Teramind offers a range of threat detection and data protection services that are bundled into packages. You choose a plan that includes all of the modules that you need. This is a very flexible approach to the provision of both threat detection and data loss prevention. So, this solution could save you a lot of money by providing multiple functions. You just need to work out exactly which security systems you currently lack and ensure you don’t over-buy.
Based in Aventura, Florida, Teramind was founded in 2014. In both the threat protection and data loss prevention fields, Teramind is up against some huge brands. Significant competitors in these fields include McAfee, Symantec, and ManageEngine, so Teramind has to work doubly hard to get noticed in the field
Teramind has done an excellent job in meeting the competition head-on. While some big names offer an on-premises solution and others present a SaaS system, Teramind provides both. In addition, the company isn’t shy about quoting its prices, which is another good sign. In an industry that loves to write Contact Us on a significant empty Price List page, Teramind publishes its prices for anyone to see. This is probably because Teramind’s prices are very affordable, so these are one of its marketing strengths.
What does Teramind DLP do?
DLP stands for Data Loss Prevention. However, Teramind DLP isn’t just that. In the Teramind system, DLP is at a plan level. The lower plans in the Teramind package list are all about user monitoring and insider threat tracking. The Teramind DLP package is the company’s top plan, and that adds to data loss prevention. So, with this package, you get productivity tracking and insider threat monitoring as well as DLP. In addition, the package offers data privacy standards auditing and reporting as well.
Teramind contends that its DLP plan replaces many other software packages that you might be considering, not just a DLP service.
How much does Teramind DLP cost?
To fully understand the Teramind DLP offering, you need to get down to its plan pricing. This lets you know exactly what you would be getting with the DLP plan.
There are three plan levels, and those services can be taken as a SaaS package or as a software bundle for on-premises installation. In all cases, the on-premises version is cheaper.
The three plans with their prices are:
- Starter On-premises: $5 per endpoint per month SaaS: $10
- UAM On-premises: $10.42 per endpoint per month SaaS: $20.83
- DLP On-premises: $12.50 per endpoint per month SaaS: $25
UAM stands for User Activity Monitoring.
For each plan, there is a minimum of five endpoints required for an account. Teramind offers lower rates for accounts that cover more than 50 endpoints.
You can get a free trial of Teramind DLP. This lasts for seven days in the Cloud version and 14 days for the on-premises version. You can also look at the live demo of the Teramind DLP system.
Teramind plan services
Each higher plan offers the services included in the lower plans plus other features.
- Starter This plan includes user activity monitoring that covers for Web activity, messaging, and email. It also includes User Behavior Analytics that profiles each user account, looking for malicious or abusive activity. It is also possible to record all actions performed by each account by video or audio. These monitoring activities can be set by policies that automatically apply different monitoring levels to other user groups.
- UAM This plan is heavily geared towards detecting insider threats and also account takeover. The activity monitoring is fully automated with an anomaly detection system that notices if a user account starts performing actions outside its regular activity. The package also includes a dynamic risk scoring system that is useful for the protection of sensitive data.
- DLP this is the only plan that includes data loss prevention features. As well as the insider threat and user monitoring services that the other programs provide, this tool has complete protection for sensitive data stores, covering personally identifiable information, protected health information, and access locations restrictions. This is a good plan for businesses that must comply with GDPR, CCPA, HIPAA, and PCI DSS.
Teramind DLP deployment options
The Cloud version of Teramind DLP doesn’t need a host on your site, but it does require an agent installed. There are agents available for:
- Windows 7 and higher
- Windows Server 2012 and higher
- macOS
- Citrix XenApp and XenDesk
- VMWare Horizon
The on-premises version installs on top of a VM and runs as a virtual appliance. It will run on:
- VMWare ESXi 6.7
- Microsoft Hyper-V
Teramind DLP Pros and Cons
Teramind DLP is a very flexible system suitable for enterprises of all sizes, thanks to its per-device pricing. However, the system isn’t perfect. Here is a summary of the strengths and weaknesses of Teramind DLP.
Pros:
- Extensive insider threat detection functions
- Sensitive data management
- Complete control over data exfiltration channels
- Variable security policies
- Extensive user activity monitoring facilities
Cons:
- No agent software for Linux
Alternatives to Teramind DLP
The lack of any agent system for Linux in the Cloud package is a little worrying. You can get around this problem if you only have Linux endpoints on your system by running the agent package over a VM. Similarly, if you opt for the on-premises version, it doesn’t matter what operating system you run on your site because the Teramind system needs to run over a VM. If you don’t want to be bothered with installing virtualization just for the DLP system, you should probably look elsewhere for your data loss prevention strategy fulfillment.
Our methodology for selecting a Teramind DLP alternative
We reviewed the market for data loss prevention systems like Teramind DLP and analyzed tools based on the following criteria:
- A package that works on all operating systems
- An option for a SaaS package
- Features that give extra protection to sensitive data
- Insider activity tracking to spot account takeover
- Data privacy standards compliance
- A free trial or a demo system for a no-cost assessment
- A good deal that offers a price within reach of all sizes of business
We created a shortlist of data loss prevention systems that we are happy to recommend with these selection criteria in mind.
Here is our list of the five best alternatives to Teramind DLP:
- ManageEngine Endpoint DLP Plus EDITOR’S CHOICE This package of data protection services includes a sensitive data discovery and classification system that can be tailored to specific standards. Other functions include user activity tracking and checks on the movement of data. Runs on Windows Server. Get a 30-day free trial.
- Digital Guardian DLP This cloud-based data loss prevention platform tracks activity on endpoints, and networks control data movements. Endpoint agents for Windows, macOS, and Linux.
- Endpoint Protector This SaaS data loss prevention package works through endpoint agents to spot threats and block data theft. It is a good choice for businesses that need to show standards compliance.
- Symantec Data Loss Prevention An package for installation on site. This system includes controls on data exfiltration points and sensitive data discovery and classification. It runs on Windows Server, Linux, or over a VM.
- Azure Information Protector A protection system that focuses on sensitive data and can monitor activities on any endpoint anywhere.
You can read more about each of these options in the following sections.
1. ManageEngine Endpoint DLP Plus (FREE TRIAL)
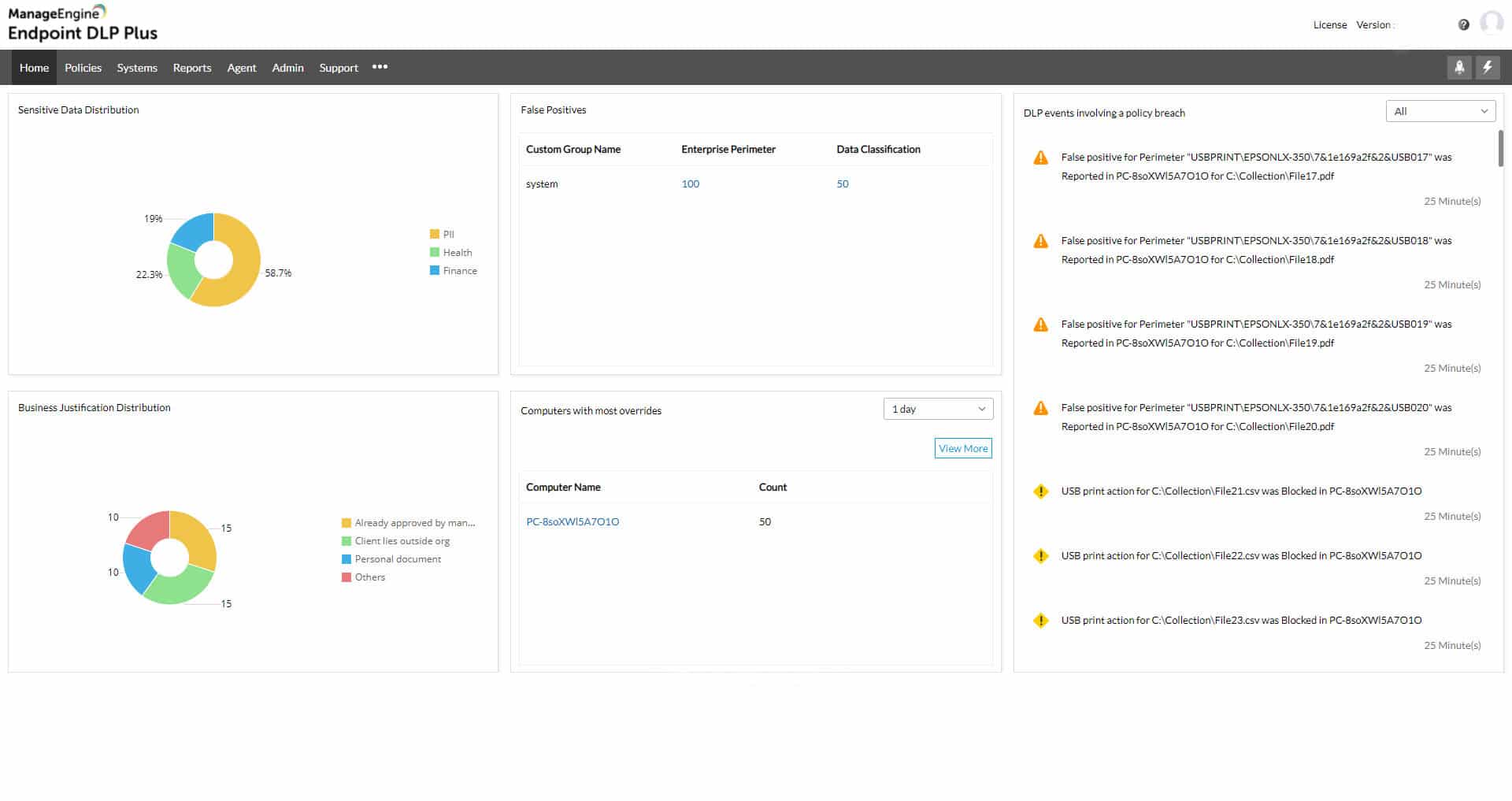
ManageEngine Endpoint DLP Plus competes well with Teramind DLP because it includes user activity monitoring as well as data classification and protection procedures. Data thieves get onto your system by hijacking user accounts and authorized staff members can go rogue for a variety of reasons, so monitoring user activity is an important defense mechanism. Data access events are the first part of activity tracking for DLP and the second is data movements. The ManageEngine system has routines to watch over both of these potential threats to data security and integrity.
Key Features:
- UEBA: User and entity behavior analytics
- Choice of Data Movement Responses: Block, allow and log, or just log
- Free Edition: To monitor up to 25 endpoints
- Automated Responses: Set up actions to trigger on alerts
- Software Download: Runs on Windows Server
Why do we recommend it?
ManageEngine Endpoint DLP Plus is a comprehensive data protection system. It includes data discovery and classification routines as well as activity tracking and file protection. This is a full package and it can also be set up to implement automated remediation. The package includes a user activity tracking routine, which competes directly with Teramind DLP.
No DLP system is going to protect all of the data on your system. They just focus on data types that are subject to regulatory controls. The primary goal for most data thieves is personally identifiable information (PII) and payment card details. When setting up Endpoint DLP Plus, you specify the types of data that you want to protect by selecting a template from the settings library.
Endpoint DLP Plus scours all of your endpoints and identifies instances of the sensitive data that concerns you. It then places controls on the files that contain that data. Once recorded, those data files will be constantly monitored for access events and changes.
The file protection mechanism uses containerization. This puts a wrapper around each file and prevents access to it other than through specified software packages. These are called trusted applications and it is expected that they will have their own access controls in place so that only authorized users can open them.
Data movement controls are not straightforward block/allow. Some users will be allowed to transfer some types of data, while other actions are blocked. This scrutiny is applied to email systems, peripheral devices, such as USB sticks, and cloud upload mechanisms.
Who is it recommended for?
This package is suitable for any business because protecting data against theft is an important task of corporate cybersecurity. However, the package is particularly important for businesses that hold personally identifiable information (PII). Small businesses with fewer than 25 endpoints can use the tool for free.
Pros:
- Discovers and Classifies Sensitive Data Instances: Creates a data catalog
- Tracks User Access to Sensitive Data Stores: Logs every event
- Protects Files: Only allows access through trusted applications
- Controls Data Movements: Via email, cloud upload, and peripheral devices
- Alerts for Suspicious Activities: Send them as tickets through Service Desk Plus
Cons:
- Not a SaaS Package: Only available for Windows Server
Endpoint DLP Plus runs on Windows Server. Small businesses can use the system free forever to monitor up to 25 computers. The paid edition, called Professional is available for a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Endpoint DLP Plus is our top pick for a Teramind DLP alternative because it provides granular sensitive data classifications along with its discovery process. This tool can be adjusted to match the requirements of data protection standards, such as PCI DSS and HIPAA, or government legislation, such as GDPR. The system will control data-related activity rather than block it and that enables the right people to get on with their jobs while preventing data theft or corruption.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/endpoint-dlp/download.html
OS: Windows Server
2. Digital Guardian DLP
Digital Guardian DLP is a SaaS platform that issues controls from its cloud location to any endpoint you enroll in the monitoring service. As a result, you can consolidate the security of multiple sites and also cloud services. In addition, the system performs live monitoring of networks as well as endpoints.
Key Features:
- A SaaS Package: No need to download or host
- Audits Access Rights Managers: Recommends account tightening
- Multi-Platform: Scans Windows, macOS, and Linux endpoints
- Network Activity Detection Through an Appliance: Either a physical device or a virtual appliance
Why do we recommend it?
Digital Guardian DLP is a cloud-based system that requires endpoint agents and a network appliance to look at activity across the site. This system doesn’t have its own sensitive data discovery process, so you need to buy a second package for that function. The system can manage data that is held on endpoints running Windows, macOS, and Linux.
The centralized functions of Digital Guardian DLP audit your access rights manager to improve the granularity of user account permissions. It is in the dashboard of the cloud server that you specify security policies. These can be applied by selecting a template from the library of Data Guardian. There are templates available for all of the significant data privacy standards.
Once you have improved the permissions structure and specified security policies, the server sets up the endpoint agents to scan sensitive data. The scanner also classifies each data instance – some will be categorized as pertinent to the standards you set. In contrast, others will be regular transaction information that doesn’t need stringent protection. The system looks for personally identifiable information (PII) and intellectual property.
Who is it recommended for?
This system provides a series of security tools as well as data loss prevention – all of them are linked. The general purpose of the package is to protect data by securing user accounts against account takeover. The system also includes constant activity teaching, which will spot both intruders and insider threats.
Pros:
- Pre-Built Compliance Policies: Get up and running quickly
- Includes a Threat Detection System: Looks for insider threats as well as intruders
- Managed Service Option: Hire Digital Guardian to run your data protection system
- SIEM Integration: Send activity data to a SIEM to contribute to threat hunting
Cons:
- Sensitive Data and Classification are Not Included: Needs a third-party tool
Digital Guardian DLP controls data exfiltration points and also acts as a threat detection system. There are endpoint agents available for Windows, macOS, and Linux. You can assess this system with a demo account.
3. Endpoint Protector
Endpoint Protector is a cloud-based data protection system that installs agents on endpoints to implement controls. Those endpoint protection units are entirely independent to continue implementing security even when the device is disconnected from the network.
Key Features:
- Implements Sensitive Data Discovery and Classification: Creates a data catalog
- Imposes Encryption at Rest and in Motion for Sensitive Data: Implemented on Windows, macOS, and Linux
- Monitors Printer Queues: Can prevent users from printing out sensitive data
Why do we recommend it?
Endpoint Protector discovers and categorizes sensitive data, making protection possible. The tool also provides controls over data movement channels, such as USB sticks. The package implements encryption to protect data and that includes encryption for USB memory sticks. The service manages data held on computers running Windows, macOS, and Linux.
Endpoint Protector is a lot like a SIEM because all endpoint agents gather log messages, generate activity reports, and then upload that information to the server for the system in the cloud.
This package includes sensitive data discovery and a classification service that identifies data stores that need extra protection. In addition, the service can impose encryption on files at rest and in motion to strengthen security.
The central system allows for the creation of security policies. These dictate how data controls are going to be applied. These strategies are then communicated to the endpoint agents for implementation. The server also scans through your access rights manager and improves the permissions structure for tighter security.
Parts of the activity reports that the endpoint agents generate rely on user and entity behavior analytics (UEBA). This profiles each user account and checks on the regular system processes run on the endpoint. Once those baselines of regular activity have been established, the endpoint agent looks for deviations in behavior. This is a classic threat detection strategy, and it helps to identify insider threats and account takeovers.
The endpoint agents watch over data exfiltration points, including USB memory sticks, printers, emails, and file transfer systems.
Endpoint Protector is a great Teramind DLP alternative because it had a more comprehensive range of deployment options. It includes endpoint agents for Windows, macOS, and Linux. This service offers threat detection as well as data loss prevention, just like Teramind DLP. In addition, it consists of discovering and classifying sensitive data, which makes it an excellent choice for businesses that need to comply with a data privacy standard.
Who is it recommended for?
This package is suitable for companies that need to control the usage and movement of some data on the system – notably personally identifiable information. The package helps with compliance with HIPAA, PCI DSS, and GDPR. You get a choice of whether to subscribe to the package as a SaaS platform or get the software and install it on your own cloud account.
Pros:
- Controls Data Exfiltration Channels: Emails, FTP, movement to USBs, and cloud uploads
- Full Stack Protection: Combines endpoint, network, and cloud security monitoring
- Offered as a SaaS Platform: Also can be installed on your cloud account
Cons:
- No Free Trial: You can get a demo
Endpoint Protector can be accessed as a service on AWS, Google Cloud Platform, or Azure for a fee. The producers of Endpoint Protector, CoSoSys, also offer the service as a SaaS platform. There are endpoint agents for Windows, macOS, and Linux. It is also possible to get the software to run as a virtual appliance on your site. You can access a demo to assess the service.
4. Symantec Data Loss Prevention
Symantec Data Loss Prevention includes security monitoring for endpoints, networks, storage devices, and cloud platforms. This is an on-premises package, but it can also monitor activities on cloud platforms.
Key Features:
- Digitizes Documents for Security Protection: Uses optical character recognition (OCR)
- Can Identify Data in Images: Looks through PDFs and JPEGs
- Offers Network Scanning: Searchers for the movement of sensitive data
Why do we recommend it?
Symantec Data Loss Prevention is available in two versions: Data Loss Prevention Core Solution for on-premises systems and Data Loss Prevention Cloud Solution, which protects data held on cloud accounts. This system has many modules, which include network scanning for the on-premises system and a Cloud Access Security Broker (CASB) in the cloud package.
As with most DLP systems, you first need to set up security policies. It is possible to select a template that includes all of the settings required for a specific data privacy standard. This is the kernel of the data protection strategy that is then applied to the data locations on your system. The system searches files, databases, and cloud storage. Data controls and access can be enforced through encryption. All data access events are recorded.
The Symantec Data Loss Prevention package is available for Windows, Windows Server, macOS, and Linux.
Who is it recommended for?
This system is very comprehensive and includes many different scanning techniques, including the detection of data in images. This is a sophisticated solution that is going to be beyond the budgets of small businesses, so large organizations and the higher end of the mid-size business market will be interested in this package.
Pros:
- Sensitive Data Discovery and Classification: Creates a data catalog
- Controls Over Data Access: Enforces access restrictions with encryption
- Multi-Platform Protection: Covers cloud services as well as on-premises activities
Cons:
- No Free Trial: No demo
5. Azure Information Protection
Azure Information Protector is a service that is offered on the Azure platform. However, this service can protect data held on other platforms and any of your sites. So, it isn’t limited to monitoring data held on Azure. You don’t need to store any data on Azure to use this service.
Key Features:
- Focused on Microsoft Products: Will also scan other cloud-based apps but has a stronger integration with Microsoft
- User Activity Tracking: Records access to sensitive data
- AI-Based Classifiers: Can spot combinations of fields that constitute sensitive data
Why do we recommend it?
Azure Information Protection is transitioning into Microsoft Purview Information Protection. Rather than expanding the capabilities of the product, this move is actually reducing the locations that the system will scan to identify sensitive data and implement protection. The system works automatically with Microsoft 365 and can be extended to look at other cloud systems.
On starting with this service, you need to set up security policies in the console. This dashboard can be accessed through any standard Web browser, and it is possible to create policies that will enforce compliance with a data privacy standard.
The system installs an agent on the network that is going to be monitored. This program scans all connected endpoints, looking for data stores. It classifies them by importance to the security policy. Protection features in this package include file copy tracking and document watermarking.
Who is it recommended for?
Although it is possible to link this scanner into third-party tools, the process isn’t easy. The data loss prevention service is very easy to use with Microsoft 365 and so the main market for this package will be companies that use that suite extensively, to the exclusion of all other productivity suites.
Pros:
- Sensitive Data Discovery and Classification: Uses multiple methodologies
- Watermarking and Copy Tracking: Identifies the source of leaked data
- Data Exfiltration Controls: USB ports, emails, printers, and file transfer utilities
Cons:
- Reduced Capabilities: Moving towards operating only on Microsoft products