Telmate, a service used by incarcerated inmates at US prisons to communicate with their friends and loved ones, has exposed a database containing tens of millions of call logs, private messages, and personal information about inmates and their contacts. The database was exposed on the web without a password or any other authentication required to access it.
Comparitech security researcher Bob Diachenko on August 13, 2020 discovered the unsecured database and immediately reported it to Global Tel Link, the company that owns and operates Telmate. The company, to its credit, responded within two hours and secured the database an hour later, but it’s possible that other unauthorized parties accessed it prior to Diachenko’s disclosure.
Telmate makes GettingOut, a service and app for iOS and Android that facilitates monitored inmate communications via voice and video calls, text and photo messages, and voicemail.
Based on samples of the data, we estimate the exposure impacts prisoners in facilities located everywhere that GTL operates. GTL is the largest provider of prison telephone services, commanding about half of the US market according to the Prison Policy Initiative.
In the wrong hands, the information stored in the database could put prisoners and the people they contact at serious risk.
GTL acknowledged the incident and took action promptly. It gave the following statement via email:
Telmate, a GTL subsidiary immediately locked down the server as a precaution upon being made aware of a vulnerability in the data system due to the actions of one of our vendors. This vulnerability was swiftly corrected, the data security team was immediately supplemented with the assistance of third-party consultants and we continue to work closely with law enforcement authorities as we conduct further inquiry into this incident. Based on the current facts of the investigation, no medical data, passwords, or consumer payment information were affected. We continue to speak with and notify necessary parties, including the affected Telmate customers – a small subset of all GTL customers – about the incident and the actions we have taken to safeguard data. The security of the data we keep is of the utmost importance to us, and we are committed to doing everything we can to keep it safe.
Timeline of the exposure
The database was indexed by search engine BinaryEdge on August 13, 2020, though it was possibly exposed for some time prior to that. Diachenko discovered the database and immediately notified GTL on the same day. About two hours later, GTL acknowledged the exposure. One hour later, the database was isolated and secured.
We do not know how long the database was exposed prior to being indexed, or whether any other unauthorized parties accessed it. Our research shows that unsecured databases can be accessed and attacked within a few hours of exposure.
What information was exposed
Many of the records appear to be collected from prison-issued tablets, which we surmise use Telmate’s GettingOut service.
The database contained three indexes:
- 227,770,157 message records
- 11,210,948 inmate records
- 78,885 administrative records containing login details for the Telmate dashboard
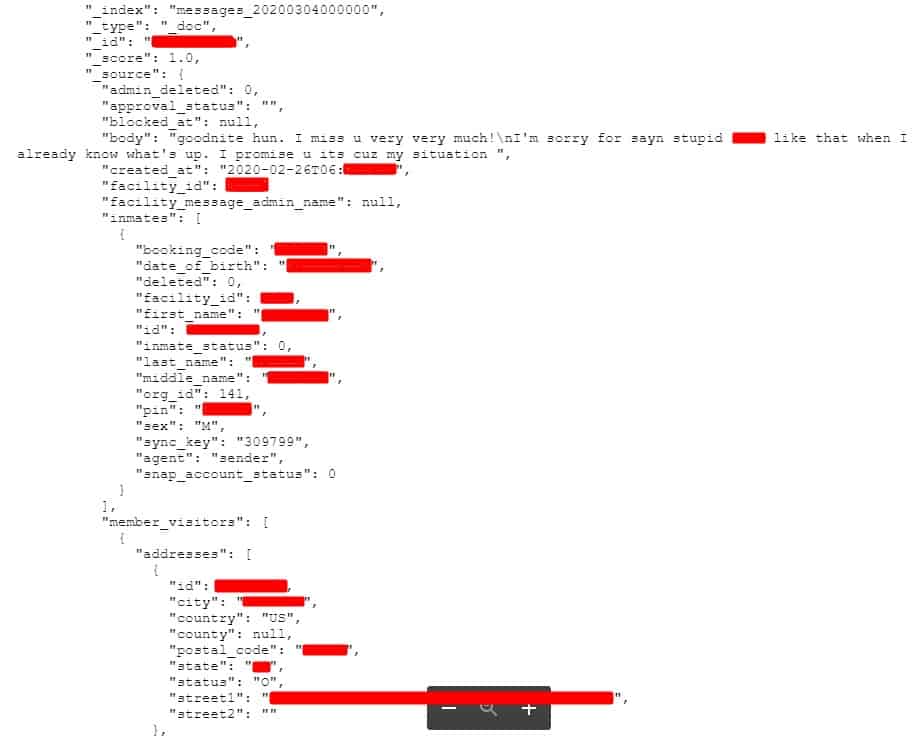
The text message records include conversations between inmates and their friends and family, as well as grievances filed by inmates requesting transfers, education programs, clothing, and legal assistance.
- Text message contents
- Timestamp
- Inmate information
- Date of birth
- Facility ID
- Full name
- Sex
- Recipient information
- Full name
- Email address
- Street address
- Status of the message (whether it was blocked by administrators)
Prisoner records contain all or some of the following information:
- Full name
- Offense
- Facility
- Account balance (used to pay GTL’s call and message fees)
Call and message recipients’ details were also recorded in the database, containing all or some of the following:
- Full name
- Email address
- Phone number
- Street address
- Driver’s license number
- IP address
Call records included call time, duration, personal info as mentioned above on both parties, and some other data, but not actual recordings.
Payment information, other than account balances, was not in the database.
No personally identifiable data was retained by Diachenko or Comparitech.
Dangers of exposed data
The exposed data could endanger inmates, their friends, and their families if it ends up in the wrong hands. A person could be at risk of retaliation for their incarcerated family member’s crime or some other transgression, for example.
Inmates’ families and friends could be subject to harassment, assault, or discrimination based on their relationship with an inmate that would otherwise be private.
Inmates and their contacts could also be at risk of targeted fraud and phishing using the emails and phone numbers contained in the database.
The login details for Telmate’s dashboard are used by personnel at prisons and jails to access call and message logs. Their exposure could give hackers the means to break into those systems and steal call recordings or other data.
About GTL and Telmate
Global Tel Link (GTL) is the USA’s largest prison telecommunications service. It has been the subject of several controversies regarding its services and treatment of inmates.
GTL owns Telmate, which makes and operates GettingOut, an internet-based app and service for inmates to make voice and video calls and send and receive text and photo messages to those on the outside.
GTL has been accused of price gouging inmates and their families with exorbitant call and message fees. Local prison systems and law enforcement agencies often get kickbacks from GTL contracts that extort a captive market, according to class action lawsuits filed in various states.
Telmate also makes Guardian, an app used to monitor parolees’ locations. The app was criticized for being too invasive, faulty, and insecure. Guardian was not implicated in the August 13 data incident.
Why we reported this incident
Comparitech security researchers routinely scan the web for unsecured databases containing personal information. Upon discovering an unsecured database, we immediately begin an investigation to identify and notify those responsible for it. We examine the data to find out who is affected, what information is exposed, and what the potential consequences might be.
Once the data has been secured, we publish a report like this one to raise awareness and mitigate possible harm to those whose private information was exposed.
Previous data incident reports
Comparitech has published several data incident reports like this one, including:
- Social media data broker exposes nearly 235 million scraped profiles
- UFO VPN exposes millions of logs including user passwords
- 42 million Iranian “Telegram” phone numbers and user IDs were breached
- Details of nearly 8 million UK online purchases leaked
- 250 million Microsoft customer support records were exposed online
- More than 260 million Facebook credentials were posted to a hacker forum
- Almost 3 billion email address leaked, many with corresponding passwords
- Detailed information on 188 million people was held in an unsecured database
- Over 2.5 million CenturyLink customer records leaked