Verbatim EasyLock and CoSoSys Endpoint Protector offer ways to protect data; however, these two systems are very different. While the EasyLock system imposes security on a USB device, Endpoint Protector controls the useability of a USB drive when connected to an endpoint that is monitored by the CoSoSys service. However, further investigation reveals a part of the Endpoint Protector system that is remarkably similar to Verbatim EasyLock.
What is a USB?
When people talk about “a USB” there are two different pieces of equipment that they could be referring to. The term “USB” stands for “Universal Serial Bus” It is a standard for a connector. The USB design has become very widely used, and the use of a converting cable with a different connector on the other end enables a wide range of devices to be connected to a desktop or a laptop.
The other “USB” is a removable device that has the USB connector fitted into it. MP3 music players fall into this category and do “dongles” that provide wireless internet to computers. The most widely-used type of USB device is a flash drive, which provides a large amount of storage space in a tiny piece of equipment.
For businesses, USBs provide great opportunities. Although these devices don’t include CPUs, they can be loaded with an operating system and a complement of software. If made bootable, the USB can provide an entire computer environment that becomes available on the computer that you connect it to and then completely removed when the device is taken out. It is a lot like a physical version of the container or virtual machine. USB flash drives can also temporarily provide extra storage space, and they also offer a way to move large amounts of data. They are also sometimes used to store backups.
On the other hand, USB devices represent a threat to data security. It is straightforward for an employee to stick a USB flash drive into the workplace computer, copy over a large amount of data, and then walk out of the building with it.
Verbatim USB devices
Verbatim is a brand of storage device. The brand started up in the USA in 1978, and it is now a division of Taiwanese conglomerate CMC Magnetics Corporation. Among the Verbatim range of products are several USD storage device models.
Verbatim produces USB drives with a storage capacity of 2 GB to 64 GB. Some of the drives from Verbatim are pre-loaded with encryption software with AES 256-bit encryption and require credentials to access them. However, other devices are shipped with minimal management software and, effectively, are entirely blank. For these unmanaged USB devices, Verbatim offers a free software download of EasyLock. This is the same software that is pre-loaded onto the encrypted USB drives.
Verbatim EasyLock
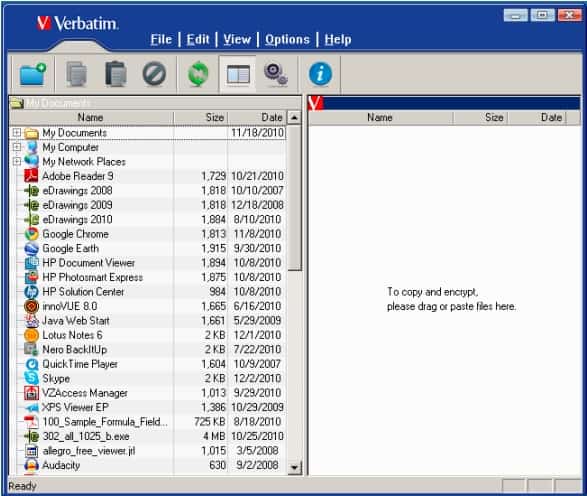
EasyLock is available for free from the Verbatim website. The download file is an executable that you should save to your Verbatim flash drive. Some Verbatim models already have EasyLock installed on them when they are sold. The software is intended for use on Store ‘n Go and Tuff ‘n Tiny models.
EasyLock creates a secure locker on the device. There are no user accounts in EasyLock, just one account with one password.
The EasyLock system includes a file explorer window that allows files to be moved into the secure area on the drive. This explorer shows all locations accessible to the drive, mainly the drives of the computer to which the USB device is connected. The user moves files through a drag-and-drop action. In addition, files can be accessed directly from the encrypted store through an appropriate editor utility, such as Word or Excel.
Pros:
- Available for free
- Familair UI – similar to explorer
- Simple drag-and-drop options
Cons:
- Better suited for smaller businesses
The encryption on the USB is entirely autonomous. The system does not rely on any software installed on the computer to which the USB device is attached. In addition, the password set up on the device is constant – that is, you don’t have the opportunity to log into it with different accounts.
Data Loss Prevention
A data loss prevention system (DLP) is essential for businesses that store the personally identifiable information (PII) of public members. The control of this type of data is regulated by legislation and industry standards in many parts of the world.
A DLP system needs to locate all stores of data and then scan through all data, identifying instances of sensitive data. Security procedures need to be strengthened around the use and movement of this data.
DLP services can protect data at rest, in motion, or both. Protection methods for data at rest include encrypting files and creating a user account with permissions for different rights on those files, such as the right to view only, edit, or copy. Protection for data in motion requires monitoring tasks that scan network traffic. It can also be necessary to take control of the ports to which USB flash drives connect. These ports can be treated like network interfaces, and they can either be blocked from connecting, or specific devices can be approved. In addition, some systems can perform sophisticated variable controls that allow particular user accounts to move specific data categories onto specific USB devices.
CoSoSys Endpoint Protector
Endpoint Protector is a DLP solution that protects data at rest and in motion. Most of the activity performed by Endpoint Protector takes place on endpoints. The system lets you create security policies in the central console, which defines what constitutes sensitive data in your system. The service then searches out data locations and scans for instances of sensitive data.
Pros:
- Custom security policies can be based on the user rather than the machine
- Automatically assesses risk based on vulnerabilities found on the endpoint
- Can alert to improper file access or insider threats (Acts as a DLP solution)
- Prevents data theft and BadUSB attacks through device control settings
Cons:
- Would like to see a trial version available for testing
The file of identified sensitive data can be encrypted for protection. The system then tracks any movements of marked files and can prevent them from being attached to emails, sent to printers, transmitted with file transfer systems or chat apps, or copied onto removable storage.
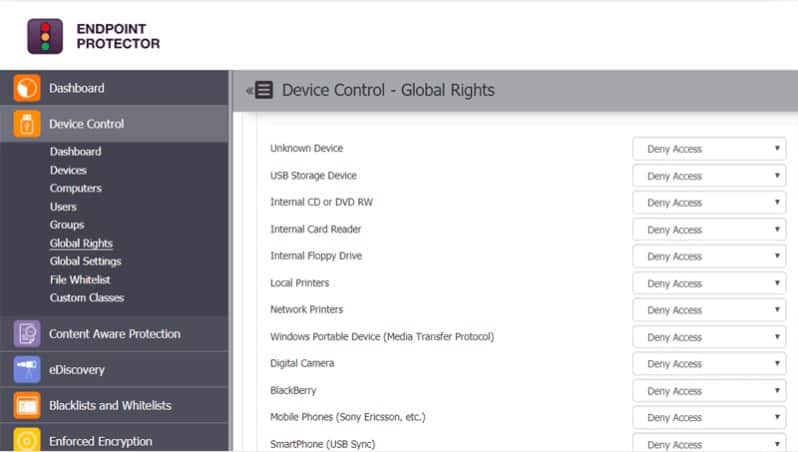
The device control services of Endpoint Protector can manage a range of storage devices, not just USBs. Other types of storage that the Endpoint Protector system can manage include DVD ROMs, printers, and digital cameras.
The USB controls included in Endpoint Protector allow system managers to block all access to USB ports, preventing USB drives from mounting. In addition, the software can identify individual USB drives and allow only listed devices to mount. These file movement controls can be applied only to files that have been placed as containing sensitive data.
The controls over data transfers onto USB drives include the enforcement of encryption. This is a USB-wide service and means that data can only be transferred onto a USB if the encryption system is present. This is called EasyLock Enforced Encryption.
EasyLock Enforced Encryption operates on an endpoint that is monitored by the CoSoSys software. It copies another program onto the device, and it is that portable system that implements encryption. That USB-resident system is called EasyLock, and it creates a secure locker on the device that is an encrypted file space and is password protected.
Users access a file manager window and transfer files from the host device to the USB device through a drag-and-drop function.
EasyLock Enforced Encryption coordinates with the Endpoint Protector endpoint agent. The agent communicates with a central server for Endpoint Protector. That chain of modules allows an administrator to manage the USBs that connect to the system remotely.
Without the EasyLock Enforced Encryption module installed on the local computer, the system administrator can’t control and log the movement of files on and off a device if that device has been approved for connection and the USB port on the computer is not blocked.
Verbatim EasyLock vs. CoSoSys Endpoint Protector head-to-head
Verbatim EasyLock is a white-labeled earlier version of the EasyLock that is integrated into Endpoint Protector. The Endpoint Protector EasyLock operates in the same way as the Verbatim EasyLock, but it has a more attractive design in its interface.
The Endpoint EasyLock can coordinate with a controlling module called EasyLock Enforced Encryption, which is not available with the Verbatim EasyLock. In addition, the ability to communicate with a central controller and impose the same security rules on all USB ports on all devices on a company’s network is available with Endpoint Protector but not with Verbatim EasyLock.
Deployment options
Verbatim EasyLock is pre-installed on Verbatim Store ‘n Go and Tuff ‘n Tiny USB devices. The software is available for free, so there is nothing to stop anyone trying to install the system on any other make or model of USB flash drive, though there is no guarantee that it will work.
The Endpoint Protector system is considerably more complicated. Zooming out from the USB-resident software, the EasyLock software will work on any USB device. It is also available to password-protect DVDs and CDs used for data storage. It can also be used on memory cards and the storage areas of devices that connect to a USB port, such as digital cameras.
The EasyLock Enforced Encryption module will run on Windows version from Windows XP up to Windows 10. It is also available for Macs running Mac OS 10.8 up to macOS 10.14.
The more comprehensive Endpoint Protector system is a central server that communicates with agents installed on endpoints running Windows, macOS, or Linux. The server is available from CoSoSys as a SaaS platform. It can also be added to an account on Azure, Google Cloud Platform, and AWS. Another option is to download the software and run it on a virtual machine.
Encryption method
Being two versions of the same software, Verbatim EasyLock and Endpoint Protector EasyLock use the same encryption system. This is AES-256. That means the Advance Encryption Standard, using a key that is 256 bits in length. AES is a symmetric cipher, which means that the same key is used for encryption and decryption. The user does not need to intervene in the encryption process because the EasyLock software manages this.
Security policy management
Verbatim EasyLock is a standalone portable program resident on the USB flash drive and doesn’t have any facilities for defining or enforcing security policies. Instead, it encrypts files copied onto the device and prevents access to the encrypted area with a password requirement.
Endpoint Protector EasyLock is precisely the same as Verbatim EasyLock. However, its interaction with EasyLock Enforced Encryption means that security policies defined in the central console for Endpoint Protector can be implemented by controlling the computer side of the transfer of files onto the USB.
Price
Verbatim EasyLock is free to download. The Endpoint Protector EasyLock is only available as part of the complete Endpoint Protector DLP package. CoSoSys doesn’t publish a price list for its system. You need to contact CoSoSys for a quote. It is possible to access a demo account for Endpoint Protector, but that shows how the central server works and doesn’t include access to the EasyLock module.
Verbatim EasyLock vs. CoSoSys Endpoint Protector EasyLock: The verdict
The Endpoint Protector version of EasyLock is newer than that offered by Verbatim. However, it isn’t possible to get the Endpoint protector EasyLock by itself. Instead, EasyLock is an excellent extra service that makes the DLP system of Endpoint Protector more comprehensive.
The Verbatim EasyLock is only intended for use with Store ‘n Go and Tuff ‘n Tiny USB devices. However, there is no access control on the download for the software so that anyone can try it on any brand of USB memory stick.
Verbatim EasyLock vs Endpoint Protector FAQs
What is EasyLock?
EasyLock is an encryption system that can operate on USB devices to create a secure locker – a private space for files. The package used AES-256 encryption in the creation of an area on the drive. The tool offers a file explorer and this enables you to move files and folders into the secure locker out of the general access area of the device. creates a secure locker on the device. There are no user accounts in EasyLock, just one account with one password.
What is Endpoint Protector client?
Endpoint Protector is a data loss prevention system that is based in the cloud and extends protection to all enrolled endpoints on a network. Each endpoint needs an agent installed on it to communicate with the central Endpoint Protector server. This is the Endpoint Protector client and it is available for Windows, macOS, and Linux.
Do you need antivirus if you have endpoint protection?
Endpoint protection is a term that describes a centrally controlled security solution for all of the devices of a business. Each endpoint has a component installed on it to enable communication with the endpoint protection service. The endpoint protection service usually includes an antivirus element or an alternative threat hunting system that substitutes for an AV. Therefore, it is not necessary to also install an antivirus package on a device that is covered by endpoint protection.