Comparitech researchers analyzed the privacy and security of 175 apps made for Muslims on Google Play, including prayer apps, Quran apps, and dating apps. We scanned each app for details of any sensitive information collected and a list of the requested permissions, such as the user’s location and contacts list. Although we did not investigate who user data is shared with once collected, our research gives a clear picture of what personal information is accessible to the app developers.
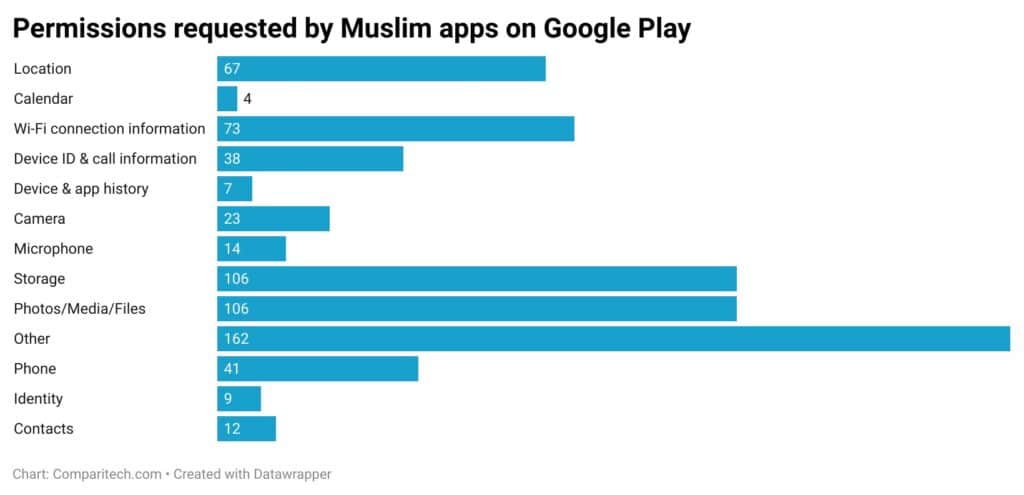
- 96 percent of the apps request permission to use “Device ID and call information”. According to Google, that permission allows the app to access your device ID, call status, phone number, and the phone number of the other party in a call. In short, the app can see who the user calls and when.
- Nearly 40 percent of apps for Muslims request access to the device’s location. Location data can be used to track users’ movements.
- 63 percent of apps request access to the user’s data storage, including photos and media.
- 7 percent requested access to users’ contacts lists. This allows developers to collect and potentially share lists of the user’s personal connections.
Not all of these permissions are malicious, but they are often unnecessary and raise questions as to what data is collected and with whom it is shared. One can surmise how authorities and other groups could use this information to spy on the whereabouts, relationships, and personal lives of the people using these apps.
Vice Motherboard in November 2020 reported that the US military was purchasing user data from Muslim Pro. Following user backlash, the app said it will no longer share data with X-Mode, a data broker that sold user locations, among other data, to the US military. Google and Apple both subsequently banned X-Mode from their app stores.
In 2021, another Vice Motherboard investigation revealed that another Muslim prayer app – Salaat First — was recording and selling Musilm’s location information to Predicio – a data broker with links to various US government agencies. Collected data includes the latitude and longitude of the app’s users, their phone models, operating systems, IP addresses, and a timestamp. The revelations prompted Google to threaten to remove apps from the Play Store that contained Predicio code.
The controversy surrounding Muslim Pro and Salaat First is what ultimately spurred Comparitech to research prayer apps for Muslims.
Which Muslim prayer apps protect your privacy?
Muslim prayer apps commonly help users stay on top of prayer times, know which direction to face when praying, read the Quran, listen to recitations, and recite prayers, among other resources. Most of these apps are available for free on Google Play and the iOS App Store, but the app developers could be monetizing the app by collecting and selling users’ personal data.
We chose the following apps based on the following criteria:
- Install-time and run-time permissions requested
- Use of third-party ads
- Vulnerabilities and leaks
- Privacy policy
Unfortunately, it’s difficult to find a prayer app that doesn’t use your location. Location info is used to determine your time zone for prayer scheduling and which direction your Qibla (compass) should face.
With that caveat, we found the following Muslim prayer apps with English text that respect your privacy:
Pillars
Pillars is a UK-based app created largely in response to privacy concerns raised by the Muslim Pro app in 2020. The app includes prayer notifications, a Qibla, and a prayer tracker, among other tools. It’s ad-free and emphasizes privacy, only requesting a handful of permissions:
- Location
- Device and app history
- Other (run at startup, network access, prevent device from sleeping, control vibration)
Pillars’ privacy policy states that although the app uses your location and some personal data, that information never leaves your phone.
The app didn’t have any of what we consider to be serious leaks, according to our tests.
Daily Islam
Daily Islam is an ad-free app that includes a Quran, prayer timer, Qibla, and other educational materials. It only requests three permissions on Android:
- Location
- Wi-fi connection information
- Other (run at startup, control vibration, prevent device from sleeping)
The developer has a short but clear privacy policy. Our tools only flagged one permission as severe and no serious leaks.
1Muslim
1Muslim is an ad-free app that requests minimal permissions and has no major security concerns, according to our tests. It includes prayer notifications and a Qibla.
The app requests permissions for:
- Location
- Storage, including photos and media
- Other (run at startup, prevent device from sleeping, set alarm, etc)
We detected one leak within the app, which is below average. Our tests found an exposed plain-text password for a repository manager.
The privacy policy is clear and concise and makes no mention of sharing data with third parties.
Deen Islamic App
Deen Islamic App is an ad-free app with Bangla and English versions. It includes a prayer timer, Quran with audio translations, Qibla, and other useful features. It only requests the following permissions:
- Location
- Other (run at startup, control vibration, prevent device from sleeping)
The privacy policy is very short but the developer does state that they retain all user info, with no mention of sharing it with third parties.
Our tools flagged one severe permission and detected one leak: an exposed Google API key.
iPray
iPray is an ad-free app that includes a prayer timer and Qibla. Notably, this app can be used offline, which is really the only surefire way to ensure an app isn’t collecting your personal data.
iPray requests the following permissions:
- Location
- Storage, including photos and media
- Other (change audio settings, run at startup, control vibration, prevent device from sleeping, etc)
The privacy policy is short but clear, stating that the app doesn’t collect or share any personal information. However, it is a bit leaky; our tools found the URL of the app’s Firebase database, a Google API key, and a generic API key.
Is Muslim Pro private?
Vice Motherboard in November 2020 reported that the US military was purchasing user data from Muslim Pro. Following user backlash, the app said it will no longer share data with X-Mode, a data broker that sold user locations, among other data, to the US military.
Although our analysis doesn’t examine who user data is shared with, we can see that Muslim Pro still requests the following permissions:
- Location
- Camera
- Storage, including photos and media
- Wi-fi connection info
- Other
None of the permissions were flagged as a security threat, but our tools did uncover four data leaks: an exposed plain text password, the URL of a Firebase database, a generic API key, and a Google API key.
Muslim Pro responded to Comparitech’s findings with the following information:
-
Plain Text Password: We don’t store any passwords on our side locally, and we use Firebase Authentication and use their SDK to let users login via email/password or change their password.
-
Firebase Database URL: This is exposed by design by Firebase. There is no way around it, but this is not a security issue at all. If anyone gets access to it, they won’t be able to do anything.
-
Google API Key: This is the same condition as the Firebase Database URL.
-
Generic API Key: This could be an API key coming from 3rd party Ad SDK. In that case it’s not an issue. For Muslim Pro’s own private API keys, they are always kept encrypted and secured using DexGuard – an industry standard tool for encryption of apps.
-
Lastly, Muslim Pro runs a public bug bounty program using a leading bug bounty platform called YesWeHack. If the app has any vulnerability or security issue, those are flagged by the security researchers on the platform, and Muslim Pro takes swift action immediately to mitigate those. At the moment, there is no security concern for the app in the platform.
Is Salaat First private?
The server hosting the Salaat First privacy policy does not have a valid SSL certificate. This prevents users from being able to open the link and read the policy. This is problematic given that users must agree to it before going on to use the app.
Following Salaat First’s last update (which, at the time of writing, is September 2023), its developers say that the app collects “network experience measurements, including location.” However, this data, they say, “does not identify you or your device.” Users can opt out of its collection in the app’s settings.
Methodology and limitations
Our analysis checked 175 apps’ Android APK files for vulnerable leaks and excessive permissions. Comparitech researchers created custom scripts to download and analyze each installation file.
Some of the leaks we checked for included but were not limited to:
- AWS API keys to access S3 storage buckets
- Facebook tokens to access someone’s profile and/or apps
- Firebase check for misconfigured databases
- Github tokens to access private repositories
- Google API tokens to access paid services with someone else’s profile
- PayPal to access banking information
- Twitter OAuth to access someone’s profile/application
- Twilio to access private accounts
- Slack webhooks to access private work spaces
- Heroku API to access hosted projects and modify/delete them
We elected not to disclose the specific leaks suffered by the apps listed so as not to encourage attacks against the apps or their users.
We then took a detailed look into the install-time and runtime permissions requested by each app. For simplicity, we often refer to these by their permission group in the article. Some permissions are security risks that open up user devices to attack (e.g. run shell scripts, read SMS), while others are purely privacy risks (access location, contact list).
Apkleaks and Quark were used for app analysis.
We examined the privacy policies of all recommended apps for any language or lack thereof that could indicate the collection and/or sharing of users’ personal data.
Are you a developer making private apps for Muslims? Think your app should be included? Let us know in the comments or contact the author on Twitter: @pabischoff