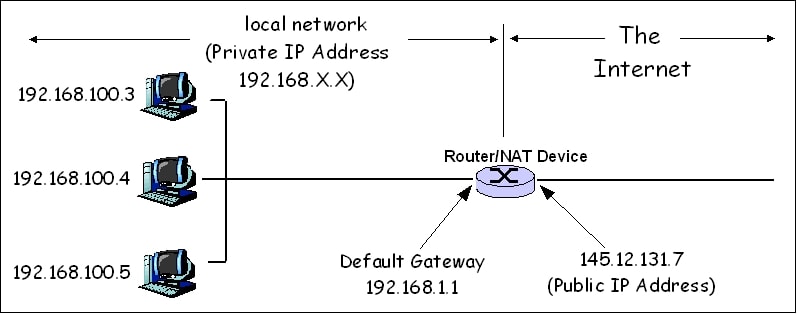
In the field of computer networking, NAT stands for Network Address Translation. In simplest terms, NAT allows many devices on a private network to share a single gateway to the internet. In turn, all of those devices will have the same public IP address—that of the gateway—and unique private IP addresses. These gateways are commonly found on wifi routers and some VPN services. For example, all of the devices connected to a NAT-enabled wifi router have different private IP addresses, but share the router’s public IP address.
JUMP STRAIGHT TO: The best VPNs with NAT Firewalls
When you visit a website, your device sends a request to the router, identifying itself with its private IP address. The router then translates the request and forwards it to the website’s server with its public-facing IP address, making a note of the originating private address. The server replies to the router with a copy of the website, which your router then forwards on to your device via the private IP address.
A firewall is a layer of protection that prevents unwanted communications between devices on a network, such as the internet.
A NAT firewall works by only allowing internet traffic to pass through the gateway if a device on the private network requested it. Any unsolicited requests or data packets are discarded, preventing communication with potentially dangerous devices on the internet. If inbound internet traffic does not have a private IP address to forward to beyond the gateway, the NAT firewall knows the traffic is unsolicited and should be discarded.
Computers and servers on the internet can only see the public IP address of the router and none of the private IP addresses of specific devices, like phones, laptops, smart TVs, internet-of-things devices, and game consoles. This is also known as IP masquerading.
How to tell if I’m behind a NAT firewall
Not sure if your wifi router has a NAT firewall enabled? Try connecting two devices to the same wifi network, such as a laptop and smartphone.
Now, on each of them, run a Google search for “what’s my IP?”
If you see the same IP address for both devices, you’re probably behind a NAT firewall. Your devices have different private (local) IP addresses, but the same public IP address.
On a VPN, it can be more difficult to determine whether a NAT firewall is being used, but you can usually find out somewhere in your VPN provider’s documentation. You might have the option to enable or disable a NAT firewall in your VPN app settings, or purchase one as an optional extra.
NAT firewalls and VPNs
A VPN, or Virtual Private Network, encrypts a device’s internet traffic and routes it through an intermediary server in a location of the user’s choosing. Because all internet traffic is “tunneled” through the VPN before reaching the internet, the NAT firewall on your wifi router can’t distinguish between requested and unsolicited traffic. Because everything comes encrypted from the VPN server, it all looks the same, rendering your router’s NAT firewall useless.
For this reason, many VPNs implement NAT firewalls. Instead of your wifi router filtering out unwanted traffic, the VPN server does it instead. Sometimes NAT firewalls are an optional extra, and sometimes they are built into VPNs by default.
Not everyone agrees that NAT firewalls and VPNs are a good combination.
VPN providers typically fall into one of two camps: those that use NAT firewalls and those that use PAT firewalls. We’ll explain the latter further down.
A VPN that uses a NAT firewall assigns each user a unique private IP address. It extends all the benefits of a wifi router’s NAT firewall, as discussed above, to your VPN connection.
The downside is that even though you are protected from unwanted communication, your device could be more easily tracked by the VPN provider or a third party.
The alternative method is to assign the same public IP address to all VPN users connected to the same server, without unique private IP addresses. This adds a significant layer of anonymity, because online activity can’t be traced back to an individual person or device by an IP address.
ExpressVPN is one provider that argues against NAT firewalls. The company says it uses a port-blocking policy in lieu of a NAT firewall:
“ExpressVPN’s servers remember all requests and broadcast them from different ports on the server. The user receives a reply from ExpressVPN, but other ports remain closed. Keeping the ports closed protects users as a firewall would.”
Port address translation
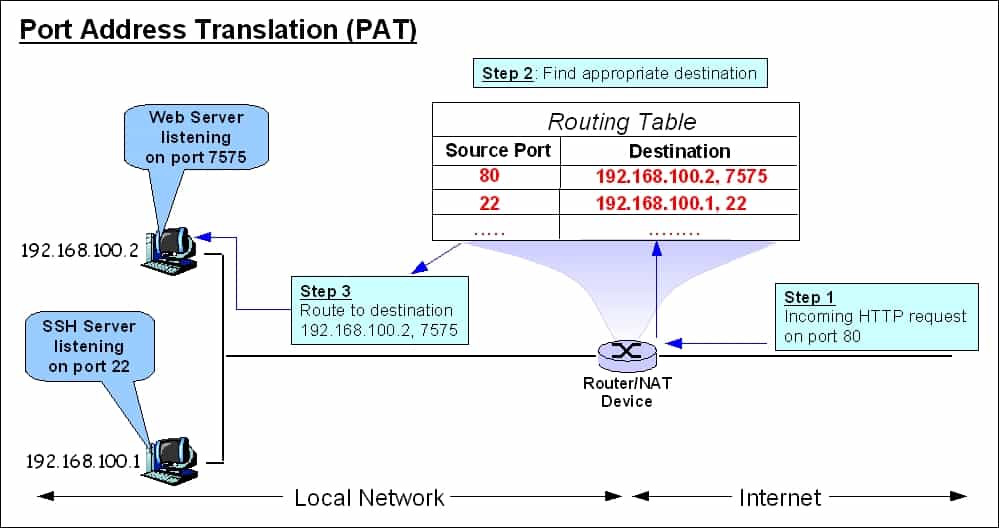
Many systems referred to as NAT firewalls are actually PAT firewalls. PAT stands for Port Address Translation. Similar to NAT, it enables a network gateway with one IP address to represent many computers. The difference is that each device is assigned a port number instead of a private IP address.
When a network gateway receives an outgoing address from a computer on the network, it replaces the computer’s return address with its own internet-compliant address and tacks a port number on the end. The gateway then makes an entry in its translation table so it knows that the port number it used represents a specific computer on the network.
This system is very popular because it cuts down the number of internet IP addresses that a company needs to own. It is also a very good system for VPN services to use because all of the traffic leaving the VPN gateway will have the same return address on it. As many VPN services have hundreds of customers connected to the same location at the same time, it is impossible to untangle which subscriber each request came from.
NAT firewalls and torrenting
Because NAT firewalls prohibit unsolicited traffic from reaching end user devices, they can cause trouble when torrenting. While behind one, you might not be able to upload (seed) files for other torrent users to download. Conversely, you may not be able to connect to as many peers from which you can download (leech) files. A NAT firewall can cut you off from a significant portion of users in a torrent swarm. The same goes for PAT firewalls.
However, that’s not to say torrenting is impossible with a NAT firewall. Most NAT firewalls these days aren’t so strict that they significantly impact download or upload performance. You might find more strict firewalls in public settings like hotels or schools, but most home routers and VPN services don’t restrict torrenting in this way.
If a NAT firewall on your local network is stopping you from torrenting, you can use a VPN to bypass it. Recall that because all inbound traffic goes through the VPN and is encrypted, your local NAT firewall can’t distinguish between solicited and unsolicited traffic. Even if the VPN has its own NAT firewall, it will likely be less strict than the one on your private network.
A handful of VPNs allow you to set up port forwarding to bypass NAT firewall restrictions while torrenting, but it’s important to note that doing so compromises security. Opening ports leaves you more vulnerable to attack, and because you’re using a special port, your internet traffic is more easily distinguished from other VPN users. That makes you easier to track.
Port forwarding is also a common feature on torrent clients like uTorrent, but the same risks apply.
Best VPN with a NAT firewall: IPVanish
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: www.IPVanish.com
Money-back guarantee: 30 DAYS
All IPVanish servers use NAT firewalls to allow users to share its public IP addresses. The apps even enable you to switch IPs at timed intervals. Because of the NAT firewall, you cannot port forward access to your device while connected. For some, this is a useful safety precaution. For others, it’s an obstacle. IPVanish says most users do not port forward and will not be affected.
Aside from the NAT Firewall, IPVanish is a quality VPN with rigorous security standards and a no-logs policy. You can connect up to 10 devices at a time, which is double what most VPNs offer. IPVanish makes apps for Windows, MacOS, iOS, Android, and Amazon Fire TV.
BEST VPN WITH NAT FIREWALL:Despite blocking port forwarding, IPVanish was built from the ground up with torrenting in mind: fast and private. It comes with a 7-day money-back guarantee.
Read our full IPVanish review.
Runner-up: VyprVPN
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: www.VyprVPN.com
Money-back guarantee: 30 DAYS
VyprVPN offers users a NAT Firewall to protect users from hackers that could otherwise reach your system through connections left open by your applications. Additionally, you can manually set which ports are used by the OpenVPN protocol. If you want to really customize your VPN connection, VyprVPN could be the one for you.
The company uses strong encryption and doesn’t log any identifying information or activity. It owns many of its own servers and data centers, which span some 60 countries.
VyprVPN makes apps for Windows, MacOS, iOS, and Android. You can connect up to five devices at a time.
NAT FIREWALL VPN:VyprVPN's NAT firewall and other security measures work to let you browse and download safely from anywhere in the world. You can test it out with a 3-day free trial.
Read our full VyprVPN review.
Best VPN without a NAT firewall: ExpressVPN
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: www.ExpressVPN.com
Money-back guarantee: 30 DAYS
ExpressVPN offers a shared IP address service and adds on security measures by using the OpenVPN protocol with 256-bit AES encryption. The AES key exchange is protected by 4096-bit RSA encryption, which is impossible to crack.
ExpressVPN doesn’t store any identifying logs and torrenting is allowed on all servers. The service is fast and includes access to thousands of servers in 94 countries. It works in China and can be used to unblock a lot of geographically restricted content on sites like Netflix and Hulu.
ExpressVPN makes apps for Windows, MacOS, iOS, Android, Linux, Amazon Fire TV, and certain wifi routers. You can connect up to three devices at once. A router counts as one device no matter how many devices are connected to it.
BEST VPN WITHOUT FIREWALL:ExpressVPN is a premium VPN with robust security and some great unblocking abilities to boot. It comes with a 30-day money-back guarantee.
Read our full ExpressVPN review.
Runner-up: NordVPN
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
- FireTV
Website: www.NordVPN.com
Money-back guarantee: 30 DAYS
NordVPN uses a shared IP address model, but a few dedicated IP addresses are available in the apps. Nord operates an impressive 5,000+ servers across more than 60 countries. It adheres to a strict zero-logs policy, and its apps are as secure as they get. This is also a good choice if you’re trying to unblock region-locked content.
A few alternative connection types are offered for a handful of servers. These include P2P-optimized servers, although torrenting is fine on any of them. Other options include Tor over VPN and double VPN.
NordVPN allows up to six simultaneous connections and makes apps for Windows, MacOS, iOS, Android, Linux, and Amazon Fire TV.
NO NAT VPN:NordVPN offers a huge number of high-speed servers and a range of different connection types. It comes with a 30-day money-back guarantee.
Read our full NordVPN review.
NAT firewall limitations
Not all computers behind a NAT firewall are immune to viruses. Nowadays, hackers have to trick computer users into installing Trojans. These programs will send out requests to the hacker’s computer. Because the incoming message from the hacker is sent in response to a request that originated from within the network, the gateway will let it through.
NAT firewalls do not protect you from phishing scams, where you receive an email from your online bank telling you to press a button in the email to connect to your account. In this trick, the email is not from your bank, but from a hacker, and when you log in to your account, you are just entering your credentials into a fake page created by the hacker.
A NAT firewall will not protect you from a man-in-the-middle attack, in which a hacker running a fake wifi hotspot captures all of your traffic by posing as the servers that you want to connect to.
There are still plenty of security weaknesses in any connection that NAT firewalls cannot protect you from. The benefit of using a VPN is that it deploys many different security procedures, including encryption and authentication certificates to prevent you from being conned or spied on.
How IP address translation works
If all of the computers in a network were to connect directly to the internet, then each would require a globally unique IP address. However, the more common configuration is to channel all of the internet communication for all of the computers on a network through one gateway. In this scenario, all of the computers need IP addresses that only need to be unique on that network.
Other private networks might use the same addresses, but that doesn’t matter because those addresses will each be unique within their respective networks. Only the gateway IP address has to be unique throughout the internet.
The gateway has to keep track of all of the computers on the private network that have sent out requests over the internet. When a response comes in, the gateway looks up which computer sent out the request in its network address translation table so that it knows where to forward the response.
When a computer on the network sends out a request to a server on the internet, the network gateway substitutes the private network address written in those communications with a unique internet address. When the session ends, that private address gets returned to the pool and will be assigned to another computer. Thus, the internet addresses on the private network are hidden and no one outside can be sure exactly which computer on the network sent the request. The gateway knows because it has a record in its network address translation table.
At the end of the connection, when the assigned address gets returned to the pool, the gateway removes the NAT entry for that address from its translation table.
Other benefits of NAT
NAT wasn’t originally intended to be used as a firewall. It was invented to make networks more portable so that not every device would need to be re-addressed if the network moved. Only the NAT device—such as a router—would require a new public facing IP address, while all the devices connected to it could continue using the same private IP addresses.
NAT is now essential when it comes to conserving global address space. The IPv4 protocol, which determines how all devices on the internet communicate, has a limited number of available IP addresses. If every device that connects to the internet required a unique IP address, we would soon run out. Connecting many devices on a private network through a single NAT gateway only uses up one IPv4 address.
IPv6 was invented to eventually replace IPv4 with a much larger address space, but adoption has been slow, so NAT is a very necessary tool to keep the internet up and running.
NAT Firewall FAQs
Will a NAT firewall protect me from viruses?
A NAT firewall ensures that only requested internet traffic can pass through a private network. This prevents communication with dangerous devices on the internet. However, while a NAT firewall does provide a private network with a layer of protection, it won’t protect you from all viruses. This is particularly the case if you inadvertently initiate the downloading of a virus through clicking on a link, for example. The device on the network will have requested that particular internet traffic and thus the virus can still be downloaded as a result.
Image credits:
- “CPT-NAT” [derived from] Miles J Pool, CC BY 4.0
- Yangliy at English Wikibooks [Public domain], via Wikimedia Commons (1), (2)