Zero Trust Networking is a modern approach to cybersecurity that challenges traditional network security models, particularly the once-popular “trust but verify” approach. Instead of assuming that everything within an organization’s network is secure, Zero Trust operates on the principle that no entity, whether inside or outside the network, should be trusted by default.
Here is our list of the best Zero Trust Networking Software:
- Check Point’s SASE Zero Trust Platform EDITOR’S CHOICE A choice of three access control platforms that deal with web applications, networks, and cloud services. This access rights system is delivered from the cloud and integrates VPN services to prevent hackers from bypassing security measures.
- Twingate ZTNA Software (FREE TRIAL) A cloud-based perimeter service that manages all access processes for on-premises and cloud-based resources.
- NordLayer (GET DEMO) A package of security tools that implement full or partial internet security that can be configured to provide Zero Trust Access in a SASE. This is a cloud-based system with device agents.
- ThreatLocker (GET DEMO) Use this platform of system security tools to create a Zero Trust Access (ZTA) environment and protect applications. This is a cloud-based package.
- UTunnel (GET DEMO) Zero Trust Networking software offering secure remote access, flexible hosting options, and robust encryption for businesses.
- CrowdStrike Falcon Zero Trust An access management system that includes integrated user behavior analysis and a threat intelligence feed. This is a cloud-based service.
- Ivanti Neurons for Zero Trust Access This cloud-based system provides Zero Trust Network Access (ZTNA) for mobile devices as well as Zero Trust Access (ZTA) for application protection.
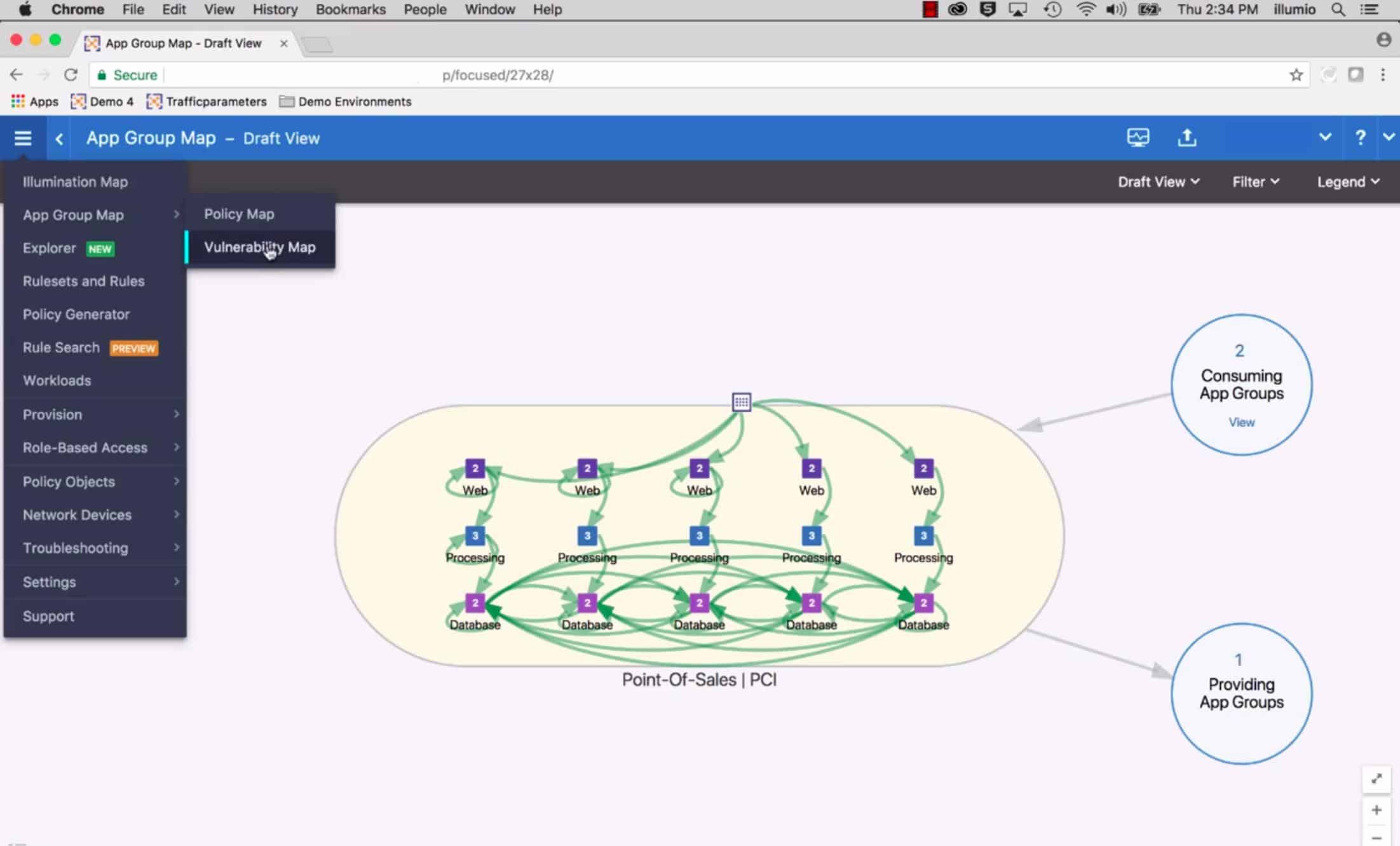
- Illumio Zero Trust Platform A choice of network-focused or endpoint-focused access rights management strategies.
- Appgate SDP This software-defined perimeter system unifies connection security, application fencing, and access rights management to create a ZTA package.
- Cisco Secure Workload Security controls that follow users across devices and also offers access rights management solutions for resources and connections.
- Absolute ZTNA This is a software-defined perimeter package that provides corporate network security across LANs and internet connections.
The core of the philosophy is called Zerto Trust Network Access (ZTNA). Each user and device is continuously verified, regardless of their location. This shift is driven by increasing concerns about cyber threats, remote work environments, and the growing complexity of IT infrastructures. In practice, Zero Trust, when applied to access for all resources would require repeated logins per session for each user. Many actions require access to multiple resources and a separate access challenge for each would make life difficult for users.
ZTNA is often accompanied by access rights technologies that both enhance authentication and ease the stress of repeated credentials demands. So, it is very common to see multi-factor authentication (MFA) used on systems that also deploy ZTNA. It is also very common for the related login demands to be fulfilled automatically by a single sign-on (SSO) mechanism.
As organizations adopt cloud services, use mobile devices, and deploy complex hybrid networks, traditional perimeter-based security methods have become insufficient. Zero Trust Networking software provides a dynamic security framework that ensures continuous authentication and authorization for every user, device, and network interaction, thereby reducing the risk of data breaches and cyberattacks. Rather than granting broad access, Zero Trust applies strict controls and principles of least privilege, ensuring users and devices only access the resources they need, when they need them.
This model offers many benefits, including reduced attack surfaces, minimized lateral movement by attackers, and better visibility into network activity. Zero Trust also helps organizations comply with stricter data protection regulations and improve overall network resilience against modern cyber threats, such as ransomware and insider threats.
What is Zero Trust Network Access (ZTNA)?
Zero Trust Network Access (ZTNA) is a shift in approach to security whereby access is denied unless it is explicitly granted and the right to have access is continuously verified.
The idea behind zero trusts is that the network devices should not be trusted by default, even if they are connected to a corporate network or have been previously verified.
The zero trust approach advocates checking the identity and integrity of devices irrespective of location and providing access to applications and services based on the confidence of device identity and device health in combination with user authentication. ZTNA reduces insider threat risks by always verifying users and validating devices before granting access to sensitive resources. For outside users, services are hidden on the public internet, protecting them from attackers, and access will be provided only after approval from their trust broker. According to Gartner, by 2022 80% of new digital business applications will be accessed via ZTNA.
Most ZTNA solutions are implemented as a Software-Defined Parameter (SDP). Zero trust networks enabled as SDPs are in a better position to manage cyber-attacks across networks. The zero trust network framework comprises the following key components:
- Visibility: This helps security teams gain deeper network visibility, and track the flow of data and device as it moves through its lifecycle.
- Micro-segmentation: With micro-segmentation, organizations can limit internal access to networks and assets to only those that need to reach those assets. This helps to reduce the total attack surface of the network. and it entails moving the perimeter to workloads.
- Least privileged access: ‘Least privilege’ principle allows users to access only the resources and applications they need to effectively do their job.
- Monitoring: AI technology can be used to continuously monitor risk and trust to ensure the right security posture is maintained.
The best Zero Trust Networking Software
With the right ZTNA solution, organizations can ensure proper user context through authentication and attribute verification before allowing access to network resources at a fraction of the cost, complexity, and security risk of the traditional approach. In this article, we’re going to review the seven best ZTNA solutions in the market. Hopefully, this will guide you in the process of choosing the right solution for your business.
Our methodology for selecting Zero Trust networking software
We reviewed the market for Zero Trust systems and analyzed the tools based on the following criteria:
- Options for Zero Trust Access (ZTA) and Zero Trust Network Access (ZTNA)
- Microsegmentation to manage access to applications
- An integrated identity and access manager or an interface to a third-party IAM
- Standardization of access to on-premises and cloud-based services
- A unified IP address management system
- A free trial or a demo package for a cost-free assessment opportunity
- Value for money that is provided by a comprehensive networking tool that is delivered at a reasonable price
With these selection criteria in mind, we identified a number of innovative Zero Trust systems that will enable you to protect on-premises and cloud-based applications.
1. Check Point’s SASE Zero Trust Platform (GET DEMO)
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: www.sase.checkpoint.com
Money-back guarantee: 30 DAYS
Check Point’s SASE, formerly Perimeter 81, is on a mission to transform traditional network security technology with one unified Zero Trust Network as a Service. Perimeter 81’s zero trust solution is offered via the following platforms:
- Zero Trust Application Access Helps to ensure zero trust access to web applications and remote network access protocols such as SSH, RDP, VNC or Telnet, through IPSec tunnels – without an agent.
- Zero Trust Network Access Helps to ensure zero trust access to on-premises and cloud resources with one unified cloud platform.
- Software-Defined Perimeter Helps organizations conceal internal network resources and assets from external entities, whether it is hosted on-premises or in the cloud.
Check Point’s SASE zero trust platforms are a scalable hardware-free solution that helps organizations provide secure access to their network infrastructure and digital assets including local and cloud resources from end-point to data-center to the cloud. It offers network visibility, resource access segmentation, and full integration with major cloud providers, giving organizations peace of mind in the cloud. The solution is ideal for SMBs, especially those looking for a modern alternative to traditional corporate VPN systems.
Key Features:
- Unified Identity Management: Streamlines user authentication across all applications.
- Microsegmentation: Enhances security by isolating network segments.
- User Access Portal: Simplifies access to applications and services.
- Two-Factor Authentication: Adds an extra layer of security for user verification.
- Network Performance Monitoring: Keeps track of network health and performance.
Why do we recommend it?
Check Point’s SASE Zero Trust Platform is a package of tools that enables a range of security strategies to be implemented. The system works like a VPN with a built in Access Rights Manager (ARM). The user gets an app and signing into that gives access to a menu of permitted applications.
The onboarding process is smooth and issue-free. When you sign up with Check Point’s SASE, you get a full management platform where you can build, manage, and secure your network. To get started, all you need to do is to sign up, invite your team, install the client apps, and create user groups. By clicking on the link in the Downloads section of the platform, you can download the client app on your preferred platform and follow the wizard to complete the installation. You can give network access to as many team members as possible, assign them to specific groups, and add or remove user permissions with a single click.
Who is it recommended for?
This is a very easy system to implement, so, it is suitable for use by businesses of all sizes. You just need to set up a list of apps and a list of users, map one to the other and then distribute the login app.
Pros:
- Broad Integration: Seamlessly integrates with major identity providers for comprehensive access management.
- Centralized Control: Offers a single management point for cloud and on-premises applications.
- Enhanced Security Features: Includes two-factor authentication, automatic WiFi protection, and a kill switch for added security.
- Global Network Reach: Supports deployment across 700 servers in 36 countries for wide coverage.
- Advanced Connectivity: Facilitates site-to-site connections and implements policy-based network segmentation for refined access control.
Cons:
- Service Complexity: Presents a suite of services which may require a detailed setup rather than a straightforward virtual network solution.
Check Point’s SASE offers flexible payment plans with billing occurring on a yearly or monthly basis. Sign up process for all plans are commitment-free and have a 30-day money-back guarantee. The table below is a summary of the various subscription plans and associated features.
Price Plan | Cost (billed annually) | Minimum No. of Users | Features |
|---|---|---|---|
Essentials | $ 8 per user/month per gateway | 5 |
|
Premium | $12 per user/month per gateway | 10 |
|
Enterprise | Custom: + $40/month per gateway | 50 |
|
EDITOR'S CHOICE
Check Point’s SASE Zero Trust Platform is our number one choice for zero trust networking software because it offers a great deal of deployment flexibility. This service is available to protect web applications through supervised and strengthened access control. Typical network and business resource access controls are also available and a software-defined perimeter offering gives a third deployment option. Check Point’s SASE Zero also offers a traditional VPN connection privacy service. Check Point’s SASE Zero Trust is a subscription service and it comes with a 30-day money-back guarantee.
Download: Access FREE Demo
Official Site: https://www.sase.checkpoint.com/demo
OS: Cloud-based
2. Twingate ZTNA Software (FREE TRIAL)
Twingate enables organizations to implement a modern zero trust network without changing existing infrastructure, and centrally manage user access to company digital assets, whether they are on-premises or in the cloud. Twingate ZTNA solution is offered as an SDP service or an alternative to a traditional VPN. It is delivered as a cloud-based service, and delegates user authentication to a third-party Identity Provider (IdP).
Key Features:
- Simplified Deployment: Offers an easy-to-implement solution for secure access.
- Robust Access Controls: Provides comprehensive control over user access.
- Detailed User Activity Logs: Ensures visibility into user activities for security and compliance.
Why do we recommend it?
The Twingate ZTNA Software system is very similar to NordLayer. Essentially, this is a VPN with udder authentication built into the access app. All users log into the app and that connects them to a hub. Applications will only accept connections from the hub, which passes authorized users.
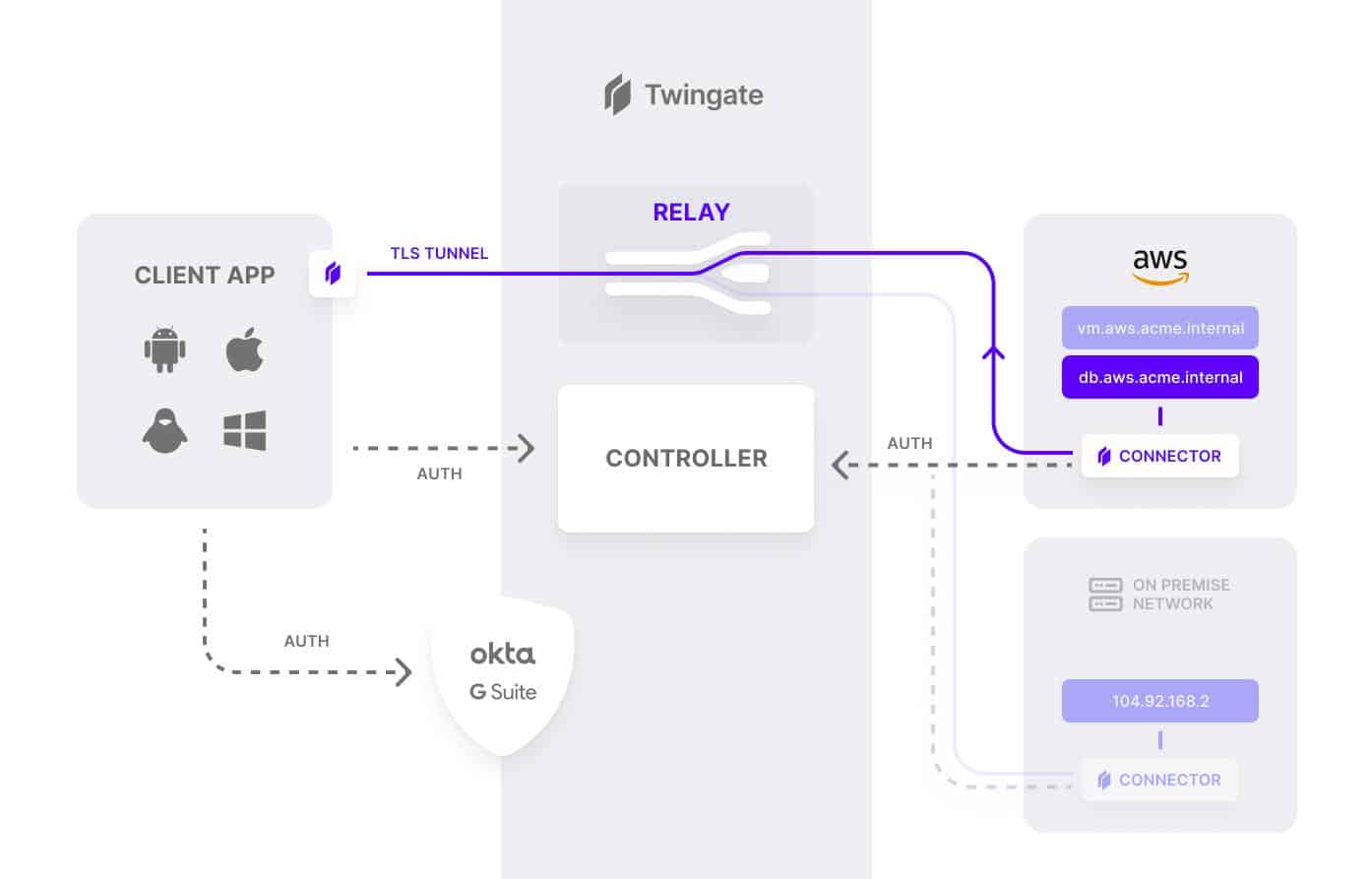
No special technical knowledge is required from end-users other than to download and install the SDP client application and authenticate with an existing identity provider. The controller handles the rest, negotiating encrypted connections between clients and resources. Once everything is confirmed, users are routed to the appropriate resources.
A key feature of the Twingate ZTNA solution is that authorization for user access is always confirmed with a second or third component depending on the sensitivity of the decision being authorized. No single component can independently make a decision to allow traffic to flow to another component or resource in your remote networks.
Who is it recommended for?
Twingate is easy to set up and use and it is particularly interesting for small businesses. If you have up to five users, you get the system for free. The SSO function is only available in the paid packages and that is a big advantage.
Pros:
- User-Friendly Security: Delivers a secure access solution that’s straightforward for users to engage with.
- Self-Service User Management: Empowers users with the ability to manage their access and authentication.
- Principle of Least Privilege: Adheres to least privilege access, granting users only the access they need.
Cons:
- Initial Setup Consideration: Requires thoughtful planning to effectively implement the environment.
The Twingate zero trust architecture relies on four components: Controller, Clients, Connectors, and Relays. These components work in tandem to ensure that only authenticated users gain access to the resources that they have been authorized to access. It is is offered in four flexible price plans as shown on the table below which also include a 14-day free trial option:
Price Plan | Cost (billed annually) | Target Market |
|---|---|---|
Starter | Free | Individuals or very small teams |
Teams | $5 / user / month | Smaller teams that need to replace a VPN for remote access |
Business | $10 / user / month | Larger teams that need more advanced access controls |
Enterprise | Custom | Companies that need comprehensive access controls, detailed auditing, and deployment automation |
3. NordLayer (GET DEMO)
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: www.nordlayer.com
Money-back guarantee: 14 DAYS
NordLayer is a business network security platform that provides tools that can be set up to create a range of secure network configurations and Zero Trust Access is one of the tools available in the system. NordLayer is a new service from Nord Security, the company behind NordVPN.
Key Features:
- Secure Remote Access: Enables secure network connectivity for remote employees.
- Site-to-Site Protection: Offers robust internet protection for connecting multiple sites.
- IAM at Application Level: Manages identities and access rights for applications.
- Virtual Office: Creates a secure, virtual office environment for distributed teams.
Why do we recommend it?
NordLayer is a similar system to the Zero Trust feature in the Perimeter 81 platform. This is an evolution of a VPN service. The company, Nord Security, added an IAM to its VPN and point all business users to a single hub server, which acts as a virtual router.
The NordLayer package offers all of the building blocks to implement a full Secure Access Service Edge (SASE) implementation for your business. However, the service is structured in such a way that you don’t have to implement the entire SASE philosophy if you don’t want to.
The key element of the system is a user app. Access to business resources is controlled through the app’s login screen. This provides a single sign-on for a menu of services and the administrator can device what applications go on each user’s list. Those systems can be on-premises, on a remote site, or on the cloud.
The NordLayer app gets remote users included in the business’s network. Access to company sites and cloud accounts is mediated through a NordLayer cloud server. The NordLayer app negotiates connection security with the server and that is active for the entire work session. Other features offer similar internet protection for the gateways of entire LANs.
NordLayer provides a very easy way to implement application access controls. Anyone who is familiar with VPNs can understand this system. There is one difference between the user app for this system in that it provides a menu of applications. The administrator sets up user accounts and allocates applications to each. When users want to get access to corporate resources, they have to log in to the access app. That login ripples through to application logins through an SSO mechanism. The package treats all users equally, whether they are on a company network, sitting at home, or roaming on a mobile device. All access passes through the NordLayer server for assessment. Higher plans get a dedicated IP address, which fronts for the entire company, providing a single public address for numerous sites and individual user devices.
Who is it recommended for?
This is another system that it easy to set up. It is particularly suitable for small businesses and enterprises that run virtual offices with lots of remote workers and cloud SaaS packages to link together. It is very easy to set up and manage – the system administrator can also be working from home.
Pros:
- Enhanced Connection Security: Ensures secure internet connections for business operations.
- Simplified Access Management: Facilitates easy access management with single sign-on capabilities.
- Roaming User Security: Allows users to securely access the network from any location.
- Application Protection: Shields individual applications from potential cyber threats.
Cons:
- Solution Flexibility: While versatile, it doesn’t offer a singular, all-inclusive cybersecurity solution.
The infrastructure for NordLayer is very easy to set up. You just need to get each user to download an app. There are apps available for Windows, macOS, Linux, iOS, and Android. After that, you need to set up your security policies and set up user access permissions in the administrator console – that can be quite a complicated task but it is guided by templates. The NordLayer service is charged for per user and it is offered in three plan levels. You can request a demo to work out which plan you will need.
The plans are:
Price Plan | Cost (billed annually) | Features |
|---|---|---|
Lite | $8 per user/month per gateway |
|
Core | $11 per user/month per gateway |
|
Premium | $14 per user/month per gateway |
|
Custom | As negotiated |
|
4. ThreatLocker (ACCESS DEMO)
ThreatLocker is a package of building blocks that create ZTA systems. The core module is its Allowlisting feature. This blocks all software from running and then selectively permits trusted applications with their own access controls to run. The service includes an Application Fencing service, which implements micro-segmentation and controls what resources an application can access
Key Features:
- Resource Access Control: Manages and restricts access to resources effectively.
- Application Allowlisting: Ensures only trusted applications are permitted to run.
- Activity Monitoring: Logs application activities for compliance and security oversight.
Why do we recommend it?
ThreatLocker is another ZTA solution that is pretty easy to set up, although it isn’t quite as straightforward as NordLayer or Perimeter 81. It works by setting up a microsegmentation plan and then generates Access Control Lists to insert into routers and implement the plan. This is a cloud-based system.
Access activity within applications is logged, which supports compliance reporting for PCI DSS, HIPAA, and GDPR. The Storage Control module blocks all USB ports on a computer and allows the administrator to enable a port for use by a specific user with a specific USB memory stick. All file movements involving the USB device are logged and the administrator should only allow a USB port to be open for a short period.
Who is it recommended for?
This is a good service for any company but it is particularly useful for those businesses that have external resources and remote workers. ACLs are very intelligent but they are difficult to get right. If you make a small mistake, a lot of users can be locked out, so this tool removes that risk.
Pros:
- Focused Application Security: Prioritizes application-level security controls for better protection.
- Micro-Segmentation: Implements detailed segmentation to safeguard specific resources.
- Compliance Support: Facilitates compliance with standards like PCI DSS, HIPAA, and GDPR through detailed logging.
Cons:
- Lacks Access Rights Management: Does not feature an integrated access rights manager for data protection.
The ThreatLocker system doesn’t include an access rights manager and if you particularly need to protect sensitive data, you will also need a separate tool for PII discovery and classification. You can assess ThreatLocker by accessing a demo.
5. UTunnel (FREE DEMO)
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: UTunnel.io
Money-back guarantee: 14 DAYS
UTunnel is a Zero Trust Networking software designed to secure network access for businesses, ensuring that every request is authenticated and validated, regardless of the user’s location or device. By leveraging Zero Trust principles, UTunnel.io enables enterprises to implement stringent security measures to protect sensitive data and corporate resources, making it an excellent choice for businesses that prioritize cybersecurity.
Key Features:
- Zero Trust Architecture (ZTA): Ensures strict access control by verifying each user and device.
- Self-Hosting Flexibility: Choose between cloud-hosted or on-premises VPN setups.
- Site-to-Site VPN: Create an SD-WAN or a SASE.
Why do we recommend it?
We recommend UTunnel because of its effective implementation of Zero Trust security, flexible deployment options, and strong encryption. It ensures that businesses can securely manage remote access and prevent unauthorized access to sensitive data, making it an excellent choice for organizations aiming to enhance their security infrastructure.
UTunnel enables businesses to adopt a Zero Trust Architecture (ZTA), a security model that assumes no user or device is inherently trusted, regardless of their location. This approach ensures that every request for access to corporate resources is continuously authenticated and validated before access is granted.
The platform also offers self-hosting capabilities, allowing businesses to host their VPN servers either on-premises or on a cloud account, giving them complete control over their network and security. Whether businesses need full control via self-hosting or prefer the convenience of cloud hosting, UTunnel.io provides a flexible and secure solution that aligns with ZTA principles.
Who is it recommended for?
UTunnel is ideal for businesses of all sizes that require secure remote access and are looking to implement Zero Trust Networking. It is particularly recommended for enterprises with strict compliance or security requirements, as well as teams that need flexibility in hosting their VPN infrastructure.
Pros:
- Strict Access Control: Continuously verifies users and devices through Zero Trust principles.
- Security Features: Kill switch and granular access controls.
- Strong Encryption: AES-256 encryption ensures robust data protection during transmission.
Cons:
- Requires technical setup for self-hosting: The self-hosting option might be too complicated for small businesses.
UTunnel offers various plans to suit businesses of all sizes, with options for both self-hosted and cloud-hosted setups. Pricing is based on the number of users and the required features, ensuring scalability and flexibility. Schedule a free demo.
6. CrowdStrike Falcon Zero Trust

CrowdStrike Falcon Zero Trust is a service that is delivered from the CrowdStrike Falcon SaaS platform. The real-time access management system incorporates threat prevention mechanisms that are also implemented in other CrowdStrike Falcon products.
Key Features:
- Integrated Access Controls: Manages both network and application access efficiently.
- BYOD Compatibility: Well-suited for environments with Bring Your Own Device policies.
- Advanced Threat Detection: Incorporates malware and intrusion detection capabilities.
Why do we recommend it?
CrowdStrike Falcon Zero Trust is implemented through a module called Falcon Identity Protection. This is based on Active Directory, which can be on-premises or Azure AD. The tool will manage access to endpoints running Windows, macOS, and Linux and it is built into the Falcon Elite package, which includes an XDR.
This service relies upon a behavior analysis system that is able to spot fraudulent access attempts and then continues to track all user actions in the system. That constant action tracking provides a backup protection service that will suspend a user account as soon as it attempts to perform actions that are outside of that user or user type’s normal pattern of activities.
Who is it recommended for?
The CrowdStrike solution isn’t as comprehensive as the other ZTA solutions on this package. Essentially, this integrates your AD system into the Falcon XDR service. The package is more about threat detection than network or application access controls. Although this solution is based in the cloud, it supervises on-premises services.
Pros:
- Device Security Assessment: Evaluates devices for security threats before allowing network access.
- Comprehensive Activity Monitoring: Tracks user activities to identify insider threats and anomalies.
- Seamless Integration: Utilizes Active Directory for straightforward deployment in existing environments.
Cons:
- Dependence on Active Directory: Requires the use of Active Directory, limiting flexibility for some organizations.
Hackers have many tricks up their sleeves to dupe or break access management systems. CrowdStrike Falcon Zero Trust blocks those techniques and logs all of its suspicions and actions. This is a cloud-based system, so you don’t have to install the software on your site in order to implement the service. Access a 15-day free trial.
7. Ivanti Neurons for Zero Trust Access
Ivanti Neurons for Zero Trust Access is a rebrand of MobileIron Zero Trust Platform that was acquired by Ivanti in 2020. This system is particularly good at managing secure access for mobile devices. The service provides device risk assessment, which scans each device for security weaknesses and viruses before letting it connect.
Key Features:
- Enhanced Remote Access: Facilitates secure access for remote workers and mobile devices.
- Strategic Microsegmentation: Implements micro-segmentation for granular access control.
- Robust Network Access Control: Provides thorough management of device access to the network.
Why do we recommend it?
Ivanti Neurons for Zero Trust Access is part of an ever-growing platform of system protection services. The system works in a similar way to the VPN-based services of NordLayer and Perimeter 81 and it is particularly good at including mobile devices into the secure corporate network.
As the network includes the internet, enrolled devices can be anywhere in the world. Secure links connect individual remote devices and site-to-site encrypted tunnels across the internet transport communications from multiple endpoints on one site to cloud-based applications. Traffic between sites is also hubbed through the Ivanti Neurons cloud-based connection security hub.
The Ivanti Neurons system operates like a VPN network. The service has access controls, which, combined with a single sign-on environment, provide granular access rights, authorizing each user for specific applications. This, effectively, provides micro-segmentation, which is a key concept of ZTA.
Who is it recommended for?
Companies that have a lot of roaming devices would benefit from this tool. If you have IoT devices that can have software loaded onto them, they could also be protected by this system. Combine this tool with the Ivanti Zero Sign-On system to ease system access for authorized users and devices.
Pros:
- Global Device Inclusion: Offers secure connectivity for devices anywhere in the world.
- Mobile Device Security: Specializes in securing mobile devices for corporate network access.
- Unified Network Management: Integrates multiple sites into a single, centrally managed network environment.
Cons:
- Lack of Transparent Pricing: Does not publicly disclose pricing information, requiring potential customers to inquire directly.
The Ivanti Neurons system is a SaaS platform, so your initial access to the management console requires no downloads. However, there will be site access control software that needs to be downloaded. Each individual device also needs a client app downloaded onto it. You can get a 30-day free trial to examine Ivanti Neurons for Zero Trust Access.
8. Illumio Zero Trust Platform
Illumio delivers zero trust micro-segmentation from endpoints to data centers to the cloud to halt cyber-attacks and the spread of ransomware. You can also use Illumio’s zero trust platform to protect against lateral movements across devices, applications, workloads, servers, and other infrastructure.
Key Features:
- Cloud Application Controls: Manages access to cloud-based applications securely.
- Authentication Measures: Enforces robust user authentication protocols.
- Enhanced Network Security: Strengthens network connections to prevent unauthorized access.
Why do we recommend it?
The Illumio Zero Trust Platform focuses on securing hybrid environments. It operates microsegmentation for resources on your network and for access to and between cloud services. This is a classic combination of connection security with VPNs and built-in access rights management. The tool provides three modules for site-to-site, cloud, and endpoint security.
Illumio is ranked as a Leader in the Forrester Wave Zero Trust eXtended (ZTX) Ecosystem Platform Providers, Q3 2020 report. Illumio received high scores in most of the evaluation criteria, including ‘Future State of Zero Trust infrastructure’, which assessed vendors on their ability to enable zero trust for remote workforces and distributed environments. Illumio zero trust solution is offered via the following platforms:
Illumio Core (formerly known as Illumio ASP) delivers visibility and segmentation for workloads and containers in data centers and containers in data centers, unifying the control of multiple sites with inter-site connection protection.
Illumio CloudSecure provides security services between cloud platforms, for example, enabling secure access to data on one platform through applications that are hosted on another.
Illumio Endpoint controls access to and from endpoints on a network and allows remote devices to securely connect into the office system.
With capabilities that span micro-segmentation, network visibility, encryption, and vulnerability management, Illumio’s zero trust platform provides opportunities for organizations to embrace and implement zero trust strategies.
Who is it recommended for?
The modular structure of the Illumio solution means that the tool is very scaleable. For example, businesses that run a traditional network with software and services on site would only need the Innumio Endpoint service to allow remote users to connect. Add Illumio Core to secure a WAN.
Pros:
- Hybrid Environment Security: Excellently secures both on-premises and cloud environments through micro-segmentation.
- Comprehensive Protection: Focuses on preventing ransomware spread and unauthorized lateral movements.
- Endpoint Vulnerability Assessment: Scans and evaluates endpoints for vulnerabilities before network admission.
Cons:
- Segmented Solutions: Distributes its zero trust functions across multiple packages, requiring integration.
Pricing details can be obtained by directly contacting the vendor. However, the vendor provides a means to obtain a total cost of ownership (TCO) estimate for Illumio Core to help you build a business case for the elimination of unnecessary hardware in your data center. Find out more.
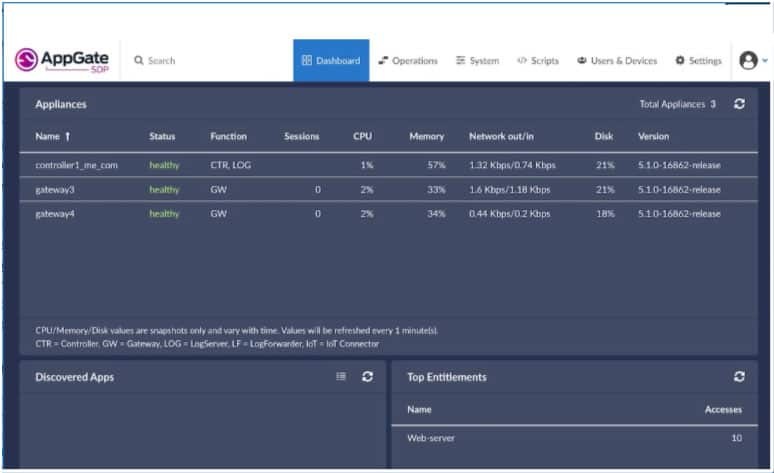
9. Appgate SDP
Appgate SDP solution is offered as a software-defined perimeter, VPN alternative, secure third party, and DevOps access based on zero trust principles and built to support hybrid IT and a distributed workforce. It is infrastructure agnostic and can be deployed in all environments: on-premises, multi-cloud (AWS, Azure, GPC), virtualized containerized environments, and legacy networks and infrastructure. Appgate was named a leader in the Forrester Zero Trust Wave 2020 report. The entire Appgate SDP solution is designed to be distributed and to offer high availability, and it can be deployed in physical, cloud, or virtual environments. The Appgate platform integrates seamlessly with third-party applications such as IdPs, LDAP, MFA, and SIEM, among others.
Key Features:
- Centralized Access Hub: Serves as a unified point for application access management.
- User-Centric Permissions: Allows for user-specific application approval.
- Flexible Virtual Network: Creates secure, virtualized network environments for diverse IT infrastructures.
Why do we recommend it?
Appgate SDP provides the classic ZTA system of combining access rights management and VPN-based connection security and it also implants ZTNA to give IoT devices and BYOD office visitors access to the corporate system. The service blocks resource access by default and then authorizes devices as well as users for access.
With Appgate SDP solution, access can be controlled from any location and to any enterprise resource with centralized policy management for servers, desktops, mobile devices, and cloud infrastructure among others. The Appgate SDP platform consists of three main components:
- Controller The controller manages user authentication and applies access policies assigned to users based on user attributes, roles, and context. It then issues entitlement tokens listing the resources the user is permitted to access.
- Client The Appgate client is software that runs on user devices and connects with Appgate appliances to receive site-based entitlement tokens after successful authentication.
- Gateway The gateway evaluates user entitlements and opens connections to resources accordingly.
Who is it recommended for?
Appgate forms a central security management center that acts as an authentication server. Access to everything from anywhere is blocked by default and then devices and users can be added to allow them in. This provides ZTNA for headless IoT devices and pre-scanned user-owned devices and also ZTA-level user access management.
Pros:
- Versatile Authentication Integration: Offers seamless connectivity with external identity providers and multi-factor authentication systems.
- Dynamic Policy Management: Enables centralized control over access rights, adapting to user roles and context.
- Pre-Connection Security Assessment: Evaluates devices for security risks before granting network access.
Cons:
- Limited Trial Availability: Does not offer a free trial for preliminary evaluation and testing.
The Appgate SDP (part of its ZTNA solution) is available for a test drive, and the virtual appliances and client software are also available for download.
10. Cisco Secure Workload
Cisco Secure Workload is a new product that Cisco has evolved from the Cisco Tetration product. This tool is implemented as a hardware appliance on-premises or as a SaaS package. Both deployment options provide application access controls whether those systems are resident on your own servers or on cloud platforms.
Key Features:
- Application-Level Security: Employs application fencing to safeguard applications.
- Flexible Deployment: Available as both a hardware appliance and a SaaS solution.
- Comprehensive Protection: Secures resources across both cloud and on-premises environments.
Why do we recommend it?
Cisco Secure Workload is an interesting combination of ZTA, allowlisting, vulnerability scanning, and anomaly-based threat detection. The system is difficult to conceptualize because it has a lot going on under the hood. However, it hardens applications against attack, fences them, and assesses each user account before permitting access.
Cisco describes its strategy as like creating firewalls at the application level. This is a microsegmentation approach but it doesn’t just check on user authorization before allowing access to an application, it also scans for anomalous activity. So, this provides threat detection as well.
The background mechanisms of the allowlisting system in Cisco Secure Workload are complicated but the basics of it work by scanning for activity that would indicate an insider threat or an account takeover, which can block otherwise authorized access. At the same time, the system provides vulnerability scanning for the protected applications to ensure that there is no easy way in.
Who is it recommended for?
Cisco says that its hardware units are affordable. However, a physical alliance always creates upfront costs that put small businesses off. However, the SaaS option is a lot easier to digest. The system is easy to set up and it can cover applications on cloud platforms just as easily as on-premises systems.
Pros:
- Integrated Threat Detection: Merges application fencing with advanced threat detection capabilities.
- Simplified Setup: Facilitates easy implementation for server-hosted and cloud-based applications.
- Continuous Security Monitoring: Offers real-time security monitoring and detailed reporting.
Cons:
- Complex Concept: The multifaceted approach may be challenging to grasp initially.
This Cisco system takes care of a lot of security issues in one bundle, so it saves both costs and time once it is running. The company provides live demo seminars to help you assess the Secure Workload package.
11. Absolute ZTNA
Absolute ZTNA is part of a package of security services that is called Absolute Edge. The unit combines with units for network security and remote access. The total package provides application security and connection security that treats user access controls equally whether they use a workstation on the network, a computer at home, or a mobile device.
Key Features:
- Device Security Assessment: Conducts thorough scanning of devices for security risks.
- User Portal Application: Provides a dedicated app for user access management.
- Robust Connection Security: Ensures secure connectivity for all user sessions.
Why do we recommend it?
Absolute ZTNA and the Absolute Edge is a similar package to the Invanti Nerons for Zero Trust Access package. In addition to providing a VPN with built-in access rights management. The tool provides device risk assessment, which scans each computer, phone, or tablet before turning on the secure connection into the access rights manager.
Each user device needs an app installed on it. The administrator sets up a list of corporate applications, which can include cloud services and SaaS packages as well as on-premises services. Next, the administrator creates a list of users and then allocates applications to each account.
The endpoint agent is available for Windows, macOS, iOS, and Android. It scans the device for risk before allowing access and the user also has to log in with valid credentials. The app then provides access to a menu of only those applications and services that have been allocated to that user account.
Who is it recommended for?
This tool is particularly good for companies that have a lot of users that need to access corporate resources through mobile devices. The device doesn’t need to be corporate property because the user just needs to install a mobile app to get access to company systems.
Pros:
- Mobile Device Management: Effectively manages and secures mobile device access to corporate resources.
- Selective Application Access: Tailors application visibility based on user authorization.
- Support for Remote Workers: Facilitates secure remote access for users outside the corporate network.
Cons:
- Limited Data Control on Personal Devices: May not offer full data management capabilities on user-owned devices.
- Lack of Linux Support: No endpoint application available for Linux devices, limiting its applicability for certain users.
The tool can track the movement of data and delete data from remote devices. However, it doesn’t offer full Mobile Content Management (MCM) because it doesn’t containerize the delivery of data to user-owned devices.
The Absolute ZTNA system and the Absolute Edge package need to be studied to be fully understood. You can start your investigation by accessing a demo.
Choosing the right ZTNA solution for your business
While ZTNA has many use cases, most organizations choose to use it as a means of access to hybrid and multi-cloud services, an alternative to VPN, and a means to eliminate over-privileged access to resources, among others.
Like most network security solutions, not all zero-trust solutions are created equal. What fits perfectly from a price, feature, and functionality standpoint for one organization may not fit for another. You need to consider a variety of factors, some of which include: What deployment model best suits your environment—cloud or on-premises? Does the deployment model meet your organization’s security and residency requirements? Does the ZTNA solution require an endpoint agent to be installed? Does the trust broker integrate with your existing identity provider? Is vendor support available in your region, and to what extent? How geographically diverse are the vendor’s edge locations worldwide? What is the total cost of ownership?
These solutions can be deployed as on-premises or standalone service, cloud service, or as a hybrid service, combining cloud and stand-alone offerings. If you find any of these solutions useful, or indeed other solutions, let us know in the comments.
Zero Trust network in software FAQs
How does a zero trust network work?
A key element of Zero Trust is that each device is scanned for security weaknesses every time it tries to connect to the network. If a device doesn’t meet the corporate security standards, it isn’t allowed to connect. This check applies equally to corporate equipment and user-owned devices. Users are also authenticated at the time of access – as with most other facility access management systems – and single sign-on is used extensively to remove the need for users to have to log on to each individual application.
What is the concept of zero trust?
Zero Trust applies security checks on access to each resource. Although this seems to require users to log on again for every action, authentication is automated behind the scenes by a single sign-on environment to prevent security checks from becoming cumbersome.
What are the benefits of Zero Trust?
Zero Trust is an appropriate security strategy in the increasingly adopted hybrid environment. When a business’s users access services on the local network, remote sites, and cloud-based apps, siloed security measures per location and platform become unmanageable. Confusing matters further, work-from-home and roaming workers need the same level of access to corporate resources as office-based employees. Thus, Zero Trust deals with security per application and authorizes each user access to a list of services, regardless of the device that the user access through or the location of the application. Devices are checked for security resilience at every access point.