Exploit kits (or exploit packs) are automated programs used by attackers to exploit known vulnerabilities in systems or applications. They can be used to secretly launch attacks while victims are browsing the web, with the goal being to download and execute some type of malware.
Because exploit kits work in the background, it can be difficult to know when you’re under attack. However, there are measures that can help you protect against these attacks, such as avoiding unknown links and keeping software up to date.
In this article, we explain more about what exploit kits are, how they work, and how cybercriminals use them. We’ll also provide tips for preventing attacks and the resulting malware payload.
What an exploit kit is
An exploit kit is a package used by cybercriminals to deliver malware. We’ll go into the details of how an attack is executed below, but the gist is that a victim visits a compromised website, and if they have certain vulnerabilities within the software on their computer, the exploit can be carried out. As a result, malware is downloaded and executed on the victim’s device.
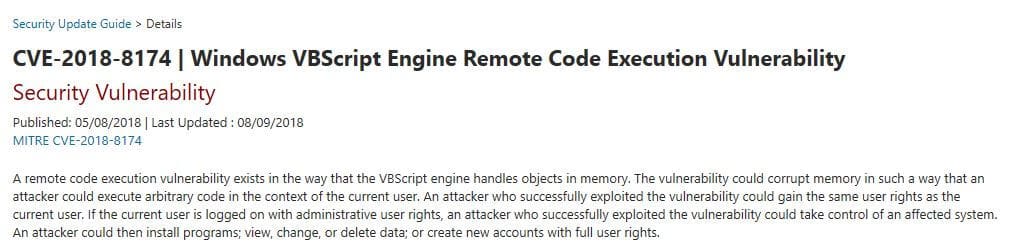
A software vulnerability is an error or bug in the code that enables an attacker to intrude on the application in some way, for example, in the case of exploits, by running an unauthorized task. Known vulnerabilities are named in a reference list of Common Vulnerabilities and Exposures (CVE). For example, CVE-2018-8174 is a highly-exploited Internet Explorer vulnerability.
Common targets for exploits are popular software with many known vulnerabilities, such as Adobe Flash, Oracle Java, and Internet Explorer. The more popular the application is, the higher chance an attacker has of attracting a suitable victim.
This is also where exploit kits come in especially handy for their users. Exploit kits target multiple vulnerabilities at the same time and comprise everything the criminal needs to carry out the attack. If one exploit isn’t suitable, another might be, increasing the cybercriminal’s chance of executing a successful attack.
The fact that these things come as pre-built kits also makes them easy to implement and more attractive for criminals with little technical knowledge.
How an exploit kit is implemented
There are several stages necessary for an exploit to be successful:
- Establish contact with the host environment through a landing page.
- Redirect to an alternative landing page and detect vulnerabilities in the host that can be exploited.
- Carry out the exploit to spread malware.
- Infect the host environment by executing the malware.
The exploit kit contains all of the code necessary to carry out each stage. If one stage is unsuccessful, that signals the end of the attack on that particular device. Here, we’ll look at these stages in more detail and examine what criteria needs to be met at each.
1. Establish contact
The first stage of the exploit uses a landing page of a website that has been compromised. Victims are encouraged to visit this site, for example, through an email link, a popup, or a malvertisement (malicious advertisement).
Once the victim clicks the link to the site or enters the URL in their browser, the initial contact has been established.
At this point, there may be some users who don’t meet certain criteria, such as those in the wrong location (often determined based on IP address or install language checks). These users are filtered out and for them, the attack is over.
2. Redirect
Remaining victims are redirected to an alternative landing page which is no longer the real website. Code embedded into this landing page then proceeds to determine if the victim’s device has any vulnerable browser-based applications that correspond to the exploits in the kit.
If no vulnerabilities are detected (that is, everything is up to date and all holes are patched), then the attack stops. But if a vulnerability is found, then the website will send traffic to the exploit.
3. Exploit
The reason for requiring a vulnerability is that the exploit kit needs to run malware on the host environment (the victim’s device). The application that was found to be vulnerable is used to download the malware.
The way the expolit is carried out depends on the application. For example, if web browsers themselves are the target, the exploit will be in the form of code embedded within the web page. Another example is commonly-targeted application Microsoft Silverlight, for which the exploit is a file.
The term ‘exploit kit’ means that there are multiple exploits bundled into one package. It will target multiple vulnerabilities, making for easier execution and an increased chance of success for the criminal.
4. Infect
After successful exploitation, malware is executed in the victim’s environment. As far as what the effect of the malware is, there are many different scenarios. Exploits kits can be used to spread various types of malware, including ransomware and Trojans like remote access trojans.
A popular use for exploit kits is to execute cryptocurrency mining software. This hijacks the victim’s computer resources for use in mining bitcoin and other cryptocurrencies, without the user’s permission.
Examples of exploit kits
Due to security patches by software developers, each exploit will have a limited lifespan. However, kit developers come up with updates of their own so that new versions of a given kit will exploit new vulnerabilities. As such, some kits have been around for a while.
Adobe Flash exploit kits were extremely popular in the past, with the phaseout of the software reportedly causing a steep decline in exploit kit development. More recent studies see a shift to Microsoft product exploits. That being said, a kit can target more than one application at a time. It can also be used to spread more than one type of malware.
Here are a few exploit kit examples:
RIG
Among the most popular exploit kits in 2018, RIG uses a variety of distribution methods and resulting payloads. It has been used to spread coin miners, banking Trojans, ransomware, and more.
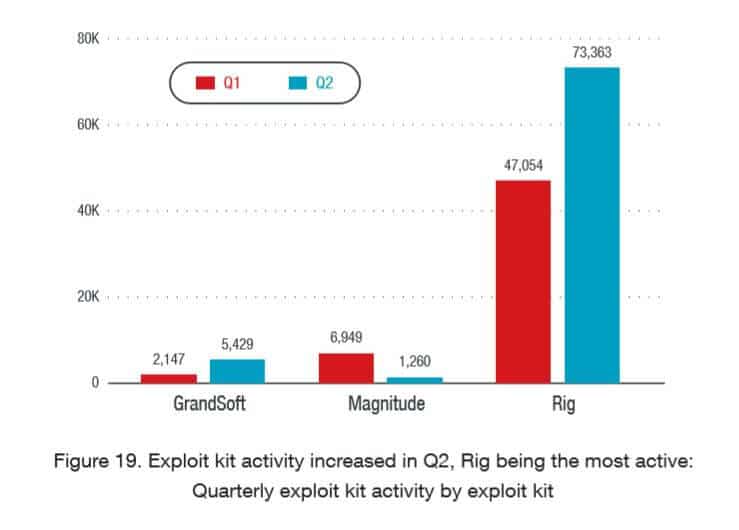
GrandSoft
While this is recognized as an older kit, it resurfaced in 2018. GrandSoft has been known to distribute ransomware (specifically GrandCrab), Trojans (AZORult and QuantLoader in particular), and miners.
Magnitude
Magnitude targets select Asian countries and delivers a specific payload. It has been around for a long time, but has changed its form. It used to include exploits for Flash Player but has been adapted to solely attack Internet Explorer vulnerabilities. The Magnitude EK version targets South Korea (by checking IP address and language, among other things) and delivers a special ransomware called Magniber.
Nuclear
While it hasn’t been in the news for a while, the Nuclear exploit kit was once a big money-maker for its creators. A report by security firm Checkpoint found that the kit was developed by someone in Russia, and the team behind it was making around $100,000 per month from the kit at the time.
Nuclear was more of an “exploit-as-a-service” where criminals would rent the kit. They would use a control panel in which they could upload malware and track their results.
Why are exploit kits successful?
Considering the attackers are using known vulnerabilities, you may wonder how these weaknesses remain exposed, allowing attacks to be successful.
A 2018 Trend Micro report [PDF] sheds some light on one of the major reasons:
“The continuous onslaught of newly discovered vulnerabilities only makes it that much harder for enterprises to catch up. Oftentimes, due to the volume of vulnerabilities and the competing priority of keeping the network available, they need to make practical tradeoffs by assigning importance to certain vulnerabilities and leaving open patches to other vulnerabilities to a later time.”
Essentially, there is simply too much to fix all in one go. Even if vulnerabilities have been patched and companies like Microsoft and Adobe have issued updates, companies can’t always update their systems immediately.
They have to prioritize which updates need to happen first and hope that they make the right decisions, as cybercriminals wait to take advantage of every weakness. Similarly, for individuals, if someone puts off an update or misses it for some reason, then there’s a much bigger chance of an exploit kit being successful.
A couple of other factors lend to the success of exploit kits, one being that initial contact is easily made, for example, by someone clicking on a rogue advertisement or a link in an email. And secondly, once initial contact has been established, it’s difficult to tell that anything untoward is going on.
How to protect against exploit kits
Because it’s so difficult to know when exploit kits are working and the fact that they’re so varied, it’s best to avoid them in the first place. Here are some tips to help:
- Keep software up to date. One of the most important reasons software is updated regularly is to patch security vulnerabilities.
- Don’t click spammy links. As always, you should avoid opening emails from anyone you don’t know and definitely don’t click on suspicious links.
- Avoid ads and popups. When it comes to popups and ads, it can be difficult to avoid clicking, as many of these are designed to trick you into doing so (for example, the “close” button is difficult to locate or the ad moves around). An adblocker can be helpful, as this will prevent ads and popups from appearing in the first place.
- Use an antivirus. An antivirus isn’t foolproof by any means, but it can detect and remove many known threats, including viruses and other types of malware that find their way on to your device.
Image credit: “Crack Wall” by Michael Krause licensed under CC BY 2.0