Logpoint SIEM searches for malicious events on an IT system by looking through logfiles and monitoring network traffic. A SIEM is able to combine detection methods and sample indicators from several points on the network in order to spot stealth attacks and advanced persistent threats.
About SIEM
SIEM stands for Security Information and Event Management. This type of system combines two methods for intrusion detection.
A host-based intrusion detection system examines the log files on each endpoint and also those traveling over the network. The two main standards for log messages are Windows Events for the Windows operating system and Syslog, which operates on Linux, macOS, and Unix. Not all log messages get automatically filed, so the first task of a SIEM system is to provide a log server that collects and stores log messages.
The SIEM tool needs to search through logs from different sources, so those messages need to be reorganized into a neutral format before saving. This task is called log consolidation. The part of SIEM that works with log files is called Security Event Management (SEM).
The second part of SIEM is SIM. This is Security Information Management and it works in real-time, gathering live data to look for patterns of malicious activity. This is network-based intrusion detection (NIDS) and it mainly operates through network monitoring.
SIM is immediate and can spot intruders very quickly. However, most hackers know how to evade detection systems such as traditional signature-based detection methods used by firewalls and NIDS systems. For example, examining packet headers doesn’t spot typical attack signatures that are split across packets.
Modern hacker methods need combinations of data to spot. This task can only be performed retrospectively. As well as scanning passing traffic, SIM monitors generate their own logs that add to the information available to the companion SEM system. So, SIM and SEM each cover for the weakness of the other.
About Logpoint
Logpoint is a partnership, with its senior partners who are all prominent cybersecurity experts. The business is headquartered in Copenhagen, Denmark and has offices in the UK, France, Germany, Sweden, Finland, the USA, and Nepal.
Logpoint SIEM is the company’s one and only product. However, the modular design of the software means that the SIEM tool is really a bundle of security facilities.
Logpoint SIEM features
As the company’s name suggests, Logpoint is very strong in log message management and analysis. However, log data analysis is just half of a SIEM system’s functionality. The Logpoint SIEM service also monitors and analyzes live data.
Key Features:
- Log Management: Capable of processing large volumes of log messages, up to one million events per second from 25,000 different sources.
- Advanced Threat Protection: Monitors and analyzes live data to detect advanced persistent threats by tracking network traffic and log data.
- User Monitoring: Assesses user accounts for suspicious activity, including failed login attempts and brute force password attacks, using User and Entity Behavior Analysis (UEBA).
- Threat Intelligence: Provides a feed of typical attack vectors and vulnerability assessments, acting as a vulnerability scanner.
- Security Standards Compliance: Strong focus on GDPR compliance with dedicated dashboard sections and pre-written report formats for auditing and reporting.
- Incident Response: Analyzes network traffic and log files to detect intrusions and insider threats, triggering alerts with recommendations for actions.
- Configuration Options: Available as a Linux-based software, virtual machine, or pre-loaded appliance, offering flexible deployment options.
Log management
Logpoint SIEM is available for businesses of any size but it will be particularly appealing to large organizations. The system is able to process large volumes of log messages. Its top throughput rate is one million events per second (EPS) from up to 25,000 different event sources.
The Logpoint SIEM software is a Linux-based system, so it is very well disposed to collect Syslog messages. However, this is not the only log message type that the system can collect. Notable among the other log message formats that Logpoint SIEM collects are Windows Event log messages.
Sourcing log messages from different sources result in a variety in the format of messages. SEM systems excel at consolidating information from many sources and in order to do this, Logpoint SIEM needs to reorganize all received log records into a neutral format. This enables log data to be stored centrally, regardless of the standard that was followed for their creation.
Advanced threat protection
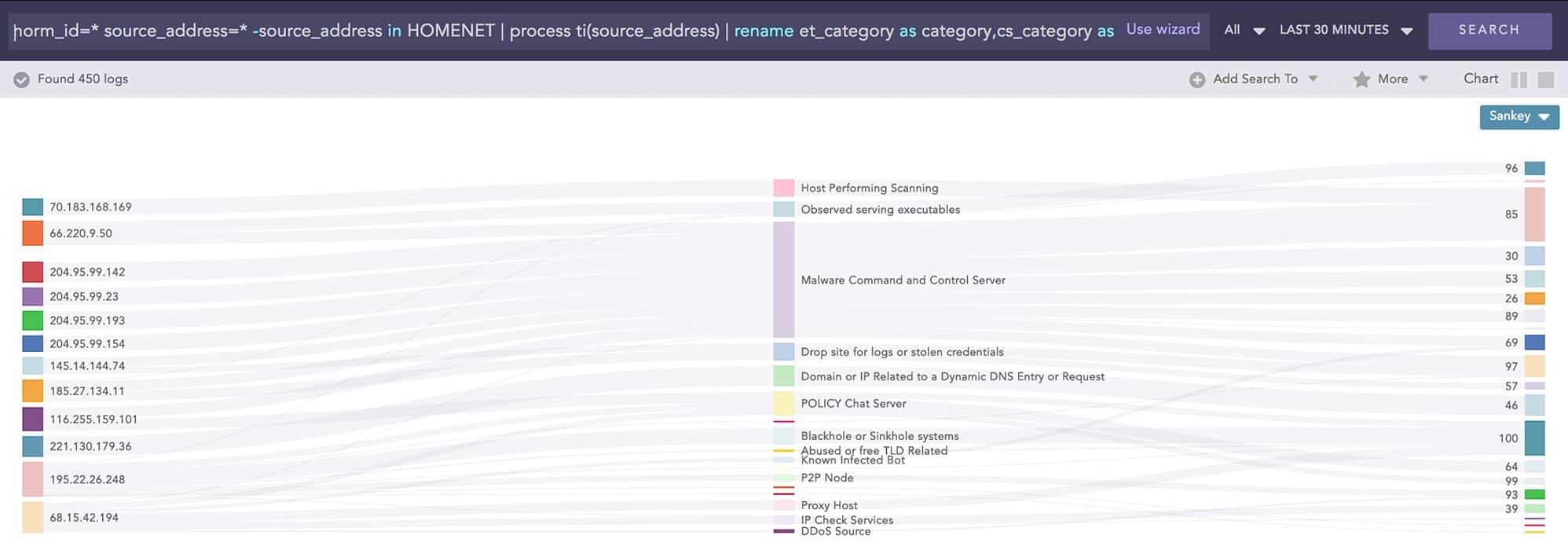
An Advanced Persistent Threat (APT) is a very common hacker activity today. It involves the hacker group gaining access to a private system and making adjustments to device configurations to make repeated undetected access a lot easier. The Logpoint SIEM service monitors system activity by tracking network traffic.
By analyzing log data and applying suspicions gleaned from that analysis to specific activity sources, the network manager can save a lot of time and resources. It avoids wasting effort on examining all traffic. The log file analysis findings give the traffic monitoring service-specific user accounts and IP addresses to look out for.
User monitoring
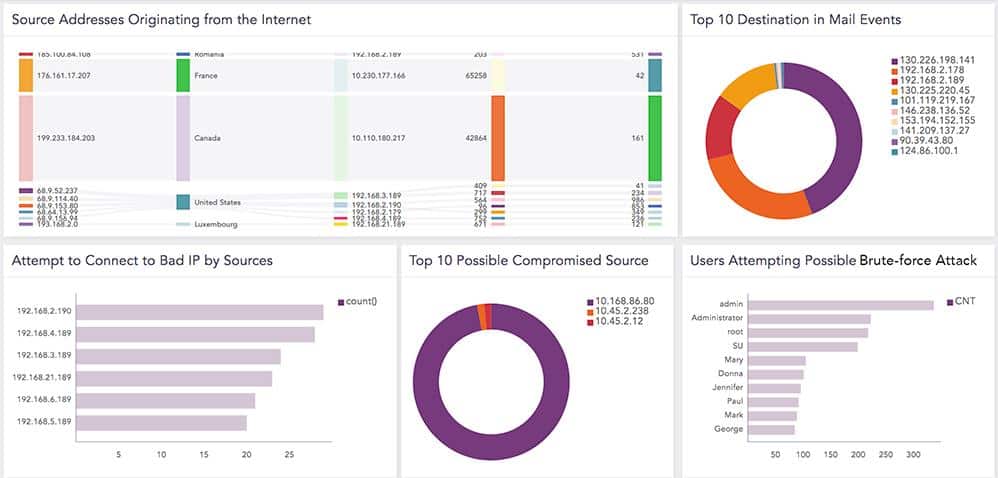
User accounts offer the easiest way for intruders to get around a system undetected. Logpoint SIEM assesses all existing accounts to identify abandoned or infrequently-used accounts that would be ideal vehicles for hackers. The Logpoint system also collects event log messages generated by Active Directory to detect failed login attempts and brute force password cracking actions.
Logpoint SIEM software includes specialized User and Entity Behavior Analysis (UEBA). This establishes a baseline for typical user behavior and the normal traffic that can be expected from each device on the network. The UEBA process uses machine learning to establish a baseline of normal activity. This is important because an out-of-the-box set of anomaly detection rules won’t apply to every user in every business in the world. When SIEMs began, applying set rules created too many false alarms. UEBA tailors alert settings to prevent legitimate activity been flagged as suspicious.
Threat intelligence
Logpoint provides the SIEM tool with information on typical attack vectors in the form of a threat intelligence feed. Analysts at Logpoint constantly research new attack methodologies and devise a list of vulnerabilities that facilitate access for advanced persistent threats. The Logpoint SIEM also acts as a vulnerability scanner and will identify points on the monitored system that need to be recalibrated in order to prevent such attacks from happening.
Security standards compliance
As an EU-based business, Logpoint is very strong on GDPR compliance. The security tool has whole sections on the dashboard that focus on compliance with GDPR and includes GDPR auditing and reporting features.
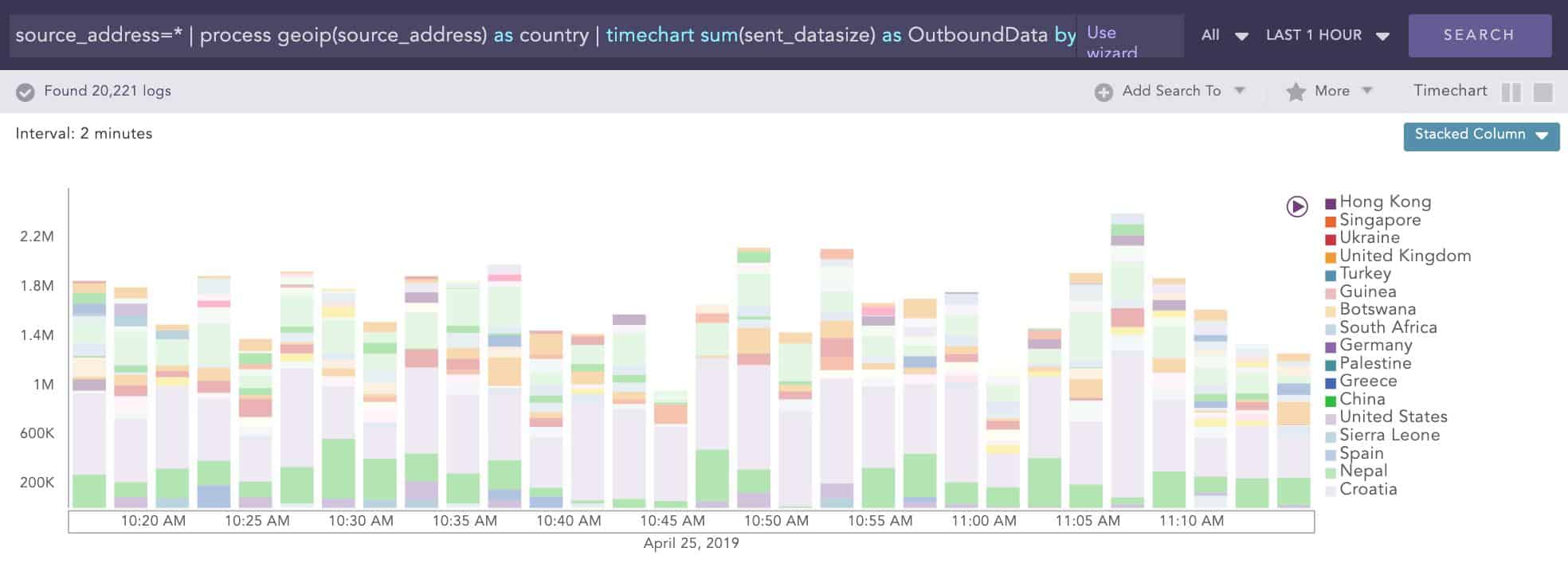
The location of data is particularly important for GDPR. This is because the regulations state that information about EU citizens should not be sent outside of the EU. Logpoint SIEM is able to track all connections by the correspondent’s physical location. This information is presented as live data and as an analytical graph of historical data.
These location-based records speed up compliance auditing and reporting for GDPR. The pre-written report formats that are shipped with Logpoint SIEM include a number of layouts that are needed for GDPR compliance.
Incident response
The incident response functions of Logpoint SIEM rely on the analysis of network traffic and log files to detect possible intrusion or insider threats. The detection of suspicious activity triggers alerts to network management staff, each with an explanation of the reasons for the warning. System scans in response to new threat intelligence also produce system hardening recommendations.
Logpoint SIEM doesn’t include automation threat mitigation actions. This could be seen as a weakness in the Logpoint SIEM service compared to more proactive rival SIEM products. Companies might be nervous about letting a computer program control activity by blocking traffic and shutting down accounts. In that case, Logpoint SIEM’s strategy of action recommendations rather than action automation would be more appealing.
Logpoint configuration options
The Logpoint SIEM software runs on Ubuntu Linux. Alternatively, it can be run on a virtual machine, in which case, it can be hosted on any server. Logpoint also offers Logpoint SIEM as an appliance with all of the SIEM software pre-loaded onto it.
Logpoint implementation
The software is not so easy to set up and usually, one of the Logpoint distributors go into the client site to set up the software. On the one hand, this bespoke service is an indication of a high-spec product but on the other hand, this installation procedure might put some potential customers off. Some might be concerned that any changes made to the IT infrastructure would require the Logpoint distributor to come back and alter the software installation, incurring call out charges.
The purchase process, as described on the Logpoint website seems to be a long, drawn-out process, starting with a workshop involving key IT staff and Logpoint consultants. This tailored, consultancy-led approach stands in great contrast to many of the major SIEM products available today.
In the rest of the industry, competitors to Logpoint have moved to cloud services. Those systems require a subscription and then the service is available immediately. Wizards in the dashboard of SaaS SIEMs guide the new user towards downloading an agent program, which then conducts an autodiscovery procedure and self-installs around the network.
Businesses that do not have an in-house IT team will struggle to find the key staff to send to the initial Logpoint implementation workshop and would be better served by one of the managed SIEM services that are now available.
Logpoint dashboard
The Logpoint user environment is colorful and attractive. The console screen is tabbed so users can switch quickly between data relating to each detection module. An example is the User Account Management screen, shown below.
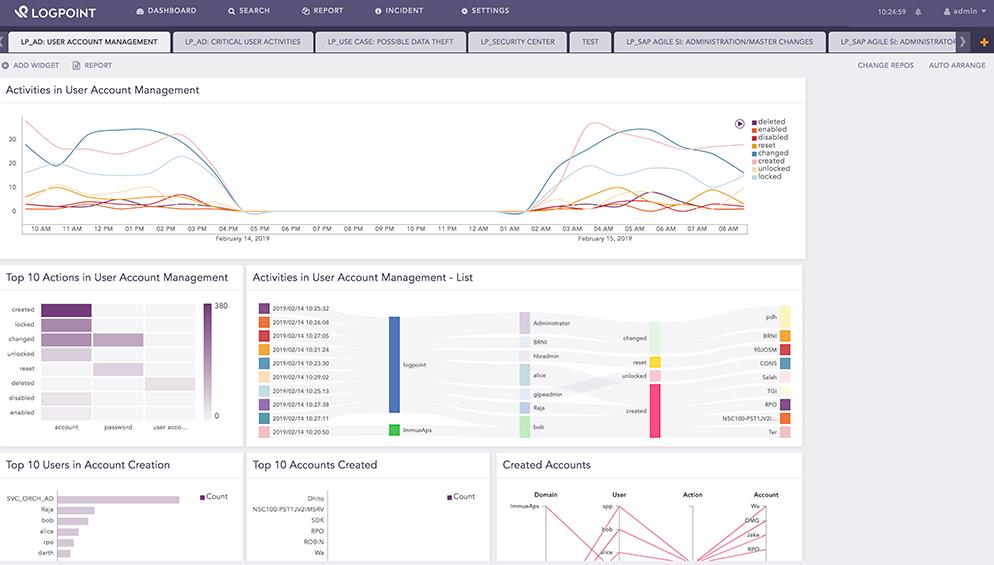
Analytical features of the console offer the opportunity to spot correlated events and decide on appropriate responses. As well as presenting incident data in graphical form, Logpoint includes pre-written report formats out of the box. The analytical engine also includes ad-hoc search and sorting functions that enable analysts to launch their own investigations.
An example of a data analysis screen is shown below.
In this example, the analyst has asked Logpoint SIEM to plot data from several days to look for an advanced persistent threat. Analysis periods can be adjusted to show events over an adjustable time period, not just recent data.
Pros:
- Flexible Metered Rate: Offers a metered rate, making it suitable for strict budgets.
- User-Friendly Interface: Features a minimalistic, colorful, and easy-to-navigate interface.
- Wide Range of Integrations: Supports a broad array of integrations for enhanced functionality.
- Support for Remediation: Includes both automated and manual remediation capabilities.
Cons:
- Enterprise-Focused: Better suited for larger enterprises, potentially less ideal for small businesses.
- Complex Setup: Requires on-site setup by Logpoint distributors, which can be cumbersome and may incur additional costs.
To find out more about pricing, register for a quote and a free demo.
Alternatives to Logpoint
Logpoint’s implementation model is very classy and all of the pre-installation meetings with consultants will probably appeal to the IT directors of large companies. However, small, budget-conscious businesses won’t have the money or the time to go through all of the hurdles that buying this security software seems to involve. Why not just sign up online for one of the other SIEM tools on the market and get it to install itself?
Logpoint is very strong on log management and analysis but there are stronger rivals that have better traffic monitoring capabilities. Businesses that want a SIEM tool to implement automated threat mitigation would also be better off with one of the other SIEM tools on the market.
To find out more about SIEM and the best systems that compete in the market, take a look at our post on the best SIEM tools. Instead, you could employ a team of SIEM experts on a subscription basis, check out the best managed SIEM services post.
Here are the best alternatives to Logpoint SIEM:
- ManageEngine EventLog Analyzer (FREE TRIAL) This system is part of a suite of infrastructure management tools that can all be integrated together. The EventLog Analyzer provides SIM functions while Log360 could be added on for SEM services. It installs on Windows and Linux. Access the 30-day free trial.
- Datadog Security Monitoring This is a cloud-based infrastructure monitoring system that includes a SIEM security monitoring module.
- McAfee Enterprise Security Manager A SIEM tool that is particularly strong on Active Directory management. It installs on Windows and macOS.
- Fortinet FortiSIEM A comprehensive includes automated defense responses. It is based on the cloud with onsite agent software.
- Rapid7 InsightIDR A cloud-based security service that includes device monitoring agent software for installation. It is easy to install and includes automated threat mitigation.
- SolarWinds Security Event Manager A SIEM tool that includes real-time incident response and pre-configured standards compliance models. This software installs on Windows Server.
- Heimdal Threat Hunting and Action Center This cloud-based system provides a SIEM and an automated response package that enhances the performance of on-premises Heimdal cybersecurity tools. Combine at least three Heimdal systems with this platform to create a company-wide cybersecurity service.
- OSSEC A free open-source IDS with a particular focus on log analysis. It installs on Windows, macOS, Linux, and Unix.
- LogRhythm NextGen SIEM Platform Includes AI methods for traffic and log analysis. It installs on Windows and Linux.
- AT&T Cybersecurity AlienVault Unified Security Management A full IDS that could be classified as SIEM plus because it includes a full range of detection methodologies and system monitors. It runs on Windows and macOS.