WebRTC is used by web browsers for voice and video chat applications like Skype for Web, Discord, and Google Hangouts. The free and open-source project lets apps set up peer-to-peer connections without the need for any extra plugins or applications, allowing for efficient real-time communication (the ‘RTC’ in WebRTC). Most modern web browsers now support and enable WebRTC by default, including desktop browsers like Chrome, Firefox, Safari, and Edge, as well as mobile browsers on Android and iOS.
The problem is that WebRTC compromises the security provided by VPNs, or virtual private networks. When a user connects to a VPN server, all of the internet traffic from their device should go through an encrypted tunnel to the VPN server. Among other benefits, this prevents websites and apps from determining the user’s real IP address, which is masked by that of the VPN server. An IP address is a string of numbers and decimals unique to every internet-connected device that can be used to determine location.
Whenever a VPN user visits a site that has WebRTC enabled, WebRTC can transmit data outside the encrypted tunnel. This exposes the user’s real IP address and location to the website, which means the user can be tracked by advertisers and other third parties.
In this article, we’ll explain how to prevent WebRTC leaks when using a VPN on all major browsers.
Preferred solution: Use a better VPN
Not all VPNs suffer from WebRTC leaks. Some have added security features to their apps that prevent WebRTC traffic from traveling outside the encrypted VPN tunnel. Of the many VPNs we’ve tested, two stand out:
While many VPNs claim to prevent IP leaks, many fail to live up to their promises. We’ve put these two VPNs through rigorous leak tests to ensure they never allow WebRTC leaks to occur under any circumstances. Both NordVPN and ExpressVPN prevent WebRTC leaks on any web browser or app.
By signing up for and installing either of these VPNs, you don’t need to worry about WebRTC leaks. No further tweaks are required.
How do I know if WebRTC is leaking?
When you connect to a VPN, your WebRTC IP address should either change to that of the VPN or be disabled entirely.
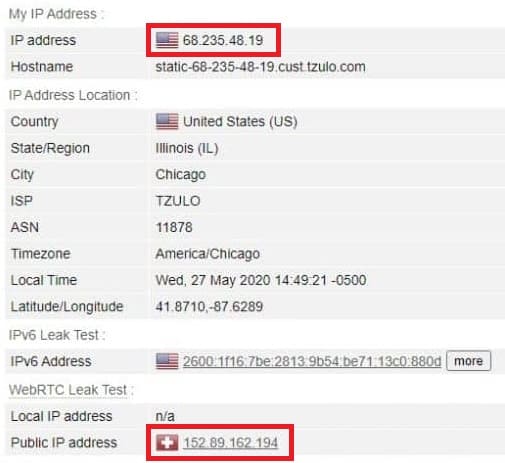
As an example, here’s my connection info while connected to a VPN that suffers from WebRTC leaks:
Notice that my standard IP address and WebRTC address are different. That’s because my real IP address is being leaked through WebRTC, and WebRTC traffic is not going through the VPN. While connected to the VPN, both addresses should both be identical.
You can run this test on your own using our VPN leak tester.
WebRTC leak severity depends on permissions granted
Before we get into other ways to prevent WebRTC leaks, we want to clarify that not all leaks are equal. When it comes to WebRTC leaks, we categorize them into two levels of severity:
- Leaks when permissions granted – less severe
- Leaks when permissions not granted – more severe
When you visit a website that uses WebRTC, your browser will usually ask your permission before allowing a website access to your camera or microphone.
If a VPN leaks your IP address before you’ve even granted that website permission to use your camera or microphone, that’s a big red flag. That means any website could use some simple javascript to monitor your IP address and expose your real location. We label this a “persistent vanilla leak,” which is the most severe type. Most VPNs that claim to prevent WebRTC leaks can at least stop this from happening.
Except for the two mentioned above, almost all VPNs suffer from the less severe version of WebRTC leaks, in which your IP address is exposed to the website only after you grant it permission to use your microphone or camera. Even though this leak is less severe, it’s still cause for concern. A VPN user should be able to safely visit WebRTC-enabled sites without exposing their IP address.
How to stop WebRTC leaks in Chrome
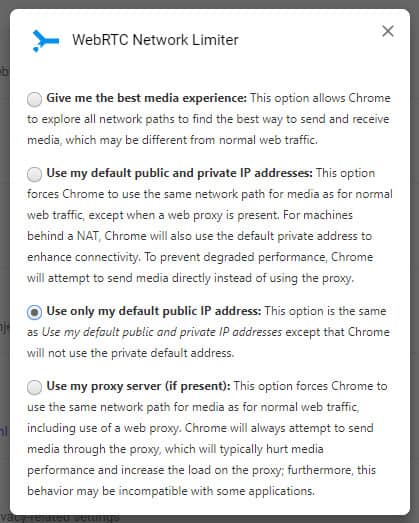
Google Chrome requires a simple browser extension to disable WebRTC. WebRTC Network Limiter lets you choose how WebRTC network traffic is routed. You can easily configure it to use only your VPN’s public IP address.
Alternatively, you can use the WebRTC Control browser extension to enable or disable WebRTC via a simple toggle switch.
See also: Best VPNs for Chrome
How to stop WebRTC leaks in Firefox
In Firefox, you can disable WebRTC in the browser settings:
- In the URL bar, enter:
about:config
- Run a search for:
media.peerconnection.enabled
- Double-click the entry to change it to False
Note that changes you make to the settings may not carry across updates, so you might need to re-adjust this setting again if your browser updates.
How to stop WebRTC leaks in Microsoft Edge
Microsoft Edge now supports both WebRTC plus its own proprietary version, dubbed ORTC. Unfortunately, Edge does not allow you to disable either. You merely get the option to hide your local IP address over WebRTC connections, but not your public IP address.
To conceal local IP addresses with mDNS hostnames, do the following
- Open Edge
- Types “about:flags” in the browser’s address bar and hit “Enter”
- Scroll down until you see “Anonymize local IPs exposed by WebRTC” or enter it in the search field
- Choose “Enabled” from the drop-down menu
A “WebRTC Leak Shield” extension is available on the Microsoft app store, but given it has no user feedback at time of writing and sparse details about the developers, we would avoid it for now.
If you’re an Edge user and you want to prevent WebRTC leaks, ExpressVPN and NordVPN will both get the job done. Websites will only see your VPN server’s public IP address and not your own when connected through either of their respective apps.
See also: Best VPNs for Microsoft Edge
How to stop WebRTC leaks in Safari
Safari blocks sites from accessing your camera and microphone by default, so we’re really only concerned about the less severe type of WebRTC leak here. You can turn WebRTC off in the developer settings:
- Open Safari and go to Safari > Preferences…
- Go to the Advanced tab and check the box at the bottom that says Show Develop menu in menu bar
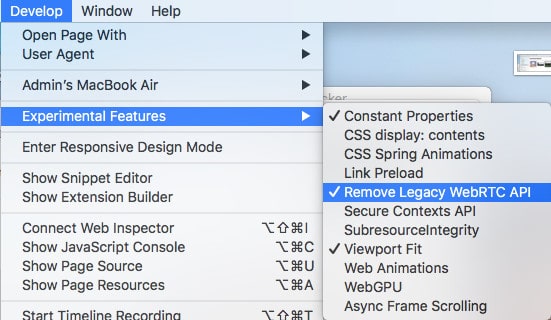
- Close the preferences menu and go to Develop > Experimental Features
- Check the option for Remove Legacy WebRTC API
See also: Best VPNs for Safari
How to stop WebRTC leaks on Android
Those with old versions of Android — such as 8.1.0 Oreo — are often advised to disable WebRTC Stun origin header in the flags menu. However, in our experience this does not work. Even if we disable every WebRTC-related setting, our real IP address leaks. In any event, this will be irrelevant to those using recent versions of Android — such as Android 13 — where the “WebRTC Stun origin header” feature is not available. You can check availability on your own device as follows:
- Open Chrome
- Type “chrome://flags” in the address bar
- Search for “WebRTC” in the “Search flags” field
Notably, ExpressVPN and NordVPN do prevent this leak when we connect through their Android apps. Websites can still see an IP address, but it’s the VPN server’s IP address and not our real IP address.
See also: Best VPNs for Android
How to stop WebRTC leaks on iOS
You can only disable WebRTC in mobile Safari on iOS 11 or earlier. The setting to disable it was removed in iOS 12. For later versions of iOS (12+), you can use ExpressVPN’s or NordVPN’s iOS app to mask your real IP address and prevent WebRTC leaks.
Disabling WebRTC on the Safari browser in iOS 11 or earlier is fairly similar to the desktop version:
- Open the Settings app on your iPhone or iPad
- Scroll down and tap on Safari > Advanced > Experimental Features
- Tap the switch next to Remove Legacy WebRTC API so it turns green
We will update this article if we come across a way to plug WebRTC leaks in iOS 12 and later.
See also: Best VPNs for iPhone
How to stop WebRTC leaks with uBlock Origin
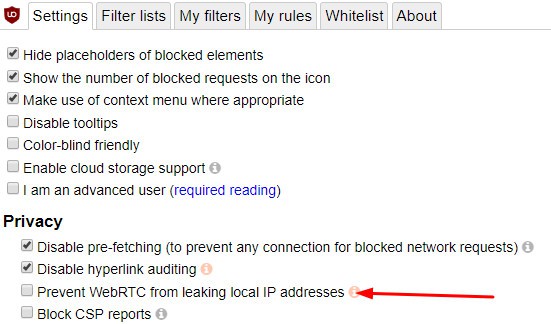
uBlock Origin is a popular browser add-on/extension for Firefox and Chrome. It can prevent your browser from leaking your device’s local IP address, but not your public IP address. For this reason, we recommend uBlock Origin more as a supplement to the other solutions in this list, and not a standalone solution.
After installing it, just go into the Settings and check the box that says, Prevent WebRTC from leaking local IP address.
What about VPN browser extensions?
There’s no shortage of browser plug-ins that claim to work like VPNs by redirecting internet traffic through a secure proxy. The vast majority of VPN browser extensions won’t protect you from WebRTC leaks. The only standalone VPN add-on we know of that does stop WebRTC leaks is NordVPN. In addition to its native desktop and mobile apps, its browser extension for Chrome and Firefox protects against WebRTC leaks.
The ExpressVPN browser extension stops WebRTC leaks, but isn’t a standalone product. Instead, users must already have installed the native VPN app. The browser extension is a way to conveniently control the app, and allows users to change the WebRTC network path so that it passes through an ExpressVPN server.
Disabling WebRTC won’t break VoIP apps
If you want to stop WebRTC leaks but like to use voice and video chat apps like Google Hangouts, Discord, and Skype, worry not. Disabling WebRTC doesn’t usually break those apps; they just have to fall back on a different method of communicating. While the call quality might suffer a bit, you can still use voice and video chat normally with WebRTC disabled.
Test for WebRTC leaks
Once you’ve applied a fix, you can check to make sure it’s working using Comparitech’s DNS leak test. This page runs a test in two parts: with the VPN connected and with the VPN disconnected. The results will show you in plain terms whether your VPN is leaking DNS, IPv6, or WebRTC traffic. You can even choose whether to allow or disallow microphone and camera permissions to determine leak severity.