You may want to start taking a closer look at your confirmation emails. It appears some websites have failed to fully secure their sign-up forms, making it possible for scammers to abuse websites with weak security as a gateway to completely bypass email spam filters. The result? Phishing links within confirmation emails from legitimate websites that are more likely to result in a successful phishing attempt.
Validation email phishing
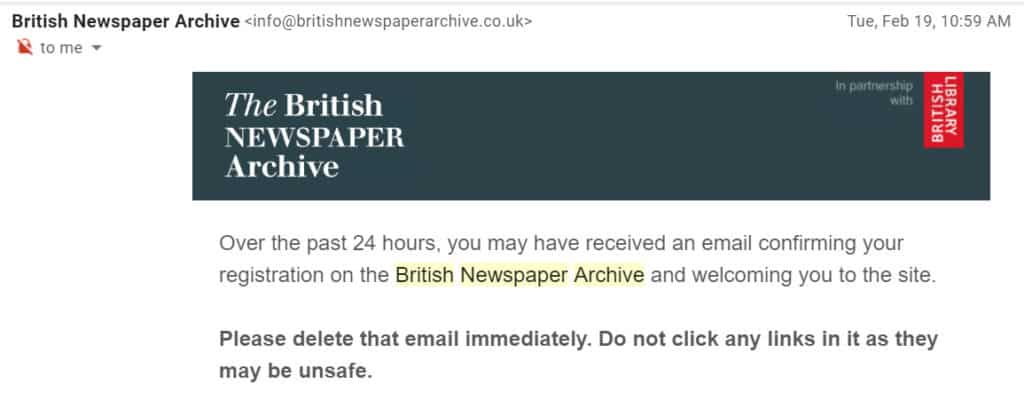
This rather clever phishing attempt came to my attention after we received a validation email from the British Newspaper Archive (and has since by observed by others, including antivirus software developer Dr. Web). To note, the British Newspaper Archive is a fully legitimate website with no spam or scam operations running that we know of. We’ve never heard of the website before, so their account validation email was suspicious.
The first thing we did was what we recommend for all suspected spam emails: We checked the sender’s email address. In this case, everything checked out.
The next thing we checked was the information provided within the email body. Here’s where the scam revealed itself.
Many websites require you to submit your first and last name in a sign-up form and then send you a confirmation or validation email that often says, in a friendly manner, “Dear So-And-So,” with information for how to finalize the sign-up process.
Comparitech found that a scammer can use a legitimate website’s account sign-up form to send spam or scam links on the scammer’s behalf. They register with the target’s email address and put a phishing link in the signup form that will be included in the confirmation email.
In this case, the scammer used my email address to sign up for an account, but instead of a first name, inserted a few choice words and a clickable hyperlink:
Generally speaking, there’s nothing that can stop someone from using your email to sign up for any website. The point of a confirmation email, in fact, is to serve as a security measure to ensure not just anyone can use your email to create an account. In this manner, simply using someone’s email address to create fake accounts serves no real purpose unless the scammer also has access to your email account, which itself would indicate a much larger problem.
In the above example, the username, which reads “Caras pron vid” (pron = porn and vid = video), is somewhat ludicrous. But what’s troubling is the fact that this scammer was able to insert a working hyperlink in a legitimate website’s account sign-up form, which was then able to make its way to my inbox.
Why is this a problem?
This particular scam appears to have taken advantage of poor web form security, allowing the scammer to insert a suspicious link in the form and completely bypass normal email spam filters. Because everything else about the email is legitimate, email spam filters would let the phishing attempts of this nature slide right through—as this one did.
The link sent to me did not appear to be as malicious as it could have been. Yet it’s conceivable scammers could just as easily send a link that immediately executes a malware and ransomware file download just using this method. Additionally, because the email comes from an official source and soars right past spam filters, which most web users now trust almost implicitly, a well-coordinated phishing attack using a website’s poorly-secured sign-up form could result in a higher-than-average response rate than most phishing email attempts.
How did the British News Archive respond?
Following the phishing attack, we sent BNA an email using their sites contact form regarding the issue. We sent a follow-up email a month later as well but did not receive a response to either contact attempt.
That said, BNA became aware of the issue less than 24 hours after it occurred (February 18, 2019). The website sent an email to everyone impacted on February 19:
Although we received no responses to our inquiry, the website fixed its sign-up security issue in a timely manner following the event.
How can users avoid account validation email phishing
At present, there’s no effective method users can employ to stop these emails from bypassing email spam filter. Although spam filters do check the email content for suspicious words, phrases, and links, one of the primary triggers is the email address itself. If the email address is coming from a whitelisted site or appears fully legitimate, it’s unlikely to be stopped by a spam filter even with a suspicious link in the content of the email.
Your best option is to do the following:
- Check to make sure the website is legitimate. Do not click any links in the confirmation email. Instead, type in the website name in Google search to verify its existence.
- Check the form name that was submitted and is given in the email. If it contains a link next to the introduction (“Dear X [hyperlink]), it’s probably a phishing attempt.
- Do NOT click on the link. Instead, contact the website in question to let them know you did not sign up to create the account yourself, and give the supposed username that was listed to sign up with your email address
Thankfully, most websites sanitize their sign-up forms, so this type of phishing attempt is rare. However, if scammers can find even one website with weak web security, it’s easy for them to create a script that can exploit this oversight and generate a mass phishing attacking that can target hundreds or thousands of people.
Related: How cybercriminals run phishing campaigns
How can websites secure their sign-up forms?
From a technical standpoint, what’s happening here is a web form that is not properly sanitizing and filtering what users submit. It’s also allowing the form to encode HTML before it gets sent to the user via email, which is why the link appears as a clickable hyperlink.
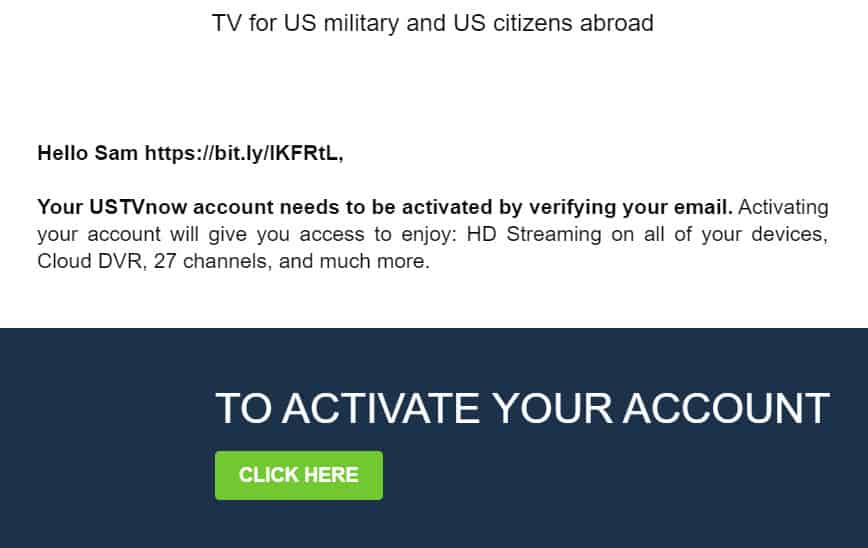
After receiving this phishing attempt, we checked the sign-up form security of several other websites. We located a similar issue on the website of the over-the-stop TV streaming service USTVnow. At that time, the site failed to properly sanitize its sign-up form and allowed users to input an HTTP link into the form:
We contacted USTVnow twice following our discovery. Our first attempt was immediately after discovering the security weakness, the second time was slightly over a month later. Neither attempt received a response related to the security issue, but USTVnow fixed the issue in the intervening month.
In USTVNow’s case, the link wasn’t encoded in HTML as a hyperlink, reducing the risk, at least marginally.
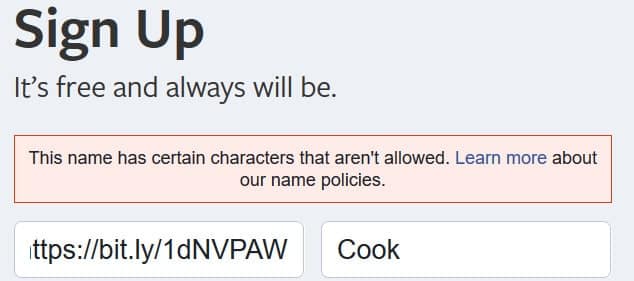
Websites can eliminate this issue by sanitizing their web form PHP to eliminate any unexpected characters, or at a minimum, by disallowing web addresses. Most top-level websites, such as Google, Yahoo, and Facebook, give a warning immediately if disallowed characters are entered into the sign-up form:
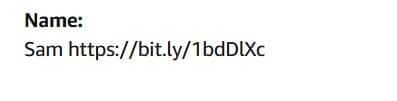
It also appears some major websites, like Amazon, let you insert non-standard entries in the sign-up form, including hyperlinks, but don’t include any form details in the confirmation email. While unusual, this at least still renders the spam attempt useless. The link will only appear in your account details on Amazon, and only as text:
Any website owner or development team should strongly consider a quick check of their account sign-up form PHP code to ensure it is properly sanitized to disallow hyperlinking.
See also:
Common phishing scams
50+ phishing statistics