Ransomware, once merely a buzzword, has become a significant threat to businesses, governments, and individuals worldwide. This malicious software encrypts a victim’s file system, often leading to irreversible data loss and substantial financial repercussions. The recent escalation in both the frequency and severity of ransomware attacks is alarming.
In 2023, reports indicated a staggering 1,900 ransomware attacks in just the US, Germany, France, and the UK, with the US experiencing 43% of all global attacks, as noted by Malwarebytes. The financial stakes in these cybercrimes have soared, with average enterprise ransom payments exceeding $100,000 and average demands reaching around $5.3 million.
The pervasiveness of ransomware across various industries is also notable. An alarming 66% of organizations reported being victims of ransomware attacks in the last year. The healthcare sector, in particular, has been hard hit, facing an average cost of $10.93 million per data breach.
High-profile attacks on entities like CNA Financial, Colonial Pipeline, and JBS USA, some of which resulted in multimillion-dollar ransoms, highlight the severity of these cyberattacks. The emergence of ransomware groups such as CL0P, exploiting zero-day vulnerabilities, signals a shift towards more aggressive ransomware strategies.
We’ve compiled over 35 vital ransomware facts, figures, and trends, complemented by expert predictions from the industry, to give a thorough perspective on this evolving cybersecurity threat.
See also: Best ransomware protection tools
Ransomware attacks increasingly also target backup repositories
According to the 2022 report from VEEAM, 95% of ransomware attacks also attempted to infect backup repositories. This underscores the dangerous nature of this growing threat and highlights how businesses may find themselves in trouble unless they have properly segregated off-site backups in place – preferably with multiple backups in multiple locations.
Hackers can successfully penetrate 93% of corporate networks
According to a December 2021 study by Positive Technologies, companies have a long way to go before they are adequately protected against hacking and ransomware attacks. According to their research, a whopping 93% of corporate networks can successfully be penetrated by hackers, allowing them to deploy ransomware, trojans, spyware, or other malicious exploits.
Only 50% of US SMBs have cybersecurity
Perhaps unbelievably, half of US small and midsize businesses have no cybersecurity in place according to a 2022 study by UpCity. This reveals that startups and SMBs are at extreme risk of ransomware attacks, and must put cybersecurity at the top of their agenda if they want to avoid losing valuable intellectual property, customer data, and other company information necessary for carrying out day-to-day.
When data loss meets dollars
Given the whole purpose of ransomware is to extract money from victims, total loss values are often the numbers people care about the most. Between 2018 and 2022, an increasingly large number of businesses, governments, and individuals faced huge losses thanks to these types of virus attacks.
In 2020, CWT, a travel-management company shelled out $4.5 million to hackers holding its data for ransom. While this represents a particularly huge payout, it’s still less than half of the attacker’s initial demand of $10 million. Additionally, the average ransom demand has increased significantly, with attackers asking for $50 million from computer giant Acer in 2021.
These past few years have seen attackers move away from targeting individuals. Instead, it’s become common to target infrastructure, with local governments, hospitals, and universities around the world suddenly facing demands for huge amounts of money. Naturally, these institutions have huge incentive to pay, and while the FBI strongly advises against it, Thycotic’s 2021 State of Ransomware report found that around 83% of victims end up paying.
The highest-profile attack of 2021 was arguably the one on Colonial Pipeline. This provided over 40% of the East Coast’s fuel, but as the ransomware attack left the company unable to bill properly, it was forced to suspend operations temporarily. Even though the company paid a $4.4 million ransom, it took a long time to get everything back online, leading to fuel purchasing restrictions in 17 US states.
This isn’t the only instance of lengthy problems following an attack. In 2019, the Baltimore City government was crippled for over a month. Estimates put the cost to recover at over $18 million dollars, although the cybercriminal behind the malware only demanded $76,000 worth of Bitcoin. The attack reportedly impacted vaccine production, ATMs, airports, and hospitals.
While many chose not to pay the cost for ransomware (and indeed, most security professionals say paying is typically a bad idea anyway), those that do pay up often find their files remain encrypted. After all, placing trust in the good graces of criminals often leads to disappointment.
With current trends, loss values are likely to exceed $265 billion by 2031. Additionally, as well as walking off with more money from ransomware in recent years, cybercriminals also caused far more damage than ever before.
- In 2022, NVIDIA had around a terabyte of proprietary information encrypted by ransomware group LAPSUS$, which proceeded to release the data when no payment was made.
- More than 10 universities across the UK and Canada were compromised after attackers successfully hacked Blackbaud, a cloud computing provider frequently used by educational institutions. Despite claiming it had successfully repelled the attack, it was later revealed that Blackbaud simply paid the ransom.
- JBS, the world’s largest meat supplier, paid $11 million to regain access to confidential files. However, in the meantime, it was forced to halt operations, leading to shortages.
- Garmin, a major player in the tech space, suffered a severe breach that brought its GPS services offline for several days. In order to regain control, the company allegedly paid a $10 million ransom.
- Cyber attacks marred the start of the 2019-2020 academic school year for two American colleges. Regis University in Denver, Colorado, had its entire phone and internet services shut down after a late August cyber attack. Meanwhile, Monroe College in New York City had files locked down due to ransomware. The school did not reveal whether or not it paid the ransom. (Source: Inside Higher Ed)
- A ransomware attack against the New Orleans city government in early 2020 cost the city over $7 million dollars. Thankfully, the city carries cybersecurity insurance and received $3 million back—which may indicate the city was still underinsured. (Source: SC Magazine)
- The Baltimore City government was hit with a massive ransomware attack in 2019 that left it crippled for over a month, with a loss value of over $18 million. (Source: Baltimore Sun)
- New York City’s capital was hit with a ransomware attack in 2019 that took several key services offline. (Source: CNET)
- The city of Riviera Beach in Florida paid a $600,000 ransom in June 2019 to recover files following a ransomware attack. (Source: CBS News)
- Multiple healthcare providers were hit with ransomware in early 2019 and paid the ransom to retrieve files. One paid $75,000 to recover its encrypted files. (Source: Health IT Security)
- Ransomware remediation costs organizations more than $1.4 million on average. (Source: Sophos)
- Even in 2016, ransomware was costing businesses more than $75 billion per year. (Source: Datto)
- The FBI’s latest IC3 report (PDF) recorded over 3,700 reported instances of ransomware in 2021. Overall, $49 million was lost. However, this only accounts for the US, and many such incidents go completely unreported.
- In 2018, businesses lost around $8,500 per hour due to ransomware-induced downtime. (Source: Govtech)
- Ransomware infections more than doubled from 2020 to 2021. (Source: Symantec)
- Symantec also found enterprises accounted for 81% of all ransomware attacks in 2018. (Source: Symantec)
- British MSP businesses reported an average payment of $5,600 in 2020. (Source: Datto)
- In 2016, less than 40% of victims paid the ransom. This has risen to 46% in 2022. (Source: Malwarebytes, Sophos)
- As of 2020, only 38% of state and local government employees are trained in ransomware prevention. In fact, 65% of executives have been asked by hackers to assist them. (Source: IBM, Hitachi-ID)
- Albany County in New York was hit by three cyberattacks in the span of three weeks in late 2019, including a Christmas day attack on the Albany County Airport Authority (ACAA) that resulted in a five-figure ransomware payment by the ACAA. (Source: Times Union)
- After getting hit by the SamSam ransomware in March 2018, Atlanta, Georgia, has spent more than $5 million rebuilding its computer network, including spending nearly $3 million hiring emergency consultants and crisis managers. (Source: Statescoop)
- A Massachusetts school district paid $10,000 in Bitcoin after a ransomware attack in April 2018. (Source: Cyberscoop)
- In 2019, 96% of organizations that paid the ransom received a decryption tool from the hackers. (Source: Coveware)
- Decryption success depends on the type of virus. Dharma variants were often unreliable after paying the ransom, compared to GrandGrab TOR which almost always delivered a successful decryption tool after a ransom was paid. (Source: Coveware)
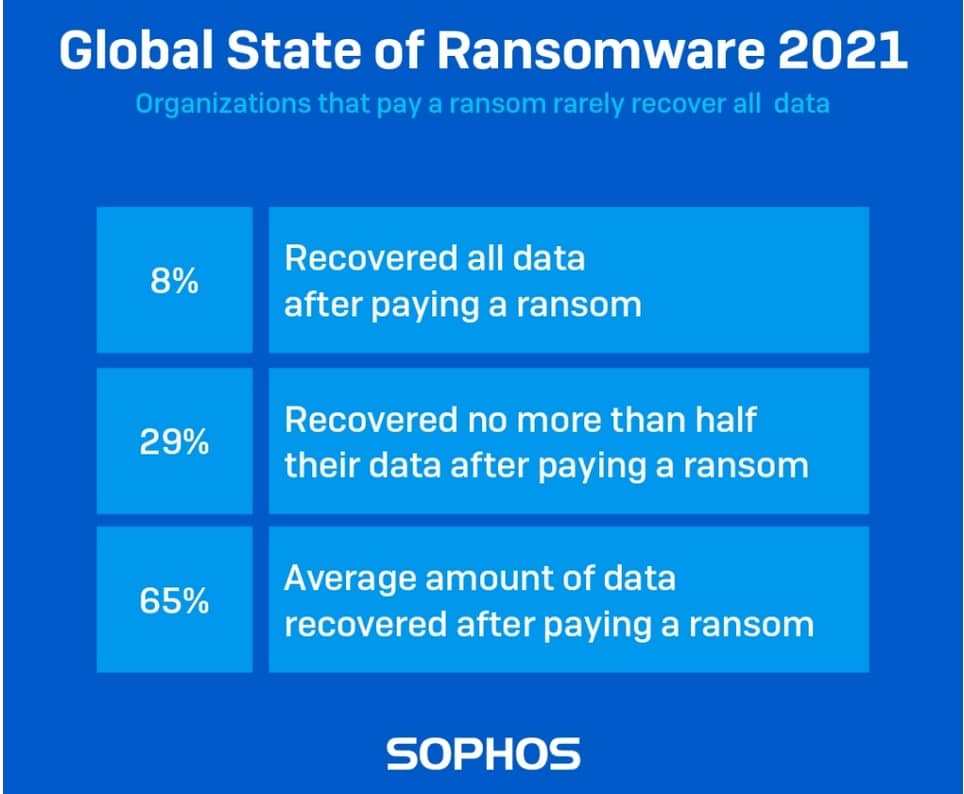
- In a 2021 survey by Sophos, just 4% of respondents who paid a ransom received their data back. The remaining victims who paid the ransom never recovered their data. (Source: Sophos)
- Bitcoin was the primary method of payment for ransomware. Around 98% of payments were made in Bitcoin. (Source: Coveware)
- The US Treasury has linked more than $5 billion of Bitcoin transactions to ransomware.
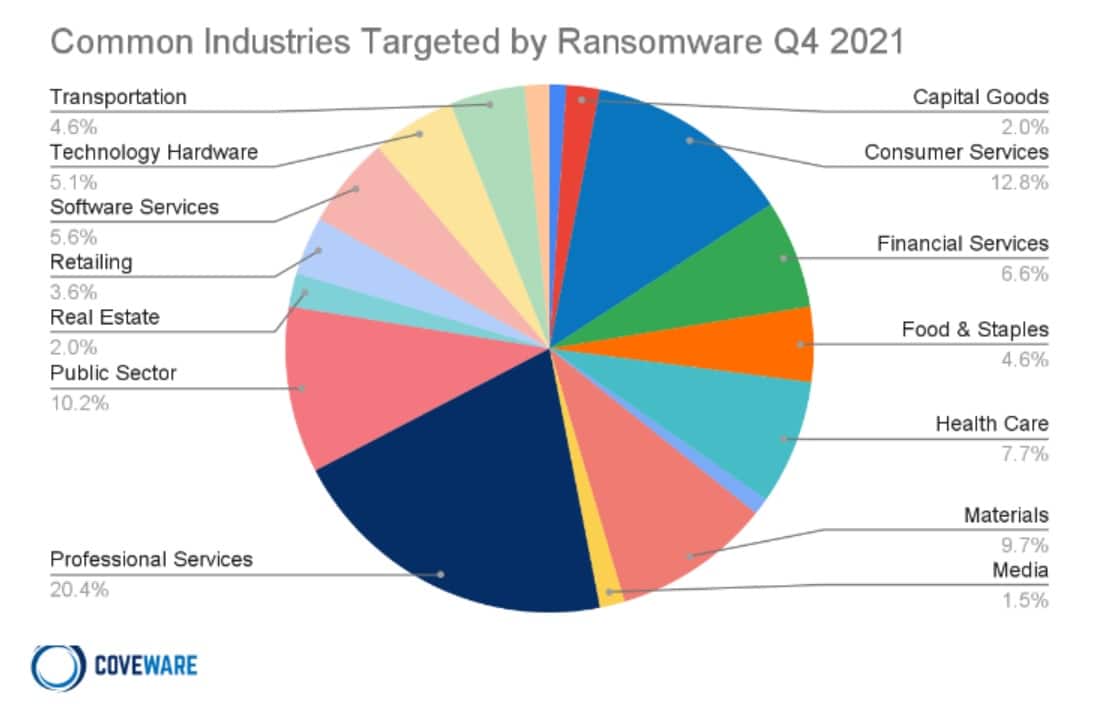
- Companies providing professional services are still the most likely to be targeted, although consumer services and public sector organizations are becoming more popular targets. (Source: Coveware)
Ransomware continues to grow, hitting consumers and businesses hard
The hard truth about ransomware is that knowing more about the threat doesn’t easily translate to a decreased impact. FedEx is a good example of this. Despite knowledge of the threat for years now, the company saw a $300 million loss in 2017 due to these crippling virus attacks. The loss was not a result of paying the ransom but primarily for the cost of disaster recovery and system downtimes. The company’s lack of cyber insurance highlights the fact that many individuals and even large, multinational businesses have yet to fully grasp the threat.
As for readiness for ransomware and other cyber threats, Sophos reports that local governments are among the least likely organizations to be able to stop their data from being encrypted. Additionally, these are the slowest to recover, with 40% needing a month or more to bounce back. Meanwhile, media, leisure, and entertainment companies are the most prepared, but still only avoided encryption a little over half of the time.
Nevertheless, as more reports roll in, it’s clear that ransomware is now the preferred medium of choice for cybercriminals. As 2022 continues to progress, we’re likely to see reports from major players indicating that year-over-year growth in virus-related ransom threats is increasing at an incredible pace.
That being said, here are some of the ways ransomware hit hard and fast in the past few years.
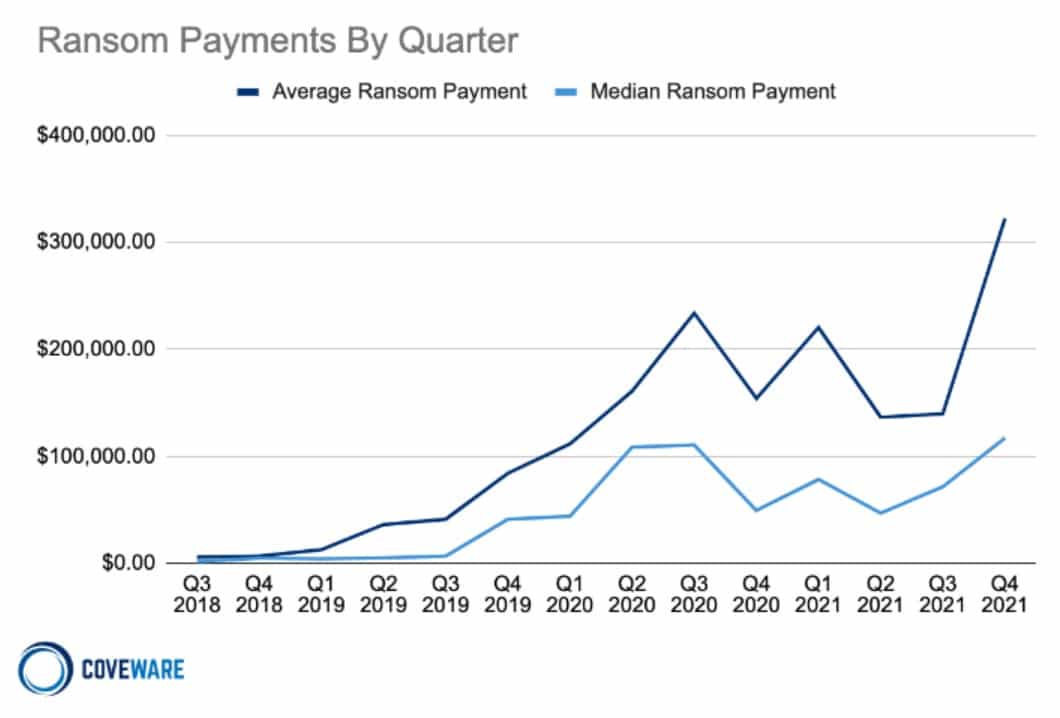
- A Q4 2021 report from Coveware found that ransomware payments are at an all time high, possibly due to a larger number of victims paying up. This itself may be because around 90% of organizations hit had ransomware insurance (Source: Coveware)
- Coveware also found that attackers are increasingly permanently destroying data, rather than targeting backups or critical parts of a company’s infrastructure. In some cases, this happened even after a ransom was paid. (Source: Coveware)
- Most users who recover their data do so in ways other than by paying the ransom. (Source: Datto)
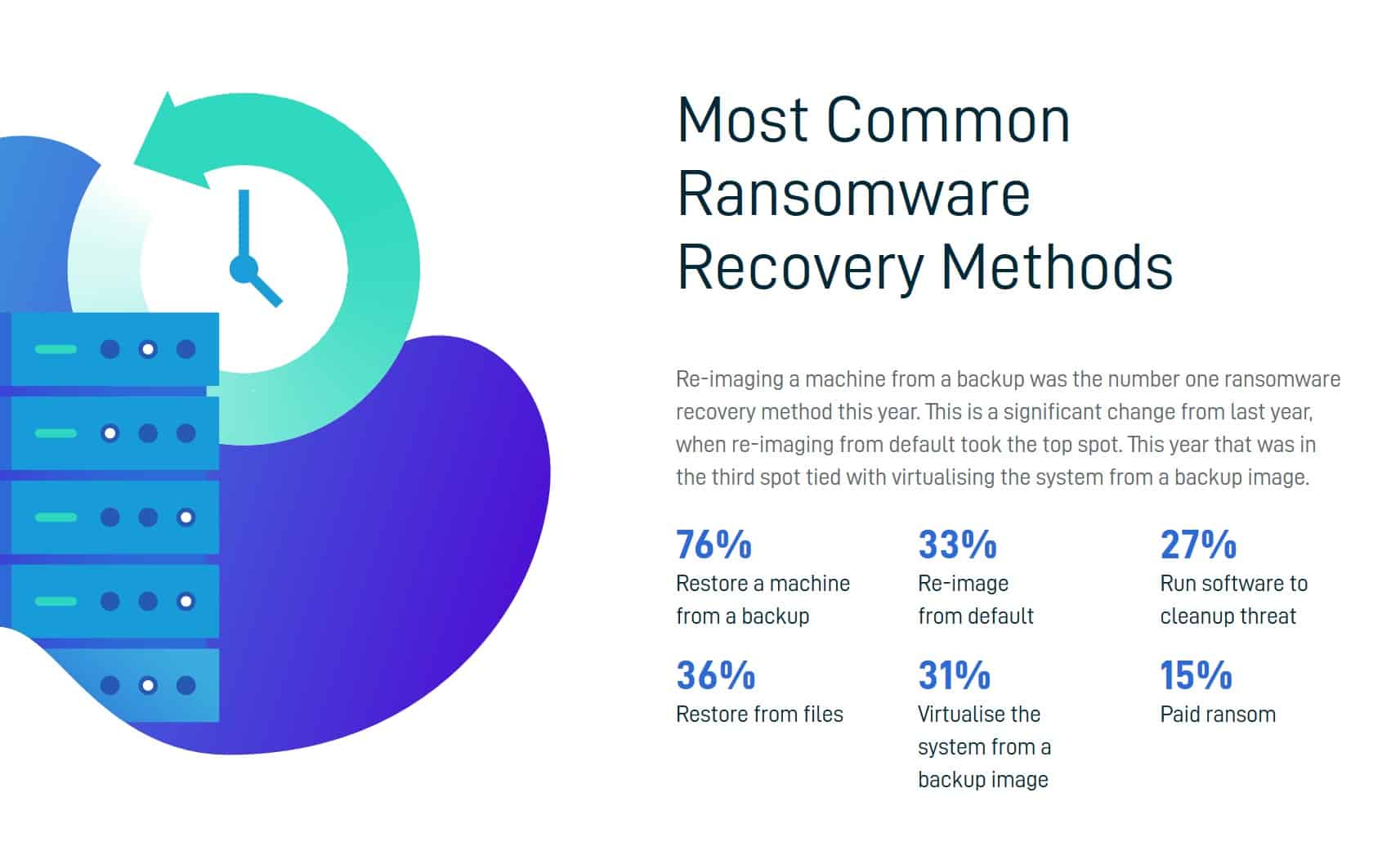
Source: Datto - According to a 2020 Ransomware Resiliency Report by NinjaOne, managed service providers (MSPs) lose far more clients following a ransomware attack than they anticipate. In fact, 57% lost 11-20% of their client base after a ransomware attack; 13% of businesses lost over 50% of their clients. Conversely, around 35% of MSPs expected to lose no more than 10% of their clients after a ransomware attack. (Source: NinjaOne)
- Around 40% of MSPs and IT professionals believe their organization could not withstand $500,000 or more in damage related to a ransomware attack. Considering 52% of businesses that suffered from a ransomware attack reported damages in excess of $500,000, many businesses could experience irreparable damage should an attack occur. (Source: NinjaOne)
- NinjaRMM reports that half of all MSPs believe they can sustain up to 2 days of downtime before losing clients, yet most affected clients actually experienced 3 to 14 days of downtime. This prolonged period of downtime could be a major factor in client churn rate but does indicate that many MSPs overestimate how quickly they’ll lose clients when downtime occurs. (Source: NinjaOne)
Ransomware predictions: 2024 and beyond
Unfortunately, ransomware isn’t going anywhere fast. Cybercriminals have learned just how lucrative encrypting data can be, especially thanks to the influx of Ransomware-as-a-Service programs that require no expertise to use. Other forms of security threats still exist, data breaches in particular, but criminals who want to extract an easy buck are regularly turning to readily-available ransomware packages.
So what can we expect in the coming years? Here are a few predictions.
- SC Media predicts that the US government will focus on cybersecurity training to combat increasingly common ransomware attacks.
- Cybersecurity Ventures predicts ransomware will cost $10.5 trillion annually by 2025, and that an attack will take place every 2 seconds by 2031. (Source: Cybersecurity Ventures)
- Security predicts a widespread shift to businesses adopting zero trust models. (Source: Security)
- A 2022 report from Trellix showed that ransomware demands grew by 3900% in 2 years, increasing from $5,000 in 2018 to $200,000 in 2020. Trellix expects the average cost of ransomware to increase further as attacks become more sophisticated. (Source: Trellix)
- Check Point predicts an increase in the number of supply-chain attacks. (Source: Check Point)
- According to RSA Security, attackers will increasingly use IoT devices to target users with ransomware. (Source: RSA Security)
See also: Cybersecurity and cybercrime statistics
FAQs about ransomware attacks
What is ransomware?
Ransomware is malicious software that can lock your files or entire computer, rendering them inaccessible. The attacker then demands payment (typically in cryptocurrencies like Bitcoin) to unlock your files or computer.
These attacks can impact individuals, businesses, or even government organizations, resulting in financial losses, disruptions, and damage to their reputation. Ransomware often infiltrates your computer via deceptive emails, dubious downloads, or by tricking you into clicking on a harmful link.
There are several types of ransomware:
- Encrypting ransomware: This variety encrypts your files, making them inaccessible until you receive a unique decryption key. Examples include WannaCry, Locky, and CryptoLocker.
- Locker ransomware: This type completely locks you out of your computer or device. A message typically appears on your screen with instructions on how to pay the ransom. An example is Reveton.
- Scareware: This type poses as a security application, claiming that your computer is infected and demanding payment to resolve the issue. Although it may not lock your files, it can be quite alarming and perplexing.
As ransomware attacks have become increasingly frequent and sophisticated, it’s essential to implement robust security measures to protect your computer and minimize the risk of an attack.
How do people get infected with ransomware?
There are a few ways that people can get infected with ransomware. One way is by clicking on a malicious email attachment. Another way is by visiting an infected website. It is also possible to get infected by downloading a malicious file from a peer-to-peer network or by installing a pirated software program that contains ransomware.
What type of data is at risk in a ransomware attack?
In a ransomware attack, any type of personal data can be at risk. This includes things like photos, documents, and even financial information.
Should I pay the ransom if my files or systems are encrypted by ransomware?
Paying the ransom if your files or systems are encrypted by ransomware is generally not recommended for several reasons:
- No guarantee of decryption: Paying the ransom does not guarantee that you will receive a decryption key or that the key provided will successfully decrypt your files. Some ransomware operators may not honor their promises, leaving you without your data even after payment.
- Encourages criminal activity: Paying the ransom financially supports the cybercriminals behind the ransomware attack, which encourages them to continue their operations and target more victims.
- Future targeting: If you pay the ransom, attackers may consider you an easy target and attempt to infect your systems again in the future.
- Funding other illegal activities: The money paid as ransom could be used to fund other criminal activities, such as identity theft, drug trafficking, or other forms of cybercrime.
- No guarantee of prevention: Even if you pay the ransom and recover your files, there is no guarantee that the attackers haven’t left other malware or backdoors in your system, which could be used for future attacks.
Instead of paying the ransom, consider the following alternatives:
- Restore from backups: If you have a recent backup of your data, you can restore your files without having to pay the ransom.
- Seek professional help: Consult with cybersecurity professionals who may be able to assist you in removing the ransomware or recovering your files.
- Check for decryption tools: Some security organizations and researchers release free decryption tools for specific ransomware variants. Search online to see if a tool is available for the ransomware affecting your system.
- Report the incident: Report the ransomware attack to your local law enforcement agency or relevant cybersecurity organizations, which may be able to provide guidance or assistance.
- Strengthen security: After recovering from a ransomware attack, implement stronger security measures to prevent future incidents. This includes updating software, using strong and unique passwords, conducting regular backups, and providing cybersecurity training for employees.
Which industries are the most targeted by ransomware attacks?
Several industries face the risk of ransomware attacks, but certain ones are more frequently targeted due to their potential for financial gain or disruption. Healthcare, finance, government, education, and manufacturing are among the sectors that are often targeted. These industries typically hold valuable or sensitive data, making them an attractive target for cybercriminals who seek to extort money by encrypting the data and demanding a ransom for its release.