Network Detection and Response (NDR) tools are becoming increasingly essential in the modern cybersecurity landscape. As cyber threats continue to grow in sophistication and volume, organizations must adopt advanced solutions to detect, analyze, and respond to potential security incidents in real-time. NDR tools provide continuous monitoring of network traffic, helping organizations identify unusual patterns, detect threats, and mitigate risks before they can cause significant damage.
Here is our list of the best network detection & response software packages:
- Barracuda Managed XDR Includes an entire security operations center to watch over your Barracuda XDR system and implement remediation for you. This is a cloud-based service.
- UnderDefense MAXI MDR Hire a team of cybersecurity experts to run your system security service for you or just contract them for on-demand advice for your in-house team.
- ExtraHop Reveal(x) This package is able to perform constant device discovery, SSL offloading, and traffic examination. Available as a network appliance or a SaaS platform.
- Gatewatcher AIonIQ This network detection and response (NDR) package is a physical or virtual appliance, gathering data through a packet sniffer and sending findings to a SIEM or a SOAR.
- Muninn This NDR package has two modules – one for detection and the other for response – that are driven by AI and are hosted on the cloud.
- CrowdStrike Falcon Firewall Management This cloud-based service interacts with your existing firewalls to collect data and pass back response instructions when it detects a threat.
- Cisco Stealthwatch Enterprise This service protects against DDoS attacks, intrusion, malware, and insider threats. Runs on Cisco’s cloud platform.
- Darktrace This cloud platform provides a vulnerability manager and an XDR for endpoints, networks, IoT devices, and industrial systems.
- Vectra NDR A SaaS package that scans network activity and enriches discovered threats by linking together events and providing annotated logs.
One of the main reasons NDR tools are necessary is the evolving nature of cyberattacks. Traditional security measures such as firewalls and antivirus software may not be sufficient to detect modern threats, including advanced persistent threats (APTs), insider threats, and zero-day vulnerabilities. These attacks are often designed to bypass traditional defenses, making it crucial for businesses to implement tools that can identify suspicious activity based on network behavior, even when it doesn’t match known attack signatures.
NDR solutions provide several critical capabilities for enhancing an organization’s security posture:
- Continuous Monitoring: NDR tools analyze network traffic in real time, allowing organizations to detect malicious activity as soon as it occurs, rather than after the fact. This quick detection is vital for limiting damage and minimizing response times.
- Anomaly Detection: By establishing baselines for normal network behavior, NDR systems can identify deviations that may indicate a security breach. This helps in recognizing threats that don’t fit conventional attack patterns.
- Automated Response: Many NDR tools come with automated response capabilities, enabling organizations to take immediate action, such as isolating affected systems or blocking malicious traffic, reducing the time it takes to contain a threat.
- Enhanced Visibility: NDR solutions offer deep visibility into network traffic, providing security teams with detailed insights into potential risks and allowing them to make informed decisions.
In today’s increasingly complex threat landscape, NDR tools are an essential part of any robust cybersecurity strategy, helping organizations stay one step ahead of attackers.
Understanding the Limitations of SIEM and EDR Tools
One common misconception is the belief that tools such as Security Information & Event Management (SIEM), Endpoint Detection and Response (EDR) solutions, and similar technologies can sufficiently protect the enterprise. But unfortunately, SIEMs have blind spots, and EDR tools provide only a ground-level view of suspicious processes and interactions within hosts on a network. EDR tools can be evaded or disabled by a determined attacker. Moreover, devices like IoT simply do not have the ability to run endpoint security software or analytics.
The Rise of Network Detection and Response (NDR)
But in recent times, organizations are embracing a concept known as Network Detection and Response (NDR) as a security strategy to address modern network security challenges. NDR is a new category of security solutions that complement and even go beyond the capabilities of log analysis tools such as SIEM and endpoint detection and response (EDR) products to provide an aerial view of the suspicious activities and interactions between all devices on the network. NDR enables organizations to protect their networks by analyzing their network activity without the headache of having to manage individual device software. It is rapidly emerging as a must-have capability in modern security operations.
How NDR Solutions Work
NDR solutions primarily use non-signature-based techniques such as machine learning, deep learning, statistical and heuristic analysis, and other techniques to detect suspicious traffic on a network. When the NDR tools detect suspicious traffic patterns, they raise alarms and where necessary provide an automatic response.
Choosing the Right NDR Solution
To select an appropriate network detection and response solution for your business, you need to consider a variety of factors. Firstly, you need to decide whether you will be best served by supervised or unsupervised machine learning. You also need to decide whether you will be best served by a managed, operated, or automated NDR solution. Other key questions to consider include; which response strategy will best meet your security goals, manual or automated? Does the solution enable alert-to-action automations? What is the false positive and false negative rate for the detections? Is the AI function of the NDR system wholly or partially dependent on rules? Is vendor support available in your region, and to what extent? What is the total cost of ownership?
The Best Network Detection & Response Software
With a variety of NDR solutions out there, choosing the right one for your business and budget can be challenging. Hopefully, this will guide you in the process of choosing an appropriate solution for your business.
Our methodology for selecting network detection & response tools
We reviewed the market for network detection and response solutions and assessed the options based on the following criteria:
- A system that can gather activity data from all points on the network
- The ability to interface with firewalls
- Access rights manager integration
- Automated responses
- Compliance reporting
- A free trial or a demo system that provides a free assessment period
- Value for money from a system that improves technician efficiency
Taking this list of requirements into consideration, we identified network defense systems that can implement automated responses to block intrusion and malware.
1. Barracuda Managed XDR

An SaaS extended detection and response tool that helps managed service provides (MSPs) gain an edge against cyber-criminals. The Barracuda Managed XDR goes one better by including a team of security experts as well a Security Operations Center (SOC) for 24×7 threat monitoring.
Key Features:
- SaaS XDR: A cloud-based extended detection and response solution.
- MSP-Friendly: Designed for managed service providers to offer as part of their services.
- Included Security Staff: Comes with a team of security experts and a Security Operations Center (SOC) for 24/7 monitoring.
- SIEM Functionality: Operates as a Security Information and Event Management system, using AI to detect threats.
Why do we recommend it?
Barracuda Managed XDR is a pass-through service that managed service providers can offer to their clients. The MSP doesn’t need to do anything other than add the XDR service to its price list. Barracuda provides ongoing system security monitoring through agents that are installed on each client’s site.
This service from Barracuda MSP, an MSP-dedicated division of Barracuda Networks, is designed as an upselling opportunity for managed service providers. Add this service to your price list and let Barracuda do all of the work.
Although XDR systems are praised for their ability to remediate detected threats automatically, false positives on breaches can cause legitimate traffic to be blocked, and no one wants that. This is why it is often necessary to involve an expert in response detection, which Barracuda MSP provides with this plan.
Staffing a Security Operations Center (SOC) can be a challenge, and sourcing cybersecurity experts in remote locations might be impossible, so this SaaS-with-staff proposal is the ideal solution that allows you to offer necessary services to your clients and keep up with the competition.
The detection system at the heart of this XDR package is actually a SIEM. Setting up this system to work for a client site requires downloading collectors and altering the settings of applications to ensure that they generate and forward the right log messages. That can be a time-consuming task, but don’t worry, the Barracuda team takes care of it.
The SIEM uses AI to speed searches through large volumes of data and identify potential indicators that need to be linked to further actions before they can be classified as threats. This service doesn’t rely on a checklist of IoCs but looks for anomalous behavior first. This means that it is able to spot zero-day attacks before their attack patterns are officially recognized.
Who is it recommended for?
This is a service offered by Barracuda MSP, which is a division of Barracuda Networks. This division specializes in providing security monitoring software to managed service providers and the managed service is an extra layer of service that provides MSPs with an extra product to offer their clients without them having to actually do anything.
Pros:
- Outsourced SOC: Provides a Security Operations Center for hire, reducing the need for an in-house security team.
- Subscription Service: Allows MSPs to offer advanced security services without additional effort.
- Automated Data Collection: Automatically gathers activity data and integrates with third-party tools.
- Customizable Reports: MSPs can create custom reports and analyses for clients.
Cons:
- Time Intensive: Initial setup involves installing collectors and configuring applications, which can be time-consuming.
The MSP isn’t kept out of the loop and you get a multi-tenanted dashboard that gives you views on the performance of the detection system for each client. It is possible to create custom reports and analyses to add value to the detection performed by Barracuda. You can request a demo to find out more about the XDR.
2. UnderDefense MAXI MDR
UnderDefense is a cybersecurity consultancy firm that offers a managed security service. The team will take over the running of your security system or you can get them on a support contract to advise your own cybersecurity team. The company doesn’t provide an off-the-peg security package. Instead, you choose your own combination of NDR, SIEM, EDR systems, etc., and the UnderDefense team will install and manage that software for you.
Key Features:
- Security Management Package: Comprehensive management of your security systems.
- Custom Solution: Tailored security setup with chosen components like NDR, SIEM, and EDR.
- Free Security Tools: Includes a Dark Web scanner, compliance guide, and risk assessment system.
- Compliance Management: Helps ensure your systems meet regulatory requirements.
Why do we recommend it?
Under Defense MAXI MDR provides a team of cybersecurity experts to run your network detection and response software. The consultants can advise you on software acquisition and install and run your security system. Alternatively, you can contract the team to advise your in-house cybersecurity department when problems are detected.
Although all of the software that this team will manage is from third-party providers, the group does provide some of its own systems. These include a Dark Web scanner, a compliance guide, and a risk assessment system. These three tools are available to any customer that signs up for a free account.
After setting up an account and trying the free tools, you can engage with an UnderDefense consultant to explain your cybersecurity needs. This can include the installation and management of a network detection and response package or other security systems.
The UnderDefense team will create a SOAR system that draws in signals from all of your individual security systems and join them together. This security operation center software will automatically send out response instructions to on-premises tools to shut down detected attacks.
The UnderDefense system is effective against automated attacks, intrusion, insider threats, and account takeovers. The consultants don’t need to come to your site. Instead, they access your system remotely from the UnderDefense offices. This creates a saving on office space and IT facilities.
Who is it recommended for?
The UnderDefense solution is suitable for businesses that like to outsource their IT services. Just as you can contract an MSP to provide IT support, you can strike a deal with UnderDefense to become your cybersecurity team. This is a good option for businesses that can’t find or afford to hire security experts.
Pros:
- Expert Consultancy: Provides access to a team of cybersecurity experts for management and advice.
- Remote Management: Security management is conducted remotely, reducing the need for on-site resources.
- Compliance Support: Offers tools and guidance to maintain regulatory compliance.
- Dark Web Monitoring: Includes a tool to scan the Dark Web for potential threats.
- Risk Assessment: Provides a system for assessing and managing security risks.
Cons:
- No Public Pricing: Pricing details are not readily available and require direct consultation.
- Third-Party Software Dependence: Relies on third-party security tools, which may require additional coordination.
Access a free account of UnderDefense to get started. This gives you the Dark Web scanner, compliance guide, and risk assessment template library. From that point, you can liaise with an UnderDefense cybersecurity consultant to set up a security support contract. Start by registering for the free demo.
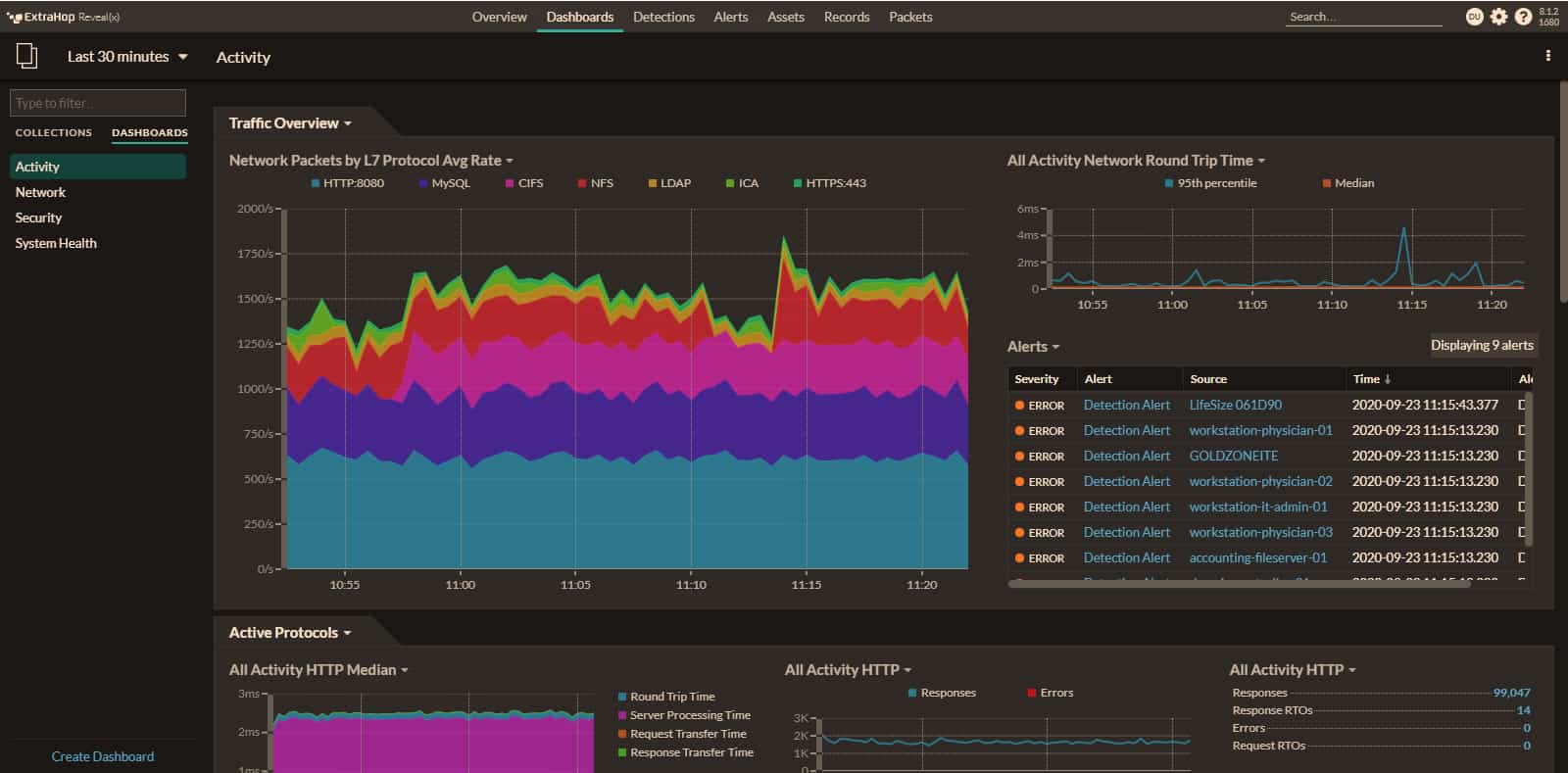
3. ExtraHop Reveal(x)
ExtraHop Reveal(x) is a detailed and flexible NDR solution ideal for any security operations teams that need better visibility into network behavior in their environment. It helps organizations identify threats, automate data gathering, and correlation, as well as response investigation. This in turn helps to improve overall cybersecurity hygiene and meet regulatory requirements.
Key Features:
- Purchase Options: Available for outright purchase or subscription.
- AI-Based Detection: Utilizes artificial intelligence for identifying threats.
- Automated Orchestration: Streamlines response actions automatically.
- Real-Time Monitoring: Provides continuous monitoring and post-intrusion insights.
- Traffic Decryption: Can decrypt encrypted traffic, including SSL and TLS.
Why do we recommend it?
ExtraHop Reveal(x) is a security monitoring package that includes a discovery cycle. This system is able to map and track network devices, endpoints, and cloud platforms. Reveal (x) Enterprise is the main NDR package from ExtraHop with the 360 version evolving into a cloud platform tracker.
ExtraHop Reveal(x) NDR software is able to detect suspicious network behaviors, prioritize investigations according to the risk score, and automate response efforts. It automatically discovers and classifies every transaction, session, device, and asset in your enterprise up to 100Gbps. One advantage of Reveal(x) is its out-of-band deployment model, which makes the operation covert so that attackers won’t know they’re being monitored. ExtraHop Reveal(x) NDR solution comes in two flavors:
- ExtraHop Reveal(x) Enterprise This is a self-managed deployment option that can be deployed on-premises or in the cloud, providing complete east-west visibility, real-time threat detection, and response inside your network perimeter.
- ExtraHop Reveal(x) 360 This is a SaaS-based deployment option that completely eliminates the installation and management overhead of the self-managed option. With Reveal(x) 360, you can unify security controls across on-premises, cloud, and IoT environments. It leverages native integrations with cloud service provider packet mirroring features to provide agentless visibility, detection, and response.
Some of the key features and capabilities of Reveal(x) include:
- Reveal(x) can be configured to monitor and passively decrypt encrypted traffic, including traffic protected by Perfect Forward Secrecy such as SSL and TLS
- Machine learning using 5000+ features
- Automated detection, investigation, and response via integration with third-party security tools such as Crowdstrike and Phantom
- Automated inventory—discovering and classifying network devices
- Peer group detection—sort devices into behavioral groups
Who is it recommended for?
ExtraHop Reveal (x) Enterprise is the edition to go for if you want network detection and response. This package is able to monitor physical and virtual environments and it can also extend out to cloud platforms. So, the service is best suited to companies that run hybrid environments.
Pros:
- Enterprise Design: Tailored for enterprise use to aid system administrators.
- Intuitive Interface: Features a user-friendly interface with a dark mode option.
- Automated Network Issue Detection: Automatically identifies network issues and assists with correlation.
- Packet Inspection: Offers inspection of SSL and TLS packets for enhanced security.
- Comprehensive Monitoring: Supports both real-time monitoring and post-intrusion investigations.
Cons:
- Complex Licensing: The licensing model can be either subscription-based or perpetual, adding complexity.
ExtraHop Reveal(x) NDR licensing can be either subscription-based or perpetual. The subscription-based option offers time-based access to ExtraHop NDR software that is installed on purchased hardware or on a virtual machine. For the perpetual licensing option, you purchase ExtraHop hardware and software.
The ExtraHop Reveal(x) is a powerful NDR tool that can help your organization detect and respond to anomalous network traffic patterns. However, in order to get the best value out of this product, you must be prepared to go through a steep learning curve and gain a good technical understanding of key protocols and application components.
4. Gatewatcher AIonIQ
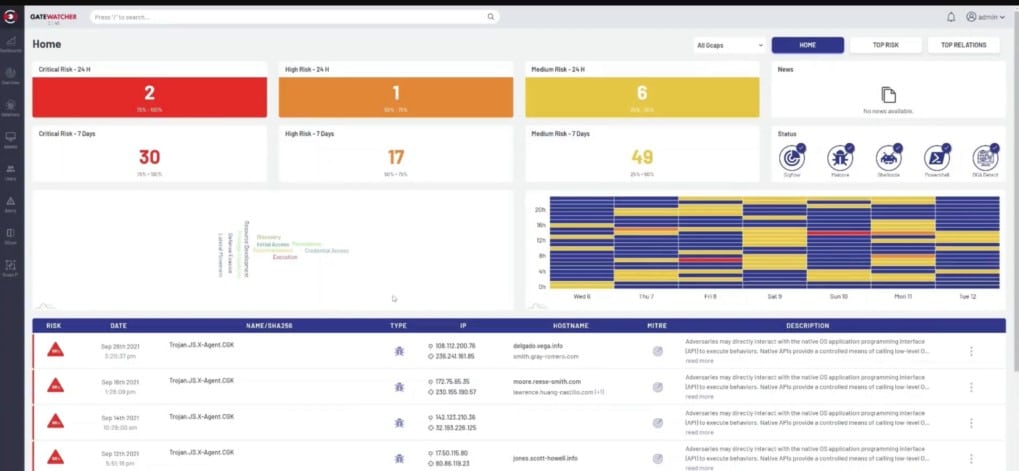
Gatewatcher AIonIQ is a cloud-based network detection and response (NDR) platform that operates on your network through the installation of two units; a packet sniffer and a server. This data-gathering tool captures all traffic by accessing a SPAN port on a switch or using a TAP. All traffic flows through the analyzer, which sends summaries to the Gatewatcher server.
Key Features:
- Traffic Capture: Captures all network traffic via SPAN port or TAP.
- Packet Analysis: Processes packets to identify threats and anomalies.
- Behavioral Profiling: Creates profiles for users and traffic sources to detect unusual behavior.
- Automated Responses: Automatically responds to threats by blocking IP addresses or suspending user accounts.
- Tool Integration: Integrates with other security tools to enhance threat detection and response.
Why do we recommend it?
Gatewatcher AIonIQ examines actual network traffic to look for intrudes and malware activity. The system creates a profile for each user and external traffic sources. It looks at which user accesses which endpoints and which locations they usually work from. Other factors that the system notes include the applications used by that account. The system then alerts on changes in behavior.
The detection system of AIonIQ works with two strategies. The first is an anomaly detection service that logs all of the activities of each user account and external source and then alerts on sudden changes in that pattern, which would indicate an intruder.
The second strand of the AIonIQ detection system is a search for indicators of known malware activity patterns. Thus, the Gatewatcher service protects systems against both manual and automated threats.
The AIonIQ system will raise an alert in the event of a threat detected. The service is also able to automatically respond to these threats by blocking a suspicious IP address at the firewall or interfacing to the local access rights manager to suspend the offending user account.
The tool would deal with malware by interfacing to the endpoint detection and response (EDR) package on that device – if there is one. The response mechanism can be turned off if a company has a Security Orchestration, Automation, and Response (SOAR) tool or a Security Information and Event Manager (SIEM) operating for threat response. In that case, the Gatewatcher system will forward threat analysis to those other systems for action.
Who is it recommended for?
This is a sophisticated system that uses machine learning to constantly adjust detection strategies and reduce the incidence of false positive reporting. The package can work with other security tools to increase response efficiency. The system is designed for the higher end of the SMB market and large organizations.
Pros:
- Automated Threat Response: Automatically responds to detected threats by blocking IP addresses or suspending user accounts.
- Tool Integration: Interfaces seamlessly with other security tools, enhancing overall security posture.
- SIEM and SOAR Coordination: Coordinates with SIEM and SOAR systems for comprehensive threat response management.
Cons:
- Pricing Transparency: Requires registration to obtain pricing information.
The Gatewatcher system is implemented as a physical network device or a virtual appliance. The software version runs over a VM or containers, so it can run on any operating system. You can register for a free demo and pricing information.
5. Muninn

Muninn is a cloud-based service that operates as two units: AI Detect and AI Prevent. This is an NDR and the AI Prevent unit is the response part of the formula rather than a vulnerability manager. This package is also available as a managed service.
Key Features:
- Operates Within the Network: Monitors and analyzes network traffic to identify threats.
- Threat Detection: Uses AI to detect insider threats and account takeovers.
- SaaS Package: Cloud-based service for flexible deployment and scalability.
Why do we recommend it?
The Muninn platform scans traffic to identify insider threats and account takeovers. The system can also be extended into endpoint activity scanning through the installation of agents. The service’s cloud base means that it isn’t constricted within one network and so it can examine traffic out to remote workers as well.
The technicians on the Muninn team set up rules that the scanner needs to look for and these are updated when new attack strategies come to light. These detection rules look for “indicators of compromise.” an IoC is a chain of events. They are important because each step might seem innocent and it is only when all of the elements are considered as a group that it becomes apparent that the activity is an attack.
An NDR’s detection system needs to scan all traffic for one of the IoCs in its list but many of the steps when considered individually represent normal activity. For example, actions opening a file on a server or sending a file with FTP could legitimately occur many times in a day within an organization. Therefore, an NDR needs more power than just the ability to work out what each packet’s purpose is.
The strategy of looking for chains of events involves recording every event. The actions of each conversation need to be linked together. When a chain fits a pattern of a threat, the system pays closer attention. However, at the same time, the detection system needs to keep monitoring events in all other conversations.
Network threat detection requires a lot of event records and the Muninn system uses AI to try to shorten the time it takes to identify a chain. This is important if you want to stop threats in progress rather than just discover that a cyberattack has recently occurred.
This package is a network intrusion prevention system (NIPS). Such systems implement automated responses by working through playbooks. The AI Prevent system scans through this database of rubles and matches the detected chain of action to the appropriate playbook. The system uses an AI-based decision tree to enable the right response to be implemented quickly.
Who is it recommended for?
The response section of this platform is called AI Prevent because its entire purpose is to stop threats while they are underway. So, it needs to be fast. This is a suitable package for a mid-sized or large organization. The higher the value of the data that a company holds the more value that business will get out of this protection system.
Pros:
- Scalable Pricing: Offers a pricing model that scales with the size of the business, making it accessible for small to large organizations.
- Fast Detection: Utilizes AI to rapidly identify and respond to threats in real-time.
- Automated Response: Implements automated threat responses using AI-based decision trees and playbooks.
Cons:
- No On-Premises Version: Available only as a cloud-based solution, which may not suit all organizations.
- No Free Trial: While a free demo is available, there isn’t a free trial period to test the full capabilities.
The pricing process starts with a minimum package for a company with 40 employees and 20 servers. The price for that size of business works out at about $800 per year ($67 per month), which is not out of the reach of the budgets of small businesses. There isn’t a free trial for the Muninn package but you can request a free demo.
6. CrowdStrike Falcon Firewall Management

CrowdStrike Falcon Firewall Management is a SaaS platform that coordinates the actions of your existing endpoint firewalls. The Falcon platform is a family of products that provide cybersecurity for sites. All the tools on the platform, including the Firewall Management unit, enhance an on-device package, called Falcon Prevent, which is an anti-virus system and also acts as an agent for all of the other Falcon services.
Key Features:
- Coordinates Firewalls: Manages and coordinates the actions of existing endpoint firewalls.
- Exploits Third-Party Tools: Enhances the capabilities of third-party firewall software and hardware.
- Implements Security Policies: Allows the creation and enforcement of comprehensive security policies.
- Automates Threat Responses: Automates responses to detected threats through coordinated firewall actions.
- SaaS Package: Cloud-based service for flexible and scalable firewall management.
Why do we recommend it?
CrowdStrike Falcon Firewall Management is one in a list of Falcon products that can be bought in a bundle. This module coordinates security activity between your existing firewalls. However, it does not provide any firewall software or hardware. The service enables you to set up a security policy and then it will apply it.
The Firewall Management system implements its security controls through the endpoint firewalls that share a device with a Falcon Prevent installation. Falcon Prevent is available for Windows, macOS, and Linux.
Firewalls are able to pick up circulating network traffic, not just those packets traveling in and out of the protected device. Therefore, stringing together firewall activity creates a network threat detection and response system. One drawback of this approach is that you need to install Falcon Prevent on every endpoint in order for Falcon Firewall management to work effectively.
The CrowdStrike Falcon Firewall Management system allows you to formulate a network security policy and then enforce it by manipulating the settings of your firewalls. The cloud-based console includes a library of templates that guide you through the process of creating a security policy. The system will then apply this finished policy to all firewalls on your network or to groups of firewalls, according to your definitions.
The new firewall settings will include a reporting mechanism, so you can see traffic throughput data in the Falcon console. The system will also search for network-bound threats, such as intruder attempts to access endpoints or the transmission of malware as it is blocked.
The live status reports show activity around the network as each firewall contributes activity information. Thus, if you have malware attempting lateral movement, you can see how the attack makes attempts on each device.
Who is it recommended for?
This tool is based in the cloud and, although it can be used as a standalone product, you are more likely to get it as part of a Falcon bundle. The Firewall Management unit is part of the Falcon Pro bundle, which provides endpoint protection and it can be bought as an add-on to the Falcon Elite bundle, which is based on an XDR.
Pros:
- Optimized Firewall Protection: Enhances the effectiveness of existing firewalls through centralized management.
- Coordinated Security: Ensures consistent security policy enforcement across all endpoints.
- On-Site Agents: Utilizes existing endpoint firewalls as agents for network-wide threat detection.
- Policy Creation Assistance: Provides templates and guides for creating robust security policies.
- Compliance Reporting: Includes mechanisms for compliance reporting and monitoring.
Cons:
- No Firewall Software Included: Relies on existing firewall software and hardware, which must be managed separately.
- Limited Network Device Visibility: Cannot directly monitor network devices like switches and routers.
One big hole in the visibility of this package is that it isn’t able to see what activity is going on at each network device, such as switches and routers. However, the philosophy behind the strategy is that ultimately, even if hackers tamper with switches, their ultimate goal is the data or other resources held on endpoints. You can get network configuration management software to protect the settings of network devices. You can start a 15-day free trial.
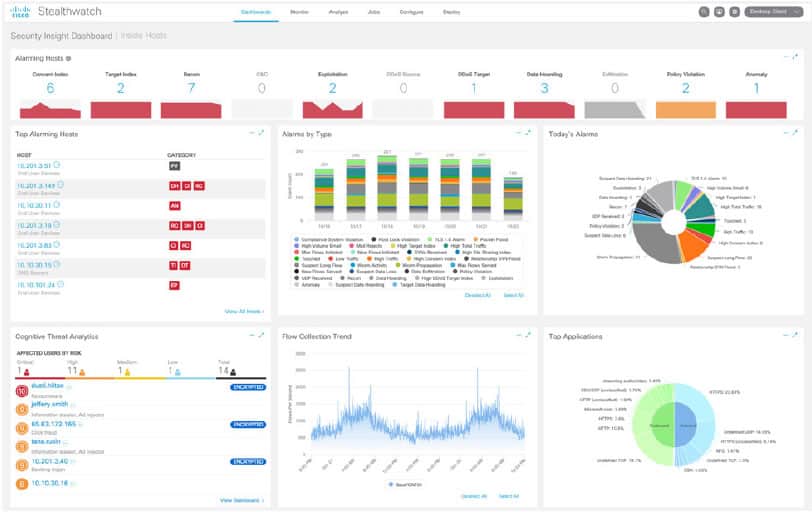
7. Cisco Stealthwatch Enterprise
Cisco Stealthwatch is an agentless Network Traffic Analysis (NTA) NDR solution that uses a combination of behavioral modeling, machine learning, security analytics, and global threat intelligence to detect and respond to threats such as ransomware, distributed-denial-of-service (DDoS) attacks, unknown malware, and insider threats. Stealthwatch can be deployed on-premises as a hardware appliance or a virtual machine called Stealthwatch Enterprise, or cloud-delivered as a SaaS solution called Stealthwatch Cloud.
Key Features:
- Network Traffic Scanning: Continuously scans network traffic to detect anomalies.
- Behavioral Analysis: Utilizes behavioral modeling to identify threats.
- DDoS Detection: Identifies Distributed-Denial-of-Service (DDoS) attacks in real-time.
- Encrypted Traffic Analytics: Analyzes encrypted traffic without decryption.
Why do we recommend it?
Cisco Stealthwatch Enterprise builds on all of the history that Cisco Systems has in network technology. This company is a major provider of switches and routers and it invented the NetFlow and IPFIX systems for network activity statistics collection and storage. This monitor uses those protocols to gather activity statistics and spot anomalies.
Stealthwatch provides enterprise-wide visibility from the private network to the public cloud and applies security analytics to detect and respond to threats in real-time. It examines traffic metadata such as NetFlow or IPFIX (Internet Protocol Flow Information Export) to build a better picture of activities within the network, which in turn can be used for identifying behavior-based anomalies. Stealthwatch can perform analytics even on encrypted traffic without breaking the encryption; and it comes integrated with Cisco SecureX and Cisco ISE platform to provide additional contextual data and boost response capabilities respectively.
Some of the primary use cases include:
- Real-time threat detection
- Incident response and forensics
- Network segmentation
- Network performance and capacity planning
There are three main components that make up the core of Stealthwatch Enterprise: the Flow Rate License, Flow Collector, and Management Console.
- Flow Rate License This is required for the collection, management, and analysis of network flows. It also defines the volume of flows that may be collected. The license is based on flows per second (fps) and may be combined in any permutation to achieve the desired level of flow capacity.
- Flow Collector The Flow Collector just as the name implies collects and leverages flow data such as NetFlow, IPFIX, and other types of flow data from switches, routers, firewalls, endpoint devices, and proxy data sources to provide comprehensive network visibility.
- Management Console The Stealthwatch Management Console aggregates, organizes, and presents analysis from up to 25 Flow Collectors, the Cisco ISE, and other sources. It uses graphical representations of network traffic, identity information, customized summary reports, and integrated security and network intelligence for comprehensive analysis.
Who is it recommended for?
You don’t have to be operating Cisco network devices in order to use this package. However, you should check that your switches and routers have IPFIX and/or NetFlow capabilities. If they don’t, they will be invisible to this security package. Run it as a virtual appliance or get it as a SaaS package.
Pros:
- Agentless Monitoring: Provides lightweight endpoint monitoring without the need for agents.
- Flexible Deployment: Available as both cloud and on-premise solutions.
- Advanced Threat Detection: Leverages behavior analysis and anomaly detection to thwart threats.
- Detailed Dashboards: Offers comprehensive live dashboards and reporting for real-time insights.
Cons:
- Enterprise Focus: Better suited for large enterprise environments.
Other optional licenses and components which can be added to enhance functionality include Cisco Stealthwatch Endpoint License—to extend visibility to end-user devices, Cisco Stealthwatch Cloud—to provide visibility and threat detection within the public cloud (AWS, Azure, Google), Cisco Stealthwatch Threat Intelligence License—provides an additional layer of protection against botnets and other attacks, Flow Sensor and the UDP Director components. Stealthwatch licenses are available as a one, three, and five-year term subscription, depending on your need and budget.
One unique thing about Stealthwatch is the fact that it is part of a broad security portfolio of security devices from Cisco, and has evolved and matured in capability and functionality over the last 20 years. However, the product is best suited for a Cisco infrastructure environment and covers areas beyond NDR function which some consider too broad and less deep. Furthermore, like most Cisco products, the setup process can be complicated. You need someone on your team with Cisco experience to maximize value from this product.
8. Darktrace
Darktrace is a cloud platform that offers vulnerability management plus threat detection and response for all corporate IT assets. The modules of the AI-driven system are divided into Prevent, Detect, Respond, and Heal categories. This is a comprehensive and complicated system that protects networks, endpoints, email systems, cloud platforms, IoT devices, and industrial systems.
Key Features:
- Vulnerability Management: Identifies and assesses security weaknesses across all assets.
- Threat Detection: Detects live threats using AI-driven analysis.
- Automated Responses: Automatically responds to threats by blocking access or suspending accounts.
- Email Security: Scans emails for phishing attempts and suspicious activities.
Why do we recommend it?
Darktrace is a cutting-edge system that is constantly evolving to keep ahead of the technologies used by rivals. The platform provides both preventative measures and live threat detection. Its systems are able to interpolate threats, which enables it to spot phishing attempts and credentials theft as well as security weaknesses.
The Darktrace service is a cloud-based platform and you can set it up to monitor any asset no matter where it is located. The system scans all of your systems from multiple sites to cloud platforms and it assesses each device for risk. Automated remediation systems can kick in at this point to identify configurations or software updates that need to be implemented for system hardening.
Darktrace has recently been through a complete overhaul, simplifying its structure and reorganizing its modules into security management phases. This service provides just about all of the software that a Security Operations Center would need. Its units include activity logging and compliance reporting, which are generated automatically to save technicians time. Whether or not you also need a SIEM would be up to your own assessment.
The security platform is very good at activity tracking and it looks for credentials theft attempts by scanning emails. The service looks for red flags such as similar domains, embedded URLs that lead to pages other than the ones displayed in the link text, and other phishing tools.
While deploying AI to try to block credentials acquisition, the tool also provides AI-based activity logging, which looks for a pattern of standard behavior per user account and then alerts on sudden changes in activity. This could identify an insider threat or an account takeover. Simultaneously, the vulnerability scanner will look at user accounts and groups, identifying weak security through permissions that are inappropriately wide or signs that accounts have been abandoned.
The live threat detection service operates a SIEM-like service, scanning network activity and endpoint processes for known malicious actions, files, and system changes. The cloud-based system reaches out to on-premises equipment, cloud platforms, and security tools to block access to suspicious IP addresses and suspend user accounts.
Who is it recommended for?
The client list of Darktrace includes very large organizations, such as Anheuser-Busch, Airbus, and The Royal Mint. This indicates that the Daktrace system is suitable for large businesses and not appropriate for SMBs. The platform is able to simultaneously monitor sites all over the globe and cover cloud platforms as well as on-premises assets.
Pros:
- Comprehensive Security Console: Offers a detailed and attractive interface for centralized security operations.
- Preventive and Live Detection: Provides both preventative measures and real-time threat detection.
- Hybrid System Security: Suitable for securing both on-premises and cloud-based systems.
- Broad Asset Coverage: Extends protection to network devices, endpoints, cloud platforms, and IoT devices.
Cons:
- Complexity: Requires a dedicated team to manage the system effectively due to its complexity.
The Darktrace system can extend security coverage to IoT devices and shopfloor systems, so there isn’t one single industry sector that this service applies to – it can protect any kind of business. However, it is complicated and it needs a team to manage it. The best way to investigate the Darktrace system is to get the free trial.
9. Vectra NDR
The Vectra NDR package is a cloud-based system that installs agents on the sites and cloud platforms that you run. The console is available on the cloud and you also have the option to download its software and run it on your computer. Furthermore, all of the threat-hunting data processing is carried out on the Vectra cloud servers.
Key Features:
- Event Correlation: Links seemingly unrelated events to identify threats.
- IoC Database: Utilizes an extensive database of indicators of compromise.
- Response Options: Allows customization of threat response actions.
- Endpoint Activity Monitoring: Monitors endpoint activities in addition to network traffic.
Why do we recommend it?
Vectra NDR is an AI-driven system with a unique threat identification system. The proprietary Attack Signal Intelligence package is an AI system that links together seemingly unrelated events to uncover a threat. The way the service deals with detected threats is up to the way you set the service up.
The Vectra NDR goes beyond the network and looks at activities on endpoints as well. It also refers to access rights management services and other security packages, such as firewalls. The extension of detection outside the network enables the system to examine communications without acquiring the responsibility for communication authentication and encryption, so it doesn’t implement SSL offloading. Instead, the tool examines network traffic as it is decrypted on the destination device.
The security service has a list of Indicators of Compromise (IoCs), which provide a matrix of threatening behavior. For example, one activity might be innocuous but represents a threat when combined with other, seemingly unrelated actions. Intruders could evade traditional threat detection systems by operating different attack-enabling actions through different accounts – Vectra NDR would spot such deceptive methods.
So, the NDR looks out for a typical action that could evolve into a threat and then brings up a list of likely follow-up actions. If none of those expected suspicious activities occur, the Vectra system escalates the security alert. If another suspicious action, which is on the list of evolving threats occurs, the system heightens the alert. This detection carries on, upgrading suspicious activity to a potential threat, and on to a certain threat.
The service can implement three possible actions on the detection of a threat and it is up to you how you set the Vectra system up. Those options are:
- An advisory alert for decision-making by a technician
- Automated response to shut down the account involved
- Packaging of activity logs for forwarding to a SIEM
So, you can get the tool to deal with a threat, get it to forward information to another tool, which you would expect to shut down the attack, or let a security analyst deal with it.
Who is it recommended for?
The Vectra NDR system is suitable for large and mid-sized businesses. There isn’t a price list and there is no free edition, so the service might not appeal to small businesses. The package is particularly useful for companies that operate hybrid environments that involve multiple sites and cloud services.
Pros:
- Comprehensive Monitoring: Extends threat detection beyond the network to include endpoints.
- Lateral Movement Detection: Identifies lateral movements and communication with command-and-control servers.
- Customizable Responses: Provides multiple options for threat management, including automated responses and advisory alerts.
Cons:
- Lack of Pricing Transparency: No publicly available pricing information.
- Cloud Dependency: Relies on cloud servers for data processing, which may not suit all environments.
The core of the Vectra system runs on the cloud so you sign up for the package online. You can access a demo to get to know how the Vectra NDR works.
Network Detection and Response FAQs
What is NDR and EDR?
Endpoint detection and response (EDR) protects servers and desktop computers; network detection and response (NDR) protects networks from malicious activity, which also protects endpoints.
Why is NDR needed?
Network detection and response (NDR) automates network security and extracts maximum value from network security tools by centralizing the collection of activity data and performing threat detection from a unified stance. Coordination with existing security tools removes the need to duplicate security systems at key locations around the network.
What is XDR in cyber security?
XDR extends network and endpoint detection and response systems by adding orchestration to the coordination features of those tools. XDR can be tuned to implement the requirements of specific data protection standards.