SQL database server like other database servers is a key asset in most organizations. Many data breaches that occur today can be traced to poorly secured database servers
Without the right security measures, a database can easily serve as a gateway for cyber attacks. A single act of negligence can compromise the safety and security of your organization’s SQL database. Attackers can inject malicious codes, and compromise the integrity, confidentiality, and availability of the database.
Implementing the right security measures will go a long way in protecting your database servers and minimizing your exposure to business and security risks. This article outlines some essential SQL Server security basics and best practices, including some of the top tools for managing SQL Server security and performance.
Here is our list of the best SQL Server security monitoring tools:
- ManageEngine EventLog Analyzer EDITOR’S CHOICE This SIEM system provides a range of security services for databases, such as SQL Server, and implements database log management. Available for Windows server and Linux. Start a 30-day free trial.
- Paessler PRTG Network Monitor (FREE TRIAL) This is a large, customizable package of network, server, and application sensors that includes an SQL Server monitor. Runs on Windows Server. Start a 30-day free trial.
- Site24x7 Infrastructure Monitoring (FREE TRIAL) This cloud-based package has an expansion plugin for SQL Server monitoring that alerts on performance problems and provides opportunities for event analysis. Start a 30-day free trial.
- Microsoft Defender for SQL This vulnerability scanner for databases identifies security weaknesses in systems and anomalous user behavior. This is a cloud-based service.
- SolarWinds Security Event Manager This on-premises SIEM system examines the log files of all applications and operating systems for indicators of compromise.
- Datadog This cloud platform of system monitoring and security services includes routines for monitoring SQL Server on-premises and in the cloud.
You can read more about each of these solutions in the following sections.
Physical Security
Information security cannot be completely achieved without proper physical security. Physical security should be the first line of defense and must include the prevention of unauthorized access to the facility where the SQL Server is hosted. Physical security deals with facility and personnel access controls, external boundary protection mechanisms, intrusion detection, and corrective actions. It protects your assets from intruders, theft, environmental threats, physical damage, among others.
Physical security should be implemented by using a layered defense approach. The idea is that if an attacker breaks through one control layer, there will be many others in the way before he or she can gain full access. Any breach in the physical security of your database server could result in loss of productivity, reputation, and customer confidence.
To enhance the physical security of the SQL Server, Microsoft recommends you do the following:
- Place the server in a room accessible only to authorized persons.
- Place computers that host a database in a physically protected location, ideally a locked computer room with monitored flood detection and fire detection or suppression systems.
- Install databases in the secure zone of the corporate intranet and do not connect your SQL Servers directly to the Internet.
- Back up all data regularly and secure the backups in an off-site location.
Network Security
Network security is concerned with the protection of the underlying networking infrastructure of your database server from unauthorized access. It combines multiple layers of defenses that implement policies and controls at the edge and in the network. Authorized users gain access to the database via the network, while unauthorized users are denied access. A network infrastructure designed with security in mind around your database server safeguards the database from losses that occur from network security incidents.
Implementing network security starts with keeping unauthorized users off the network. This is where network firewalls come into play. Firewalls play an important role in securing the SQL Server application. By putting your database behind a firewall, you create another layer of security preventing malicious traffic from reaching your server. Firewalls can also help prevent malicious outbound traffic such as data exfiltration.
Firewalls will be most effective if you adhere to the following recommended guidelines from Microsoft:
- Put a firewall between the server and the internet. Enable your firewall. If your firewall is turned off, turn it on. If your firewall is turned on, do not turn it off.
- Divide the network into security zones separated by firewalls. Block all traffic, and then selectively admit only what is required.
- In a multi-tier environment, use multiple firewalls to create screened subnets.
- When you are installing the server inside a Windows domain, configure interior firewalls to allow Windows Authentication.
- If your application uses distributed transactions, you might have to configure the firewall to allow Microsoft Distributed Transaction Coordinator (MS DTC) traffic to flow between separate MS DTC instances. You will also have to configure the firewall to allow traffic to flow between the MS DTC and resource managers such as SQL Server.
- Disable all unnecessary ports and protocols including NetBIOS and Server Message Block on your SQL Server, Web servers, and Domain Name System (DNS) to reduce the attack surface. Allow only protocols and ports that are essential to the functioning of the SQL Server such as TCP 1433 (database engine), 2383 (analysis services), 4022 (service broker), and UDP 1343 (browser access).
Application and Data Security
Microsoft SQL Server provides several built-in features that enable the security of the application and the data contained within it. The database administrator can leverage these features, or use additional security measures as needed, to address the security needs of the SQL application and data.
Some of the additional security measures may among other things include:
- Protection against SQL and other Injection attacks Just as the name suggests, SQL injection is an attack in which malicious code or commands is injected into query strings. These commands can damage or corrupt the database or be used to exfiltrate sensitive data. You can thwart SQL injection attacks by sanitizing all database inputs to ensure they do not contain characters that can be used to execute code. It is best practice to use stored procedures and parameterized commands while avoiding dynamic SQL, and restricting permissions on all users. You also need to guard against connection string injection attacks that occur during SQL Server login. If an SQL Server login string is not checked for valid keyword pairs, an attacker can add extra characters that can perform unauthorized actions on the server. You can mitigate this risk by using the SqlConnectionStringBuilder to create and validate connection strings at run time, or use the more secure Windows authentication wherever possible.
- Verbose errors exploitation SQL Server generates all kinds of logs such as error logs, system event logs, performance counter data, among others. You need to find a way to make sure these errors don’t fall into the wrong hands. Otherwise, attackers may use it to identify inherent vulnerabilities that they may want to exploit. Ensure that all procedural code uses error handling, to prevent these default SQL Server error messages from reaching the user.
- Privilege escalation attacks These attacks occur when users somehow assume the privileges of a trusted account, such as an account owner or an administrator. This enables them to gain unauthorized access to data and database functions. To mitigate this risk, always run users as least-privileged accounts, assign only needed permissions, and block the ability to execute code from administrative or owner accounts. This limits the amount of damage that can occur if an attack succeeds. If a user requires extra permissions to perform a task, use certificates to sign stored procedures or impersonation only for the duration of the task.
- Distributed denial of service (DDoS) attacks Production SQL Server databases may be subject to DDoS attacks, in which attackers flood the database with fake queries, slowing performance for legitimate users, and eventually resulting in downtime. If you run SQL Server in the cloud, you can leverage DDoS protection services, which can capture and divert malicious traffic away from your database.
SQL Server Security Best Practices
The following are some key SQL Server security best practices that can enhance the security of your SQL database:
- Backup regularly The need for regular backup of your database cannot be overemphasized. Backups protect the availability of data and ensure that your database remains resilient in the face of data breaches, ransomware, or denial of service attacks. Consider investing in a good SQL Server backup solution as part of your security strategy. This provides you with a lifeline to restore mission-critical data in the event of an attack.
- Regular Security Audits Security audits are a regulatory requirement for most industries. But beyond that, SQL Server security audits help prevent potential attacks and in maintaining a healthy SQL database. Efforts should be geared towards identifying missing database objects, repeated server login failures, and permissions or configuration changes. Microsoft provides a built-in tool called SQL Server Audit which can be used to create server-level and database-level audits.
- Follow the Principle of Least Privilege This is a tried and tested principle that helps to lower your asset exposure to risk. The plan is to grant SQL Server services and users only the appropriate rights required to perform a task and no more. For service accounts, run and associate SQL Server services using the lowest possible permissions and privileges.
- Have a Strong Password Policy Setting a strong password or preferably a passphrase that is hard to guess is essential to the security of your database. Consider using Kerberos authentication, Windows Authentication for connections to SQL Server, and a password manager for better password management.
- Apply updates regularly The importance of regular updates cannot be overemphasized. The OS and SQL Server updates contain important security enhancements that maintain the health and security of your database. Test these updates and apply them to your production server as soon as possible.
- Use Encryption The built-in SSL/TLS and Windows Data Protection API (DPAPI) encryption protocol enable encryption of data in transit and data at rest respectively. This protects the confidentiality of your database.
- Use SQL Monitoring Tools SQL monitoring tools provide an automated means of managing the security and performance of your database server. The tool should be capable of scanning and detecting changes to server settings.
The Top Tools for SQL Server Security
Several tools on the market can automate the management of the security and performance of your SQL Server. Below is a review of some of the top tools for managing SQL Server security and performance. Hopefully, this will guide you in the process of choosing the right solution for your business.
Our methodology for selecting SQL Server security tools
We reviewed the market for security systems that protect SQL Server instances and assessed the options based on the following criteria:
- Activity monitoring for servers and applications
- Utilities that are able to gather statistics from within SQL Server instances
- SQL Server log collection and analysis
- User account activity monitoring
- Tracking of the server resources that support databases
- A free trial or a demo for a pre-purchase assessment
- Value for money from an SQL Server monitoring tool that can also watch over other applications
1. ManageEngine EventLog Analyzer (FREE TRIAL)

ManageEngine EventLog Analyzer provides a number of security services for SQL Server databases. First of all, this is a system-wide SIEM system that protects all assets from intrusion or automated malicious attacks. So, all of the assets that surround an SQL Server database instance are protected. For the database itself, the EventLog Analyzer operates within the database and around its log files.
Key Features:
- Database discovery
- Database transaction monitoring
- Alerts for SQL attacks
Why do we recommend it?
ManageEngine EventLog Analyzer is a similar package to the SolarWinds Security Event Manager. The system acts as a log server and will process Windows Event logs and Syslog messages as well as logs from applications, such as SQL Server. The tool consolidates all of those messages into a common format so that they can be searched and stored together.
The EventLog Analyzer is able to track transactions with your database and report on activity for object creation and data transactions per user. The system will also perform security monitoring, raising alerts if attacks are identified. The EventLog Analyzer is able to provide analysis of user connections and permissions to help you redefine accounts and tighten security. As well as protecting SQL Server databases, this system will perform security monitoring for Oracle, MySQL, and MariaDB databases.
Three are four editions of the EventLog Analyzer:
- Free Edition: Collects and archives logs and provides compliance reporting for five log sources
- Workstation package: Provides the same services as the Free Edition but for 100 workstations.
- Premium Edition: Full security monitoring for one site.
Distributed Edition: Full security monitoring for multiple sites.
Who is it recommended for?
This package is accessible for any size of business because there is a Free edition. That version will only collect logs from five sources, which isn’t much. So, most companies will need to step up to one of the paid editions. The package is particularly appealing for businesses that need to comply with PCI DSS, GDPR, FISMA, ISO 27001, or SOX.
Pros:
- Full security scanning for all applications and data
- Log collection, analysis, and filing
- Compliance management
Cons:
- TSaaS version doesn’t provide application log analysis
The software for ManageEngine EventLog Analyzer installs on Windows Server or Linux. It is a system-wide security monitoring tool and log manager for all of your applications, not just SQL Server databases. There is a SaaS package of the SIEM but it doesn’t include SQL Server monitoring. You can assess the on-premises tool with a 30-day free trial.
EDITOR'S CHOICE
ManageEngine EventLog Analyzer is our top pick for an SQL Server security tool because this package offers comprehensive log management and monitoring capabilities. It collects, analyzes, and reports on SQL Server logs, providing real-time alerts for suspicious activities, unauthorized access, or potential security breaches. The tool will track changes in SQL Server configurations and monitor user activities for compliance with GDPR, HIPAA, and SOX.EventLog Analyzer features advanced auditing capabilities, enabling administrators to maintain detailed records of database activities, including user logins, failed attempts, and queries executed. This logging identifies anomalous behavior and potential insider threats. The tool also provides a reporting engine and customizable dashboards that visualize of security metrics. Its comprehensive feature set and strong focus on database security make it a valuable asset for organizations seeking to safeguard their SQL Server environments.
Download: Get a 30-day free trial
Official Site: manageengine.com/products/eventlog/
OS: Windows Server, Linux, or cloud
1. Paessler PRTG Network Monitor (FREE TRIAL)
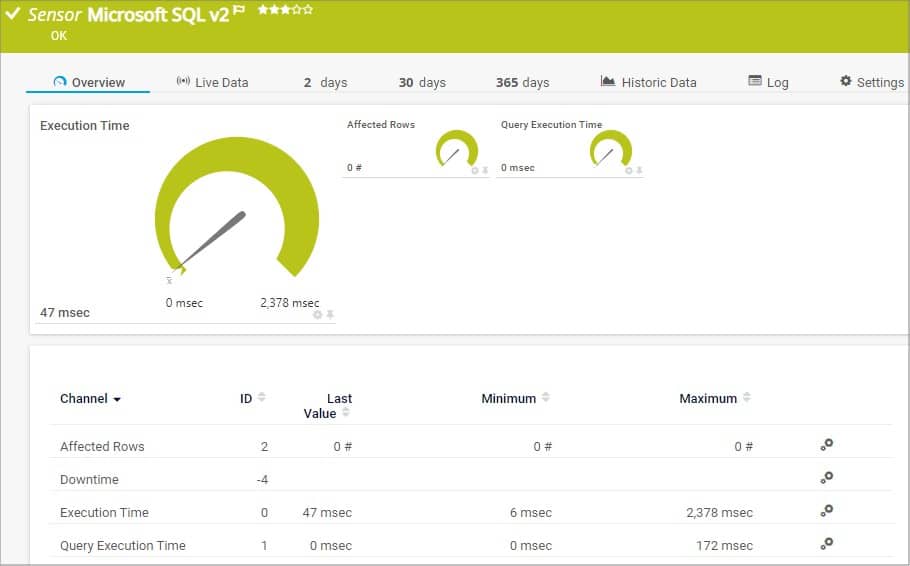
Paessler PRTG is an agentless network monitoring tool that lets you monitor your network, routers, switches, and servers. With PRTG, you can measure the time an SQL query needs for its entire request, including the establishment of the connection, the execution of the query, the handling of the transaction, and the termination of the connection, all of which can be visualized on the PRTG dashboard.
Key Features:
- SQL Server performance monitoring
- Device availability tests
- Server activity metrics
- Full-stack observability
- Monitors Azure SQL as well as SQL Server
Why do we recommend it?
Paessler PRTG Network Monitor isn’t limited to monitoring networks. IT will also monitor servers and applications. The service will track action within an SQL Server database while also looking out for server resources. This enables the monitoring service to spot when the resources that SQL Server databases need are running low.
The PRTG licensing model is based on sensors (parameters that can be monitored on a device such as CPU load, port status, or network traffic); and comes with pre-configured sensors for all major databases. For Microsoft SQL, PRTG offers the Microsoft SQL v2 Sensor which monitors the response time of an entire request as well as the response time of an individually defined query.
PRTG comes in different editions and variants such as:
- PRTG Enterprise Monitor—targeted at large networks with thousands of devices and systems across multiple locations.
- PRTG Hosted Monitor—a cloud-based option that allows you to monitor from the cloud
- PRTG Desktop—allows you to manage multiple PRTG servers.
- PRTG Mobile App—allows you to check your network, devices, and sensors while on the go.
Who is it recommended for?
This system is customizable. All buyers receive the same software package that includes all of the monitoring systems of PRTG. you will never need all of them. Customers pay for an allowance of sensors and then choose which to turn on. Thus, you don’t have to pay for services that you don’t need.
Pros:
- Drag and drop editor makes it easy to build custom views and reports
- Supports a wide range of alert mediums such as SMS, email, and third-party integrations into platforms like Slack
- Supports a freeware version
- Historical analysis tools
- A SaaS platform or software for Windows Server
Cons:
- Is a very comprehensive platform with many features and moving parts that require time to learn
A free 30-day-trial with full access to all the features is available for download.
3. Site24x7 Infrastructure Monitoring (FREE TRIAL)
Site24x7 Infrastructure Monitoring is an expandable cloud-based platform that has a plugin to provide SQL Server monitoring capabilities. This plugin adds an extra screen to the Site24x7 dashboards and extra instructions to the data-gathering on-site agent.
Key Features:
- Live performance tracking
- Log analysis
- Database attributes tracking
Why do we recommend it?
Site24x7 Infrastructure Monitoring with the SQL Server monitoring plugin provides detailed activity reports on SQL Server databases and is embedded in a system that also provides server and application monitoring. So you can see in, under, and above your SQL Server instances. The tool also provides SQL Server log analysis.
The Site24x7 system gathers activity and response data from within a database and shows aggregated statistics live in the system dashboard. It also stores that data for capacity planning. The platform provides a Log Management unit that includes a data analyzer and that can be used to assess SQL Server logs.
Who is it recommended for?
The entire Site24x7 platform provides a wide range of IT system monitoring and management units and is suitable for all types and sizes of businesses. However, the SQL Server plugin specifically caters to the owners of SQL Server databases. Activating the plugin doesn’t cancel all of the other modules, so you get full-stack observability along with the SQL Server monitoring services.
Pros:
- Correlated performance tracking with server and application monitoring
- Database details
- DevOps support
Cons:
- No on-premises version
The Site24x7 Infrastructure plan is affordable for small businesses. There is a fee for each plugin that gets activated but the first plugin is free in the base package. That standard package will monitor up to five physical servers. You can try out the Site24x7 system by accessing a 30-day free trial.
4. Microsoft Defender for SQL
Microsoft Defender for SQL is an SQL Server security tool that helps to detect and mitigate potential SQL database vulnerabilities and anomalous activities that pose a threat to your database.
Key Features:
- SQL Server performance monitoring
- Device availability tests
- Alerts for performance problems
Why do we recommend it?
This SQL Server security monitoring service is part of the Microsoft Defender for Cloud platform, which is hosted on Azure. This tool will track your SQL Server instances wherever they are hosted – the package isn’t limited to monitoring Azure-hosted services. Your instances can be on your own servers, on AWS, Google Cloud Platform, or Azure.
Microsoft Defender for SQL comprises two separate Microsoft Defender plans:
- Microsoft Defender for Azure SQL database servers: This plan is designed to protect Azure SQL database, Azure SQL managed instance, and dedicated SQL pool in Azure synapse.
- Microsoft Defender for SQL Servers on machines: This plan extends the protections for your Azure-native SQL Servers to fully support hybrid environments and protect SQL Servers hosted in Azure and other cloud environments, and even on-premises machines: including SQL Server on virtual machines and on-premises SQL Servers.
Who is it recommended for?
This is a great option for businesses of all sizes. Azure doesn’t impose minimum charges on its services, so even very small businesses can afford it. The Microsoft Defender for Cloud is able to provide security monitoring for many other assets, not just SQL Server databases.
Pros:
- Is a full suite of patch management tools
- Can manage patches for a variety of Windows tools
- Ideal for system administrators
Cons:
- Better suited for Windows products
You can enable these plans at the subscription level (from Microsoft Defender for Cloud or via the REST API, Azure CLI, PowerShell, or Azure Policy), or you can enable at the resource level. When you enable either of these plans, all supported resources that exist within the subscription (including future resources created on the same subscription) are protected.
5. SolarWinds Security Event Manager

SolarWinds Security Event Manager (SEM) enables database administrators to monitor server logs, track database error rates, audit SQL user logins, maintain SQL Server security, and detect cyber attacks. With SEM, you can track, report, and alert on specific events done against a SQL database that may signal potential threats, and generate SQL Server audit log reports for compliance purposes. SEM provides out-of-the-box event correlation rules that study database transactions, detect known threats, and track malicious and non-trusted activities.
Key Features:
- Threat hunting
- Log collection
- User behavior analytics
- Alerts for security events
- Database attack detection
Why do we recommend it?
The SolarWinds Security Event Manager is a SIEM that is able to collect event logs from all across the network, which includes the logs of applications, such as SQL Server. Although this package provides system-wide security alerts, it also provides a log viewer for manual analysis. It is possible to set up your own searches and define alerts on different factors.
SEM supports various security assessment protocols and applications to help you defend against SQL injection attacks and maintain a secure database. SEM leverages its pre-built SQL injection rules and alerts to keep you informed. It can detect and disable malicious users and processes, as well as perform other automated threat responses to help secure your database when SQL injection indicators are detected. A free trial is available for download, so you can determine whether it’s right for your business.
Who is it recommended for?
This system is an on-premises software package for Windows Server. However, it is able to collect logs from other operating systems and also from cloud platforms. The service can accept logs from SQL Server instances running on premises or on the cloud. The service is suitable for large companies that have many technologies to protect.
Pros:
- Offers both incident response tools as well as automated remediation and prevention
- Enterprise-focused SIEM with a wide range of integrations
- Simple log filtering, no need to learn a custom query language
- Dozens of templates allow administrators to start using SEM with little setup or customization
- The historical analysis tool helps find anomalous behavior and outliers in the network
Cons:
- SEM Is an advanced SIEM product built for professionals, requires time to fully learn the platform
Try SolarWinds Security Event Manager (SEM) with a fully functional 30-day free trial.
6. Datadog
Datadog is an agent-based on-premises and cloud infrastructure monitoring service for cloud applications, servers, databases, tools, and services. Datadog uses its auto-discovery service to explore and identify applications, devices, and servers in your network. Once all devices and links have been identified, you can overview all activity from the Datadog dashboard, and any changes to the network can be automatically spotted.
Key Features:
- System-wide monitoring
- Cloud and on-premises SQL Server monitoring
- Security option with a SIEM
Why do we recommend it?
Datadog provides a large platform of system monitoring modules and it is able to provide performance monitoring in its Infrastructure Monitoring package. For security monitoring, you should look at the Cloud SIEM service. This tool is hosted on the Datadog cloud platform and it can collect logs from any source, including other cloud platforms and your on-premises systems. SQL Server is one of the applications that can feed logs into the package.
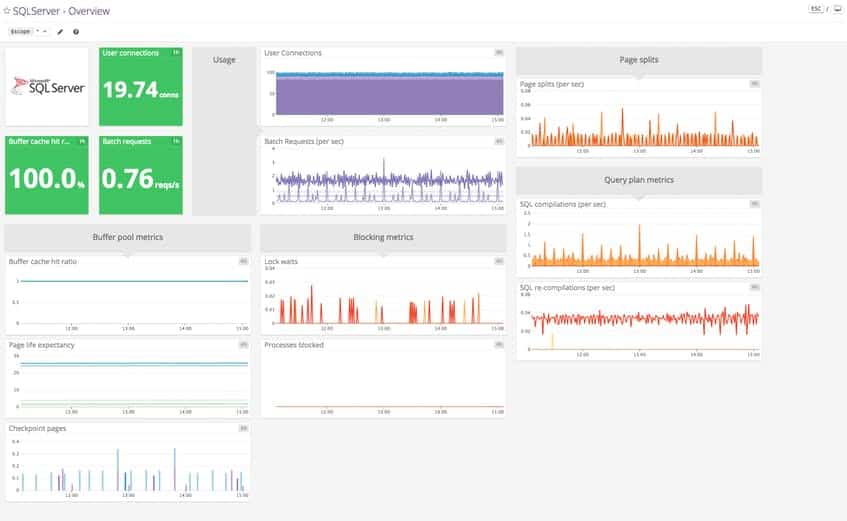
Datadog provides end-to-end visibility into the health and performance of your SQL Server instances. It provides tools and key metrics for SQL Server monitoring, including two out-of-the-box dashboards for SQL Server:
- A screenboard that gives you a real-time overview of your SQL Server instances.
- A timeboard that’s well suited for correlating SQL Server metrics with system metrics and events.
Who is it recommended for?
This system is suitable for any business of any size. It is particularly useful for multi-site organizations and companies that operate a hybrid environment with both on-premises and cloud-based assets.
Pros:
- Leverages machine learning to improve alerting, reporting, and queue management
- Excellent dashboards – great for solo admins or NOC teams
- Can easily see historic metrics as well as a live view of your IT assets
- Highly flexible – scales well across various environments
Cons:
- Would like to see a longer trial period for in-depth testing





