
How often do you get a question on your Android device about whether you want to give an app access to some application or other? This little popup appears so often that many people click on “Allow” without giving it a second thought.
Do you know how many apps you have given access to your personal information? While you hope that app-owners won’t abuse this access, with accusations rife against data-hungry companies like Facebook, you can’t be too careful.
Thankfully, with a little know-how, you can take steps to secure your Android device by changing your settings manually. In this post, we explain how to do just that.
How to discover app permissions
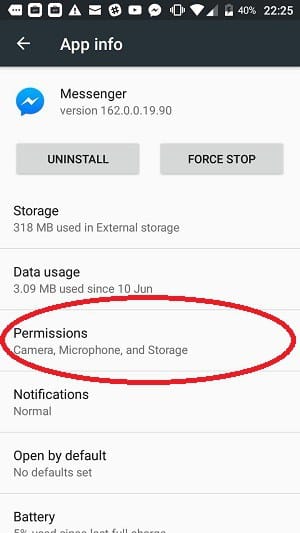
Information on the permissions that your apps have is easy to gather. First, go to the Settings screen. Scroll down to the Device section and then tap on Apps.
The next screen lists all of the apps on your phone.
Tap on an app to see all options. Select Permissions.
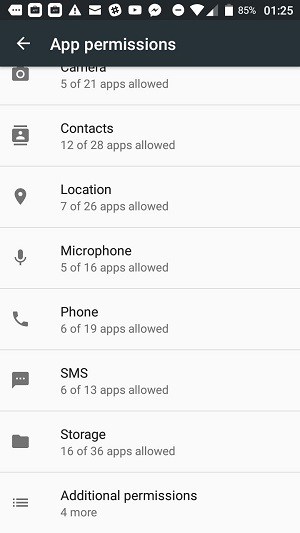
Now you can see the permissions that you granted to the selected apps.
Withdrawing permissions from apps
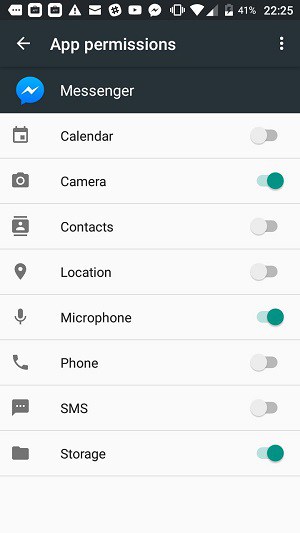
The services on your phone that apps can gain permission to access are:
- Calendar
- Camera
- Contacts
- Location
- Microphone
- Phone
- SMS
- Storage
If you granted access to one of these data stores or services, you can take that permission away by tapping on the slider next to the permission category.
Permission categories
Each of those categories you see in the permission screen for each app is not the name of an app, but the name of a category of apps. The Android operating system includes access functions that enable independently-written utilities to access the services of the operating system. There are a number of functions that each of these categories in the Permissions screen give access to.
Giving permission to access one of these categories gives apps access to operating system functions. Android contains all apps in a “sandbox,” which is an isolated environment that keeps those apps away from the operating system. Permissions break through that security measure.
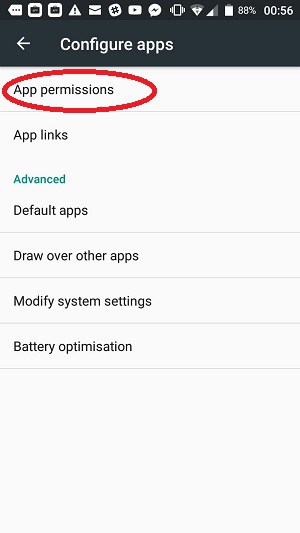
Configure app permissions
You can get another view of your app permissions through the Configure apps menu. To navigate to this location, go back to the Settings screen, tap on Apps, and then press the cog symbol in the header of the Apps screen.
This gives you the Configure apps options. Tap on App permissions to proceed.
In the App permissions screen, you will see an option that wasn’t available in the list of permissions categories that you arrived at by examining individual apps. The Body sensors category provides apps with access to motion, environmental and position sensors within the device. Examples include accelerometers, gyroscopes, thermometers, and magnetometers.
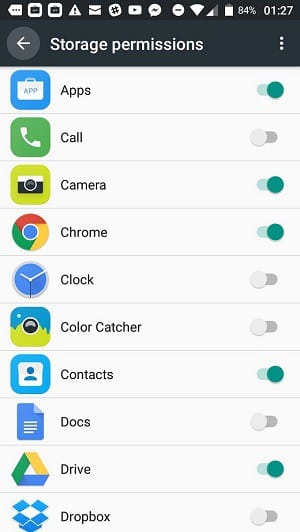
A line below each category tells you how many apps have that permission and how many apps installed on your phone could feasibly use that permission. This message is the format X of Y apps allowed where X is the number of apps with access and Y is the number of the apps with capabilities to use that category of service.
Click on one of these categories to get a list of all apps that have that permission.
Click on the slider next to a category to turn its accessibility off. All apps that have this permission will have that access removed.
Back in the Configure apps screen, scroll down to the bottom of the permissions list. You will see that the last list item is called Additional permissions.
In the Additional permissions screen you will see four options:
- Car information
- Read email attachments
- Read instant messages
- Write instant messages
If you tap on an option that lists the number of apps that apply to that category as 0 of 0, the resulting screen will simply read No permissions. If any of those categories could be used by at least one app on your phone, tapping on that category would lead to an app list that gives you the option of turning each use off with a slider.
Deny app access to system settings
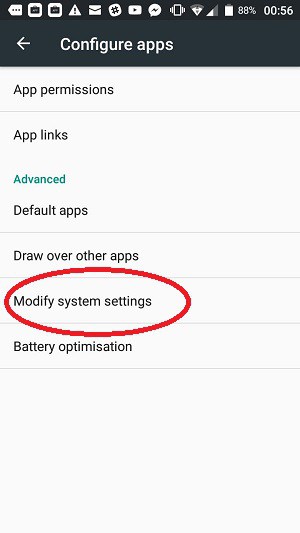
Although this guide is focused on “app permissions,” the task of securing your phone would not be complete without checking on the system settings that apps are allowed access to. You can view these settings via the Configure apps screen.
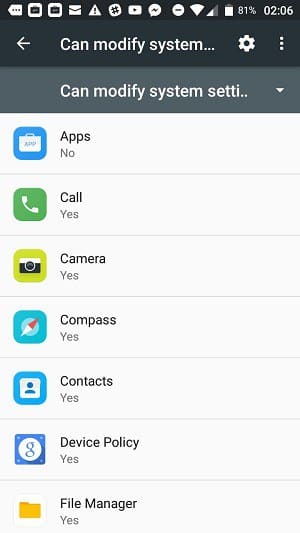
Tap on Modify system settings to proceed. The next screen shows every app installed on your phone with a message that tells you whether it can modify system settings.
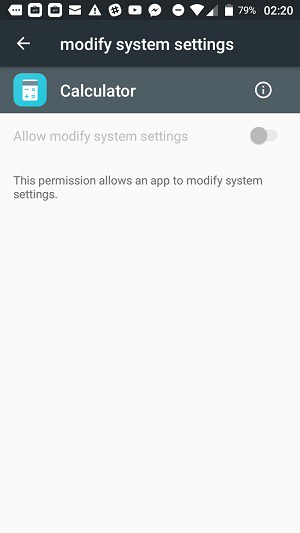
Tap on one of these apps to see a slider that enables you to block the app from accessing system settings.
The idea of letting apps access your system is worrying. It is difficult to understand which settings each app needs because they are itemized on the screens. There is no “Settings” page that provides details.
Prevent overlays
Malware can masquerade as a genuine app. You might click on Allow to a permissions demand without realizing that the app name that seems genuine is really an illegal app that contains a deceptive function. Such a malicious app can detect the apps that you want to open and then overlay them, mimicking the real app.
These types of apps are designed to gather authentication credentials for real online services. They can achieve this goal by making sure that the fake app covers the real version that you opened.
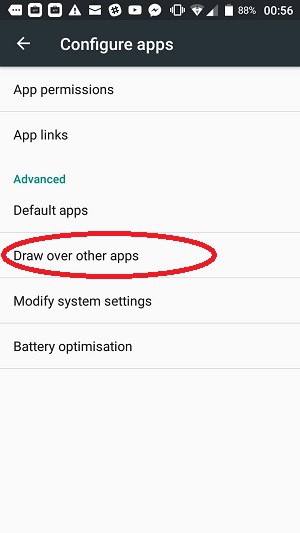
In order to perform this trick, the malware app needs to achieve the status of always being on top of all open apps. You can turn off this capability. Go back to the Configure apps screen.
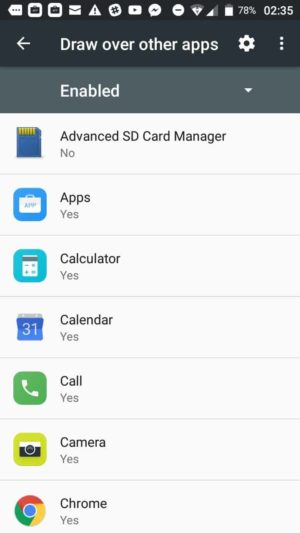
Tap on Draw over other apps to see which apps can overlay the screen. In the following list, you will see each installed app and whether it can overlay others.
To remove this permission, tap on an app that has the permission that you want to remove. This will take you to a screen in which you can turn the permission off with a slider.
App permission consequences
Now let’s take a look at some of the categories that apps might ask for access to. The consequences of granting access can be very damaging.
SMS permissions
If you allow a new app to access SMS, that new utility will be able to access MMS messaging systems as well as any SMS app you have on your phone, not just the one default SMS tool that comes with the Android operating system.
Furthermore, an app with permission to access SMS will be able to read all of the messages you have stored in your SMS apps. It will also be able to intercept and read (and possibly alter) incoming messages and it will even be allowed to send out SMS messages from your phone.
Phone call permissions
The permission to access any communication service on your phone is a gift to any malware that wants to replicate itself by sending out Trojan programs to your Contacts list. If the program can send those infections out from your Phone number, the hacker that wrote the original malware saves a lot of money and also hides his identity.
A malicious money-making app with permission to access your phone’s call functions can rack up your bill and make a ton of money for its owner by making repeated calls to premium numbers owned by the hacker.
Camera permissions
Apps that have the permission to access your camera can take screenshots of your activities, take photos and videos of you and your friends, and send those images and video files back to the writer of the app.
Similarly, if an app has access to your microphone, any recording tool on your phone can be manipulated to record you without your knowledge.
Location permissions
The location feature on your phone can tell burglars when you are away from your home and can tell the owners of location-restricted websites and services that you are outside of their operating area so they can block you.
More prosaically, leaving location turned on allows Google — via Google Maps — to keep track of your whereabouts. This information is subsequently stored in your Google Timeline.
Operating system and storage permissions
Giving an app permission to access your storage allows data thieves to steal your information. It also opens the door to ransomware that can encrypt all of the files on your device and make them inaccessible until you pay for the decryption key.
Allowing an app to gain control of system settings could mean you lose access to your phone.
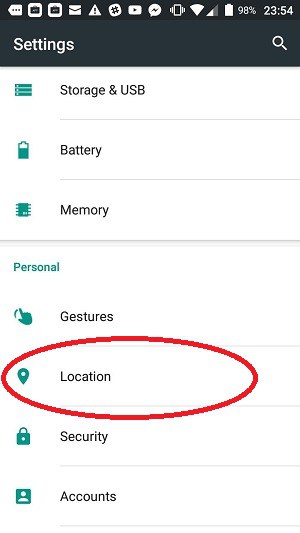
Turn off location services completely
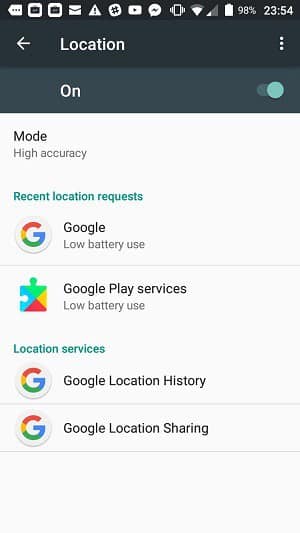
On Android, the only way you can turn off access permissions is on a per app basis, as described above. This is the case with all categories except for the Location services of your phone. These can be turned off completely.
Go to the Settings screen, scroll down to the Personal section, and tap on Location.
Click on the slider at the top of the Location screen.
You might be tempted to turn off location services in an attempt to defeat geo-restricted websites that try to block access from other countries. This will rarely work as your IP address will still be visible. Some websites can also locate your device using information gleaned from cell tower triangulation and nearby wifi access points.
If your aim is to bypass geo-restrictions, the best option is to use a VPN. This allows your device to assume the IP address of any server in the VPN provider’s network. If you connect to a server in the US, for example, it will look to the wider internet as if you’re based in the US.
Loapi Trojan
An example of a malware nightmare that will ruin your phone if you allow it to access the system is the Loapi Trojan, which Kaspersky Labs spotted towards the end of 2017. This malware is advertised as an antivirus utility or an adult content app. Once it is installed, the app will constantly demand permission to access the system. It will repeat the demand over and over again until you tap on Allow. You restart your phone to try to turn the app off, but that won’t work. When your phone starts up again, the first thing you will see is that demand for access.
The Loapi Trojan has a wide range of malicious functions. These include:
- Launching DDoS attacks on command on other internet-connected devices
- Cryptocurrency mining
- Frantic web page access to bump up income from recorded visits
The design of the Trojan enables its controller to load up new attacks on your phone at will. So this is a backdoor that will allow a constant stream of attacks to download onto your phone.
When investigating this Trojan, Kaspersky Labs loaded it onto a smartphone. Within two days, the excessive processing caused by the virus caused the device’s battery to bloat and the phone’s cover to warp. Basically, if you unintentionally download Loapi, you might as well throw your phone away.
The Trojan’s antivirus sweep will detect other antivirus programs running on your phone and alert you to allow removal of those programs, which Loapi falsely labels as malware. Again, the app will not take Deny for an answer. The prompt to allow the removal of those programs will not stop until you tap on Allow.
If you have Loapi on your phone, you might try all of the steps outlined in this guide to remove its permissions. However, the defense mechanisms of this malware suite will lock the phone and shut down the settings screens, making it impossible for you to revoke its access rights. This vicious app is just one example of malware that will render your phone unusable.
Joker malware
A more recent example of problematic malware is Joker malware. This family of malicious apps has been attacking Android users since 2016. Media outlets reported in 2020 that the malware had infected many different apps. The malware returned in 2021, updated, targeting millions of Android users. Joker malware is now so widespread that cybersecurity firm Zscaler has created a dedicated team to research the threat.
Joker’s apps are knockoffs of legitimate apps. When you download them from Play or a different market, the app contains no malicious code other than a “dropper.” This obscures the app’s payload for hours — or even days. The dropper then downloads a malicious component and then drops it into the app. Apps recently found hiding Joker malware include:
- Free Affluent Message
- PDF Photo Scanner
- delux Keyboard
- Comply QR Scanner
- PDF Converter Scanner
- Font Style Keyboard
- Translate Free
- Saying Message
- Private Message
- Read Scanner
- Print Scanner
When you download an infected app, this tricks the Android notification system by asking for permission to read all notifications. Once you grant this permission, it hides all notifications of malicious behavior. Since these notifications are hidden, criminals can:
- Steal personal information
- Access and copy your contact list
- Monitor your text messages
- Sign you up for fraudulent services
- Send text messages to premium numbers
If you have downloaded any of the apps listed above, you should immediately uninstall them. To find and delete apps on Android, follow these steps:
- Open the Google Play Store app
- At the top right, tap the profile icon
- Tap Manage apps & devices and then Installed
- Go through the list of displayed applications
- Next to the app you want to remove, tap Uninstall
Wrapping Up
It’s time to take back control of your Android device. You need to adjust all of those permissions and tighten up the security of your phone.
Be very careful about where you get your apps from and avoid third-party Android app stores. Never respond to spam SMS messages and avoid following links in web pages while using your phone. You also need to make a vow to pay attention to those permission notifications and select Deny unless there is a very good reason to tap on Allow. If an app won’t work without those permissions, you may want to consider uninstalling it.
See also:
Cybercrime stats
Identity theft stats
Ransomware stats










Phones are not safe, computers the same, only way to be safe is Not to use any online connection, get a home land line without internet access!
Buy go landline did not take my right away from using the internet I really love the internet would love to keep it but I swear to God if it continues and nothing’s getting done about it everybody needs to just go landline and just do what we used to do that is Ghost satellite with a computer at home we never had all these security hacks no matter what we did where we went on the internet I cannot recall anyone saying they were hacked
… plus a field, a cow, and a gun!
Cheers,
Stephen
what needs to allow the modify system settings on my Moto g stylus phone
Hi, Kellie,
Look under Settings -> Privacy -> Permissions Manager and then select each of the apps you want to manage the permissions for.
Cheers,
Stephen
Oh I see, it’s an example, lol I said, hey, they got it wrong…
I forgot to say, I can no longer use my phone number in addresses nor sign in, my phone gets burning out but recently it’s cold as ice, both temps around same time during night and morning, I called my old android Motorola number when I saw my old android number in google account, a guy answered but I still have the phone…he swore he’d erase all and stop, December last, I saw it again and called, he was astounded at the situation continuing, yeah right, I do not know him, but he the same guy, I have all these settings seem like for the handicapped or blind, and two sets of settings and they are still using my name and I can’t delete any apps from two years ago up to now because it just won’t delete and when I look up an app, it adds to the list even though not installed or purchased, so much apple didn’t help if they don’t change these comments as they have my emails and my lock sim in apple to sim cArd and my phone account to cellular instead of AT&T read at top on left, they get everything I download and got a google account with Spanish and found one with the phone number in addresses from Japan
The whole article was very informative. I plan on implementing most if not all the suggestions. Now I won’t feel like taking my phone for a drive and throwing it out the window when i think it’s fighting with me. Thank God for tech savvy people!
Basically, no apps need access to anything? Could u clarify ‘ not allow ‘ apps to have access to anything by showing an example if an app u would allow various permissions and access ?
Thank u
I’m so confused
I keep denying all permissions on my camera app and they keep being turned on in by my phone it keeps collecting data and cache even when not being used as a camera it feels like it is spying o me
Sounds like it’s spying on you! Does your battery run low fairly quickly? Does your phone get hot or has it slowed down a lot?
My life its so miserable because I feel someone controls me illegally and monitoring all of my apps I use. Please people help me because its gives me an anxiety and sometimes its so hard for me to live happy and meaningful life. I don’t believe we live in free country we live controll country where there is no privacy exist
same problem and it not fair that there isn’t a app or program that can make sure u have secure device. help me aswell as have no idea why people are doing this to me ad is make me feel really ill. I Don’t know what to do…
THANKS
The game War Wings on google play asks for complete permissions on what seems like everything on my phone. I un installed it after trying it out. Really a great game, but like so many like mine craft that my kids like, they all want permissions. How save do you think it is for these 2 games?
It is so difficult to work out which companies are honorouble and which just want access to your device for malicious purposes. Even if you find a small app that you like, there is no guarantee that the company won’t be bought out by less scrupulous operators. The best advice that I can give is to block all permissions except in the very few cases, where you trust the app provider completely.
Sorry if this is a duplicate message to your very informative article Stephen. You say in the Article “and avoid following links in web pages while using your phone” which is almost impossible. And to send a photo in a text message you have to give the app permission 2 access your storage . So how do I trust clicking on the link to go to the nordvpn page? LOL but great article regardless. Thank you for the help
Do we actually need any apps?
Would it not be safer just to set up bookmarks to the websites that you wish to have access to, as I believe that apps are just bookmarks packaged up to get onto our computer devices.
Perhaps, we the customers, should demand that our devices are delivered to us completely locked down for privacy, so that we can open up permissions, as we feel fit. I am sure many people do not realise how ‘open’ their devices actually are. Maybe we should all lobby the Information Conmissioner’s Office for the right to complete privacy in all areas of technology, not just data.