted USB stick is visible to the system.
- Click on Change above the disk creation parameters panel.
- In the Disk details window, choose a Disk letter, the Disk size of the partition, the File system type, and the Encryption algorithm.
- Click on OK. This returns you to the main Rohos screen.
- Enter a password for the device.
- Repeat the password.
- Click on Create Disk.
Is rohos secure?
Rohos Disk Encryption provides the AES-256 cipher. This is uncrackable and it is the same encryption system used by banks around the world and the US military. You improve the security of your encrypted disk by choosing a complex password that is impossible to guess.
Is Rohos Logon Key Safe?
Rohos Logon Key uses uncrackable AES encryption with a 256-bit key. The file that contains the password for the security system cannot be moved or copied off the USB device and the file is protected against unauthorized access. These measures make Rohos Logon Key safe and secure.




