Phishing attacks use social engineering in emails and messages to persuade people to hand over information such as passwords or financial information, or to get them to perform certain tasks such as downloading malware or completing a wire transfer. Phishing schemes continue to become more sophisticated with targeted attacks (spear phishing) posing a threat to many businesses.
While spam filters catch many phishing emails, newer and more sophisticated ones get through. There is evidence that most people are aware of the existence of phishing attacks. Indeed, many companies provide training and simulations to teach employees how to spot malicious emails and messages.
That said, scammers still have success with this form of cyber attack and its use remains prevalent. Plus, cybercriminals are changing tactics to get around the anti-phishing measures in place.
Here’s a rundown of phishing statistics and facts for 2023:
1. Phishing attacks are still extremely common
According to APWG’s Phishing Activity Trends Report for Q2 2023 phishing attacks are finally beginning to trend downward after years of growth. Despite this, we’re still seeing over 300,000 phishing attacks every quarter.

Additionally, for the first quarter of 2023, APWG saw more than 40,000 unique email subject lines every month. This shows that hackers are more likely than ever to tailor their approach rather than using the same template for every victim.
2. Loaders are the most popular attack avenue
Cofense’s Q3 2023 Intelligence Trends Review found that loaders remained the most common tool for phishing. Other popular avenues include infected PDF files, keyloggers, and remote access tools. This variance is interesting considering that just five years ago, almost 74 percent of phishing attacks involved credential phishing (stealing usernames and passwords).
These attacks can be difficult to stop as the emails typically show no signs of being malicious. Many originate from hijacked business email accounts, a tactic known as business email compromise or BEC. Plus, attackers often go a step further and host fake login pages (phishing sites). For example, these could end in “.windows.net,” making the site seem legitimate and the scam even more difficult to spot.
3. Spear phishing emails are the most popular targeted attack vector
According to Slashnext’s 2023 State of Phishing Report, the vast majority of all phishing attempts were targeted. Specifically, there was a 45 percent increase in spear-phishing, social engineering, and smishing attacks.
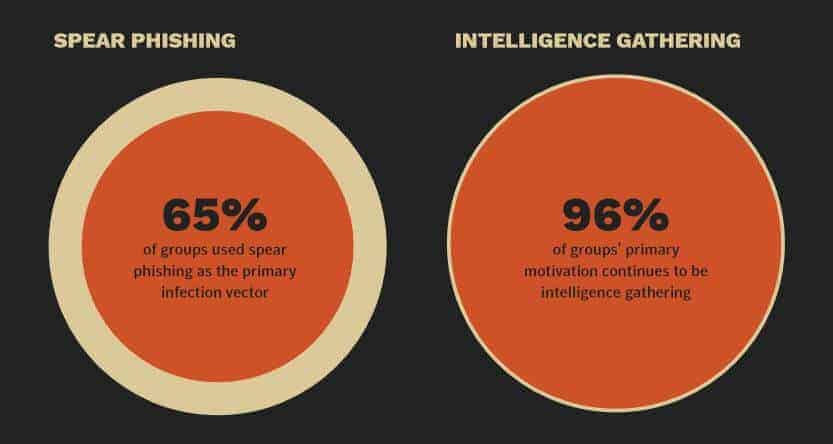
Unfortunately, this shows that little has changed on this front in the last few years since Symantec’s Internet Security Threat Report 2019 found spear-phishing emails to be used by almost two-thirds (65 percent) of all known groups carrying out targeted cyber attacks. The report also tells us that 96 percent of targeted attacks are carried out for the purpose of intelligence gathering.
4. Human intelligence is the best defense against phishing attacks
Stanford University’s The Psychology of Human Error report found that 88 percent of all data breaches are a result of human error. The World Economic Forum agrees, going as far to attribute error to 95 percent of all cybersecurity issues to this.
In its 2019 report, Cofense reiterates the importance of awareness training in thwarting phishing attempts. It cites an example in which a phishing attack on a major healthcare company was stopped within just 19 minutes. Users reported receiving suspicious emails and the security operations center was able to take swift action. Despite this newfound focus on training, however, a follow-up to Stanford’s study found that roughly one-quarter of all employees have fallen victim to a phishing attack in the last year.
5. Phishing attacks are getting more sophisticated
Attackers often use trusted domains to trick people into believing their links are safe. Previously, many scammers used Amazon AWS to host their phishing sites but nowadays, the #1 threat is shady Bing redirect URLs. Victims are often directed towards Google, LinkedIn, Baidu, or Dropbox instead, with AWS falling out of the top 10 entirely in Q3 2023.
Cofense also confirmed Symantec’s findings regarding attackers’ ability to quickly capitalize on current events. They corroborated that in 2020, there was an influx of COVID-19 related phishing, often claiming to provide financial assistance for impacted citizens.
6. ChatGPT is a huge advantage for scammers
Zscaler’s ThreatLabs 2023 Phishing Report found that AI tools like ChatGPT could create fake login pages with minimal coding expertise or input from the user. It further suggests that this service could be used to create polymorphic malware or other malicious code. Slashnext even found instances of scammers combining ChatGPT with Google Translate to craft more believable phishing emails.
The flipside of this is that we can also use AI-powered tools to detect phishing links. There’s still some way to go on this, though: Securelist found that ChatGPT-3 could detect phishing links 87.2 percent of the time, but it had a 23.2 percent false-positive rate, which makes it effectively useless without further improvement.
7. There are many different types of target
Although credential phishing is no longer the most popular tactic, it remains far more common than we’d like. The APWG report sheds some light on the types of credentials attackers are after.

There’s been a marked change lately. Social media accounts are now twice as popular a target as they were in 2022, while attempts to get shipping info have dropped by a third. We’re also seeing a substantial number of phishing emails targeting gaming platforms and social media, perhaps as these accounts are often linked together.
8. Smaller organizations see a higher rate of malicious emails
Symantec combines numbers for various types of email threats, including phishing, email malware, and spam, and reports that employees in smaller organizations are more likely to receive those types of threats. For example, for an organization with 1–250 employees, roughly one in 323 emails will be malicious. For an organization of 1001–1500 employees, the rate is far lower with one in 823 emails being malicious.
9. Malicious emails are most likely to hit mining companies
Symantec also breaks down malicious email rates by industry. Mining tops the list with one in 258 emails being malicious. This is closely followed by agriculture, forestry, and fishing (one in 302) and public administration (also one in 302). Manufacturing, wholesale trade, and construction follow as the next most heavily targeted industries.
10. Sweden is the biggest target in Europe
According to Proofpoint’s 2023 State of the Phish, 94 percent of Swedish companies were at risk of phishing attacks. Despite this threat, fewer than one fifth of Swedish businesses provide phishing-awareness training.
11. Many data breaches stem from phishing attacks
Verizon’s 2022 Data Breach Investigation Report found that phishing is one of the top threat action varieties in data breaches, with 30 percent of data breaches involving phishing. In its 2023 report, this trend continued, with stolen credentials being used in around 40 percent of all social engineering incidents.
12. Knowledge of phishing terms varies among generations
Proofpoint notes that while awareness of terms like “malware” and “ransomware” are increasing year over year, they’re still fairly poorly understood. Only around a third of respondents could actually define what these words meant.
13. Sextortion is a common tactic in phishing campaigns
Phishing schemes based on sextortion scams represent a growing issue. These emails are typically generic, but attackers prey on human emotion by using fear and panic to encourage victims to submit a ransom payment. Scammers usually request payment in bitcoin or another cryptocurrency to help avoid detection.
The Internet Crime Complaint Center (IC3) 2021 report revealed that there were over 18,000 reports of sextortion that year, with total losses amounting to more than $13.5 million.
14.There is no such thing as a 100% safe link or filetype
Cofense’s research indicates that infected .pdf files account for almost 50 percent of phishing email attachments. However, .html and .htm files make up another 30 percent. In fact, a non-trivial percentage of infected files use the seemingly-harmless .mp3 and .tif formats, normally used for music and images.
Additionally, even if the email’s attachment is “safe”, its contents may not be. It’s increasingly common for attackers to embed images of QR codes that lead to malicious websites as these are often missed by anti-spam/phishing tools.
15. SEGs are far from free of phishing attacks
Many users wrongly believe that using a Secure Email Gateway (SEG) protects them from phishing attacks. Unfortunately, that’s far from the truth. In 2023, Cofense saw a nearly 45 percent increase in the number of indicators of compromise vs the year prior.
Cofense cites the main reason being that even the most progressive automated detection can’t keep up with advances in the sophistication of phishing techniques. For instance, we’re seeing many attackers embed malicious QR codes, abuse Google’s amp URLs to redirect to their sites, and adopt less common file types. Plus, as with all systems, SEGs are prone to configuration errors.
16. Malicious attachments exploiting CVE-2017-11882 remain common
CVE-2017-11882 is a remote code execution vulnerability that exists in Microsoft Office software. This vulnerability was identified in 2017 and subsequent updates patch the flaw. Despite this, according to Cofense, this vulnerability remains the top non-Emotet malware delivery method.
Vulnerabilities like this remain a target for attackers as some companies are slow to update their software. However, as users catch up and patch the CVE-2017-11882 vulnerability, we will likely see associated attacks diminish.
17. Some phishing attack payloads are location-aware
If you think your location doesn’t matter when it comes to cyberattacks, you may be wrong. According to Cofense, the geolocation of a user (as per their IP address) often determines how a payload behaves once delivered. For example, the content could be benign in one country but malicious in another.
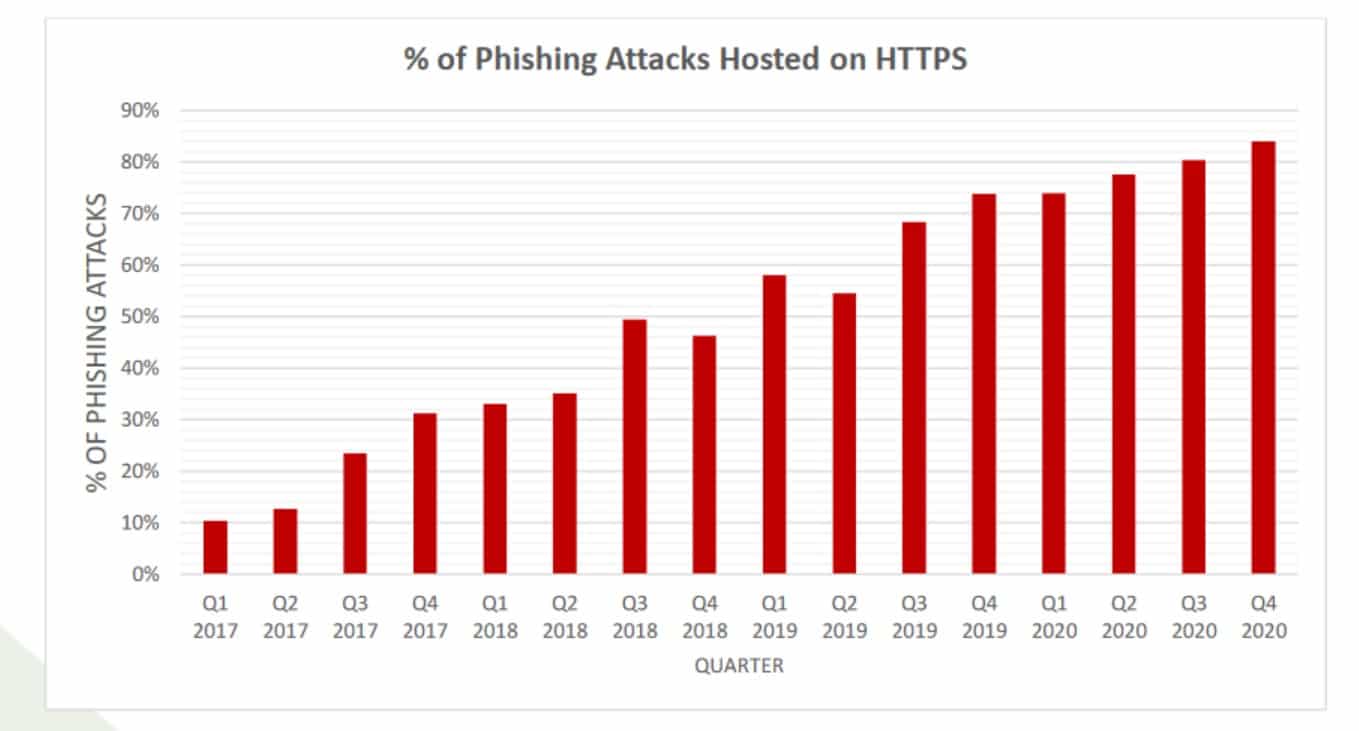
18. SSL is no longer an indicator of a safe site.
For many years, one of the primary tips for avoiding phishing sites has been to examine URLs carefully and avoid sites that don’t have an SSL certificate. “HTTPS” in the URL (versus “HTTP”) signifies that a site has an SSL certificate and is protected by the HTTPS encryption protocol.
However, this is no longer a good tactic for recognizing dubious sites. As reported by APWG, a whopping 84 percent of phishing sites examined in Q4 of 2020 used SSL. This continues the long-running trend of increasing around 3% every quarter, though unfortunately, later reports no longer provide this information.
19. Gift cards are still a popular form of payment in BEC attacks
The APWG also provided insight into how attackers request payment. In BEC attacks, in particular, 34 percent of attackers requested they be paid in gift cards in Q2 2023.
However, gift cards are less popular than they have been. Instead, we’re seeing more instances (around 44 percent) of advance fee fraud, where people are asked for upfront payment for non-existent goods or services.
20. A custom phishing page costs $3–12
On the attacker side, phishing schemes are part of a large underground industry. Symantec shows us some facts and figures from the dark web, such as the going rate for a phishing webpage is $3–12.

It doesn’t stop there. Securelist found that hackers are selling template phishing kits that can be tailored to specific targets for as little as $40.
21. 67% of phishing attempts have blank subject lines
According to a report from AtlasVPN, almost 70% of all phishing email attempts contain an empty subject line. Some of the most commonly used subject lines cybercriminals use are ‘Fax Delivery Report’ (9%), ‘Business Proposal Request’ (6%), ‘Request’ (4%), and ‘Meeting’ (4%).
22. Almost 900 fake Amazon sites were in use on Amazon prime Day 2022
AtlasVPN reported a surge in retail websites impersonating Amazon on one of the year’s busiest shopping days. In the 90 days up to July 12, 2022, 1,633 fake sites were detected, with 897 spoof Amazon sites active on Prime Day.
Phishing projections for 2024 and beyond
Based on phishing statistics from the past year, we can expect to see a couple of key trends as we move through 2024 and into 2025:
- Attacks will increase in sophistication. Kaspersky believes that the rapid proliferation of AI-powered tools will lead to more effective, convincing spear-phishing attempts.
- We’ll see the rise of another new malware family: Qakbot was taken down by the FBI, but Cofense believes it won’t be long before a similarly-dangerous replacement is created.
- Hackers will turn to less-common languages in a bid to avoid detection: Securelist notes the emerging threat of programming languages like Golang and Rust being used instead of more traditional alternatives.
We can’t be certain what the future holds, but we can say with some confidence that phishing will remain a significant threat to both individuals and businesses in the immediate future.
FAQs about phishing
How can I tell if an email is fake?
There are some telltale signs that an email isn’t legit. These include some of the following:
- The subject line is blank
- The sender’s name doesn’t match their email address.
- The email asks you for personally identifying information, such as a username and password.
- Poor spelling and grammar are used in the body text.
What should I do if I handed over my login details?
If the authenticity of an email has fooled you, you should change your account password immediately. If you’ve accidentally provided online banking details to an attacker, you should contact your bank asap to avoid money being stolen. For social media phishing, the attacker may have sent messages to your contacts, so it’s worth letting them know your account has been hacked and to get in touch via another channel (phone, text, WhatsApp).
What are the most common types of phishing attacks?
Some common types of phishing attacks include:
- Clone phishing: A phishing attack where the attacker creates a replica of a legitimate website or email to trick users into entering their personal information.
- Spear phishing: A type of phishing attack that is targeted at a specific individual or organization. The attacker will often create a fake email that appears to come from a legitimate source, such as a company or organization with which the victim is familiar.
- Phishing with malware: A phishing attack where the attacker includes malicious software (malware) in the email or website to infect the victim’s computer.
- Vishing: This attack uses voice messages instead of email or websites. The attacker may call the victim and pretend to be from a legitimate organization, such as a bank, to trick them into revealing personal information.
Smishing: This phishing attack uses text messages instead of email or websites. The cybercriminal may send a text message that appears to be from a legitimate organization, such as a bank, to trick the victim into revealing information about themselves.
How can I report a phishing attack?
You can report phishing attacks to the Anti-Phishing Working Group (APWG) at www.antiphishing.org. This website also provides resources and information on phishing attacks and how to protect yourself from them.









Hello!
Thank you for the amazing compilation of the phishing facts, I have read the entire piece and I am ready to refer to it over and over again.