![]()
Ultrasonic tracking uses soundwaves that are picked up by device microphones to gather data, pinpoint a user’s location, and more. The methodology utilizes sounds that can’t be heard by humans, but can be detected by various devices, such as smartphones and tablets. This tracking can be used for a variety of purposes, including gathering information about individual users across devices and discovering your exact location to serve you targeted ads.
This technology can be useful for users, for example, by offering you real-time deals at the grocery store, but it does have its downfalls. There are obvious privacy concerns with apps accessing your device’s microphone, especially when they do so without explicit permission. Privacy enthusiasts are also concerned about the lack of a universal standard in the industry, and security concerns include the vulnerability of the technology to hacking attempts.
In this post, we explain exactly what ultrasonic tracking is, how it works, and what it’s used for. We’ll also discuss the privacy and security implications of ultrasonic tracking and steps you can take to block ultrasonic tracking.
What is ultrasonic tracking?
Ultrasonic sound waves are those with a frequency that is too high (generally above 18 kHz) to be audible to the human ear. For example, a dog whistle makes ultrasonic sounds—the dog can hear it, even though you can’t.
In the past several years, developers have found uses for these sounds in mobile device tracking. The sounds are encoded with data to create beacons which can be transmitted from any type of speaker and picked up by a listening device.
The beacons can be embedded within everyday sounds such as the audio of a TV or web advertisement. They can even be interlaced into the music that you hear in stores and elevators, or broadcast without any covering sounds.
By using your device’s microphone to listen for the beacons, phone manufacturers and app developers can put them to a range of uses. Some general applications for this technology are:
- Building user profiles: By detecting beacons embedded in web pages, advertisements, and even physical markers, advertisers can build a profile of your activities, both online and offline. They can track you across devices and even form links between you and other people. For example, your phone receiving a beacon from your friend’s smart TV would link you to that person.
- Device pairing: Ultrasonic beacons can create connections between devices, for example, between a phone and a Chromecast device.
- Proximity detection: The technology can detect your exact location, such as within a store. This can be used for self-guided museum tours or to receive custom deals when you pass through a specific section of a store.
- Data transmission: Ultrasonic tracking doesn’t rely on wifi or other connectivity, so it could have a wide range of potential uses in cases where connections are unavailable.
While some of these use cases benefit customers, others carry a privacy invasion risk.
Privacy concerns with ultrasonic tracking
The concept of your device tracking you using sounds can be unnerving, to say the least. Apps need to record sound in order to detect the ultrasonic beacons, so there’s a concern that other sounds (conversations, for example) may be recorded too.
Fortunately, access to your device’s microphone requires your express permission, usually requested when you first install the app in question. Unfortunately, many smartphone and other device users are too trusting and frequently grant permissions requested by newly-installed apps without giving it a second thought.
Since the apps only need the ultrasonic sounds, they can filter out the audible parts of recordings, minimizing privacy concerns. In theory, to protect user privacy, all apps using ultrasonic tracking should do this. Of course, it’s difficult to confirm whether or not they do practice audio filtering for user privacy. And even if they are filtering, depending on the type of filter being used, the full audio (including audible sounds) may need to be stored, albeit temporarily.
This activity is illegal in some parts of the world. In Australia, for example, it is unlawful “to overhear, record, monitor or listen to a private conversation” without the express consent of all parties. However, there’s no doubt the logistics of policing such laws would be difficult.
So where is the industry headed in terms of privacy? Here are three notable milestones that have helped shape its direction:
- March 2016: Federal Trade Commission (FTC) warnings were issued to advertisers using SilverPush ultrasonic tracking technology.
- October 2016: A study found that ultrasonic tracking could be used to override the privacy afforded the Tor browser.
- May 2017: A German study revealed hundreds of Android apps were using ultrasonic tracking technology, with many lacking clear privacy policies.
Let’s look at each of these events in more detail.
1. SilverPush FTC warnings
When ultrasonic tracking started to gain traction in 2016, one of the companies at the forefront of the trend was SilverPush, a provider of cross-device tracking software. SilverPush has operations in 12 countries and boasts an impressive client list, including Coca Cola, Unilever, KFC, and Levi’s.
The company developed its tracking technology in 2014 and appeared to gain market share in the following couple of years. One version of their software used smartphone microphones to listen for beacons embedded in the audio of TV advertisements. Logs of TV content viewed could then be used in analytics and targeted advertising.
In March 2016, the FTC sent out warning letters to the developers of 12 phone apps that integrated SilverPush ultrasonic receptors. One paragraph in that letter read:
For example, the code is configured to access the device’s microphone to collect audio information even when the application is not in use. Moreover, your application requires permission to access the mobile device’s microphone prior to install, despite no evident functionality in the application that would require such access.
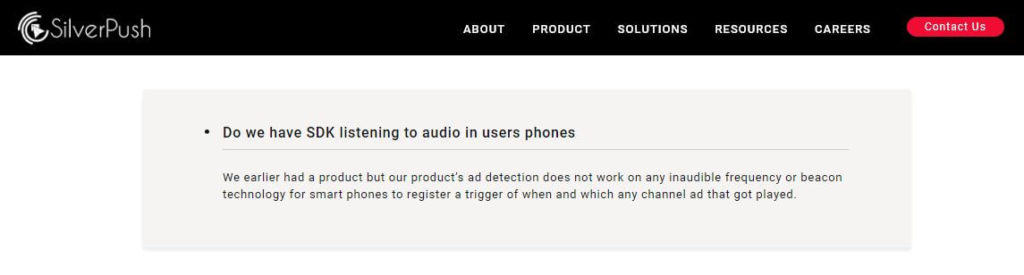
According to the SilverPush’s website, it no longer uses ultrasonic tracking in its campaigns:
We earlier had a product but our product’s ad detection does not work on any inaudible frequency or beacon technology for smart phones […]
It is unclear whether the developers of the offending apps altered their apps or simply pulled them from the market. However, the issuance of letters by the FTC garnered lots of media attention and put a critical spotlight on SilverPush and ultrasonic tracking technology.
2. Ultrasonic tracking found to override Tor privacy
One concerning discovery was that ultrasonic tracking can even reveal the internet activities of those who take measures to conceal their online identities. The use of ultrasonic tracking was proven as a method to identify users of the Tor network.
This hack was discovered and demonstrated by researchers at University College London and the University of California, Santa Barbara in October 2016.
The same study found that ultrasonic cross-device tracking could be used to inject fake audio beacons and leak the private information of users.
One of the main concerns of these researchers was the haphazard way in which ultrasonic technology is being deployed.
According to Giovanni Vigna, Professor at the University of California, Santa Barbara (UCSB):
[…] leaving ultrasound completely unchecked causes confusion, and implementations are flawed because they’re ad hoc. There are risks that are only going to become worse without standardization.
They suggest that operating systems could incorporate a standard methodology that serves to improve ultrasonic tracking privacy and security. However, such a standard has yet to be adopted.
3. German Android app study
A report from Germany’s Braunschweig Technical University [PDF], published in May 2017, revealed the discovery of 234 Android apps that incorporated ultrasonic receptors. Not all of these apps were participatory and the owners of hosting devices may not have known that their phones were tracking their activities.
In the wake of this study, Google assured users that it removed any violating apps from the store or ensured developers updated their privacy policies accordingly.
Google now stipulates that developers must expressly state in their privacy policies when ultrasonic beacons are being used and what their purpose is. Stricter policies likely acted as a deterrent to developers using the technology so it’s no surprise that the use of ultrasonic tracking in advertising has since fallen out of favor, at least publically.
Are ultrasonic signals secure?
Aside from privacy concerns, there are issues surrounding the security of ultrasonic tracking.
The transmission and reception of beacons have to happen almost instantaneously for the technology to be effective. This leaves very little time for authentication and encryption. The quick turnaround means that many interactions are performed without identity authentication, and data is relayed in an unencrypted format.
This leaves the door open for hackers who can manipulate communications. One real-world example of an ultrasonic tracking attack involved a beacon being played repeatedly in order to skew data. Other misuses could include intercepting bank account details on instore signaling systems, faking ticket codes, stealing store credits and gift cards, and transmitting false data.
In 2017, researchers at Zhejiang University in China developed DolphinAttack [PDF]. This was a method to gain access to smart appliances and other IoT devices through voice-activated virtual assistants, such as Siri, Alexa, and Google Assistant.
The researchers were able to send human-inaudible voice commands to Amazon Echo and iPhones. These devices provide access to web browsers on other internet-connected devices, allowing attackers to open infected websites.
Such a strategy could be used to introduce fileless malware, such as tracking systems, click generators, spyware, botnet controllers, and keyloggers. It could also be used to control devices such as home assistants and perhaps even security systems.
Who uses ultrasonic tracking?
With so many privacy and security risks, the technology hasn’t seen as much general use as was originally expected. However, there are still many companies utilizing ultrasonic tracking in some shape or form. Here are a few examples:
Shopkick
Shopkick tracks shoppers as they pass through stores and offers reward gift points. Points are automatically accumulated on the phone app as it passes beacons.
Lisnr
Lisnr specializes in ticketing and payment transmission. As with Shopkick, this app requires customer participation and is not a covert tracking system.
Google Nearby
Google Nearby is a useful feature that enables you to communicate with nearby devices. It relies on a combination of ultrasonic signaling, Bluetooth, and wifi to establish proximity.
Fanpictor
Fanpictor produces an application for audience involvement at shows and sporting events. This uses ultrasonic signaling to coordinate the phones of audience members and create a light show, as demonstrated in the video below.
Amazon Dash Buttons
Although the physical version of this product has been discontinued, some existing units are still in use. Amazon Dash Buttons can be used to reorder common household items at the push of a button and use ultrasonic signaling to communicate with your device.
How to block ultrasonic tracking
Your main defense system against ultrasonic tracking is vigilance. Although every computerized device with a microphone is at risk, the main target for these systems is the smartphone and access are facilitated by listening apps. Here are some tips for avoiding ultrasonic tracking.
1. Don’t grant access to your microphone
While you might be in a hurry to use an app, it’s always important to think twice before granting permissions, especially for things like your microphone and camera. Note that some apps may not work if you don’t grant all permissions, so you may be forced to make a decision about how important the operation of that app is to you.
Aside from heeding this advice for future installs, you may also want to check your existing app permissions. You can check out our guides for securing Android and iOS app permissions for more information.
2. Read privacy policies carefully
Let’s face it, we all hate reading privacy policies. But the fact is, they contain a lot of important information. Check for any mention of using your phone’s microphone and for what purpose it may be used. Be especially wary of policies that mention the microphone or audio where it doesn’t make sense for that particular app.
Be aware that app developers often use alternative language in their policies so that it’s more difficult to spot suspicious practices. For example, “inaudible sounds” might be used instead of “ultrasonic tracking.”
Also note that the app store screening processes won’t always catch violating policies, so an offending app (that doesn’t disclose ultrasonic use in its policy) may slip by unnoticed. In this case, it’s even more important to look out for what permissions are being requested.
3. Look out for possible patches or extensions
In the past, developers have come up with various tools that help users avoid ultrasonic tracking. For example, the SilverDog Chrome extension released in 2017 acts as an audio firewall to block ultrasonic beacons. And PilferShush is an Android app that listens for ultra-high frequencies to alert you when an app might be using them.
That being said, the development of these types of apps was more prominent when there was all more hype surrounding SilverPush and the German Android app study. Things seem to have slowed since then, and we’re not really seeing any apps or extensions designed for the mass market. Should we start to see an increase in the adoption of ultrasonic technology, however, no doubt the app development will follow.



Trusting stated policies of corporations is like trusting piranhas not to bite you when they’re starving and there’s blood in the water. And no one’s mentioned here the most dangerous adversary of all time: governments.
It seems to me there’s a simple solution, applied long ago to the storage of music on CDs, I think: require all manufacturers of any and all devices with mics to use microphones that do not have ultrasonic capability. Can not transmit ultrasound. I’ll bet an independent manufacturer could make a bundle from aftermarket non-US mics.
What do I do and whome do I contact if I suspect hackers are tracking me through ultrasonic tracking for their own personal gain
I’m experiencing malicious sound waves in residence and out in public (Sonic?) Is their an app. that can eliminate
this type of activity?
Different countries have different methods for reporting cases of hacking but you could start by consulting your local police for information.
Is it unlawful to submit someone to ultrasonic tracking with out their knowledge or permission.
If so where does one go to report this matter.
The laws surrounding ultrasonic tracking would depend on your location, but bear in mind there may be some legal gray areas, no matter where you are. In some regions, tracking of any kind without consent is unlawful, but some services may have information about tracking hidden in their terms of service. As for reporting, it would probably make sense to start with local law enforcement who should be able to provide you with more information.