Snort is one of the most widely used open-source network intrusion detection systems (NIDS) and intrusion prevention systems (IPS). Known for its flexibility, scalability, and security capabilities, Snort is trusted by IT professionals and cybersecurity teams to detect and prevent a wide variety of attacks, including malware, DDoS (Distributed Denial-of-Service), and buffer overflow attacks.
With its ability to analyze network traffic in real time and generate alerts based on predefined or custom rules, Snort plays a vital role in securing networks and systems from potential threats.
To use Snort effectively, network administrators need a clear understanding of its syntax, rules, and configuration. This is where a Snort cheat sheet comes in handy. A cheat sheet serves as a concise, easy-to-reference guide that simplifies the process of working with Snort by providing quick access to essential commands, rule structures, and configuration tips. It’s an invaluable tool for both beginners and experienced users who want to streamline their workflow and maximize the efficiency of their Snort deployment.
Here, we offer a comprehensive Snort cheat sheet, designed to help users navigate Snort’s vast array of features. We cover everything from basic commands and configuration options to more advanced rule-writing techniques. Whether you’re setting up Snort for the first time, writing custom rules, or troubleshooting an existing installation, our cheat sheet will guide you through the most important aspects of Snort.
With the right knowledge and tools, Snort can be a powerful asset in any organization’s cybersecurity toolkit. This cheat sheet ensures that users can quickly access the information they need to harness Snort’s full potential, enhancing network security and performance.
All the tables provided in the cheat sheets are also presented in tables below which are easy to copy and paste.
The Snort Cheat Sheet covers:
- Sniffer mode, Packet logger mode, and NIDS mode operation
- Snort rules format
- Logger mode command line options
- NIDS mode options
- Alert and rule examples
View or Download the Cheat Sheet JPG image
Right-click on the image below to save the JPG file ( 2443 width x 1937 height in pixels), or click here to open it in a new browser tab. Once the image opens in a new window, you may need to click on the image to zoom in and view the full-sized jpeg.
View or Download the cheat sheet PDF file
Download the cheat sheet PDF file here. When it opens in a new browser tab, simply right click on the PDF and navigate to the download menu.
What’s included in this cheat sheet
The following categories and items have been included in the cheat sheet:
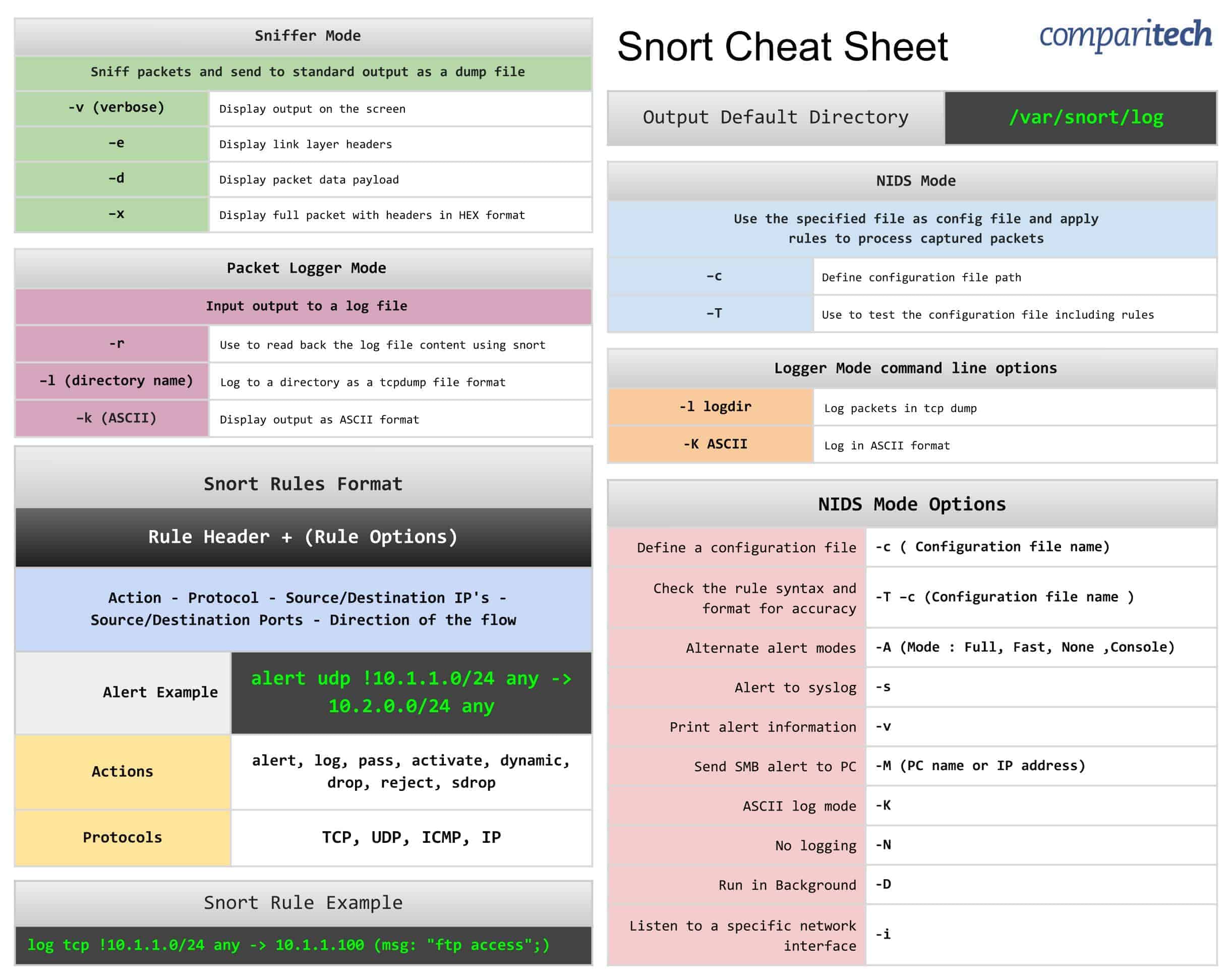
Sniffer Mode
Sniffer Mode |
|
|---|---|
Sniff packets and send to standard output as a dump file |
|
-v (verbose) | Display output on the screen |
–e | Display link layer headers |
–d | Display packet data payload |
–x | Display full packet with headers in HEX format |
Packet Logger Mode
Packet Logger Mode |
|
|---|---|
Input output to a log file |
|
-r | Use to read back the log file content using snort |
–l (directory name) | Log to a directory as a tcpdump file format |
–k (ASCII) | Display output as ASCII format |
NIDS Mode
NIDS Mode |
|
|---|---|
Use the specified file as config file and apply rules to process captured packets |
|
–c | Define configuration file path |
–T | Use to test the configuration file including rules |
Snort rules format
Snort Rules Format |
|
|---|---|
Rule Header + (Rule Options) |
|
Action - Protocol - Source/Destination IP's - Source/Destination Ports - Direction of the flow |
|
Alert Example | alert udp !10.1.1.0/24 any -> 10.2.0.0/24 any |
Actions | alert, log, pass, activate, dynamic, drop, reject, sdrop |
Protocols | TCP, UDP, ICMP, IP |
Logger mode command line options
Logger Mode command line options |
|
|---|---|
-l logdir | Log packets in tcp dump |
-K ASCII | Log in ASCII format |
NIDS mode options
NIDS Mode Options |
|
|---|---|
Define a configuration file | -c ( Configuration file name) |
Check the rule syntax and format for accuracy | -T –c (Configuration file name ) |
Alternate alert modes | -A (Mode : Full, Fast, None ,Console) |
Alert to syslog | -s |
Print alert information | -v |
Send SMB alert to PC | -M (PC name or IP address) |
ASCII log mode | -K |
No logging | -N |
Run in Background | -D |
Listen to a specific network interface | -i |
Snort rule example
Snort Rule Example | log tcp !10.1.1.0/24 any -> 10.1.1.100 (msg: "ftp access";) |
|---|
Output Default Directory
Output Default Directory | /var/snort/log |
|---|
Snort FAQs
How can Snort help with network intrusion detection?
Snort operates as a packet sniffer. It can then apply detection rules to look for signs of intrusion. The tool is able to examine traffic as it travels into the network and also packets that are leaving the network.
Can Snort detect zero day network attacks?
Snort can identify zero-day attacks by looking for types of action against specific types of targets. This generalization and behavior scanning means that the Snort detection rules don’t need to rely on previously reported attacks for guidelines.
What are the three modes of Snort?
Snort has three operating modes:
- Packet Sniffer – Reads packets from the network and displays them in the Snort console
- Packet Logger – Reads packets from the network and writes them to a file
- NIDS – Network intrusion detection system that applies rules to scan through packets