More than 300 million records containing the personal information of VPN users was exposed on the web without a password, Comparitech researchers report. 45 million of the records included user account info such as email addresses, full names, and encrypted passwords.
Based on our findings, ActMobile Networks Inc appears to be the owner of the data. The company operates Dash VPN, FreeVPN.org, and Dash Net Accelerated VPN, among others. However, ActMobile denied ownership of the data, saying it “does not maintain databases” in an email response to Comparitech.
Comparitech’s head of cybersecurity research, Bob Diachenko, discovered the exposed database on October 8, 2021 and immediately reported it to ActMobile in accordance with our responsible disclosure policy. The database was shut down a week later on October 15.
The data has since been leaked on hacker forums, increasing users’ risk of attack.
Comparitech has taken additional steps to verify the data’s legitimacy and has confirmed that at least one user from the database did have an account with Dash VPN.
Timeline of the exposure
Here’s what we know happened:
- October 6, 2021 – The database was indexed by search engines.
- October 8, 2021 – Diachenko discovered the exposed data and immediately alerted ActMobile per our responsible disclosure policy. The company did not respond to any of our attempts at contact to ActMobile support, team members, domain registrants, and server administrators. After multiple failed attempts to contact the company privately, Diachenko sent an alert on Twitter.
- October 15, 2021 – The database was closed.
- November 1, 2021 – The data was leaked on hacker forums.
The data was exposed for at least a week in total and has since been uploaded to hacker forums. Our honeypot experiments show attackers can find and steal unprotected data in a matter of hours, so users can assume the worst.
What data was exposed?
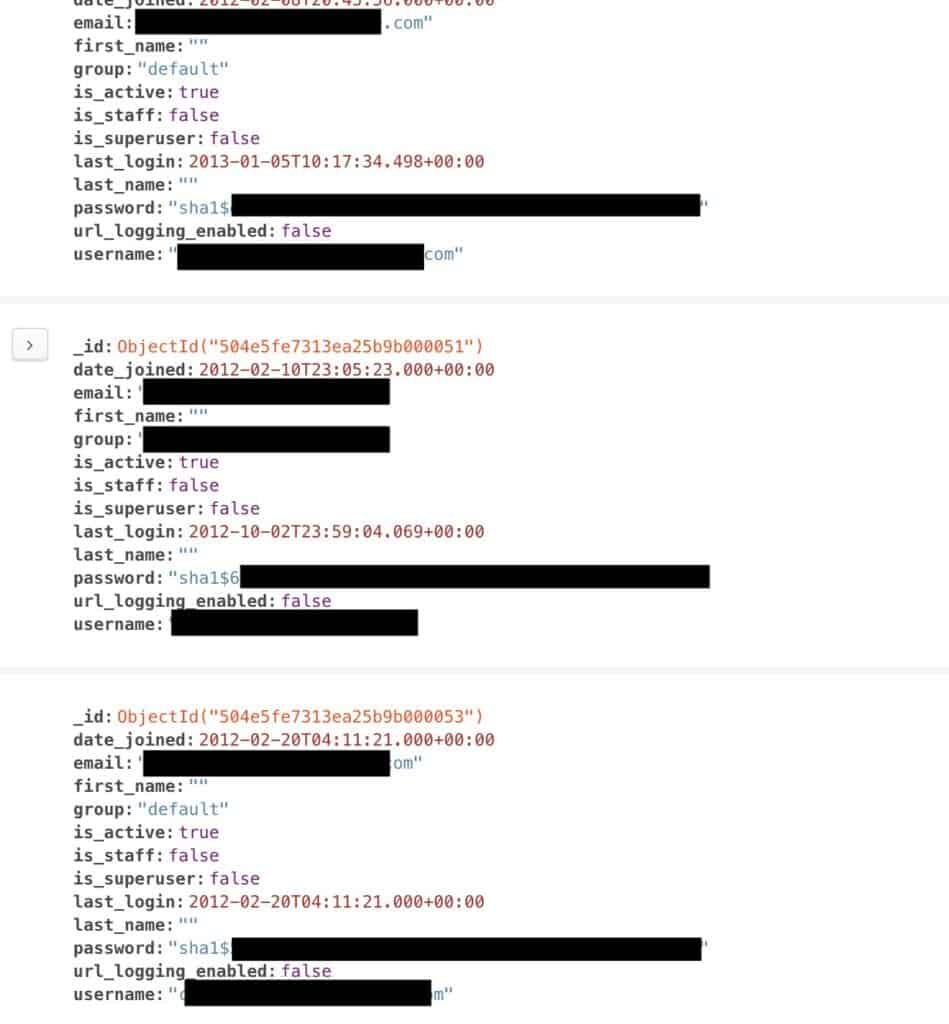
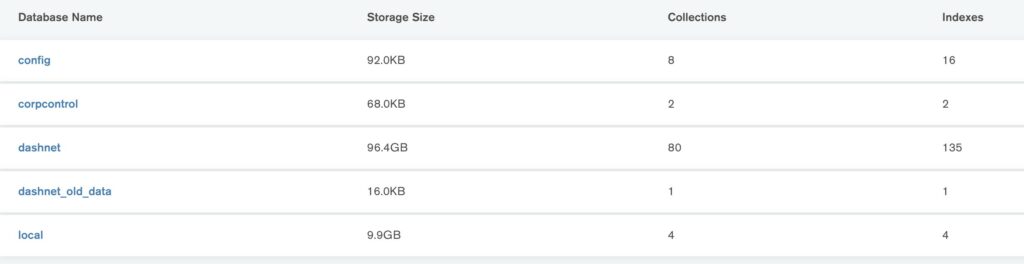
The MongoDB database was found at a France-based IP address and contained more than 100GB of data. That data can be divided up into three categories:
- 45 million user records, including…
- Email address
- Encrypted password
- Full name
- Username
- Last login date
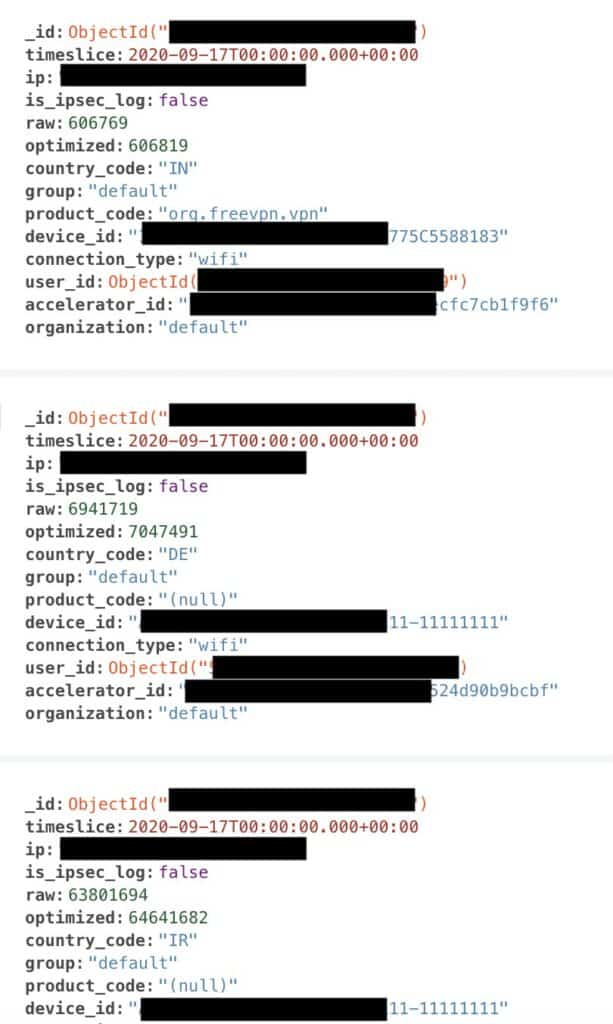
- 281 million user device info records, including…
- IP address
- Country code
- Connection type (wi-fi or mobile)
- Device and user ID
- Accelerator ID
- 6 million purchase records, including…
- Product purchased
- Receipt
Additionally, more than 4 million “APN tokens” were exposed. We’re not quite sure what these are, but they could be used for the Apple Push Notification service, or they could be related to Access Point Names used to connect mobile devices to the internet over a cellular network.
No credit cards or other payment information were included.
Dangers of exposed data
Although the passwords were hashed and thus shouldn’t be accessible, we advise anyone concerned users to immediately change their passwords. Any other accounts that share the same password should be changed as well to avoid credential stuffing. Enable two-factor authentication when possible.
Regardless of who is really responsible for the data, users should be on the lookout for targeted phishing messages purportedly from ActMobile, its brands, or related companies. Scammers might pose as one of these organizations to trick users into clicking a malicious link or download. Never click on unsolicited links or attachments.
Finally, we recommend VPN users who value their privacy choose a no-logs VPN. In particular, IP addresses collected by VPNs could be used to corroborate online activity and trace it back to an individual user. Comparitech recommends true zero-logs VPNs that don’t collect your IP address or device identifiers, among other data.
Whose data is this?
ActMobile Networks’ sole reply to Comparitech’s multiple attempts at disclosure flat out denied ownership of the data, saying, “We do not maintain databases, so whatever is referenced is false. Furthermore, if you write about us we will take action.”
But if the data doesn’t belong to ActMobile, who does it belong to? Our findings don’t support ActMobile’s claim:
- The SSL certificate of the exposed server belonged to the actmobile.com domain.
- At least one user whose email was exposed confirmed they had an account with Dash VPN
- The exposed database repository containing most of the user information was labeled “Dashnet”. There are several references in the database to ActMobile’s VPN brands, such as in package names.
- The WHOIS record for the IP address where the data was hosted lists ActMobile Networks as the owner
If ActMobile is being honest about not owning the data, then someone must have tried very hard to make it seem as though ActMobile is responsible.
US-based ActMobile Networks operates or white labels its VPN service to at least four VPN brands: FreeVPN.org, Dash VPN, Dash Net Accelerated VPN, and VPN Pro. Although the connection between these brands isn’t immediately clear, clues in the database, their websites, and their app store pages hint at their relationship:
- Dash VPN and Dashnet Accelerated VPN both share the same support email address.
- DashVPN, Dashnet Accelerated VPN, and FreeVPN.org all list the same street address in Pleasanton, California as their headquarters.
- The Amazon app store page for Dash VPN lists the FreeVPN.org email address, privacy policy, and website under its developer information.
- Dashnet Accelerated VPN’s website, listed on the Google Play store, leads to Dash VPN’s website.
Both FreeVPN.org and Dash Net Accelerated VPN have privacy policies that guarantee they do not collect any of the user’s personal data when using the VPN. But as we can see above, they clearly collect users’ IP addresses and device identifiers, so that claim wouldn’t hold up in a Comparitech VPN review. Dash VPN does not have a privacy policy on its site, but its Amazon App store page points to the FreeVPN.org privacy policy.
At time of writing, FreeVPN.org has a 4.3-star average rating and more than 1 million installs on Google Play. On the Apple Store, it is ranked #31 in the Utilities category with a 4.4-star rating.
Dash VPN, also called Dash Office and VPN Dash (the branding is not consistent), has more than 500,000 installs and a 4.4 star review on Google Play. It has a 4.6-star rating on the Apple store.
Dash Net Accelerated VPN has more than 50,000 installs on Google Play and a 3.7-star rating. It does not appear to be on the Apple App Store.
Why we reported this incident
Comparitech’s cybersecurity research team routinely scans the internet for unsecured databases holding personally identifiable information. When we discover one, we promptly begin an investigation to find out to whom it belongs, what information is stored, who might be affected, and potential harm to end users.
After identifying and verifying the party responsible for the data, we send an alert in accordance with our responsible disclosure policy. Once the data is secured, we publish an article like this one to raise awareness about the incident and curb harm to data subjects.
This is not the first time Comparitech has uncovered an exposed database of VPN users. In July 2020, UFO VPN exposed millions of log files about users of its service, including their account passwords and IP addresses, despite claiming that it keeps no logs.
Previous data incident reports
Comparitech has published several data incident report similar to this one, including:
- Personal info of 106 million international visitors to Thailand exposed online
- 35 million US residents’ personal details exposed on the web
- India visa agency exposes 6,500 traveler’s visa applications on the web
- Prison phone service Telmate exposes messages, personal info of millions of inmates
- Social media data broker exposes nearly 235 million scraped profiles
- 42 million Iranian “Telegram” phone numbers and user IDs were breached
- Details of nearly 8 million UK online purchases leaked
- 250 million Microsoft customer support records were exposed online
- More than 260 million Facebook credentials were posted to a hacker forum
- Almost 3 billion email address leaked, many with corresponding passwords
- Detailed information on 188 million people was held in an unsecured database