Network security auditing is an essential task for modern enterprises that involves auditing your IT assets and policies. An audit can help expose potential vulnerabilities.
Here is our list of the best network security auditing tools:
- N-able N-sight EDITOR’S CHOICE This remote monitoring and management software offers an attack surface scanning module as an added extra, which is suitable for use by managed service providers to protect the networks of their clients. This is a cloud-based package. Start a 14-day free trial.
- Intruder (FREE TRIAL) A cloud-based vulnerability scanner with the monthly scans, on-demand scanning, and the services of a pen-testing team.
- ManageEngine Vulnerability Manager Plus (FREE TRIAL) This package of system security checks sweeps your network and checks for security weaknesses. Runs on Windows and Windows Server.
- Atera (FREE TRIAL) A SaaS platform for managed service providers that includes remote monitoring and management systems, such as its auditor report generator.
- ManageEngine Log360 (FREE TRIAL) A SIEM package that collects logs from network endpoints and cloud platforms and stores them for compliance auditing. Runs on Windows Server.
- Site24x7 Network Configuration Manager (FREE TRIAL) This unit on a cloud platform of system monitoring and management tools locks down the settings of network devices.
- Netwrix Auditor Network security auditing software with configuration monitoring, automated alerts, and a Rest API.
- Nessus Free vulnerability assessment tool with over 450 configuration templates and customizable reports.
- Trellix XDR Platform This cloud package draws activity data from multiple sources, including endpoints and networks.
- Nmap Open-source port scanner and network mapper available as a command-line interface or as a GUI (Zenmap).
- OpenVAS Vulnerability assessment tool for Linux users with regular updates.
- Acunetix A Web application security scanner that can detect over 50,000 network vulnerabilities when integrated with OpenVAS.
- Kaseya VSA RMM software with IT asset discovery, custom dashboards, reports, and automation.
- Spiceworks Inventory A free web-based network IT asset management tool that automatically discovers network devices via an on-site agent.
- Network Inventory Advisor inventory scanning tool compatible with Windows, Mac OS, and Linux devices.
- Metasploit Penetration testing tool that allows you to hack into exploits in your network.
It can also provide you with a high-order overview of the network which can be useful when trying to solve specific problems. Security audits can also give you an understanding of how protected your organization is against known security threats.
In this article, we take a look at the best network security auditing tools including port scanners, vulnerability scanners, patch managers, and more to help you audit your network for security concerns and stop security breaches.
The Best Network Security Auditing Tools
Our methodology for selecting network security auditing tools
We reviewed the market for network security auditing tools and analyzed the options based on the following criteria:
- A mix of automated vulnerability assessors and penetration testing tools
- Full activity logging for data protection standards compliance
- Automated asset discovery a software inventory
- Logfile and device configuration tamper protection
- Nice to have linked patch manager and configuration manager
- A free trial period for cost-free assessment or a free tool
- A system that offers value for money or a free tool that offers complete security sweeps
1. N-able N-sight (FREE TRIAL)
N-able N-sight is a cloud-based remote monitoring and risk management tool that enables a central IT department to manage several sites simultaneously. Many businesses need to be able to track the use of data for data security standards compliance and getting data access tracking built-in with a monitoring tool is a great help. N-able N-sight has network security auditing tools built-in to get your system compliant to standards such as PCI-DSS and HIPAA.
Key Features
- MSP-Centric Functionality: Ideal for managing multiple client networks.
- Compliance Auditing Features: Assists in adhering to standards like PCI-DSS, HIPAA.
- PII Tracking and Protection: Ensures sensitive data is securely handled.
- Network Scanning: Identifies security weaknesses, misconfigurations, open ports, and potential vulnerabilities.
- Vulnerability Assessment and Risk Reporting: Discovers and ranks security issues based on their severity and potential impact.
Why do we recommend it?
N-able N-sight is a cloud platform of tools for use by managed service providers (MSPs). This bundle includes network monitoring that can operate over several sites. This part of the system provides device discovery and inventory management. The service also offers a patch manager to keep operating systems and software up-to-date, thus blocking exploits that can assist intruders to get on the network. The package also provides security monitoring for endpoints and network devices.
The remote monitoring and management tools in N-able N-sight include PII exposure vulnerability assessments. The usage analysis system included with the RMM enables data managers to identify data usage trends and manage data risk.
The N-able N-sight system includes a Risk Intelligence module, which locates all PII and tracks access to it. Ad hoc scans in the package are particularly useful for data security compliance auditors. These include inappropriate permissions discovery and reports on leaked or stolen data.
Other standard maintenance tools in the RMM service help to protect data from accidental loss. For example, the RMM includes a comprehensive backup and restore function.
Digital security features in the bundle include endpoint detection and response to secure desktop devices. Patch management keeps all firmware and operating systems up to data and closes down exploits in software. The N-able N-sight service also includes an anti-virus package and a firewall for the entire network and all of its devices.
Who is it recommended for?
This RMM system is suitable for monitoring network devices and also endpoints. However, those endpoints need to be running Windows, macOS, and Android, or iOS. The patch manager in the package only works for Windows. So, this package is really only optimal for networks that run Windows on all of their endpoints. This is a SaaS package, which means that it can be accessed from any operating system. However, if you are going to be monitoring systems that include Linux computers, N-able N-sight is not a good fit.
Pros:
- Robust Multi-Tenant Management: Capable of handling large-scale operations.
- Customizable Dashboards: Offers tailored views and reports.
- Integrated Data Usage Monitoring: Identifies potential data theft and misuse.
- Comprehensive Backup and Recovery: Enhances data protection capabilities.
- Remote Monitoring and Management (RMM): Includes RMM features to remotely manage and troubleshoot client systems.
Cons:
- Primarily for MSPs and Large Enterprises: Not ideal for small networks.
- Windows-Centric Patch Management: Limited utility for non-Windows endpoints.
N-able N-sight is charged for by subscription and there are no installation fees. You can get a 14-day free trial to check out all of the services in N-able N-sight risk-free.
EDITOR'S CHOICE
N-able N-sight is our top pick for a network security auditing tool because it provides proactive security management, vulnerability detection, and compliance reporting. Its vulnerability scanning capabilities offer in-depth analysis of network infrastructure, identifying potential risks, misconfigurations, and outdated software that could be exploited by attackers. This feature ensures that IT teams can quickly remediate issues before they become security breaches. Another key strength is N-sight’s automated patch management system. It ensures that all devices and software are up-to-date with the latest security patches, reducing the risk of attacks targeting known vulnerabilities. The tool also integrates real-time threat monitoring to detect unusual activity across the network, enabling faster incident response. N-sight includes a compliance auditing unit, offering built-in templates for HIPAA, PCI-DSS, and GDPR. This feature simplifies compliance processes by automatically generating audit-ready reports, which is crucial for organizations needing to meet regulatory requirements. The wider N-sight package is a remote monitoring and management (RMM) system that allows IT teams to manage devices and troubleshoot security issues from a centralized platform. A multi-tenant architecture is ideal for use by managed service providers.
Download: Get a 14-day FREE Trial
Official Site: https://www.n-able.com/products/n-sight-rmm/trial
OS: Cloud based
2. Intruder (FREE TRIAL)
Intruder is a vulnerability scanner that is delivered from the cloud. The basic function of the service performs a monthly scan of each customer’s system and launches intermediate scans if a new threat goes into the service’s threat intelligence database.
Key Features
- Frequent Scan Options: Choose your desired frequency for vulnerability scans.
- Cloud-Based Efficiency: Accessible and manageable from anywhere.
- Expansive Vulnerability Database: Covers over 9,000 known vulnerabilities.
- Visual Performance Metrics: Clear, graphical representations of network health.
Why do we recommend it?
Intruder.io is a vulnerability scanning system, which documents your network’s security weaknesses. This service can be run as an external scan, which identifies the security loopholes that hackers could use to get in. It also provides an internal network scan option, which will examine each device connected to your network and identify misconfigurations and software weaknesses that will help intruders move from one device to another and alter network devices to make secret activities hidden.
When a company signs up for the service and sets up an account, the first task that the tool performs is a full vulnerability check of the entire system. This process repeats every month. Whenever an intruder gets an update to its threat intelligence database, it launches an intermediate scan on all of its customers’ systems, specifically examining the hardware and software that are vulnerable to the newly-discovered exploit.
As it is based in the cloud, the intruder service sees your network as any outside hacker would see it. The sweep covers every single element of IT infrastructure on the customer’s site and also those cloud services that the client uses. A scan covers 9,000 known vulnerabilities, including web application vulnerabilities to tricks such as SQL injection attacks and cross-site scripting.
Thanks to an agent that needs to be installed on the network, the Intruder scan also looks for vulnerabilities to insider threats.
Intruder is paid for by subscription. Customers of the service have the option of three plans: Essential, Pro, and Verified. The Essential plan gets you an automatic monthly scan. The Pro plan gets the monthly scan plus a facility for on-demand vulnerability scanning. The Verified plan includes the services of a human penetration testing team as well as the benefits contained in the Pro plan.
Who is it recommended for?
Any business would benefit from the Inteder.io system. It is made more accessible by the presentation of three plans. The plan levels provide monthly automated vulnerability scans at a low cost, which will appeal to smaller businesses and the top plan includes the services of a human penetration testing team, which meets the requirements of large companies that need to prove compliance with data security standards. This is a cloud-based system and its vulnerability database gets updated automatically behind the scenes, so your system is always scanned for the most recently discovered security weaknesses.
Pros:
- Intuitive User Interface: User-friendly and visually appealing for easy navigation.
- Automated Vulnerability Detection: Scans new devices and suggests updates.
- Cloud-Hosted Convenience: No need for on-premise infrastructure.
- Web Application Vulnerability Assessment: Comprehensive testing for web-based vulnerabilities.
- Tiered Pricing Model: Accessible to businesses of various sizes.
Cons:
- Complex Feature Exploration: Requires time to fully understand all functionalities.
- Limited Frequency in Basic Plan: Essential plan restricts scan frequency.
Scans occur automatically once a month with the Essential plan. On-demand scans aren’t available with that plan, but they are included with the Pro plan. Intruder is available for a 30-day free trial.
3. ManageEngine Vulnerability Manager Plus (FREE TRIAL)
ManageEngine Vulnerability Manager Plus is a security system that scans a system for weaknesses and documents them and then implements measures to remove them. The system looks at installed software and device settings to identify weaknesses that hackers are known to exploit. These checks extend to endpoints and network appliances.
Key Features
- System Configuration Analysis: Tightens security settings across devices.
- Comprehensive Software Assessments: Examines installed software for vulnerabilities.
- Updated Threat Intelligence: Receives regular updates on new security threats.
Why do we recommend it?
ManageEngine Vulnerability Manager Plus is a great bundle of tools that provide the discovery of all assets, scans for weaknesses, and tools to remediate discovered exploits. The identification of exploits and their resolution can be linked together so problems get fixed automatically. You can also choose to keep these two phases separate to require manual involvement – it’s your choice. The package offers three plans and the remediation tools, which are a patch manager and a configuration manager are only included in the top edition.
The vulnerability scan is a periodic security audit and it provides an automated system check that is more thorough than manual procedures. The sweeps are able to scan through devices running Windows, macOS, and Linux. It will look at the operating system of each device connected to the network and also search through all installed software. It can assess the settings of security tools, such as firewalls, and will also audit web services and communication protocol settings to ensure that there are no weak points.
Agents installed on endpoints launch a vulnerability check every 90 minutes. The service includes a subscription to a threat intelligence feed and this gets updated whenever a new vulnerability is discovered. The arrival of a threat discovery triggers a system scan to detect the presence of that vulnerability.
Remediation measures in the tool include a patch manager that automatically detects the availability of software and operating system updates and will roll them out on a schedule. The system will also recommend actions to take in order to close down any loopholes that it discovers during its vulnerability scans.
Who is it recommended for?
ManageEngine Vulnerability Manager Plus is only available for Windows Server. So, you need to have a server running Windows if you want to use this software. The appeal of this network security auditing tool is widened to businesses of all sizes by the three plans that are available for the tool. The first of these is free and it covers 25 devices. This is a great offer for small businesses because that capacity is enough to protect a fairly standard small business network. The top plan gives you automated remediation and that will appeal to mid-sized and large enterprises.
Pros:
- Proactive Vulnerability Scanning: Regular checks for system weaknesses.
- Versatile OS Compatibility: Scans devices running Windows, macOS, and Linux.
- Automated Patch Management: Deploys updates to address identified vulnerabilities.
- Free Version for Small Networks: Suitable for managing up to 25 devices.
- Actionable Remediation Advice: Provides clear guidance for fixing vulnerabilities.
Cons:
- Windows Server Requirement: Only available for Windows Server environments.
- Complex Ecosystem: Extensive features necessitate a learning curve.
Vulnerability Manager Plus is runs on Windows and Windows Server and it is available in three editions: Free, Professional, and Enterprise. The free version is limited to monitoring 25 computers. The Professional edition covers one site and Enterprise edition covers WANs. Both paid systems are offered on a 30-day free trial.
Related post: Network Configuration Management Software
4. Atera (FREE TRIAL)
Atera is a package of services for monitoring and management tools for remote systems. The SaaS platform also has a section of utilities designed for use by the management team of a managed service provider. Among all of the tools in this bundle is a reporting facility that can generate a range of system audit reports.
Key Features
- MSP-Oriented Design: Tailored for managed service providers’ requirements.
- Per-Technician Subscription: Flexible pricing model based on technician count.
- Security Auditing Reports: Detailed reports for comprehensive security analysis.
Why do we recommend it?
Atera is offered in versions for IT departments and managed service providers (MSPs). The system is a remote monitoring and management (RMM) system with an integrated ticketing system, so it is a complete package for an IT support team, whether in-house or contracted in. Access to remote systems requires individual technician accounts with credentials and these enable the actions of each support operative to be logged. This is a great security auditing feature by itself. The Atera package creates and maintains hardware and software inventories. The software register provides the basis for an automated patch manager, which documents and tightens the security of the supported systems.
The service is designed for use by managed service providers. When a system is enrolled in the service, the Atera server downloads an agent onto the target network. This uses SNMP to gather information on each of the devices composing the network.
The result of this scan is a network asset inventory, which is updated constantly and provides a basis for all of the automated network monitoring activities of the package. That network monitor works on a system of performance expectation thresholds, which trigger alerts if problems are detected. Atera offers a network mapping system as a paid add-on.
Who is it recommended for?
Atera is priced per technician, which means support teams of any size will find the package useful. All of the functions offered by the Atera package are available for a single, independent freelance technician. That’s the same package offered to very large support organizations. As it is a SaaS package, a support technician can access the system from anywhere, even from home.
Pros:
- Comprehensive Remote Monitoring: Efficient setup for client network monitoring.
- Adaptable Reporting Tools: Customizable reports for various audit needs.
- Asset Inventory Tracking: Maintains updated hardware and software inventories.
- Network Discovery Updates: Constantly refreshes network device information.
Cons:
- No Linux Agent: Limited utility for networks with Linux systems.
- Additional Cost for Network Mapping: Key feature requires extra payment.
Atera is a subscription service and there are three plan levels for the service. This makes the package suitable for businesses of all sizes. As it is a SaaS platform, you don’t need to host any software on-site and all of the operating data and performance records are stored on Atera’s cloud server. You can get a free trial to assess the package.
5. ManageEngine Log360 (FREE TRIAL)
ManageEngine Log360 is a SIEM that offers compliance auditing and reporting for HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA. The system is composed of a central server and many device agents. The agents collect log messages and forward them to the server.
The log manager in Log360 consolidates arriving log messages by converting them into a common format. It then files those records so that they can be searched for compliance auditing.
Key Features
- Extensive Log Collection: Gathers data from a wide array of sources.
- Unified Log Management: Consolidates and organizes log data effectively.
- Compliance-Focused Reporting: Tailored for standards like HIPAA, PCI DSS, GDPR.
Why do we recommend it?
ManageEngine Log360 is a SIEM system. A SIEM searches through log files and so, Log360 also includes a log manager that gathers, consolidates, and files log messages. These records are made available for the automated security searches o the IEM and there is a data viewer that allows manual ad-hoc data analysis. Those log files are made available for compliance auditing. As well as gathering log messages from network devices, operating systems, and software packages, the Log360 package also creates its own records by tracking user activity and building a profile of typical behavior per account. The system also data loss prevention.
Log messages are shown live in the dashboard of Log360 as they arrive and they can be loaded into the data viewer from files. The data viewer includes search tools for analysis and the package includes pre-written compliance reports for security assessments.
The threat hunter of the SIEM is supplied with a threat intelligence feed. Once it discovers suspicious behavior, it generates an alert, which is displayed in the dashboard. You can also get the system to channel those alerts through your service desk team management tool for technician action.
Who is it recommended for?
Log360 is a very large package. It is available for Windows Server, but it is able to gather logs from other operating systems, including cloud platforms. The tool provides Active directory analysis and improvement as well as log message collection and analysis. All of this is suitable for businesses that have become too large to keep track of, so it is probably more functionality than a small business would need. The Log360 system is suitable for mid-sized and large organizations. Very large businesses particularly need the automated detection services built into this package and companies that need to comply with HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA will get the most value out of this package.
Pros:
- Real-Time Security Monitoring: Immediate alerts for detected security incidents.
- In-Depth Data Analysis: Comprehensive tools for thorough log examination.
- Automated Compliance Reports: Streamlines the reporting process for audits.
- Threat Intelligence Integration: Keeps pace with emerging security threats.
Cons:
- Windows Server Restriction: Not available for Linux server environments.
- Complexity for Smaller Organizations: May be overwhelming for small businesses.
The server for Log360 is available for Windows Server. The agents are available for a list of operating systems, including Linux, AWS, and Azure. You can assess ManageEngine Log360 with a 30-day free trial.
6. Site24x7 Network Configuration Manager (FREE TRIAL)
Site24x7 is an effective network security auditing tool that offers robust capabilities for monitoring and analyzing security events across an organization’s network. By integrating with a wide range of network devices, servers, and applications, it collects and processes security logs to help administrators detect vulnerabilities, unauthorized access, and suspicious activities in real time.
Key Features:
- Log Management: Collects and analyzes logs from a wide range of network devices, servers, and applications.
- Real-Time Alerts: Offers real-time alerts on security events.
- Records Security Issues: unauthorized access attempts, failed logins, and configuration changes.
Why do we recommend it?
The Site24x7 platform provides comprehensive visibility into the security health of the network, ensuring that organizations can maintain a secure infrastructure and proactively address potential threats. The tool is able to track and analyze security logs from various sources, including firewalls, routers, and intrusion detection systems.
This system enables businesses to monitor network traffic, identify potential attack vectors, and understand patterns of malicious activity. Site24x7’s customizable alerting system notifies administrators about security events such as failed login attempts, unauthorized access, and configuration changes, enabling a quick response to mitigate risks.
The Network Configuration Manager provides detailed reports and dashboards that present security metrics that facilitate data analysis and the identification of trends. Report templates help businesses meet compliance requirements for standards like PCI-DSS, HIPAA, and GDPR by offering pre-built compliance templates and automated report generation. The platform’s extensive data retention and auditing features support thorough investigations, enabling organizations to maintain detailed logs for future reference or audits.
Who is it recommended for?
Site24x7 is recommended for businesses of all sizes that need to enhance their network security auditing capabilities. It is particularly beneficial for monitoring and securing large or complex network infrastructures. Organizations in regulated industries, such as finance, healthcare, and e-commerce, can benefit from Site24x7’s built-in compliance reporting for standards like PCI-DSS, HIPAA, and GDPR.
Pros:
- Customizable Dashboards: Easy-to-read dashboards that allow administrators to monitor security metrics and analyze data efficiently.
- Compliance Reporting: IPre-built templates for compliance standards like PCI-DSS, HIPAA, and GDPR, streamlining audit processes and ensuring regulatory compliance.
- Scalability: Scales effectively for businesses of all sizes, making it suitable for both small companies and large enterprises with complex network infrastructures.
Cons:
- No On-Premises Version: This is a cloud-based SaaS platform
Site24x7 includes many system monitoring and management tools in one plan – you can’t sign up just for the Network Configuration Manager by itself. You can try out this cloud-hosted package with a 30-day free trial.
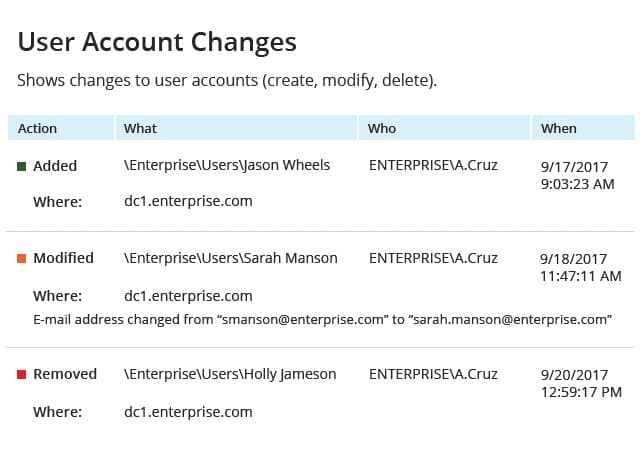
7. Netwrix Auditor
Netwrix Auditor is a network security auditing software that can monitor configuration changes in your environment. Through the dashboard, you can view information on system changes including Action, Who, What, When, and Where. All of the information provides you everything you need to know about the nature of the changes and what happened.
Key Features
- User Access Insights: Monitors and reports on data access patterns.
- Comprehensive Audit Reports: Detailed documentation for security audits.
- Automated Security Controls: Implements measures to secure network configurations.
Why do we recommend it?
Netwrix Auditor is a comprehensive security auditing tool that examines user accounts and data locations above all other considerations. The package can be run continuously, which allows it to act as an intrusion detection system. The network device auditing feature in this system looks at access accounts and permission levels, issues such as telnet access without security, logon attempts, and configuration changes. As well as issuing live warnings whenever a security weakness or threat is detected, the Netwrix system also writes its discoveries to log files. These logs can be used for compliance auditing and reporting.
The user can also view the same information about login attempts and port scanning attempts. Failed logins are marked with a red box, which helps you to see immediately if someone is trying to break into your network. You can also view hardware monitoring information on CPU temperature, power supply, and cooling fan status.
An alerts system provides an automated incident response. You can configure scripts that Netwrix Auditor will execute when an alert is generated. For example, if a divide fails then you can configure the settings to generate a Helpdesk ticket for your team to start the remediation process.
Who is it recommended for?
Of all the systems on this list, this package is probably closest to ManageEngine Log360. It performs activity tracking for each user account, which can identify account takeover events. Like Log360, this tool will raise an alert if it discovers a threat and it will also organize log messages for auditing. However, Netwrix Auditor isn’t classified as a SIEM. The tool is heavily focused on Microsoft products, so you wouldn’t choose Netwrix Auditor if you use Linux and LAMP solutions. A free Community Edition will appeal to small businesses.
Pros:
- In-depth Auditing and Reporting: Enhances file security and access tracking.
- Device Health Monitoring: Includes hardware status checks.
- Script-Driven Remediation: Facilitates automated response to security events.
- Help Desk Integration: Streamlines incident management processes.
Cons:
- Limited Cisco Device Support: May have compatibility issues with certain network hardware.
- Complex Alerting System: Could benefit from more intuitive alert configurations.
Netwrix Auditor is one of the top network security auditing tools for those who want a solution with automation and a rest API. There is a free community edition, but you’ll have to purchase the software if you want to view more in-depth detail on network events. Contact the company directly for a quote. You can download the 20-day free trial.
8. Nessus
Nessus is a free vulnerability assessment tool that can be used for auditing, configuration management, and patch management. Nessus is well-equipped to confront the latest threats releasing plugins for new vulnerabilities within an average of 24 hours. Plugins are added automatically so the user is ready to discover new cyber-attacks.
Key Features
- Comprehensive Vulnerability Assessment: Extensive testing for over 50,000 vulnerabilities.
- Free Version Availability: Accessible option for small-scale environments.
- Severity Categorization of Issues: Prioritizes vulnerabilities based on risk level.
Why do we recommend it?
Nessus is a well-known and highly respected vulnerability scanner. This package was originally a free, open-source project but it has now gone proprietary. The tool is available in a free version but that has less functionality than the paid options and it is limited to scanning 16 IP addresses. Nessus will provide you with a list of vulnerabilities on your network devices and endpoints. These results can be stored as reports and they categorize all discovered exploits by severity.
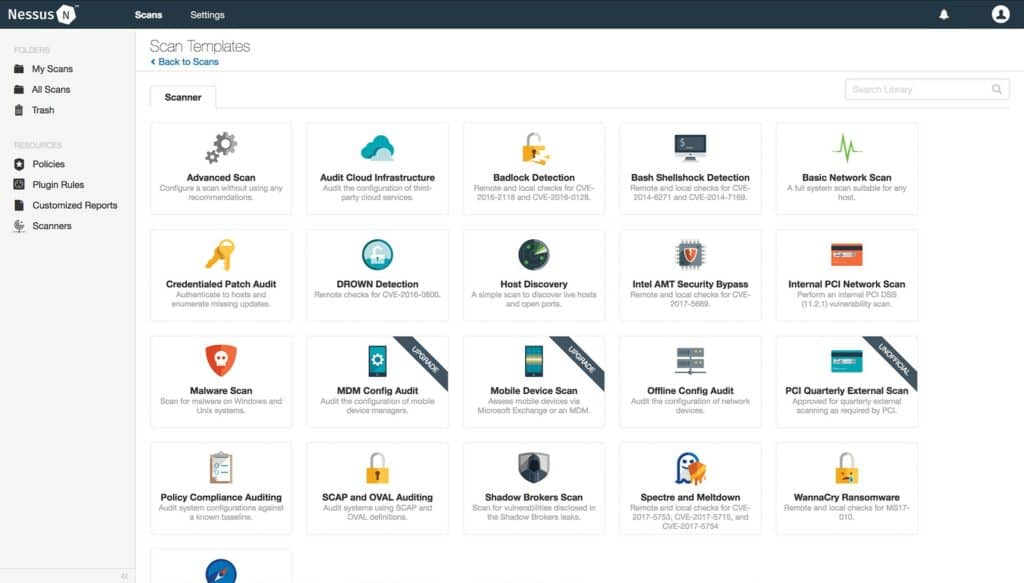
Configuring Nessus is easy because you have the support of over 450 different configuration templates. For example, there is a range of scan templates including Basic Network Scan, Advanced Scan, Malware Scan, Host Discovery, WannaCry Ransomware, and more. The variety of templates makes it easy to find the vulnerabilities you need.
You can also generate customizable reports to reflect on new entry points. Create reports detailing specific vulnerabilities by host or plugin. For example, you could generate a Hosts Executive Summary report and see how many hosts are categorized as Critical, High, Medium, Low, and Info. Reports can be created in HTML, CSV, and .nessus XML to share with your team.
Who is it recommended for?
The Nessus system is a good option for mid-sized and large organizations. Small businesses can use Nessus Essentials for free. The OpenVAS system was created as a free, open-source fork of Netssus when the owner of the Nessus project decided to turn it into a commercial product. So, anyone interested in Nessus should also examine OpenVAS as well.
Pros:
- Regular Plugin Updates: Quickly adapts to new cyber threats.
- User-Friendly Interface: Simplifies the vulnerability assessment process.
- Customizable Reporting: Tailored reports for different organizational needs.
Cons:
- Resource-Intensive Scans: Can impact system performance during scans.
- Limited Integration Options: May not work seamlessly with all existing security tools.
- Higher Cost for Enterprise Solutions: Price point may be prohibitive for smaller networks.
Nessus is ideal if you’re looking for an auditing solution that is equipped to discover new online threats. The Essentials version of Nessus is available for free and can scan up to 16 IPs. Paid versions start at $2,990 (£2,257) for Nessus Professional, which comes with a one-year subscription and unlimited IPs. You can start with Nessus Professional on a 7-day free trial.
9. Trellix XDR Platform
The Trellix XDR Platform is a full system security monitoring package that includes endpoint monitoring and network monitoring. The network security unit, called an NDR adds to the endpoint monitoring service. While the endpoint monitor looks for anomalous behavior on each device, the NDR catches lateral movement attempts between endpoints – a technique that is used by malware to spread around the enterprise.
Key Features
- Lateral Movement Detection: Identifies and blocks spread of malware across devices.
- Anomalous Access Identification: Flags unexpected or unauthorized access attempts.
- Comprehensive Threat Mitigation: Responds to and neutralizes detected threats.
Why do we recommend it?
The Trellix XDR package is hosted on the cloud and installs agents on your site. The combination of endpoint protection and network scanning covers all bases. The tool focuses on hosts, where all executables run, to find malware and intruders. The network detection feature is able to isolate infected devices by blocking all traffic that emanates from malware in attempts to extend the attack to other devices.
Having a user account stolen or getting malware on one endpoint is bad enough but when intruders use that account to get to sensitive data on other devices or when ransomware spreads to all computers, you are really in trouble. Automated responses in the Trellix XDR stop those horrors from occurring.

All of the discoveries and responses of the Trellix system are stored in logs for later analysis. The measures taken to protect your system also need to be recorded to form part of compliance reporting. So, this system is doubly important for companies that handle sensitive data and need to follow data protection standards.
There are always new attack techniques appearing and finding software that already has characteristic recognition built into it for every possible attack type is impossible. So, the backup protection of the NDR is vital because it blocks movement no matter what the methods of the malware or the intruder are.
Who is it recommended for?
Every business needs to protect its data against theft and corruption. Blocking access before it happens is better than trying to trap a malicious actor. NDR is preventative because any unimportant endpoint can be an entry point to malware or intruders due to user carelessness. You need to stop those malicious actors from getting from a user device to an important data store.
Pros:
- Cloud-Hosted Efficiency: Offers flexibility and ease of access.
- Endpoint and Network Monitoring Synergy: Covers all bases for security monitoring.
- Automated Log Storage for Compliance: Useful for regulatory adherence.
Cons:
- Constant Internet Dependence: Requires uninterrupted online connectivity.
You can investigate Trellix XDR further by requesting a demo.
10. Nmap
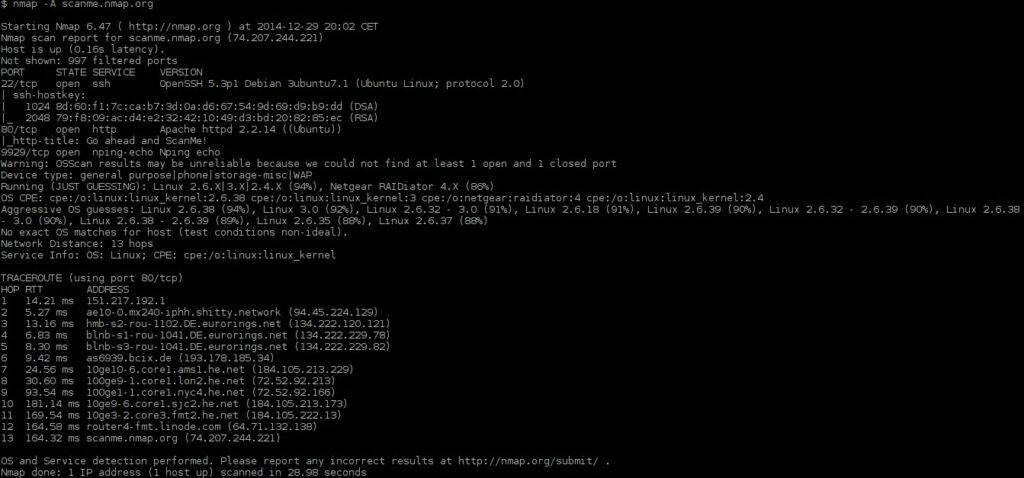
Nmap is an open-source port scanner and network security scanner. With Nmap, you can discover hosts and find open ports vulnerable to being attacked. The software tells you whether ports are open, closed or filtered, via a command-line interface. The interface also tells you additional information such as the Port, State, Service, and Version of entities discovered. You can use the program to identify what OS version a piece of software is running so that you can patch any glaring weaknesses.
Key Features
- Open-Source Port Scanner: Widely used for network security scanning.
- Command-Line Utility: Offers granular control for experienced users.
- Zenmap GUI Front-End: Provides a more user-friendly interface option.
Why do we recommend it?
Nmap is well known in network administration circles as a network discovery tool. It is a command line tool that can be integrated into scripts. The layout of the results of this utility can be a little hard to read and if you want to look at the layout of the network, you would be a lot better off downloading Zenmap, which is a companion system to Nmap and offers a GUI frontend. The Zenmap system is able to save the network device information discovered by Nmap, which makes it a useful network documentation tool.
There is also the option to create automated scans. Nmap allows you to write scripts in Lua to run scans automatically. Automating scans is beneficial because it saves you time so that you don’t have to run scans manually to discover vulnerabilities.
If you’re not a fan of command-line interfaces then you can switch to Zenmap, the GUI version of Nmap. With Zenmap the user can save scan profiles and run common scans without having to manually set up a scan every time. You can also save scan results to review later on.
Who is it recommended for?
Nmap is used by network administrators, hackers, and penetration testers. As it is free, there is no reason not to download Nmap and have it on your computer for ad-hoc investigations. It is possible to get Nmap and Zenmap to run on Windows. If you like to write your own scripts and you have time to learn the Lua scripting language, you will really like Nmap.
Pros:
- Free and Versatile Tool: Suitable for various network exploration tasks.
- Strong Community Support: Benefits from a large open-source community.
- High Customizability: Supports scripting for tailored scans.
Cons:
- No Built-In GUI: Requires separate installation of Zenmap for graphical interface.
- Steep Learning Curve: Best suited for network professionals.
- Limited Proactive Protection Features: Focuses on scanning rather than ongoing monitoring.
Nmap is a popular port scanning tool because it’s simple enough for new users and offers more experienced users a ton of advanced features. It’s also free! Nmap is available for Linux, Windows, UNIX, and FreeBSD. You can download the program for free.
11. OpenVAS
OpenVAS is an open-source vulnerability scanning software aimed at Linux environments that offers authenticated and unauthenticated testing.
Key Features
- Open-Source Vulnerability Scanner: Tailored for Linux environments.
- Customizable Testing Scripts: Allows for personalized vulnerability assessments.
- Free Usage: Accessible for all sizes of organizations.
Why do we recommend it?
OpenVAS is a fork of Nessus. Contributing developers to Nessus walked out and created their own version when Nessus turned into a commercial product. This project is sponsored by Greenbone Networks but it is still completely free. The package has a list of more than 50,000 network vulnerabilities, which makes this one of the most comprehensive internal vulnerability scanners. Greenbone has built a more user-friendly system around the OpenVAS code, called Greenbone Enterprise Appliance – which is a paid product.
OpenVAS is constantly updated to detect the latest vulnerabilities with the Greenbone Network Vulnerability Tests public feed, which includes over 50,000 different vulnerabilities.
Who is it recommended for?
OpenVAS is a great system but it is not very easy to use. Businesses of all sizes would benefit from using this tool. You will need to dedicate a member of staff to learning how to use the OpenVAS system effectively and that study can take quite a while. However, it is necessary to create your own on-site expert in the tool because there is no professional support available for the system. OpenVAS is only available for Linux.
Pros:
- Extensive Vulnerability Database: Covers a wide range of known security threats.
- Regular Updates: Maintains relevance with evolving cybersecurity challenges.
Cons:
- Complex Interface: Can be challenging for those without technical expertise.
- Lacks Professional Support: Relies on community-driven resources.
It’s a good fit for enterprises looking for an affordable vulnerability scanning tool for testing out the defenses of a network. OpenVAS is available for free.
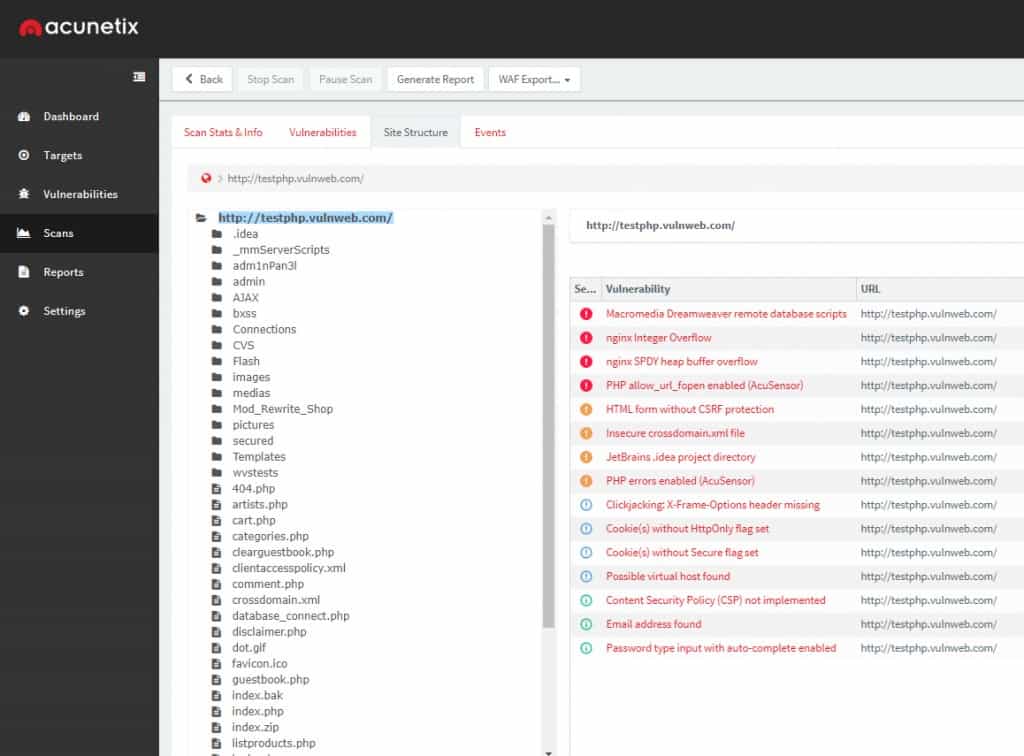
12. Acunetix
Acunetix is a web application security scanner and one of the top network security auditing software that can test for over 50,000 network vulnerabilities when integrated with OpenVAS. It discovers issues like open ports that leave your systems open to being compromised.
Key Features
- Web Application Security Scanner: Specialized in testing web applications.
- Integration with OpenVAS: Expands network vulnerability assessment capabilities.
- CI/CD Tool Interfaces: Facilitates DevOps workflows.
Why do we recommend it?
Acunetix offers a way to integrate OpenVAS into a CI/CD pipeline because it offers an integration of the free scanner into its own application security testing service. This integration is easier to manage in the Cloud version because, on that platform, both the application tester and the network scanner are fully integrated into one interface. Acunetix is known as a DevOps tool because it can be used to look for vulnerabilities in code that is under development and it can also work as a Web vulnerability scanner for operations teams.
OpenVAS scan results can be viewed through the Acunetix dashboard, which details the severity and status of vulnerabilities. The tool can also test for weak passwords on database servers, FTP, IMAP, SSH, POP3, SSH, Telnet, socks, and more.
There is also a configuration management feature that automatically detects misconfigurations in your network. You can use the feature to discover issues such as weak SNMP community strings or TLS/SSL ciphers that attackers can exploit. Having vulnerabilities listed allows you to organize your remediation and eliminate entry points more effectively.
Any issues you discover can be monitored with external tools including Jira, GitHub, and Microsoft TFS. The integrations give you the option to choose where you want to see your environment.
Who is it recommended for?
Businesses that develop their own Web applications will get the full benefit of the Acunetix system. However, it can be used as a standalone external vulnerability scanner for Web applications by operations teams. It excels in checking Web application code. If you want to use it with OpenVAS to get network security auditing, it is better to opt for the cloud SaaS package offered by Acunetix. The Acunetix system can be self-hosted on Linux, macOS, and Windows, but if you go down that route, you have to install OpenVAS separately on Linux and then manually link the two packages together.
Pros:
- Comprehensive Web Vulnerability Testing: In-depth examination of web apps.
- Configurable Management Features: Tailors scanning and reporting processes.
- Extensive Plugin Support: Enhances functionality with integrations.
Cons:
- Cost Consideration: Priced higher than many similar tools.
- Limited Free Trial: Access to demo rather than a full trial version.
Acunetix is worth a look for users who want an auditing tool that’s easy to navigate that can integrate with other tools. To discover the pricing of this tool, you need to get a quote. You can access a demo of Acunetix Online, which already has the OpenVAS system integrated.
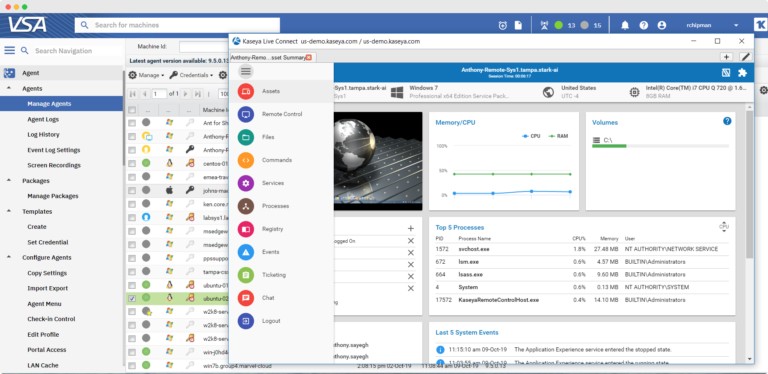
13. Kaseya VSA
Kaseya VSA is an RMM software that can discover and manage endpoints. The tool automatically stores audit information from devices throughout your network. View discovered devices in a list format and view data including name, OS type, CPU, RAM, disk volumes, license, manufacturer, and more. A search bar helps you to navigate and find the performance data you need.
Key Features
- Asset Management Capabilities: Comprehensive tracking of network devices.
- Security Management Tools: Includes patch management and EDR.
- MSP-Friendly Design: Ideal for service providers managing multiple networks.
Why do we recommend it?
Kaseya VSA is a remote monitoring and management (RMM) tool that was designed for use by MSPs. The package includes network discovery and mapping utilities, which lets you identify all of your equipment, logs that are getting old or out of date, and spot rogue devices connected to the network. The remote monitoring and management tools in the package extend to mobile devices and IoT equipment and it can also monitor cloud services and the internet connections to them. All of these monitoring phases produce system security information, which can be stored for compliance auditing. Security protection systems that can be added on to the Kaseya VSA package include a backup service, patching, EDR, DDoS protection, and a Web application firewall (WAF).
The platform itself is highly customizable. The user can create custom dashboards to manage their devices. The dashboard lets you track the status of a patch, agents, and operating systems. There are also customizable reports that you can use to manage devices.
Policy-based automation enables you to automatically complete tasks like software, patch, and antivirus deployment. On the communities, Automation Exchange, there are over 500 scripts included out-of-the-box you can use to configure your monitoring environment.
Who is it recommended for?
As already stated, Kaseya VSA was designed for use by managed service providers. However, it could also be used by in-house IT support teams. The main competitor on this list for Kaseya VSA is Atera. Kaseya recommends that MSPs use this tool in conjunction with Kaseya BMS, which is a professional services automation (PSA) package. IT departments should combine Kaseya VSA with the Vortex package, which is an IT Service Desk package. All of these systems are SaaS bundles that are hosted in the cloud.
Pros:
- Remote Monitoring and Management: Effective for overseeing distributed environments.
- Customizable Interface: Tailors dashboards to specific monitoring needs.
- Policy-Based Automation: Streamlines routine management tasks.
Cons:
- Complex Interface for Certain Features: Can be overwhelming for some users.
- Additional Cost for Certain Features: Some functionalities require extra payment.
Kaseya VSA is ideal for larger companies looking for an automated IT inventory management tool. To find out pricing details, you will have to contact the company directly for a quote. You can also start a 14-day free trial.
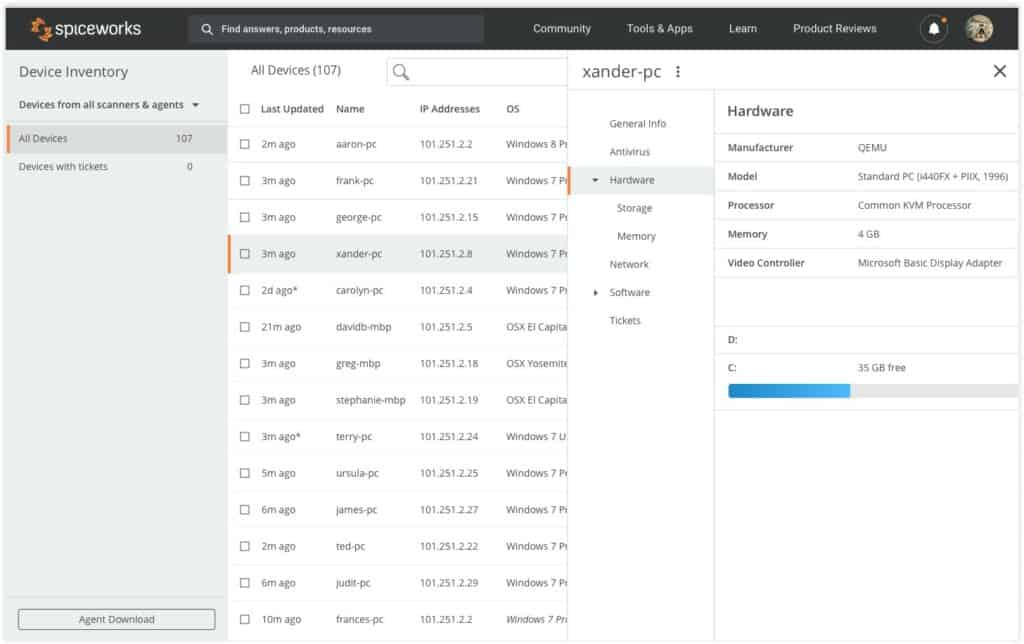
14. Spiceworks Inventory
Spiceworks Inventory is a free network inventory tool that is delivered in a Web interface. After signing up for a free account, you need to download a collector agent onto one of the computers on your network. That agent is available for Windows and macOS.
Once set up, this tool scans your network to compile an inventory. The scanner is launched by entering an IP address range. The scan results list installed software packages on each device as well as that computer’s manufacturer, MAC address, and open ports.
Key Features
- Free Network Inventory Tool: Cost-effective solution for device tracking.
- Web-Based Interface: Accessible from anywhere with internet connectivity.
- Customizable Reporting: Tailors inventory reports to specific needs.
Why do we recommend it?
Spiceworks Inventory is a free, ad-supported online system that is very easy to set up and use. This tool provides an on-demand scan of your network that compiles an inventory. The list details factors such as device type, make, model, and whether it has antivirus installed on it. It is also possible to get the scanner to run regularly on a schedule and email you an inventory report. There is also a companion Help Desk system available from Spiceworks and that is also free to use. Spiceworks offers very useful tools, such as connectivity testers that enable you to check on the availability of devices within your network and across the internet.
You can use the tool to configure email reports. The user can create customized reports and email them to other employees on a schedule. Customization options include the ability to select what columns to display.
For example, if you wanted to generate a report on whether devices had antivirus installed then you can select the AntiVirus Name, Antivirus Version, and AntiVirus Up-to-Date? Options to verify the device is protected.
Who is it recommended for?
This tool is ideal for small businesses and particularly oner-managers who don’t know much about IT but need to get to grips with tracking their network equipment. The system is Web-based and it will install an agent program on one of your computers in a guided process. This is just as easy as downloading a piece of software through an installer, which is a task that everyone has already performed. So, you don’t need specialist IT skills to get this service up and running.
Pros:
- Automatic Device Detection: Streamlines inventory process.
- Cross-Platform Support: Works with Windows and macOS.
- Easy to Use: Ideal for small businesses and less tech-savvy users.
Cons:
- Limited NOC Ticketing Functionality: Could benefit from enhanced features.
- Simplified UI: May lack depth for more complex network environments.
Spiceworks Inventory is an excellent tool if you want to take an inventory of Windows and Mac devices without paying anything upfront. The software is available completely free with support for unlimited devices and users. Download Spiceworks Inventory for free.
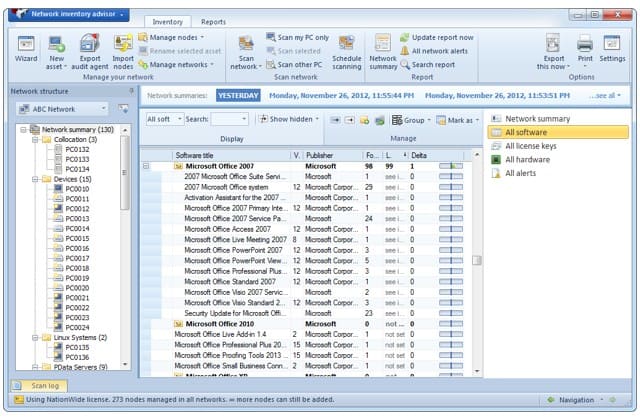
15. Network Inventory Advisor
Network Inventory Advisor is an inventory scanning tool that can automatically detect Windows, Mac OS, Linux, and SNMP-enabled devices. Device data is displayed in a list format detailing the OS and storage space of devices.
Key Features
- Hardware Asset Inventory: Tracks physical devices across the network.
- Software License Management: Helps maintain compliance with licensing.
- Multi-OS Coverage: Supports Windows, macOS, and Linux environments.
Why do we recommend it?
Network Inventory Advisor is a low-cost system monitoring and management tool that provides a network scan for asset inventory creation. The package will generate a database of all of your equipment and then scan each endpoint to compile a software inventory. The tool then provides periodic sweeps of the network to update those lists. Software management features support license management and highlight patch statuses but the package doesn’t include an automated patch manager.
You can navigate inventory data to view All license keys, All hardware, All software, All Alerts or a Network Summary. In the All Alerts view you can view a list of notifications on your environment. The notifications tell you about hardware/software changes and storage issues.
The software licensing management feature that can track software licenses. For example, the tool scans for serial numbers and license codes to help you keep your software up to date. This tool can collect software licenses for a range of providers including Microsoft, Symantec, Autodesk, Adobe, Corel, and more.
Who is it recommended for?
Although it is possible to buy a license for Network Inventory Advisor to track a network with a very large number of endpoints, this tool is most suitable for small businesses. You buy a perpetual license with a capacity limit. The smallest package available is for 25 devices. The software installs on Windows and macOS and it can scan endpoints running Windows, macOS, and Linux.
Pros:
- Comprehensive Device Tracking: In-depth inventory of network assets.
- Versatile Licensing Tracking: Manages various software licenses effectively.
Cons:
- Better for License Management: More focused on software tracking than security.
- Limited Trial Duration: Could offer a longer evaluation period for thorough testing.
Network Inventory Advisor is intended for those looking for a simple inventory management solution that can manage a range of devices. They offer a scalable pricing model starting at $89 (£68.65) for 25 nodes going up to an unlimited custom package. There’s a 15-day free trial.
Related post: File Activity Monitoring Software
16. Metasploit
Metasploit is an open-source penetration testing software for Windows, Mac OS, and Linux, that many companies use to test network defenses. Running a penetration test with Metasploit allows you to find vulnerabilities in your network from the perspective of an attacker. The Metasploit framework comes with a range of exploits with almost 500 different payloads you can use to simulate a cyberattack.
Key Features
- Penetration Testing Software: Simulates cyberattacks for security preparedness.
- Extensive Payload Options: Nearly 500 payloads for varied testing scenarios.
- Security Auditing Focus: Assesses network defenses against potential threats.
Why do we recommend it?
Metasploit Framework is a highly respected penetration testing tool for networks and Web assets. Its paid version, Metasploit Pro, is fully automated and is really a vulnerability scanner. However, those who want to perform a manual exploration of a system would be happy with the free version. Metasploit is a package of tools and they fall into two categories – system investigation tools and system attack tools. The exploration tools effectively document the security status of your network and if you go for the paid version you can get all of that work done at the push of a button.
The tool offers plugins that can integrate with other monitoring services such as Nessus Pro and Nmap. For example, you can import Nmap scans directly into Metasploit. The integrations that are compatible with these external services enable the security software to work alongside other tools in your cybersecurity strategy.
Who is it recommended for?
Metasploit is a tool that is designed for cybersecurity consultants rather than for network managers. Its main rivals aren’t on this list but can be found in The Best Network Penetration Testing Tools. The appealing feature of Metasploit is that it can be extended by adding in third-party tools and it is also possible to import the results of other security scanning tools, such as Nmap. You need to have specialist cybersecurity training to get the best out of this tool. Even the automated Metasploit Pro is more appropriate for use by a pen tester than by a network manager.
Pros:
- Free Version for Basic Use: Accessible for smaller-scale testing.
- Customizable Testing Options: Tailors tests to specific network environments.
Cons:
- Advanced Skill Requirement: Best used by cybersecurity professionals.
- Limited User Interface in Free Version: Requires comfort with command-line tools.
Metasploit is available as an open-source (Metasploit Framework) or commercial tool (Metasploit Pro). The commercial version includes additional features like network discovery and a remote API. To find out pricing information you’ll have to contact the company directly. There is a 14-day free trial available for the commercial version.
Choosing a network security audit tool
Auditing your network, managing your IT inventory, and checking for vulnerabilities is something that every company needs to do. Conducting simple tasks like maintaining an inventory of devices and regularly searching for configuration issues ensures that your network is prepared for the future. If you don’t regularly monitor your network infrastructure there’s no way you can manage new vulnerabilities effectively.
Network Security Auditing FAQs
How does an IT audit differ from a security assessment?
An IT security audit checks that specific security controls are in place. A cybersecurity assessment is a high-level study that determines the effectiveness of those cybersecurity controls and rates an organization’s cybersecurity preparedness. Audits follow a list of requirements, such as those specified by HIPAA or PCI DSS and assessments make sure a company is secure against all known current cybersecurity attack strategies.
How often should security audits be performed?
A system that is high risk or new should be audited quarterly. Stable systems can be audited twice a year.
How do you audit cloud security?
Cloud security audits are not much different to audits of on-premises systems. The audit will be tailored according to any standards that the company works to, such as HIPAA or PCI DSS.