Software company, DATAIR Employee Benefit Systems, Inc., has started notifying people of a data breach following a ransomware attack way back in December 2022. LockBit claimed the attack and published its negotiation chats with the company. After communications broke down, LockBit demanded $250,000 and placed the organization on its data leak site.
According to the data breach letter, DATAIR discovered the ransomware attack in December 2022. It hired global cybersecurity professionals to help contain the attack and received forensic evidence on March 26, 2024. Based on the investigation (which also involved the FBI), it was found that “an unauthorized party had possibly gained access to personal identifiable information about certain DATAIR client members.”
The letter doesn’t explain why the investigation took so long and why people weren’t alerted to this potential data breach after LockBit’s posting on the dark web. The letter doesn’t seem to confirm exactly what ‘personal identifiable information’ was involved, either.
Comparitech has contacted DATAIR for more information and to ask whether the below chat logs posted by LockBit are genuine. We will update this article if we receive a response.
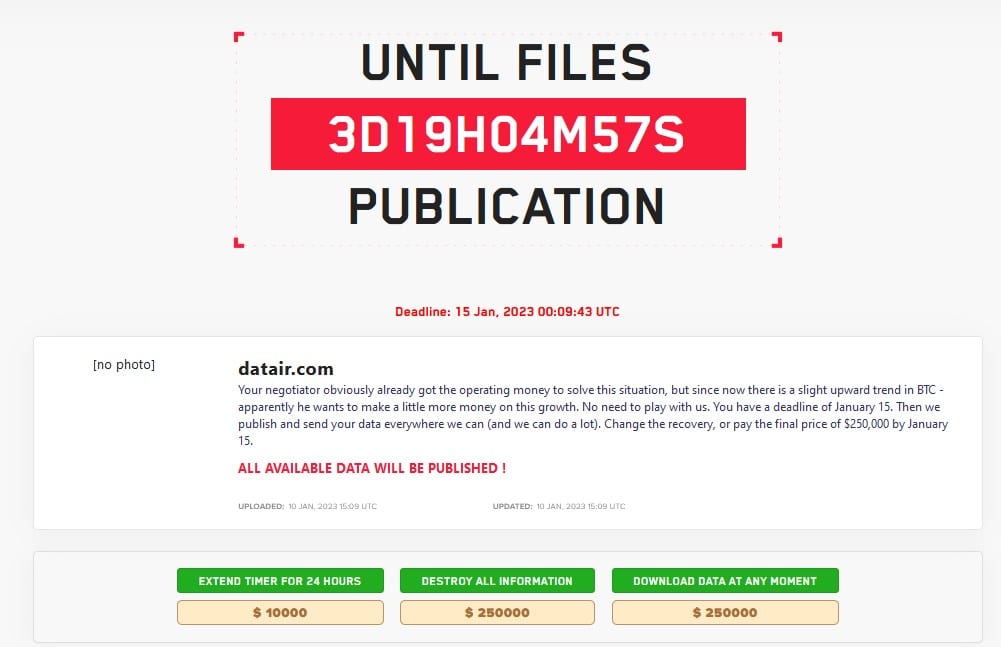
LockBit chat negotiations with DATAIR
In the chat negotiations posted by LockBit and shared via DarkFeed.io, DATAIR first appeared to contact its attackers on December 24, 2022. LockBit suggests it has blocked all of its servers and has stolen 178 GB of data. At this time, the hackers demand $150,000 and provide proof of stolen files. DATAIR says it will work on it.

On December 26, LockBit warns DATAIR it has just one day left. DATAIR replies on December 29 to say it is working to meet their demands and is trying to set up the transfer of funds. On December 30, LockBit says it believes DATAIR is insured against such incidents and demands $10,000 to answer DATAIR’s question as to how they got into its systems.

On January 3, LockBit says if it hasn’t received the money in two days, the ransom will increase by $50,000. DATAIR also asks if one of LockBit’s team has called its offices, to which LockBit says it did it to “show their capabilities.”
After this, it appears negotiation chats shut down as LockBit ups its price to $250,000 on January 7 and says it’ll publish data on January 15. On January 10, it published DATAIR to its data leak site.
In the data breach notification, DATAIR confirms it didn’t pay a ransom. In our contact with DATAIR, we have asked whether there was any intention to pay the ransom as per the alleged negotiation chats or whether this was just a delaying tactic.
Who is LockBit?
LockBit is one of the most prolific ransomware gangs of recent years after first appearing in 2019. It is believed the group is based in Russia, and, as demonstrated above, LockBit often extorts victims twice. One demand is to decrypt systems, the other is to delete any stolen data.
According to our data, LockBit is responsible for 368 confirmed ransomware attacks across the globe. These attacks have affected at least 12.05 million records.
So far this year, LockBit is behind 21 confirmed attacks with a further 207 unconfirmed claims.
About DATAIR Employee Benefit Systems, Inc.
Since 1967, DATAIR has been providing software and services for employee benefit professionals. It is headquartered in Westmont, Illinois.
