
For another year in a row, phishing attacks remain the most prominent threat for US organizations. Over the last two years, nearly 600,000 phishing attacks have been reported–with many more expected during the remainder of this year. As many as 79 percent of US organizations experienced a successful phishing attack in 2021.
Cybercriminals adapted in 2021, finding new ways to exploit the large number of people working from home and the increasing popularity of cryptocurrency. They found new ways to steal billions of dollars from consumers and businesses with business email compromise (BEC) scams being particularly lucrative.

What happened in 2021?
- Phishing scams have increased by more than 34 percent from 2020 to 2021 with 323,972 reports made to the IC3 (compared to 241,342 in 2020). These reported scams make up 38 percent of all internet crimes reported to the IC3 in 2021
- $44,213,707 was lost to these phishing scams in 2021– a decrease of 18 percent from 2020 ($54,241,075 lost)
- The average victim loss also decreased by 40 percent from 2020, with $136 lost per victim compared to $225 in 2020 (IC3)
- Business Email Compromise (BEC)/Email Account Compromise (EAC) accounted for 19,954 complaints from organizations in 2021– an increase of 3 percent on 2020’s figures (19,369) (IC3)
- $2,395,953,296 was lost to these BEC/EAC scams in 2021– a 28 percent increase on 2020’s figure ($1.87bn) (IC3)
- The average loss to BEC/EACs increased by nearly 25 percent, with organizations losing $120,074 on average, up from $96,372 in 2020 (IC3)
- 79 percent of US organizations experienced a successful phishing attack last year, nearly 4 percent lower than the global average but a 6.5 percent year-on-year increase (Proofpoint)
- 18 percent of US organizations dealt with immediate financial loss as a result of these attacks, slightly higher than the global average of 17 percent (Proofpoint)
- 33 percent of all data breaches (537 of 1,613) against US organizations were caused by phishing/smishing/BEC attacks in 2021 (ITRC)
This report looks at the state of phishing scams from 2021, analyzing top trends, the most standout attacks of the year, and industry insights into what needs to be done to prevent these types of attacks in the future.
What trends did we see in 2021?
- The Identity Theft Resource Center suggested attackers prefer phishing (and ransomware) because they “require less effort, are largely automated, and generate payouts that are much higher than taking over the accounts of individuals.” This is reflected in the fact that the majority of data breaches logged by the ITRC (33 percent) were caused by phishing/smishing/BEC attacks.
- The IC3 paints a similar picture with its continued growth of general phishing attacks (excluding BEC/EAC scams) reported in 2021. For the second year in a row, the amount of money generated by phishing scams has decreased. This suggests that while scammers continue to increase the number of successful attacks, consumers are seemingly more clued up on their tactics, resulting in a decrease in the amount lost. This means that scammers are having to generate an even greater number of phishing attacks to get anywhere close to the amounts lost in the past.
- BEC/EAC complaints are a completely different story, though–the number of attacks has only increased slightly but the amount lost to these attacks is record-breaking. In 2021, the IC3 saw an increase in the exploitation of virtual video calls and meetings. Scammers hacked into emails to gain access to virtual meetings to learn about business operations, spoofed emails from CEOs where it was claimed they were in an online meeting so unable to transfer funds from their own computer, and went as far as joining meetings as CEOs, using still photos and fake audio to suggest the video software wasn’t working and to trick employees into conducting wire transfers.
- There was an uptick of TOAD (Telephone-oriented attack delivery) in 2021, using fraudulent emails, call centers, well-designed websites, and mobile apps. Due to even more people working from home, these attacks were capable of targeting both personal and organizational email addresses. (Proofpoint)
- 10.7 million phishing and counterfeit pages were discovered in 2021, a 53 percent increase from 2020 (6.9 million). The average number of phishing and counterfeit pages detected per day also increased from 19,000 to 29,000 in 2021. (Bolster)
- Cryptocurrency-related phishing sites increased by 1,800 percent, accounting for 20 percent of all targets in November 2021. This drastic interest from attackers was likely due to Bitcoins’ increase in value around this time, reaching an all-time high of $64,400 for one BTC on November 12th. (F5 Labs)

What was the cost?
The IC3’s Annual Crime Report states that phishing attacks cost victims $44,213,707 in 2021, down by over $10 million from $54,241,075 in 2020 (not including BEC/EAC scams which we look at separately shortly).
The average victim loss in 2021 was $136, down by over 39 percent on 2020’s figures ($225) and 73 percent less than 2019’s figures ($504). This has been a continued trend year on year and shows that while phishing attacks are growing at an exponential rate, the money made from them is falling quite dramatically.
In 2021, phishing attacks made up 38 percent of all cybercrimes reported to the IC3 but only 0.64 percent of the overall losses. In 2020, phishing attacks accounted for almost 30 percent of the reported crimes and 1 percent of victim losses. And in 2019, phishing attacks accounted for a little over 25 percent of the reported crimes but 1.7 percent of victim losses.
Once again in 2021, there have been huge increases in phishing attacks but a significant decrease in losses. What is the reason for this?
Phishing scams are known to be a “get rich quick” crime for many criminals. At the click of a button, thousands of phishing emails can be sent. However, the awareness surrounding phishing attacks is growing. As we have seen, however, the financial gains from BEC/EAC scams have grown exponentially in recent years. This is thanks, in part, to companies having an increasing reliance on video conferencing software due to more employees working from home.
In those meetings, the fraudster would insert a still picture of the CEO with no audio, or a ‘deepfake’ audio through which fraudsters, acting as business executives, would then claim their audio/video was not working properly. The fraudsters would then use the virtual meeting platforms to directly instruct employees to initiate wire transfers or use the executives’ compromised email to provide wiring instructions. – IC3
Proofpoint reports that “indiscriminate” bulk phishing attacks increased by 12 percent year over year, while other more targeted attacks such as spear phishing/whaling and BEC were up by 20 percent and 18 percent, respectively.
We can see this reflected in the figures from IC3, too. While the number of BEC/EAC scams only increased by 3 percent from 2020 to 2021 (19,369 to 19,954), the amount lost to these types of scams increased by more than 28 percent from $1.87bn to $2.4bn. Although phishing still takes prominence for the number of attacks, other types of social engineering attacks incur bigger financial losses. In 2021, this $2.4 billion in BEC/EAC losses equated to 33 percent of the total reported losses from all types of scams ($2.4bn of $6.9bn).
The elderly are often targeted by scammers in phishing attacks, the IC3 found that the over 60s tend to lose more to phishing attacks. 5,831 over 60s were victims of phishing attacks in 2021. This was down by nearly 21 percent from 2020, which saw 7,353 elderly victims affected. The amount lost to these scams more than halved from 2020 too, falling from $18.8 million lost to $9.2 million lost. But this still accounted for 24 percent of the total loss of all scams. The average loss for the elderly per phishing attack was $1,572, which is over 10 times more than the average lost to a phishing scam for all ages ($136).
As our most up-to-date report, The United States of Elder Fraud, has found, the elderly are subject to an exponential amount of financial abuse each year with our estimates putting total losses at around $113.7bn. Often seen as “easy targets” and with median net worths stretching into the hundreds of thousands, phishing campaigns targeting over 60s are seen as fruitful.
How much of all of the above losses were recovered?
Of the 847,376 cases reported to the IC3 in 2021, the Recovery Asset Team (RAT) assisted in 1,726 cases (a mere 0.20 percent of cases). When involved, though, the RAT enjoyed a 74 percent success rate, (down 8 percent from 2020) freezing over $329m of the $443m lost in these specific cases. Nevertheless, the recovered amount still only accounts for around 4.8 percent of the total reported losses to the IC3 ($6.9 billion).
How did it happen?
Phishing attacks come in a wide variety of different types with the 323,972 reports received by the IC3 including phishing, smishing (text-phishing), vishing (voice-phishing), and pharming (website redirecting) and a further 19,954 include BEC/EACs. While the IC3 doesn’t provide any further breakdown by type of phishing attack, we can see trends elsewhere.
According to the victims that submitted state-specific data about phishing scams to the IC3:
- Puerto Rico saw the highest average cost per victim with average losses of $24,910. This is over 180 times more than the average loss of $136.
- California and Montana saw the second-highest average losses with $4,380 and $3,843 respectively.
- Rhode Island saw the lowest average loss with just $31 lost per victim–over $100 less than the average.
It’s no surprise that California was the state with the highest number of complaints (2,942) and, therefore, the highest amount lost to phishing scams ($12,884,518). However, with 170 victims, Alaska had the highest rate of phishing scams with 23.20 victims per 100,000 of the population. This was closely followed by Wisconsin with 17.50 victims per 100,000 of the population (1,032 victims in total). At the other end of the scale was Puerto Rico with 1.62 victims per 100,000 of the population (53 victims in total).
According to the victims that submitted state-specific data about BEC/EAC scams to the IC3:
- South Dakota saw the highest average cost per victim with average losses of $357,264. This is nearly three times the average loss of $120,074.
- Puerto Rico saw the second-highest losses alongside New York, with $274,128 and $183,836 respectively.
- Rhode Island once again saw the lowest average loss with $32,462 lost per victim–over a third lower than the average loss.
California reported the highest number of complaints again (3,017), and the highest number of victim losses with $403.6 million lost in total. This equated to a slightly above-average loss of $133,796 per incident.
With 134 victims, the District of Columbia had the highest rate of BEC scams with 20 victims per 100,000 of the population. This was double second-place Iowa’s rate of 9.85 victims per 100,000 of the population (142 victims in total). Puerto Rico remains the state with the lowest rate of victims with just 1.04 per 100,000 of the population (34 victims in total).
What the above figures have shown us is that BEC scams had a huge impact on US businesses in 2021. But how did organizations fare against other types of phishing scams?
Proofpoint’s survey of US organizations found that in 2021:
- 79 percent of US businesses experienced a successful phishing attack, compared to the global average of 82 percent
- Of these businesses (multiple options could be selected):
- 52 percent lost data (2020 = 58%)
- 43 percent suffered credential/account compromise (2020 = 55%)
- 40 percent were infected with ransomware (2020 = 55%)
- 28 percent had other malware infections (2020 = 31%)
- 18 percent suffered financial loss/wire transfer fraud (2020 = 35%)
As we can see, these figures are a dramatic improvement on 2020’s figures. But the loss of data for US businesses does remain well above the global average of 44 percent.
Proofpoint’s survey also covered specific types of phishing attacks and the number carried out on each organization. What the below table demonstrates is that US organizations are often subject to higher volumes of these attacks than the average global business. For example, 27 percent of US businesses were attacked by 11 to 25 vishing campaigns compared to the global average of 20 percent.

How does this transfer across each industry?
According to KnowBe4’s Phishing by Industry Benchmarking Report, the most at-risk small industries (1 to 249 employees) are education (32.7% at risk), healthcare (32.5% at risk), and retail/wholesale (31.5% at risk). Hospitality (39.4%), healthcare (36.6%), and energy and utilities (34%) are the most at-risk medium-sized companies (250 to 999 employees). And insurance (52.3%) consulting (52.2%), and energy and utilities (50.9%) are the most at-risk large industries (1,000+ employees).
The vulnerability of healthcare organizations continued into 2021. The Healthcare Information and Management Systems Society’s (HIMSS) annual survey revealed 45 percent of healthcare organizations suffered a security incident as the result of a phishing attack in 2021. This was by far the most common type of attack. In second place was ransomware attacks at 17%. Email phishing remained the most common point of compromise (71% of cases) and general email phishing is the most occurring type of phishing (71%), closely followed by spear-phishing (67%).

Emails are usually the easiest and cheapest way for criminals to create phishing attacks. Proofpoint reports that link-based templates remained the most used technique, but have dropped from 68 to 65 percent. This was followed by data entry (increasing from 23% to 26%), and attachments remained the same year on year, used in 9 percent of phishing emails.
WebTitan has noticed a rise in a new way to distribute phishing scams by using QR codes. While phishing emails use masked hyperlinks (often with changing texts), you can still hover your mouse over a hyperlink to see the URL. QR codes, however, don’t provide this pre-checking method and instead take you directly to the malicious website. WebTitan states this could lead to the entering of bank credentials or other sensitive information which will be exploited by attackers. It’s possible that we may see more QR code phishing in years to come, with many healthcare, retail, and hospitality organizations using these codes as a way to keep documents electronic and avoid physical print-outs.
What’s even more worrying is the increase of phishing websites available online. Bolster has reported a 53 percent increase in phishing and counterfeit pages, increasing from 6.9 million in 2020 to 10.7 million in 2021. The average number of pages detected per day also increased year on year from 19,000 to 29,000.
The key events used by scammers
Trending topics
Throughout the pandemic, scams have focused predominantly on COVID-19, regularly shifting to fit the narrative of the world at that time. Proofpoint claims there was an uptick in campaigns that latched onto vaccine mandates and organization policies, relevant to what was going on in June 2021.
Other popular trends that cybercriminals utilized were:
- Streaming shows, such as ‘Squid Game”
- Pop-culture events, such as Justin Beiber’s world tour
- Economic issues, such as US unemployment programs (see below)
Holiday shopping scams
As seen in our 2020 report, e-commerce scams are a recurring threat throughout the holiday period. In November 2021, there was a 208 percent increase in the number of phishing campaigns impersonating Amazon, according to F5 Labs. This coincides with the festive period and a rise in online shopping.
Cryptocurrency
In recent years, cryptocurrency-related scams have skyrocketed. Our recent worldwide crypto report uncovered that crypto rug pulls and scams have netted cybercriminals over $25 billion with $8.4 billion of this being stolen in 2021 alone. This is mirrored in the rise in crypto-related phishing scams. For example, during the early months of 2021, phishing attempts in the cryptocurrency sector saw just 1 percent on average, but in November this percentage jumped to 20 percent.
This huge rise in November correlates with the crypto market seeing a major increase in value. Bitcoin, for example, broke records with a cost of $64,400 for just one BTC on November 12th 2021. As we have seen in other cyberattacks, whenever there is financial wealth to be had, hackers are quick to adapt and profit from it.
US Financial Aid Scam
An ongoing phishing campaign, reported by ESET, saw fraudsters mimicking information from ‘The American Rescue Plan’ (also called the COVID-19 Stimulus Package). This quickly became a popular method of phishing with tens of domains connected to the campaign popping up in July 2021, including “relief”, “rescue”, “care”, ‘covid” and more. WeLiveSecurity claims that many people fell for this scam because they were unaware that a form of payment wasn’t necessary for the application.
Aryeh Goretsky, a distinguished researcher from ESET describes that: “The American Rescue Plan phishing campaign, along with others using similar pretenses to trick users into giving away sensitive information, shows that even after a year and a half, the pandemic continues to create fertile ground for scammers. People should treat online forms with the utmost caution, and only access government websites by directly navigating to them, never from links in emails or elsewhere. Federal government websites end with a .GOV domain.”
Why did it happen?
Proofpoint describes 2021 as a “year-long case of déjà vu”, and that’s precisely what it was.
From employees working from home and increases in video calls to online shopping and the use of emails and texts, scammers were able to take advantage of the continued reliance on online activities and communication.
Ultimately, by impersonating important figures on key topics such as vaccine mandates, exploiting vulnerabilities such as families in desperate need of financial help, and weaving their way in amid other influxes of information, scammers cleverly adapted their phishing campaigns to suit. Plus, phishing emails, like all scams, usually try to instill a sense of urgency in victims. This creates pressure to act, which, when teamed with all of the other chaos and confusion, could lead to more people handing over private or financial information in a panic.
Aren’t they easy to spot, though?
No– not always.
A report by Verizon analyzed phishing templates and found the rate of clicks is improving, but clicks are still in the tens of millions.

As the figure above demonstrates, people are getting better at reporting phishing. There has been a steady 10 percent increase in phishing test emails being reported in the last half a decade. Verizon also found that just 2.9 percent of emails are clicked on. However, even though this seems low, it still equates to 33,473,532 potential accounts phished out of 1.15bn.
A study by IBM Security also suggests the click rate of phishing campaigns that added phone calls (vishing or voice phishing) were three times more effective, gaining a click from 53.2 percent of victims– compared to the average click rate for targeted phishing campaigns being 17.8 percent.
Despite these figures, many studies are confident that people (employees in particular) are becoming more aware of phishing scams.
For example, Proofpoint’s survey found that 53 percent of working adults globally know what the term “phishing” means. However, US workers answered correctly 49 percent of the time.
A previous Proofpoint survey also found that older generations are more likely to know what phishing is:
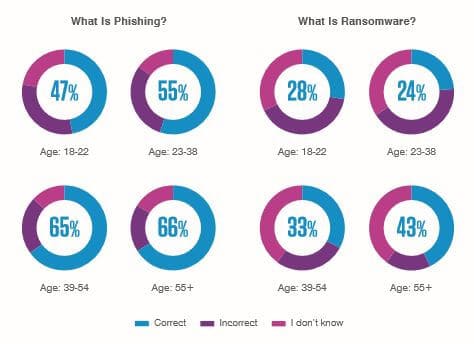
But when it comes to other more specific types of phishing, e.g. “smishing” and “vishing,” older generations were less likely to know.
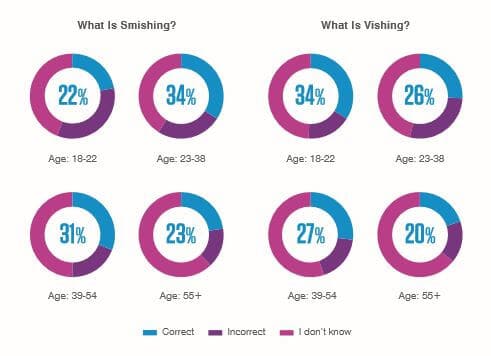
What does this suggest?
That amid the mass spam phishing emails are many cleverly-crafted, targeted phishing campaigns that are incredibly successful. Yes, the over 55s may be more aware of what phishing is, but as we have already noted, they are often a more “fruitful” candidate for scammers. Therefore, scammers may feel they can invest more time into the finite details of these scams as the payout is far greater.
It is also important to note here that the “over 60s” age group accounts for a large chunk of people. All of the other age brackets cover just 9 years each, while the over 60s covers more than 40 years. So even though over 55s in the workplace may be savvier when it comes to what phishing is, many of those over 60 (especially those in the over 70/80/90 brackets) may be unaware of what phishing is or may be less able to spot a sophisticated phishing email.
In the Psychology of Human Error report by Tessian, it was found that just 8 percent of people aged 51 and above felt they had clicked on a phishing email at work (compared to 19 percent of 18 to 30 year olds, 32 percent of 31 to 40 year olds, and 29 percent of 41 to 50 year olds), Stanford University Professor, Jeff Hancock, suggests that while “The older generation have, in many ways, the potential tools and mindsets needed for detecting phishing attacks,” they may also be more reluctant to admit that they’ve made a mistake in fear of “losing face.”
Proofpoint’s more recent survey also finds that there are still misconceptions about emails and phishing. In the US, 42 percent of workers believe emails with familiar logos are safe. Here are some other email misconception statistics globally:

With so many misconceptions, what are some of the main ways scammers are convincing people into clicking an email phishing link?
Knowbe4 reports that email subjects referring to COVID-19 are no longer successful and instead, emails associated with HR and security-related notifications are on the rise. Some of the top US email subject lines across 2021 included:
- Password Check Require Immediately
- IT: Information Security Policy Review
- Vacation Policy Update
Based on a report by ESET, financial organizations were the most frequently impersonated websites, with the vast majority being banks. Chase Bank, Wells Fargo, and Citibank were the most impersonated banks with Chase representing 15 percent of the whole finance category. The second-largest category being impersonated with phishing URLs was social media, including Facebook, WhatsApp, and Instagram.
Another hugely important factor in the success of phishing campaigns is the fact that many employees were working from home.
Proofpoint uses the phrase “pandemic fatigue” to describe how COVID has impacted people in 2021. The exhaustion from the pandemic is taking its toll, especially when it comes to job performance. The report claims that attention spans are short, many feel displaced or disconnected, and employees are struggling to stay engaged in work environments.
A report by Malwarebytes found that one-in-four employees (27 percent) felt overwhelmed by threats and jaded by cybersecurity procedures. While in the same report, 71 percent of organizations have implemented new cybersecurity training for their staff, it seems the experience of dealing with potential attacks from home is more frightening than it was in the workplace.
What needs to be done?
There is no silver bullet when it comes to protecting both consumers and organizations from phishing scams. But if 2021 taught us anything about cybersecurity, it’s that training for all situations and being able to adapt to ever-changing threats is key. This includes:
- Providing regular cybersecurity training for all employees: Our research above highlights how a lack of training and/or knowledge can provide easy access for cybercriminals. But, due to how quickly cybercriminals can adapt their scams, one-off training sessions aren’t likely the answer. Rather, as KnowBe4’s research highlights, ongoing cybersecurity training can dramatically reduce phishing attacks. Without any training from the platform, 31.4 percent of employees were likely to fall victim to a phishing scam. After one training session, this decreased to 16.4 percent. And after ongoing training for a year, it reduced even further to 4.8 percent.
- Using behavioral science to mimic “real-life” attacks: Masha Arbisman, the Behavioral Engineering Manager for the Paranoids (the information security team at Verizon Media) believes “the simulations and training offered by most security education teams do not mimic real life situations, do not parallel the behaviors that lead to breaches, and are not measured against real attacks the organization receives. This is why it is important to progress from the traditional security awareness model to that of using behavioral science to change the habits that lead to attack path breaking actions.” She goes on to say they have used the Huang and Pearlson model (which suggests that cybersecure behaviors are driven by the attitudes, beliefs, and values of an organization) in combination with behavioral science techniques. She says, “Over two years, the approach tripled adoption of a password manager and decreased the overall phishing susceptibility of employees by half.”
- Introducing phishing-specific legislation: As of May 2022, only 23 states had laws that were specifically aimed at phishing schemes. While all other states may cover phishing within computer crime, identity theft, and data protection laws, for example, having phishing-specific legislation will help mitigate attacks by providing further clarity for law enforcement and ensuring greater enforcement.
- Educating consumers: At a basic level, consumers should be encouraged to take simple measures, whether that’s by social media companies, e-commerce sites, or financial institutions. Users should be encouraged to install anti-virus and anti-spam software, to be kept up to date with the latest phishing schemes, be warned not to click on any links within emails, texts, or posts without first checking their validity, be asked to create a unique password with each account, and advised never to hand over sensitive information online, via social media, or through email unless they are 100% comfortable it a trusted person/account.
- Implementing multi-factor authentication: In order to prevent phishers from accessing personal information, the legitimate identity of the user can be verified using two- or multi-factor authentication. As opposed to single-factor authentication which uses only a username/email address and password, two-factor authentication requires an additional layer of information, e.g. a one-time-password (OTP) sent to the user’s phone. Multi-factor adds another layer of security. However, while these do add a timely element to the authentication process and are far more secure than single-factor authentication, they aren’t without their vulnerabilities, too. Man-in-the-middle attacks, SIM swapping, technical support scams, fake 2FA pages or pop-ups, and scareware are all examples of how scammers have adapted to these extra layers of protection.
- Having zero trust: A new concept on how to approach security problems (as implemented by President Biden for entities working with the government), is having zero trust. This assumes that a breach has already happened and works to make it as difficult as possible for attackers to work through the network with multiple checks in place. It recognizes where data is held and who has access to it, and by implementing multiple levels of authorization it aims to prevent any outsiders from accessing protected data. This should be used by the smallest of organizations to the largest (as seen by the US government) and should minimize the level of threat received.
- Seek the best threat intelligence – Keeping up to date with the current threat landscape is key to being prepared. It is a necessity to source multi-point threat intelligence feeds to gain the most valuable insights available.
As with most types of cybercrimes, a multi-layered approach is necessary. As we have seen, human error and lack of education are at the heart of many of these scams, which is why education on a consumer level and organizational level is essential. Unfortunately, this still won’t remove the threat, which is why users, technology providers, governments, law enforcement agencies, and organizations need to enlist the help of anti-phishing techniques, tools, legislation, and vigilance wherever possible.
Insights and observations
- Subdomains are often used to trick victims into clicking on links. For example, a cybercriminal might register “scam.com” and then use subdomains to obscure it, e.g. paypal.com.scam.com. This is particularly effective against mobile users because the address bar on smartphones is much smaller, thus hiding the full URL.
- QR codes help remove any potential pitfalls with users noticing scam URLs like the above as they take you straight to the offending website.
- HTTPS is no longer a reliable means to determine whether a site is safe or not. In fact, more than half of phishing sites use HTTPS.
- Phishing is often the first step of infiltrating a larger system. It could be used to steal credentials, for example, that give the attacker access to the victim’s system. From there they can steal data, install ransomware, or impersonate the victim by hijacking accounts.
- We should all assume that all of our email addresses are publicly available and anyone, including scammers, can target them.
- Before sending any new emails out, crooks test their messages with SpamAssassin or a similar tool on a separate system. SpamAssassin provides a “Score” – a subjective assessment of the probability that a specific email is spam. This score is an opportunity to make edits before sending actual emails to ensure they don’t get caught in spam filters.
Phishing attacks by sector
Healthcare
As noted previously, 45 percent of healthcare cybersecurity professionals reported that their organization had been attacked by phishing in 2021.
Our research determined that medical breaches have accounted for more than 342 million leaked records since 2009. Medical organizations are a prime target for phishing scams with so much personal data to offer to attackers. Below are just a couple of examples of medical breaches that suffered large-scale phishing attacks in 2021:
- Mongolia Health Systems – 492,861 patients affected – several employee email accounts were compromised as a result of a phishing attack. The accounts were used to divert a wire transfer that occurred between May 10, 2021, and August 15, 2021, and they contained the protected health information of 398,164 patients. The health system went on to suffer a second data breach as a result of the first which resulted in a total of 492,861 victims being impacted.
- Orlando Family Physicians – 447,426 patients affected – Email accounts containing protected health information of hundreds of thousands of people were accessed by an unauthorized person in April 2021. An employee had responded to a phishing email and disclosed their account credentials.
Education
The University of Central Missouri and Vanderbilt University based in Nashville, Tennessee, are just two American universities highlighted as being part of a large-scale phishing campaign. Attackers used the COVID-19 variant, Omicron as a lure to steal university login credentials. Thousands of messages that targeted dozens of universities used spoofed versions of Office 365 login portals to gain login information of unsuspecting students.
Phishing may also be used to infiltrate school systems to launch larger attacks, such as ransomware. For example, the K-12 Cybersecurity Resource Center found that just 2 percent of all cyber incidents captured on its incident map in 2021 were due to BEC attacks alone, but ransomware accounted for 62 percent of all attacks. And it is these attacks that have a devastating impact on schools–as our recent report suggests. In 2021, ransomware attacks cost schools and colleges $3.56bn in 2021.
Government
The US Federal Government Risk in 2022 report by Black Kite found the biggest vulnerability the top 100 defense contractors analyzed face is phishing attacks. 32 percent of these organizations were classed as being susceptible.
We can see this from our research that looked at government agencies in the UK. On average, government employees there receive 2,400 malicious emails per year (including phishing and spam emails). While just 0.32 percent of staff opened a malicious email on average, this did result in an estimated 8.62 million malicious emails being opened in total.
Meanwhile, in the US, President Biden has implemented a new principle for organizations working with the government. On January 26, 2022, the Office of the Management and Budget (OMB) released a memo titled “Moving the US Government Towards Zero Trust Cybersecurity Principles.” The memo specifically refers to government agencies, vendors, and contractors that work with the government to cut down on the number of cyber attacks they see. One key point from the memo reports that phishing-resistant multi-factor authentication (MFA) is now required for these organizations.
How is 2022 looking?
The ITRC has released a H1 2022 data compromise report, which reveals a few details on the state of phishing so far for 2022. Phishing once again remained the root cause of data compromises in H1 2022. During the first half of 2022, 219 out of a total of 734 breaches (30 percent) were due to phishing/smishing/BEC attacks. This is a similar rate to 2021’s figures where 33 percent (537 of 1,613) of data breaches were due to phishing/smishing/BEC attacks. 2021’s figures do seem slightly higher, but, as breaches are often reported a month or so after they occur, 2022’s figures may rise.
Globally, the Anti-Phishing Working Group (APWG) has already, in the first and second quarters of 2022, recorded 1,025,968 and 1,097,811 phishing attacks respectively. Q1 was recorded as being the worst-ever quarter for phishing, and the first time a quarterly total has exceeded one million attacks. But with Q2 exceeding this even further, 2022 looks set to be a record-breaking year for global phishing attacks.
As for the cost of these attacks –the Q2 report states that the average amount requested in a wire transfer for BEC attacks in Q2 was $109,467, up from $91,436 in Q1 2022. This is double the average amount witnessed in Q4 of 2021, too ($50,027).
Another global report by Vade, found that, in the first half of 2022, the financial services industry represented 34 percent of all unique phishing URLs detected. As with 2021, banks were the most impersonated target for phishing scams. Other impersonated targets included cloud and internet/telco (19%), social media (17%), e-commerce (10%), and the government (just 1 percent).
Another interesting find by Vade is that phishing threat actors like to keep their work within business hours, attacking most often on weekdays, especially Monday through to Wednesday.
Conclusion
If one thing’s clear from the above, it’s that scammers are always going to adapt to ensure the success of their campaigns. And they will continue to utilize our vulnerabilities to their advantage. Scammers continued to find ways to prey on the biggest vulnerabilities and used them to their advantage. This is likely to be the same story in 2022, too, with figures already suggesting large increases in attacks and $ amounts lost.
While attackers moved away from COVID-19, many new interests have found their way to the forefront. Cryptocurrency-related scams grew and are likely to continue to grow throughout 2022.
Whatever the rest of this year may bring in terms of the pandemic, cybercriminals will, as they always do, remain one step ahead. That’s why it’s vital users, organizations, and government entities remain vigilant, invest time in training, and pay extra attention to messages requesting any personal information or to perform any further actions, e.g. clicking on a link or downloading a file.
Data researcher: Charlotte Bond
Sources
Black Kite – https://blackkite.com/wp-content/uploads/2022/05/Federal-Report-2022.pdf
Bolster – https://boost.bolster.ai/rs/540-RFH-299/images/2022_PhishingandFraudReport.pdf
ESET (WeLiveSecurity) – https://www.welivesecurity.com/wp-content/uploads/2021/09/eset_threat_report_t22021.pdf
F5 Labs – https://www.f5.com/labs/articles/threat-intelligence/holiday-phishing-trends-for-2021
HIMMS Cyber Security Survey – https://www.himss.org/sites/hde/files/media/file/2022/01/28/2021_himss_cybersecurity_survey.pdf
IC3 – https://www.ic3.gov/Media/PDF/AnnualReport/2021_IC3Report.pdf
IBM – https://www.ibm.com/downloads/cas/ADLMYLAZ
ITRC – https://www.wsav.com/wp-content/uploads/sites/75/2022/01/20220124_ITRC-2021-Data-Breach-Report.pdf
KnowBe4 – https://www.knowbe4.com/hubfs/2022-Phishing-by-Industry-Benchmarking-Report.pdf
Malwarebytes – https://www.malwarebytes.com/wp-content/uploads/sites/2/2023/08/malwarebytes_enduringfromhome_report_final-1-1.pdf
Pew Research Center – https://www.pewresearch.org/social-trends/2022/02/16/covid-19-pandemic-continues-to-reshape-work-in-america/
Proofpoint – https://www.proofpoint.com/sites/default/files/threat-reports/pfpt-uk-tr-state-of-the-phish-2022.pdf
WebTitan – https://www.spamtitan.com/web-filtering/category/cybersecurity-advice/
